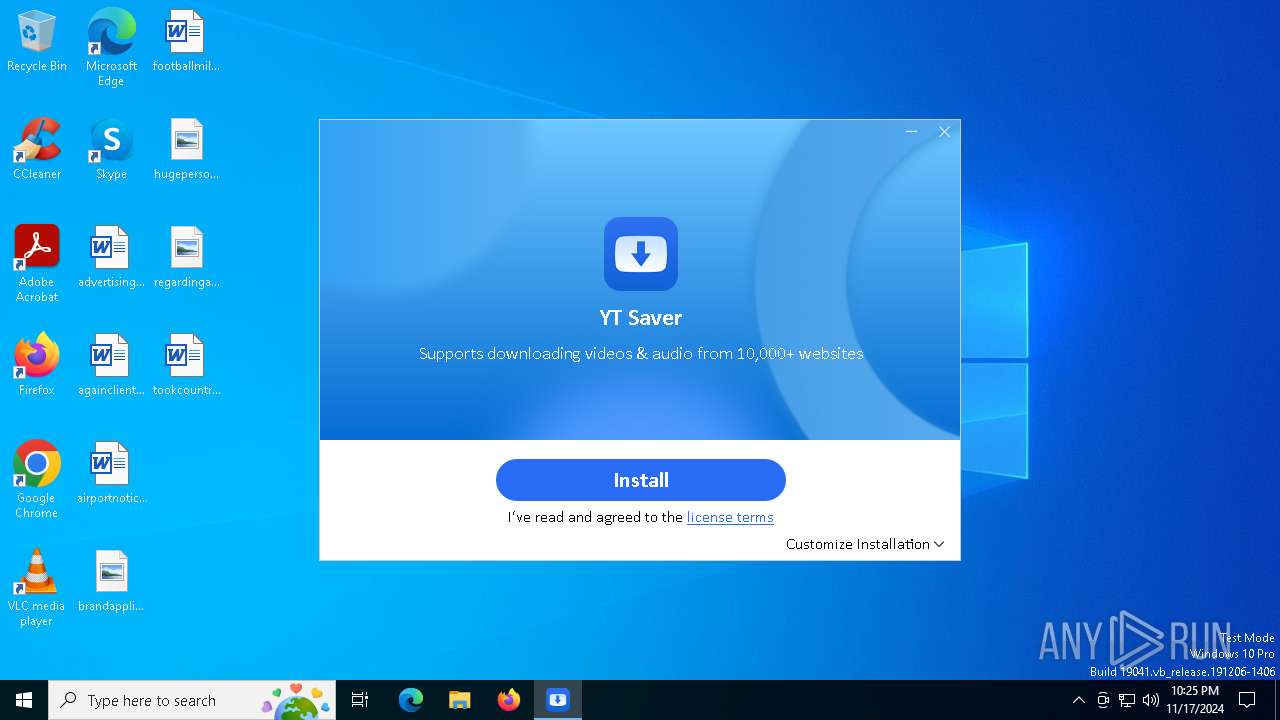
| File name: | ytsaver.exe |
| Full analysis: | https://app.any.run/tasks/c3bf3e31-0661-40bc-830b-3c4f9d040206 |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2024, 22:25:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | CB114E37B257CEB0F85A6805A0E62D83 |
| SHA1: | 27D2F5376031DEBD55DB0EFDEC904179C6365780 |
| SHA256: | 6BE58B000FCDAD911FCD64C5D3BB8EF715A027607D3996E20F6A234302C455E6 |
| SSDEEP: | 98304:i2E1lELAv2o7vQvocA7z10PqIvSMqzkRvtldmk3nrNaRlnYD8Lj2KOLldYjAwVxt:rwkqNf5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
- ytsaver_v9.2.0_x64.exe (PID: 6644)
Get information on the list of running processes
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
- cmd.exe (PID: 4680)
Starts CMD.EXE for commands execution
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
Drops 7-zip archiver for unpacking
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4680)
The process drops C-runtime libraries
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
Process drops legitimate windows executable
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
INFO
Creates files in the program directory
- ytsaver.exe (PID: 2428)
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
Checks supported languages
- ytsaver.exe (PID: 2428)
Reads the machine GUID from the registry
- ytsaver.exe (PID: 2428)
Reads the computer name
- ytsaver.exe (PID: 2428)
Create files in a temporary directory
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
- ytsaver_v9.2.0_x64.exe (PID: 6644)
- ytsaver.exe (PID: 2428)
Checks proxy server information
- ytsaver.exe (PID: 2428)
The process uses the downloaded file
- ytsaver_v9.2.0_x64.tmp (PID: 2980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:08:26 02:01:33+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 2227712 |
| InitializedDataSize: | 1016832 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1dc1a3 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 24.8.26.1 |
| ProductVersionNumber: | 5.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileDescription: | YT Saver |
| FileVersion: | 24.8.26.1 |
| LegalCopyright: | Copyright (c) 2024 YT Saver Studio. All rights reserved. |
| ProductName: | YT Saver |
| ProductVersion: | 5.0.0.0 |
Total processes
143
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1176 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2428 | "C:\Users\admin\AppData\Local\Temp\ytsaver.exe" | C:\Users\admin\AppData\Local\Temp\ytsaver.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: YT Saver Version: 24.8.26.1 Modules
| |||||||||||||||
| 2980 | "C:\Users\admin\AppData\Local\Temp\is-CR9FI.tmp\ytsaver_v9.2.0_x64.tmp" /SL5="$403B4,162285202,784384,C:\Users\admin\AppData\Local\Temp\tmp123_downloader\download\ytsaver_v9.2.0_x64.exe" /verysilent /wait_run /DIR="C:\Program Files\YT Saver" /LANG=english | C:\Users\admin\AppData\Local\Temp\is-CR9FI.tmp\ytsaver_v9.2.0_x64.tmp | ytsaver_v9.2.0_x64.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4032 | "C:\Users\admin\AppData\Local\Temp\ytsaver.exe" | C:\Users\admin\AppData\Local\Temp\ytsaver.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: YT Saver Exit code: 3221226540 Version: 24.8.26.1 Modules
| |||||||||||||||
