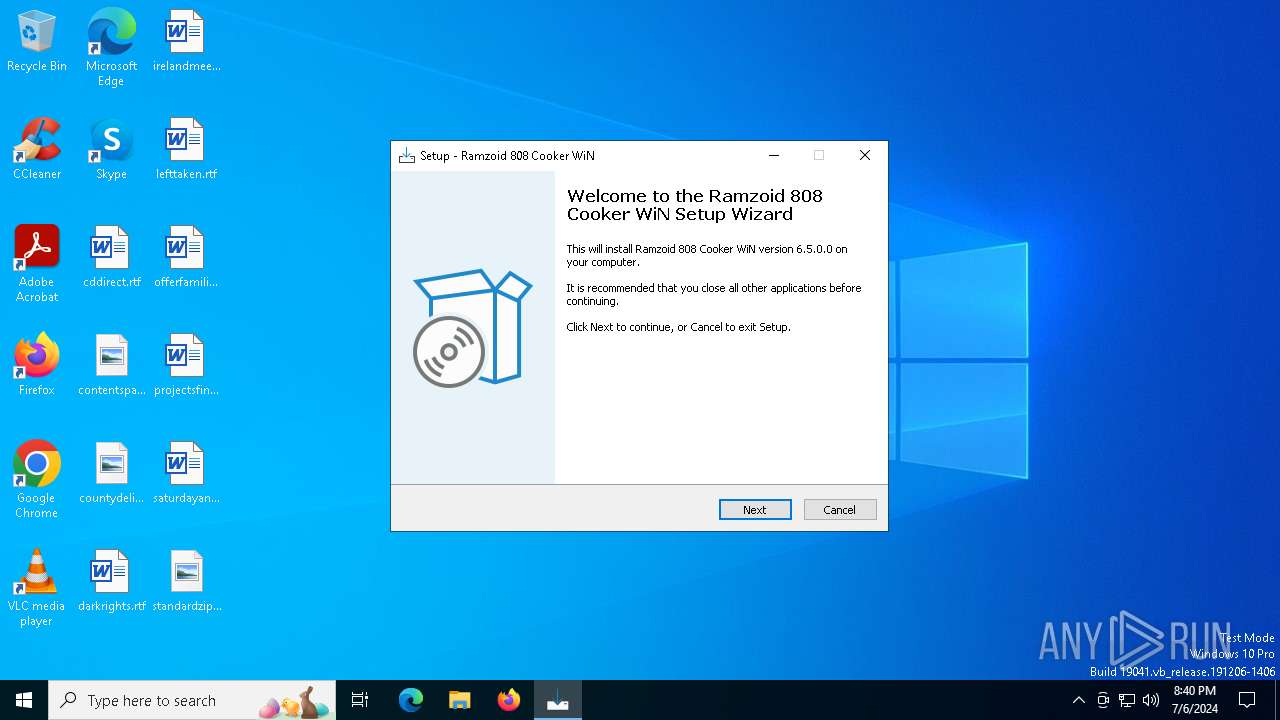
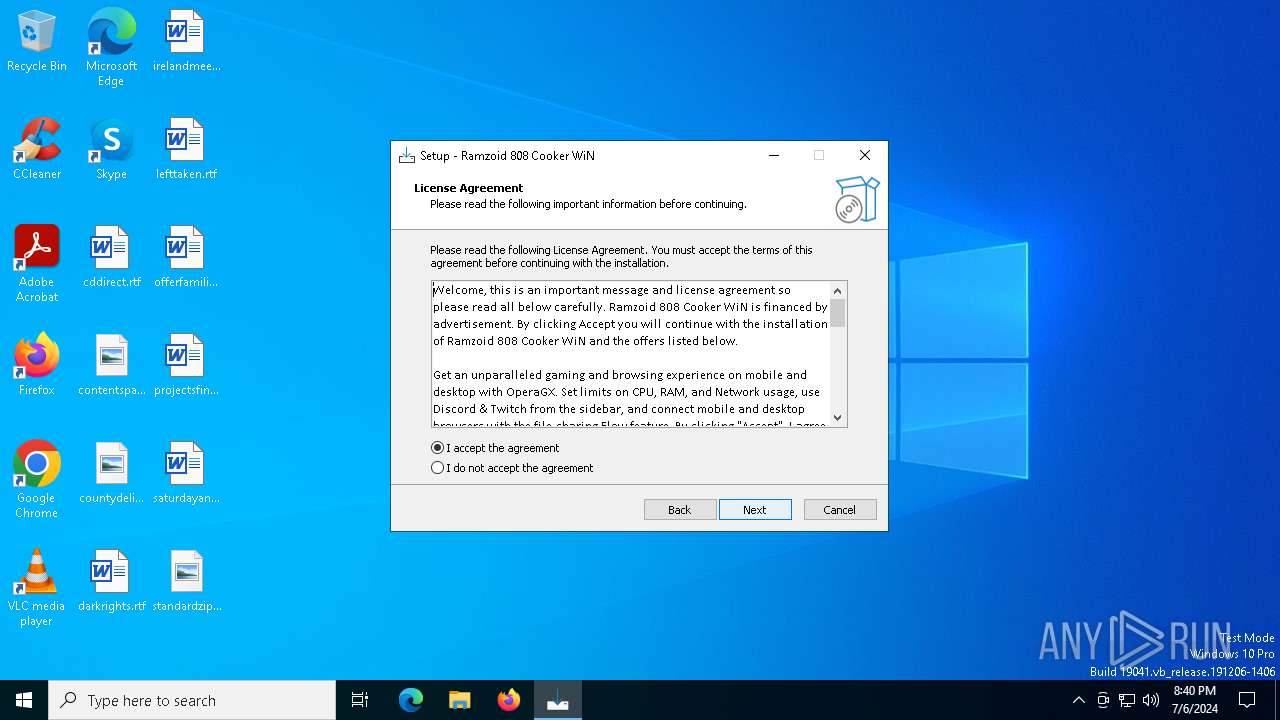
| File name: | Ramzoid 808 Cooker WiN.exe |
| Full analysis: | https://app.any.run/tasks/ff54ae4f-d8ca-4b47-924f-c5005f1b3f65 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2024, 20:40:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5AE0C097380A61C3B446BFF5CA19A965 |
| SHA1: | ECB44125CE048923038A6BB227C61B62B477CD10 |
| SHA256: | 6B57B14D2318A3A4EB00CA7EF50D20772C4D6D32478F44ECD8FBC1ED70888DFE |
| SSDEEP: | 49152:hdixrq3Bdw9SYUJ/fFrSnIhVha3DzNvSmG5PmaHX5Y7+rAM5QFLY7YphlwNW1IZ+:Wrq3BdwJwXFroI8fZG5j35s+rTQFnLjJ |
MALICIOUS
Drops the executable file immediately after the start
- Ramzoid 808 Cooker WiN.exe (PID: 6256)
- Ramzoid 808 Cooker WiN.exe (PID: 6408)
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
SUSPICIOUS
Executable content was dropped or overwritten
- Ramzoid 808 Cooker WiN.exe (PID: 6256)
- Ramzoid 808 Cooker WiN.exe (PID: 6408)
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Reads the date of Windows installation
- Ramzoid 808 Cooker WiN.tmp (PID: 6280)
Reads security settings of Internet Explorer
- Ramzoid 808 Cooker WiN.tmp (PID: 6280)
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Checks Windows Trust Settings
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Reads the Windows owner or organization settings
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
INFO
Checks supported languages
- Ramzoid 808 Cooker WiN.exe (PID: 6256)
- Ramzoid 808 Cooker WiN.tmp (PID: 6280)
- Ramzoid 808 Cooker WiN.exe (PID: 6408)
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
- identity_helper.exe (PID: 8104)
Reads Environment values
- Ramzoid 808 Cooker WiN.exe (PID: 6256)
- Ramzoid 808 Cooker WiN.tmp (PID: 6280)
- Ramzoid 808 Cooker WiN.exe (PID: 6408)
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Reads the computer name
- Ramzoid 808 Cooker WiN.tmp (PID: 6280)
- Ramzoid 808 Cooker WiN.exe (PID: 6408)
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
- identity_helper.exe (PID: 8104)
Create files in a temporary directory
- Ramzoid 808 Cooker WiN.exe (PID: 6256)
- Ramzoid 808 Cooker WiN.exe (PID: 6408)
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Process checks computer location settings
