| File name: | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221 |
| Full analysis: | https://app.any.run/tasks/796abebd-dbcf-4698-a61b-27e91da66ad4 |
| Verdict: | Malicious activity |
| Analysis date: | November 03, 2023, 04:41:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | E64E7F97E9EFC38453D60451DB5ADA3D |
| SHA1: | 3B74BC0C9AFADBF8325C7FA2F51B80D2FC1165B1 |
| SHA256: | 6B80CDF715E4A596E4B83A157A78AEF69C8F900BD1F39554DC378A6BA007B752 |
| SSDEEP: | 24576:TRqzAC91XJppppppppOppFpppprppLppppUppvpppppSpyppppp7pp/ppppYppuz:TRqzAC91f8W4cNTtSRieKo8DnbucE+Dd |
MALICIOUS
Drops the executable file immediately after the start
- SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe (PID: 2700)
SUSPICIOUS
The process executes VB scripts
- SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe (PID: 2700)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 712)
Executing commands from a ".bat" file
- wscript.exe (PID: 712)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 712)
Reads the Internet Settings
- mshta.exe (PID: 1824)
- SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe (PID: 2700)
- wscript.exe (PID: 712)
Runs shell command (SCRIPT)
- wscript.exe (PID: 712)
INFO
Checks supported languages
- SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe (PID: 2700)
Reads the computer name
- SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe (PID: 2700)
Create files in a temporary directory
- SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe (PID: 2700)
Reads Internet Explorer settings
- mshta.exe (PID: 1824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:08:16 13:05:35+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 67584 |
| InitializedDataSize: | 130048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7d8 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
36
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Start.vbs" | C:\Windows\SysWOW64\wscript.exe | — | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
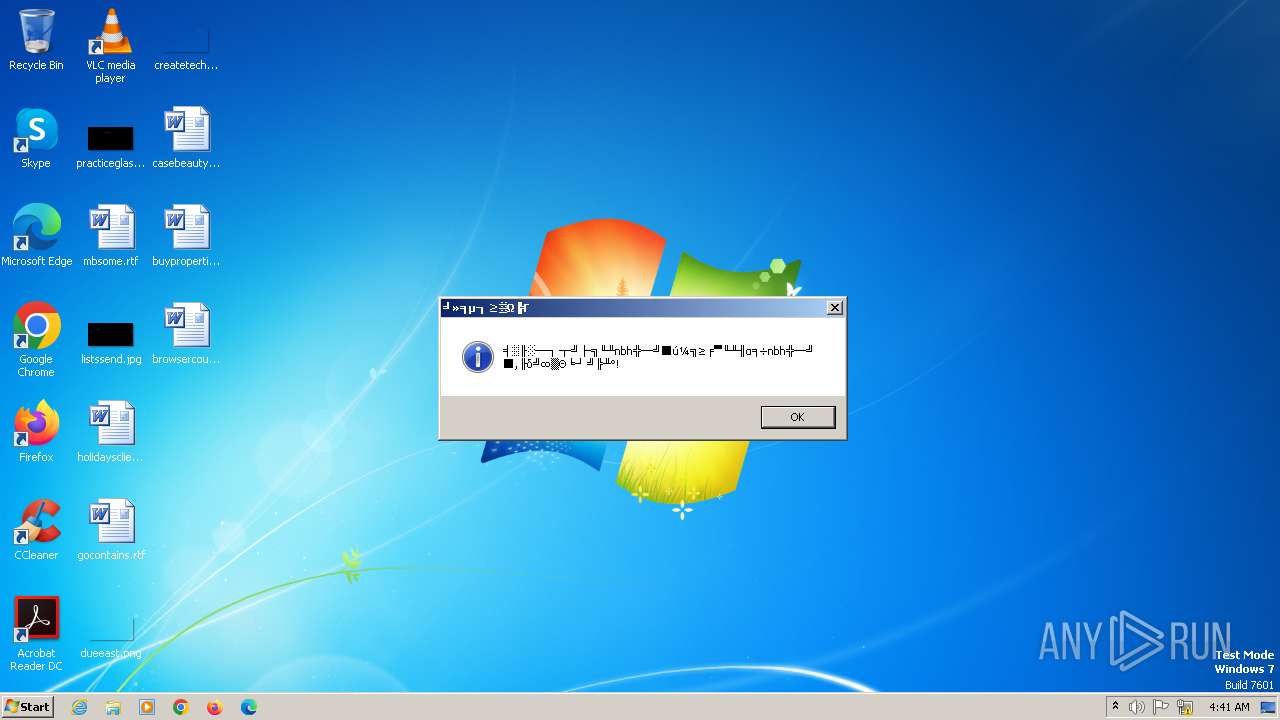
| 1824 | mshta vbscript:msgbox("╡▒╟░─┐┬╝├╗╙╨nbh╬─╝■ú¼╗≥╒▀╙╨╢α╕÷nbh╬─╝■,╟δ╝∞▓Θ╘┘╝╠╨°!",64,"╛»╕µ┐≥▒Ω╠Γ")(window.close) | C:\Windows\SysWOW64\mshta.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2380 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\autorun.bat" " | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2700 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 776
Read events
1 749
Write events
27
Delete events
0
Modification events
| (PID) Process: | (2700) SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2700) SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2700) SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2700) SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2700) SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (712) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
5
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\ErrorBattery.fig | image | |
MD5:53D61563128D6FE848BED8F427E68711 | SHA256:95E2CFC94C70573A2B736F00AB0E31FD9B9D2018D9D152116C6C895FE0F80B8E | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\RUUGetInfo.exe | executable | |
MD5:05A1D67FFFD046672E922846508BA5BC | SHA256:50A414B87AEFD0DAC43006EB6BE7625B7B000B0864E97DC16BD41534EECDEF0F | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\Start.vbs | text | |
MD5:E48C10D7D79BD6064C0E604D2F13B2C1 | SHA256:CE2C30A7C0454D327AF7356606D7D1E35EE39F7B606C175017E41A84CB411F37 | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\rapitool.exe | executable | |
MD5:B8ECF00387346D8617065C06CED04317 | SHA256:275578EE82C8F25B7C01C9C6CD6FD39D422FF674397B6872C0621C9C0067511D | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\autorun.bat | text | |
MD5:BE0BCAE3EF20DAF6B9CD186D35BA89B4 | SHA256:262DF4F72767D7B75B2E5A5A279C83BC12E6AA0C3BB873C4517A5A8919B5F8F6 | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\ROMUpdateUtility.exe | executable | |
MD5:16EFD6906EE87A9661E4ED99C47BC398 | SHA256:1E74591944E35F0B3AB9DE6FBACD0369AF8DBC3492C961A8CBE39DE48DBAFD94 | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\EnterBootloader.exe | executable | |
MD5:D63532C47DFA3884ADC498E97BE429B9 | SHA256:50F1ED738A1FC8F877B6E4EC1F2774B504A05E93698D0DB5DE9B317A080BA0B9 | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\RUUResource.dll | executable | |
MD5:F558C5FC1A428021CFEB1ADF37BD4EC0 | SHA256:5BD59C1ED513D190DF62E8EA793E52D7004B71844EEDAFF15E57614A81A6B6F4 | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\ModelID.fig | image | |
MD5:DEE99F14DF08E82CE4609335EE95B620 | SHA256:0C71A2D62D0B4F97ED47EA90A554A616AE47B8D8B2A23D1285F46CD54AF4AF23 | |||
| 2700 | SecuriteInfo.com.Win32.Trojan.Dropper.Heur.30301.16221.exe | C:\Users\admin\AppData\Local\Temp\ROMUpdateUtility.cfg | text | |
MD5:E91EB770E2AE5FEB91F27FC68E866395 | SHA256:0CD66E4618A1AACF87D8C5E517585E4E794E7CEB359C04F1E45332F9FBCAFDF9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |