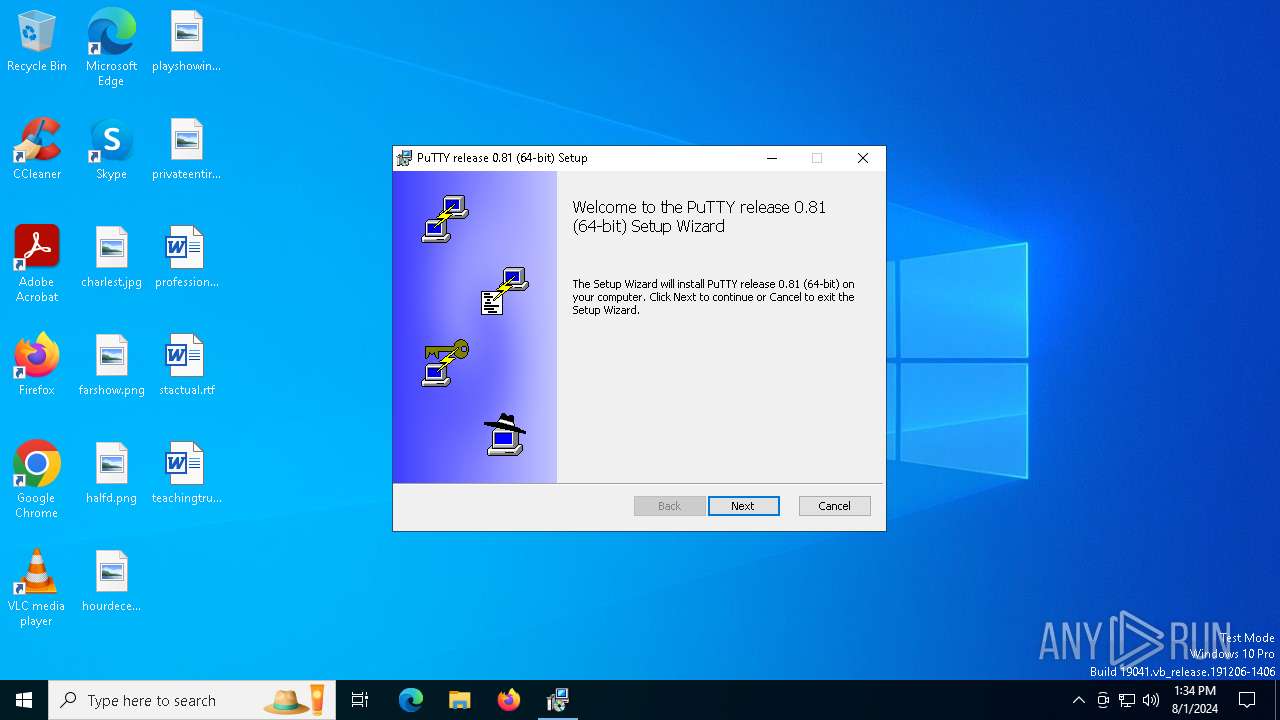
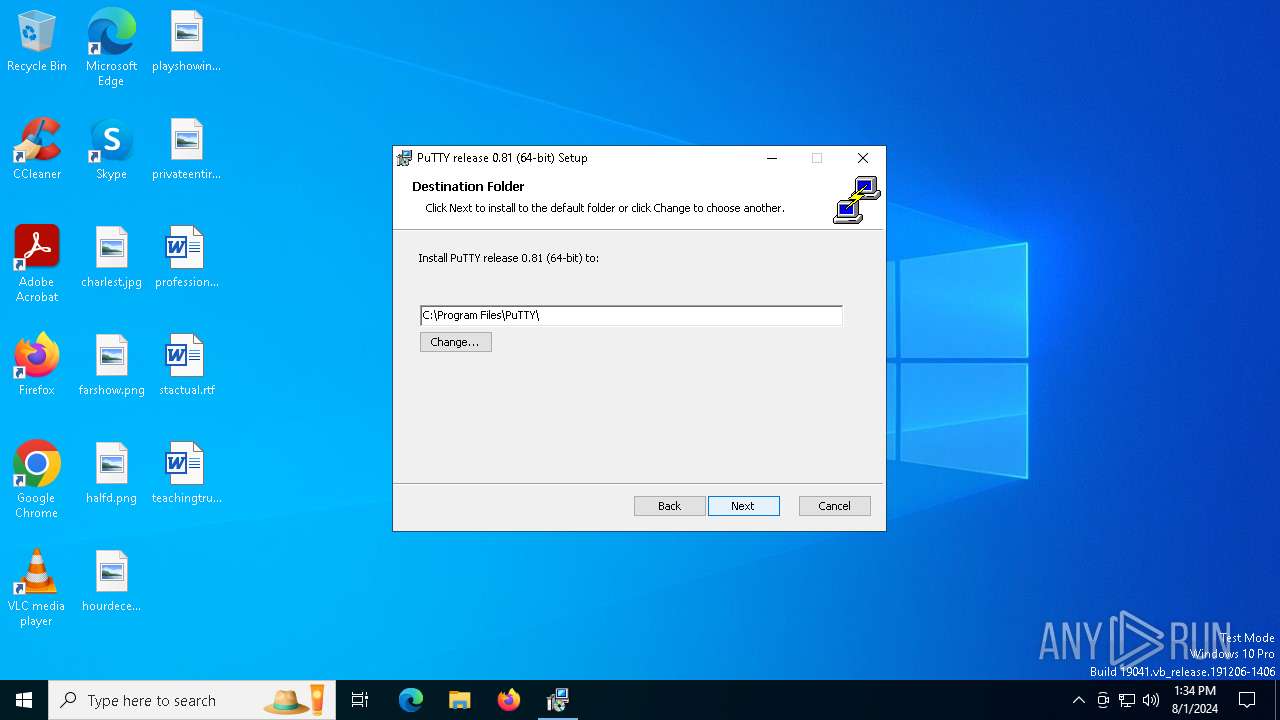
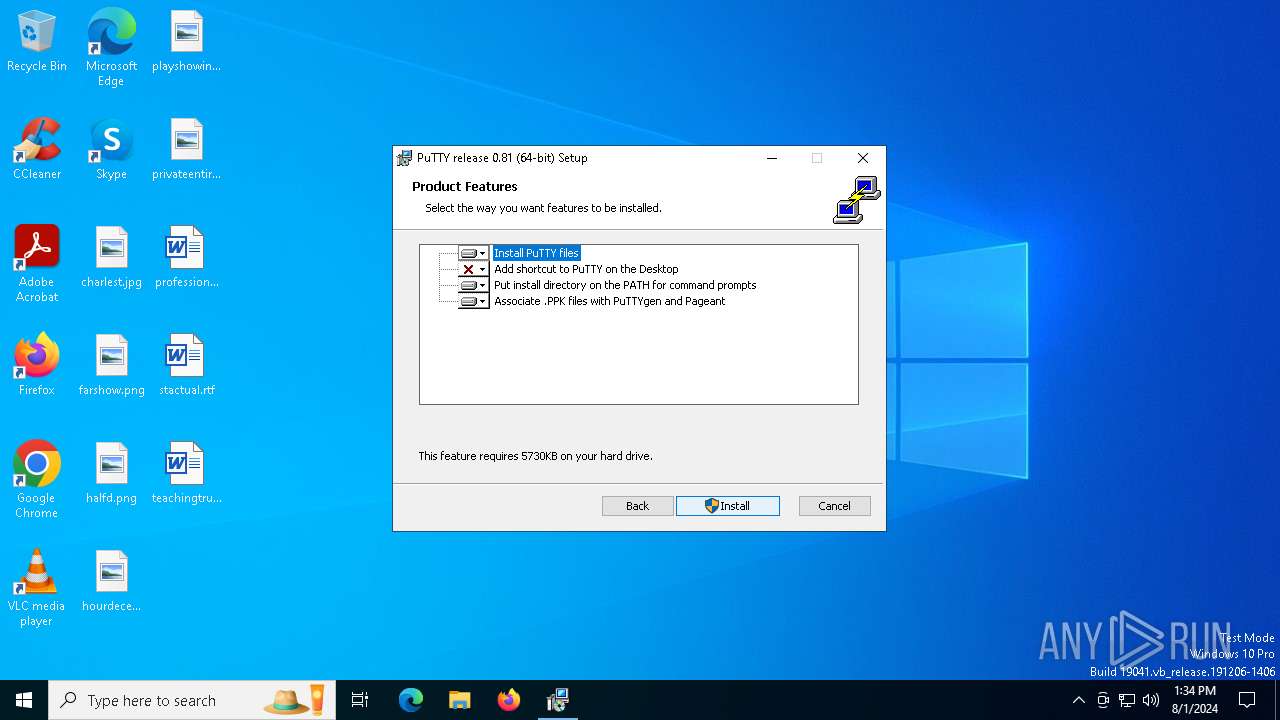
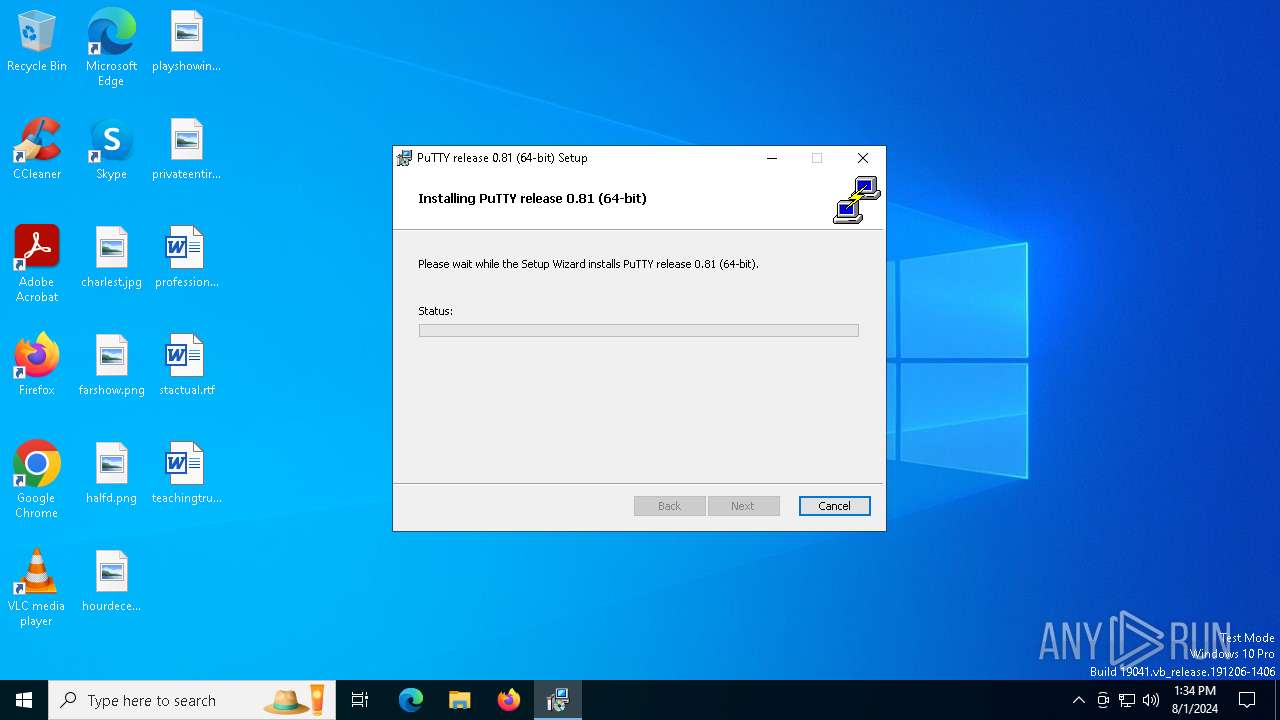
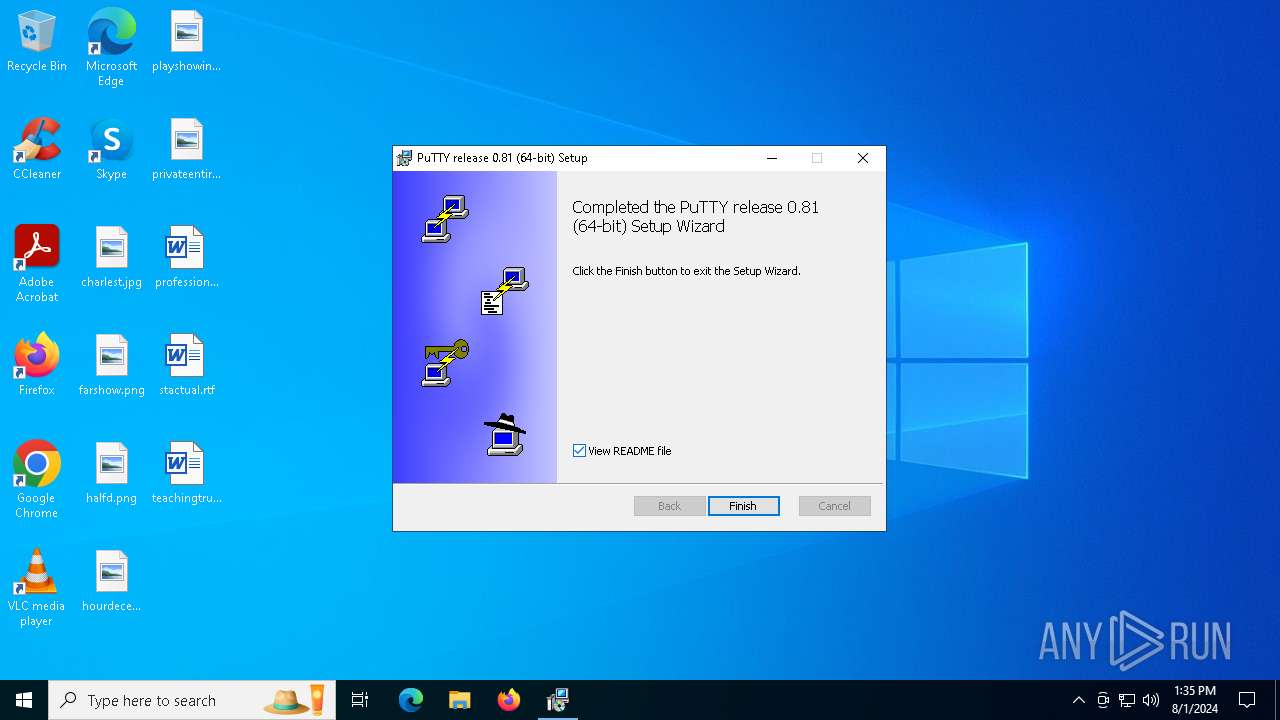
| download: | /~sgtatham/putty/0.81/w64/putty-64bit-0.81-installer.msi |
| Full analysis: | https://app.any.run/tasks/f55604b0-83f3-4c72-818e-ed89378d032c |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 13:34:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: PuTTY release 0.81 installer, Author: Simon Tatham, Keywords: Installer, Comments: This installer database contains the logic and data required to install PuTTY release 0.81 (64-bit)., Template: x64;1033, Revision Number: {CD423CA9-77AE-420D-911E-E30753A041AA}, Create Time/Date: Sat Apr 6 10:49:02 2024, Last Saved Time/Date: Sat Apr 6 10:49:02 2024, Number of Pages: 200, Number of Words: 2, Number of Characters: 0, Name of Creating Application: Windows Installer XML Toolset (), Security: 2 |
| MD5: | E09759AA290CF38F481F3F25384EA7AA |
| SHA1: | 92BAD6635166A6579B38D3065FB10D589A9BD98D |
| SHA256: | 6C297C89D32D7FB5C6D10B1DA2612C9557A5126715C4A78690D5D8067488F5F2 |
| SSDEEP: | 98304:rZ3iKwHRKnGsb6HFhDSVcO8aLIzXMbMspk19RziDlW1j5u/TRD4IP5KwGTkS0kv9:c4VgaA |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 6888)
- msiexec.exe (PID: 7076)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 5944)
Checks Windows Trust Settings
- msiexec.exe (PID: 7076)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7076)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4692)
Reads the date of Windows installation
- msiexec.exe (PID: 4692)
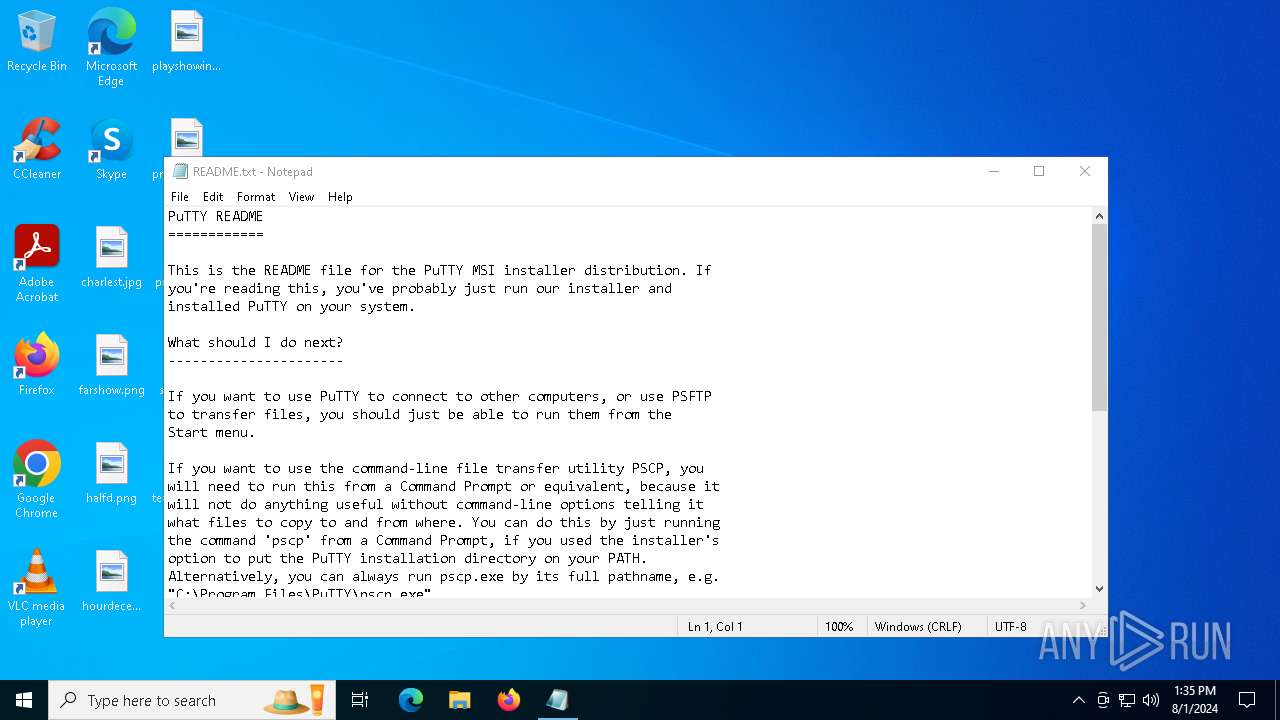
Start notepad (likely ransomware note)
- msiexec.exe (PID: 4692)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6888)
- notepad.exe (PID: 5924)
Reads the software policy settings
- msiexec.exe (PID: 6888)
- msiexec.exe (PID: 7076)
Creates files or folders in the user directory
- msiexec.exe (PID: 6888)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7076)
- msiexec.exe (PID: 6888)
Reads the computer name
- msiexec.exe (PID: 7076)
- msiexec.exe (PID: 4692)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7076)
Creates a software uninstall entry
- msiexec.exe (PID: 7076)
Process checks computer location settings
- msiexec.exe (PID: 4692)
Checks proxy server information
- msiexec.exe (PID: 6888)
Checks supported languages
- msiexec.exe (PID: 7076)
- msiexec.exe (PID: 4692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | PuTTY release 0.81 installer |
| Author: | Simon Tatham |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install PuTTY release 0.81 (64-bit). |
| Template: | x64;1033 |
| RevisionNumber: | {CD423CA9-77AE-420D-911E-E30753A041AA} |
| CreateDate: | 2024:04:06 10:49:02 |
| ModifyDate: | 2024:04:06 10:49:02 |
| Pages: | 200 |
| Words: | 2 |
| Characters: | - |
| Software: | Windows Installer XML Toolset () |
| Security: | Read-only recommended |
Total processes
133
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4692 | C:\Windows\syswow64\MsiExec.exe -Embedding 4C4B2F4790BF981113FE43A3A88D9579 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5924 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Program Files\PuTTY\README.txt | C:\Windows\SysWOW64\notepad.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5944 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6632 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6888 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\putty-64bit-0.81-installer.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7076 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 341
Read events
14 034
Write events
288
Delete events
19
Modification events
| (PID) Process: | (7076) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000DA72C69817E4DA01A41B000070170000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7076) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000DA72C69817E4DA01A41B000070170000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7076) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000506E049917E4DA01A41B000070170000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7076) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000506E049917E4DA01A41B000070170000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7076) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000C8D1069917E4DA01A41B000070170000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7076) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000F7980B9917E4DA01A41B000070170000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7076) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7076) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000095C6829917E4DA01A41B000070170000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000111F919917E4DA013817000070180000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000111F919917E4DA013817000078060000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
10
Suspicious files
32
Text files
3
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7076 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_93702E680A5530C052C8D2BA33A2225F | binary | |
MD5:06C7CF9F1E7D34B86CA099CBE2F02499 | SHA256:DD49830D669EADDB476101FE24AAF6EB4BEFD673CBABBDF4B223D157DBC25042 | |||
| 6888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\AEACCDA8653DD8D7B2EA32F21D15D44F_383EB3891E16580A90C892D349C28A00 | der | |
MD5:8576B6152266EB131E672D80E9A1CDB8 | SHA256:9413E8F8F7327899FF8F2D3BEEAEF75D5835E632812192E4A997652734CD2BA7 | |||
| 7076 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:90545B4A66B5D108F033B27D23E4E225 | SHA256:355C7C09BA24385F42FC601149BB8B1B10AB0F583A245318FAC66D534B8E5707 | |||
| 6888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\AEACCDA8653DD8D7B2EA32F21D15D44F_383EB3891E16580A90C892D349C28A00 | binary | |
MD5:CBD14B0D8EDDE59F22048705ABD4EE87 | SHA256:8A8D86066F9F26D85B31272845324B29F5E3B2FED315CB3E7B2F736D39F6E7E3 | |||
| 6888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\18E6B4A57A6BC7EC9B861CDF2D6D0D02_C3B142D2C5374581DC2FDFFDEDBDEDDB | binary | |
MD5:DF19193F5E2F7EDBC3DBBC5A88A2D960 | SHA256:D2E5CFA45288C2E5F05AD1EFC560F6E521531FAFA40BCE84118B7A4927209131 | |||
| 7076 | msiexec.exe | C:\Program Files\PuTTY\pageant.exe | executable | |
MD5:DE75A8F6B061E2647DCBD7C405F956AF | SHA256:5CF5B9411F2E0D0525AA057643D6D5D159D87F5FEC86AB3689F261643A018A9B | |||
| 7076 | msiexec.exe | C:\Program Files\PuTTY\pscp.exe | executable | |
MD5:8276E93346B422948795636C7BA69911 | SHA256:15416C2DBCEDBE0BC6E01FD541A275064DDB4DBEDDC62843EE35984CE897CC4D | |||
| 6888 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI7E15.tmp | executable | |
MD5:D9AC1B56EDF330A6EB7894AB293F14F6 | SHA256:097F1C3F27B18010448D77E3F70C4D9F774CB9C5AB435C62BAA1C00E4CADD5EF | |||
| 7076 | msiexec.exe | C:\Windows\Temp\~DF7062CF2937903A74.TMP | binary | |
MD5:90545B4A66B5D108F033B27D23E4E225 | SHA256:355C7C09BA24385F42FC601149BB8B1B10AB0F583A245318FAC66D534B8E5707 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
46
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6888 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
4168 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6888 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
6604 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6888 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVD%2BnGf79Hpedv3mhy6uKMVZkPCQQUDyrLIIcouOxvSK4rVKYpqhekzQwCEQCOP7%2B5G%2BbaBBukH3qYOtYe | unknown | — | — | whitelisted |
6628 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4060 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5336 | SearchApp.exe | 2.23.209.168:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4168 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4168 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6888 | msiexec.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |