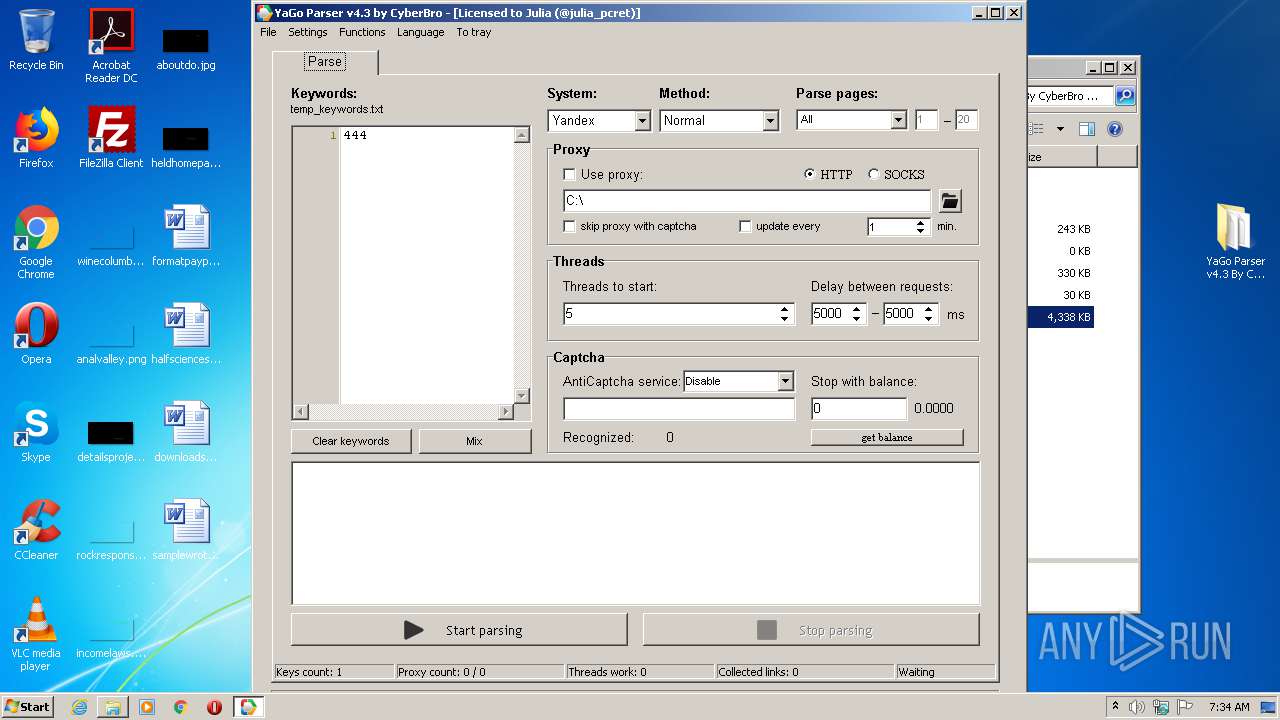
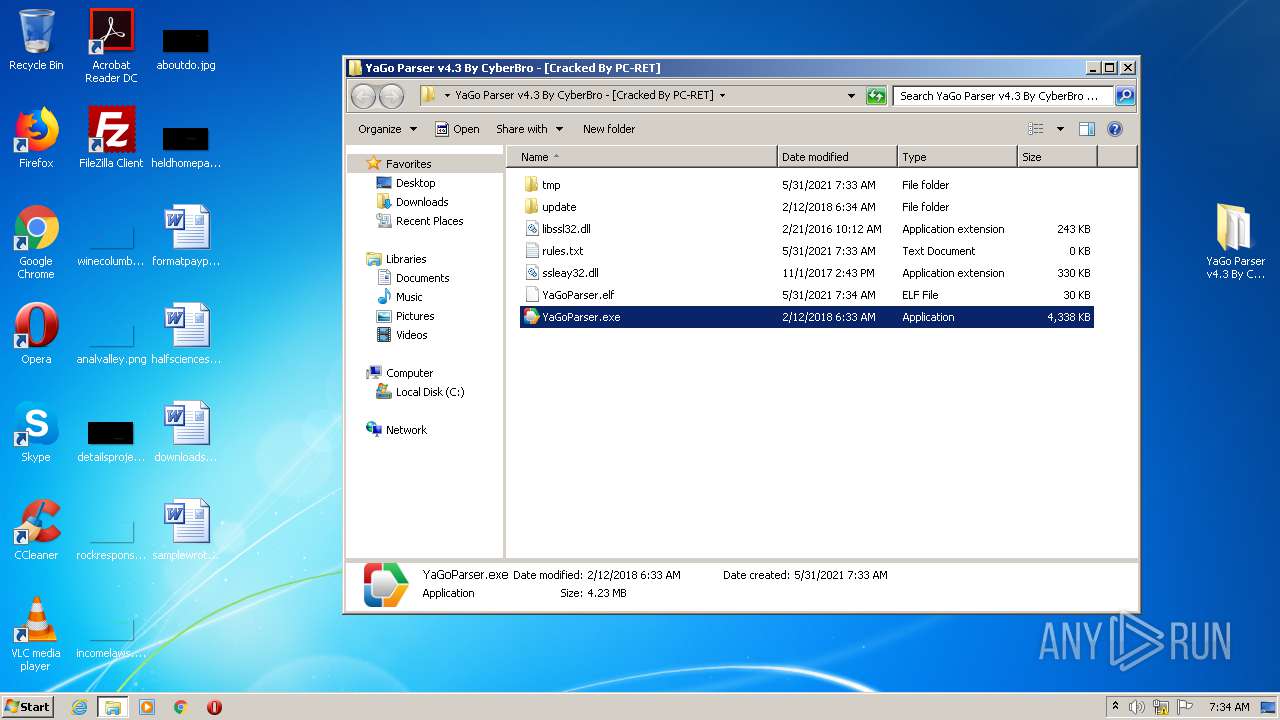
| File name: | YaGo_Parser_v4.3_By_CyberBr_-__Cracked_By_PC-RET_.rar |
| Full analysis: | https://app.any.run/tasks/58105957-44fc-49ed-9c51-426e1666e5b7 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2021, 06:32:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 581107865EAC9200DE42DD49EA56F13E |
| SHA1: | 216072CC3162D06A951A983502E3D1AB0A74E36E |
| SHA256: | 6C9D30A9492BCEC1F134266CD69689BB82766B307472E6879CF037DB7BBA8DB0 |
| SSDEEP: | 24576:kmoYkHAESVydRHd/7SwAAzN2kGmaYtJBl8tNY+ll4gK96ajn3wgb99rF8DKt5o:h6HAcf9/7wMN2JYtJBCg+X4gSQw99SDB |
MALICIOUS
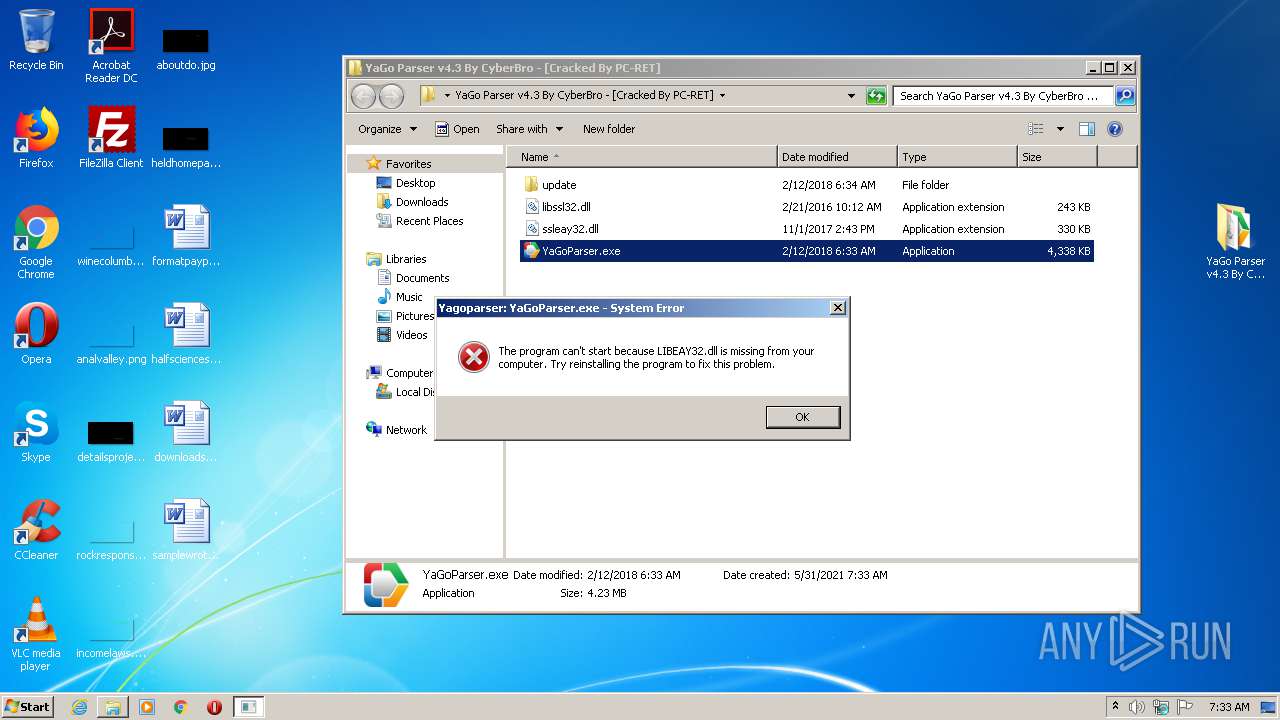
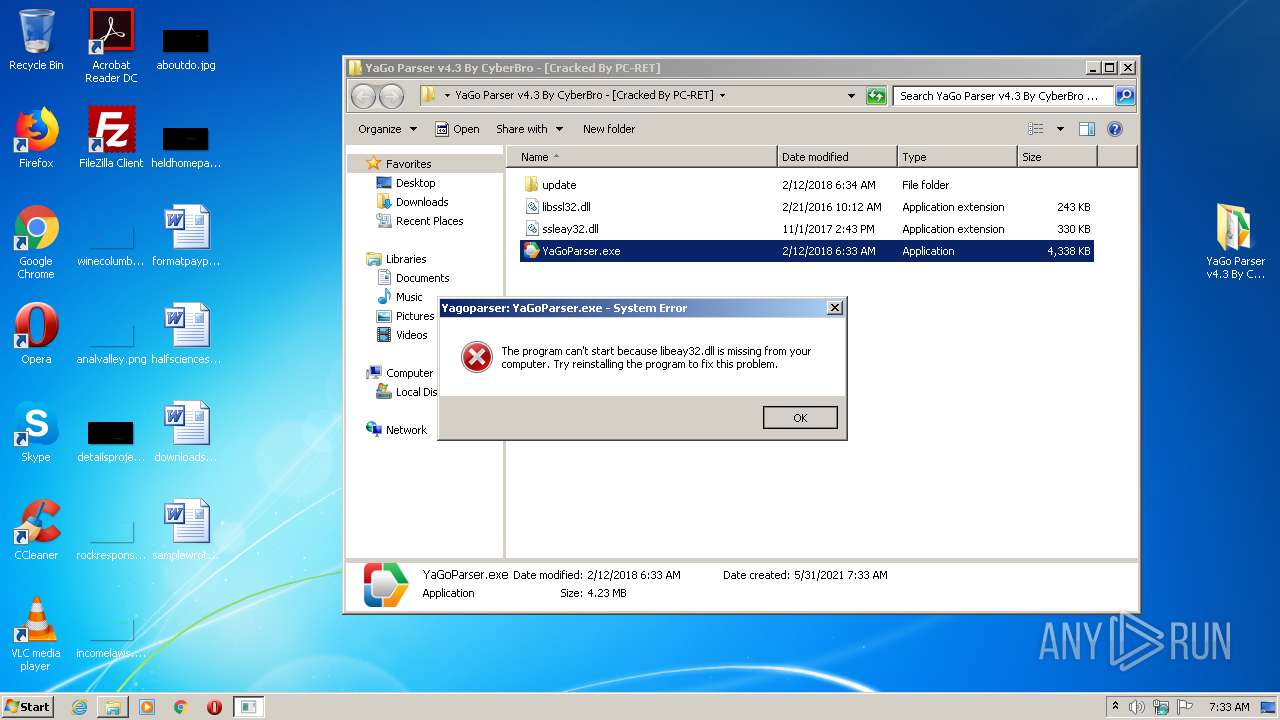
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3180)
- YaGoParser.exe (PID: 1772)
Application was dropped or rewritten from another process
- YaGoParser.exe (PID: 1772)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2552)
Drops a file with too old compile date
- WinRAR.exe (PID: 2552)
Creates files in the user directory
- YaGoParser.exe (PID: 1772)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2552)
INFO
Manual execution by user
- YaGoParser.exe (PID: 1772)
- explorer.exe (PID: 3768)
Reads the hosts file
- YaGoParser.exe (PID: 1772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
44
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1772 | "C:\Users\admin\Desktop\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\YaGoParser.exe" | C:\Users\admin\Desktop\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\YaGoParser.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\YaGo_Parser_v4.3_By_CyberBr_-__Cracked_By_PC-RET_.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3180 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3768 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
841
Read events
814
Write events
27
Delete events
0
Modification events
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\YaGo_Parser_v4.3_By_CyberBr_-__Cracked_By_PC-RET_.rar | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
3
Suspicious files
0
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1772 | YaGoParser.exe | C:\Users\admin\Desktop\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\YaGoParser.elf | text | |
MD5:— | SHA256:— | |||
| 1772 | YaGoParser.exe | C:\Users\admin\Desktop\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\tmp\position_memory.txt | text | |
MD5:— | SHA256:— | |||
| 1772 | YaGoParser.exe | C:\Users\admin\Desktop\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\settings.ini | text | |
MD5:— | SHA256:— | |||
| 1772 | YaGoParser.exe | C:\Users\admin\Desktop\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\tmp\temp_keywords.txt | text | |
MD5:— | SHA256:— | |||
| 2552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2552.14227\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\YaGoParser.exe | executable | |
MD5:C4CC656582461C2F87539387FFB3AC43 | SHA256:98CE40BAAC050FFC9582723EDA3468E32D231A8F9A57A6AA1CB8E6EF52EEE729 | |||
| 2552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2552.14227\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\libssl32.dll | executable | |
MD5:0FE22A92CA281CE90559B271C59720E0 | SHA256:697DBE0B9635F723568D0911D1C48A91C326F116F674003B26D5653EC157B4DE | |||
| 2552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2552.14227\YaGo Parser v4.3 By CyberBro - [Cracked By PC-RET]\ssleay32.dll | executable | |
MD5:1EB4662D9344702823EFCCF6D071F5AD | SHA256:C4DBED05760A52833D8D714686EE48EFBEC44B182D354A9AE8942768A9A19CD2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report