| download: | Tftpd32.shtml |
| Full analysis: | https://app.any.run/tasks/6af75bb0-5c92-4c68-8438-5336630b04c5 |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 14:37:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines |
| MD5: | 8A07640E4C7F072C1E5D753BAB933EDD |
| SHA1: | 0C6B5B4A1F0443AB23309007D070BC1C3EE00CB5 |
| SHA256: | 6C005B91D62AE783C3E0FDBBD59D07DDB736C2697481A9F60899C4461B5488BE |
| SSDEEP: | 768:wcpfkjdeUhSbXnXwPsjFQp2bIbaOPPiIBGL/Q7QOLY9icU4LJY2AbOFOwAWIzzRo:zdTrXwdiIBGL4kOLY9ipmJY2Ab7hWIZo |
MALICIOUS
Application was dropped or rewritten from another process
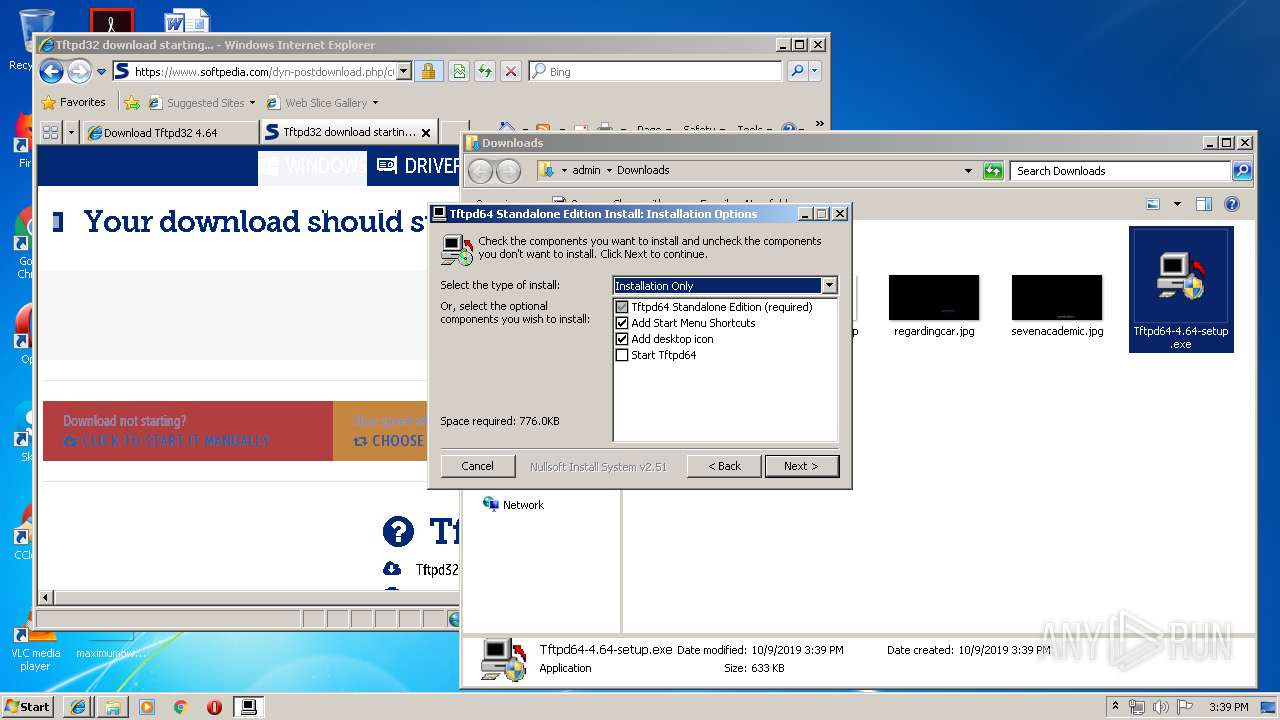
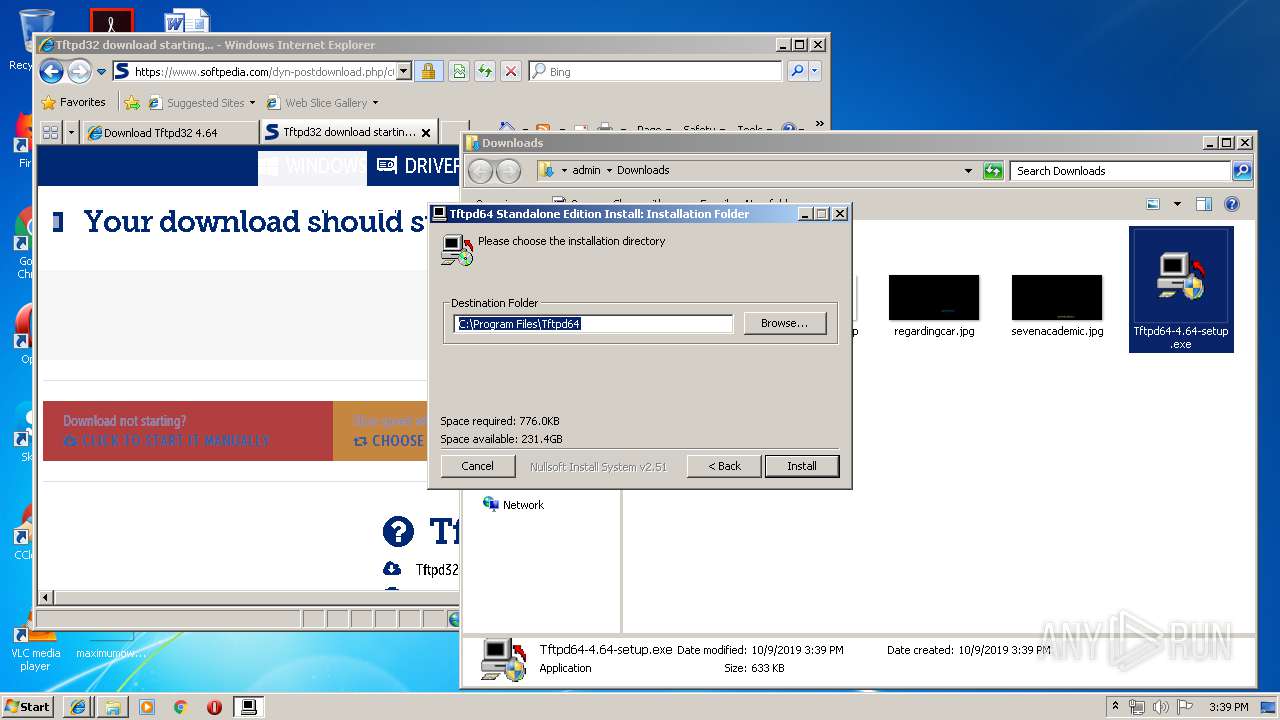
- Tftpd64-4.64-setup.exe (PID: 3620)
- Tftpd64-4.64-setup.exe (PID: 4012)
SUSPICIOUS
Creates files in the program directory
- Tftpd64-4.64-setup.exe (PID: 4012)
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2740)
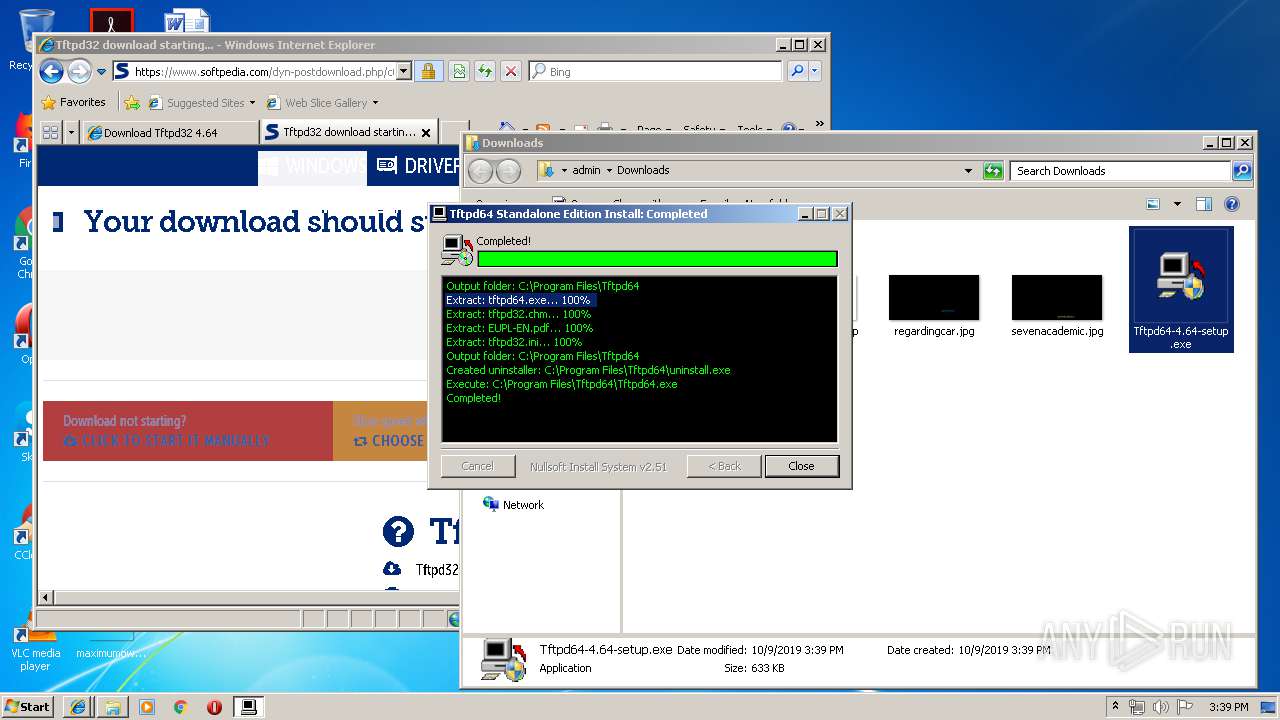
Executable content was dropped or overwritten
- iexplore.exe (PID: 2836)
- iexplore.exe (PID: 1388)
- Tftpd64-4.64-setup.exe (PID: 4012)
Creates a software uninstall entry
- Tftpd64-4.64-setup.exe (PID: 4012)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2836)
Reads internet explorer settings
- iexplore.exe (PID: 3260)
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 2436)
Dropped object may contain Bitcoin addresses
- Tftpd64-4.64-setup.exe (PID: 4012)
Reads Internet Cache Settings
- iexplore.exe (PID: 3260)
- iexplore.exe (PID: 2436)
- iexplore.exe (PID: 1388)
Creates files in the user directory
- iexplore.exe (PID: 1388)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2740)
- iexplore.exe (PID: 2836)
Reads settings of System Certificates
- iexplore.exe (PID: 2836)
Manual execution by user
- Tftpd64-4.64-setup.exe (PID: 3620)
- Tftpd64-4.64-setup.exe (PID: 4012)
- explorer.exe (PID: 3212)
Application launched itself
- iexplore.exe (PID: 2836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| Title: | Download Tftpd32 4.64 |
|---|---|
| language: | english |
| ContentType: | text/html; charset=utf-8 |
| viewport: | width=980 |
| HTTPEquivXUACompatible: | IE=edge |
| Description: | Download Tftpd32 - DHCP, TFTP, SNTP and Syslog servers and a TFTP client bundled inside a single package, with advanced configuration options and security settings |
| Keywords: | Tftpd32, download Tftpd32, Tftpd32 free download, FTP server, Syslog server, TFTP client, FTP, server, syslog, TFTP |
| msapplicationTileImage: | https://cdnssl.softpedia.com/_img/favicon_512.png?2015 |
Total processes
48
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1388 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2836 CREDAT:268545 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2836 CREDAT:79874 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Tftpd32.shtml.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3212 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3260 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2836 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
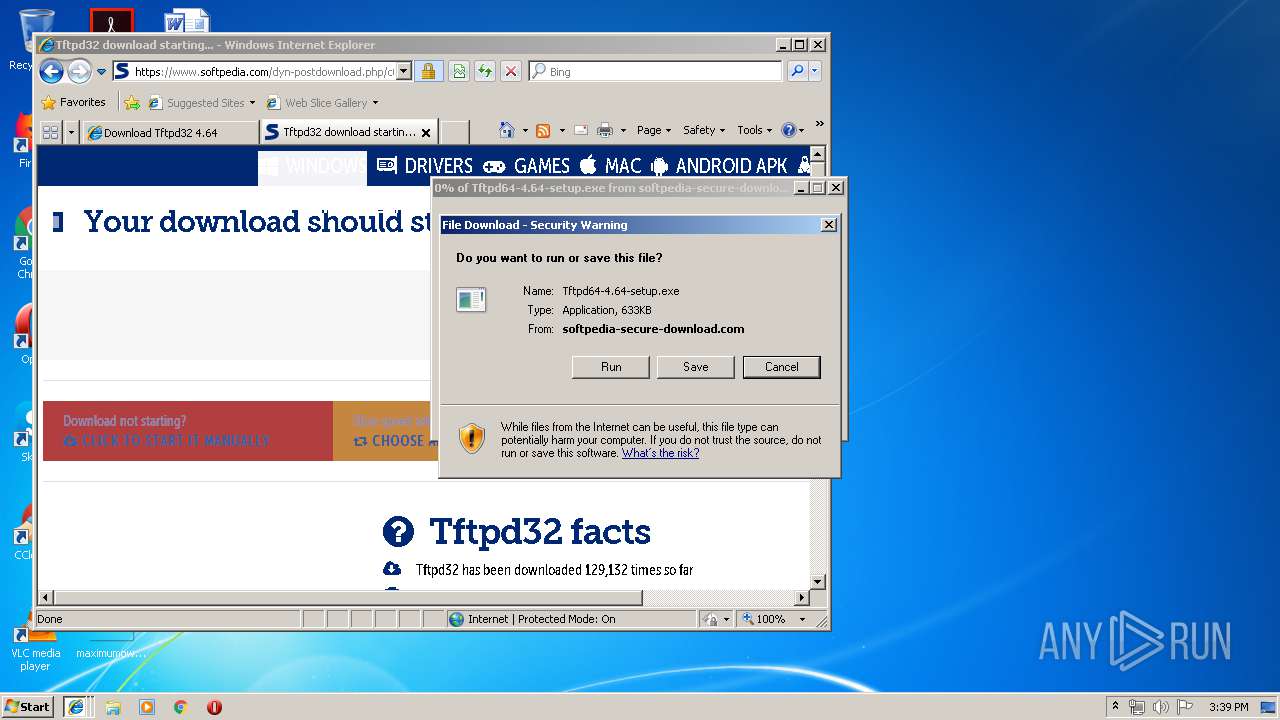
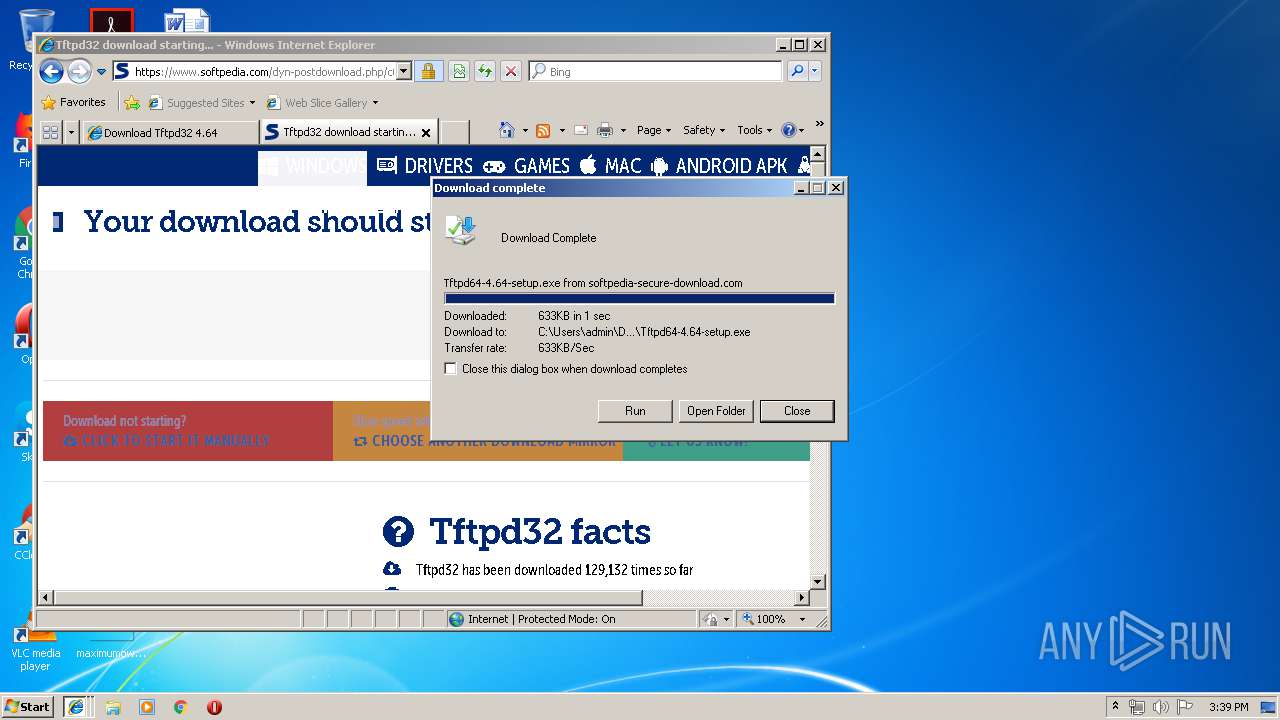
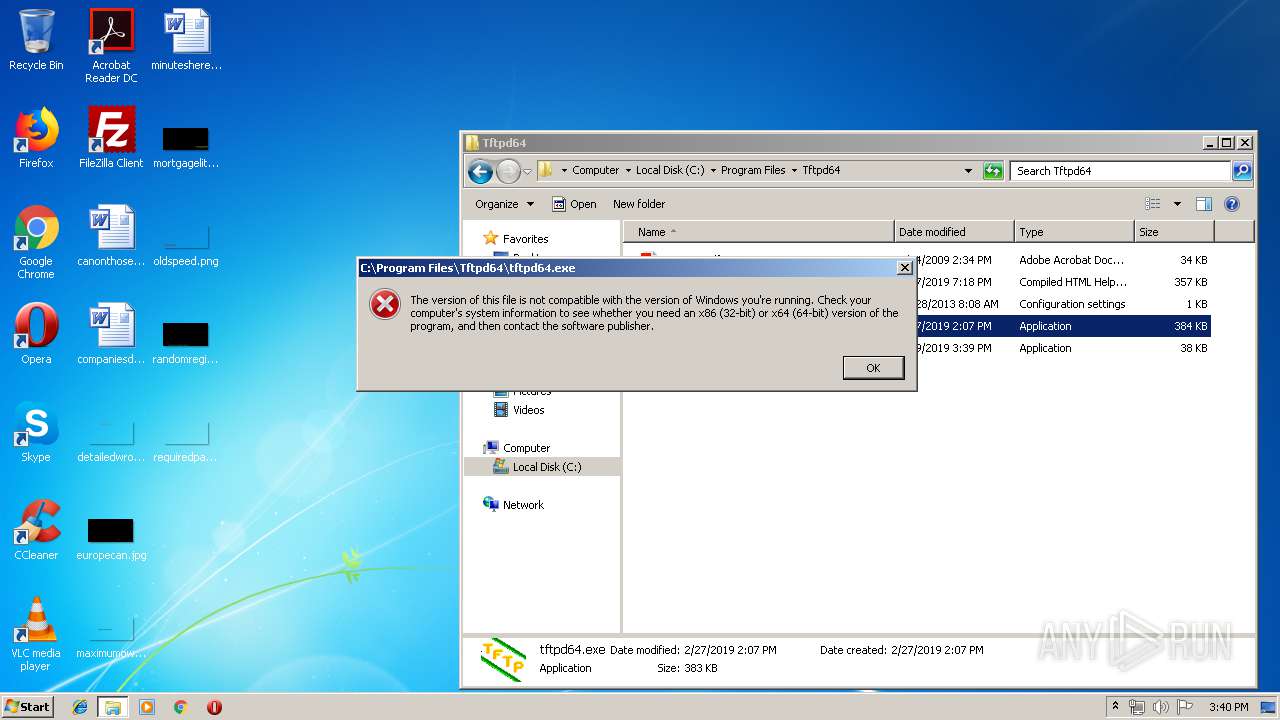
| 3620 | "C:\Users\admin\Downloads\Tftpd64-4.64-setup.exe" | C:\Users\admin\Downloads\Tftpd64-4.64-setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4012 | "C:\Users\admin\Downloads\Tftpd64-4.64-setup.exe" | C:\Users\admin\Downloads\Tftpd64-4.64-setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 931
Read events
1 705
Write events
221
Delete events
5
Modification events
| (PID) Process: | (3260) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (3260) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3260) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070A00030009000E0025001500C803 | |||
| (PID) Process: | (3260) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | LoadTime |
Value: 8 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
7
Text files
124
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\Tftpd32[1].png | — | |
MD5:— | SHA256:— | |||
| 3260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\Cesar-FTP[1].gif | — | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\fonts-mobile[1].css | — | |
MD5:— | SHA256:— | |||
| 3260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\consent[1].js | text | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\consent[1].js | text | |
MD5:— | SHA256:— | |||
| 3260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\_min[1].txt | text | |
MD5:— | SHA256:— | |||
| 3260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\_min[1] | text | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\_min[1].txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
108
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2836 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3260 | iexplore.exe | GET | 301 | 172.217.23.162:80 | http://securepubads.g.doubleclick.net/tag/js/gpt.js | US | html | 249 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3260 | iexplore.exe | 69.16.175.42:443 | cdnssl.softpedia.com | Highwinds Network Group, Inc. | US | malicious |
4 | System | 172.217.22.2:445 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
4 | System | 172.217.22.2:139 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
2836 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2436 | iexplore.exe | 69.16.175.42:443 | cdnssl.softpedia.com | Highwinds Network Group, Inc. | US | malicious |
4 | System | 172.217.23.174:445 | www.google-analytics.com | Google Inc. | US | whitelisted |
3260 | iexplore.exe | 172.217.23.162:80 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
4 | System | 172.217.23.174:139 | www.google-analytics.com | Google Inc. | US | whitelisted |
3260 | iexplore.exe | 172.217.23.162:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
2436 | iexplore.exe | 172.217.23.162:80 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
cdnssl.softpedia.com |
| malicious |
pagead2.googlesyndication.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
www.google-analytics.com |
| whitelisted |
windows-cdn.softpedia.com |
| whitelisted |
www.softpedia.com |
| suspicious |
stats.g.doubleclick.net |
| whitelisted |
softpedia-secure-download.com |
| unknown |