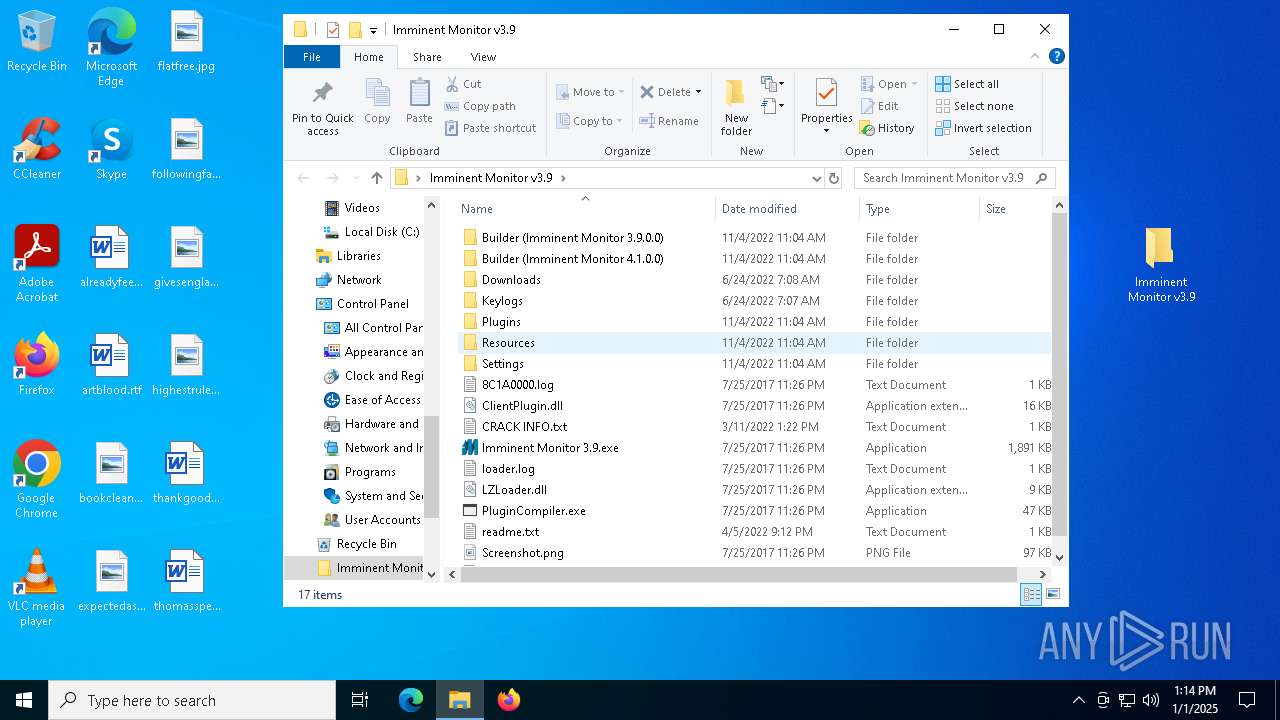
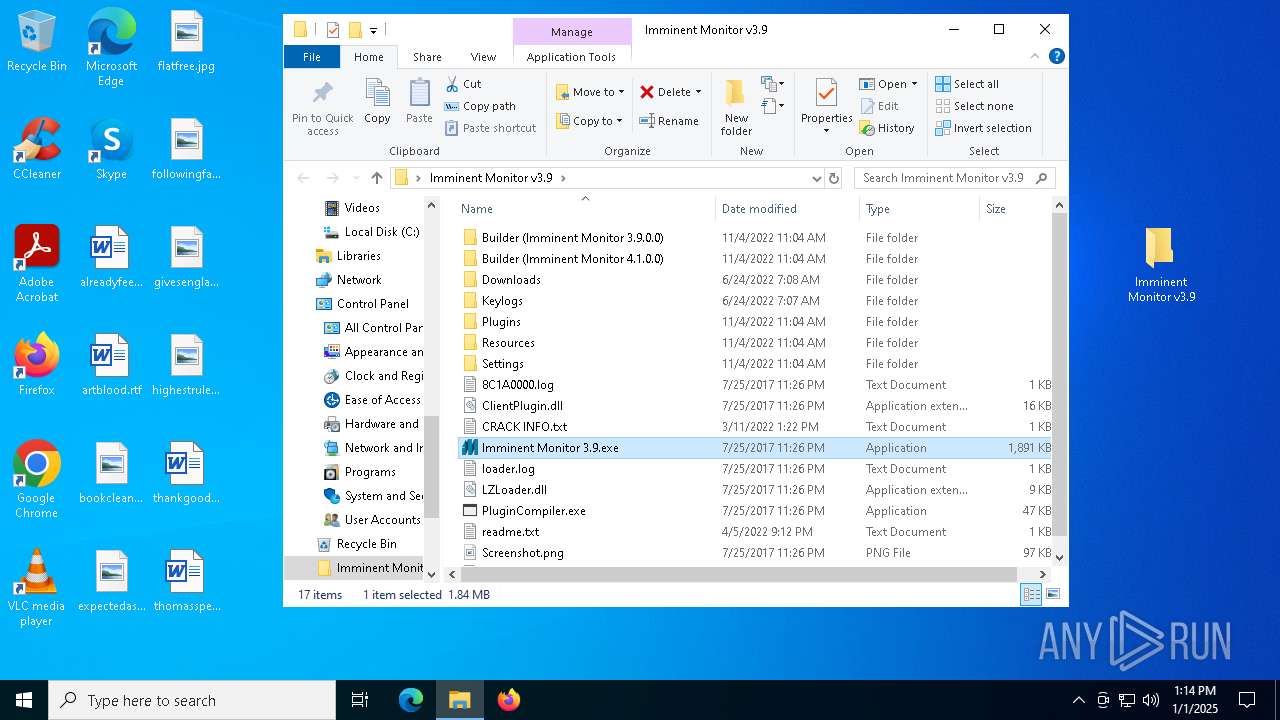
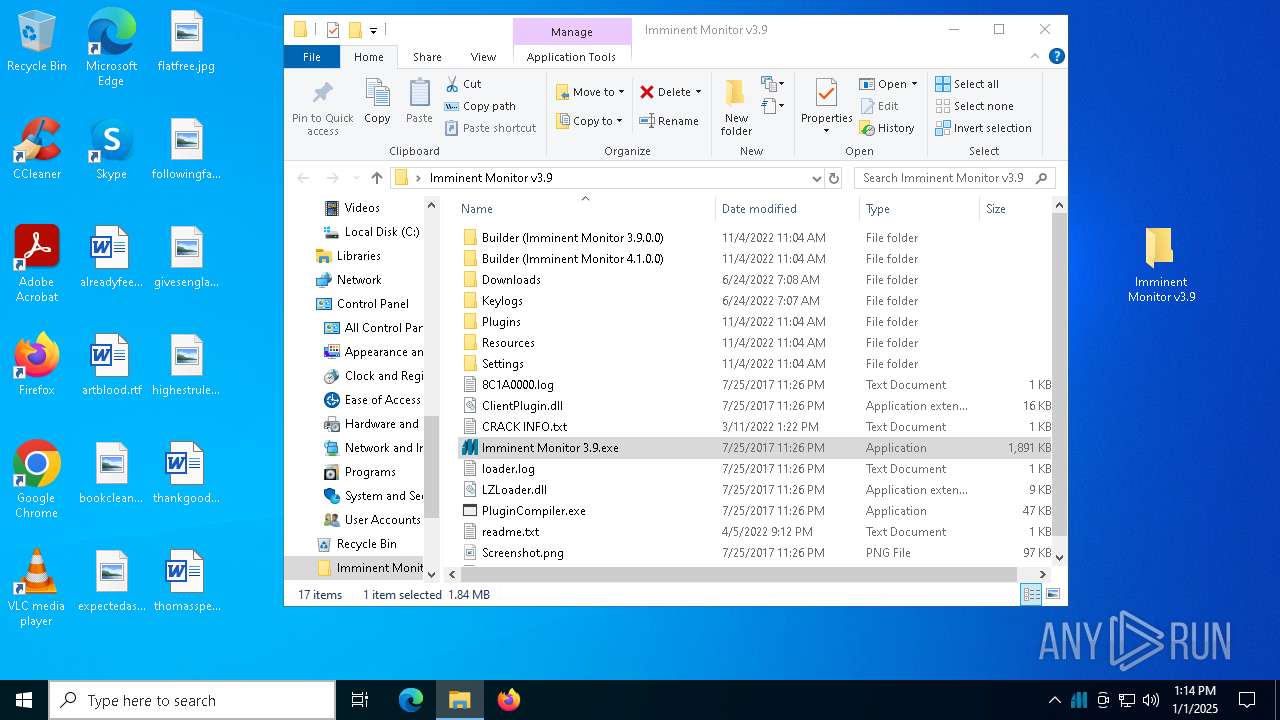
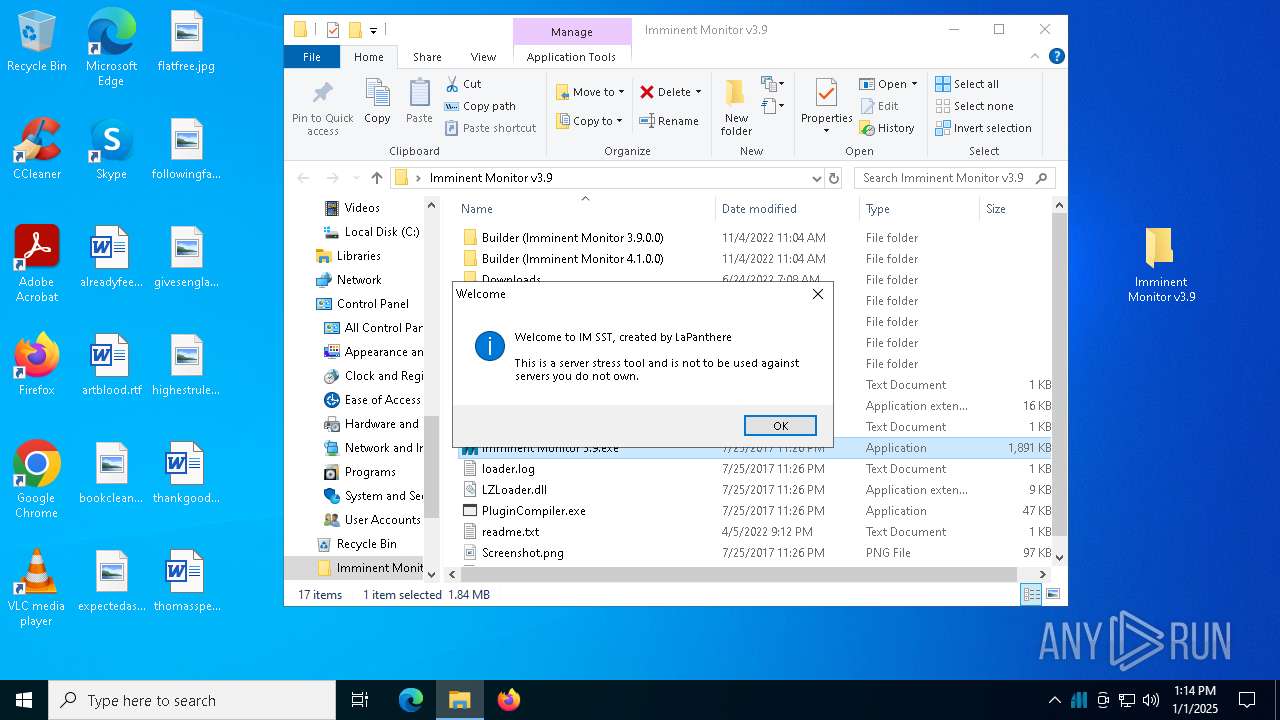
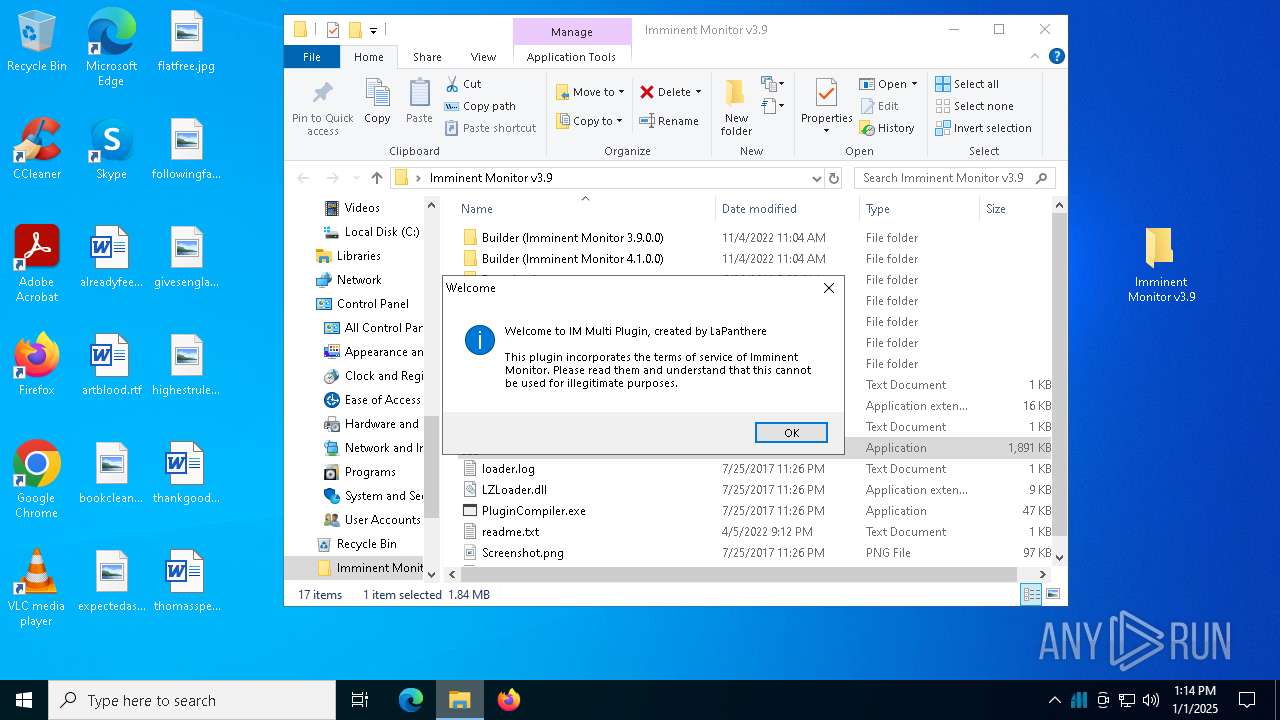
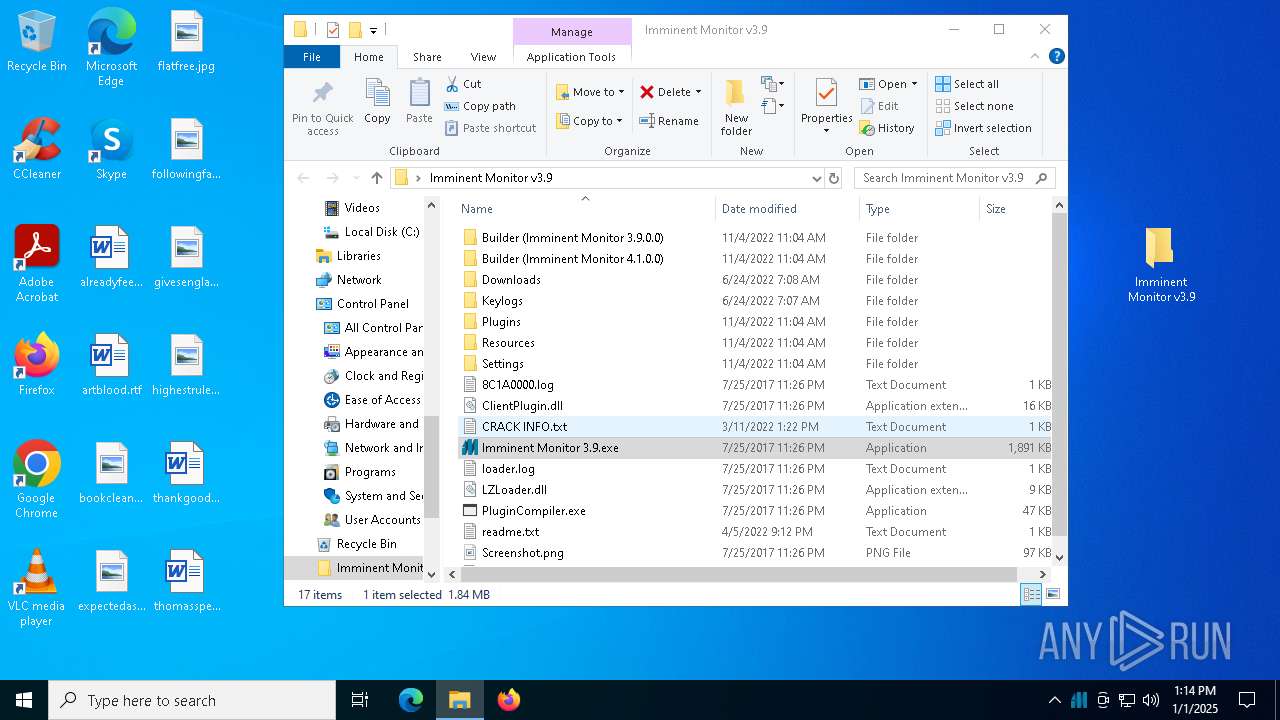
| File name: | Imminent Monitor v3.9.zip |
| Full analysis: | https://app.any.run/tasks/94979c50-3e5b-408c-9b69-de241e9b117c |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2025, 13:14:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | DFB2138BA9567F89ECC7EC2483E1DF0C |
| SHA1: | E848759964BBDE4E73028992CDC89527E1C318CE |
| SHA256: | 6C7B6FAF5A493F036E6B69A0F4C9C7F1B86C068A56CE4D8D9A92C8EBDE0EAE99 |
| SSDEEP: | 98304:bkpqjhDeTRvEuXA1/pri9b4UhWl9WSykAPb4MN7O931gyLUyZgp/bPoP4ED:bPjhDeTR01/YF4Takw4MNPsZYDOD |
MALICIOUS
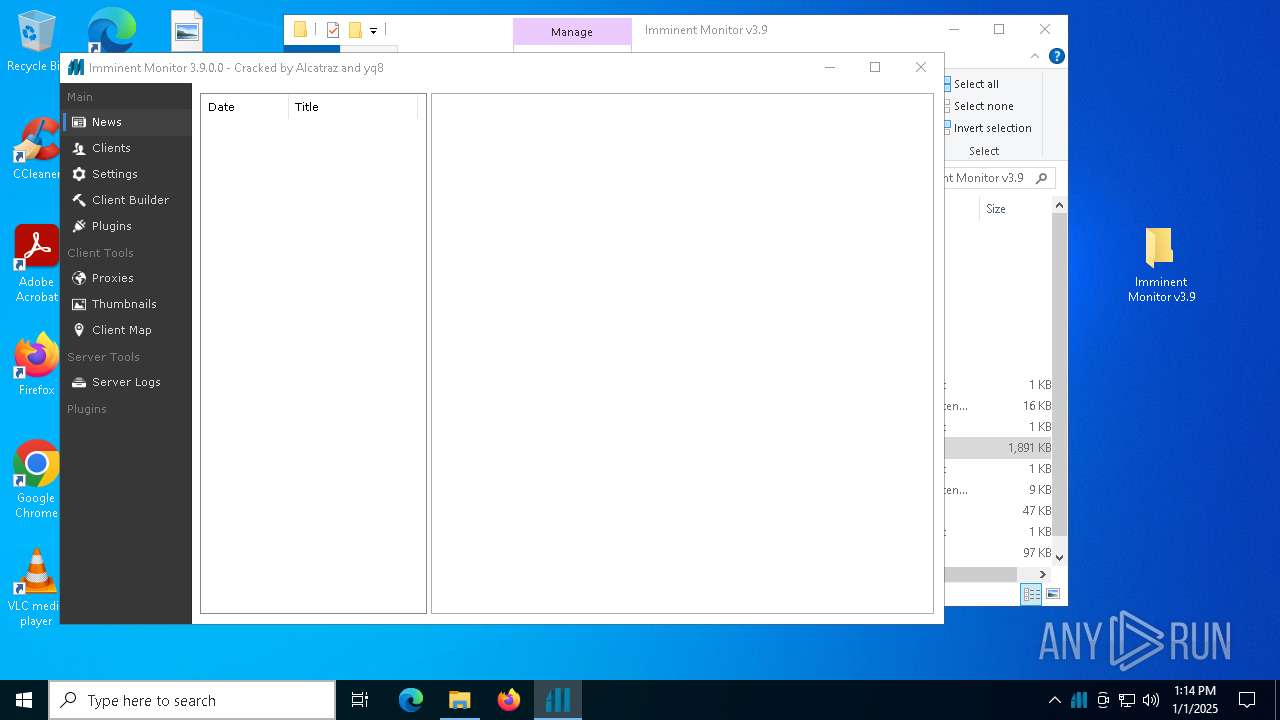
Starts Visual C# compiler
- Imminent Monitor 3.9.exe (PID: 3188)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6900)
Uses .NET C# to load dll
- Imminent Monitor 3.9.exe (PID: 3188)
Executable content was dropped or overwritten
- csc.exe (PID: 748)
- csc.exe (PID: 4388)
INFO
Checks supported languages
- Imminent Monitor 3.9.exe (PID: 3188)
- csc.exe (PID: 748)
- cvtres.exe (PID: 4872)
- csc.exe (PID: 4388)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6900)
The process uses the downloaded file
- WinRAR.exe (PID: 6900)
Reads the computer name
- Imminent Monitor 3.9.exe (PID: 3188)
Create files in a temporary directory
- cvtres.exe (PID: 4872)
- csc.exe (PID: 748)
- csc.exe (PID: 4388)
- Imminent Monitor 3.9.exe (PID: 3188)
Reads the machine GUID from the registry
- Imminent Monitor 3.9.exe (PID: 3188)
- csc.exe (PID: 748)
- cvtres.exe (PID: 4872)
- csc.exe (PID: 4388)
Confuser has been detected (YARA)
- Imminent Monitor 3.9.exe (PID: 3188)
Manual execution by a user
- Imminent Monitor 3.9.exe (PID: 3188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2017:07:25 23:26:48 |
| ZipCRC: | 0x4874fc6c |
| ZipCompressedSize: | 62 |
| ZipUncompressedSize: | 84 |
| ZipFileName: | Imminent Monitor v3.9/8C1A0000.log |
Total processes
132
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 748 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\2vlkiggp.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | Imminent Monitor 3.9.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 1228 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3188 | "C:\Users\admin\Desktop\Imminent Monitor v3.9\Imminent Monitor 3.9.exe" | C:\Users\admin\Desktop\Imminent Monitor v3.9\Imminent Monitor 3.9.exe | — | explorer.exe | |||||||||||
User: admin Company: Imminent Methods Integrity Level: MEDIUM Description: Imminent Monitor Version: 3.9.0.0 Modules
| |||||||||||||||
| 3288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4388 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\8_rn5vu3.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | Imminent Monitor 3.9.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 4444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4548 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESE5EF.tmp" "c:\Users\admin\AppData\Local\Temp\CSCE5EE.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.9672 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 4872 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESB49E.tmp" "c:\Users\admin\AppData\Local\Temp\CSCB49D.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.9672 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 6900 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Imminent Monitor v3.9.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 229
Read events
2 211
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Imminent Monitor v3.9.zip | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
13
Suspicious files
0
Text files
411
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\ClientPlugin.dll | executable | |
MD5:2B02DE4647260361B18DE39DF5AF1AC6 | SHA256:94E757AAF2F333D53EB0DD4F941FBD445D36FC27383201D60B3C1073CAC20EC1 | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\CRACK INFO.txt | text | |
MD5:1A804E8D3B4F6334E7D0F25371F3E582 | SHA256:95C233833E84BF7A2E357D05ABF5B018BBE1D4ADA63E0A17C564CB08ED266B87 | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\loader.log | text | |
MD5:8BCF05365B0B48E11F694F89BCF413F2 | SHA256:6AE863196E1AE95B6219882F75FDE8EA4DCB1D8EF4124F20D1E0B9B85A2831CF | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\Plugins\StressTester.imp | bs | |
MD5:CBD96B52EA3BE94011D2372C06A4A804 | SHA256:281F876F3BB526E0F7554208E7415B19B653561DBFC0D8CD2E01FB55545B8C69 | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\PluginCompiler.exe | executable | |
MD5:540ACCC16897D3039F610AD6CEF9B673 | SHA256:937D40D109C7B0AA6246639A8F3D5893C6DD62DEC94816B2CF5A0E89BE2BE325 | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\LZLoader.dll | executable | |
MD5:F93937B67A4A89EF91E122DDD30BB35C | SHA256:0245467395E61C0E873612F38705E47A4B72ACAAF0A3BA02EE65B20470488825 | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\readme.txt | text | |
MD5:F18053F678DCDA3F48498F3E8D843357 | SHA256:A6AEA03D68DA010E29FB09416573221B2DBE7FC4799C243099E1EF8FB330C294 | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\Plugins\DisableWebcamLights.imp | bs | |
MD5:EF9E22457EB8581D51603DE1AAD87BD3 | SHA256:9F6D7226856CF5D4EEBE724AE8CEB35BB4AFBBCA2140193F9540F8FAD6FBB501 | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\Builder (Imminent Monitor 4.1.0.0)\dnlib.dll | executable | |
MD5:0AB0C1BF5F465F5793E984B03303DE67 | SHA256:D9085E523927AAF38D78C998AF8743AB59EE7AEFEE01A5ACB380E9E7F96864D3 | |||
| 6900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6900.7902\Imminent Monitor v3.9\Imminent Monitor 3.9.exe | executable | |
MD5:67EB6B75152046AEA39083F45D4E9492 | SHA256:9078149DC6EE62AEA91749BA2DB9ABA15C9518F92BFE709B3BBA8523F92CD2E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
43
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
396 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6552 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
396 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 2.16.164.112:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |