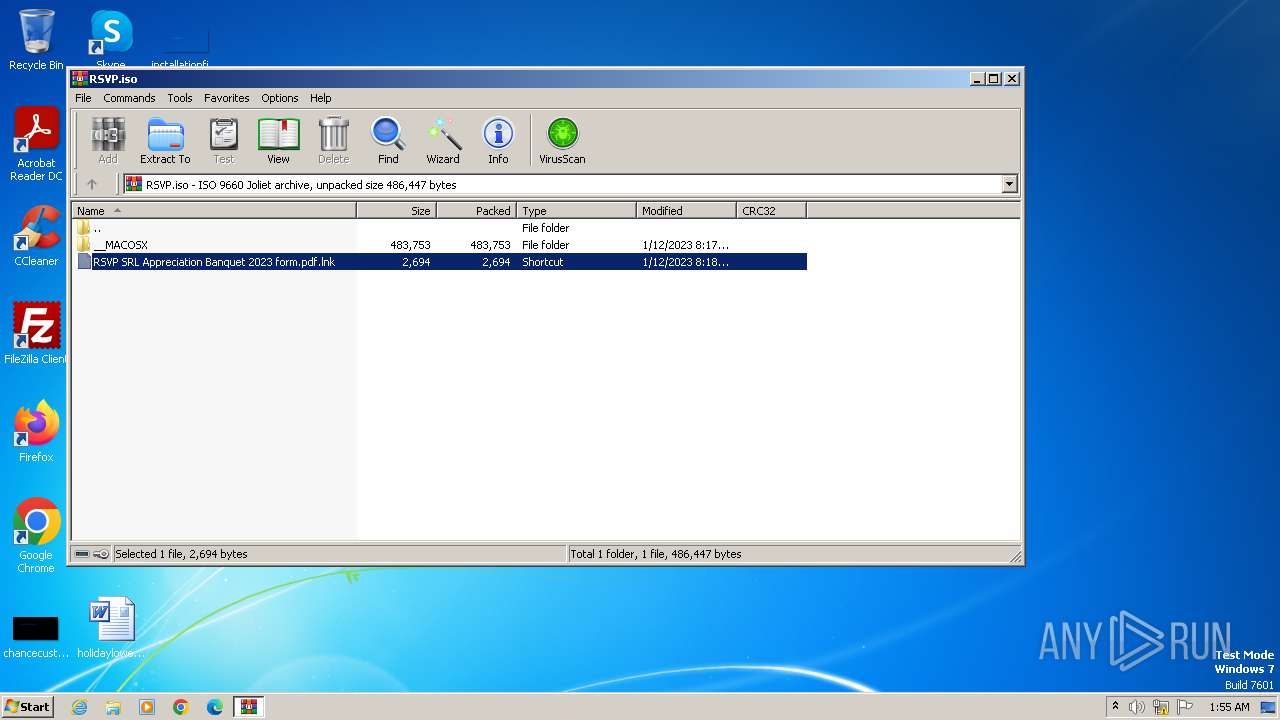
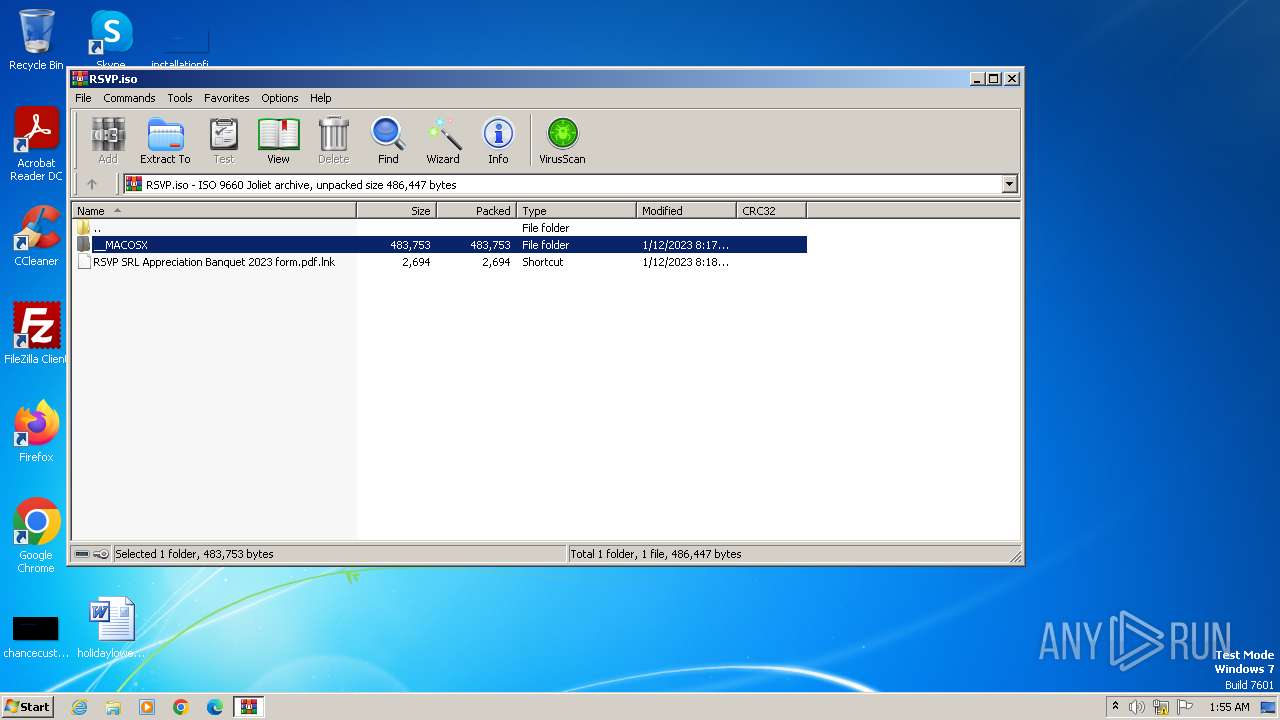
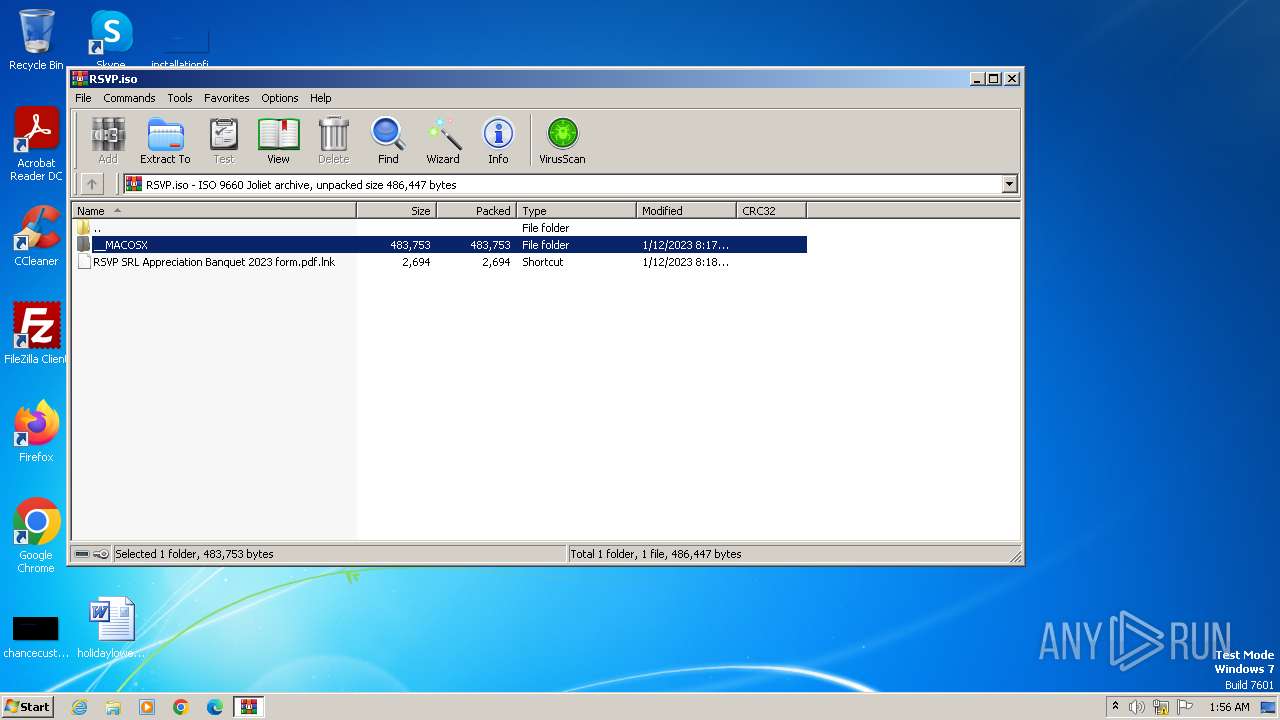
| File name: | RSVP.iso |
| Full analysis: | https://app.any.run/tasks/a13f51f2-ea85-4e24-810a-d2ae42c6d622 |
| Verdict: | Malicious activity |
| Analysis date: | November 11, 2023, 01:55:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | ISO 9660 CD-ROM filesystem data 'CDROM' |
| MD5: | D18419A0C74974D7F0CB4083C1D38908 |
| SHA1: | E97356129FACDC6461EEEDAE8DAD7BBBA4773F18 |
| SHA256: | 6B78BA25CD4B74D5741139DB842CBD441B9C95A73DD07BB2D33EE7FBAF5AEF9F |
| SSDEEP: | 6144:yGUvbNVlXmvvPv2v2Rq7GZ42aj4XJNVtEWSjYfuuWBNPcACWoA32:yGUD/EvvPv2v2QY4vjkvfEWHCDb |
MALICIOUS
Reads the value of a key from the registry (SCRIPT)
- wscript.exe (PID: 3488)
- wscript.exe (PID: 3644)
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 3488)
- wscript.exe (PID: 3644)
SUSPICIOUS
The process executes JS scripts
- WinRAR.exe (PID: 3448)
Access the System.Security .NET namespace (SCRIPT)
- wscript.exe (PID: 3488)
- wscript.exe (PID: 3644)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 3488)
- wscript.exe (PID: 3644)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 3488)
- wscript.exe (PID: 3644)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
ISO
| System: | LINUX |
|---|---|
| VolumeName: | CDROM |
| VolumeBlockCount: | 422 |
| VolumeBlockSize: | 2048 |
| RootDirectoryCreateDate: | 2023:01:12 15:24:54-05:00 |
| Software: | GENISOIMAGE ISO 9660/HFS FILESYSTEM CREATOR (C) 1993 E.YOUNGDALE (C) 1997-2006 J.PEARSON/J.SCHILLING (C) 2006-2007 CDRKIT TEAM |
| VolumeCreateDate: | 2023:01:12 15:25:32.00-05:00 |
| VolumeModifyDate: | 2023:01:12 15:25:32.00-05:00 |
| VolumeEffectiveDate: | 2023:01:12 15:25:32.00-05:00 |
Composite
| VolumeSize: | 844 KiB |
|---|
Total processes
39
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
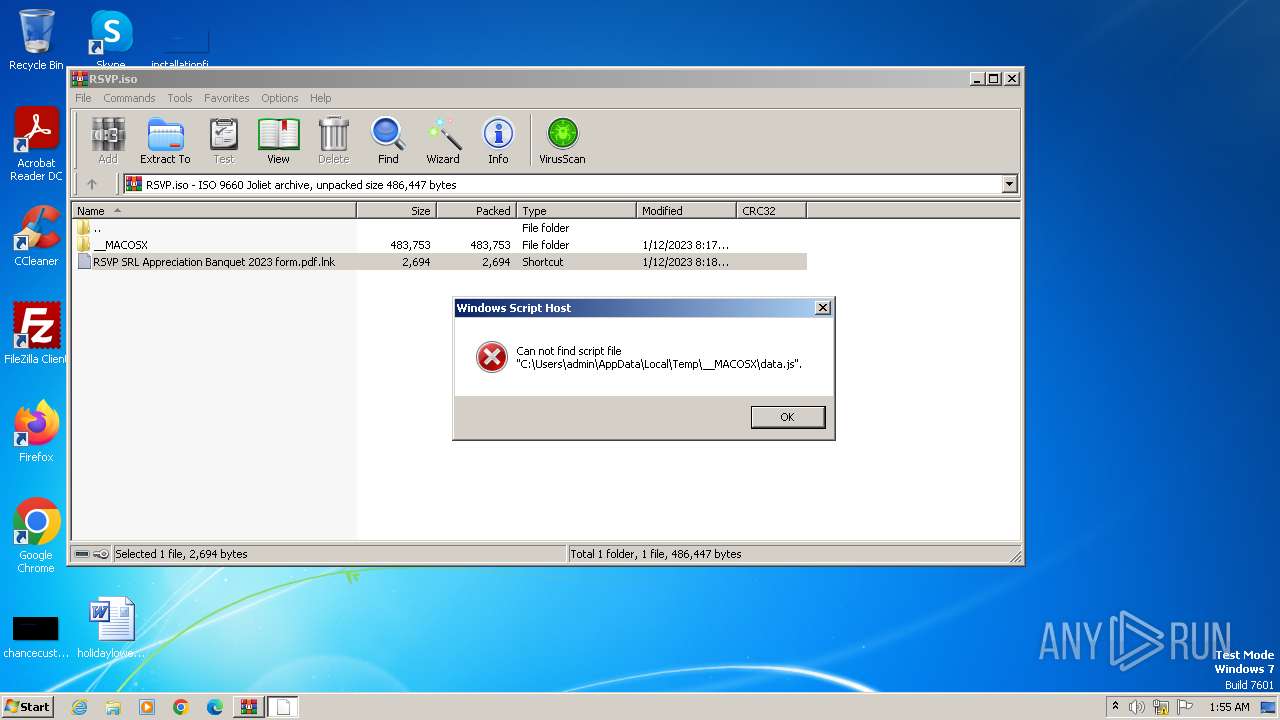
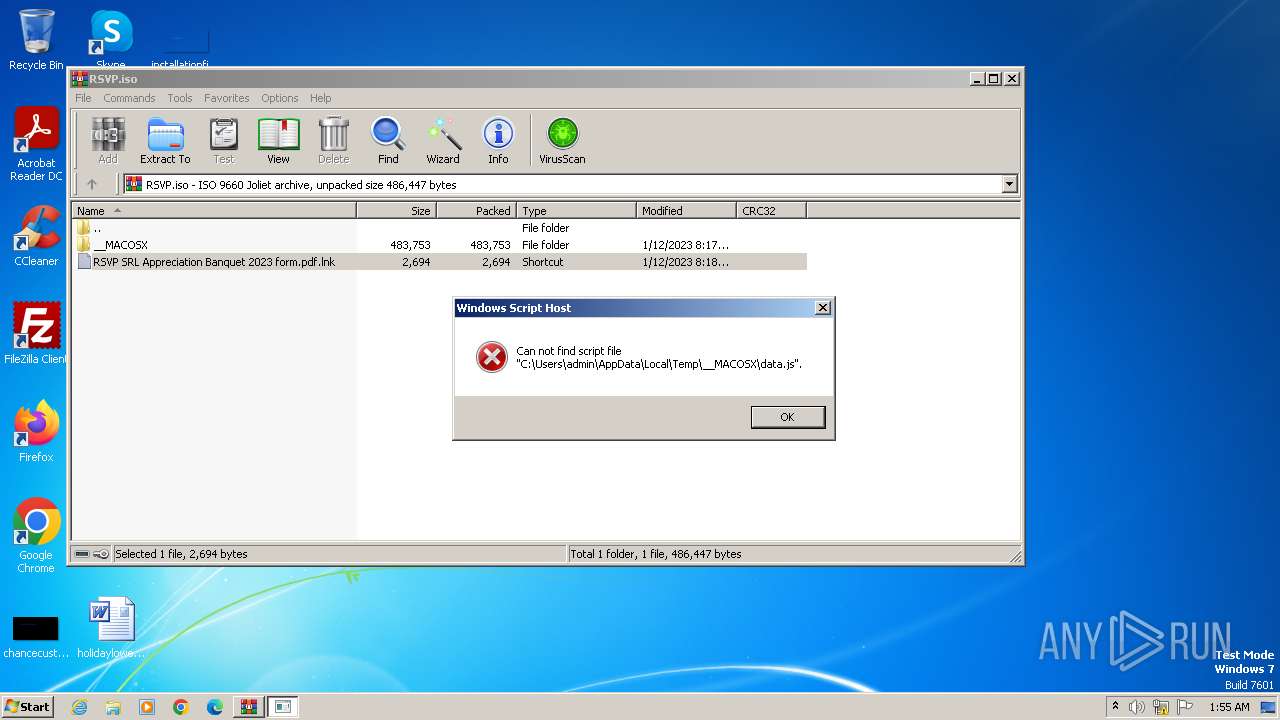
| 2900 | "C:\Windows\System32\wscript.exe" .\__MACOSX\data.js | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3372 | "C:\Windows\System32\wscript.exe" .\__MACOSX\data.js | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RSVP.iso" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3488 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.23732\data.js" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3524 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3644 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.23950\data.js" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
2 201
Read events
2 182
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
2
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.21226\RSVP SRL Appreciation Banquet 2023 form.pdf.lnk | binary | |
MD5:38D59A5CE4F795AF232D2E79FB39F90D | SHA256:BD7EF7AECB267CC372B2A96CBCBCFF284B71553CD4A5D42304BBE5C033DA6DD8 | |||
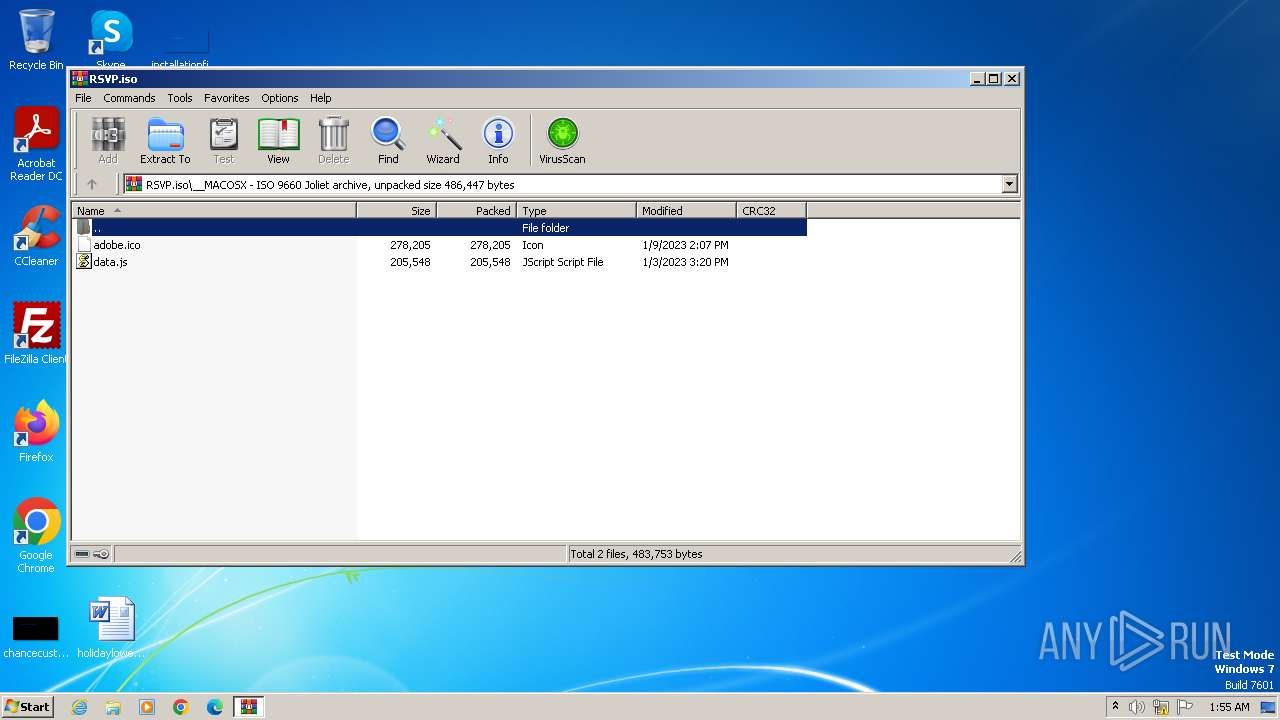
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.23950\data.js | text | |
MD5:7B0FE68E9A320F814EE956C7121C86B6 | SHA256:722968F89A70FA5DA845180D16855DF3220E5F6A7362EE5BD5F26A3F175B171E | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.22975\adobe.ico | image | |
MD5:9BE3303513A46EEA2BB691B7BAE2F402 | SHA256:2FEF612265D6834CFC712920EC6003EA85445FDB793FAFDC5671093FD1464872 | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.23732\data.js | text | |
MD5:7B0FE68E9A320F814EE956C7121C86B6 | SHA256:722968F89A70FA5DA845180D16855DF3220E5F6A7362EE5BD5F26A3F175B171E | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.22503\RSVP SRL Appreciation Banquet 2023 form.pdf.lnk | binary | |
MD5:38D59A5CE4F795AF232D2E79FB39F90D | SHA256:BD7EF7AECB267CC372B2A96CBCBCFF284B71553CD4A5D42304BBE5C033DA6DD8 | |||
| 3488 | wscript.exe | C:\Users\admin\AppData\Local\Temp\sxs9A4.tmp | xml | |
MD5:E7F29C8A4C11BDA93FC1DECE806EDC9E | SHA256:F6BE4AA084E0E3C127B8F4B3BE6A6714869325AD91EF89309C26E7EC8CFBFEFA | |||
| 3644 | wscript.exe | C:\Users\admin\AppData\Local\Temp\sxs1220.tmp | xml | |
MD5:E7F29C8A4C11BDA93FC1DECE806EDC9E | SHA256:F6BE4AA084E0E3C127B8F4B3BE6A6714869325AD91EF89309C26E7EC8CFBFEFA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |