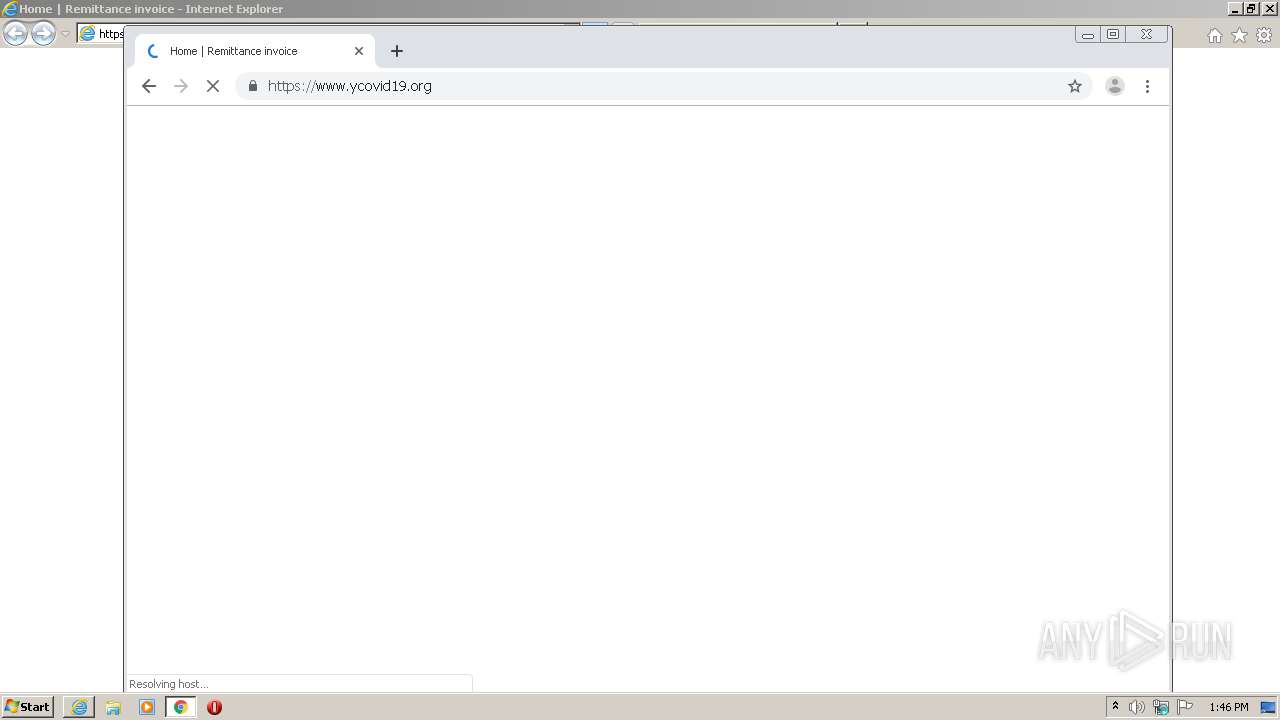
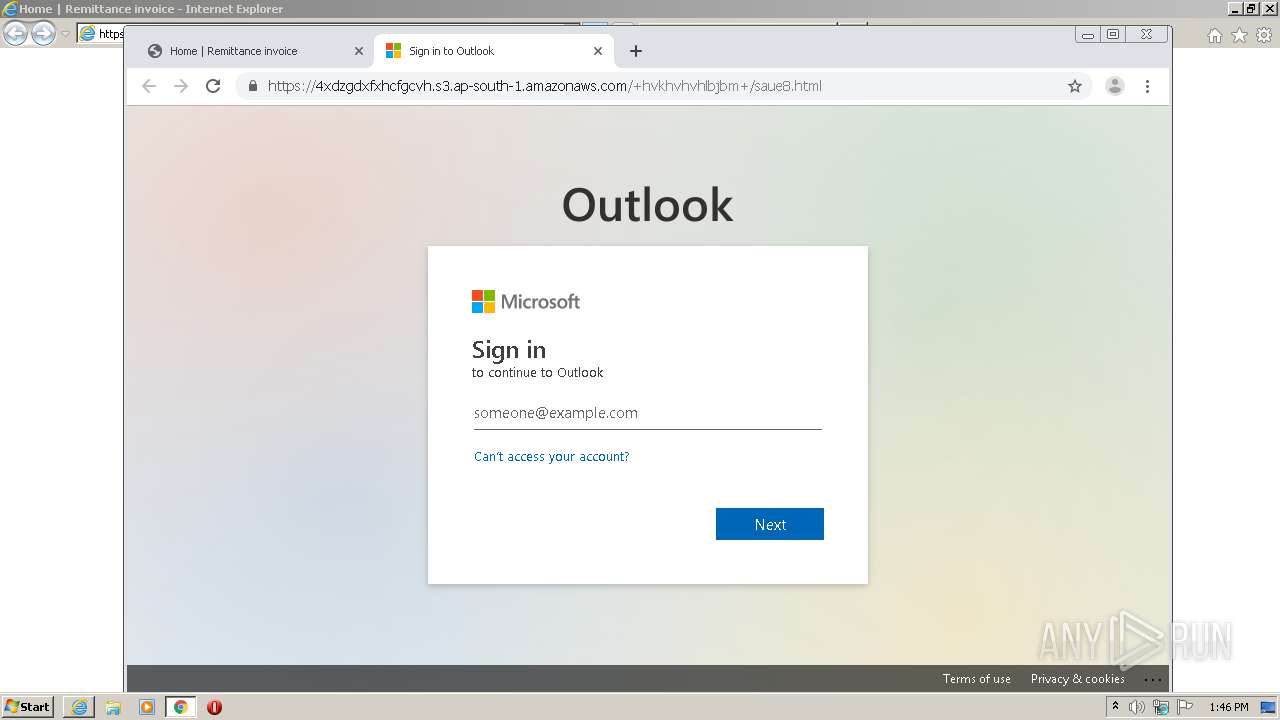
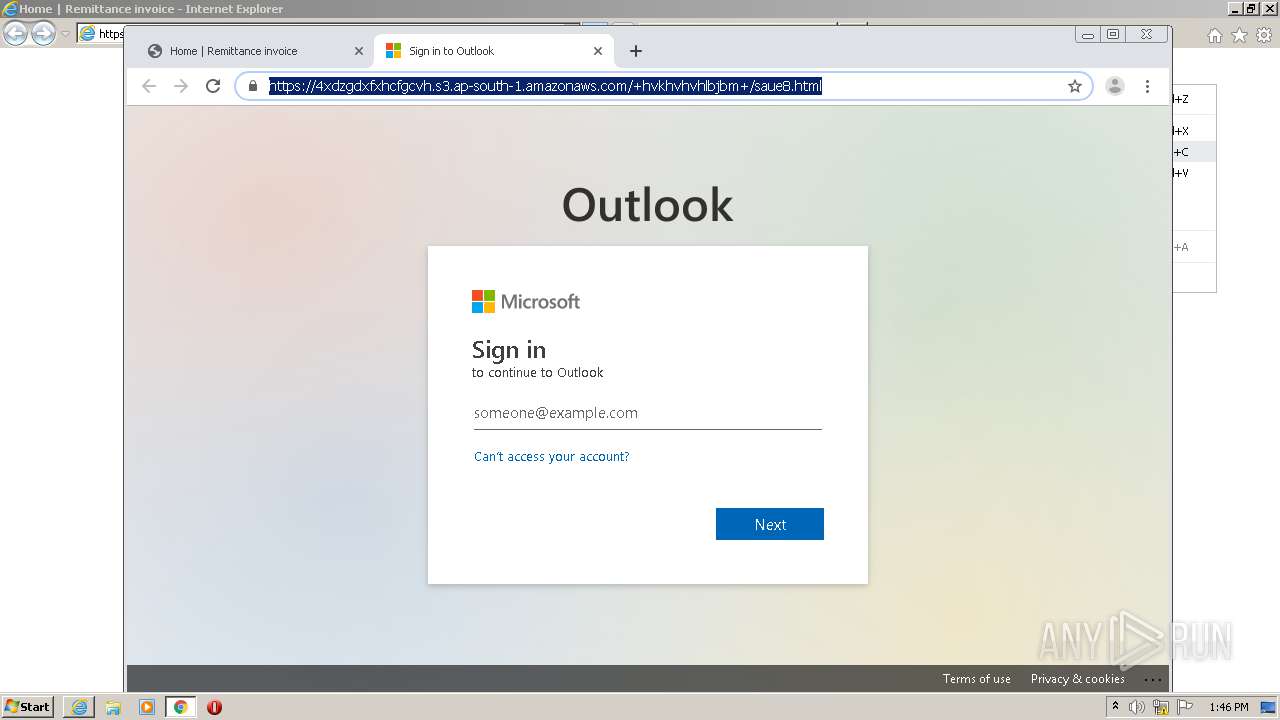
| URL: | https://nam11.safelinks.protection.outlook.com/?url=http%3A%2F%2Fwww.ycovid19.org%2F&data=04%7C01%7Cgail.gordon%40wizards.com%7C0f4f3e4d31e443a56dde08d91a23b86e%7C701edd3ec7a84789b1ce8a243620d68f%7C0%7C0%7C637569563013806008%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C0&sdata=Xv1UGoAkVMAGssJ%2BX4o9ElTZUk%2FuEK4HkXwSYVxgC%2BY%3D&reserved=0 |
| Full analysis: | https://app.any.run/tasks/a9fc0215-c05a-43fe-8d64-0d6d60a705d1 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2021, 12:45:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8265EA9D9D7A7139B45D42B3CECA9723 |
| SHA1: | EF012EF75F6724416E6DF53452D408C12711E933 |
| SHA256: | 6C65455532827428DF5BA4DE65222E563F382A1F135D96E764A95312FFEFC826 |
| SSDEEP: | 6:2LV9iRXPNHszlTLCRn1bsWLjVoyTaAL1sz5N6eVaVbeAiJbUuRCmVB7IAXLkcidW:2LqVsx61IOVoPl5sKP7RPBcyLkhE |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2064)
INFO
Application launched itself
- iexplore.exe (PID: 372)
- chrome.exe (PID: 2064)
Changes internet zones settings
- iexplore.exe (PID: 372)
Reads the hosts file
- chrome.exe (PID: 2064)
- chrome.exe (PID: 2500)
Changes settings of System certificates
- iexplore.exe (PID: 372)
Reads settings of System Certificates
- iexplore.exe (PID: 3956)
- iexplore.exe (PID: 372)
Manual execution by user
- chrome.exe (PID: 2064)
Reads internet explorer settings
- iexplore.exe (PID: 3956)
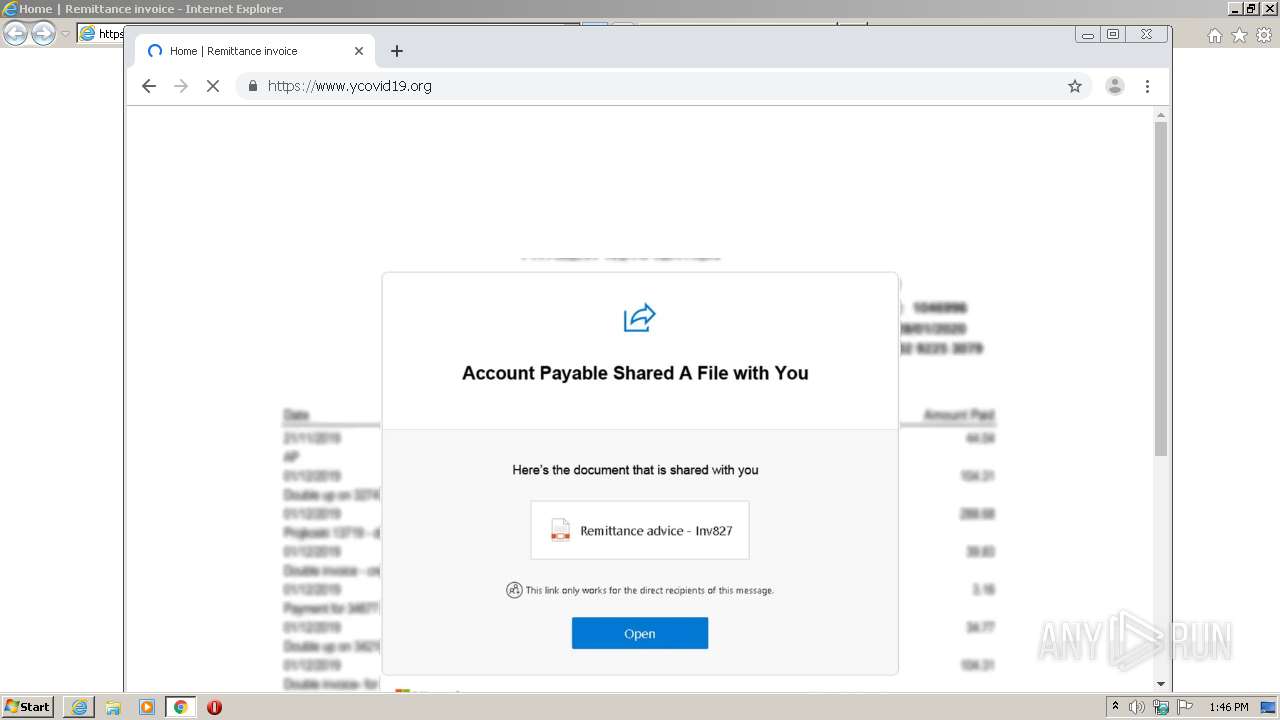
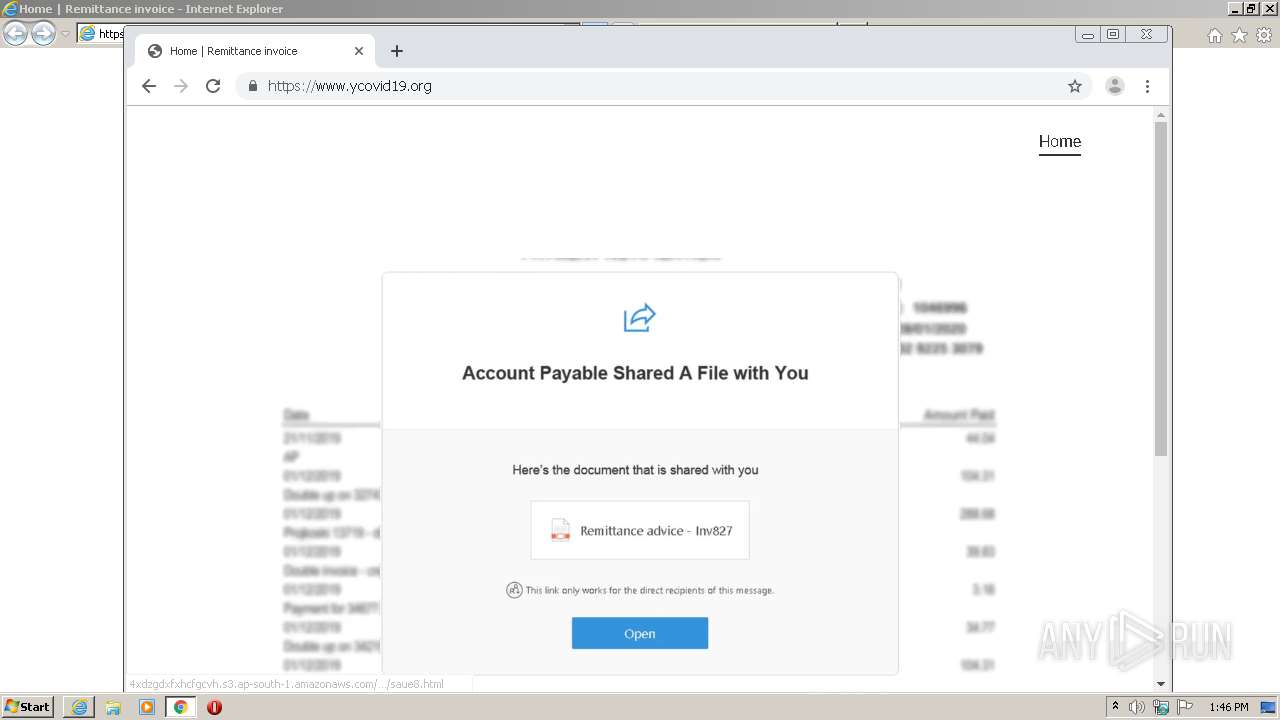
Drops Coronavirus (possible) decoy
- iexplore.exe (PID: 3956)
Adds / modifies Windows certificates
- iexplore.exe (PID: 372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
79
Monitored processes
41
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://nam11.safelinks.protection.outlook.com/?url=http%3A%2F%2Fwww.ycovid19.org%2F&data=04%7C01%7Cgail.gordon%40wizards.com%7C0f4f3e4d31e443a56dde08d91a23b86e%7C701edd3ec7a84789b1ce8a243620d68f%7C0%7C0%7C637569563013806008%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C0&sdata=Xv1UGoAkVMAGssJ%2BX4o9ElTZUk%2FuEK4HkXwSYVxgC%2BY%3D&reserved=0" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,5183609452478628022,13063727677680979598,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11940954366486359528 --mojo-platform-channel-handle=2868 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,5183609452478628022,13063727677680979598,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9891066180378196032 --renderer-client-id=18 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3984 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,5183609452478628022,13063727677680979598,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13998195015312453786 --mojo-platform-channel-handle=4732 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,5183609452478628022,13063727677680979598,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6778732036385807861 --mojo-platform-channel-handle=3776 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6a69a9d0,0x6a69a9e0,0x6a69a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,5183609452478628022,13063727677680979598,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5913282903684407245 --mojo-platform-channel-handle=2920 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,5183609452478628022,13063727677680979598,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15168467138915537808 --renderer-client-id=34 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4076 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,5183609452478628022,13063727677680979598,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17295155780078712426 --mojo-platform-channel-handle=3936 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,5183609452478628022,13063727677680979598,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2095494396519184547 --mojo-platform-channel-handle=3296 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
838
Read events
696
Write events
134
Delete events
8
Modification events
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 4005445136 | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30887084 | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
43
Text files
305
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab2FA2.tmp | — | |
MD5:— | SHA256:— | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar2FA3.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60A5087F-810.pma | — | |
MD5:— | SHA256:— | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6DB145CFEEC544B1582FED1ADA3370DD | binary | |
MD5:— | SHA256:— | |||
| 2064 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2064 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\973b3d32-11db-4ccd-bfdc-b9528b351ed0.tmp | — | |
MD5:— | SHA256:— | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\644B8874112055B5E195ECB0E8F243A4 | der | |
MD5:— | SHA256:— | |||
| 2064 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2064 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFf41e2.TMP | text | |
MD5:— | SHA256:— | |||
| 2064 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFf41f1.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
83
DNS requests
41
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3956 | iexplore.exe | GET | 301 | 52.49.20.157:80 | http://www.ycovid19.org/ | IE | — | — | suspicious |
2500 | chrome.exe | GET | 301 | 52.49.20.157:80 | http://www.ycovid19.org/ | IE | — | — | suspicious |
3956 | iexplore.exe | GET | 200 | 23.203.65.92:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
3956 | iexplore.exe | GET | 200 | 2.22.9.80:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | unknown | der | 1.16 Kb | whitelisted |
3956 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 631 b | whitelisted |
3956 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://crl.globalsign.com/root-r3.crl | US | der | 1.72 Kb | whitelisted |
3956 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertGlobalRootCA.crl | US | der | 631 b | whitelisted |
372 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEA8aVkWYLIkXQFXHYN8Oxso%3D | US | der | 471 b | whitelisted |
3956 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGCDPAjbzpoUYuu%2B39wE%3D | US | der | 1.48 Kb | whitelisted |
372 | iexplore.exe | GET | 200 | 131.253.33.200:80 | http://www.bing.com/favicon.ico | US | image | 4.19 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3956 | iexplore.exe | 104.47.56.156:443 | nam11.safelinks.protection.outlook.com | Microsoft Corporation | US | suspicious |
3956 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
372 | iexplore.exe | 131.253.33.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 23.203.65.92:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | unknown |
3956 | iexplore.exe | 52.49.20.157:80 | www.ycovid19.org | Amazon.com, Inc. | IE | suspicious |
3956 | iexplore.exe | 52.49.20.157:443 | www.ycovid19.org | Amazon.com, Inc. | IE | suspicious |
3956 | iexplore.exe | 2.22.9.80:80 | crl.identrust.com | Akamai International B.V. | — | unknown |
2500 | chrome.exe | 142.250.181.237:443 | accounts.google.com | Google Inc. | US | suspicious |
2500 | chrome.exe | 142.250.185.131:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3956 | iexplore.exe | 151.101.2.2:443 | fonts.jimstatic.com | Fastly | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nam11.safelinks.protection.outlook.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
www.ycovid19.org |
| suspicious |
crl.identrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
crl3.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1040 | svchost.exe | Potentially Bad Traffic | ET INFO Suspicious Domain Request for Possible COVID-19 Domain M1 |
3956 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |
3956 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious TLS SNI Request for Possible COVID-19 Domain M1 |
3956 | iexplore.exe | Potentially Bad Traffic | ET INFO Possible COVID-19 Domain in SSL Certificate M2 |
1040 | svchost.exe | Potentially Bad Traffic | ET INFO Suspicious Domain Request for Possible COVID-19 Domain M1 |
372 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious TLS SNI Request for Possible COVID-19 Domain M1 |
372 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious TLS SNI Request for Possible COVID-19 Domain M1 |
372 | iexplore.exe | Potentially Bad Traffic | ET INFO Possible COVID-19 Domain in SSL Certificate M2 |
372 | iexplore.exe | Potentially Bad Traffic | ET INFO Possible COVID-19 Domain in SSL Certificate M2 |
1040 | svchost.exe | Potentially Bad Traffic | ET INFO Suspicious Domain Request for Possible COVID-19 Domain M1 |