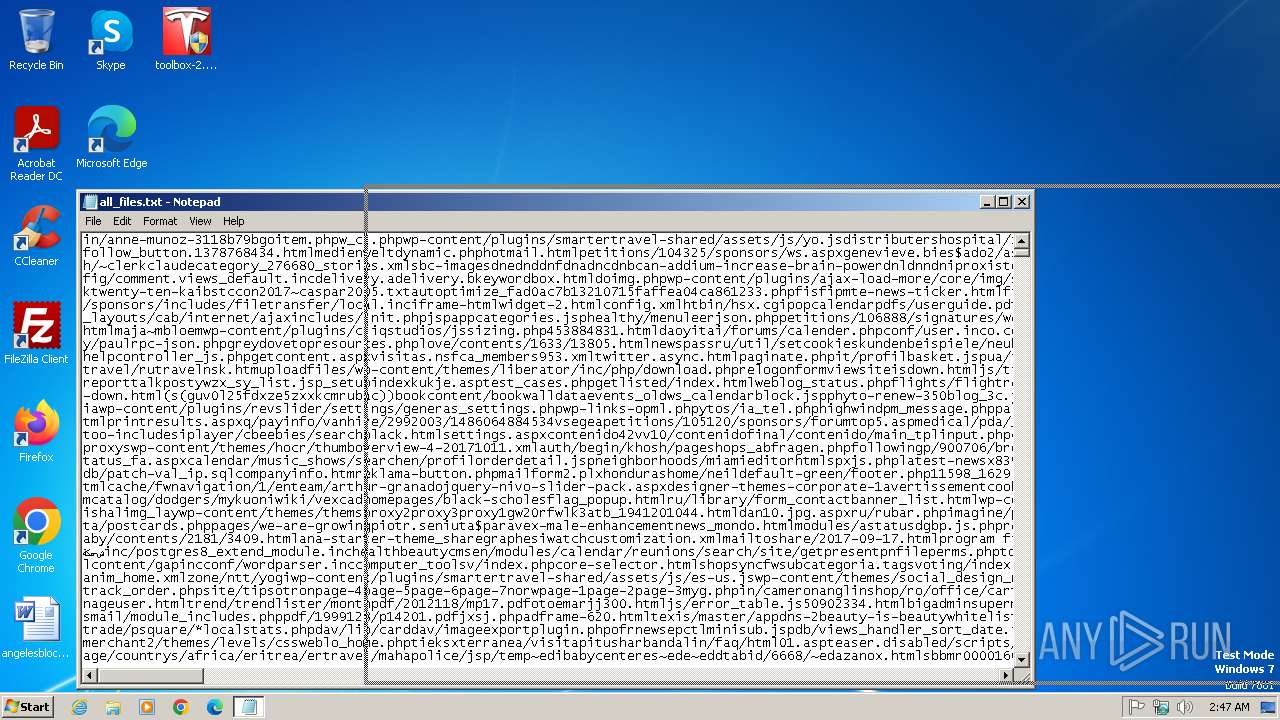
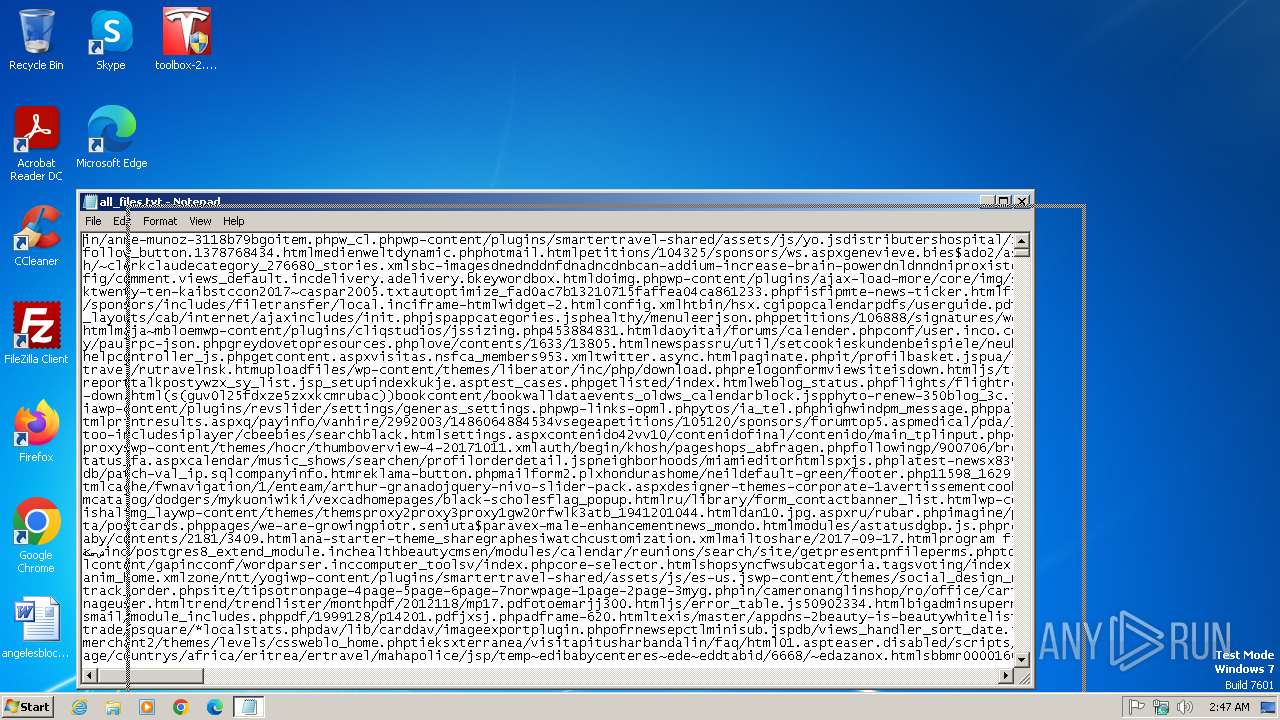
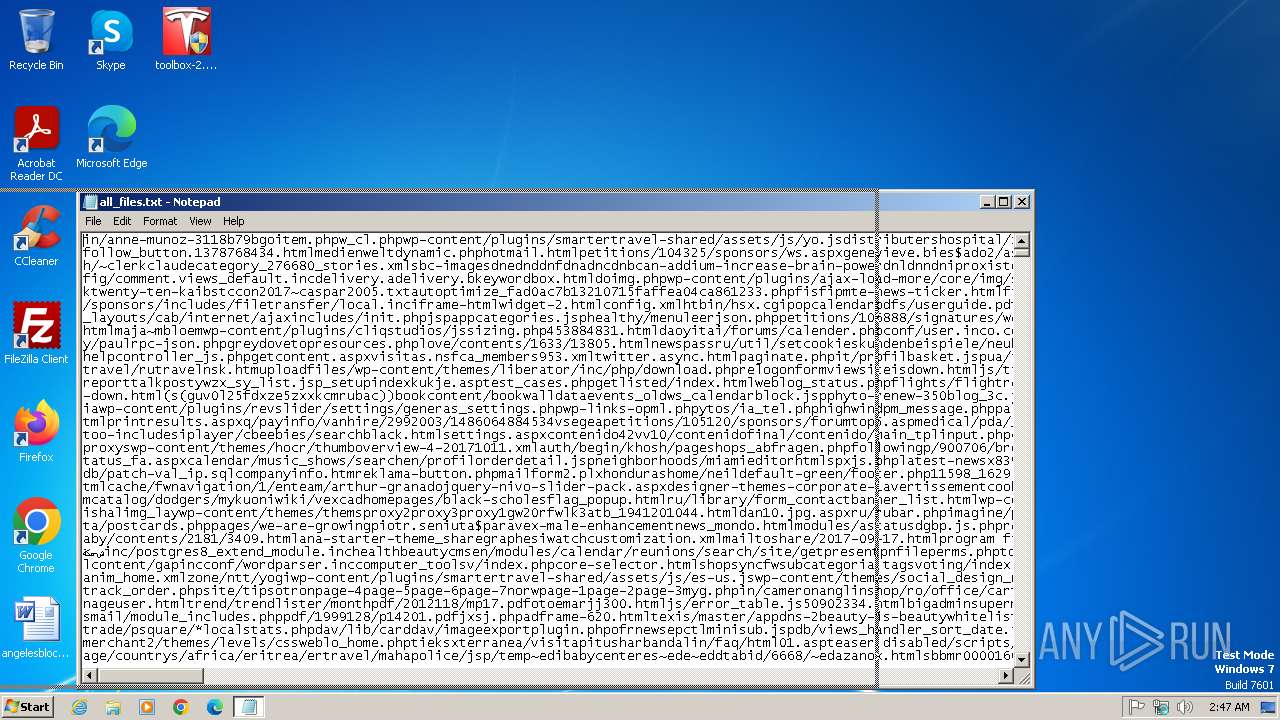
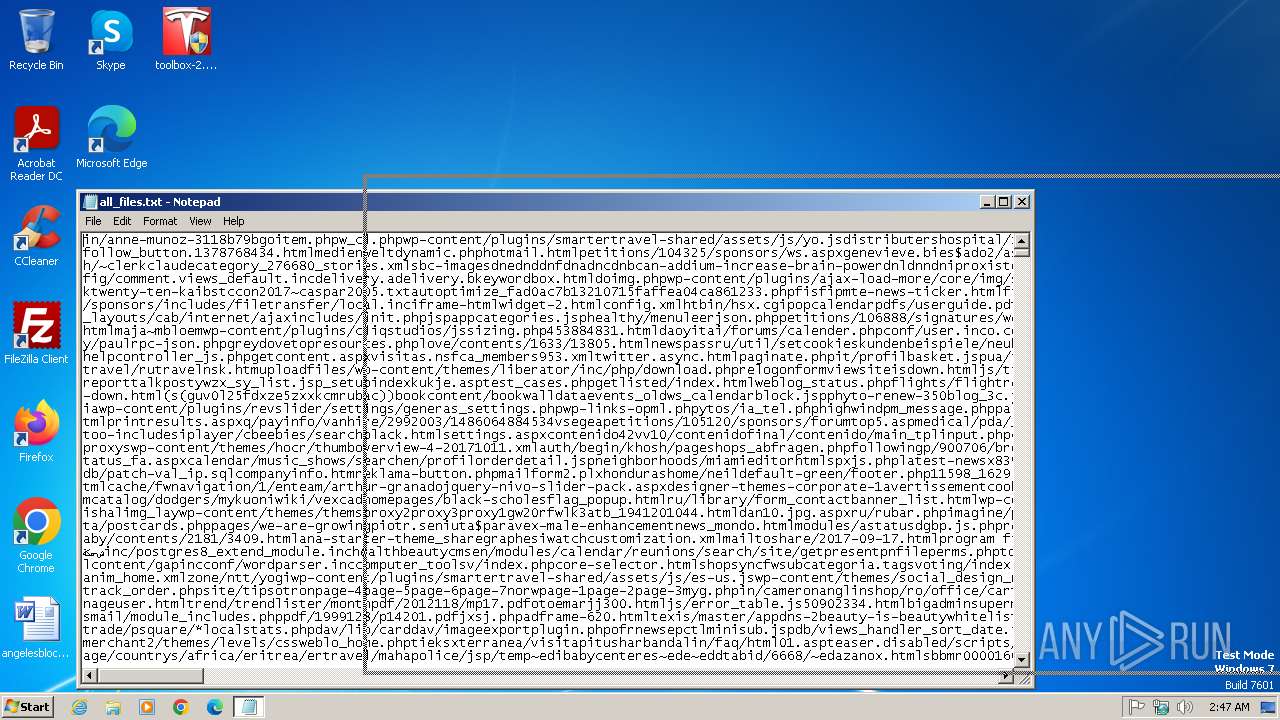
| File name: | all_files.txt |
| Full analysis: | https://app.any.run/tasks/453b1ab6-b51f-40e7-b5c2-53ac3d6b36c4 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 02:47:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text |
| MD5: | AA3A1B6150F27DA642B66104D7409B7E |
| SHA1: | AFA25E71ADA92E922616B0CBE52211B442557902 |
| SHA256: | 6C319D7997173BB42BAD59EA9DD2257B98B09DF85B1E545BDC54D5A4B47440B3 |
| SSDEEP: | 49152:x8SkTEW94hboq+ozruqkdWWIhmMlKOmnLACZpB+KVQAGVTYAXnrRIsISf8IscHv+:B2BbGXE/EzXvDa+FeWNwHHXnDNAM |
MALICIOUS
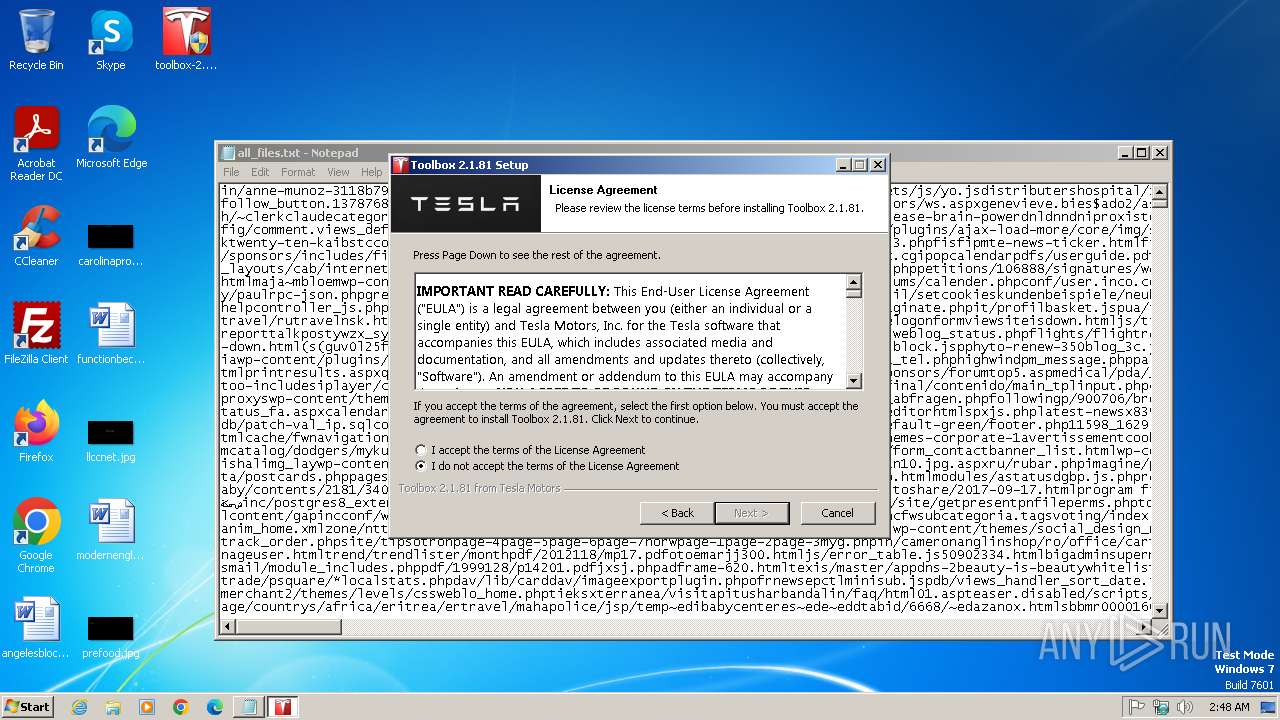
Executing a file with an untrusted certificate
- vc_redist.x86.exe (PID: 2612)
- vc_redist.x86.exe (PID: 1888)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
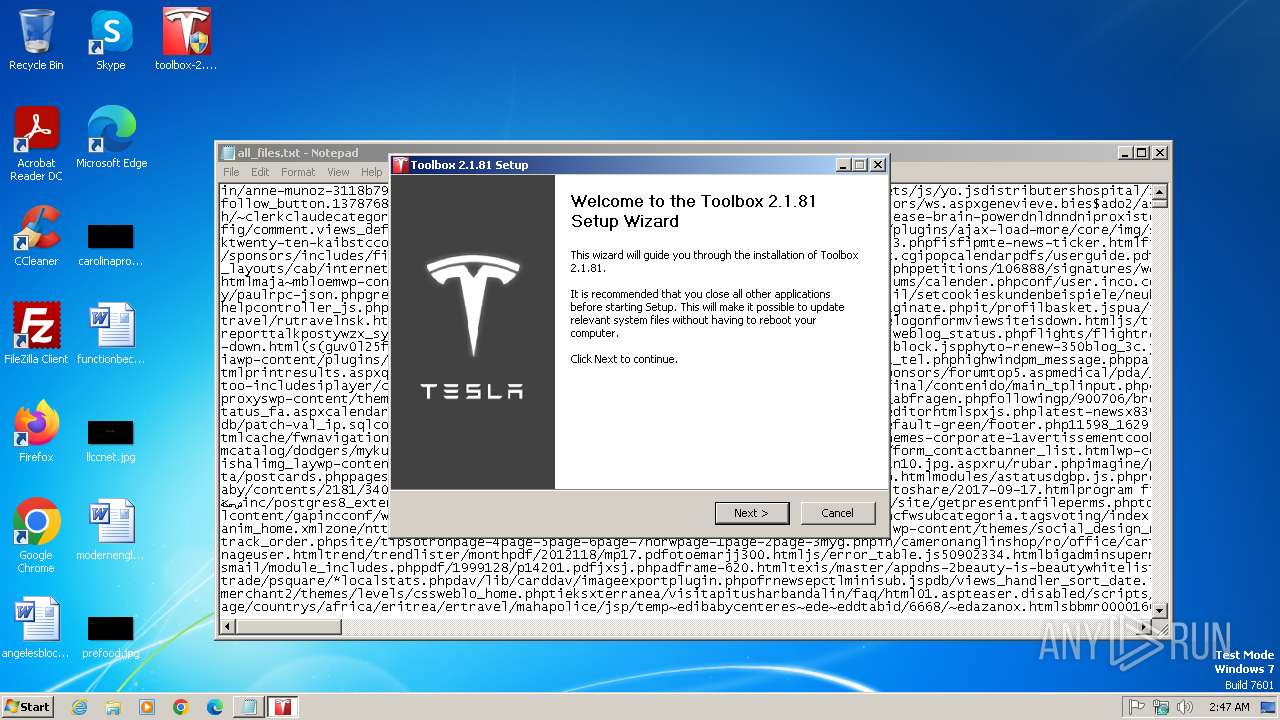
- toolbox-2.1.81-win32.exe (PID: 2592)
Application launched itself
- vc_redist.x86.exe (PID: 2612)
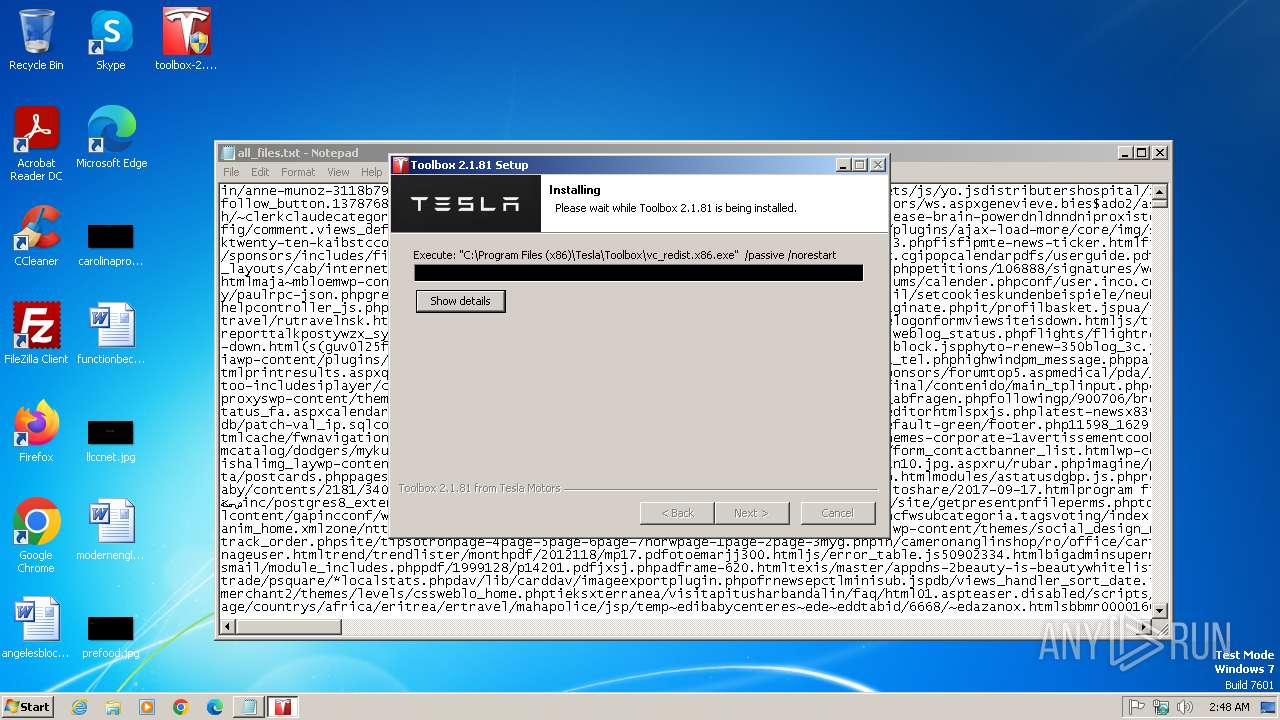
Process drops python dynamic module
- toolbox-2.1.81-win32.exe (PID: 2592)
Executable content was dropped or overwritten
- vc_redist.x86.exe (PID: 1888)
- toolbox-2.1.81-win32.exe (PID: 2592)
Process drops legitimate windows executable
- vc_redist.x86.exe (PID: 1888)
- toolbox-2.1.81-win32.exe (PID: 2592)
The process creates files with name similar to system file names
- toolbox-2.1.81-win32.exe (PID: 2592)
There is functionality for taking screenshot (YARA)
- toolbox-2.1.81-win32.exe (PID: 2592)
Searches for installed software
- vc_redist.x86.exe (PID: 1888)
INFO
Manual execution by a user
- toolbox-2.1.81-win32.exe (PID: 1964)
- toolbox-2.1.81-win32.exe (PID: 2592)
Reads the computer name
- toolbox-2.1.81-win32.exe (PID: 2592)
- vc_redist.x86.exe (PID: 2612)