| 4680 | "C:\WINDOWS\system32\cmd.exe" /c tasklist | findstr "ytsaverw.exe" > "C:\Users\admin\AppData\Local\Temp\findProcessRes.txt" | C:\Windows\SysWOW64\cmd.exe | — | ytsaver_v9.2.0_x64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5580 | findstr "ytsaverw.exe" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5956 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6644 | "C:\Users\admin\AppData\Local\Temp\\tmp123_downloader\download\ytsaver_v9.2.0_x64.exe" /verysilent /wait_run /DIR="C:\Program Files\YT Saver" /LANG=english | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\download\ytsaver_v9.2.0_x64.exe | ytsaver.exe | ||||||||||||
User: admin Company: LuckyDog Software, Inc. Integrity Level: HIGH Description: YT Saver Setup Version: Modules
| |||||||||||||||
Total events
699
Read events
699
Write events
0
Delete events
0
Modification events
Executable files
174
Suspicious files
1
Text files
45
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\language\language.ini | text | |
MD5:9E1B2B68BD6C0659E369208BF05E0A7E | SHA256:54BA6C41E4325FA82D9FAEE282177B760458F11650A38B307D392142D4DCBF37 | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\language\en.ini | text | |
MD5:392D79D1A07352C235097E6A174B05DC | SHA256:B37D70EA7BDA94052BD16375A3C3CF0226435DF0C569690E0C1736CE160C40A2 | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\app.ico | image | |
MD5:4C35EA7789A96B442BDBF47E322700E7 | SHA256:D7FC87D66327A44FA62B54FEFB48A30289BB7F612A203D3EC4836B407118C266 | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\language\pt.ini | text | |
MD5:814C05D844AA7114325961D98E4B7F39 | SHA256:BA235326E879BD84A299A27E8573173BEA24F13940BDEBA09CF81C44DE062395 | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\language\de.ini | text | |
MD5:7600392615FB3364639F91D17B703D9B | SHA256:20938AE05569356EB1AA0340A34CBD5CD59508A6A14AD290D692CD40E9FE7926 | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\language\it.ini | text | |
MD5:3FF2A4D21D1C5ED0DD3D6D46BB382E9E | SHA256:56D5DEC45FE2197854620E7CCD83A9868A84A06A76E119F442D8364CFF9BD671 | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\language\ko.ini | text | |
MD5:AF1426090DE2F940A525DDD33A874D84 | SHA256:425351AF6720CE5A7A3EC8A01B9A5D123BF296979879BF757611B180019EAB21 | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\language\jp.ini | text | |
MD5:43B800F080B54C8E857B02205A7017A9 | SHA256:4EBB722D810ABD6FC1002B960CD1DA84E5B59EA6E42359DA86744C5BE373851C | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\language\vn.ini | text | |
MD5:1021F6663FA6A477F3E10FE814BA6D6A | SHA256:7DA6DB3E7EF574BAF67A9614474BE527AF7825845314250D91C989B81582F718 | |||
| 2428 | ytsaver.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\8b88b\skin\btn\btn_cancel_hover.png | image | |
MD5:C55EA4EE9B20218BEEBE666DCFAF0AAD | SHA256:85B3E131D81AC8D51BC546FD02888929035C2AA7DDF22FF63CCFF46285B2134D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
49
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5220 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2464 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5220 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4292 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2428 | ytsaver.exe | 142.250.186.110:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
2428 | ytsaver.exe | 172.67.71.100:443 | download.ytsaver.net | CLOUDFLARENET | US | unknown |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
download.ytsaver.net |
| unknown |
www.google-analytics.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |