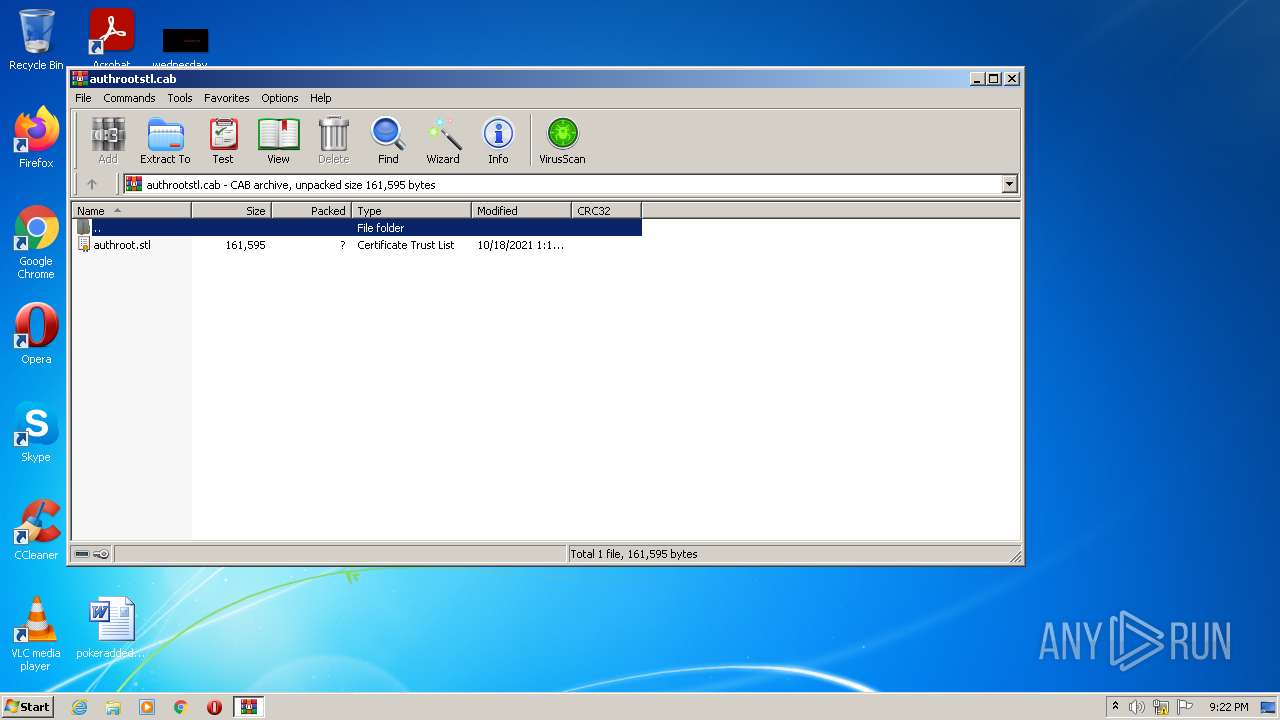
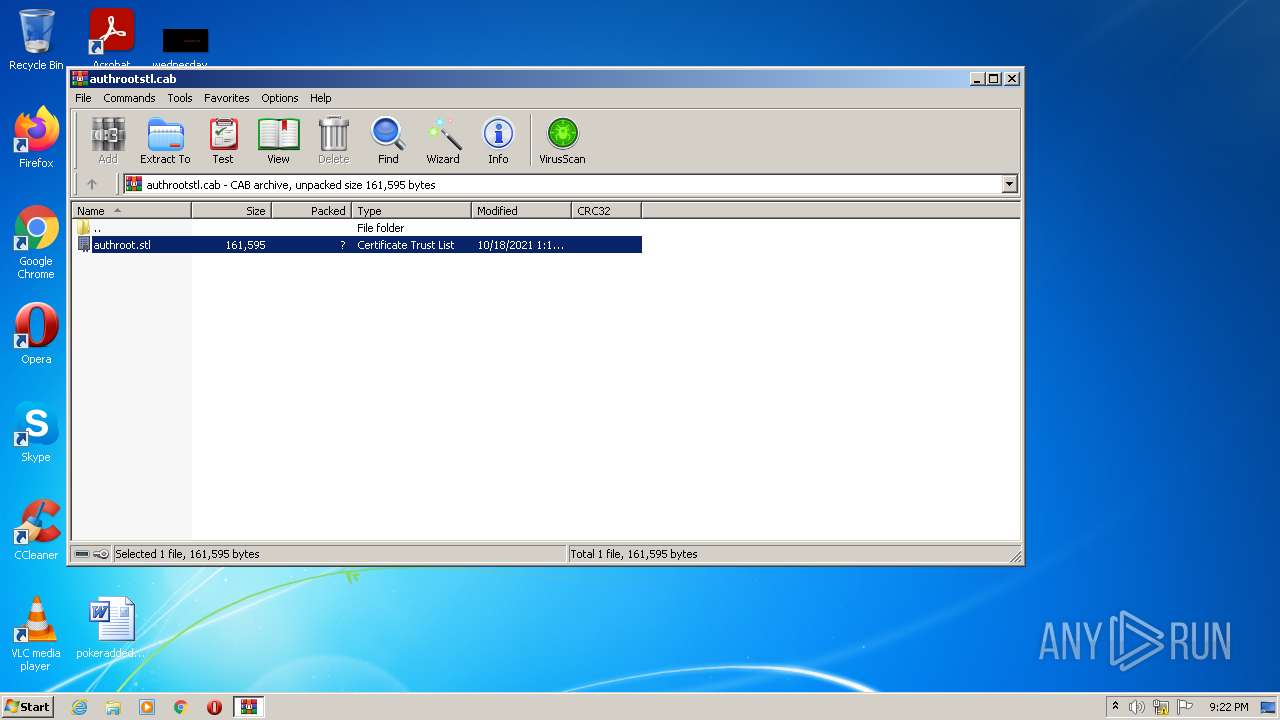
| download: | authrootstl.cab |
| Full analysis: | https://app.any.run/tasks/7a1b0c52-9a19-404d-875e-dd69db6c4622 |
| Verdict: | Malicious activity |
| Analysis date: | January 04, 2022, 21:21:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/vnd.ms-cab-compressed |
| File info: | Microsoft Cabinet archive data, 61414 bytes, 1 file |
| MD5: | ACAEDA60C79C6BCAC925EEB3653F45E0 |
| SHA1: | 2AAAE490BCDACCC6172240FF1697753B37AC5578 |
| SHA256: | 6B0CECCF0103AFD89844761417C1D23ACC41F8AEBF3B7230765209B61EEE5658 |