- Ramzoid 808 Cooker WiN.tmp (PID: 6280)
Checks proxy server information
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Creates files in the program directory
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Reads the machine GUID from the registry
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Reads the software policy settings
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
- slui.exe (PID: 1228)
Creates files or folders in the user directory
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Creates a software uninstall entry
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
Manual execution by a user
- msedge.exe (PID: 1768)
Reads Microsoft Office registry keys
- msedge.exe (PID: 1768)
- Ramzoid 808 Cooker WiN.tmp (PID: 6440)
- msedge.exe (PID: 7492)
- msedge.exe (PID: 5856)
Application launched itself
- msedge.exe (PID: 5856)
- msedge.exe (PID: 1768)
- msedge.exe (PID: 7492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:06:10 14:47:11+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 90112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.5.0.0 |
| ProductVersionNumber: | 6.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Ramzoid 808 Cooker WiN Setup |
| FileVersion: | 6.5.0.0 |
| LegalCopyright: | Ramzoid 808 Cooker WiN |
| OriginalFileName: | |
| ProductName: | Ramzoid 808 Cooker WiN |
| ProductVersion: | 6.5.0.0 |
Total processes
200
Monitored processes
52
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1724 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4620 --field-trial-handle=2416,i,4400116244573632278,352928357156905293,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
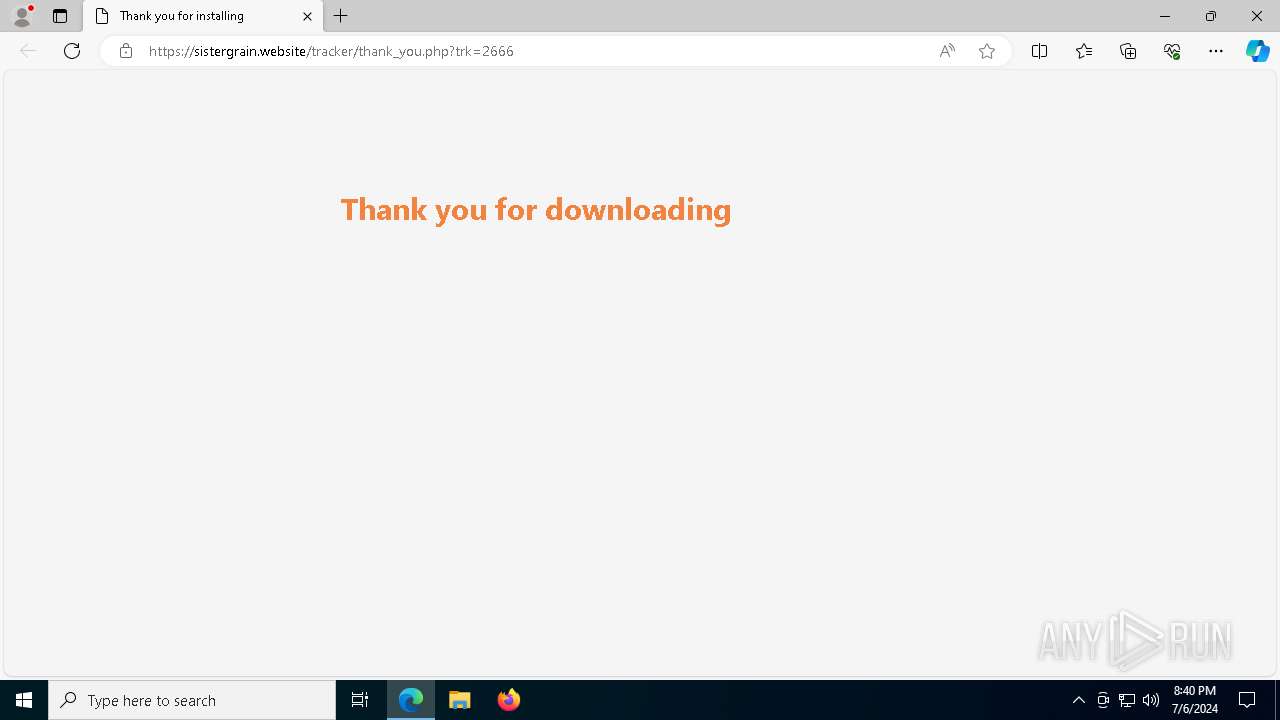
| 1768 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate --single-argument https://sistergrain.website/tracker/thank_you.php?trk=2666 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1796 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2fc,0x300,0x304,0x2f8,0x310,0x7ffd9e325fd8,0x7ffd9e325fe4,0x7ffd9e325ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2220 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4912 --field-trial-handle=2412,i,17179076061007510780,7440875212547563777,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2888 