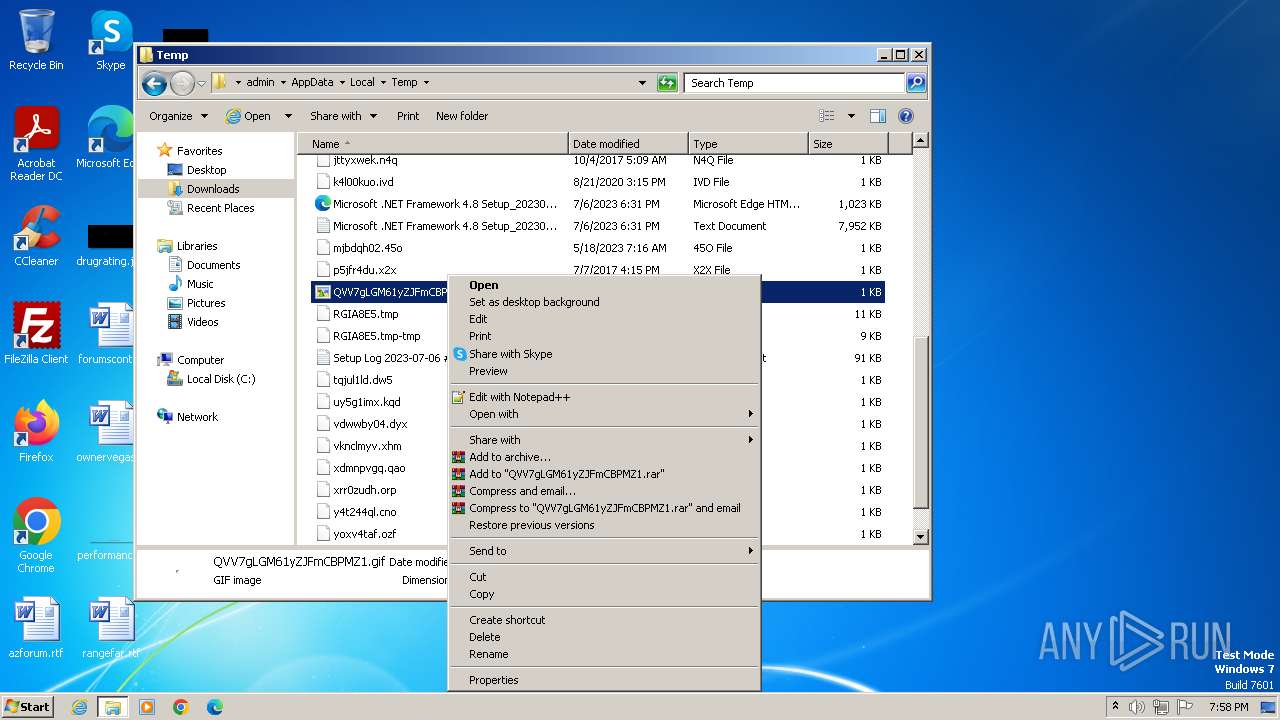
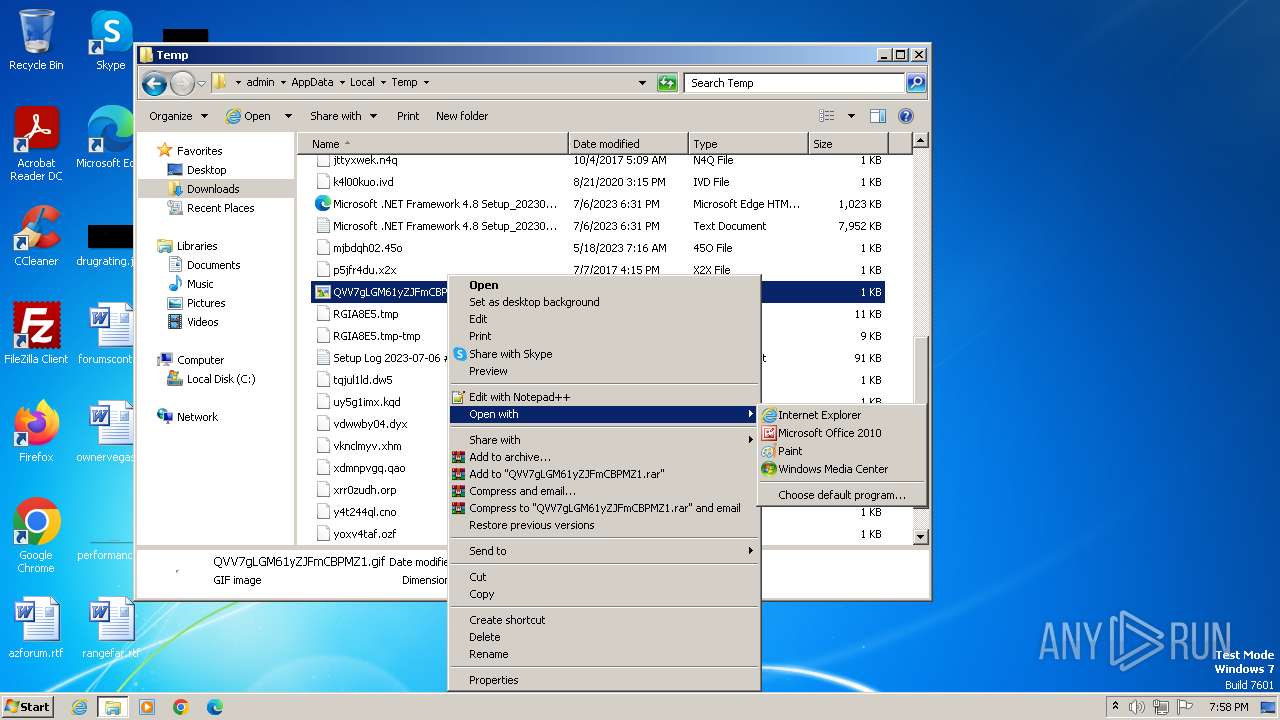
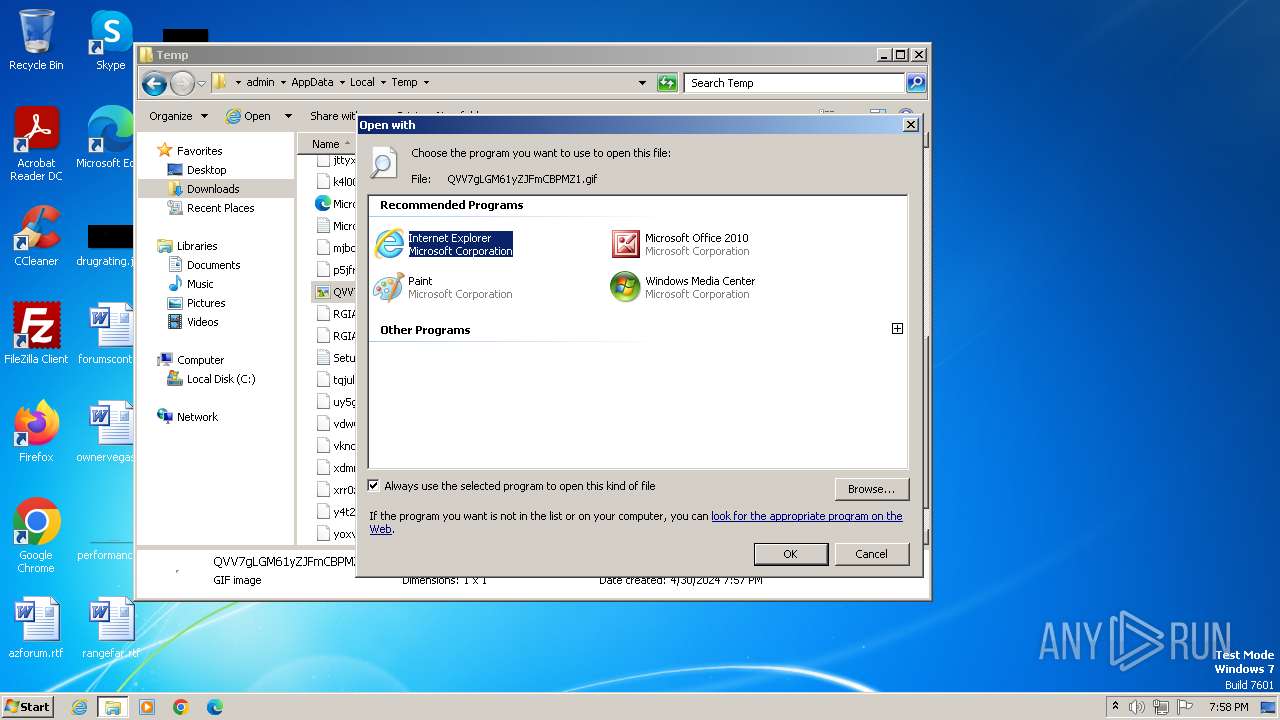
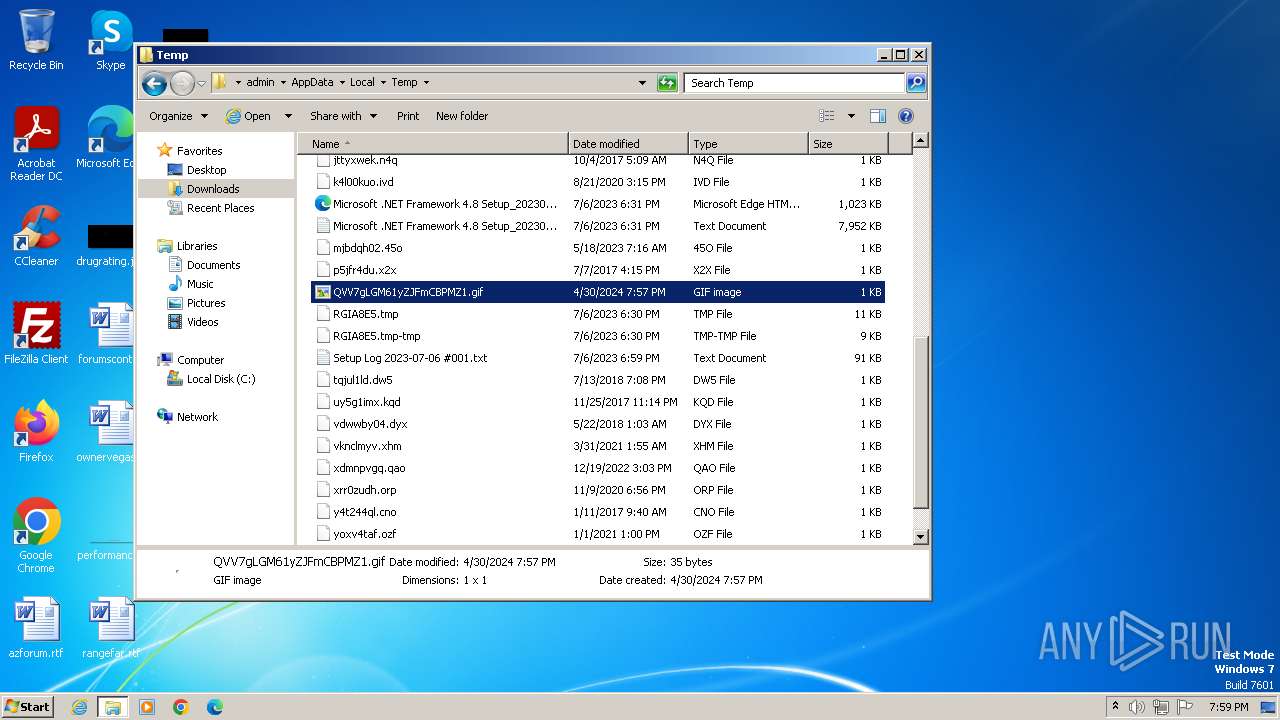
| download: | /tmid_a/QVV7gLGM61yZJFmCBPMZ1 |
| Full analysis: | https://app.any.run/tasks/6476f04b-bd71-4664-883f-b7644adbde85 |
| Verdict: | Malicious activity |
| Analysis date: | April 30, 2024, 18:57:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
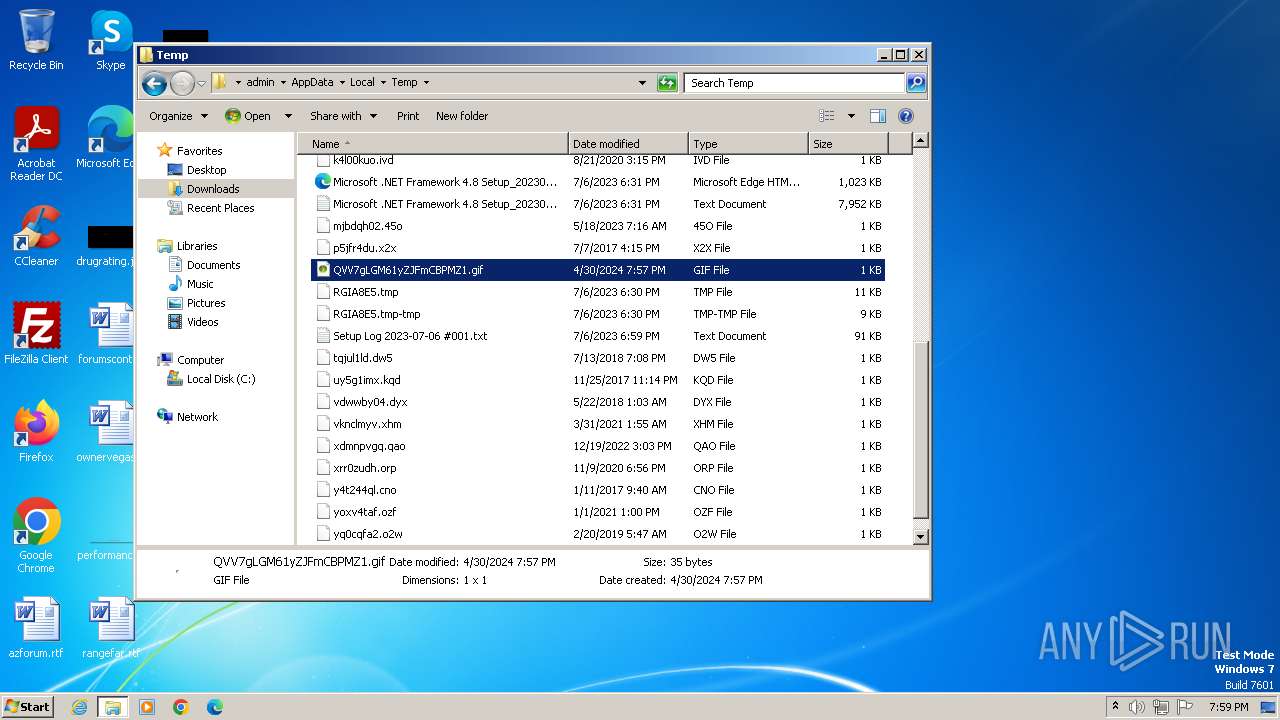
| MIME: | image/gif |
| File info: | GIF image data, version 89a, 1 x 1 |
| MD5: | C2196DE8BA412C60C22AB491AF7B1409 |
| SHA1: | 5FBD472222FEB8A22CF5B8AA5DC5B8E13AF88E2B |
| SHA256: | 6ADC3D4C1056996E4E8B765A62604C78B1F867CCEB3B15D0B9BEDB7C4857F992 |
| SSDEEP: | 3:CUkrllHh/:qJ/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- ehsched.exe (PID: 2860)
Reads the Internet Settings
- wmplayer.exe (PID: 1832)
- wmplayer.exe (PID: 3644)
- setup_wm.exe (PID: 3492)
- unregmp2.exe (PID: 4044)
- wmplayer.exe (PID: 4052)
Reads security settings of Internet Explorer
- wmplayer.exe (PID: 3644)
- setup_wm.exe (PID: 3492)
- wmplayer.exe (PID: 1832)
- wmplayer.exe (PID: 4052)
Detected use of alternative data streams (AltDS)
- wmplayer.exe (PID: 4052)
Reads settings of System Certificates
- unregmp2.exe (PID: 4044)
Executable content was dropped or overwritten
- unregmp2.exe (PID: 4044)
Process drops legitimate windows executable
- unregmp2.exe (PID: 4044)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2504)
- iexplore.exe (PID: 580)
- explorer.exe (PID: 1036)
- rundll32.exe (PID: 2664)
- ehshell.exe (PID: 948)
- ehtray.exe (PID: 3000)
- rundll32.exe (PID: 3564)
Application launched itself
- iexplore.exe (PID: 580)
- iexplore.exe (PID: 2368)
Checks supported languages
- ehshell.exe (PID: 2636)
- wmpnscfg.exe (PID: 2504)
- ehshell.exe (PID: 948)
- wmplayer.exe (PID: 1832)
- ehsched.exe (PID: 2860)
- ehtray.exe (PID: 3000)
- ehrec.exe (PID: 3176)
- wmplayer.exe (PID: 3644)
- setup_wm.exe (PID: 3492)
- wmplayer.exe (PID: 4052)
Reads the computer name
- wmpnscfg.exe (PID: 2504)
- ehshell.exe (PID: 2636)
- ehshell.exe (PID: 948)
- wmplayer.exe (PID: 1832)
- ehtray.exe (PID: 3000)
- ehsched.exe (PID: 2860)
- ehrec.exe (PID: 3176)
- setup_wm.exe (PID: 3492)
- wmplayer.exe (PID: 3644)
- wmplayer.exe (PID: 4052)
Process checks computer location settings
- ehshell.exe (PID: 2636)
- setup_wm.exe (PID: 3492)
- wmplayer.exe (PID: 1832)
- wmplayer.exe (PID: 4052)
Reads the machine GUID from the registry
- ehshell.exe (PID: 2636)
- ehshell.exe (PID: 948)
- wmplayer.exe (PID: 1832)
- ehsched.exe (PID: 2860)
- ehtray.exe (PID: 3000)
- ehrec.exe (PID: 3176)
- setup_wm.exe (PID: 3492)
- wmplayer.exe (PID: 4052)
Creates files or folders in the user directory
- ehshell.exe (PID: 2636)
- wmplayer.exe (PID: 1832)
- wmplayer.exe (PID: 4052)
Creates files in the program directory
- ehshell.exe (PID: 2636)
- ehsched.exe (PID: 2860)
- unregmp2.exe (PID: 4044)
Reads Environment values
- wmplayer.exe (PID: 1832)
- ehshell.exe (PID: 2636)
- setup_wm.exe (PID: 3492)
- wmplayer.exe (PID: 4052)
Checks proxy server information
- wmplayer.exe (PID: 1832)
- setup_wm.exe (PID: 3492)
- wmplayer.exe (PID: 4052)
Create files in a temporary directory
- setup_wm.exe (PID: 3492)
- wmplayer.exe (PID: 4052)
- unregmp2.exe (PID: 4044)
Drops the executable file immediately after the start
- unregmp2.exe (PID: 4044)
Reads the software policy settings
- unregmp2.exe (PID: 4044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .gif | | | GIF89a bitmap (60) |
|---|---|---|
| .gif | | | GIF bitmap (generic) (30) |
| .bs/bin | | | PrintFox (C64) bitmap (10) |
EXIF
GIF
| GIFVersion: | 89a |
|---|---|
| ImageWidth: | 1 |
| ImageHeight: | 1 |
| HasColorMap: | Yes |
| ColorResolutionDepth: | 1 |
| BitsPerPixel: | 1 |
| BackgroundColor: | - |
Composite
| ImageSize: | 1x1 |
|---|---|
| Megapixels: | 0.000001 |
Total processes
61
Monitored processes
19
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 580 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\QVV7gLGM61yZJFmCBPMZ1.gif | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 948 | "C:\Windows\eHome\ehshell.exe" "C:\Users\admin\AppData\Local\Temp\QVV7gLGM61yZJFmCBPMZ1.gif" | C:\Windows\ehome\ehshell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Windows Media Player\wmplayer.exe" /SkipFUE /RemoteOCXLaunch /SuppressDialogs | C:\Program Files\Windows Media Player\wmplayer.exe | ehshell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.7601.23517 (win7sp1_ldr.160812-0732) Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:580 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2524 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:580 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2636 | "C:\Windows\eHome\ehshell.exe" "C:\Users\admin\AppData\Local\Temp\QVV7gLGM61yZJFmCBPMZ1.gif" | C:\Windows\ehome\ehshell.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2664 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\QVV7gLGM61yZJFmCBPMZ1.gif | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2860 | C:\Windows\ehome\ehsched.exe | C:\Windows\ehome\ehsched.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Scheduler Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
45 763
Read events
44 521
Write events
1 090
Delete events
152
Modification events
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: rundll32.exe | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Slideshow |
| Operation: | write | Name: | Shuffle |
Value: 0 | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Slideshow |
| Operation: | write | Name: | Loop |
Value: 1 | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Slideshow |
| Operation: | write | Name: | Mute |
Value: 0 | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Slideshow |
| Operation: | write | Name: | Speed |
Value: 1 | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000034000000A00400008002000000000000 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31103792 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
Executable files
1
Suspicious files
20
Text files
40
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{A6FF7ABF-0723-11EF-9E36-12A9866C77DE}.dat | binary | |
MD5:69124D5485AEBD8AAF241F05C3B76F4D | SHA256:81B32435D7AF7EE47A50BD3D623C52E6D00F3F738DE41B4B6C26615719903C5D | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:48E7D35E092E87A10F297087107246CF | SHA256:015CB4E889C2332DC0EE2DEBCACD128AA4ECC5D1CF6E768D86A2225C58649850 | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:C6D114C1CFD5270A45C7E187E06263BA | SHA256:E40B26AC2682A33E4483D304203BB0E88428146E29D508C8E17643B4D0DB3230 | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:A30BDF19821A44DA995446C4EAFB7DB8 | SHA256:EC08B7C551456BE4D80C826FF08E7D7D88634F4CBFB9D2B6ADCAA0B41E456F18 | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{A6FF7AC0-0723-11EF-9E36-12A9866C77DE}.dat | binary | |
MD5:62CEE56E44D3DC3772320EDDF75CE45E | SHA256:593DCE56080B00DD34DD19F6C522A6B387D32AE8DCBD8CADDEB893E37B04B1F9 | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:796883E29D785DD87F72CB8E666F17E8 | SHA256:1EF825CC9409C21BF8511973A738A43391F1E2D222BA1054CB3F888ED698C27E | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF26F064CE5442DAF8.TMP | gmc | |
MD5:35CE4D583CF8D35BF385BABA8D15080E | SHA256:7C4CC58E4B20E2C5612A713258B3D561ADC79F99552EE0EF5B31B4026374CCA1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
28
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
580 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ad60d6d0de85f697 | unknown | — | — | unknown |
580 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c9646b9ecb5ec723 | unknown | — | — | unknown |
1832 | wmplayer.exe | GET | 302 | 23.53.35.48:80 | http://redir.metaservices.microsoft.com/redir/allservices/?sv=5&locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | unknown | — | — | unknown |
580 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
580 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
1832 | wmplayer.exe | GET | 200 | 23.53.35.44:80 | http://onlinestores.metaservices.microsoft.com/serviceswitching/AllServices.aspx?sv=5&locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | unknown | — | — | unknown |
1832 | wmplayer.exe | GET | 200 | 23.53.35.44:80 | http://onlinestores.metaservices.microsoft.com/bing/bing.xml?locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | unknown | — | — | unknown |
1832 | wmplayer.exe | GET | 200 | 23.53.35.38:80 | http://images.windowsmedia.com/svcswitch/mg4_wmp12_30x30_2.png | unknown | — | — | unknown |
1832 | wmplayer.exe | GET | 200 | 23.53.35.38:80 | http://images.windowsmedia.com/svcswitch/media_guide_16x16.png | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1a460631b50eba60 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
580 | iexplore.exe | 23.48.203.76:443 | www.bing.com | Akamai Technologies Tokyo ASN | US | unknown |
580 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
580 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
580 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
2892 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
1832 | wmplayer.exe | 23.53.35.48:80 | redir.metaservices.microsoft.com | Akamai International B.V. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
redir.metaservices.microsoft.com |
| whitelisted |
onlinestores.metaservices.microsoft.com |
| whitelisted |
images.windowsmedia.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4052 | wmplayer.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
Process | Message |
|---|---|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|