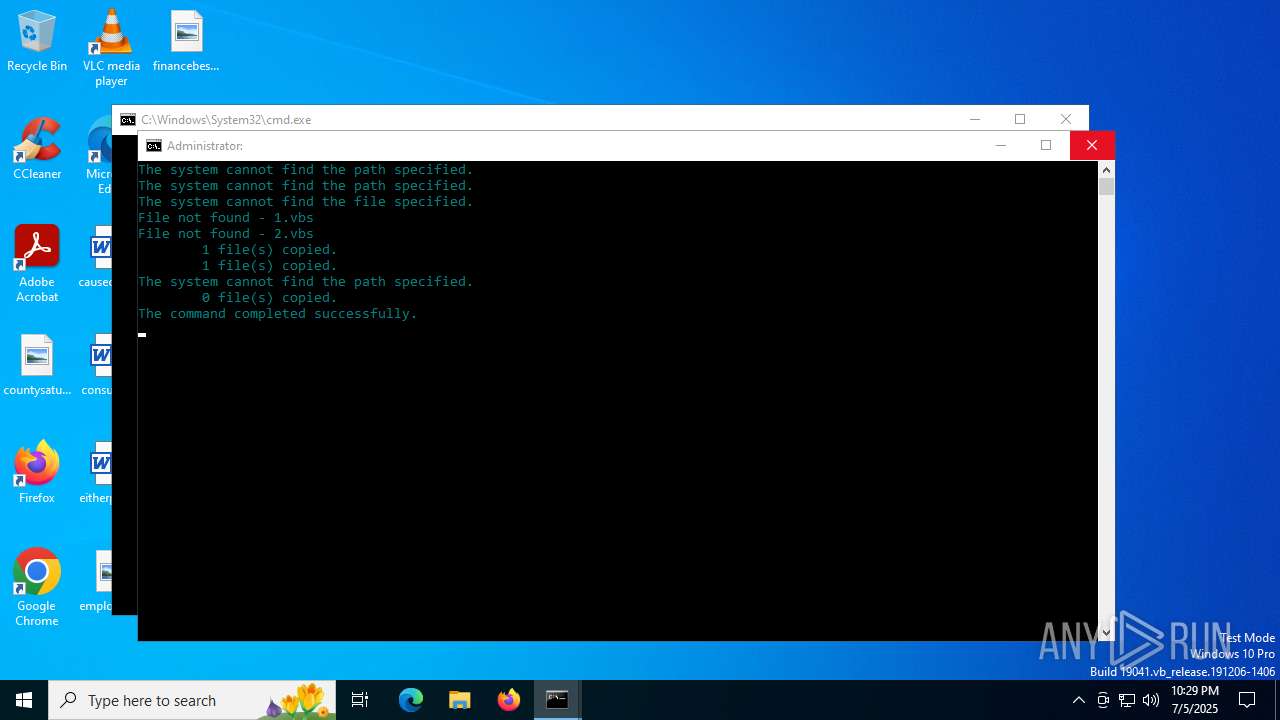
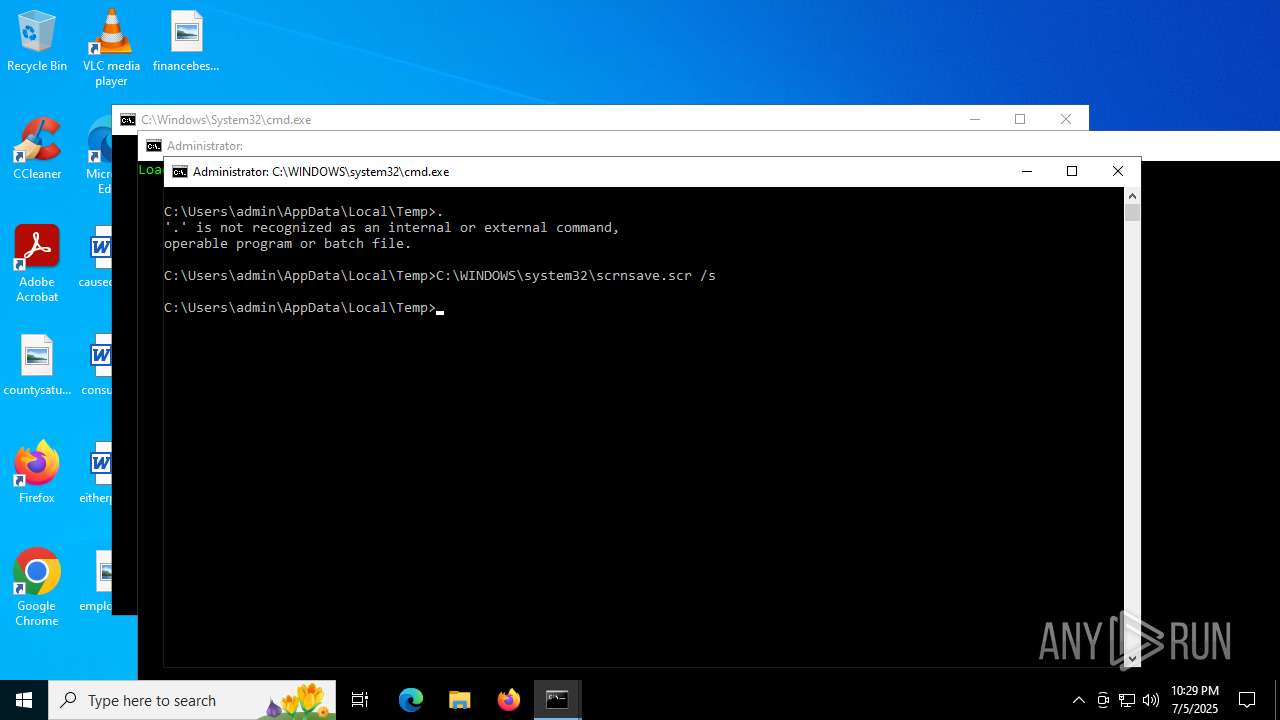
| File name: | main.bat |
| Full analysis: | https://app.any.run/tasks/47f4ee4b-5d4a-40a4-b4fc-aef0d36acd44 |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2025, 22:29:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 79C7765D6388FA991D30DFF5DB93FB8D |
| SHA1: | 0B44A17C3D359EF2D36892D0C552B76547B636F3 |
| SHA256: | 6C84B56C59DD149857603BE66D45A344BC02E628F8E53F863848ADA52134E569 |
| SSDEEP: | 96:bVehI8ocEWYbQjUnSXfeWaNLTtI5tcc7XPM7SF8q4RzzKMs0UsqQ6l9o7:bVehILenSLqdQT/hFUsT6fs |
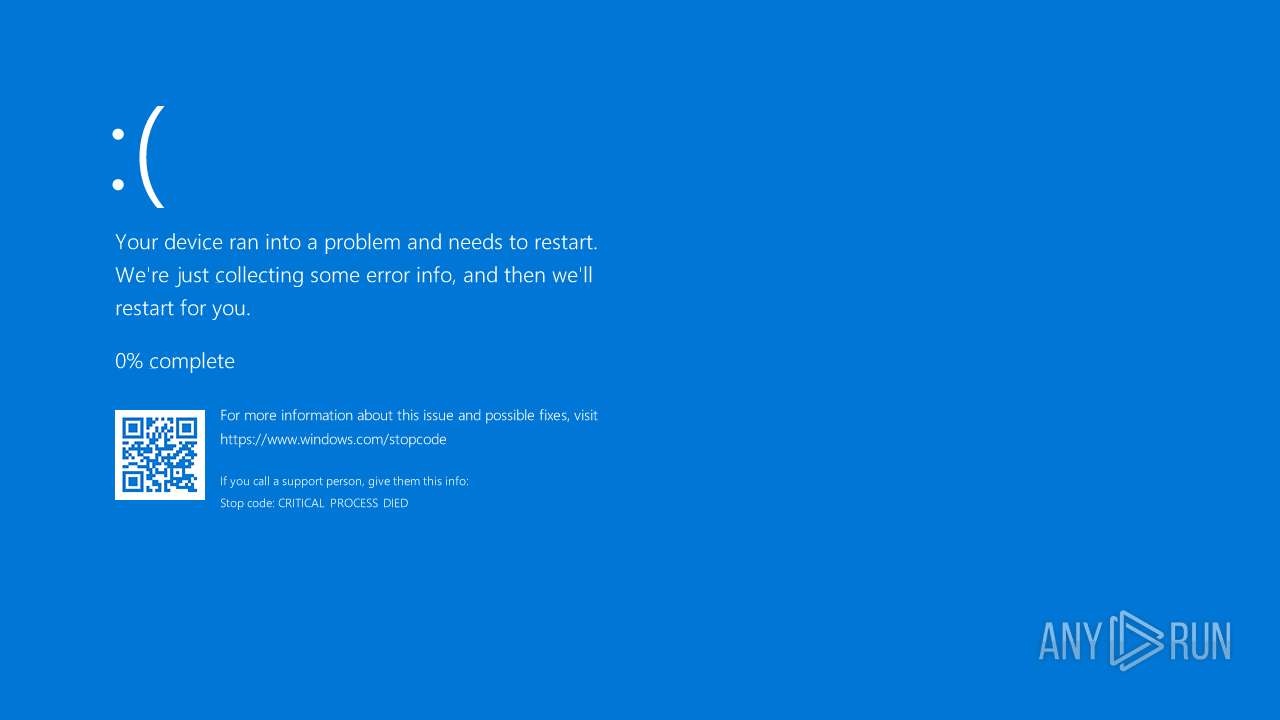
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 2804)
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4932)
- net.exe (PID: 3584)
Create files in the Startup directory
- cmd.exe (PID: 7052)
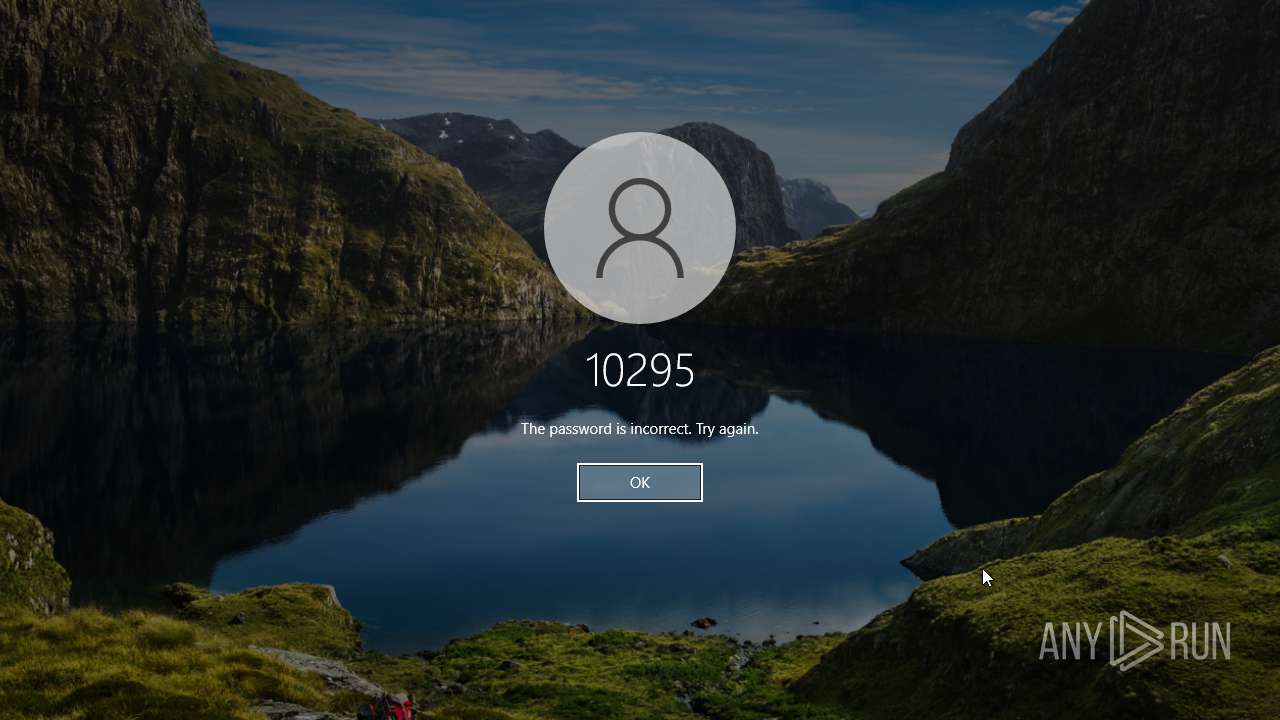
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 7052)
- net.exe (PID: 1192)
- net.exe (PID: 3588)
- net.exe (PID: 3980)
- net.exe (PID: 3564)
- net.exe (PID: 2076)
- net.exe (PID: 6868)
- net.exe (PID: 4788)
- net.exe (PID: 6552)
- net.exe (PID: 3780)
- net.exe (PID: 6256)
- net.exe (PID: 6336)
- net.exe (PID: 3980)
- net.exe (PID: 4828)
- net.exe (PID: 4880)
- net.exe (PID: 3588)
- net.exe (PID: 4788)
- net.exe (PID: 6868)
- net.exe (PID: 6552)
- net.exe (PID: 7048)
- net.exe (PID: 6336)
- net.exe (PID: 3564)
- net.exe (PID: 1948)
- net.exe (PID: 4880)
- net.exe (PID: 3160)
- net.exe (PID: 3388)
- net.exe (PID: 4960)
- net.exe (PID: 1332)
- net.exe (PID: 6668)
- net.exe (PID: 2132)
- net.exe (PID: 2716)
- net.exe (PID: 7136)
- net.exe (PID: 6256)
- net.exe (PID: 3740)
- net.exe (PID: 3688)
- net.exe (PID: 1512)
- net.exe (PID: 4684)
- net.exe (PID: 5436)
- net.exe (PID: 6868)
- net.exe (PID: 6680)
- net.exe (PID: 6552)
- net.exe (PID: 5576)
- net.exe (PID: 6796)
- net.exe (PID: 3980)
- net.exe (PID: 5552)
- net.exe (PID: 2464)
- net.exe (PID: 868)
- net.exe (PID: 1564)
- net.exe (PID: 1028)
- net.exe (PID: 7156)
- net.exe (PID: 5720)
- net.exe (PID: 2800)
- net.exe (PID: 2120)
- net.exe (PID: 6900)
- net.exe (PID: 1128)
- net.exe (PID: 3564)
- net.exe (PID: 6936)
- net.exe (PID: 3672)
- net.exe (PID: 5168)
- net.exe (PID: 1212)
- net.exe (PID: 6936)
- net.exe (PID: 2220)
- net.exe (PID: 4760)
- net.exe (PID: 5780)
- net.exe (PID: 2180)
- net.exe (PID: 1984)
- net.exe (PID: 1332)
- net.exe (PID: 6668)
- net.exe (PID: 2132)
- net.exe (PID: 3584)
- net.exe (PID: 6780)
- net.exe (PID: 3688)
- net.exe (PID: 4684)
- net.exe (PID: 6200)
- net.exe (PID: 2180)
- net.exe (PID: 6140)
- net.exe (PID: 6948)
- net.exe (PID: 6868)
- net.exe (PID: 2536)
- net.exe (PID: 6164)
- net.exe (PID: 5184)
- net.exe (PID: 2320)
- net.exe (PID: 4860)
- net.exe (PID: 2696)
- net.exe (PID: 6348)
- net.exe (PID: 4552)
- net.exe (PID: 3028)
- net.exe (PID: 6264)
- net.exe (PID: 856)
- net.exe (PID: 2132)
- net.exe (PID: 6348)
- net.exe (PID: 3964)
- net.exe (PID: 6796)
- net.exe (PID: 4960)
- net.exe (PID: 6256)
- net.exe (PID: 4860)
- net.exe (PID: 3672)
- net.exe (PID: 2220)
- net.exe (PID: 1356)
- net.exe (PID: 2356)
- net.exe (PID: 4664)
- net.exe (PID: 6264)
- net.exe (PID: 4788)
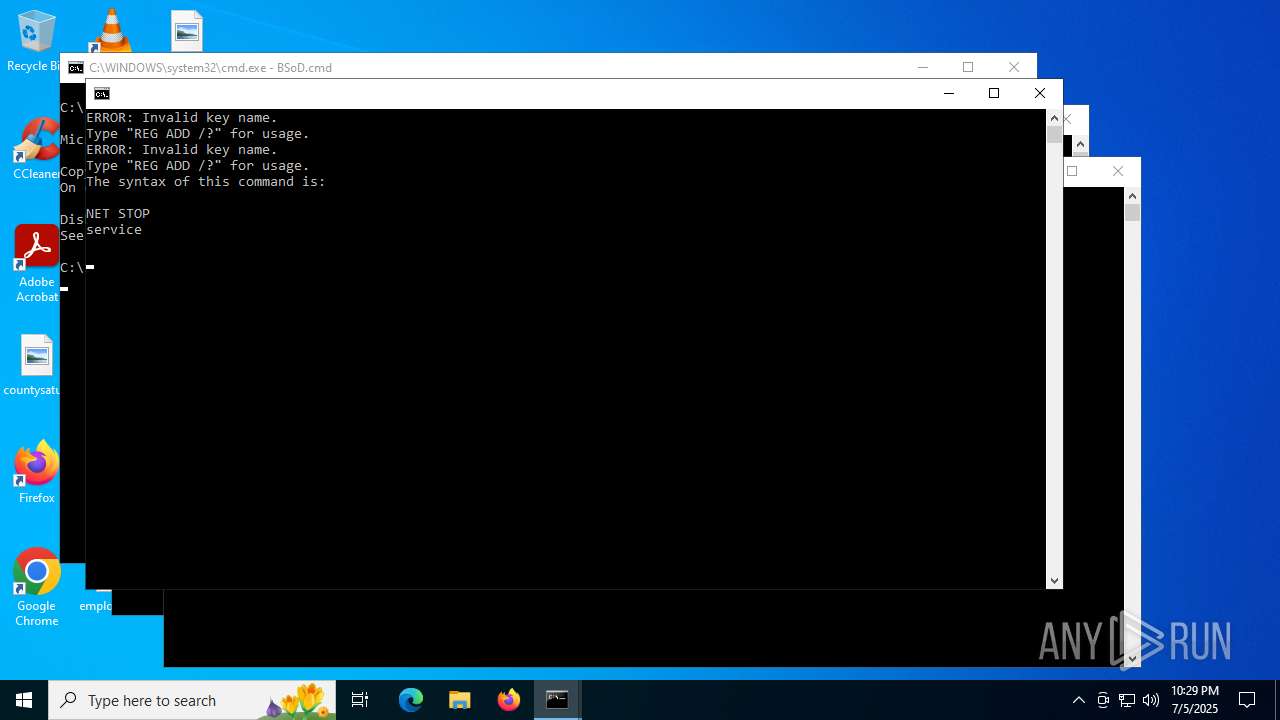
Disables task manager
- reg.exe (PID: 7048)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 2492)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 6724)
- cmd.exe (PID: 5772)
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4932)
The process executes VB scripts
- cmd.exe (PID: 6724)
Executing commands from a ".bat" file
- wscript.exe (PID: 2492)
- cmd.exe (PID: 888)
- cmd.exe (PID: 5772)
- cmd.exe (PID: 3620)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2492)
- cmd.exe (PID: 5772)
- cmd.exe (PID: 888)
- cmd.exe (PID: 7052)
- cmd.exe (PID: 3620)
Application launched itself
- cmd.exe (PID: 5772)
- cmd.exe (PID: 888)
- cmd.exe (PID: 7052)
- cmd.exe (PID: 3620)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4932)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4932)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7052)
Executing commands from ".cmd" file
- cmd.exe (PID: 7052)
Starts application with an unusual extension
- cmd.exe (PID: 684)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 7052)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 7052)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 7052)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 7052)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 7052)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 7052)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 7052)
Windows service management via SC.EXE
- sc.exe (PID: 5960)
Executable content was dropped or overwritten
- Dism.exe (PID: 1332)
- cmd.exe (PID: 7052)
Starts SC.EXE for service management
- cmd.exe (PID: 7052)
Stops a currently running service
- sc.exe (PID: 4960)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 6472)
- DismHost.exe (PID: 1192)
The process creates files with name similar to system file names
- Dism.exe (PID: 1332)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 7052)
- net.exe (PID: 2388)
Process drops legitimate windows executable
- cmd.exe (PID: 7052)
The process checks if it is being run in the virtual environment
- cmd.exe (PID: 7052)
The process drops C-runtime libraries
- cmd.exe (PID: 7052)
Creates file in the systems drive root
- cmd.exe (PID: 7052)
- cmd.exe (PID: 2800)
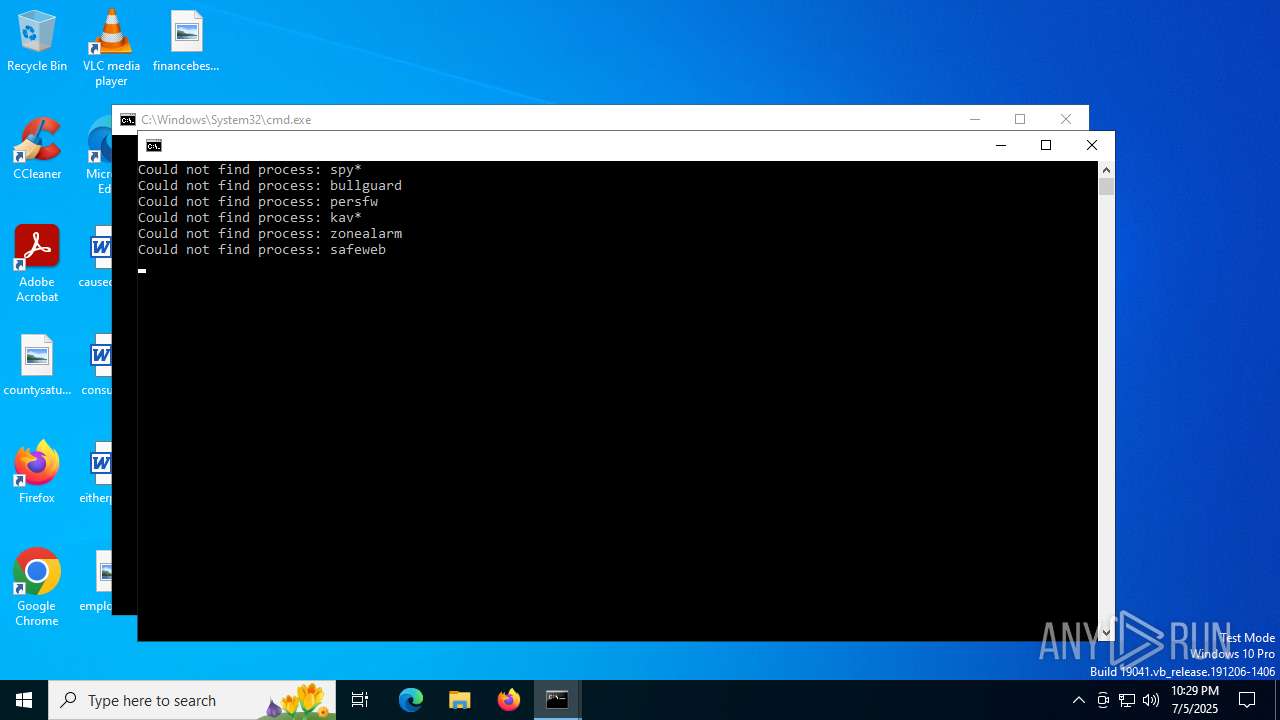
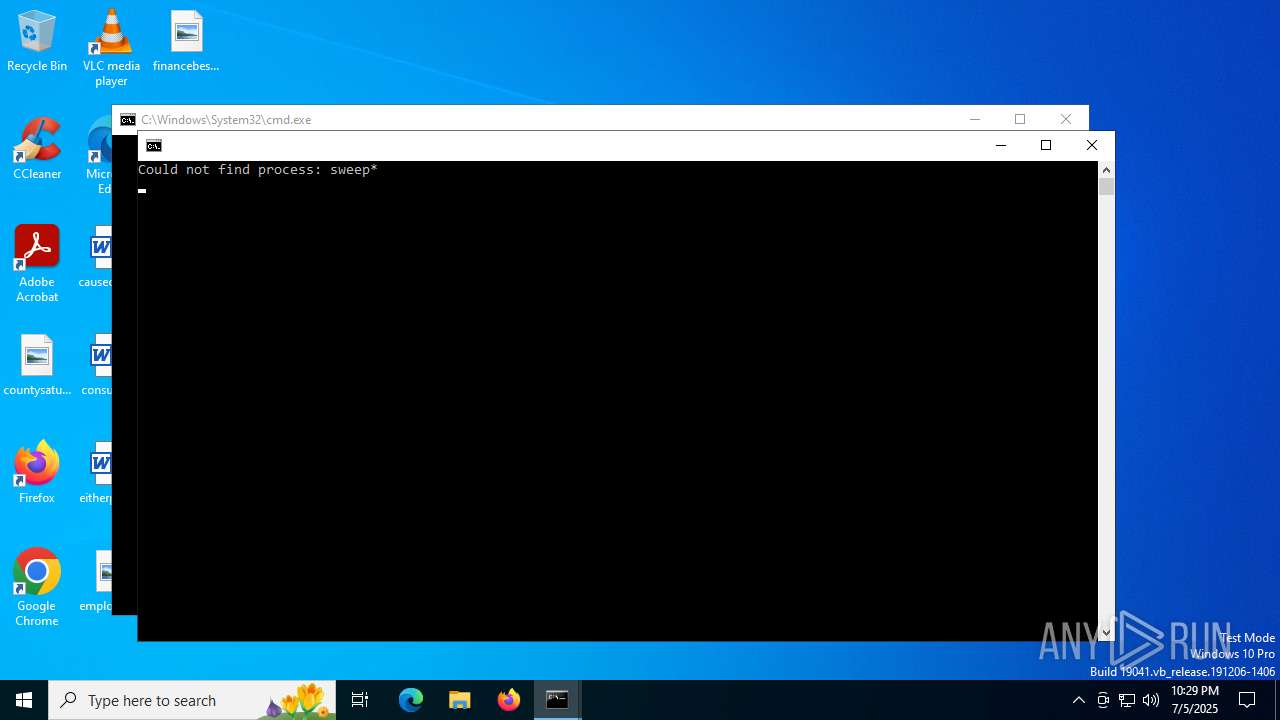
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2800)
Creates or modifies Windows services
- reg.exe (PID: 2680)
INFO
Checks supported languages
- mode.com (PID: 3620)
- scrnsave.scr (PID: 2716)
- DismHost.exe (PID: 6472)
- DismHost.exe (PID: 1192)
Reads the computer name
- scrnsave.scr (PID: 2716)
- DismHost.exe (PID: 6472)
- DismHost.exe (PID: 1192)
Starts MODE.COM to configure console settings
- mode.com (PID: 3620)
Launching a file from the Startup directory
- cmd.exe (PID: 7052)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6948)
- WMIC.exe (PID: 2044)
Create files in a temporary directory
- Dism.exe (PID: 1332)
The sample compiled with english language support
- Dism.exe (PID: 1332)
- cmd.exe (PID: 7052)
The sample compiled with korean language support
- cmd.exe (PID: 7052)
The sample compiled with russian language support
- cmd.exe (PID: 7052)
The sample compiled with japanese language support
- cmd.exe (PID: 7052)
The sample compiled with french language support
- cmd.exe (PID: 7052)
The sample compiled with chinese language support
- cmd.exe (PID: 7052)
The sample compiled with german language support
- cmd.exe (PID: 7052)
The sample compiled with spanish language support
- cmd.exe (PID: 7052)
The sample compiled with Italian language support
- cmd.exe (PID: 7052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
469
Monitored processes
331
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | find /i "IPv4" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | C:\WINDOWS\system32\net1 user 27026 14513 /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | tskill /A anti* | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\cmd.exe /K bsod.cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\system32\net1 user 25920 2809 /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\system32\net1 user 29063 19975 /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | net user 12782 22265 /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | reg delete "HKEY_LOCAL_MACHINE\system\CurrentControlSet\Services\Mouclass" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 868 | net user 12705 2713 /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 868 | C:\WINDOWS\system32\net1 user 26731 19536 /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 460
Read events
11 453
Write events
5
Delete events
2
Modification events
| (PID) Process: | (6724) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (3196) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31190524 | |||
| (PID) Process: | (3196) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
| (PID) Process: | (7048) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (2680) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Mouclass |
| Operation: | write | Name: | Start |
Value: 4 | |||
| (PID) Process: | (856) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\mouclass\Enum |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (856) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\mouclass |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
154
Suspicious files
6
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6724 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:D14A6C18536B08C2D91CC10129CEC2CA | SHA256:88F0E55BE41422957E8F4FEC8CAF0F9ED4E68D1F0290171BA8F4BD26C19FA17D | |||
| 7052 | cmd.exe | C:\Users\admin\AppData\Local\Temp\restart.bat | text | |
MD5:995F43DB4634D90C81AB3B716FAA1FF5 | SHA256:1AECC13A454167B47D503E8B9576A04DB3E8C4C7510AE8077140DC8EF17E5145 | |||
| 7052 | cmd.exe | C:\Users\admin\AppData\Local\Temp\windowswimn32.bat | text | |
MD5:9905E5A33C6EDD8EB5F59780AFBF74DE | SHA256:C134B2F85415BA5CFCE3E3FE4745688335745A9BB22152AC8F5C77F190D8AEE3 | |||
| 7052 | cmd.exe | C:\Users\admin\AppData\Local\Temp\rest.bat | text | |
MD5:52D75448C46016F3F860076C2472FCE8 | SHA256:29C6A4EDF2D211C6F583AB051A579FC0E8D72F2C88959BFB7FD36380425F9CFE | |||
| 7052 | cmd.exe | C:\Users\admin\AppData\Local\Temp\bsod.cmd | text | |
MD5:995F43DB4634D90C81AB3B716FAA1FF5 | SHA256:1AECC13A454167B47D503E8B9576A04DB3E8C4C7510AE8077140DC8EF17E5145 | |||
| 1332 | Dism.exe | C:\Users\admin\AppData\Local\Temp\822C6C98-4296-40D6-8A76-EE78945D0A18\DismCorePS.dll | executable | |
MD5:35A07968EC37231249F3F072AE555E3A | SHA256:E5F25E5A170CB3D165C3D143EAE967B96AB80F88FB09176DA8591B0B68C77E00 | |||
| 7052 | cmd.exe | C:\Users\Default\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\rest.bat | text | |
MD5:96DD21A13A959DBDE9B32EE41DBB7E21 | SHA256:0B4CD78BEA7B71D32ADDCB6AD47880529959D897ED74B8494226842195744048 | |||
| 7052 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\rest.bat | text | |
MD5:96DD21A13A959DBDE9B32EE41DBB7E21 | SHA256:0B4CD78BEA7B71D32ADDCB6AD47880529959D897ED74B8494226842195744048 | |||
| 3196 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:E0686496E44806099666EB03A66D302D | SHA256:9FBBDF08F333DAE845FFF9DAF7FFE831D07753D8EA07DA6069FB67D6FE5BAFB5 | |||
| 1332 | Dism.exe | C:\Users\admin\AppData\Local\Temp\822C6C98-4296-40D6-8A76-EE78945D0A18\DismProv.dll | executable | |
MD5:AB0DBC4F05B33EAAA447E31ACCAB8D21 | SHA256:6A3C3F07BDDBC3079873F8799F2C19ADDDC59F15D6B2DBA6E9314E5626BFD2A0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
37
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3948 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.100.181.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4648 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3692 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4140 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3948 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3948 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 95.100.181.32:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=1332 TID=5952 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=1332 TID=5952 Loading Provider from location C:\WINDOWS\system32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=1332 TID=5952 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=1332 TID=5952 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=1332 TID=5952 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=1332 TID=5952 Connecting to the provider located at C:\WINDOWS\system32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
Dism.exe | PID=1332 TID=5952 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=1332 TID=5952 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=1332 TID=5952 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |