| File name: | 563900-Copy of Copmuter-IT-Service-Catalog-Inventory-Template.xls |
| Full analysis: | https://app.any.run/tasks/0d28c226-31fe-4954-94a1-05d05e9e41c5 |
| Verdict: | No threats detected |
| Analysis date: | April 11, 2019, 07:52:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
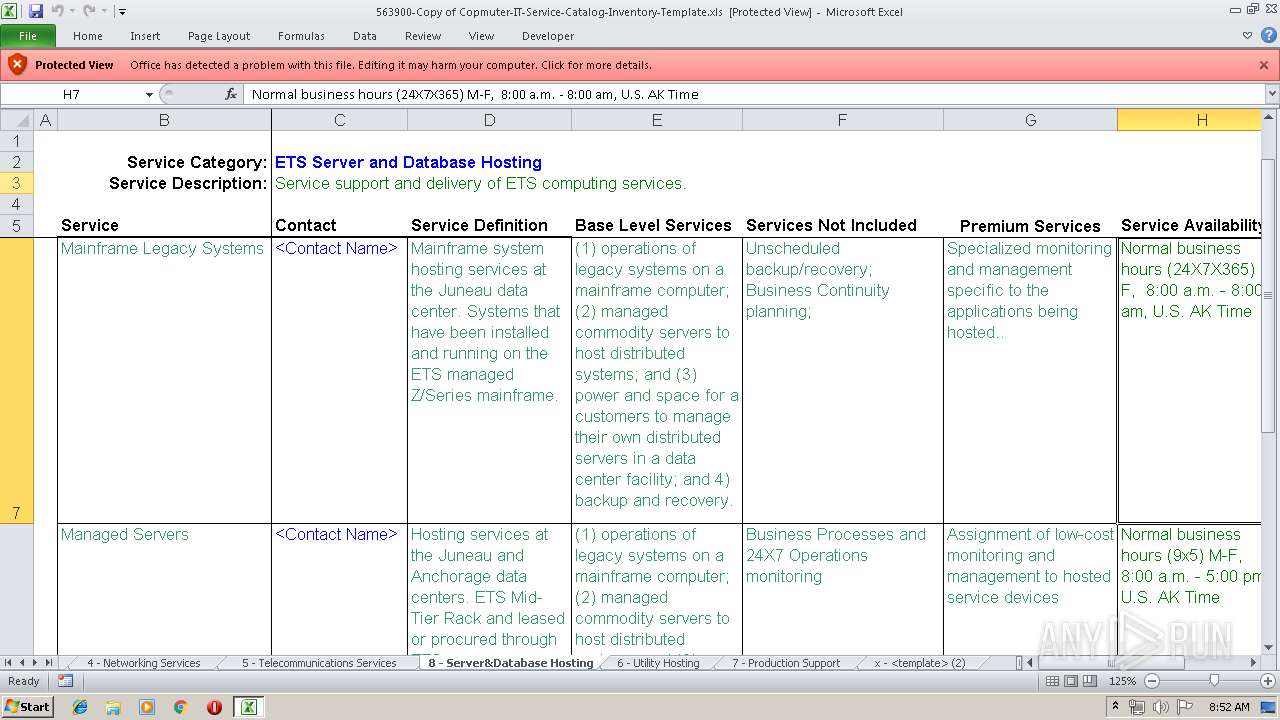
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Title: IT Service Catalog Template, Subject: IT Service Management, Author: ITILworx, Comments: Copyright @ 2004 ITILworxVersion 1.12, Last Saved By: Windows User, Name of Creating Application: Microsoft Excel, Last Printed: Sat Sep 4 20:34:50 2004, Create Time/Date: Wed Aug 14 23:07:56 2002, Last Saved Time/Date: Thu Mar 28 10:01:40 2019, Security: 0 |
| MD5: | 91C924E92C2F7397AE2BCA066D15B2ED |
| SHA1: | 63595CF9FCEE3961248FDB3A123A7014E297EFCD |
| SHA256: | 6B63D2C8A136FD8BAEA8D77AD704B84852E940650BC9BD39E8D68BA504853E11 |
| SSDEEP: | 3072:64A4+rk3hOdsylKlgryzc4bNhZFGzE+cL/gEcrdhgfiIz99yybTLUI:LVck3hOdsylKlgryzc4bNhZF+E+W/gE8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- EXCEL.EXE (PID: 2560)
Starts Microsoft Office Application
- EXCEL.EXE (PID: 2560)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2560)
- EXCEL.EXE (PID: 2800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
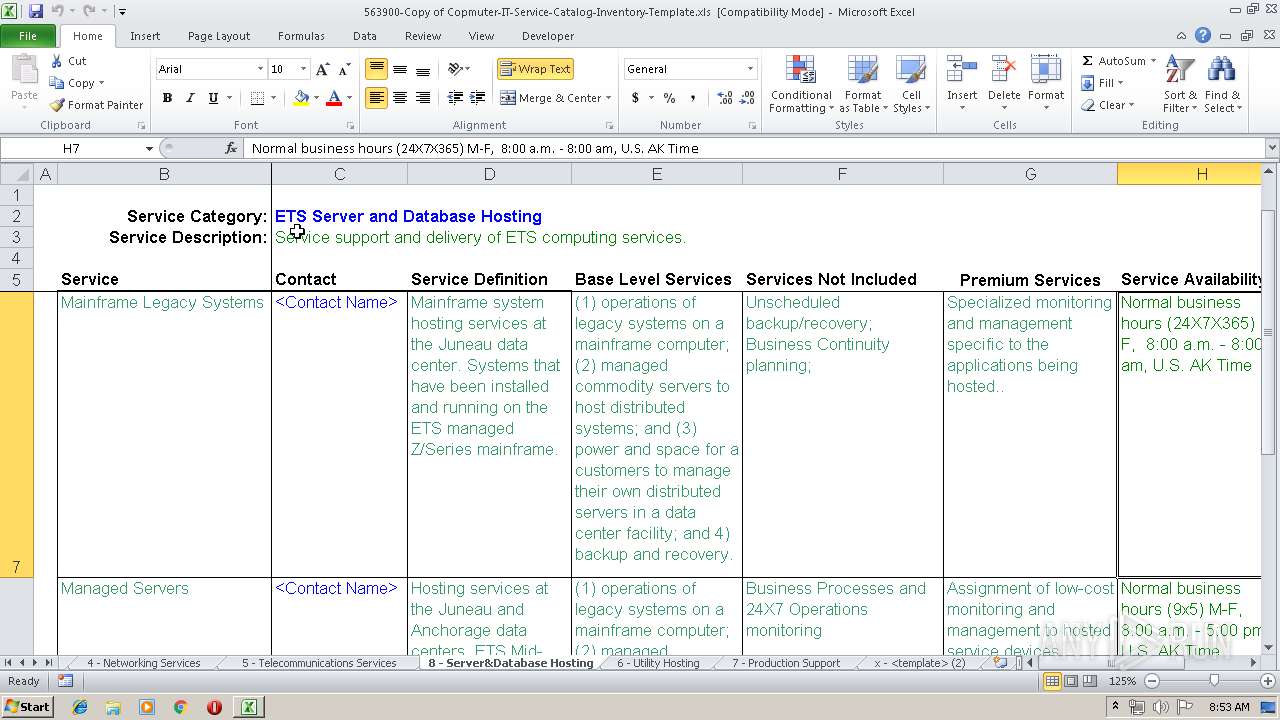
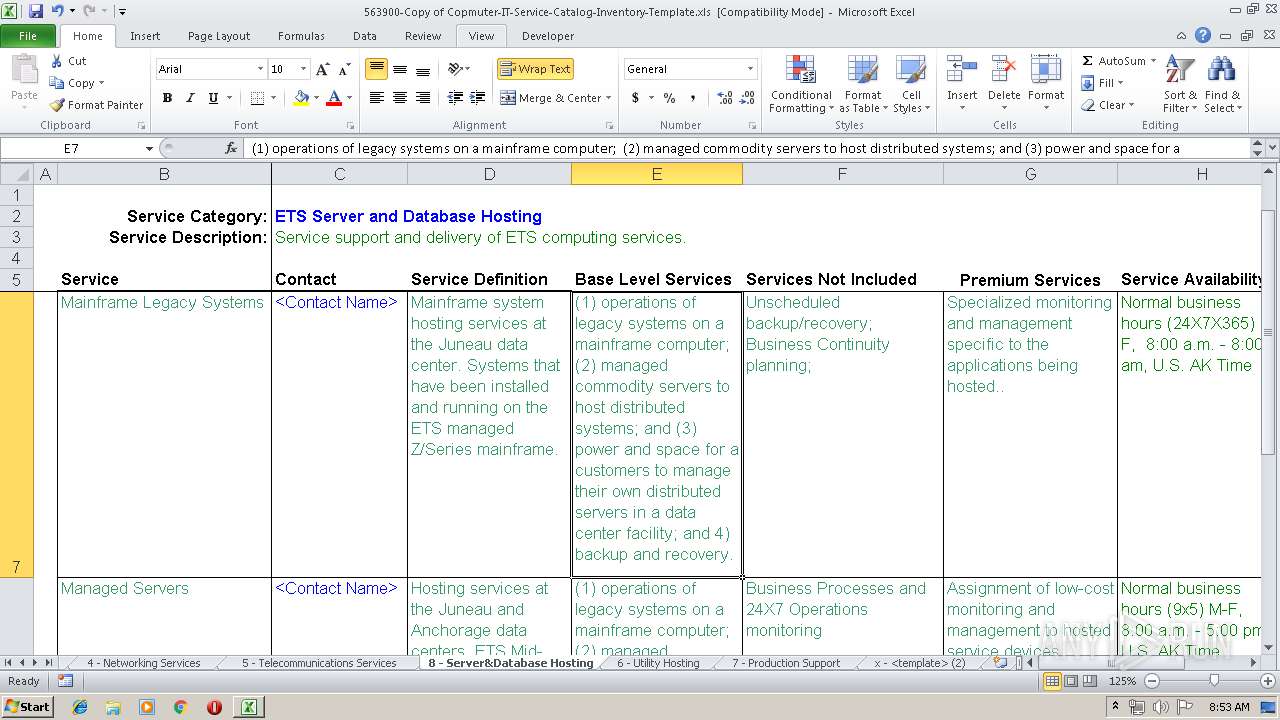
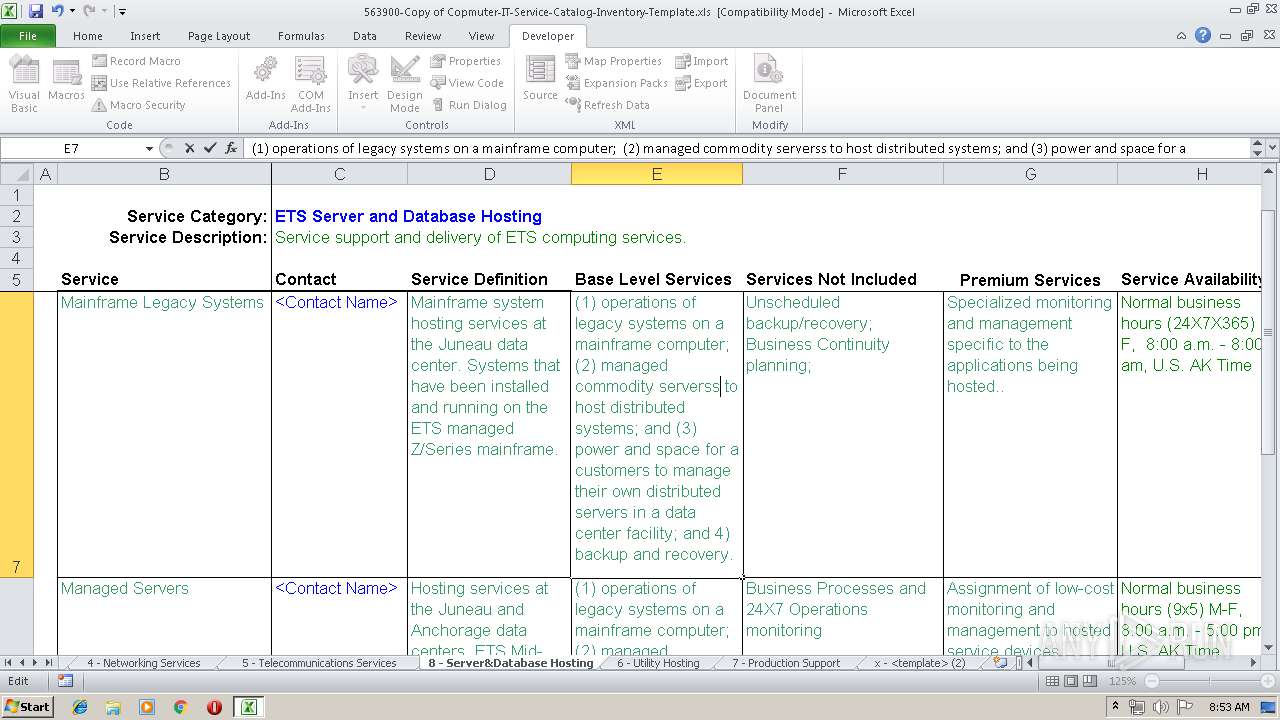
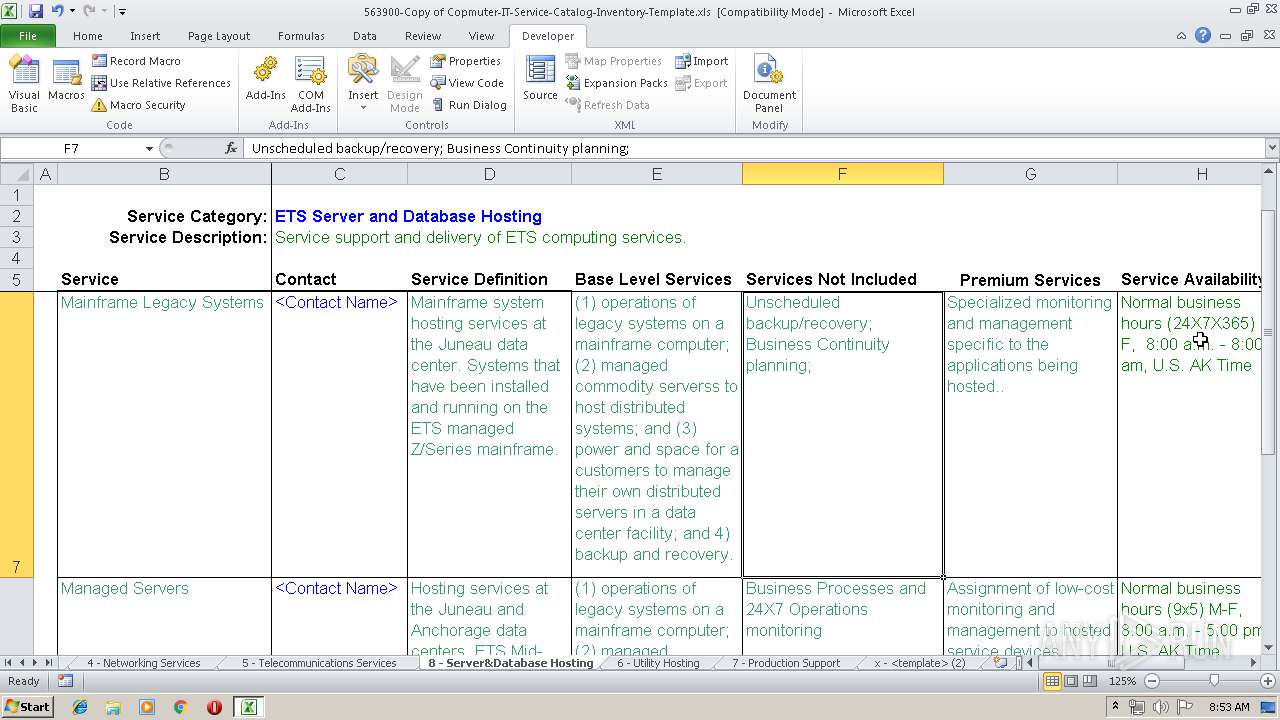
| Title: | IT Service Catalog Template |
|---|---|
| Subject: | IT Service Management |
| Author: | ITILworx |
| Comments: | Copyright @ 2004 ITILworx Version 1.12 |
| LastModifiedBy: | Windows User |
| Software: | Microsoft Excel |
| LastPrinted: | 2004:09:04 19:34:50 |
| CreateDate: | 2002:08:14 22:07:56 |
| ModifyDate: | 2019:03:28 10:01:40 |
| Security: | None |
| Company: | ITILworx |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CodePage: | Windows Latin 1 (Western European) |
| HyperlinkBase: | http://www.itilworx.com |
| Hyperlinks: |
|
| Publisher: | ITILworx |
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2560 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
977
Read events
923
Write events
39
Delete events
15
