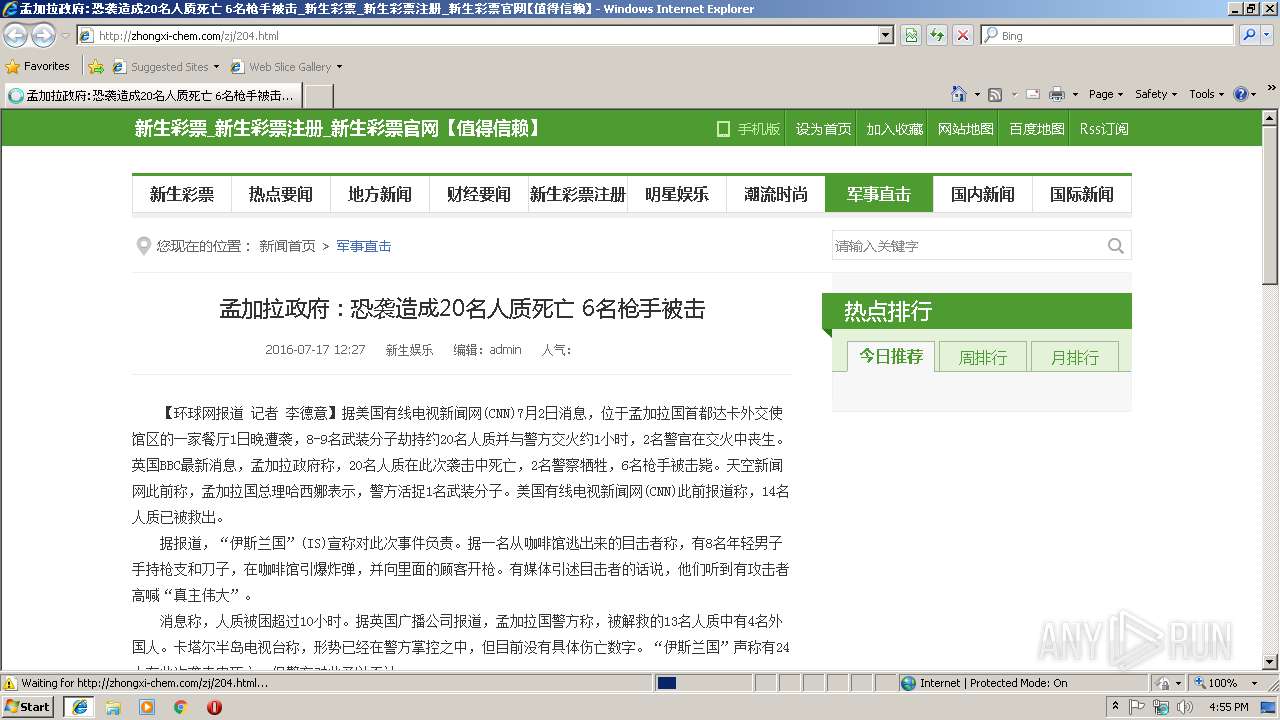
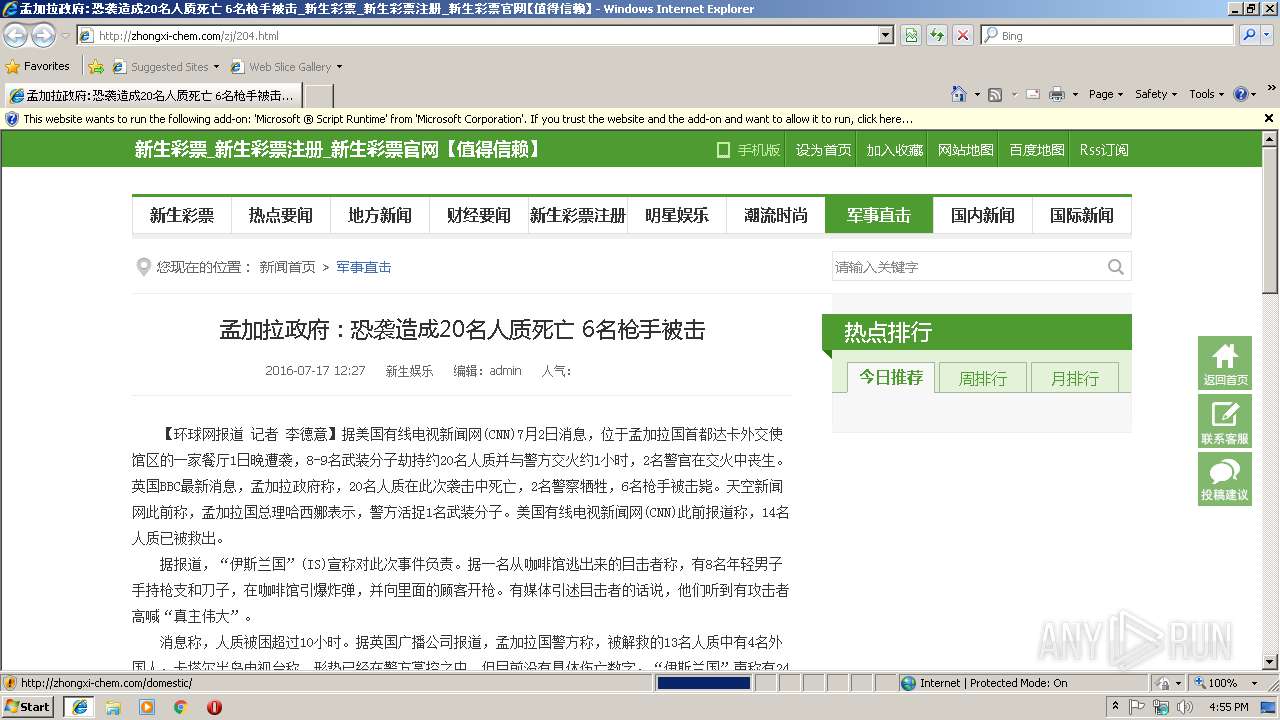
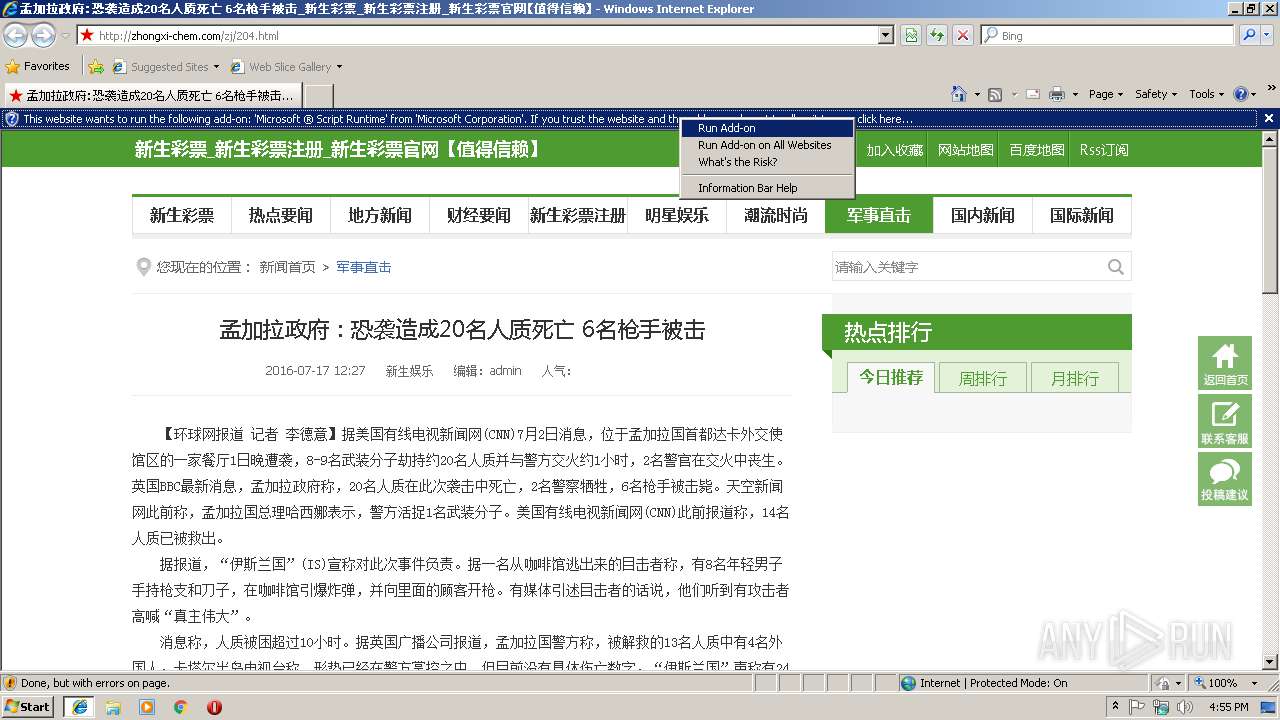
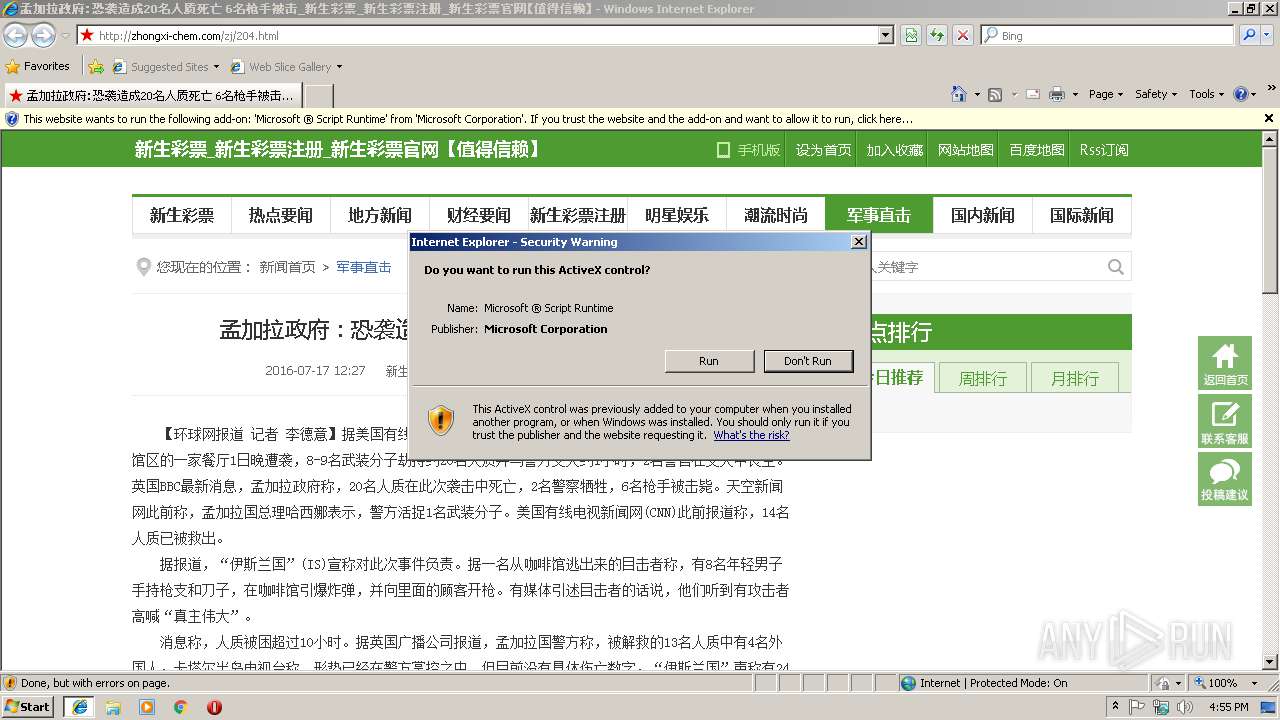
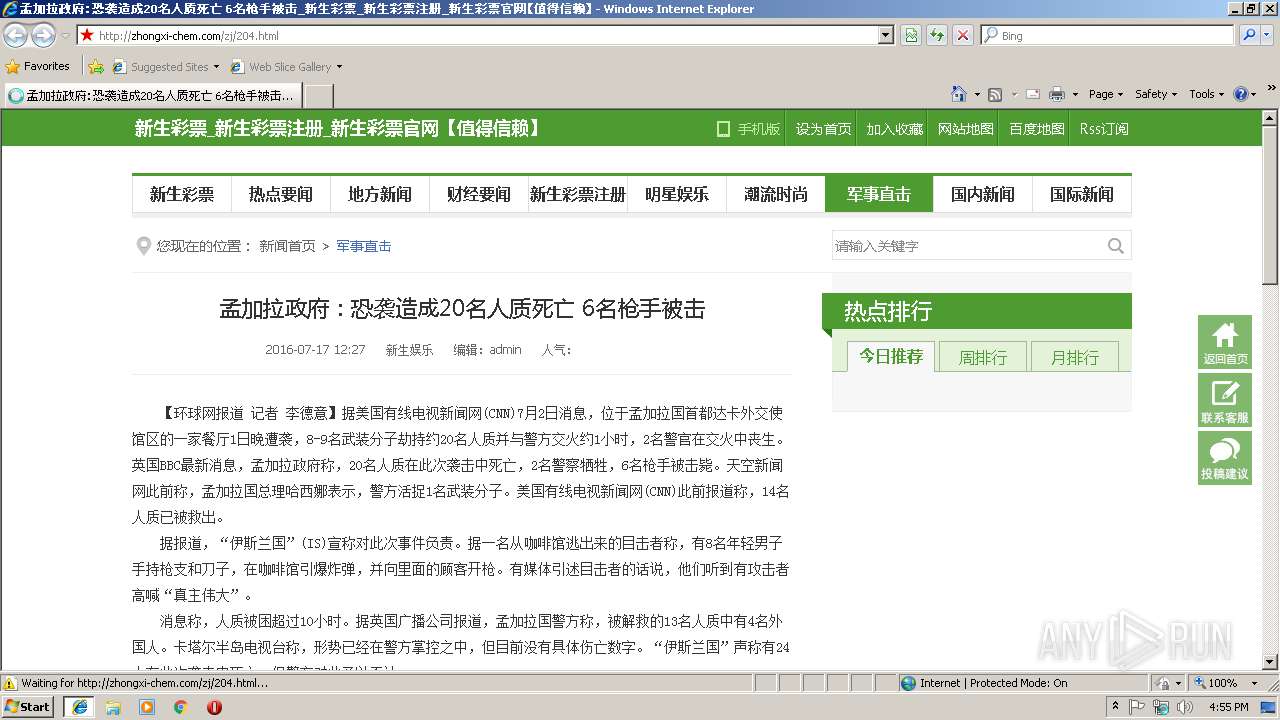
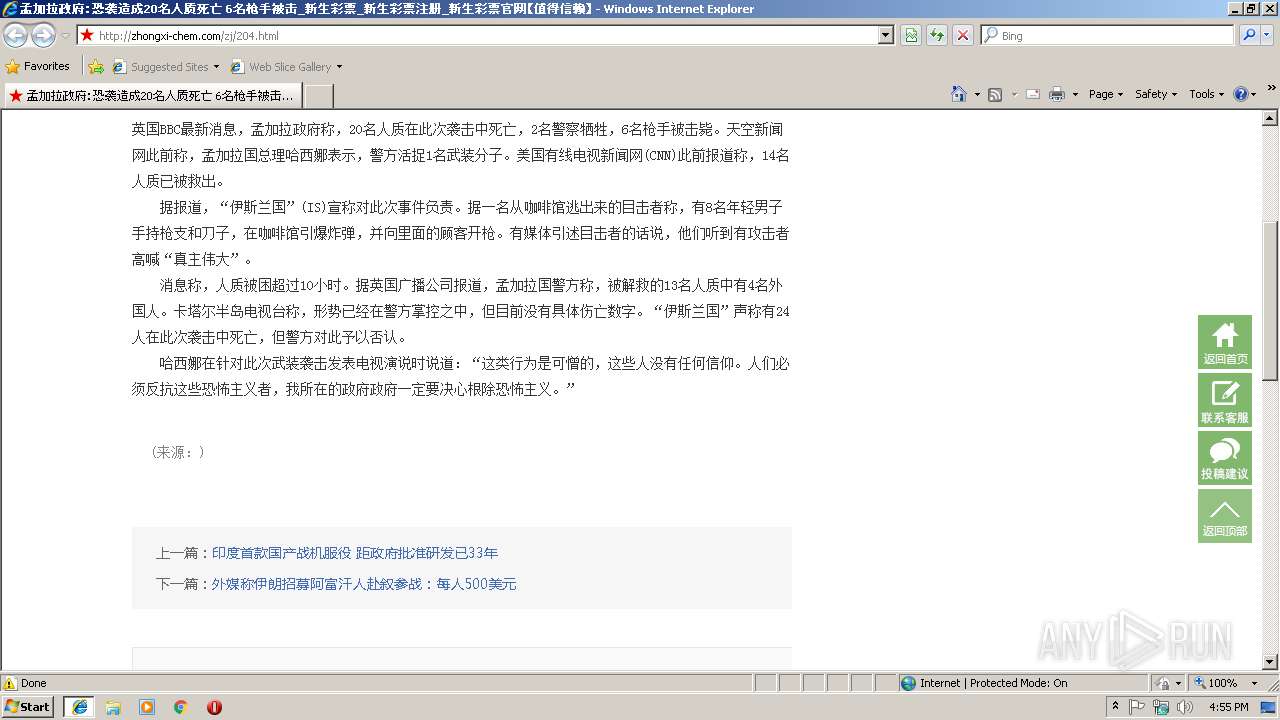
| URL: | http://zhongxi-chem.com/zj/204.html |
| Full analysis: | https://app.any.run/tasks/58087764-606a-45ba-956c-1c0fa76d49ae |
| Verdict: | Malicious activity |
| Threats: | Ramnit is a highly modular banking trojan and worm that evolved from a file-infecting virus into a powerful cybercrime tool. It specializes in financial fraud, credential theft, remote access, and malware delivery, being a serious threat to businesses and individuals. First spotted in 2010, Ramnit became popular after the 2014 takedown of the GameOver Zeus botnet, as cybercriminals sought alternatives for banking fraud. |
| Analysis date: | December 06, 2018, 16:54:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3E8ACF3E0FFAF01AA620A921DBF58AD9 |
| SHA1: | 70D984316482F4DA60C5430B969A077633A37189 |
| SHA256: | 6CAE5A5D692334AA6F7CF26FF523E841235B4047E0C0F7F2D9C1C413AF250743 |
| SSDEEP: | 3:N1KEX1227LQ:CEJ8 |
MALICIOUS
RAMNIT was detected
- iexplore.exe (PID: 3716)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3440)
Reads Internet Cache Settings
- iexplore.exe (PID: 3716)
Reads internet explorer settings
- iexplore.exe (PID: 3716)
Changes internet zones settings
- iexplore.exe (PID: 3440)
Reads settings of System Certificates
- iexplore.exe (PID: 3716)
Creates files in the user directory
- iexplore.exe (PID: 3716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
33
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3440 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3716 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3440 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
444
Read events
373
Write events
68
Delete events
3
Modification events
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {AFE32107-F977-11E8-834A-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C00040006001000370009001603 | |||
Executable files
0
Suspicious files
0
Text files
23
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\newsshow[1].css | text | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@baidu[1].txt | text | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\calendar[1].js | text | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\jsLibrary2014[1].js | text | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\wb[1].js | text | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@zhongxi-chem[1].txt | text | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\detail2014[1].png | image | |
MD5:— | SHA256:— | |||
| 3440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[3].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
16
DNS requests
4
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3716 | iexplore.exe | GET | — | 154.210.235.232:80 | http://zhongxi-chem.com/js/jsLibrary2014.js | US | — | — | malicious |