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x264,0x268,0x26c,0x260,0x274,0x7ffd9e325fd8,0x7ffd9e325fe4,0x7ffd9e325ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3596 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5080 --field-trial-handle=2412,i,17179076061007510780,7440875212547563777,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3724 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4920 --field-trial-handle=2416,i,4400116244573632278,352928357156905293,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3392 --field-trial-handle=2416,i,4400116244573632278,352928357156905293,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
19 033
Read events
18 890
Write events
135
Delete events
8
Modification events
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 281900002F1B94B3E4CFDA01 | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: B0B3A7B5CD67D28EDD67F1520FA29AD87AE4C3C6C443F861F5C400DBDC4C47CD | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Ramzoid 808 Cooker WiN_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.3.1 | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Ramzoid 808 Cooker WiN_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\Setup | |||
| (PID) Process: | (6440) Ramzoid 808 Cooker WiN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Ramzoid 808 Cooker WiN_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Setup\ | |||
Executable files
8
Suspicious files
248
Text files
100
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6440 | Ramzoid 808 Cooker WiN.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:CDCFDC3D02652D208B5EA429ACC7B8C9 | SHA256:32E40AB5D9BA80B7223BC5F03558187AD0B2CE09DE2BE988EE03549A63C336A1 | |||
| 6440 | Ramzoid 808 Cooker WiN.tmp | C:\Users\admin\AppData\Local\Temp\is-4RJH0.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
| 5856 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:C771BB0788EF16FBA5F4663F6E8C5583 | SHA256:64F3D26B391A3A0C23DD3755C90D2259B21ED071269A912DCA73A732C95DAE1B | |||
| 5856 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:C7E2197BAE099B13BBB3ADEB1433487D | SHA256:3460EEAF45D581DD43A6E4E17AF8102DDAFF5AEAA88B10099527CF85211629E9 | |||
| 5856 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | binary | |
MD5:7A23DF7B1988BA227EDFECD40DBA5DF8 | SHA256:4B1348087A91C1278E00777A2A385AA357B71A639302F2F40C3A29B7902C3D80 | |||
| 5856 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF1d1129.TMP | binary | |
MD5:D38E65900351368940616574EEA58831 | SHA256:B185F10E1AFDF0EEC98946C2A838EF8A7D95F5C1CD8B43CD82430F908FFF069A | |||
| 5856 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:99EE9F3878A68C103B7B424F43A7BFE8 | SHA256:710390534AAD7E096CBB6BD62CE4CEC55459F12BF80D305EDF3005165D6FA2F7 | |||
| 6440 | Ramzoid 808 Cooker WiN.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:BE2504CEA98D5DF5411788F347B657AE | SHA256:1822962CDF27C4795000F1AC0ED7204F7B1D1E7D923BA259439B1D09CDCFA303 | |||
| 1768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\ac172ad7-73d4-413f-9273-1084b0b26e84.tmp | binary | |
MD5:9CF773CBCF4E8CE9BA957BDAB951BE3D | SHA256:850013860C52DD75AE552E5A76B4F81F531B6C8D35D733F6E851F4C704CC90E4 | |||
| 1768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1d1262.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
95
DNS requests
61
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6392 | svchost.exe | GET | 206 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/83515e92-fb06-47fc-9eeb-072b3031aa1c?P1=1720574499&P2=404&P3=2&P4=cTGb%2b57%2b4LkfK2XbNVX7GgZbZf17gKxtbF8c4D04TNfftX6iCdbFizFQQuE9vxKyp5CAHO9CdwVj3dyrjd3%2bhw%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | GET | 206 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/83515e92-fb06-47fc-9eeb-072b3031aa1c?P1=1720574499&P2=404&P3=2&P4=cTGb%2b57%2b4LkfK2XbNVX7GgZbZf17gKxtbF8c4D04TNfftX6iCdbFizFQQuE9vxKyp5CAHO9CdwVj3dyrjd3%2bhw%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | HEAD | 200 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/83515e92-fb06-47fc-9eeb-072b3031aa1c?P1=1720574499&P2=404&P3=2&P4=cTGb%2b57%2b4LkfK2XbNVX7GgZbZf17gKxtbF8c4D04TNfftX6iCdbFizFQQuE9vxKyp5CAHO9CdwVj3dyrjd3%2bhw%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | GET | 206 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/83515e92-fb06-47fc-9eeb-072b3031aa1c?P1=1720574499&P2=404&P3=2&P4=cTGb%2b57%2b4LkfK2XbNVX7GgZbZf17gKxtbF8c4D04TNfftX6iCdbFizFQQuE9vxKyp5CAHO9CdwVj3dyrjd3%2bhw%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | HEAD | 200 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8a8067c7-27c2-4f62-8fcc-6dc648197b6b?P1=1720856613&P2=404&P3=2&P4=C2hdoiCicjgyizlun%2f24Clu1J9oJPi9UFEEuW%2bNGqE7BlSCipOG%2br3c3dOGI%2fxSpj5qGFurrwE4cNGlaGv4Kcg%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | GET | 206 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8a8067c7-27c2-4f62-8fcc-6dc648197b6b?P1=1720856613&P2=404&P3=2&P4=C2hdoiCicjgyizlun%2f24Clu1J9oJPi9UFEEuW%2bNGqE7BlSCipOG%2br3c3dOGI%2fxSpj5qGFurrwE4cNGlaGv4Kcg%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | GET | 206 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8a8067c7-27c2-4f62-8fcc-6dc648197b6b?P1=1720856613&P2=404&P3=2&P4=C2hdoiCicjgyizlun%2f24Clu1J9oJPi9UFEEuW%2bNGqE7BlSCipOG%2br3c3dOGI%2fxSpj5qGFurrwE4cNGlaGv4Kcg%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | GET | 206 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/83515e92-fb06-47fc-9eeb-072b3031aa1c?P1=1720574499&P2=404&P3=2&P4=cTGb%2b57%2b4LkfK2XbNVX7GgZbZf17gKxtbF8c4D04TNfftX6iCdbFizFQQuE9vxKyp5CAHO9CdwVj3dyrjd3%2bhw%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | GET | 206 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8a8067c7-27c2-4f62-8fcc-6dc648197b6b?P1=1720856613&P2=404&P3=2&P4=C2hdoiCicjgyizlun%2f24Clu1J9oJPi9UFEEuW%2bNGqE7BlSCipOG%2br3c3dOGI%2fxSpj5qGFurrwE4cNGlaGv4Kcg%3d%3d | unknown | — | — | unknown |
6392 | svchost.exe | GET | 206 | 23.48.23.162:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8a8067c7-27c2-4f62-8fcc-6dc648197b6b?P1=1720856613&P2=404&P3=2&P4=C2hdoiCicjgyizlun%2f24Clu1J9oJPi9UFEEuW%2bNGqE7BlSCipOG%2br3c3dOGI%2fxSpj5qGFurrwE4cNGlaGv4Kcg%3d%3d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4448 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
368 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4180 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2568 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2568 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6440 | Ramzoid 808 Cooker WiN.tmp | 188.114.96.3:443 | sistergrain.website | CLOUDFLARENET | NL | unknown |
1060 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
sistergrain.website |
| unknown |
go.microsoft.com |
| whitelisted |
c.pki.goog |
| unknown |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |