| File name: | DumpFiles.7z |
| Full analysis: | https://app.any.run/tasks/592e4490-b41b-4496-9999-e2ffad678471 |
| Verdict: | Malicious activity |
| Analysis date: | February 10, 2022, 16:23:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | EA4D39FDAD743C29853EA6353613DC6E |
| SHA1: | 716C78914ACA71C23131D81880EBCE1309C1C998 |
| SHA256: | 6B2B3B4E45991E913CF6464D467BAAE5FEA604DD9C2289A4F2E93175775BF85B |
| SSDEEP: | 49152:rcijqdOvZVCdqF2lTXzZJW7RE6m9KgJveBhe0Dx6:rcIqMVCdq23F6m90B1g |
MALICIOUS
Loads dropped or rewritten executable
- AteraAgent.exe (PID: 1068)
- AteraAgent.exe (PID: 3636)
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageMonitoring.exe (PID: 3172)
- AgentPackageAgentInformation.exe (PID: 2836)
- AgentPackageMonitoring.exe (PID: 2692)
- AgentPackageSTRemote.exe (PID: 956)
- AgentPackageWindowsUpdate.exe (PID: 2140)
- AgentPackageTicketing.exe (PID: 2528)
- AgentPackageADRemote.exe (PID: 460)
- AgentPackageUpgradeAgent.exe (PID: 656)
- AgentPackageUpgradeAgent.exe (PID: 2900)
- AgentPackageInternalPoller.exe (PID: 3224)
- AgentPackageInternalPoller.exe (PID: 320)
- AgentPackageHeartbeat.exe (PID: 2660)
- AgentPackageNetworkDiscovery.exe (PID: 2312)
- AgentPackageHeartbeat.exe (PID: 704)
- AgentPackageProgramManagement.exe (PID: 632)
- AgentPackageTaskScheduler.exe (PID: 3560)
- AgentPackageHeartbeat.exe (PID: 2108)
- AgentPackageMonitoring.exe (PID: 852)
- MsiExec.exe (PID: 676)
- svchost.exe (PID: 2016)
- Splashtop_Software_Updater.exe (PID: 556)
- SRUtility.exe (PID: 3148)
- SRManager.exe (PID: 3780)
- SRAgent.exe (PID: 2908)
- SRFeature.exe (PID: 3856)
- SRServer.exe (PID: 3172)
- SRUtility.exe (PID: 1304)
- AgentPackageHeartbeat.exe (PID: 3300)
- SRUtility.exe (PID: 3368)
- AgentPackageSTRemote.exe (PID: 676)
- AgentPackageHeartbeat.exe (PID: 3752)
- AgentPackageInternalPoller.exe (PID: 3204)
Application was dropped or rewritten from another process
- AteraAgent.exe (PID: 3636)
- AteraAgent.exe (PID: 1068)
- AgentPackageMonitoring.exe (PID: 2692)
- AgentPackageAgentInformation.exe (PID: 2836)
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageMonitoring.exe (PID: 3172)
- AgentPackageSTRemote.exe (PID: 956)
- AgentPackageWindowsUpdate.exe (PID: 2140)
- AgentPackageTicketing.exe (PID: 2528)
- AgentPackageADRemote.exe (PID: 460)
- AgentPackageUpgradeAgent.exe (PID: 2900)
- AgentPackageUpgradeAgent.exe (PID: 656)
- AgentPackageInternalPoller.exe (PID: 3224)
- AgentPackageInternalPoller.exe (PID: 320)
- AgentPackageProgramManagement.exe (PID: 632)
- AgentPackageTaskScheduler.exe (PID: 3560)
- AgentPackageNetworkDiscovery.exe (PID: 2312)
- AgentPackageHeartbeat.exe (PID: 2108)
- AgentPackageHeartbeat.exe (PID: 704)
- AgentPackageHeartbeat.exe (PID: 2660)
- PreVerCheck.exe (PID: 3172)
- AgentPackageMonitoring.exe (PID: 852)
- SetupUtil.exe (PID: 1480)
- SetupUtil.exe (PID: 2152)
- SetupUtil.exe (PID: 3864)
- SRSelfSignCertUtil.exe (PID: 2600)
- SSU_Clean.exe (PID: 1032)
- Splashtop_Software_Updater.exe (PID: 556)
- SRService.exe (PID: 3608)
- SRService.exe (PID: 2204)
- SRManager.exe (PID: 3780)
- SSUService.exe (PID: 2444)
- SRService.exe (PID: 3132)
- SRUtility.exe (PID: 3148)
- SRAgent.exe (PID: 2908)
- SRFeature.exe (PID: 3856)
- SRAppPB.exe (PID: 3712)
- SRServer.exe (PID: 3172)
- SRUtility.exe (PID: 1304)
- AgentPackageHeartbeat.exe (PID: 3300)
- AgentPackageInternalPoller.exe (PID: 3204)
- SRDetect.exe (PID: 3544)
- SRUtility.exe (PID: 3368)
- AgentPackageHeartbeat.exe (PID: 3752)
- AgentPackageSTRemote.exe (PID: 676)
Changes settings of System certificates
- AteraAgent.exe (PID: 3636)
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageTicketing.exe (PID: 2528)
Drops executable file immediately after starts
- AgentPackageUpgradeAgent.exe (PID: 656)
- SplashtopStreamer3360.exe (PID: 2536)
- MsiExec.exe (PID: 676)
- Splashtop_Software_Updater.exe (PID: 556)
Loads the Task Scheduler COM API
- AgentPackageUpgradeAgent.exe (PID: 2900)
- AgentPackageTaskScheduler.exe (PID: 3560)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2300)
- AteraAgent.exe (PID: 1068)
- AteraAgent.exe (PID: 3636)
- AgentPackageAgentInformation.exe (PID: 3664)
- cmd.exe (PID: 1976)
- cscript.exe (PID: 3320)
- AgentPackageAgentInformation.exe (PID: 2836)
- AgentPackageMonitoring.exe (PID: 2692)
- AgentPackageMonitoring.exe (PID: 3172)
- AgentPackageSTRemote.exe (PID: 956)
- AgentPackageTicketing.exe (PID: 2528)
- AgentPackageWindowsUpdate.exe (PID: 2140)
- AgentPackageADRemote.exe (PID: 460)
- cmd.exe (PID: 4040)
- cscript.exe (PID: 2488)
- AgentPackageUpgradeAgent.exe (PID: 656)
- AgentPackageUpgradeAgent.exe (PID: 2900)
- AgentPackageInternalPoller.exe (PID: 3224)
- AgentPackageProgramManagement.exe (PID: 632)
- AgentPackageHeartbeat.exe (PID: 2660)
- AgentPackageInternalPoller.exe (PID: 320)
- AgentPackageTaskScheduler.exe (PID: 3560)
- AgentPackageNetworkDiscovery.exe (PID: 2312)
- AgentPackageHeartbeat.exe (PID: 704)
- AgentPackageHeartbeat.exe (PID: 2108)
- SplashtopStreamer3360.exe (PID: 2536)
- PreVerCheck.exe (PID: 3172)
- cmd.exe (PID: 484)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 3248)
- cmd.exe (PID: 1380)
- cmd.exe (PID: 3920)
- cmd.exe (PID: 2996)
- cmd.exe (PID: 1976)
- AgentPackageMonitoring.exe (PID: 852)
- SetupUtil.exe (PID: 2152)
- SetupUtil.exe (PID: 3864)
- cmd.exe (PID: 3580)
- SetupUtil.exe (PID: 1480)
- cmd.exe (PID: 1432)
- SRSelfSignCertUtil.exe (PID: 2600)
- SSU_Clean.exe (PID: 1032)
- SSUService.exe (PID: 2444)
- Splashtop_Software_Updater.exe (PID: 556)
- SRService.exe (PID: 2204)
- SRService.exe (PID: 3608)
- SRService.exe (PID: 3132)
- SRManager.exe (PID: 3780)
- SRUtility.exe (PID: 3148)
- SRServer.exe (PID: 3172)
- SRAppPB.exe (PID: 3712)
- SRFeature.exe (PID: 3856)
- SRAgent.exe (PID: 2908)
- SRDetect.exe (PID: 3544)
- SRUtility.exe (PID: 1304)
- AgentPackageHeartbeat.exe (PID: 3300)
- SRUtility.exe (PID: 3368)
- AgentPackageSTRemote.exe (PID: 676)
- AgentPackageHeartbeat.exe (PID: 3752)
- AgentPackageInternalPoller.exe (PID: 3204)
Reads the computer name
- WinRAR.exe (PID: 2300)
- AteraAgent.exe (PID: 1068)
- AteraAgent.exe (PID: 3636)
- AgentPackageAgentInformation.exe (PID: 3664)
- cscript.exe (PID: 3320)
- AgentPackageAgentInformation.exe (PID: 2836)
- AgentPackageMonitoring.exe (PID: 2692)
- AgentPackageMonitoring.exe (PID: 3172)
- AgentPackageWindowsUpdate.exe (PID: 2140)
- AgentPackageSTRemote.exe (PID: 956)
- AgentPackageTicketing.exe (PID: 2528)
- cscript.exe (PID: 2488)
- AgentPackageADRemote.exe (PID: 460)
- AgentPackageUpgradeAgent.exe (PID: 656)
- AgentPackageInternalPoller.exe (PID: 3224)
- AgentPackageUpgradeAgent.exe (PID: 2900)
- AgentPackageProgramManagement.exe (PID: 632)
- AgentPackageInternalPoller.exe (PID: 320)
- AgentPackageHeartbeat.exe (PID: 2660)
- AgentPackageTaskScheduler.exe (PID: 3560)
- AgentPackageNetworkDiscovery.exe (PID: 2312)
- AgentPackageHeartbeat.exe (PID: 704)
- AgentPackageHeartbeat.exe (PID: 2108)
- SplashtopStreamer3360.exe (PID: 2536)
- SetupUtil.exe (PID: 2152)
- AgentPackageMonitoring.exe (PID: 852)
- SetupUtil.exe (PID: 3864)
- SetupUtil.exe (PID: 1480)
- SSU_Clean.exe (PID: 1032)
- SRSelfSignCertUtil.exe (PID: 2600)
- Splashtop_Software_Updater.exe (PID: 556)
- SRService.exe (PID: 3132)
- SRService.exe (PID: 2204)
- SRService.exe (PID: 3608)
- SSUService.exe (PID: 2444)
- SRManager.exe (PID: 3780)
- SRUtility.exe (PID: 3148)
- SRAgent.exe (PID: 2908)
- SRAppPB.exe (PID: 3712)
- SRFeature.exe (PID: 3856)
- SRServer.exe (PID: 3172)
- AgentPackageHeartbeat.exe (PID: 3300)
- AgentPackageInternalPoller.exe (PID: 3204)
- AgentPackageSTRemote.exe (PID: 676)
- AgentPackageHeartbeat.exe (PID: 3752)
- SRUtility.exe (PID: 3368)
Executed as Windows Service
- msiexec.exe (PID: 316)
- vssvc.exe (PID: 3416)
- AteraAgent.exe (PID: 3636)
- SSUService.exe (PID: 2444)
- SRService.exe (PID: 3608)
Reads Windows owner or organization settings
- msiexec.exe (PID: 2428)
- msiexec.exe (PID: 316)
Reads the Windows organization settings
- msiexec.exe (PID: 2428)
- msiexec.exe (PID: 316)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2300)
- msiexec.exe (PID: 316)
- AteraAgent.exe (PID: 3636)
- AgentPackageUpgradeAgent.exe (PID: 656)
- AgentPackageMonitoring.exe (PID: 2692)
- SplashtopStreamer3360.exe (PID: 2536)
- MsiExec.exe (PID: 676)
- AgentPackageMonitoring.exe (PID: 852)
- AgentPackageTicketing.exe (PID: 2528)
- SetupUtil.exe (PID: 3864)
- Splashtop_Software_Updater.exe (PID: 556)
Starts Microsoft Installer
- WinRAR.exe (PID: 2300)
Reads Environment values
- vssvc.exe (PID: 3416)
- AteraAgent.exe (PID: 1068)
- AteraAgent.exe (PID: 3636)
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageMonitoring.exe (PID: 3172)
- AgentPackageMonitoring.exe (PID: 2692)
- AgentPackageAgentInformation.exe (PID: 2836)
- AgentPackageSTRemote.exe (PID: 956)
- AgentPackageWindowsUpdate.exe (PID: 2140)
- AgentPackageTicketing.exe (PID: 2528)
- AgentPackageADRemote.exe (PID: 460)
- AgentPackageUpgradeAgent.exe (PID: 656)
- AgentPackageInternalPoller.exe (PID: 3224)
- AgentPackageUpgradeAgent.exe (PID: 2900)
- AgentPackageInternalPoller.exe (PID: 320)
- AgentPackageProgramManagement.exe (PID: 632)
- AgentPackageTaskScheduler.exe (PID: 3560)
- AgentPackageNetworkDiscovery.exe (PID: 2312)
- AgentPackageHeartbeat.exe (PID: 2660)
- AgentPackageHeartbeat.exe (PID: 704)
- AgentPackageHeartbeat.exe (PID: 2108)
- AgentPackageMonitoring.exe (PID: 852)
- AgentPackageHeartbeat.exe (PID: 3300)
- AgentPackageSTRemote.exe (PID: 676)
- AgentPackageHeartbeat.exe (PID: 3752)
- AgentPackageInternalPoller.exe (PID: 3204)
Application launched itself
- msiexec.exe (PID: 316)
Searches for installed software
- msiexec.exe (PID: 316)
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageProgramManagement.exe (PID: 632)
- AgentPackageAgentInformation.exe (PID: 2836)
Creates a software uninstall entry
- msiexec.exe (PID: 316)
- Splashtop_Software_Updater.exe (PID: 556)
Drops a file with a compile date too recent
- msiexec.exe (PID: 316)
- AteraAgent.exe (PID: 3636)
- AgentPackageUpgradeAgent.exe (PID: 656)
- SplashtopStreamer3360.exe (PID: 2536)
Creates files in the Windows directory
- AteraAgent.exe (PID: 1068)
- AteraAgent.exe (PID: 3636)
- AgentPackageSTRemote.exe (PID: 956)
- AgentPackageUpgradeAgent.exe (PID: 656)
- SplashtopStreamer3360.exe (PID: 2536)
- PreVerCheck.exe (PID: 3172)
- msiexec.exe (PID: 3488)
- MsiExec.exe (PID: 676)
- msiexec.exe (PID: 316)
- SetupUtil.exe (PID: 2152)
- SetupUtil.exe (PID: 1480)
- svchost.exe (PID: 2016)
- SSU_Clean.exe (PID: 1032)
- Splashtop_Software_Updater.exe (PID: 556)
- SRManager.exe (PID: 3780)
- SSUService.exe (PID: 2444)
- SRServer.exe (PID: 3172)
Creates files in the program directory
- AteraAgent.exe (PID: 1068)
- msiexec.exe (PID: 316)
- AgentPackageMonitoring.exe (PID: 3172)
- AgentPackageWindowsUpdate.exe (PID: 2140)
- AteraAgent.exe (PID: 3636)
- AgentPackageSTRemote.exe (PID: 956)
- AgentPackageInternalPoller.exe (PID: 3224)
- AgentPackageAgentInformation.exe (PID: 2836)
- AgentPackageProgramManagement.exe (PID: 632)
- AgentPackageInternalPoller.exe (PID: 320)
- AgentPackageMonitoring.exe (PID: 2692)
- AgentPackageMonitoring.exe (PID: 852)
- MsiExec.exe (PID: 676)
- SetupUtil.exe (PID: 3864)
- AgentPackageTicketing.exe (PID: 2528)
- SRSelfSignCertUtil.exe (PID: 2600)
- Splashtop_Software_Updater.exe (PID: 556)
- SRService.exe (PID: 3132)
- SRManager.exe (PID: 3780)
- SRAgent.exe (PID: 2908)
- SSUService.exe (PID: 2444)
Creates a directory in Program Files
- AteraAgent.exe (PID: 3636)
- msiexec.exe (PID: 316)
- Splashtop_Software_Updater.exe (PID: 556)
- SRService.exe (PID: 3132)
- SRManager.exe (PID: 3780)
- SRAgent.exe (PID: 2908)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 3636)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 316)
- AteraAgent.exe (PID: 3636)
- AgentPackageUpgradeAgent.exe (PID: 656)
- AgentPackageMonitoring.exe (PID: 2692)
- SplashtopStreamer3360.exe (PID: 2536)
- MsiExec.exe (PID: 676)
- AgentPackageMonitoring.exe (PID: 852)
- AgentPackageTicketing.exe (PID: 2528)
- Splashtop_Software_Updater.exe (PID: 556)
Reads the time zone
- svchost.exe (PID: 2016)
Reads Windows Product ID
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageAgentInformation.exe (PID: 2836)
Executes scripts
- cmd.exe (PID: 1976)
- cmd.exe (PID: 4040)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageAgentInformation.exe (PID: 2836)
- MsiExec.exe (PID: 676)
- SetupUtil.exe (PID: 3864)
Adds / modifies Windows certificates
- AgentPackageTicketing.exe (PID: 2528)
Starts itself from another location
- AgentPackageUpgradeAgent.exe (PID: 656)
Drops a file with too old compile date
- AgentPackageMonitoring.exe (PID: 2692)
- MsiExec.exe (PID: 676)
- msiexec.exe (PID: 316)
- AgentPackageMonitoring.exe (PID: 852)
- Splashtop_Software_Updater.exe (PID: 556)
Removes files from Windows directory
- MsiExec.exe (PID: 676)
- SetupUtil.exe (PID: 1480)
- SSU_Clean.exe (PID: 1032)
- Splashtop_Software_Updater.exe (PID: 556)
- SplashtopStreamer3360.exe (PID: 2536)
- SSUService.exe (PID: 2444)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3888)
- cmd.exe (PID: 484)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 3248)
- cmd.exe (PID: 1380)
- cmd.exe (PID: 3920)
- cmd.exe (PID: 1976)
- cmd.exe (PID: 2996)
Changes default file association
- MsiExec.exe (PID: 676)
Uses REG.EXE to modify Windows registry
- MsiExec.exe (PID: 676)
Creates/Modifies COM task schedule object
- reg.exe (PID: 3732)
- SRService.exe (PID: 3132)
Creates or modifies windows services
- Splashtop_Software_Updater.exe (PID: 556)
- SRManager.exe (PID: 3780)
INFO
Checks supported languages
- msiexec.exe (PID: 2428)
- vssvc.exe (PID: 3416)
- msiexec.exe (PID: 316)
- MsiExec.exe (PID: 2920)
- sc.exe (PID: 3388)
- MsiExec.exe (PID: 676)
- msiexec.exe (PID: 3488)
- taskkill.exe (PID: 2280)
- taskkill.exe (PID: 1948)
- taskkill.exe (PID: 2932)
- taskkill.exe (PID: 4012)
- taskkill.exe (PID: 3536)
- taskkill.exe (PID: 3692)
- taskkill.exe (PID: 3268)
- taskkill.exe (PID: 2064)
- regedit.exe (PID: 276)
- regedit.exe (PID: 4084)
- reg.exe (PID: 3732)
- wevtutil.exe (PID: 2648)
- wevtutil.exe (PID: 3380)
- svchost.exe (PID: 2016)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 2300)
Checks Windows Trust Settings
- msiexec.exe (PID: 2428)
- msiexec.exe (PID: 316)
- cscript.exe (PID: 3320)
- cscript.exe (PID: 2488)
- SRManager.exe (PID: 3780)
Reads the computer name
- msiexec.exe (PID: 2428)
- msiexec.exe (PID: 316)
- vssvc.exe (PID: 3416)
- MsiExec.exe (PID: 2920)
- sc.exe (PID: 3388)
- MsiExec.exe (PID: 676)
- msiexec.exe (PID: 3488)
- taskkill.exe (PID: 2280)
- taskkill.exe (PID: 1948)
- taskkill.exe (PID: 2932)
- taskkill.exe (PID: 3536)
- taskkill.exe (PID: 3268)
- taskkill.exe (PID: 3692)
- taskkill.exe (PID: 2064)
- taskkill.exe (PID: 4012)
- wevtutil.exe (PID: 2648)
- wevtutil.exe (PID: 3380)
Dropped object may contain URL to Tor Browser
- WinRAR.exe (PID: 2300)
Reads settings of System Certificates
- msiexec.exe (PID: 2428)
- msiexec.exe (PID: 316)
- AteraAgent.exe (PID: 3636)
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageMonitoring.exe (PID: 3172)
- AgentPackageSTRemote.exe (PID: 956)
- AgentPackageWindowsUpdate.exe (PID: 2140)
- AgentPackageTicketing.exe (PID: 2528)
- AgentPackageInternalPoller.exe (PID: 3224)
- AgentPackageADRemote.exe (PID: 460)
- AgentPackageAgentInformation.exe (PID: 2836)
- AgentPackageInternalPoller.exe (PID: 320)
- AgentPackageProgramManagement.exe (PID: 632)
- AgentPackageHeartbeat.exe (PID: 2660)
- AgentPackageHeartbeat.exe (PID: 704)
- AgentPackageMonitoring.exe (PID: 2692)
- AgentPackageHeartbeat.exe (PID: 2108)
- SRManager.exe (PID: 3780)
- AgentPackageMonitoring.exe (PID: 852)
- AgentPackageHeartbeat.exe (PID: 3300)
- SSUService.exe (PID: 2444)
- AgentPackageHeartbeat.exe (PID: 3752)
Reads CPU info
- svchost.exe (PID: 2016)
Reads Microsoft Office registry keys
- AgentPackageAgentInformation.exe (PID: 3664)
- AgentPackageAgentInformation.exe (PID: 2836)
Dropped object may contain Bitcoin addresses
- SRAgent.exe (PID: 2908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
165
Monitored processes
82
Malicious processes
40
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | regedit.exe /s "C:\Windows\TEMP\{B7C5EA94-B96A-41F5-BE95-25D78B486678}\InstRegExp.reg" | C:\Windows\regedit.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 320 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageInternalPoller\AgentPackageInternalPoller.exe" ebfacb49-64ce-4228-8744-397b6d001845 "68f8d0a5-6704-4249-8ed2-a1a61ea2b200" agent-api.atera.com/Production 443 or8ixLi90Mf "syncdevices" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageInternalPoller\AgentPackageInternalPoller.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageInternalPoller Exit code: 0 Version: 21.6.0.0 Modules
| |||||||||||||||
| 460 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageADRemote\AgentPackageADRemote.exe" ebfacb49-64ce-4228-8744-397b6d001845 "04982b1a-7b76-4a80-a1f5-26ed8db9fea1" agent-api.atera.com/Production 443 or8ixLi90Mf "eyJBZENvbW1hbmRUeXBlIjo1LCJJbnN0YWxsYXRpb25GaWxlVXJsIjpudWxsfQ==" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageADRemote\AgentPackageADRemote.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageADRemote Exit code: 0 Version: 4.4.0.0 Modules
| |||||||||||||||
| 484 | C:\Windows\System32\cmd.exe /C "taskkill.exe /F /IM SRApp.exe /T" | C:\Windows\System32\cmd.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
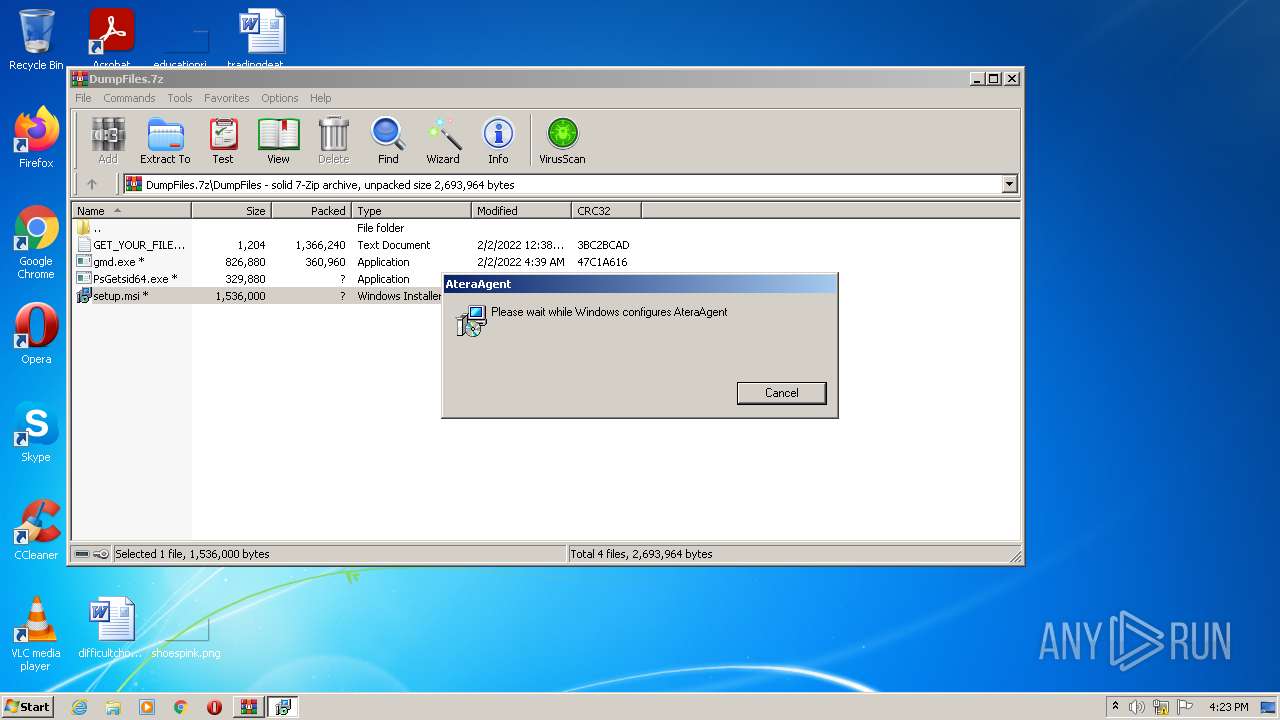
| 556 | C:\Windows\Temp\{B7C5EA94-B96A-41F5-BE95-25D78B486678}\Splashtop_Software_Updater.exe /S /Caller=SVR | C:\Windows\Temp\{B7C5EA94-B96A-41F5-BE95-25D78B486678}\Splashtop_Software_Updater.exe | MsiExec.exe | ||||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop software updater enables updates and enhancements to the SmartView browser extension. Exit code: 0 Version: 1.5.6.19 Modules
| |||||||||||||||
| 632 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageProgramManagement\AgentPackageProgramManagement.exe" ebfacb49-64ce-4228-8744-397b6d001845 "da03519c-4a8f-4a70-a3eb-935a86f99018" agent-api.atera.com/Production 443 or8ixLi90Mf "syncinstalledapps" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageProgramManagement\AgentPackageProgramManagement.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageProgramManagement Exit code: 0 Version: 20.6.0.0 Modules
| |||||||||||||||
| 656 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageUpgradeAgent\AgentPackageUpgradeAgent.exe" ebfacb49-64ce-4228-8744-397b6d001845 "50dca861-006f-4a80-a51f-f8cdfc4dd8f5" agent-api.atera.com/Production 443 or8ixLi90Mf "checkforupdates" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageUpgradeAgent\AgentPackageUpgradeAgent.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks LTD Integrity Level: SYSTEM Description: AgentPackageUpgradeAgent Exit code: 0 Version: 23.6.0.0 Modules
| |||||||||||||||
| 676 | C:\Windows\system32\MsiExec.exe -Embedding B6D0B25F91DB254D545ED72A7D3BF5DC E Global\MSI0000 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 676 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageSTRemote\AgentPackageSTRemote.exe" ebfacb49-64ce-4228-8744-397b6d001845 "8464ac7f-95c3-4444-9997-031207abaf87" agent-api.atera.com/Production 443 or8ixLi90Mf "downloadifneeded" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageSTRemote\AgentPackageSTRemote.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageSTRemote Exit code: 0 Version: 18.12.0.0 Modules
| |||||||||||||||
Total events
101 524
Read events
99 701
Write events
1 798
Delete events
25
Modification events
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\DumpFiles.7z | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
352
Suspicious files
90
Text files
180
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 316 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 316 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
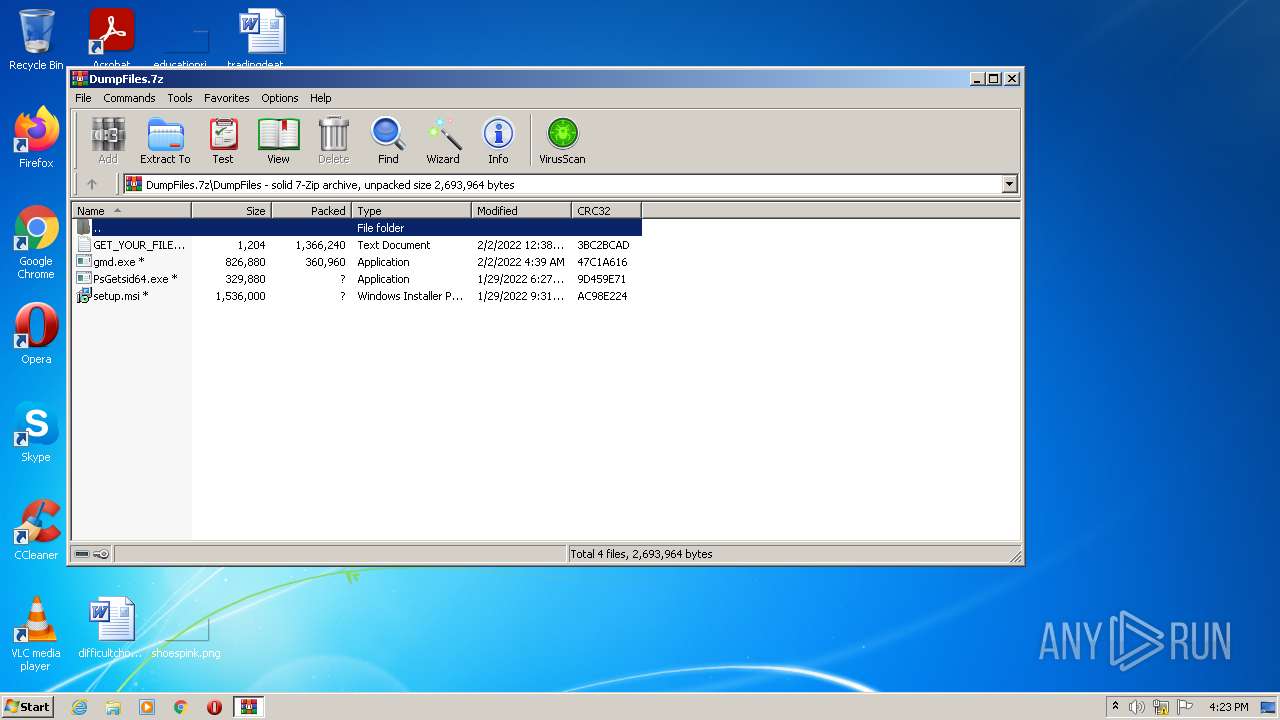
| 2300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2300.38350\DumpFiles\GET_YOUR_FILES_BACK.txt | text | |
MD5:— | SHA256:— | |||
| 2300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2300.38350\DumpFiles\setup.msi | executable | |
MD5:— | SHA256:— | |||
| 316 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF81441487BF5A12B4.TMP | gmc | |
MD5:— | SHA256:— | |||
| 316 | msiexec.exe | C:\Windows\Installer\e846f.ipi | binary | |
MD5:— | SHA256:— | |||
| 316 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{ff02fb7e-d6da-47f2-b03b-88cccc0d13e9}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
| 316 | msiexec.exe | C:\Windows\Installer\MSI8AD6.tmp | binary | |
MD5:— | SHA256:— | |||
| 2300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2300.38350\DumpFiles\gmd.exe | executable | |
MD5:— | SHA256:— | |||
| 316 | msiexec.exe | C:\Windows\Installer\e846e.msi | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
53
DNS requests
34
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3636 | AteraAgent.exe | GET | — | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0ff66268f039194e | US | — | — | whitelisted |
3636 | AteraAgent.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEA9Pb936OTbfiKMzmkd4EHs%3D | US | der | 471 b | whitelisted |
3780 | SRManager.exe | GET | 200 | 23.37.43.27:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEHhvSYT5N0gvTTb3x7RJTGs%3D | NL | der | 1.47 Kb | shared |
2444 | SSUService.exe | POST | — | 107.22.247.100:80 | http://ds1.devicevm.com/ | US | — | — | suspicious |
3780 | SRManager.exe | GET | 200 | 23.37.43.27:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | NL | der | 1.52 Kb | whitelisted |
3636 | AteraAgent.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | US | der | 471 b | whitelisted |
3636 | AteraAgent.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0ddb956bfdb9c6b2 | US | compressed | 4.70 Kb | whitelisted |
3636 | AteraAgent.exe | GET | 200 | 104.18.11.39:80 | http://cacerts.thawte.com/ThawteRSACA2018.crt | US | der | 1.14 Kb | whitelisted |
2444 | SSUService.exe | GET | 301 | 34.200.72.34:80 | http://sn.splashtop.com/file_system/apt_repository/dists/ProtoSSU01/released/binary-i386/Packages.gz | US | html | 134 b | suspicious |
3636 | AteraAgent.exe | GET | 200 | 104.18.11.39:80 | http://cacerts.digicert.com/DigiCertEVCodeSigningCA-SHA2.crt | US | der | 1.69 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3636 | AteraAgent.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3636 | AteraAgent.exe | 40.119.152.241:443 | agent-api.atera.com | Microsoft Corporation | US | suspicious |
3664 | AgentPackageAgentInformation.exe | 40.119.152.241:443 | agent-api.atera.com | Microsoft Corporation | US | suspicious |
3172 | AgentPackageMonitoring.exe | 40.119.152.241:443 | agent-api.atera.com | Microsoft Corporation | US | suspicious |
956 | AgentPackageSTRemote.exe | 40.119.152.241:443 | agent-api.atera.com | Microsoft Corporation | US | suspicious |
2140 | AgentPackageWindowsUpdate.exe | 40.119.152.241:443 | agent-api.atera.com | Microsoft Corporation | US | suspicious |
956 | AgentPackageSTRemote.exe | 52.9.141.147:443 | my.splashtop.com | Amazon.com, Inc. | US | suspicious |
2528 | AgentPackageTicketing.exe | 152.199.23.209:443 | api.nuget.org | MCI Communications Services, Inc. d/b/a Verizon Business | US | suspicious |
3224 | AgentPackageInternalPoller.exe | 40.119.152.241:443 | agent-api.atera.com | Microsoft Corporation | US | suspicious |
956 | AgentPackageSTRemote.exe | 18.66.248.5:443 | download.splashtop.com | Massachusetts Institute of Technology | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
agent-api.atera.com |
| suspicious |
cacerts.thawte.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ps.pndsn.com |
| suspicious |
ps.atera.com |
| suspicious |
cacerts.digicert.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
my.splashtop.com |
| suspicious |
api.nuget.org |
| whitelisted |
download.splashtop.com |
| suspicious |
Threats
26 ETPRO signatures available at the full report
Process | Message |
|---|---|
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUtility::OSInfo] OS 6.1(7601) Service Pack 1 x64:0 (Last=0) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::FindHeader] Name:C:\Windows\TEMP\SplashtopStreamer3360.exe (Last=0) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::FindHeader] Sign Size:7776 (Last=0) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::FindHeader] Header offset:429568 (Last=183) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::UnPackFiles] FreeSpace:234124738560 FileSize:34159616 (Last=0) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\Windows\TEMP\unpack\setup.msi (34159616) (Last=0) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::UnPackFiles] UnPack count:1 len:34159616 File:(null) (Last=0) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::UnPackFiles] FreeSpace:234090573824 FileSize:15 (Last=183) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::UnPackFiles] (2/5)UnPack file name:C:\Windows\TEMP\unpack\run.bat (15) (Last=122) |
SplashtopStreamer3360.exe | [2536]2022-02-10 16:27:28 [CUnPack::UnPackFiles] UnPack count:2 len:15 File:(null) (Last=0) |