3716 | iexplore.exe | GET | — | 154.210.235.232:80 | http://zhongxi-chem.com/css/newsshow.css | US | — | — | malicious |
3716 | iexplore.exe | GET | — | 154.210.235.232:80 | http://zhongxi-chem.com/js/jquery2.0.js | US | — | — | malicious |
3716 | iexplore.exe | GET | — | 154.210.235.232:80 | http://zhongxi-chem.com/js/calendar.js | US | — | — | malicious |
3716 | iexplore.exe | GET | 200 | 111.206.37.189:80 | http://api.share.baidu.com/s.gif?l=http://zhongxi-chem.com/zj/204.html | CN | — | — | whitelisted |
3716 | iexplore.exe | GET | 200 | 154.210.235.232:80 | http://zhongxi-chem.com/zj/204.html | US | html | 184 Kb | malicious |
3716 | iexplore.exe | GET | 200 | 154.210.235.232:80 | http://zhongxi-chem.com/uploads/allimg/c160717/14DH94M3P-H625_lit.jpg | US | image | 9.27 Kb | malicious |
3716 | iexplore.exe | GET | 200 | 154.210.235.232:80 | http://zhongxi-chem.com/js/wb.js | US | text | 33.3 Kb | malicious |
3716 | iexplore.exe | GET | 200 | 154.210.235.232:80 | http://zhongxi-chem.com/css/newsshow.css | US | text | 4.80 Kb | malicious |
3716 | iexplore.exe | GET | 200 | 154.210.235.232:80 | http://zhongxi-chem.com/js/jsLibrary2014.js | US | text | 3.86 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3440 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3716 | iexplore.exe | 154.210.235.232:80 | zhongxi-chem.com | MULTACOM CORPORATION | US | suspicious |
3716 | iexplore.exe | 111.206.37.189:80 | push.zhanzhang.baidu.com | China Unicom Beijing Province Network | CN | malicious |
3440 | iexplore.exe | 154.210.235.232:80 | zhongxi-chem.com | MULTACOM CORPORATION | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
zhongxi-chem.com |
| malicious |
push.zhanzhang.baidu.com |
| whitelisted |
api.share.baidu.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3716 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS DRIVEBY EXE Embeded in Page Likely Evil M1 |
3716 | iexplore.exe | A Network Trojan was detected | ET TROJAN PE EXE or DLL Windows file download Text |
3716 | iexplore.exe | A Network Trojan was detected | ET TROJAN RAMNIT.A M2 |