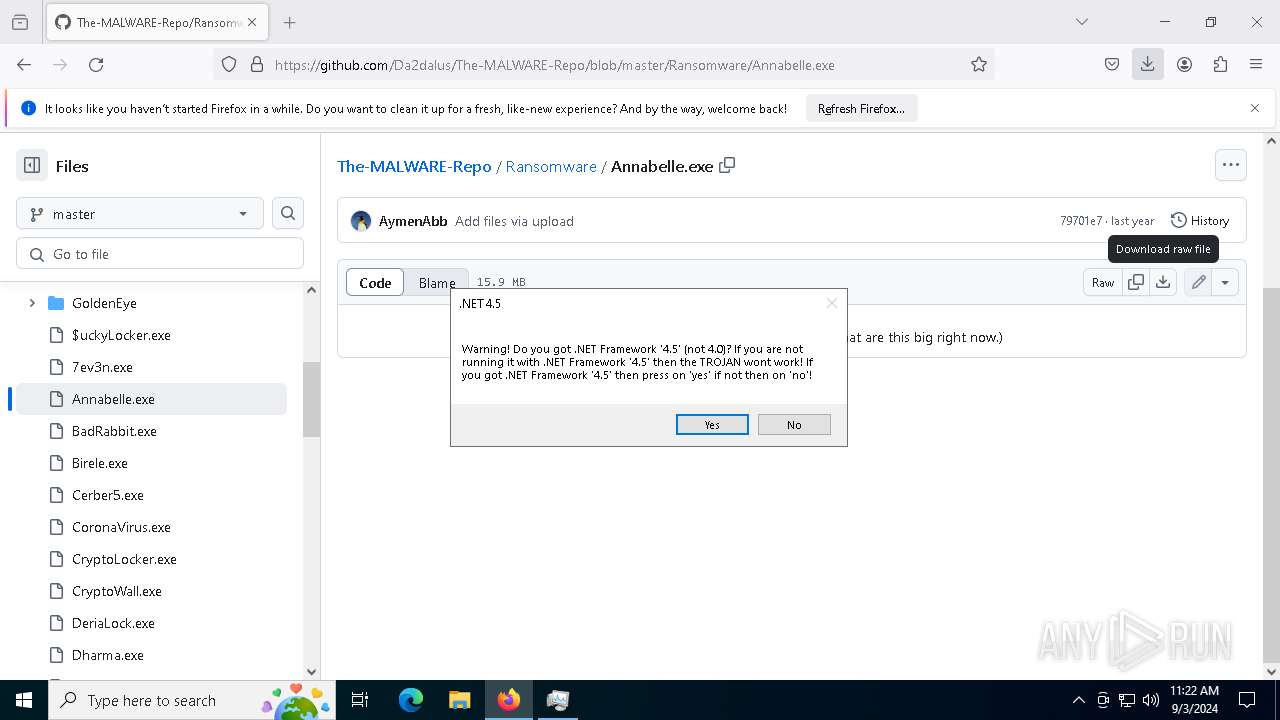
| download: | /Da2dalus/The-MALWARE-Repo/blob/master/Ransomware/PetrWrap |
| Full analysis: | https://app.any.run/tasks/e5818915-178f-4679-be7e-6c81df343aea |
| Verdict: | Malicious activity |
| Analysis date: | September 03, 2024, 11:18:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 text, with very long lines (1616) |
| MD5: | 8C23821041E2CB794FE4EB32FD6A5A69 |
| SHA1: | 7CFC0BFB51BDCAC31D882E7B1D7532CD71E96226 |
| SHA256: | 6BA31251DA1B41A3FFE5E31D4F487CFC77FC14D1394886CD4787A338CEF5813A |
| SSDEEP: | 6144:zNoCV3uokeOvHS1d1+CNs8wbiWQK95vZJT3CqbMrhryf65NRPaCieMjAkvCJv1V5:ZoCV3uokeOvHS1d1+CNs8wbiWQK95vZK |
MALICIOUS
Deletes shadow copies
- Annabelle.exe (PID: 5708)
Changes the autorun value in the registry
- Annabelle.exe (PID: 5708)
Disables Windows Defender
- Annabelle.exe (PID: 5708)
UAC/LUA settings modification
- Annabelle.exe (PID: 5708)
Disables the Run the Start menu
- Annabelle.exe (PID: 5708)
Changes image file execution options
- Annabelle.exe (PID: 5708)
Changes the login/logoff helper path in the registry
- Annabelle.exe (PID: 5708)
SUSPICIOUS
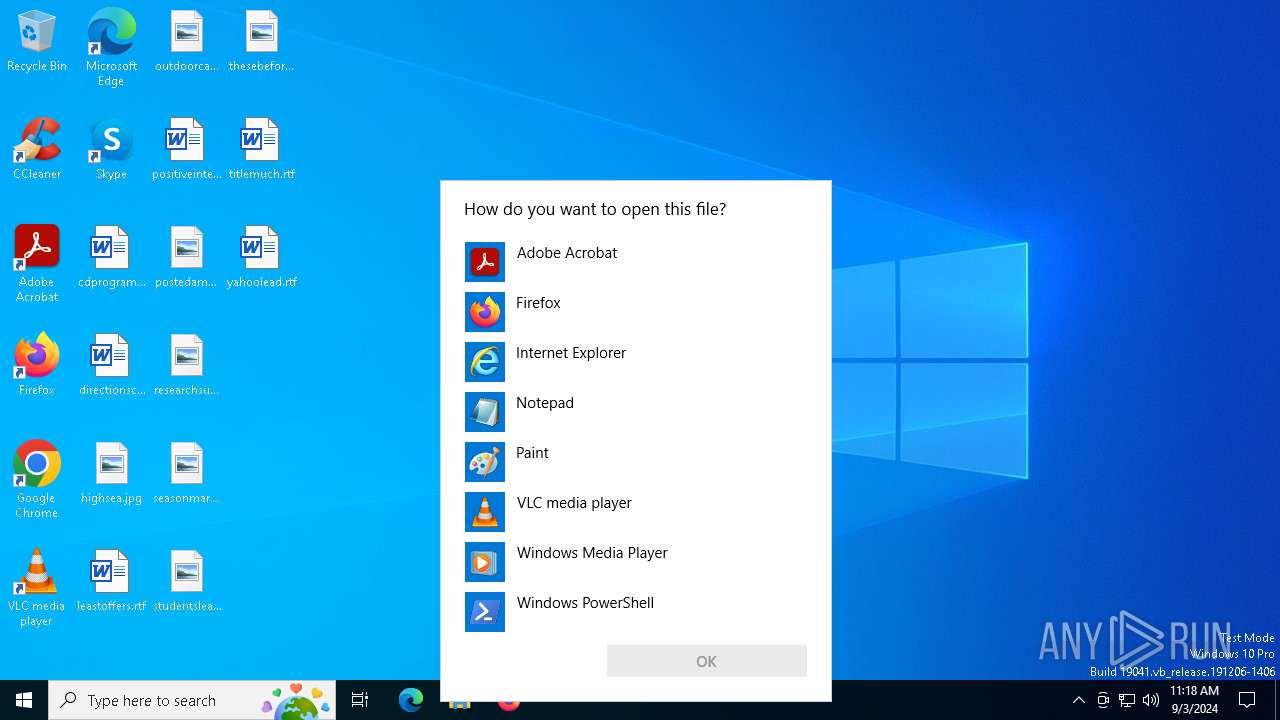
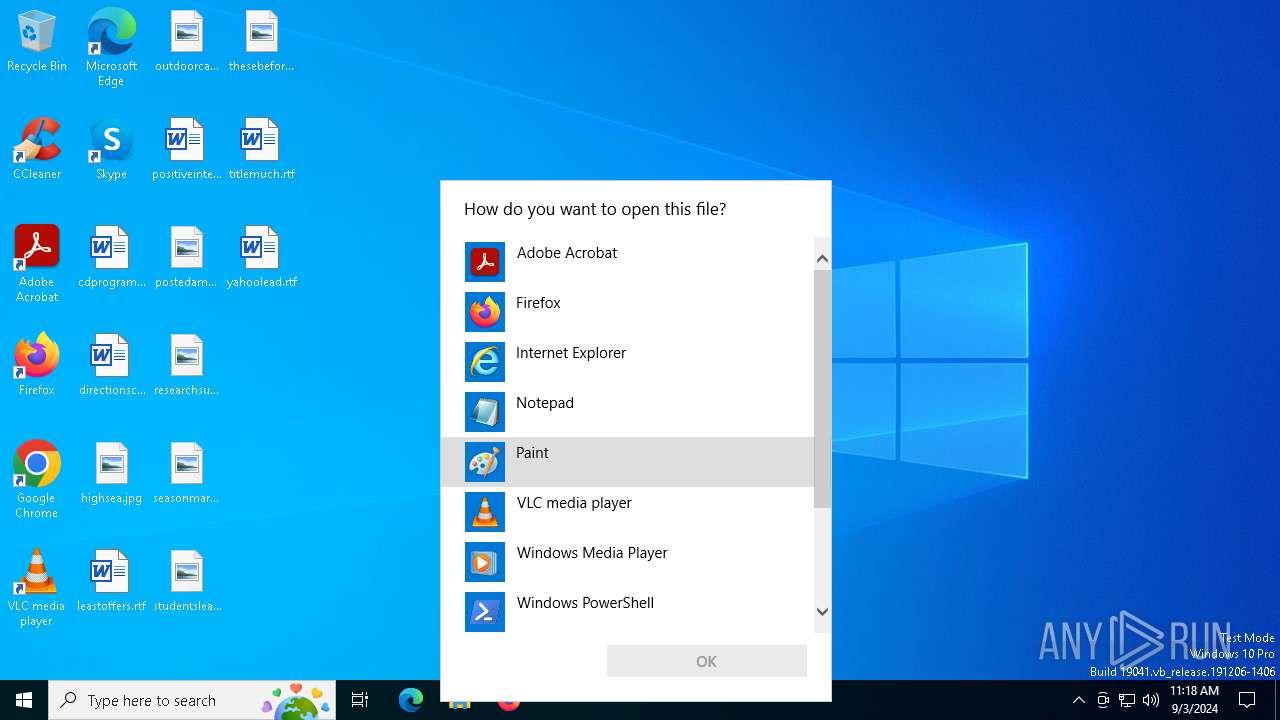
Creates file in the systems drive root
- OpenWith.exe (PID: 5700)
- Annabelle.exe (PID: 5708)
Uses NETSH.EXE to change the status of the firewall
- Annabelle.exe (PID: 5708)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 1700)
- Annabelle.exe (PID: 5708)
The system shut down or reboot
- Annabelle.exe (PID: 5708)
Executes as Windows Service
- VSSVC.exe (PID: 6196)
Reads the date of Windows installation
- Annabelle.exe (PID: 5708)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 1064)
INFO
Application launched itself
- firefox.exe (PID: 7004)
- firefox.exe (PID: 2524)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5700)
- firefox.exe (PID: 2524)
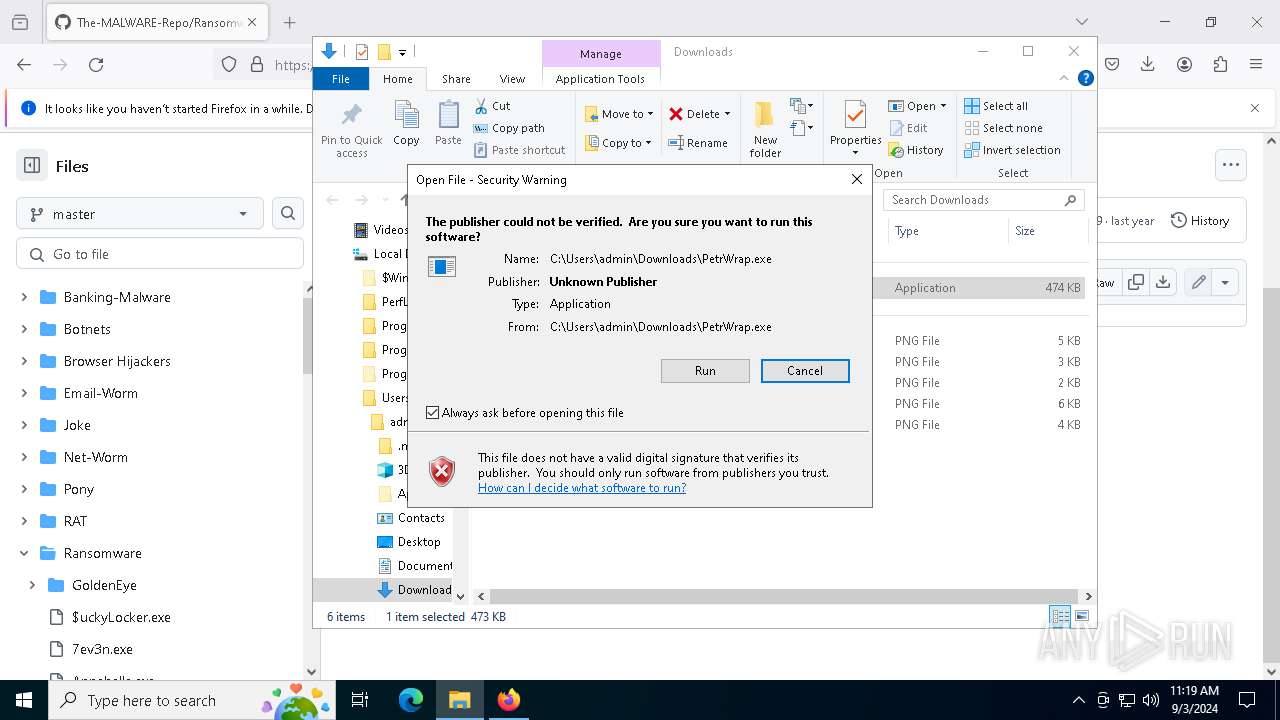
Manual execution by a user
- firefox.exe (PID: 7004)
- PetrWrap.exe (PID: 3268)
- Taskmgr.exe (PID: 6212)
- Taskmgr.exe (PID: 188)
Reads the machine GUID from the registry
- Annabelle.exe (PID: 5708)
The process uses the downloaded file
- firefox.exe (PID: 2524)
- Annabelle.exe (PID: 5708)
Executable content was dropped or overwritten
- firefox.exe (PID: 2524)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 188)
- OpenWith.exe (PID: 5700)
Reads the computer name
- Annabelle.exe (PID: 5708)
- ShellExperienceHost.exe (PID: 1700)
Checks supported languages
- Annabelle.exe (PID: 5708)
- PetrWrap.exe (PID: 3268)
- ShellExperienceHost.exe (PID: 1700)
Process checks computer location settings
- Annabelle.exe (PID: 5708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| Title: | The-MALWARE-Repo/Ransomware/PetrWrap at master · Da2dalus/The-MALWARE-Repo · GitHub |
|---|---|
| RoutePattern: | /:user_id/:repository/blob/*name(/*path) |
| RouteController: | blob |
| RouteAction: | show |
| CurrentCatalogServiceHash: | f3abb0cc802f3d7b95fc8762b94bdcb13bf39634c40c357301c4aa1d67a256fb |
| RequestId: | E906:3A117:13A3BEAA:13F715D7:66D6F078 |
| HtmlSafeNonce: | 936b113779555b8b8ffac2ed046596d441cbcc651cd0202437541fd5f7db9976 |
| VisitorPayload: | eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFOTA2OjNBMTE3OjEzQTNCRUFBOjEzRjcxNUQ3OjY2RDZGMDc4IiwidmlzaXRvcl9pZCI6IjE4NTcxOTQwMzAwMjg3NDY4NzIiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ== |
| VisitorHmac: | 690744fd6f41f841d478cbb691014369a4348f624706abae652381e4fe4036e9 |
| HovercardSubjectTag: | repository:271970028 |
| GithubKeyboardShortcuts: | repository,source-code,file-tree,copilot |
| GoogleSiteVerification: | Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I |
| OctolyticsUrl: | https://collector.github.com/github/collect |
| AnalyticsLocation: | /<user-name>/<repo-name>/blob/show |
| UserLogin: | - |
| Viewport: | width=device-width |
| Description: | A repository full of malware samples. Contribute to Da2dalus/The-MALWARE-Repo development by creating an account on GitHub. |
| AppleItunesApp: | app-id=1477376905, app-argument=https://github.com/Da2dalus/The-MALWARE-Repo/blob/master/Ransomware/PetrWrap |
| TwitterImageSrc: | https://repository-images.githubusercontent.com/271970028/2f632b80-aff8-11ea-8ba8-bcd0dc908b66 |
| TwitterSite: | @github |
| TwitterCard: | summary_large_image |
| TwitterTitle: | The-MALWARE-Repo/Ransomware/PetrWrap at master · Da2dalus/The-MALWARE-Repo |
| TwitterDescription: | A repository full of malware samples. Contribute to Da2dalus/The-MALWARE-Repo development by creating an account on GitHub. |
| Hostname: | github.com |
| ExpectedHostname: | github.com |
| HTTPEquivXPjaxVersion: | 3acea8dabf2adba10e07a2933e6f52fe8aaf60d9218f519668c3a85ffb973c51 |
| HTTPEquivXPjaxCspVersion: | 43bc2a0e2750a1219c17b5bf1ec22aae37041bbc018bc5e27bb7708f80e7ab88 |
| HTTPEquivXPjaxCssVersion: | fccf03f5b6a75b525f9275cba7313774f880dbf7bfc1c8feacff07fc90de9ca0 |
| HTTPEquivXPjaxJsVersion: | 5286f5563ab12752d59d134c15e95ef0634a4f34578c04759d093507d326bef9 |
| TurboCacheControl: | no-cache |
| GoImport: | github.com/Da2dalus/The-MALWARE-Repo git https://github.com/Da2dalus/The-MALWARE-Repo.git |
| OctolyticsDimensionUser_id: | 63458929 |
| OctolyticsDimensionUser_login: | Da2dalus |
| OctolyticsDimensionRepository_id: | 271970028 |
| OctolyticsDimensionRepository_nwo: | Da2dalus/The-MALWARE-Repo |
| OctolyticsDimensionRepository_public: | |
| OctolyticsDimensionRepository_is_fork: | - |
| OctolyticsDimensionRepository_network_root_id: | 271970028 |
| OctolyticsDimensionRepository_network_root_nwo: | Da2dalus/The-MALWARE-Repo |
| TurboBodyClasses: | logged-out env-production page-responsive |
| BrowserStatsUrl: | https://api.github.com/_private/browser/stats |
| BrowserErrorsUrl: | https://api.github.com/_private/browser/errors |
| ThemeColor: | #1e2327 |
| ColorScheme: | light dark |
Total processes
248
Monitored processes
31
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 1073807364 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) | |||||||||||||||
| 1108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5064 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 5236 -prefMapHandle 5344 -prefsLen 34713 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {dd35ac45-4739-4f0f-b0d1-d31f5a7dc3e7} 2524 "\\.\pipe\gecko-crash-server-pipe.2524" 2a420eb4710 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2248 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5500 -childID 3 -isForBrowser -prefsHandle 5396 -prefMapHandle 5288 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1508 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {950b1d56-8ea0-4a68-97fd-736e70d62f7f} 2524 "\\.\pipe\gecko-crash-server-pipe.2524" 2a41eec34d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2936 -childID 1 -isForBrowser -prefsHandle 2928 -prefMapHandle 2924 -prefsLen 30953 -prefMapSize 244343 -jsInitHandle 1508 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {0d867656-fe4b-4856-a1fa-e5225ad1615f} 2524 "\\.\pipe\gecko-crash-server-pipe.2524" 2a41e75cd90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2524 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2584 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6636 -childID 6 -isForBrowser -prefsHandle 6628 -prefMapHandle 4380 -prefsLen 31242 -prefMapSize 244343 -jsInitHandle 1508 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e5261957-8167-451b-8bd4-11ae0a71d0eb} 2524 "\\.\pipe\gecko-crash-server-pipe.2524" 2a423c48850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2820 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | Annabelle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 957
Read events
33 728
Write events
224
Delete events
5
Modification events
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-205 |
Value: Word | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @wmploc.dll,-102 |
Value: Windows Media Player | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000000000000030000000E0000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0500000006000000010000000400000008000000020000000C0000000B0000000A00000009000000070000000000000003000000FFFFFFFF | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\40\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 93 | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 92F0D66600000000 | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5700) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
11
Suspicious files
245
Text files
37
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2524 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:7A97B8DBC4F98D175F958C00F463A52A | SHA256:92074D2ED1AA1FD621287E35DB9EF1AE3DC04777EFAE5F09E7A3B4534C201548 | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:33C32A57EED3D7203159589B589F4EBF | SHA256:3C38CC8C5E802816FC13343D3AE68D80C71685F76BC16E2534F7009BA6D0DEF9 | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\AlternateServices.bin | binary | |
MD5:F342C17657D37F43B0A3DE24FE02B0B4 | SHA256:0C7AF1F4BCD1F20423CD04B6520D30E946B760DAA3BB31F1AB3DA911CD6217C7 | |||
| 2524 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:A095852877AD0CD8F5816653E8833AF6 | SHA256:FE66869435E82A7249891BB6517FFD3066F5A37A22CDE53040DDA71EFDB52BF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
90
DNS requests
147
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2524 | firefox.exe | POST | 200 | 23.32.238.82:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
8 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2524 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2524 | firefox.exe | POST | 200 | 23.32.238.82:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
2524 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2524 | firefox.exe | POST | 200 | 23.32.238.82:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
2524 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
2524 | firefox.exe | POST | 200 | 23.32.238.82:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
2524 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/s/wr3/XjA | unknown | — | — | unknown |
2524 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5644 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6320 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5644 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |