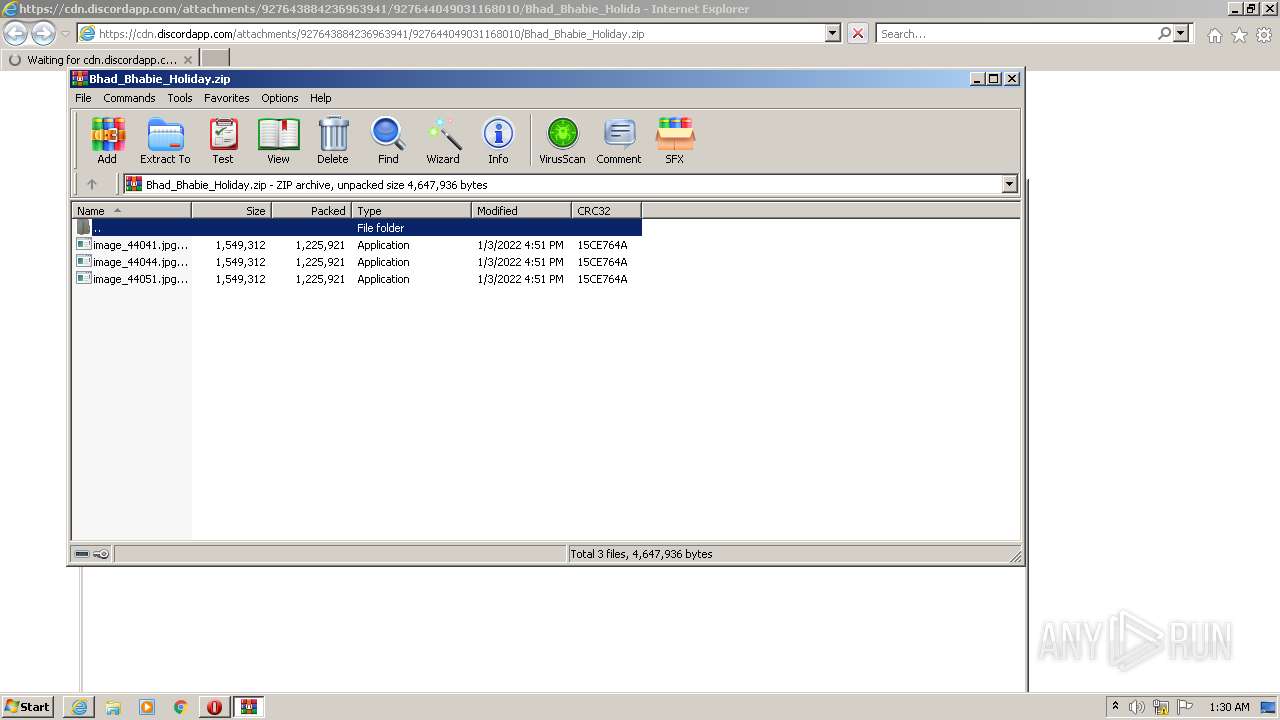
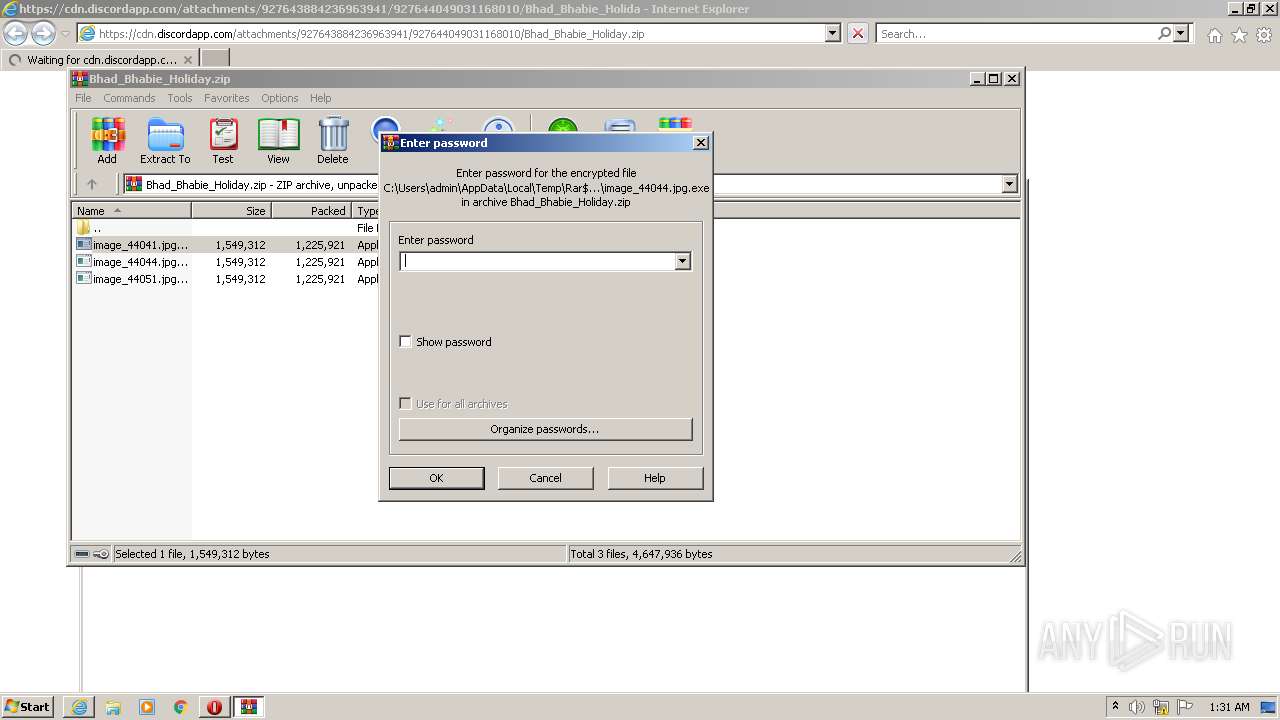
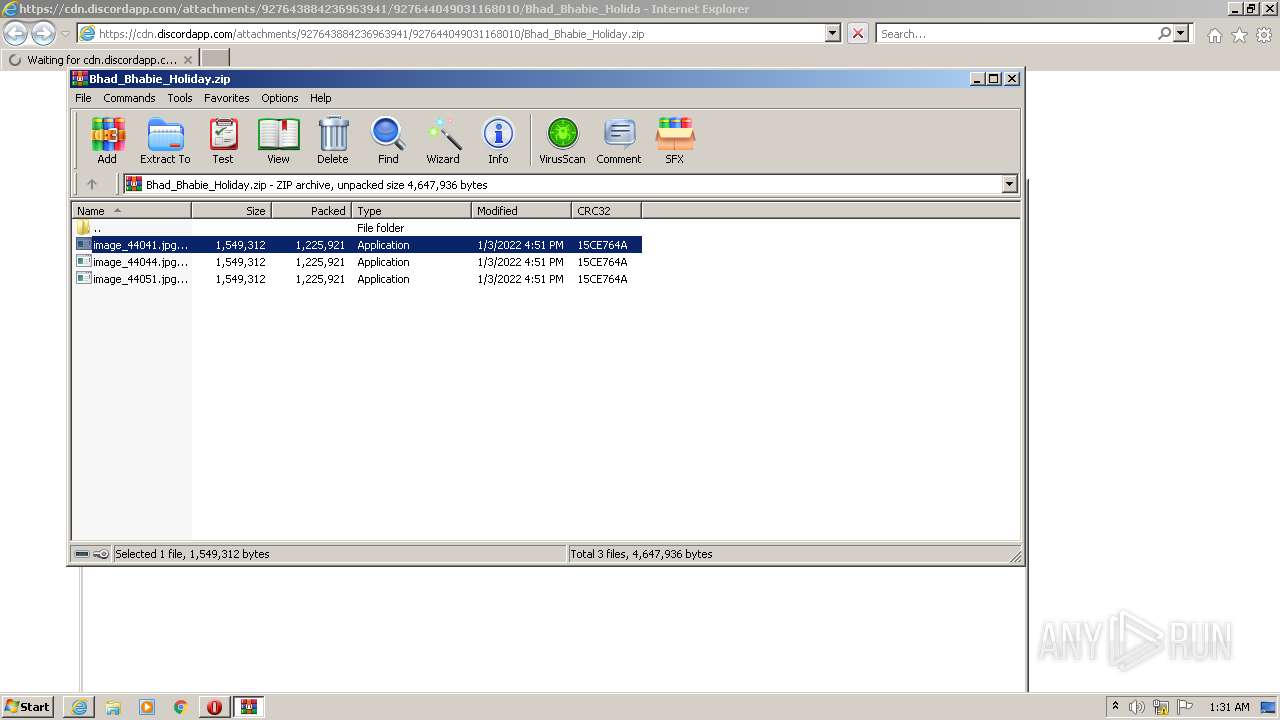
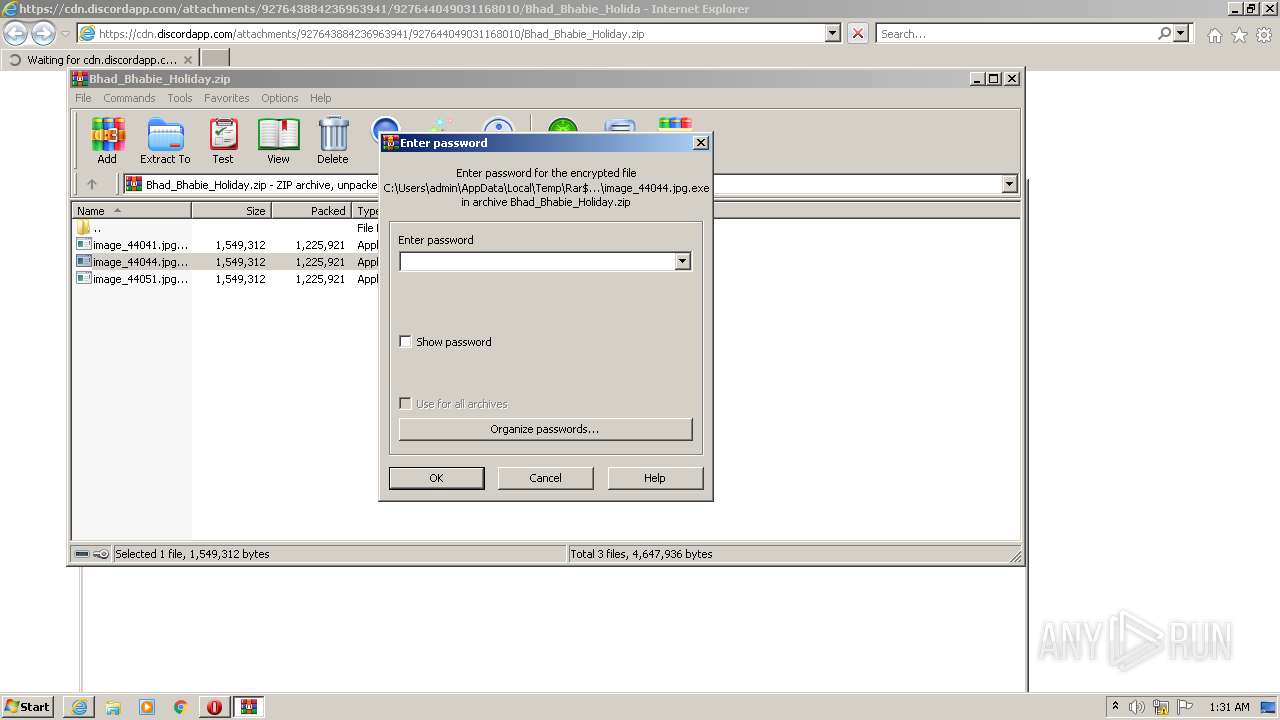
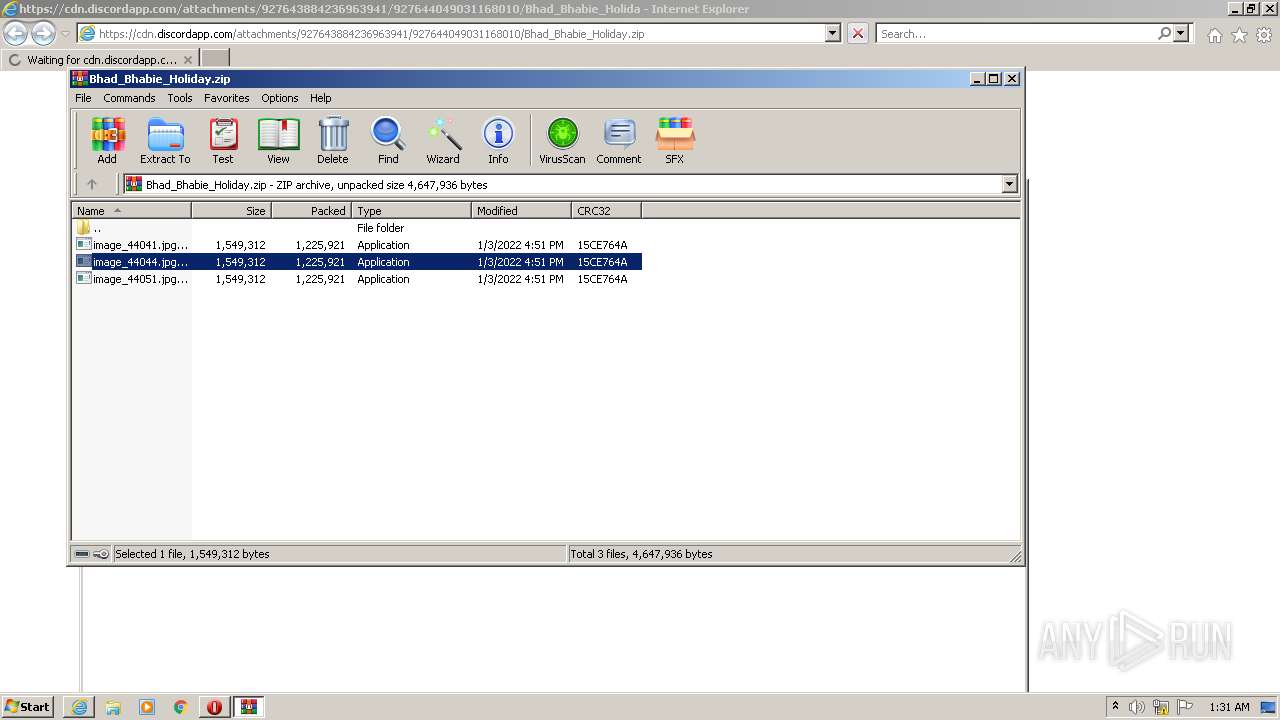
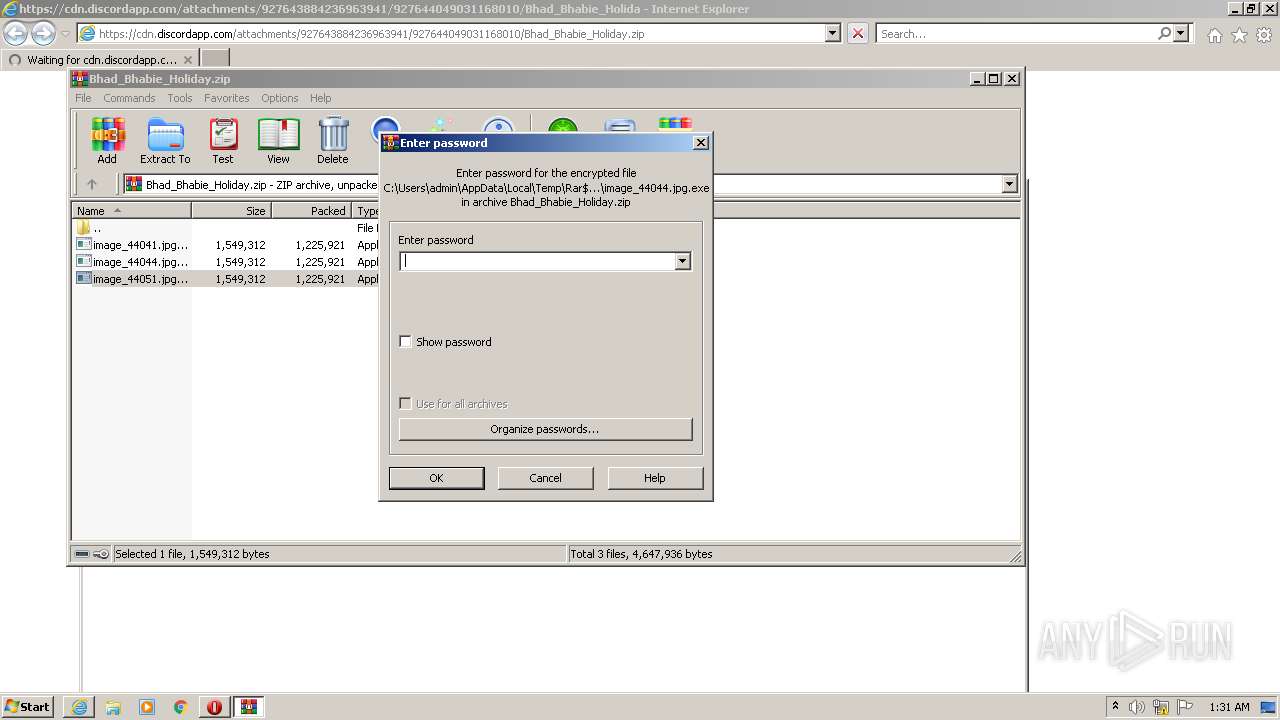
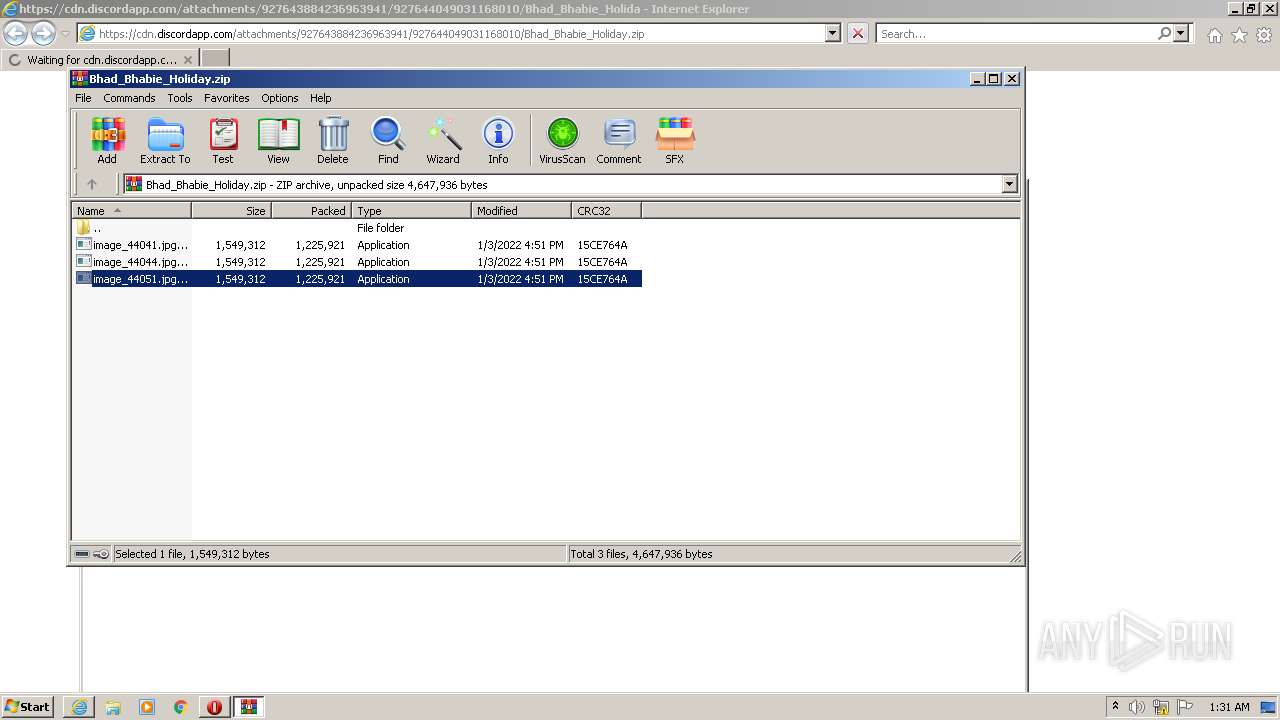
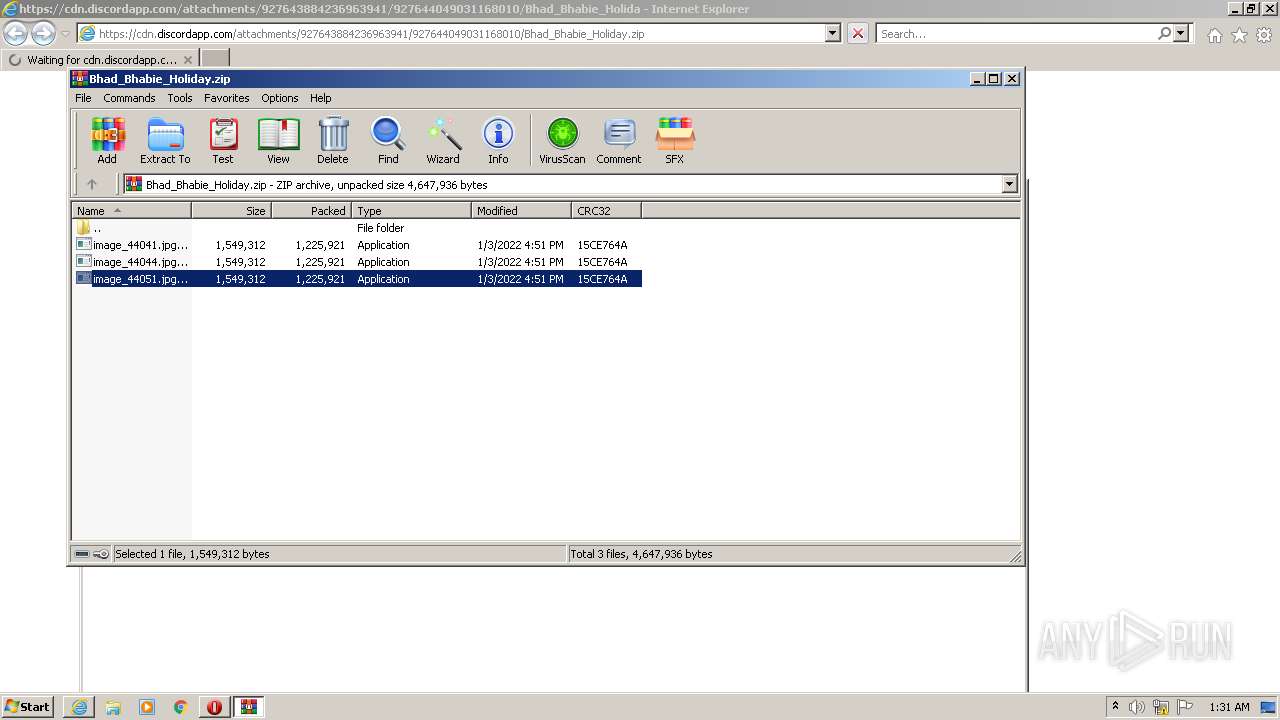
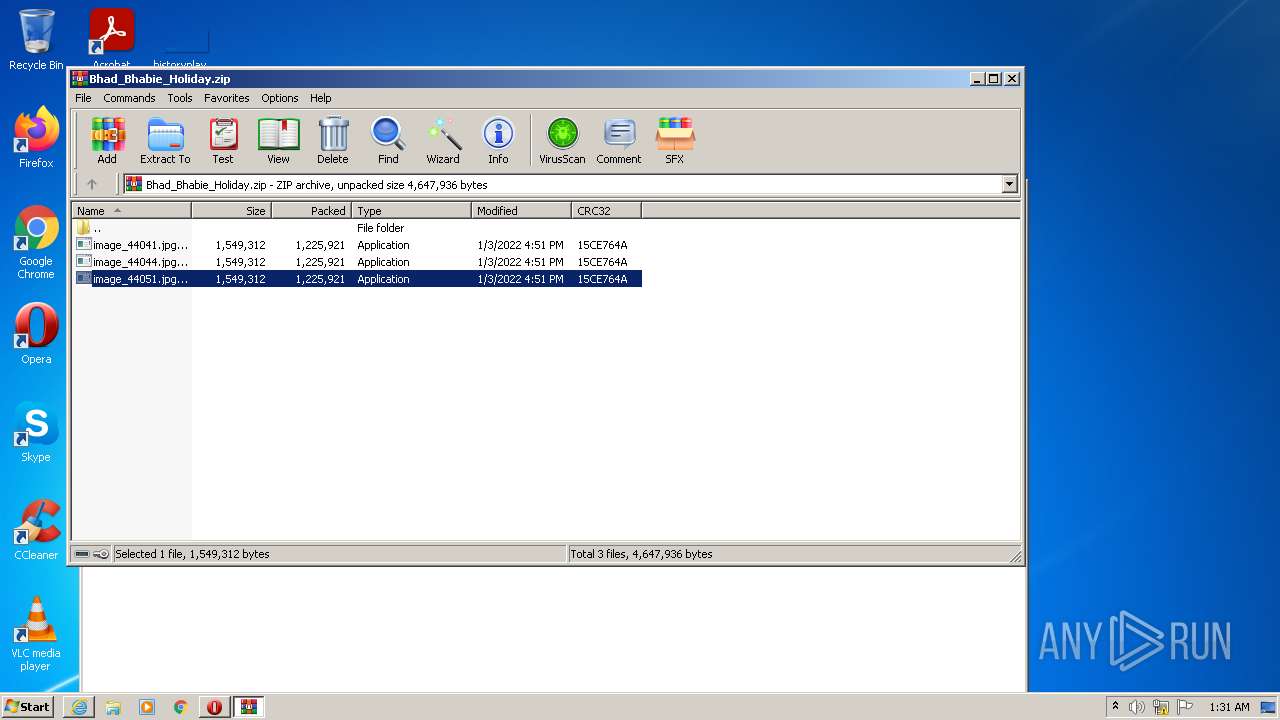
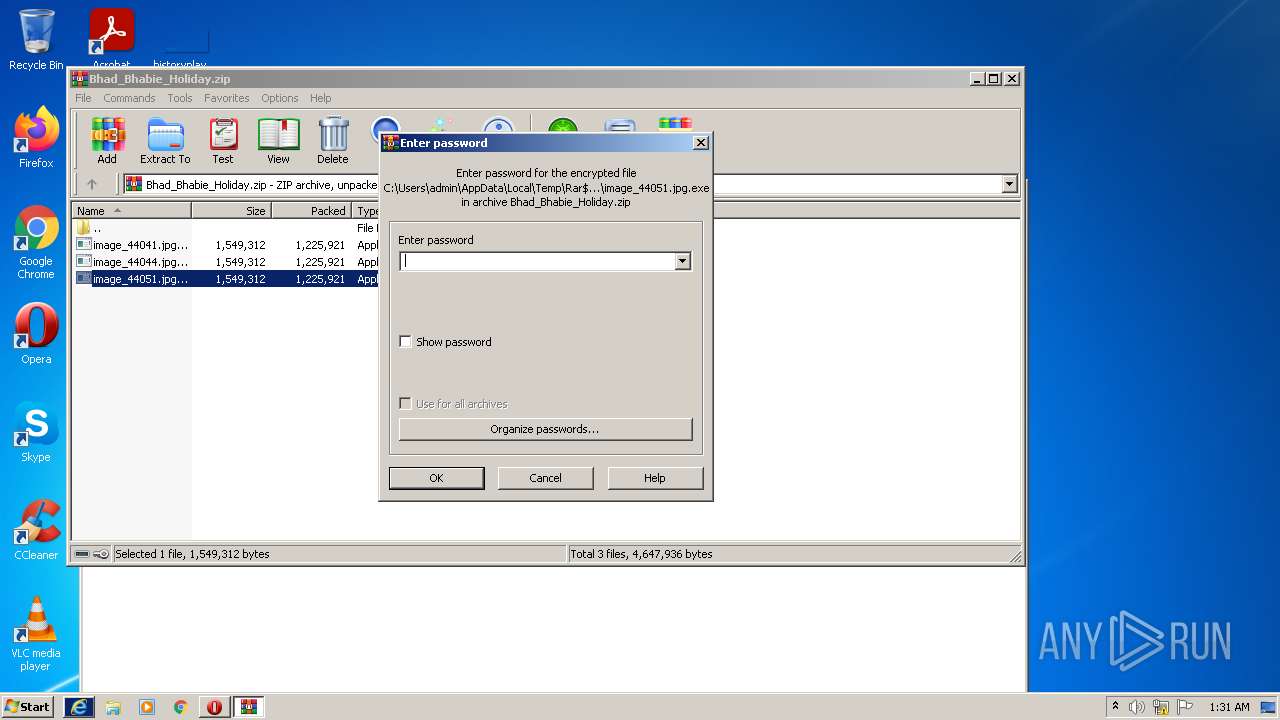
| URL: | https://cdn.discordapp.com/attachments/927643884236963941/927644049031168010/Bhad_Bhabie_Holiday.zip |
| Full analysis: | https://app.any.run/tasks/f3d1c07b-88b8-4f06-80fa-c9e192ab9f42 |
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2022, 01:30:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 86C912F4B30289E9D25C453C6EC707F4 |
| SHA1: | 1D97BDB58EAC19E7D358F0C4CA1B83BA383CDB48 |
| SHA256: | 6C22564D52B49C5F42B9B65D173D7204A8CEE8DF8610B838C47A88E34B3206B0 |
| SSDEEP: | 3:N8cCWdy6//mSdWYTiWgTJ3wGVJNuMALKYVn:2cry6XfW+1gTJAGsBLF |
MALICIOUS
Application was dropped or rewritten from another process
- image_44051.jpg.exe (PID: 2940)
- image_44041.jpg.exe (PID: 2148)
- image_44044.jpg.exe (PID: 2596)
- image_44051.jpg.exe (PID: 3264)
- image_44051.jpg.exe (PID: 2280)
Changes settings of System certificates
- image_44051.jpg.exe (PID: 3264)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3240)
Checks supported languages
- WinRAR.exe (PID: 424)
- image_44041.jpg.exe (PID: 2148)
- image_44044.jpg.exe (PID: 2596)
- image_44051.jpg.exe (PID: 2940)
- image_44051.jpg.exe (PID: 2280)
- image_44051.jpg.exe (PID: 3264)
Reads the computer name
- WinRAR.exe (PID: 424)
- image_44041.jpg.exe (PID: 2148)
- image_44044.jpg.exe (PID: 2596)
- image_44051.jpg.exe (PID: 2940)
- image_44051.jpg.exe (PID: 3264)
- image_44051.jpg.exe (PID: 2280)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 424)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 424)
Reads Environment values
- image_44041.jpg.exe (PID: 2148)
- image_44044.jpg.exe (PID: 2596)
- image_44051.jpg.exe (PID: 2940)
- image_44051.jpg.exe (PID: 3264)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 424)
Adds / modifies Windows certificates
- image_44051.jpg.exe (PID: 3264)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2760)
Checks supported languages
- iexplore.exe (PID: 2760)
- opera.exe (PID: 2224)
- iexplore.exe (PID: 3240)
Reads the computer name
- iexplore.exe (PID: 2760)
- iexplore.exe (PID: 3240)
- opera.exe (PID: 2224)
Application launched itself
- iexplore.exe (PID: 2760)
Reads settings of System Certificates
- iexplore.exe (PID: 2760)
- image_44041.jpg.exe (PID: 2148)
- image_44044.jpg.exe (PID: 2596)
- image_44051.jpg.exe (PID: 2940)
- iexplore.exe (PID: 3240)
- image_44051.jpg.exe (PID: 3264)
Manual execution by user
- opera.exe (PID: 2224)
- image_44051.jpg.exe (PID: 3264)
- image_44051.jpg.exe (PID: 2280)
Check for Java to be installed
- opera.exe (PID: 2224)
Checks Windows Trust Settings
- iexplore.exe (PID: 2760)
- iexplore.exe (PID: 3240)
Dropped object may contain Bitcoin addresses
- opera.exe (PID: 2224)
Reads the date of Windows installation
- opera.exe (PID: 2224)
- iexplore.exe (PID: 2760)
Creates files in the user directory
- opera.exe (PID: 2224)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
9
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 424 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\Bhad_Bhabie_Holiday.zip" | C:\Program Files\WinRAR\WinRAR.exe | opera.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb424.41587\image_44041.jpg.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb424.41587\image_44041.jpg.exe | WinRAR.exe | ||||||||||||
User: admin Company: Murray Hurps Software Pty Ltd Integrity Level: MEDIUM Description: Ad Muncher Exit code: 0 Version: 4.94.34121 (Free) Modules
| |||||||||||||||
| 2224 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | Explorer.EXE | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2280 | "C:\Users\admin\Desktop\image_44051.jpg.exe" | C:\Users\admin\Desktop\image_44051.jpg.exe | Explorer.EXE | ||||||||||||
User: admin Company: Murray Hurps Software Pty Ltd Integrity Level: HIGH Description: Ad Muncher Exit code: 0 Version: 4.94.34121 (Free) Modules
| |||||||||||||||
| 2596 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb424.42254\image_44044.jpg.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb424.42254\image_44044.jpg.exe | WinRAR.exe | ||||||||||||
User: admin Company: Murray Hurps Software Pty Ltd Integrity Level: MEDIUM Description: Ad Muncher Exit code: 0 Version: 4.94.34121 (Free) Modules
| |||||||||||||||
| 2760 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cdn.discordapp.com/attachments/927643884236963941/927644049031168010/Bhad_Bhabie_Holiday.zip" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2940 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb424.42523\image_44051.jpg.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb424.42523\image_44051.jpg.exe | WinRAR.exe | ||||||||||||
User: admin Company: Murray Hurps Software Pty Ltd Integrity Level: MEDIUM Description: Ad Muncher Exit code: 0 Version: 4.94.34121 (Free) Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2760 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3264 | "C:\Users\admin\Desktop\image_44051.jpg.exe" | C:\Users\admin\Desktop\image_44051.jpg.exe | Explorer.EXE | ||||||||||||
User: admin Company: Murray Hurps Software Pty Ltd Integrity Level: HIGH Description: Ad Muncher Exit code: 0 Version: 4.94.34121 (Free) Modules
| |||||||||||||||
Total events
30 142
Read events
29 792
Write events
349
Delete events
1
Modification events
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 632464032 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937483 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 932465282 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937483 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
10
Suspicious files
40
Text files
20
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2224 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00003.tmp | xml | |
MD5:— | SHA256:— | |||
| 2224 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr6AFD.tmp | xml | |
MD5:— | SHA256:— | |||
| 2224 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 2224 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\0VC4WFBZM5CL9DNP0LJF.temp | binary | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2224 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2224 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr6ABD.tmp | text | |
MD5:— | SHA256:— | |||
| 2224 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
30
DNS requests
18
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3240 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2224 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
2760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2224 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
2760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2760 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?289cf79653f4f370 | US | compressed | 4.70 Kb | whitelisted |
2148 | image_44041.jpg.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3541700a08366138 | US | compressed | 59.9 Kb | whitelisted |
2760 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?eebe35231b25f1cc | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3240 | iexplore.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2760 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2760 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2760 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2224 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2224 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2224 | opera.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2224 | opera.exe | 185.26.182.112:443 | sitecheck2.opera.com | Opera Software AS | — | malicious |
3240 | iexplore.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2760 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
transfer.sh |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2224 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2224 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2224 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Potentially Bad Traffic | ET POLICY Observed DNS Query to File Transfer Service Domain (transfer .sh) |
2148 | image_44041.jpg.exe | Potential Corporate Privacy Violation | ET POLICY Observed File Transfer Service SSL/TLS Certificate (transfer .sh) |
2596 | image_44044.jpg.exe | Potential Corporate Privacy Violation | ET POLICY Observed File Transfer Service SSL/TLS Certificate (transfer .sh) |
2940 | image_44051.jpg.exe | Potential Corporate Privacy Violation | ET POLICY Observed File Transfer Service SSL/TLS Certificate (transfer .sh) |
3264 | image_44051.jpg.exe | Potential Corporate Privacy Violation | ET POLICY Observed File Transfer Service SSL/TLS Certificate (transfer .sh) |
— | — | Potential Corporate Privacy Violation | ET POLICY Observed File Transfer Service SSL/TLS Certificate (transfer .sh) |