| File name: | WINWORD.EXE |
| Full analysis: | https://app.any.run/tasks/7eec0c8c-8ba6-40bd-9080-8d9ff23610b5 |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2024, 10:40:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CEAA5817A65E914AA178B28F12359A46 |
| SHA1: | 534A7EA9C67BAB3E8F2D41977BF43D41DFE951CF |
| SHA256: | 6C959CFB001FBB900958441DFD8B262FB33E052342948BAB338775D3E83EF7F7 |
| SSDEEP: | 6144:tlsHe0BivO39zYpmH+kAzkA7ZUgbc6AYJ8rEdrEbAgMMV6NX5ZNeVgjYf3:InIO39YAeNLFjAYarEdrEb5P6VxYP |
MALICIOUS
The DLL Hijacking
- WINWORD.EXE (PID: 2044)
- msiexec.exe (PID: 2080)
SUSPICIOUS
Checks Windows Trust Settings
- Setup.exe (PID: 1356)
Reads settings of System Certificates
- Setup.exe (PID: 1356)
Reads security settings of Internet Explorer
- Setup.exe (PID: 1356)
Searches for installed software
- Setup.exe (PID: 1356)
Reads the Internet Settings
- Setup.exe (PID: 1356)
- msiexec.exe (PID: 1392)
- msiexec.exe (PID: 376)
- msiexec.exe (PID: 2348)
- msiexec.exe (PID: 1928)
- msiexec.exe (PID: 2688)
- msiexec.exe (PID: 2848)
- msiexec.exe (PID: 3052)
- msiexec.exe (PID: 880)
- msiexec.exe (PID: 3220)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 2104)
- msiexec.exe (PID: 3672)
- msiexec.exe (PID: 3884)
- msiexec.exe (PID: 1772)
- msiexec.exe (PID: 2520)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2080)
Disables SEHOP
- msiexec.exe (PID: 2080)
Creates/Modifies COM task schedule object
- MSOHTMED.EXE (PID: 2056)
- msiexec.exe (PID: 2080)
Changes default file association
- MSOHTMED.EXE (PID: 2056)
- msiexec.exe (PID: 2080)
INFO
Process drops legitimate windows executable
- WINWORD.EXE (PID: 2044)
- Setup.exe (PID: 1356)
- msiexec.exe (PID: 1392)
- msiexec.exe (PID: 2080)
- msiexec.exe (PID: 2348)
- msiexec.exe (PID: 376)
- msiexec.exe (PID: 2688)
- msiexec.exe (PID: 3220)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3672)
- msiexec.exe (PID: 3884)
- msiexec.exe (PID: 1772)
Checks supported languages
- WINWORD.EXE (PID: 2044)
- Setup.exe (PID: 1356)
- msiexec.exe (PID: 2080)
- msiexec.exe (PID: 1836)
- msiexec.exe (PID: 1928)
- msiexec.exe (PID: 1392)
- msiexec.exe (PID: 2348)
- msiexec.exe (PID: 376)
- msiexec.exe (PID: 2580)
- msiexec.exe (PID: 632)
- msiexec.exe (PID: 2672)
- msiexec.exe (PID: 2848)
- msiexec.exe (PID: 880)
- msiexec.exe (PID: 2688)
- msiexec.exe (PID: 2520)
- msiexec.exe (PID: 3052)
- msiexec.exe (PID: 3220)
- msiexec.exe (PID: 3152)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3312)
- msiexec.exe (PID: 2104)
- msiexec.exe (PID: 3672)
- msiexec.exe (PID: 3884)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 1772)
- msiexec.exe (PID: 3820)
- msiexec.exe (PID: 2328)
- addinutil.exe (PID: 1984)
- addinutil.exe (PID: 2260)
- MSOHTMED.EXE (PID: 2056)
- MSICC3F.tmp (PID: 2424)
Reads the computer name
- WINWORD.EXE (PID: 2044)
- msiexec.exe (PID: 2080)
- Setup.exe (PID: 1356)
- msiexec.exe (PID: 1836)
- msiexec.exe (PID: 1392)
- msiexec.exe (PID: 1928)
- msiexec.exe (PID: 2348)
- msiexec.exe (PID: 632)
- msiexec.exe (PID: 376)
- msiexec.exe (PID: 2580)
- msiexec.exe (PID: 2688)
- msiexec.exe (PID: 2672)
- msiexec.exe (PID: 2520)
- msiexec.exe (PID: 2848)
- msiexec.exe (PID: 3052)
- msiexec.exe (PID: 3220)
- msiexec.exe (PID: 3152)
- msiexec.exe (PID: 880)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3312)
- msiexec.exe (PID: 2104)
- msiexec.exe (PID: 3672)
- msiexec.exe (PID: 3884)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 3820)
- msiexec.exe (PID: 1772)
- msiexec.exe (PID: 2328)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2044)
- Setup.exe (PID: 1356)
- msiexec.exe (PID: 2080)
- msiexec.exe (PID: 1772)
- MSOHTMED.EXE (PID: 2056)
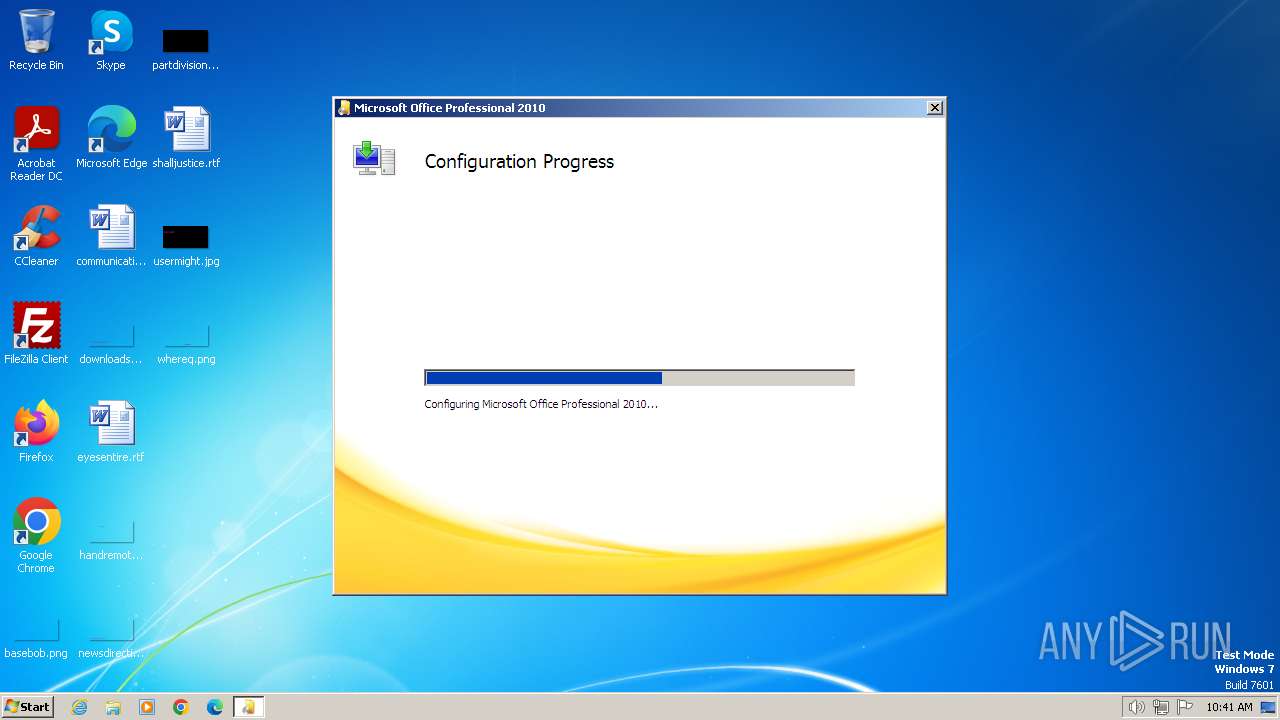
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 2044)
- Setup.exe (PID: 1356)
- msiexec.exe (PID: 1392)
- msiexec.exe (PID: 2080)
- msiexec.exe (PID: 2348)
- msiexec.exe (PID: 376)
- msiexec.exe (PID: 2688)
- msiexec.exe (PID: 3220)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3672)
- msiexec.exe (PID: 3884)
- msiexec.exe (PID: 1772)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 2044)
- Setup.exe (PID: 1356)
- msiexec.exe (PID: 2080)
- msiexec.exe (PID: 1836)
- msiexec.exe (PID: 1928)
- msiexec.exe (PID: 1392)
- msiexec.exe (PID: 2348)
- msiexec.exe (PID: 632)
- msiexec.exe (PID: 376)
- msiexec.exe (PID: 2580)
- msiexec.exe (PID: 2688)
- msiexec.exe (PID: 2672)
- msiexec.exe (PID: 2520)
- msiexec.exe (PID: 2848)
- msiexec.exe (PID: 3052)
- msiexec.exe (PID: 3220)
- msiexec.exe (PID: 880)
- msiexec.exe (PID: 3152)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3312)
- msiexec.exe (PID: 2104)
- msiexec.exe (PID: 3672)
- msiexec.exe (PID: 3884)
- msiexec.exe (PID: 3820)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 2328)
- msiexec.exe (PID: 1772)
- addinutil.exe (PID: 1984)
- addinutil.exe (PID: 2260)
Reads Environment values
- WINWORD.EXE (PID: 2044)
- msiexec.exe (PID: 2080)
Create files in a temporary directory
- Setup.exe (PID: 1356)
- msiexec.exe (PID: 2080)
Creates a software uninstall entry
- msiexec.exe (PID: 2080)
Application launched itself
- msiexec.exe (PID: 2080)
Creates files or folders in the user directory
- WINWORD.EXE (PID: 2044)
Starts application with an unusual extension
- msiexec.exe (PID: 2080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2006:10:27 23:54:48+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 5120 |
| InitializedDataSize: | 334848 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x10cc |
| OSVersion: | 4 |
| ImageVersion: | 10 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.0.4518.1014 |
| ProductVersionNumber: | 12.0.4518.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft Office Word |
| FileVersion: | 12.0.4518.1014 |
| InternalName: | WinWord |
| LegalCopyright: | © 2006 Microsoft Corporation. All rights reserved. |
| LegalTrademarks1: | Microsoft® is a registered trademark of Microsoft Corporation. |
| LegalTrademarks2: | Windows® is a registered trademark of Microsoft Corporation. |
| OriginalFileName: | WinWord.exe |
| ProductName: | 2007 Microsoft Office system |
| ProductVersion: | 12.0.4518.1014 |
Total processes
66
Monitored processes
31
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | C:\Windows\system32\MsiExec.exe -Embedding CFCFA25CCE33B1278ED4D4C1895EFC4F | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 632 | C:\Windows\system32\MsiExec.exe -Embedding A10504DBAD53544753570D49C078486A E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | C:\Windows\system32\MsiExec.exe -Embedding E0802B0355920F961567BB15C924E9C7 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Common Files\Microsoft Shared\OFFICE14\Office Setup Controller\Setup.exe" -Embedding | C:\Program Files\Common Files\Microsoft Shared\OFFICE14\Office Setup Controller\Setup.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Setup Bootstrapper Exit code: 0 Version: 14.0.6010.1000 Modules
| |||||||||||||||
| 1392 | C:\Windows\system32\MsiExec.exe -Embedding 0E4629F8F4AD8C15201743D9FCB7A886 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | C:\Windows\system32\MsiExec.exe -Embedding CE33664D124CA9CDBAB39DB7DFBFE177 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1836 | C:\Windows\system32\MsiExec.exe -Embedding 52925EE971A317DEADDF2EBAC729C03C E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | C:\Windows\system32\MsiExec.exe -Embedding A4E681F11C51BB91DB067D0042A47485 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1984 | "C:\Windows\Microsoft.NET\Framework\v3.5\addinutil.exe" -PipelineRoot:"C:\Program Files\Common Files\Microsoft Shared\VSTA\Pipeline.v10.0\." -Rebuild | C:\Windows\Microsoft.NET\Framework\v3.5\addinutil.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: AddInUtil.exe Exit code: 0 Version: 3.5.30729.5420 built by: Win7SP1 Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\AppData\Local\Temp\WINWORD.EXE" | C:\Users\admin\AppData\Local\Temp\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
Total events
84 629
Read events
79 023
Write events
4 693
Delete events
913
Modification events
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
210
Suspicious files
131
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR12F7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1356 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Setup0000054c\BRANDING.XML | xml | |
MD5:10B211A922F7CA1A15B98F595A10A7BD | SHA256:01B34D2E5BE5247D802D5E1EEC1C641B55B8959243C27163500511D55FF51DA0 | |||
| 1356 | Setup.exe | C:\Users\admin\AppData\Local\Temp\SetupExe(2024011010404554C).log | text | |
MD5:7D1C16D1D3A6EE2DC40601CF4500529E | SHA256:4AFA1F6E738AB197CB475C4C02A36CACDD286FFCFF04EDA7BA98BB1016CBE2BA | |||
| 1356 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Setup0000054c\OSETUP.DLL | executable | |
MD5:1ECF60135F91F9362BD99B9D45B7738E | SHA256:405A8AF843BD0076091A11628574F57313FB0A5908EA975D8F9E830C9C879DB5 | |||
| 1356 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Setup0000054c\OSETUPUI.DLL | executable | |
MD5:196A884E700B7EB09B2CD0A48ECCBC3A | SHA256:12BABD301AB2F5A0CD35226D4939E1E200D5FCF90694A25690DF7AD0EA28B55A | |||
| 2080 | msiexec.exe | C:\Windows\Installer\MSI22A8.tmp | executable | |
MD5:CB6AAB53E5D4893327ADE765CFF283F2 | SHA256:A0DBBA68F7B3FBFF7FE368F5478AE60D2D840158ED0E70FF0A1C48C305D8F986 | |||
| 2080 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF38C4AC21EF5F3F2F.TMP | binary | |
MD5:187F58A576B1D4AEB78672A830A92A19 | SHA256:F4BE5F7A050431CEE430DD276F34C766A0419CE27BB0FCA0132A92FAB107F246 | |||
| 2080 | msiexec.exe | C:\Windows\Installer\MSI280F.tmp | executable | |
MD5:B8255A1BC3C307557741D2C99B8256D1 | SHA256:796AEA9A46FB7704222A7FE1F4E27455B14640C816D6F961344F89DC47537B33 | |||
| 2080 | msiexec.exe | C:\Windows\Installer\MSI2607.tmp | executable | |
MD5:9F0B9BC54BB73DFB7CF85520DA1A08CB | SHA256:0D44D40E8BDA72A3D6CA26665100B256848E2183029A6728C18AD97CD650547F | |||
| 2080 | msiexec.exe | C:\Windows\Installer\MSI250A.tmp | binary | |
MD5:0832ED4A0A5549C897F2E68FECF2CF1E | SHA256:1F3BD0A2D8CA618B42067E8CA760653857E8B2A18308AF1EE849A7618E7036F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|