Modification events
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | mw: |
Value: 6D773A00000A0000010000000000000000000000 | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 000A00003E8FB48F3BF0D40100000000 | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | mw: |
Value: 6D773A00000A0000010000000000000000000000 | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2560) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\1069AA |
| Operation: | write | Name: | 1069AA |
Value: 04000000000A00006300000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C003500360033003900300030002D0043006F007000790020006F006600200043006F0070006D0075007400650072002D00490054002D0053006500720076006900630065002D0043006100740061006C006F0067002D0049006E00760065006E0074006F00720079002D00540065006D0070006C006100740065002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000109AE5903BF0D401AA691000AA69100000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
4
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR63CD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF0FC1FCBD5CC4E065.TMP | — | |
MD5:— | SHA256:— | |||
| 2800 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_6053220F-AE8E-4F3E-998E-0DDE6A68B616.0\~DF6A42CF467FC6FC99.TMP | — | |
MD5:— | SHA256:— | |||
| 2800 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_6053220F-AE8E-4F3E-998E-0DDE6A68B616.0\~DF89B3DD5FCDB48E4D.TMP | — | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Excel\563900-Copy of Copmuter-IT-Service-Catalog-Inventory-Template.xls | document | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\563900-Copy of Copmuter-IT-Service-Catalog-Inventory-Template.xls | document | |
MD5:— | SHA256:— | |||
| 2800 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_6053220F-AE8E-4F3E-998E-0DDE6A68B616.0\mso6CB6.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_6053220F-AE8E-4F3E-998E-0DDE6A68B616.0\D65B7B61.xls | document | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6246E9EE.emf | emf | |
MD5:— | SHA256:— | |||
| 2800 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_6053220F-AE8E-4F3E-998E-0DDE6A68B616.0\9194DE4.emf | emf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report