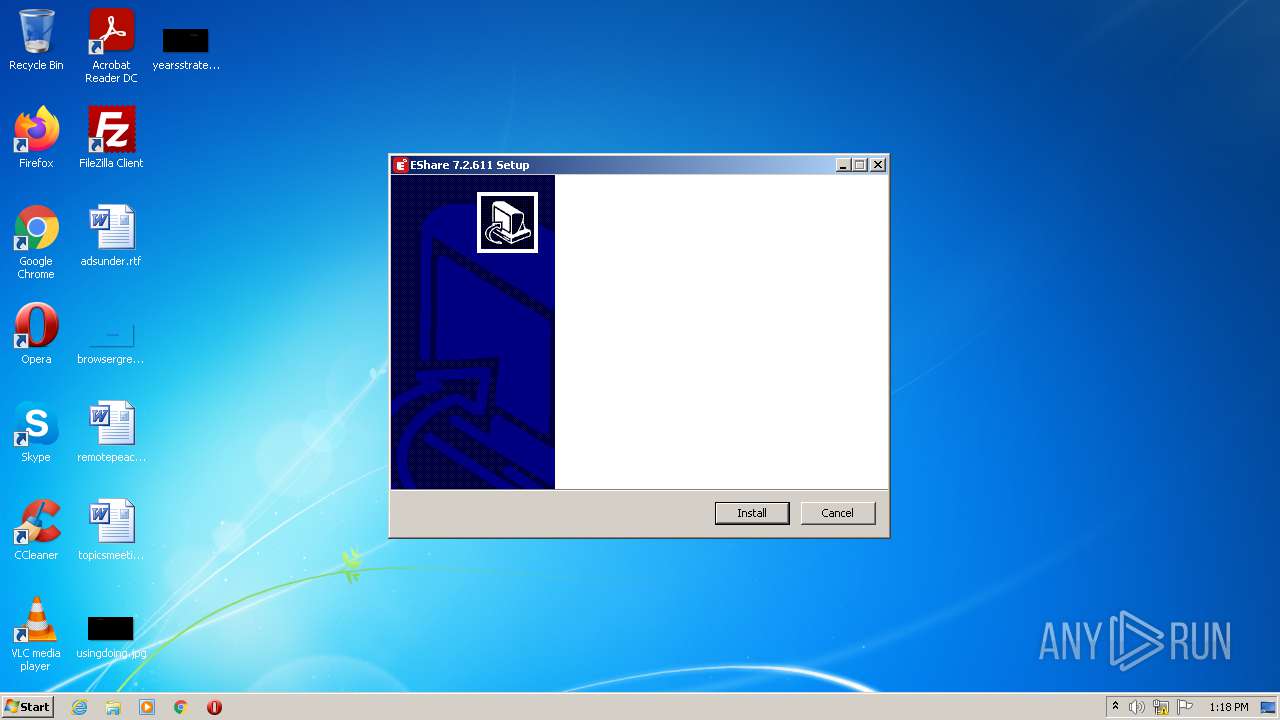
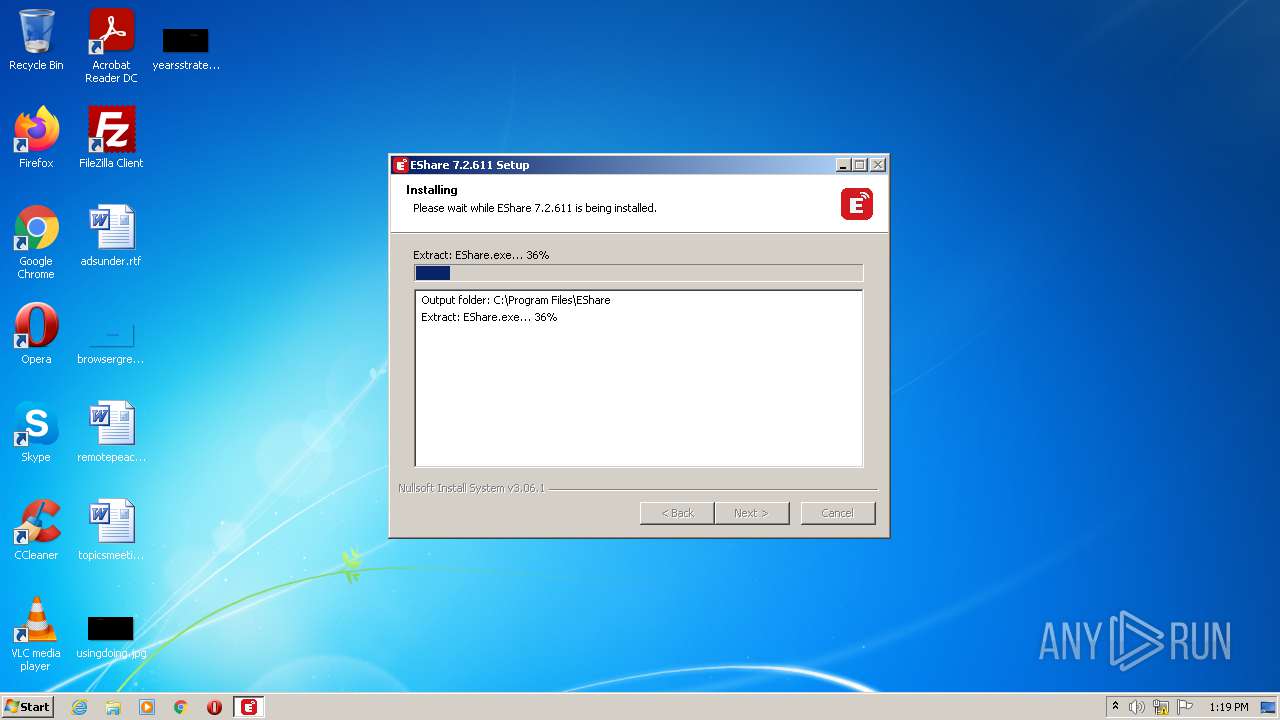
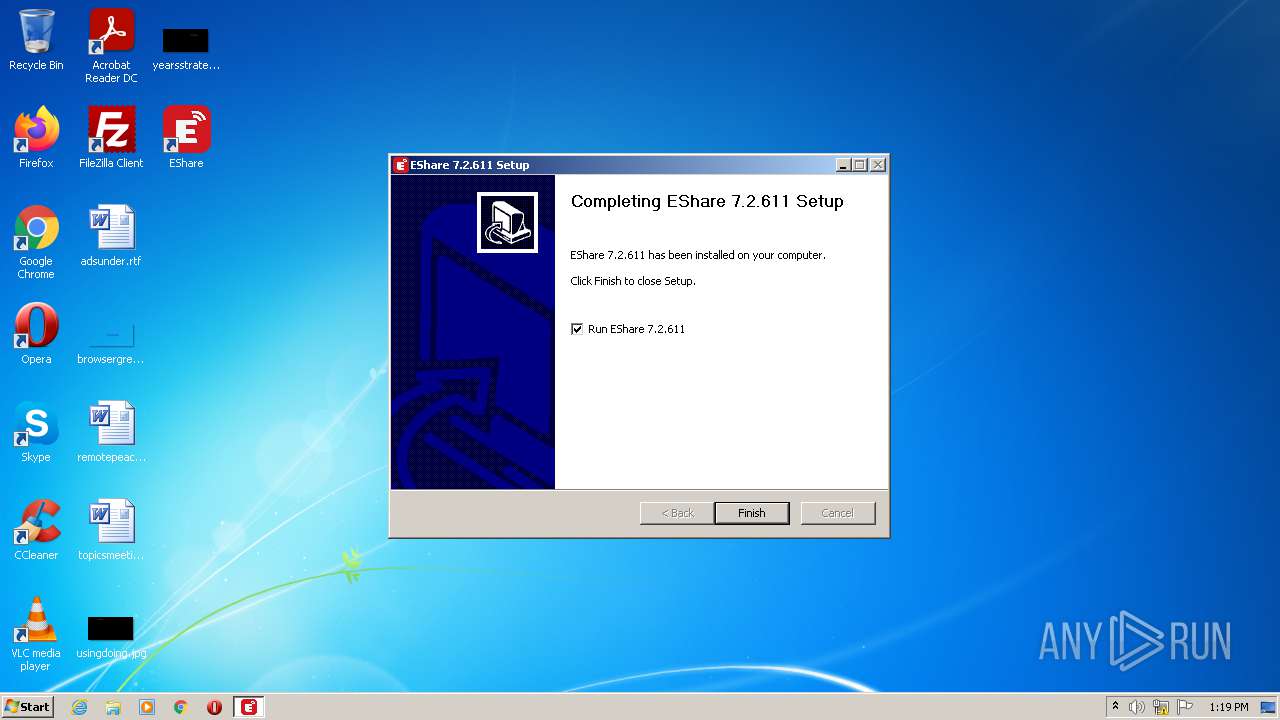
| File name: | EShareClient.exe |
| Full analysis: | https://app.any.run/tasks/b7c6a643-b263-4cfe-8481-8217191a5fa3 |
| Verdict: | Malicious activity |
| Analysis date: | August 03, 2021, 12:18:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | A35416BCF2F8E5657BB998912494F48F |
| SHA1: | AAF6642B6E2E67F11D80CACAE2D601C3573DE757 |
| SHA256: | 6B2D4203E75416125E35A2C7190017A166277C71EB3C2533425EEED1E6C65931 |
| SSDEEP: | 393216:4x8ioEzAAOS6BA/IFOaCuw4AwNZxoP68cEI30WX2jAQSyX:4Sio2A16IFOaCcA4PoPqBX2XNX |
MALICIOUS
Loads dropped or rewritten executable
- EShareClient.exe (PID: 2344)
- RemoteControlService.exe (PID: 872)
- EDisplayDriverInstall.exe (PID: 3024)
Drops executable file immediately after starts
- EShareClient.exe (PID: 2344)
- RemoteControlService.exe (PID: 872)
- EDisplayDriverInstall.exe (PID: 3024)
Application was dropped or rewritten from another process
- RemoteControlService.exe (PID: 872)
- ESystemRemoteService.exe (PID: 1820)
- EDesktop.exe (PID: 1128)
- EDisplayDriverInstall.exe (PID: 3024)
- EDesktopUAC.exe (PID: 2524)
- EShare.exe (PID: 3744)
Adds new firewall rule via NETSH.EXE
- nsF300.tmp (PID: 3784)
SUSPICIOUS
Executable content was dropped or overwritten
- EShareClient.exe (PID: 2344)
- RemoteControlService.exe (PID: 872)
- EDisplayDriverInstall.exe (PID: 3024)
Checks supported languages
- EShareClient.exe (PID: 2344)
- RemoteControlService.exe (PID: 872)
- ESystemRemoteService.exe (PID: 1820)
- EDesktop.exe (PID: 1128)
- EDesktopUAC.exe (PID: 2524)
- EDisplayDriverInstall.exe (PID: 3024)
- nsF224.tmp (PID: 148)
- nsF300.tmp (PID: 3784)
- EShare.exe (PID: 3744)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 2272)
- cmd.exe (PID: 3060)
Reads the computer name
- EShareClient.exe (PID: 2344)
- RemoteControlService.exe (PID: 872)
- EDisplayDriverInstall.exe (PID: 3024)
- ESystemRemoteService.exe (PID: 1820)
- EShare.exe (PID: 3744)
Drops a file that was compiled in debug mode
- EShareClient.exe (PID: 2344)
- EDisplayDriverInstall.exe (PID: 3024)
Creates a directory in Program Files
- RemoteControlService.exe (PID: 872)
