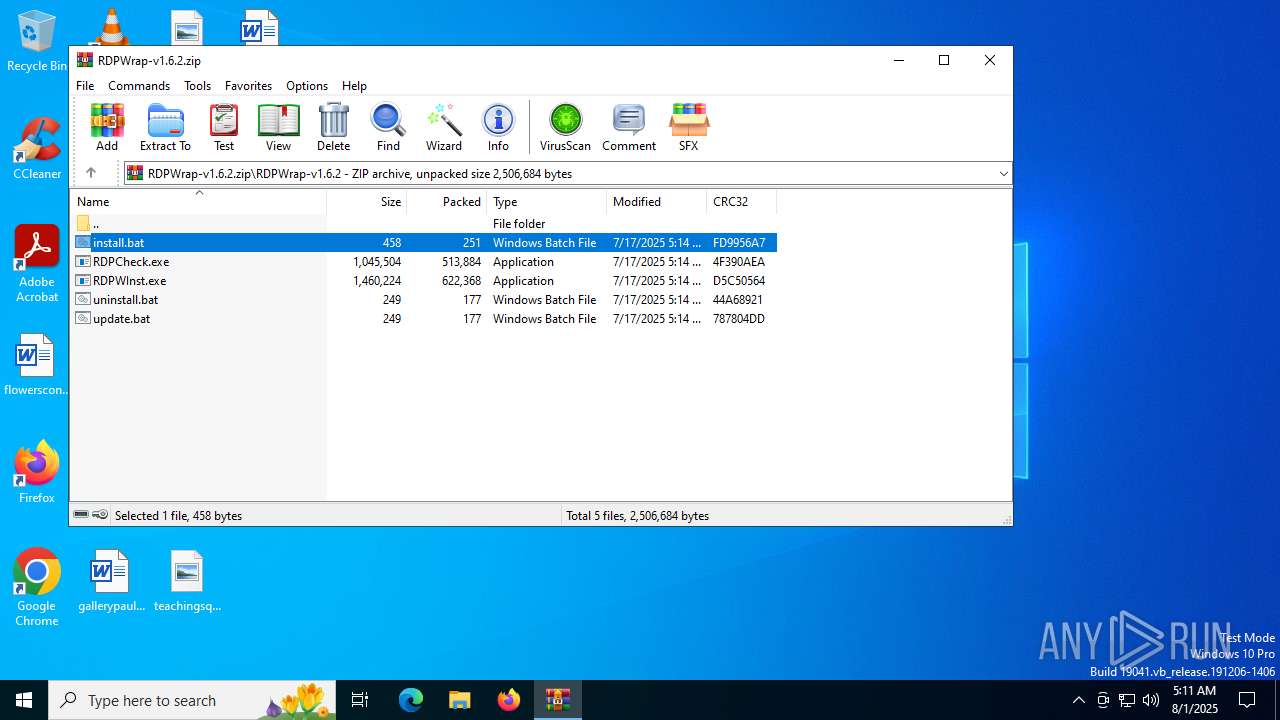
| File name: | RDPWrap-v1.6.2.zip |
| Full analysis: | https://app.any.run/tasks/1317bd0a-121f-4507-94ce-21bfa9d36c88 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 05:11:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | D4310F2E4D207E79B57D290FE57C96F8 |
| SHA1: | 0FA03467F9155B7291412D24A2D8876E9130DED4 |
| SHA256: | 6AC4F536FABA96FE94C3F08A948D81F27A16A7A11B7CF79E35A910AD49DB3114 |
| SSDEEP: | 49152:Udk1ItzWcN+eM0rBmnC09/L4d99t6N318ZfCOEVLmalFNuJRyb5Sp198ZZw359EH:UmitqC+eMABq9/Lct6N3iFCvZmgQUMly |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 2972)
Generic archive extractor
- WinRAR.exe (PID: 2972)
Changes the autorun value in the registry
- CCleaner64.exe (PID: 5352)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2972)
- CCleaner64.exe (PID: 3392)
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
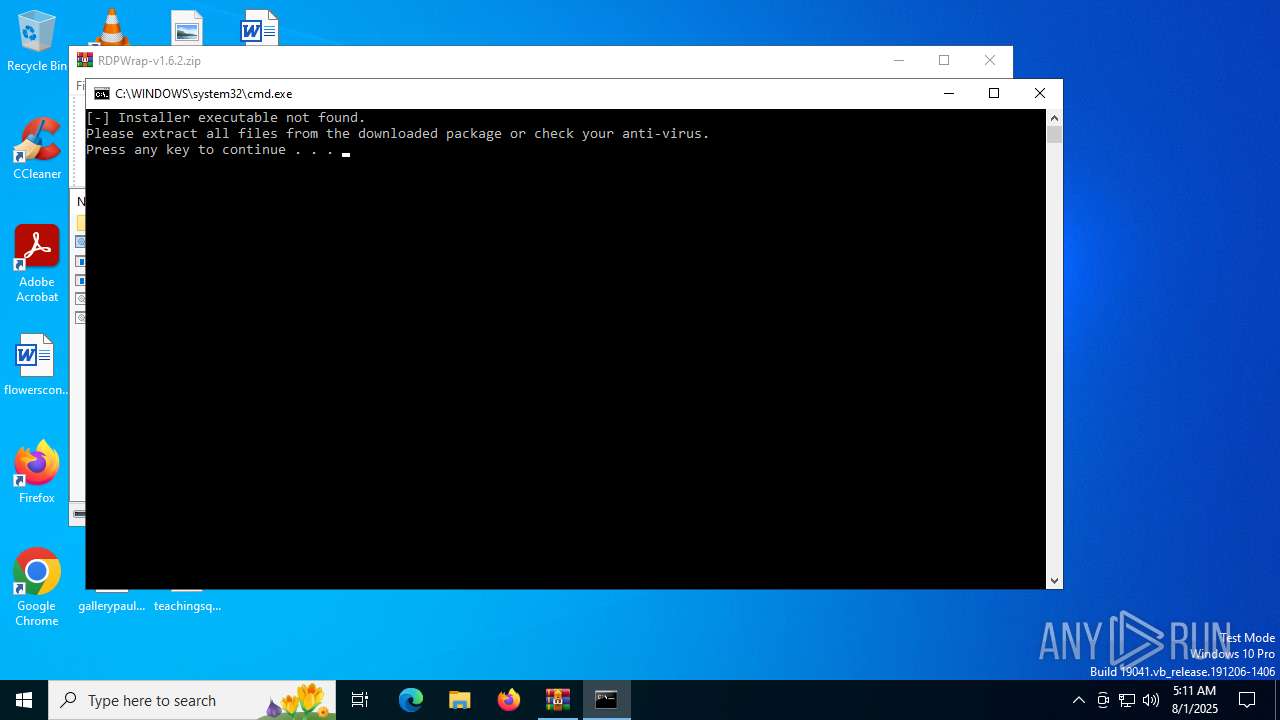
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2972)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2972)
Reads the date of Windows installation
- CCleaner64.exe (PID: 3392)
- CCleaner64.exe (PID: 5724)
Application launched itself
- CCleaner64.exe (PID: 3392)
- CCleaner64.exe (PID: 5724)
Executable content was dropped or overwritten
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
Reads Internet Explorer settings
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
Searches for installed software
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
The process verifies whether the antivirus software is installed
- CCleaner64.exe (PID: 5352)
- CCleaner64.exe (PID: 5724)
INFO
Checks supported languages
- CCleaner64.exe (PID: 3392)
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
Reads Environment values
- CCleaner64.exe (PID: 3392)
- CCleaner64.exe (PID: 5352)
- CCleaner64.exe (PID: 5724)
Reads the computer name
- CCleaner64.exe (PID: 3392)
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
Process checks computer location settings
- CCleaner64.exe (PID: 3392)
- CCleaner64.exe (PID: 5724)
Manual execution by a user
- CCleaner64.exe (PID: 3392)
- mspaint.exe (PID: 6620)
Reads the machine GUID from the registry
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
The sample compiled with english language support
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
Checks proxy server information
- CCleaner64.exe (PID: 5724)
Creates files or folders in the user directory
- CCleaner64.exe (PID: 5724)
Reads CPU info
- CCleaner64.exe (PID: 5352)
- CCleaner64.exe (PID: 5724)
Reads the software policy settings
- CCleaner64.exe (PID: 5724)
- CCleaner64.exe (PID: 5352)
Launching a file from a Registry key
- CCleaner64.exe (PID: 5352)
Reads product name
- CCleaner64.exe (PID: 5352)
- CCleaner64.exe (PID: 5724)
Creates files in the program directory
- CCleaner64.exe (PID: 5352)
- CCleaner64.exe (PID: 5724)
Create files in a temporary directory
- mspaint.exe (PID: 6620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:08:01 01:05:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | RDPWrap-v1.6.2/ |
Total processes
146
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1588 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2972 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\RDPWrap-v1.6.2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3392 | "C:\Program Files\CCleaner\CCleaner64.exe" | C:\Program Files\CCleaner\CCleaner64.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 4520 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5352 | "C:\Program Files\CCleaner\CCleaner64.exe" /monitor | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Version: 6.20.0.10897 Modules
| |||||||||||||||
| 5724 | "C:\Program Files\CCleaner\CCleaner64.exe" /uac | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 6240 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa2972.40681\install.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6620 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Downloads\lasking.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 923
Read events
26 701
Write events
162
Delete events
60
Modification events
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RDPWrap-v1.6.2.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
4
Suspicious files
9
Text files
11
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5724 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:802931C43120602F493E7FDB14022F09 | SHA256:FE9297B7BDC3E1654059ECA3D33C761399A149091E951391AB4C4FEE224C3645 | |||
| 5724 | CCleaner64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\ccupdate638_free[1].exe | — | |
MD5:— | SHA256:— | |||
| 5724 | CCleaner64.exe | C:\Program Files\CCleaner\temp_ccupdate\ccupdate638_free.exe | — | |
MD5:— | SHA256:— | |||
| 5724 | CCleaner64.exe | C:\Program Files\CCleaner\gcapi_17540251535724.dll | executable | |
MD5:F17F96322F8741FE86699963A1812897 | SHA256:8B6CE3A640E2D6F36B0001BE2A1ABB765AE51E62C314A15911E75138CBB544BB | |||
| 5724 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | der | |
MD5:C22301B5245B697AA0D960E7D3A2D560 | SHA256:8E63BB9D833DDFF90DB225799A6B20821540B2A10AB3764EE07767259765DA0E | |||
| 5724 | CCleaner64.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ccc0fa1b9f86f7b3.customDestinations-ms | binary | |
MD5:A0BCE1B5E09E3CA2D6B20D28405FEA14 | SHA256:088340570FE6FF79E6835F98174ED1620DC51C7A5650A9173711D0263963AF86 | |||
| 5724 | CCleaner64.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ENTL3F10RSZ9HYHR2SCA.temp | binary | |
MD5:A0BCE1B5E09E3CA2D6B20D28405FEA14 | SHA256:088340570FE6FF79E6835F98174ED1620DC51C7A5650A9173711D0263963AF86 | |||
| 5724 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:2DFD9F80E1934838044D256EB17AC360 | SHA256:6E63E498856647376412A123F397906DDA7014A1C68A9369B1466721281199A4 | |||
| 5724 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:014CAFD36E30490E6A9721E92CC83FC4 | SHA256:7C9184C147DEAC91A73EFFD6EFBB769336841E1B3DE1C1F65DEEC21735133C50 | |||
| 5724 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E573CDF4C6D731D56A665145182FD759_AFB3BE9383420FBAFF24AD413EEA555E | der | |
MD5:30C0A26840E4A055314C21765D65CD24 | SHA256:E68360BF8D836C30A664A532CA446153E882FD7BA60EC7EEE37CC75D98085399 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
33
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3556 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3540 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3556 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5724 | CCleaner64.exe | GET | 200 | 23.48.23.10:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
5724 | CCleaner64.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
5724 | CCleaner64.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
5724 | CCleaner64.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAXfj0A2M0oL7zuU%2F%2F2jetU%3D | unknown | — | — | whitelisted |
5724 | CCleaner64.exe | GET | 200 | 216.58.206.67:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7064 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.3.109.244:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3540 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CCleaner64.exe | [2025-08-01 05:12:33.283] [error ] [ini_access ] [ 5724: 4060] [000000: 0] Incorrect ini_accessor configuration! Fixing relative input path to avoid recursion. Input was: Setup
|
CCleaner64.exe | [2025-08-01 05:12:33.283] [error ] [settings ] [ 5724: 4060] [000000: 0] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner64.exe | OnLanguage - en
|
CCleaner64.exe | [2025-08-01 05:12:33.752] [error ] [settings ] [ 5724: 1712] [D2EC45: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2025-08-01 05:12:33.767] [error ] [Burger ] [ 5724: 1712] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | [2025-08-01 05:12:33.767] [error ] [Burger ] [ 5724: 1712] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | file:///tis/optimizer.tis(1288) : warning :'async' does not contain any 'await'
|
CCleaner64.exe | file:///tis/optimizer.tis(1131) : warning :'await' should be used only inside 'async' or 'event'
|
CCleaner64.exe | OnLanguage - en
|