| SSDEEP: | 1536:EysgU6qmzixT64jYMZ8HbVPGfVDwm/xLZ9rP:wF6qmeo4eH1m9wmLvrP |
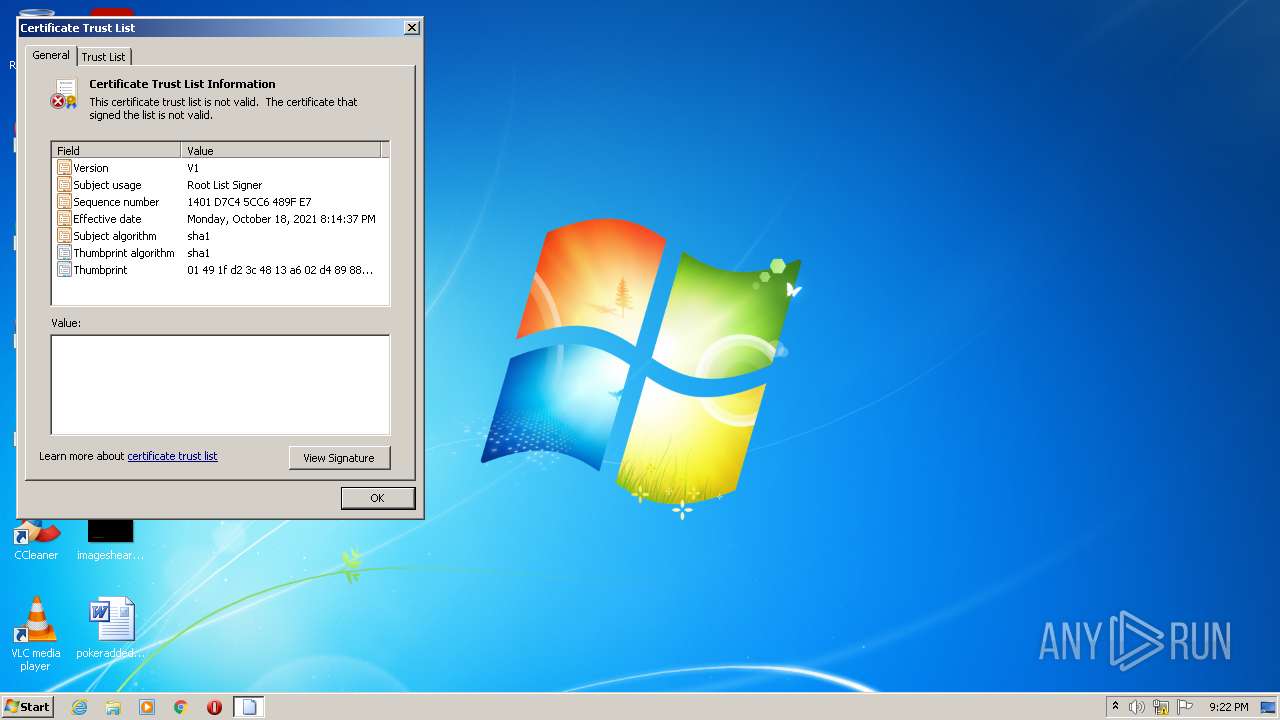
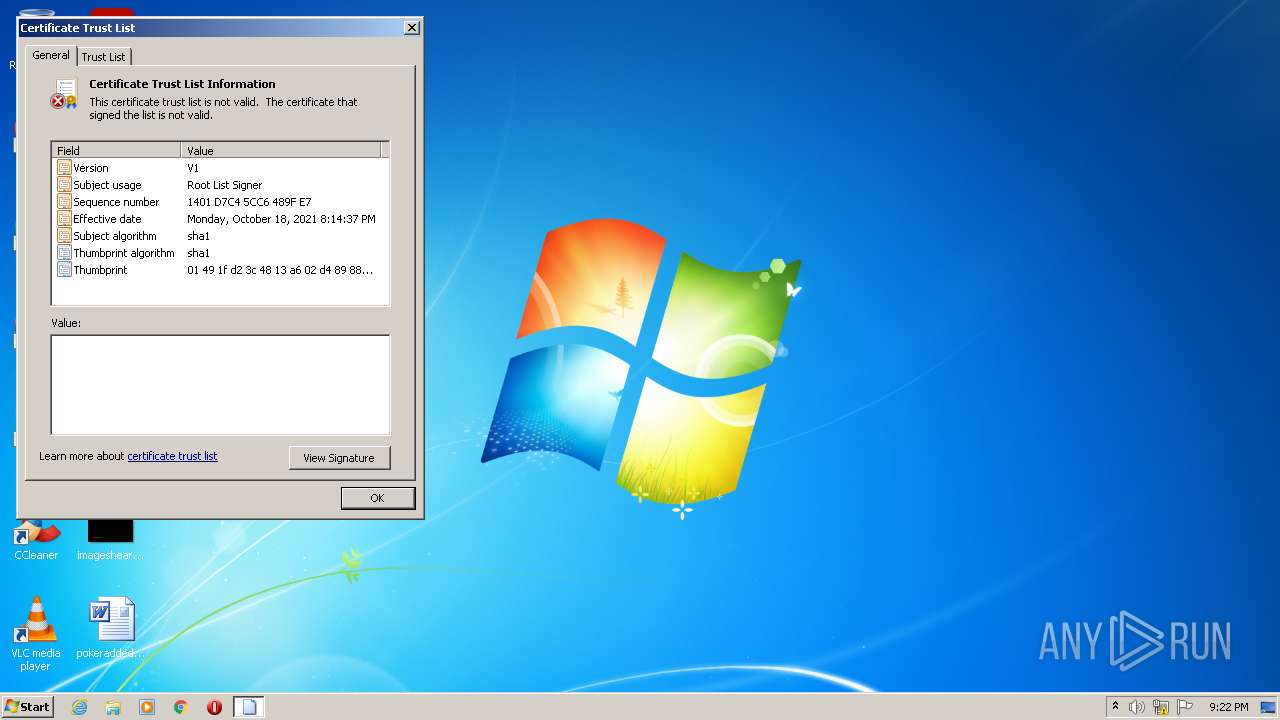
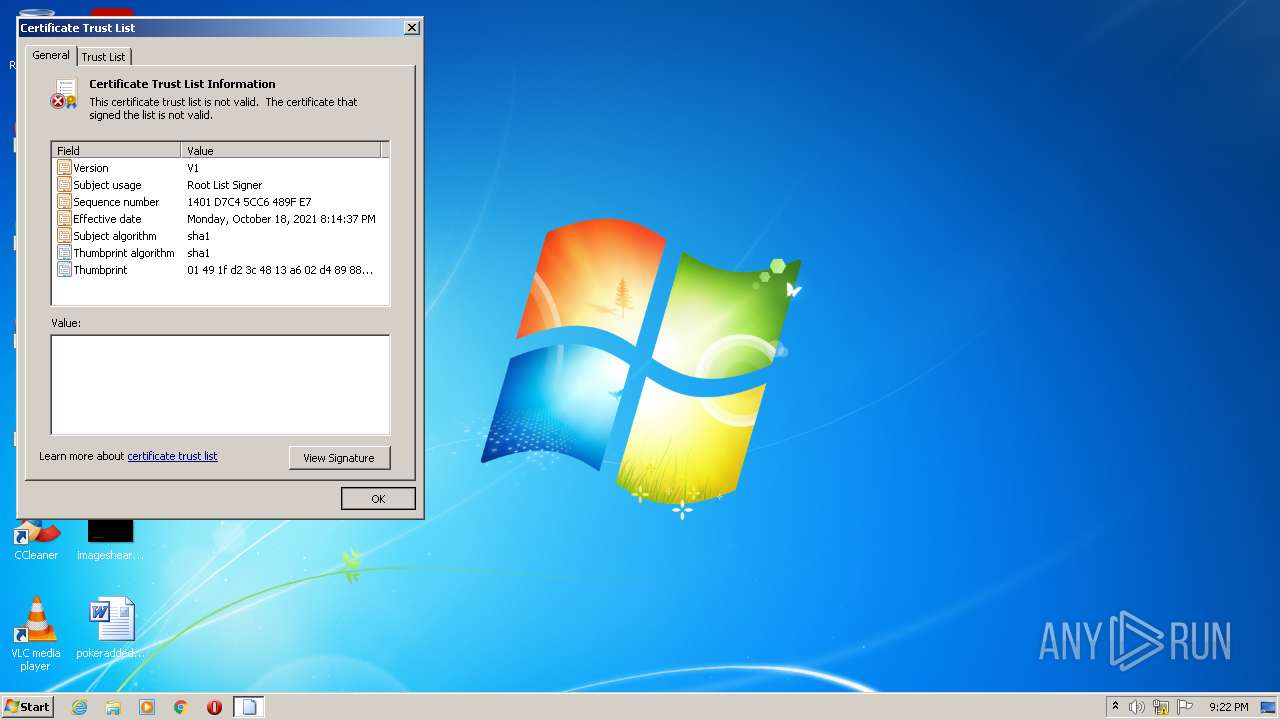
MALICIOUS
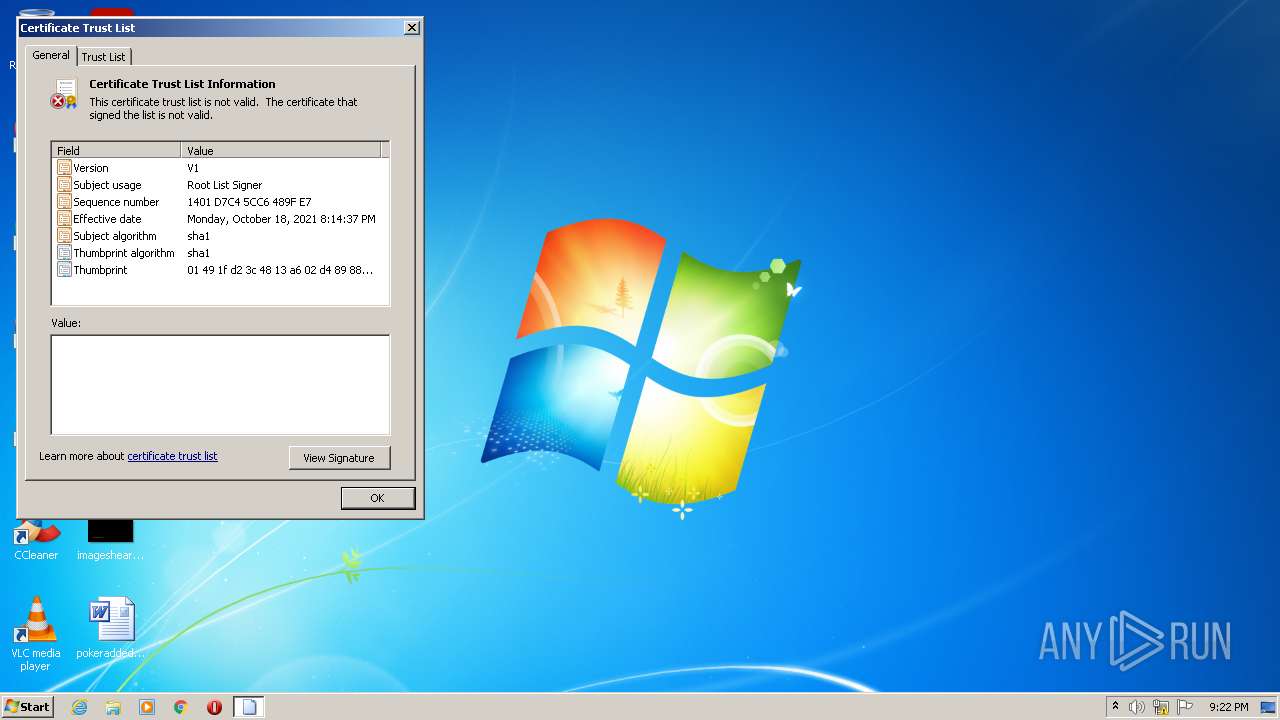
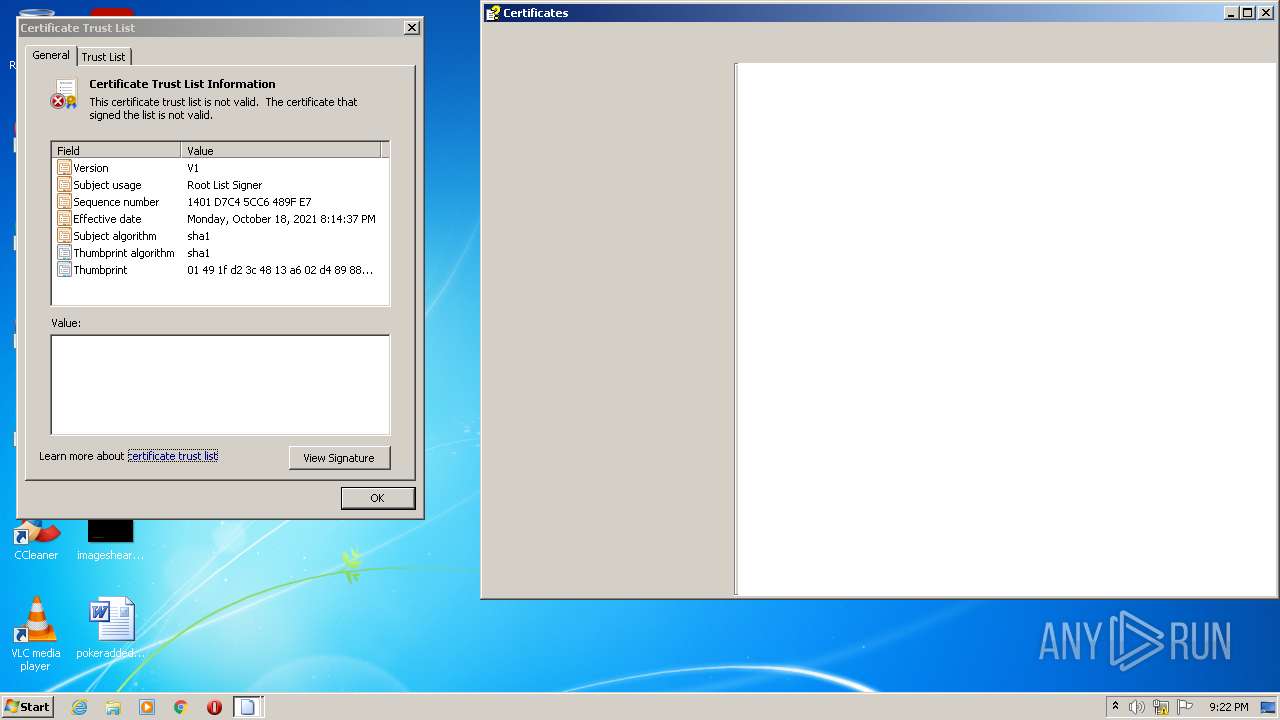
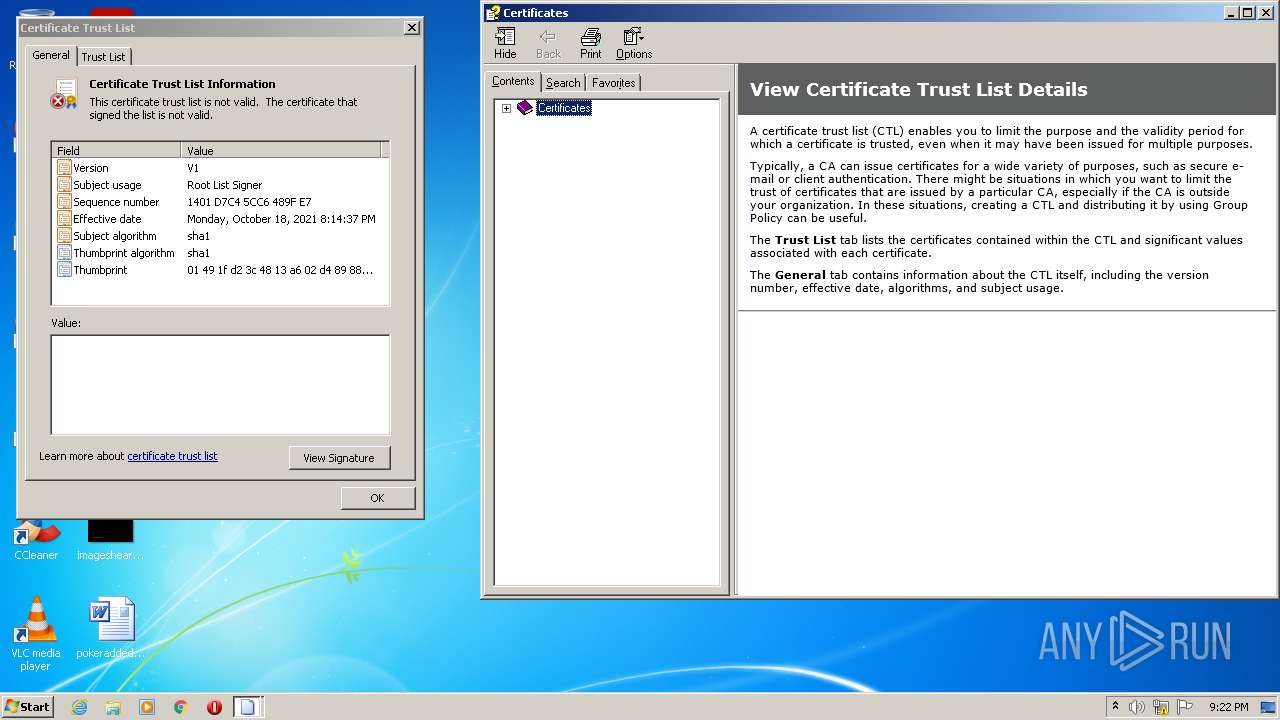
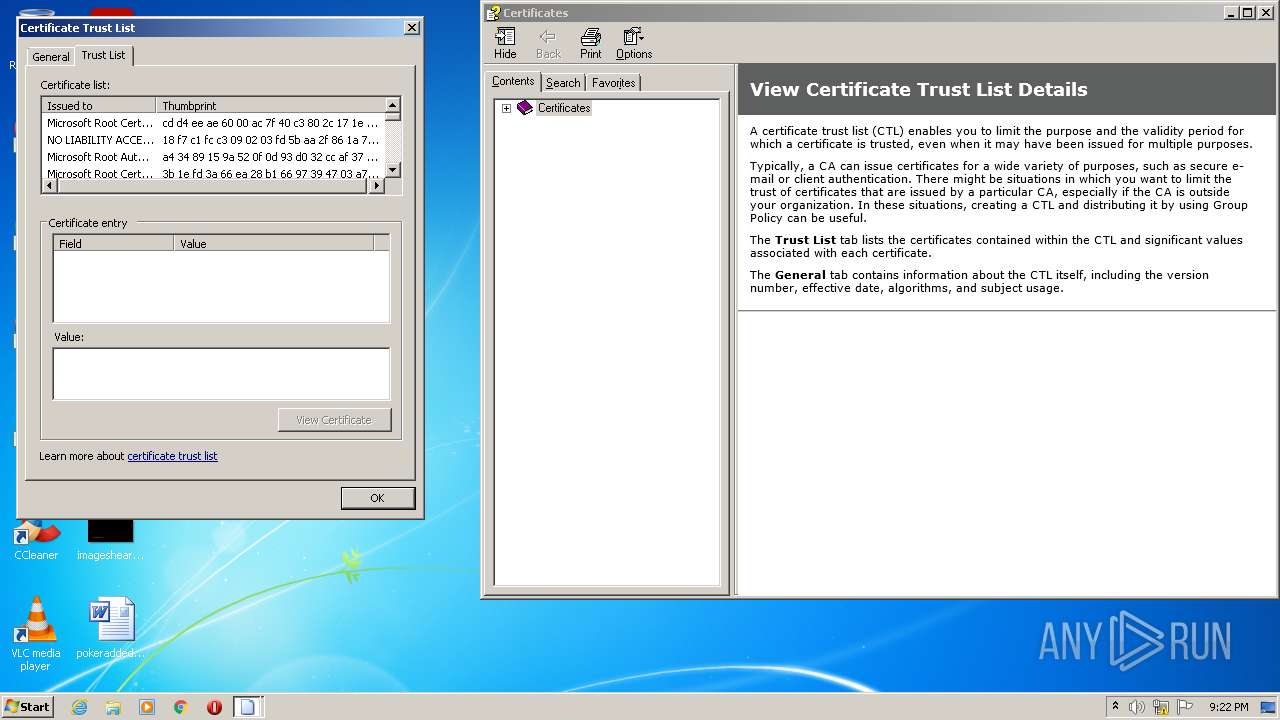
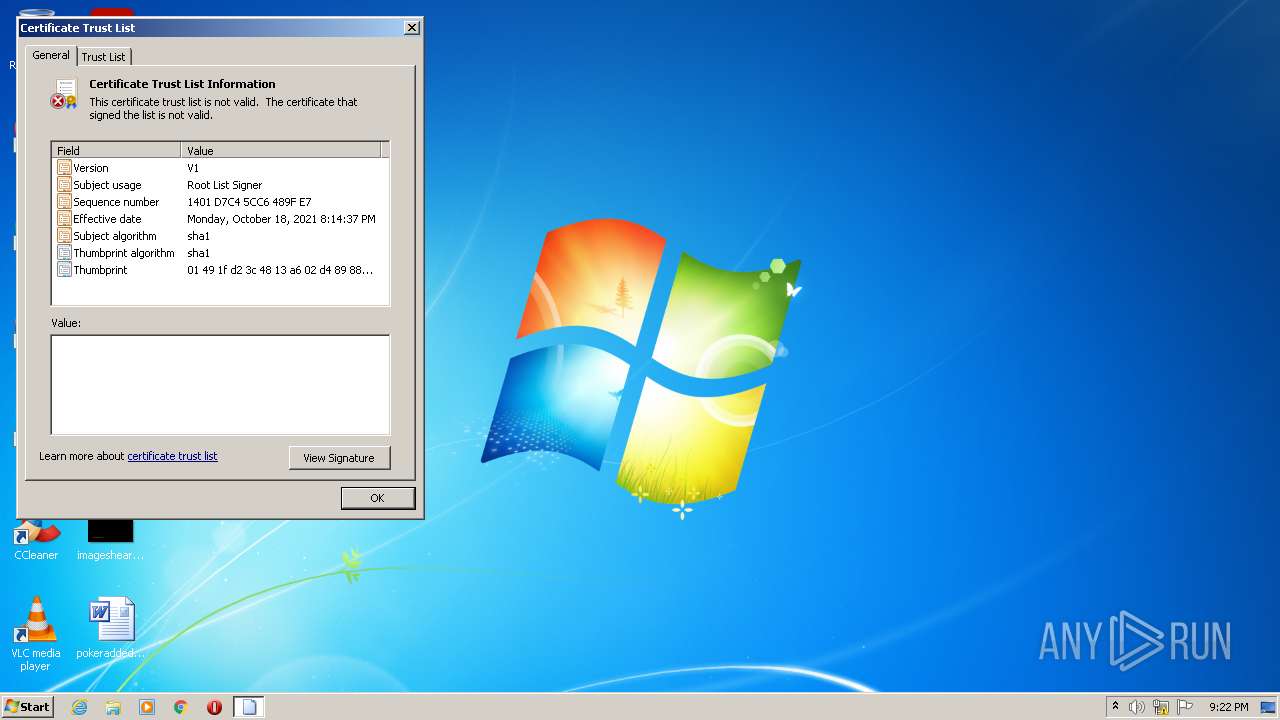
Changes settings of System certificates
- rundll32.exe (PID: 3164)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3136)
Reads the computer name
- WinRAR.exe (PID: 3136)
Reads internet explorer settings
- rundll32.exe (PID: 3164)
Reads Microsoft Outlook installation path
- rundll32.exe (PID: 3164)
INFO
Checks supported languages
- rundll32.exe (PID: 2104)
- rundll32.exe (PID: 2180)
- rundll32.exe (PID: 3164)
Manual execution by user
- rundll32.exe (PID: 2104)
- rundll32.exe (PID: 2180)
- rundll32.exe (PID: 3164)
Reads the computer name
- rundll32.exe (PID: 2180)
- rundll32.exe (PID: 3164)
- rundll32.exe (PID: 2104)
Checks Windows Trust Settings
- rundll32.exe (PID: 3164)
- rundll32.exe (PID: 2180)
- rundll32.exe (PID: 2104)
Reads settings of System Certificates
- rundll32.exe (PID: 2180)
- rundll32.exe (PID: 3164)
- rundll32.exe (PID: 2104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
39
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2104 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtOpenCTL C:\Users\admin\Desktop\authroot.stl | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2180 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtOpenCTL C:\Users\admin\Desktop\authroot.stl | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3136 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Windows\authrootstl.cab" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3164 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtOpenCTL C:\Users\admin\Desktop\authroot.stl | C:\Windows\system32\rundll32.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
14 607
Read events
14 528
Write events
79
Delete events
0
Modification events
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Windows\authrootstl.cab | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3164 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Classic[1].css | text | |
MD5:CC4D7BA649AAA5A35021A14AB523478B | SHA256:A0249F6329ED8FE1AF5FB72A6CABB2C334BFA055EEDA3FB58836FBCBB3CA5FC3 | |||
| 3164 | rundll32.exe | C:\Users\admin\AppData\Roaming\Microsoft\HTML Help\hh.dat | chm | |
MD5:F9B0D56BCA79D8972A32831D1947813E | SHA256:4929907966A33AD7C90CFF30F041906821E976B486CBE16F78EA8840D9E9FDBE | |||
| 3164 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\IMTC659.tmp | binary | |
MD5:5D0E5693027A0E5ADF1D49847779B65C | SHA256:AC0710AABAAEAAC65507050647FA9D97A82639DA0D1D6B436800B177478C6D6B | |||
| 3164 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\~DFCC2E8C4BA8EE51DC.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 3164 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\script[1].js | text | |
MD5:CEF2EA950EA13E14EC6E41984D0DE940 | SHA256:6F921EE8365EC9B65B05E120353B1A598E6C55C56C99F3E2250B1087F30021EA | |||
| 3136 | WinRAR.exe | C:\Users\admin\Desktop\authroot.stl | cat | |
MD5:D99661D0893A52A0700B8AE68457351A | SHA256:BDD5111162A6FA25682E18FA74E37E676D49CAFCB5B7207E98E5256D1EF0D003 | |||
| 3164 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\~DF504EFA3F82F9BE76.TMP | binary | |
MD5:72F5C05B7EA8DD6059BF59F50B22DF33 | SHA256:1DC0C8D7304C177AD0E74D3D2F1002EB773F4B180685A7DF6BBE75CCC24B0164 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3164 | rundll32.exe | GET | 404 | 2.21.143.74:80 | http://www.microsoft.com/pki/certs/MicCerLisCA2011_2011-03-29.crt | unknown | xml | 341 b | whitelisted |
3164 | rundll32.exe | GET | 404 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4fd03cf74ba662d5 | US | xml | 341 b | whitelisted |
3164 | rundll32.exe | GET | 404 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0b4cd4ea205e2f46 | US | xml | 341 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3164 | rundll32.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
— | — | 2.21.143.74:80 | www.microsoft.com | Telia Company AB | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
www.microsoft.com |
| whitelisted |