- EShareClient.exe (PID: 2344)
- EDisplayDriverInstall.exe (PID: 3024)
Creates files in the program directory
- EShareClient.exe (PID: 2344)
- RemoteControlService.exe (PID: 872)
- EDisplayDriverInstall.exe (PID: 3024)
Drops a file with too old compile date
- RemoteControlService.exe (PID: 872)
- EDisplayDriverInstall.exe (PID: 3024)
Executed as Windows Service
- ESystemRemoteService.exe (PID: 1820)
Creates a software uninstall entry
- EDisplayDriverInstall.exe (PID: 3024)
- RemoteControlService.exe (PID: 872)
- EShareClient.exe (PID: 2344)
Starts application with an unusual extension
- EShareClient.exe (PID: 2344)
Uses NETSH.EXE for network configuration
- nsF224.tmp (PID: 148)
- nsF300.tmp (PID: 3784)
Reads Environment values
- netsh.exe (PID: 2476)
- netsh.exe (PID: 1192)
Uses NETSTAT.EXE to discover network connections
- cmd.exe (PID: 2764)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 2272)
Starts CMD.EXE for commands execution
- EShare.exe (PID: 3744)
INFO
Reads the computer name
- netsh.exe (PID: 2476)
- netsh.exe (PID: 1192)
- NETSTAT.EXE (PID: 3752)
- NETSTAT.EXE (PID: 1268)
- NETSTAT.EXE (PID: 1264)
- NETSTAT.EXE (PID: 3300)
Checks supported languages
- netsh.exe (PID: 2476)
- NETSTAT.EXE (PID: 3300)
- netsh.exe (PID: 1192)
- findstr.exe (PID: 3392)
- NETSTAT.EXE (PID: 3752)
- findstr.exe (PID: 3792)
- NETSTAT.EXE (PID: 1268)
- findstr.exe (PID: 4076)
- findstr.exe (PID: 400)
- NETSTAT.EXE (PID: 1264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | 6 |
| OSVersion: | 4 |
| EntryPoint: | 0x348f |
| UninitializedDataSize: | 2048 |
| InitializedDataSize: | 141824 |
| CodeSize: | 26112 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2020:08:01 04:43:17+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Aug-2020 02:43:17 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 01-Aug-2020 02:43:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006411 | 0x00006600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.40243 |
.rdata | 0x00008000 | 0x00001398 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.13775 |
.data | 0x0000A000 | 0x00020338 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.0208 |
.ndata | 0x0002B000 | 0x00012000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0003D000 | 0x00011730 | 0x00011800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.58538 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.29922 | 1320 | UNKNOWN | English - United States | RT_MANIFEST |
103 | 1.98048 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.73893 | 514 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.91148 | 248 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.89887 | 238 | UNKNOWN | English - United States | RT_DIALOG |
205 | 2.68733 | 494 | UNKNOWN | English - United States | RT_DIALOG |
206 | 2.86626 | 228 | UNKNOWN | English - United States | RT_DIALOG |
211 | 2.9304 | 218 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
66
Monitored processes
24
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Users\admin\AppData\Local\Temp\nsgB97F.tmp\nsF224.tmp" netsh advfirewall firewall delete rule name="EShare" | C:\Users\admin\AppData\Local\Temp\nsgB97F.tmp\nsF224.tmp | — | EShareClient.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 400 | findstr 52020 | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | "C:\Users\admin\AppData\Local\Temp\EShareClient.exe" | C:\Users\admin\AppData\Local\Temp\EShareClient.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 872 | "C:\Program Files\EShare\RemoteControlService.exe" | C:\Program Files\EShare\RemoteControlService.exe | EShareClient.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1128 | "C:/Program Files/ESystemRemoteService/EDesktop.exe" | C:\Program Files\ESystemRemoteService\EDesktop.exe | — | ESystemRemoteService.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1192 | netsh advfirewall firewall delete rule name="EShare" | C:\Windows\system32\netsh.exe | — | nsF224.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | netstat -aon | C:\Windows\system32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1268 | netstat -aon | C:\Windows\system32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1820 | "C:\Program Files\ESystemRemoteService\ESystemRemoteService.exe" | C:\Program Files\ESystemRemoteService\ESystemRemoteService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 1.1.3.1130 Modules
| |||||||||||||||
| 2272 | cmd /c "netstat -aon|findstr 52020" | C:\Windows\system32\cmd.exe | — | EShare.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 441
Read events
3 308
Write events
133
Delete events
0
Modification events
| (PID) Process: | (2344) EShareClient.exe | Key: | HKEY_CURRENT_USER\Software\EShare |
| Operation: | write | Name: | audio |
Value: true | |||
| (PID) Process: | (872) RemoteControlService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\EDesktop.exe |
| Operation: | write | Name: | (default) |
Value: C:\Program Files\ESystemRemoteService\EDesktop.exe | |||
| (PID) Process: | (872) RemoteControlService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ESystemRemoteService |
| Operation: | write | Name: | DisplayName |
Value: ESystemRemoteService 1.1 | |||
| (PID) Process: | (872) RemoteControlService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ESystemRemoteService |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\ESystemRemoteService\uninst.exe | |||
| (PID) Process: | (872) RemoteControlService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ESystemRemoteService |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\ESystemRemoteService\EDesktop.exe | |||
| (PID) Process: | (872) RemoteControlService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ESystemRemoteService |
| Operation: | write | Name: | DisplayVersion |
Value: 1.1 | |||
| (PID) Process: | (872) RemoteControlService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ESystemRemoteService |
| Operation: | write | Name: | URLInfoAbout |
Value: www.ee-share.com | |||
| (PID) Process: | (872) RemoteControlService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ESystemRemoteService |
| Operation: | write | Name: | Publisher |
Value: EShare | |||
| (PID) Process: | (3024) EDisplayDriverInstall.exe | Key: | HKEY_CURRENT_USER\Software\VirtualMonitor |
| Operation: | write | Name: | EShare Virtual Monitor Assistant4 |
Value: 20201102 | |||
| (PID) Process: | (3024) EDisplayDriverInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\devcon.exe |
| Operation: | write | Name: | (default) |
Value: C:\Program Files\EShare Virtual Monitor Assistant4\devcon.exe | |||
Executable files
25
Suspicious files
0
Text files
8
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2344 | EShareClient.exe | C:\Program Files\EShare\uninst.exe | executable | |
MD5:— | SHA256:— | |||
| 2344 | EShareClient.exe | C:\Program Files\EShare\EShare.exe | executable | |
MD5:— | SHA256:— | |||
| 2344 | EShareClient.exe | C:\Users\admin\AppData\Local\Temp\nsgB97F.tmp\InstallOptions.dll | executable | |
MD5:0A9FB96A7579B685EC36B17FC354E6A3 | SHA256:B34FB342F21D690AAC024B6F48A597E78D15791EF480AC55159CD585D0F64AF7 | |||
| 2344 | EShareClient.exe | C:\Users\admin\AppData\Local\Temp\nsgB97F.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 2344 | EShareClient.exe | C:\Users\admin\AppData\Local\Temp\nsgB97F.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 2344 | EShareClient.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\EShare\EShare.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2344 | EShareClient.exe | C:\Users\admin\AppData\Local\Temp\nsgB97F.tmp\LangDLL.dll | executable | |
MD5:014A3BE4A7C1CCB217916DBF4F222BD1 | SHA256:09ACFC5EE34A1DFA1AF3A9D34F00C3B1327B56641FEEBD536E13752349C08AC8 | |||
| 2344 | EShareClient.exe | C:\Program Files\EShare\CrashSender1402.exe | executable | |
MD5:870D76914C77619FD05F44BB732BA5F8 | SHA256:CA3CBD2F17F923961FFF0897D8095D4DA9435A2B70FC5C8788820034D618743A | |||
| 872 | RemoteControlService.exe | C:\Program Files\ESystemRemoteService\EDesktop.exe | executable | |
MD5:FE782D4B47BF92D507B156BBEC62E097 | SHA256:B3CA4777736639A4672460A321E2C8A89A5B7B29BAAFFD96400615F3705B9C4C | |||
| 2344 | EShareClient.exe | C:\Program Files\EShare\VirtualAudioCable.exe | executable | |
MD5:428601614B64551A240494EF3997FFB0 | SHA256:5D12E2D9068F02109E149A9A114B1168F456B175D95E508F8C9511EF673FDEFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
EShare.exe | registerRenderers...........
|
EShare.exe | load en.qm
|
EShare.exe | INFO 2021-08-03 13:19:09.081 ************************************************************************ |
EShare.exe | |
EShare.exe | INFO 2021-08-03 13:19:09.081 EShare Client Start ver:: 7.2.611 |
EShare.exe | |
EShare.exe | DEBUG 2021-08-03 13:19:09.081 a.isPrimary true |
EShare.exe | |
EShare.exe | DEBUG 2021-08-03 13:19:09.081 a.isSecondary false |
EShare.exe | |