- vc_redist.x86.exe (PID: 1888)
Checks supported languages
- toolbox-2.1.81-win32.exe (PID: 2592)
- vc_redist.x86.exe (PID: 2612)
- vc_redist.x86.exe (PID: 1888)
Create files in a temporary directory
- toolbox-2.1.81-win32.exe (PID: 2592)
- vc_redist.x86.exe (PID: 1888)
Creates files in the program directory
- toolbox-2.1.81-win32.exe (PID: 2592)
The sample compiled with english language support
- vc_redist.x86.exe (PID: 1888)
- toolbox-2.1.81-win32.exe (PID: 2592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1888 | "C:\Program Files (x86)\Tesla\Toolbox\vc_redist.x86.exe" /passive /norestart -burn.unelevated BurnPipe.{41139438-50EE-424E-B8A1-4659C4771077} {F53D871E-9B58-445F-B40F-4FE02F7BD26E} 2612 | C:\Program Files (x86)\Tesla\Toolbox\vc_redist.x86.exe | vc_redist.x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015 Redistributable (x86) - 14.0.24215 Exit code: 1638 Version: 14.0.24215.1 Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\Desktop\toolbox-2.1.81-win32.exe" | C:\Users\admin\Desktop\toolbox-2.1.81-win32.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2592 | "C:\Users\admin\Desktop\toolbox-2.1.81-win32.exe" | C:\Users\admin\Desktop\toolbox-2.1.81-win32.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2612 | "C:\Program Files (x86)\Tesla\Toolbox\vc_redist.x86.exe" /passive /norestart | C:\Program Files (x86)\Tesla\Toolbox\vc_redist.x86.exe | — | toolbox-2.1.81-win32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015 Redistributable (x86) - 14.0.24215 Exit code: 1638 Version: 14.0.24215.1 Modules
| |||||||||||||||
| 2736 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\all_files.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 265
Read events
1 261
Write events
4
Delete events
0
Modification events
| (PID) Process: | (2736) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 214 | |||
| (PID) Process: | (2736) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 140 | |||
| (PID) Process: | (2736) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (2736) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
Executable files
130
Suspicious files
2
Text files
897
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2592 | toolbox-2.1.81-win32.exe | C:\Users\admin\AppData\Local\Temp\nsd628E.tmp\modern-wizard.bmp | image | |
MD5:70E067D8627BDCF11EED2F984308A912 | SHA256:40C0C9CF5765F114398A48CA12271C7148FAC6E0D1F0BA912963C4279C0E84D6 | |||
| 1888 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{e2803110-78b3-4664-a479-3611a381656a}\.ba1\1029\license.rtf | text | |
MD5:F2D8C94464B459E9EB907C3FEB941A9C | SHA256:F2DB4BF289198917EC1CF8FBC8B65A91A96C76EDEF46476CEE4F9E88FF8B9936 | |||
| 1888 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{e2803110-78b3-4664-a479-3611a381656a}\.ba1\1045\license.rtf | text | |
MD5:E544B7FBAF6DB4DE6DB8A7D099FCE21F | SHA256:3EB6AD3F289D8D5C8A946CA1609B1538E83959D285C40EEE297CEBC1CFD8265D | |||
| 1888 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{e2803110-78b3-4664-a479-3611a381656a}\.ba1\1046\license.rtf | text | |
MD5:9C2457FBEDD9770A006876032DF57259 | SHA256:83FFDD5E96773C92B5A5C3352D0F61FA6A1D32D1876B87BE24CCC5F80C0FC794 | |||
| 2592 | toolbox-2.1.81-win32.exe | C:\Users\admin\AppData\Local\Temp\nsd628E.tmp\System.dll | executable | |
MD5:C17103AE9072A06DA581DEC998343FC1 | SHA256:DC58D8AD81CACB0C1ED72E33BFF8F23EA40B5252B5BB55D393A0903E6819AE2F | |||
| 2592 | toolbox-2.1.81-win32.exe | C:\Users\admin\AppData\Local\Temp\nsd628E.tmp\modern-header.bmp | image | |
MD5:8586D654E04B1E58DE06527CF4ED8726 | SHA256:8F39A98B4D5E87BF91A0B80BB6E9E21CC7C030DFB3689BEBEEB68878E33C6766 | |||
| 1888 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{e2803110-78b3-4664-a479-3611a381656a}\.ba1\wixstdba.dll | executable | |
MD5:4D20A950A3571D11236482754B4A8E76 | SHA256:A9295AD4E909F979E2B6CB2B2495C3D35C8517E689CD64A918C690E17B49078B | |||
| 1888 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{e2803110-78b3-4664-a479-3611a381656a}\.ba1\1036\license.rtf | text | |
MD5:B2425005ED1EC70689F598544842F760 | SHA256:276DED59422B72402E7AEF6431628F705ABC465D14ED24AF2E53C22DDC86E35F | |||
| 2592 | toolbox-2.1.81-win32.exe | C:\Users\admin\AppData\Local\Temp\nsd628E.tmp\nsDialogs.dll | executable | |
MD5:C10E04DD4AD4277D5ADC951BB331C777 | SHA256:E31AD6C6E82E603378CB6B80E67D0E0DCD9CF384E1199AC5A65CB4935680021A | |||
| 1888 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{e2803110-78b3-4664-a479-3611a381656a}\.ba1\1042\license.rtf | text | |
MD5:D66807A2D5E059061BF3C8CF60238C3C | SHA256:503C25737668D3234B6E7BFFFE664A657868E57D93E65400930E460FEF13472B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |