| download: | Diagnostic_v2.0.4.2_AllInOne_20190502_V3.zip |
| Full analysis: | https://app.any.run/tasks/b17e1bf6-6f49-4226-a4b2-6b40f180cea3 |
| Verdict: | Malicious activity |
| Analysis date: | October 06, 2019, 16:52:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 82BEC4DCEE57D76DFEFDF1F2DB124465 |
| SHA1: | 1656FCD0DEAF0AA0C524FA6B2955F122B3AC56CD |
| SHA256: | 6AADF4A004FE39F9CD390519D74A944929E67B44E4BAE662FA599BF00DBA57C0 |
| SSDEEP: | 393216:kwMgD8He2Ga0dmkH2lwyorTrTDnZh5+msYmngf8Qx7jouSm2vLyDDnEM8aGO4EpS:tMgD8He2GndmkH2lwyYTrTDnZ/+msYm1 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1844)
- setup.exe (PID: 3268)
- 8169DiagV2.exe (PID: 1376)
Application was dropped or rewritten from another process
- setup.exe (PID: 912)
- setup.exe (PID: 3268)
- OEMINF.EXE (PID: 2908)
- DEVCON.EXE (PID: 4040)
- DEVCON.EXE (PID: 3100)
- DEVCON.EXE (PID: 2096)
- DEVCON.EXE (PID: 2844)
- 8169DiagV2.exe (PID: 1376)
- rtkbind.exe (PID: 2000)
- rtkbind.exe (PID: 3776)
- rtkbind.exe (PID: 2024)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3620)
- setup.exe (PID: 3268)
- DrvInst.exe (PID: 1536)
- rtkbind.exe (PID: 2000)
- rtkbind.exe (PID: 3776)
- DrvInst.exe (PID: 1420)
- rtkbind.exe (PID: 2024)
Executed as Windows Service
- vssvc.exe (PID: 3340)
Searches for installed software
- setup.exe (PID: 3268)
Executed via COM
- DrvInst.exe (PID: 2940)
- DrvInst.exe (PID: 1536)
- DrvInst.exe (PID: 2796)
- DrvInst.exe (PID: 1420)
- DrvInst.exe (PID: 3232)
- DrvInst.exe (PID: 2952)
Creates files in the program directory
- OEMINF.EXE (PID: 2908)
- 8169DiagV2.exe (PID: 1376)
- setup.exe (PID: 3268)
Creates files in the Windows directory
- rtkbind.exe (PID: 2000)
- DrvInst.exe (PID: 1536)
- DrvInst.exe (PID: 2952)
- rtkbind.exe (PID: 3776)
- DrvInst.exe (PID: 1420)
- DrvInst.exe (PID: 2796)
- DrvInst.exe (PID: 3232)
- rtkbind.exe (PID: 2024)
Removes files from Windows directory
- DrvInst.exe (PID: 1536)
- rtkbind.exe (PID: 2000)
- DrvInst.exe (PID: 2796)
- DrvInst.exe (PID: 2952)
- rtkbind.exe (PID: 3776)
- DrvInst.exe (PID: 1420)
- DrvInst.exe (PID: 3232)
- rtkbind.exe (PID: 2024)
Creates files in the driver directory
- DrvInst.exe (PID: 1536)
- rtkbind.exe (PID: 2000)
- DrvInst.exe (PID: 2952)
- rtkbind.exe (PID: 3776)
- DrvInst.exe (PID: 1420)
- DrvInst.exe (PID: 2796)
- rtkbind.exe (PID: 2024)
- DrvInst.exe (PID: 3232)
Creates a software uninstall entry
- setup.exe (PID: 3268)
INFO
Manual execution by user
- setup.exe (PID: 912)
- setup.exe (PID: 3268)
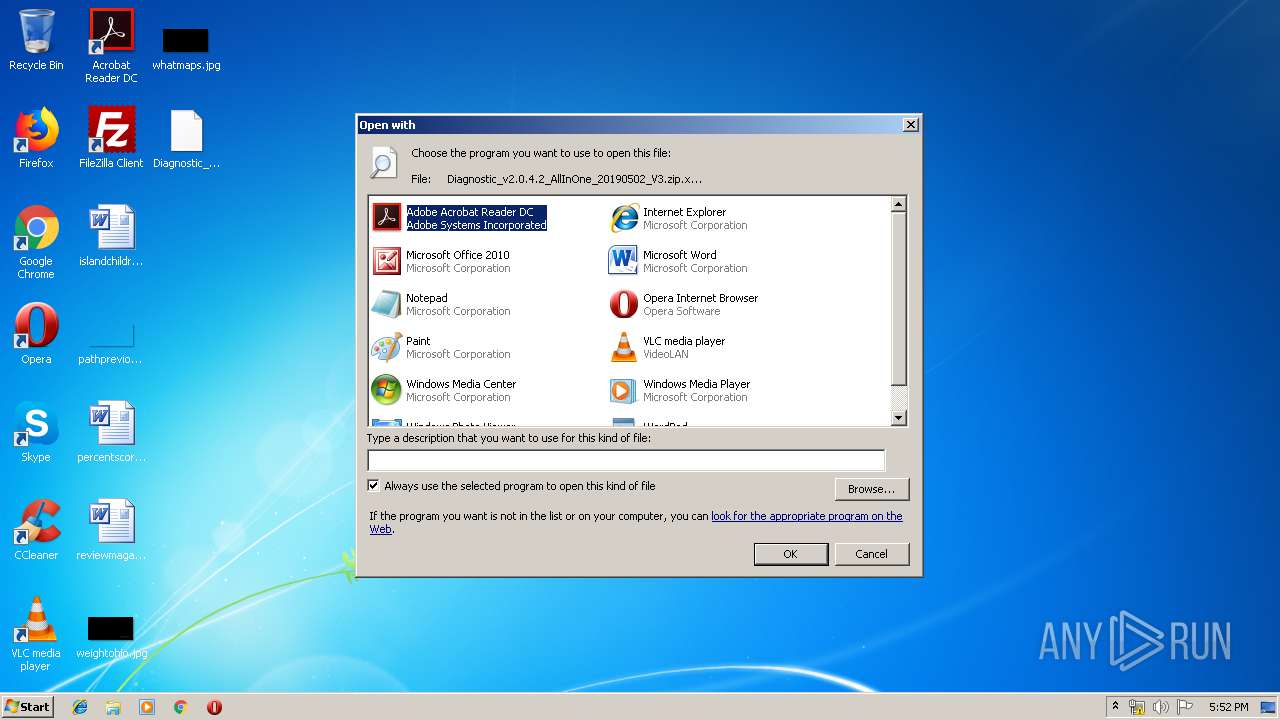
Modifies the open verb of a shell class
- rundll32.exe (PID: 1496)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (44.4) |
|---|---|---|
| .kmz | | | Google Earth saved working session (33.3) |
| .zip | | | ZIP compressed archive (22.2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:05:29 11:25:26 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release/ |
Total processes
63
Monitored processes
21
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 912 | "C:\Users\admin\Desktop\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\setup.exe" | C:\Users\admin\Desktop\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Realtek Integrity Level: MEDIUM Description: InstallScript Setup Launcher Unicode Exit code: 3221226540 Version: 2.0.4.2 Modules
| |||||||||||||||
| 1376 | "C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\8169DiagV2.exe" | C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\8169DiagV2.exe | — | setup.exe | |||||||||||
User: admin Company: Realtek Semiconductor Corporation. Integrity Level: HIGH Description: Realtek NIC Diagnostic Utility Exit code: 0 Version: 2, 0, 4, 2 Modules
| |||||||||||||||
| 1420 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{6dc51620-613d-5cc6-1eb8-7c25bd23ce33}\rtteampt.inf" "0" "646b10b97" "000004DC" "WinSta0\Default" "000004B0" "208" "C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\rtteampt\win7" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
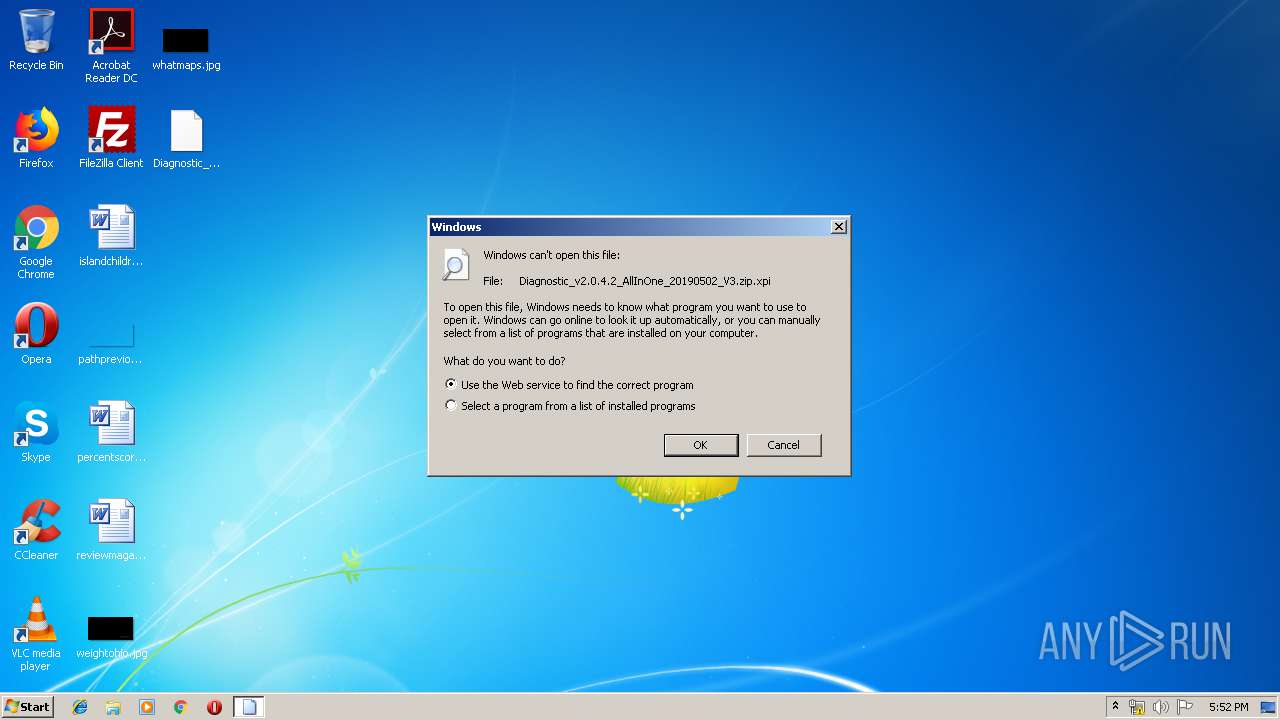
| 1496 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Diagnostic_v2.0.4.2_AllInOne_20190502_V3.zip.xpi | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1536 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{32bcaead-1ba9-17c0-59a6-3a541c06230f}\rtndpt60.inf" "0" "654eb810f" "000004B0" "WinSta0\Default" "00000270" "208" "C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\protdrv\win7" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1844 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2000 | rtkbind.exe /i /f PROTDRV\WIN7\RtNdPt60.inf /p RTK_RtNdPt60 | C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\rtkbind.exe | 8169DiagV2.exe | ||||||||||||
User: admin Company: Realtek Semiconductor Corp. Integrity Level: HIGH Description: RtkBind Application Exit code: 0 Version: 1, 0, 0, 9 Modules
| |||||||||||||||
| 2024 | rtkbind.exe /i /f RtTeamPt\WIN7\RtTeamPt.inf /p RTK_TEAMPT | C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\rtkbind.exe | 8169DiagV2.exe | ||||||||||||
User: admin Company: Realtek Semiconductor Corp. Integrity Level: HIGH Description: RtkBind Application Exit code: 0 Version: 1, 0, 0, 9 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\DEVCON.EXE" remove RTK_VLANMP | C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\DEVCON.EXE | — | OEMINF.EXE | |||||||||||
User: admin Company: Windows (R) Codename Longhorn DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.0.6000.16386 built by: WinDDK Modules
| |||||||||||||||
| 2796 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{4ebf730f-f0a8-4616-fc5f-255c542c7849}\rtvlanpt.inf" "0" "6abd3168b" "00000270" "WinSta0\Default" "000005BC" "208" "C:\Program Files\Realtek\Realtek Ethernet Diagnostic Utility\rtvlanpt\win7" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 754
Read events
2 036
Write events
684
Delete events
34
Modification events
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000070000000200000009000000080000000000000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000040000000200000003000000FFFFFFFF | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\35\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\1 |
| Operation: | write | Name: | 5 |
Value: 50003100000000001C4D655F100057696E52415200003A0008000400EFBE1C4DBC5E1C4D655F2A0000000AC1000000000C000000000000000000000000000000570069006E00520041005200000016000000 | |||
| (PID) Process: | (1496) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\1 |
| Operation: | write | Name: | MRUListEx |
Value: 050000000400000003000000010000000000000002000000FFFFFFFF | |||
Executable files
64
Suspicious files
101
Text files
259
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x0404.ini | text | |
MD5:EC1F8F71FA21C49BC96A17C81AD51598 | SHA256:60F176F3014342F48468FF7EA67280FA3A671C4721EBEFE7B4EE789FF65C87DF | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x0405.ini | text | |
MD5:9FB56981DD06830B30CD9CADF54270D6 | SHA256:9302A3E694DE8CC84947B41350A7F8AE0880E5D2F3FDBD67CD56444BF0BC3A43 | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x040b.ini | text | |
MD5:48DD00B7D72FB37F937DB5714BF8A725 | SHA256:AA0097E47CAA4933793155E45FC91EEF6B035DAAF22F9EA32EB509CC4811DD5C | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x040a.ini | text | |
MD5:E872C54C58EEF055BC791D3EEAD093C3 | SHA256:1739D42ED181F36AB4F524C01B57A4102C2F7510661D973A1077A4E88AC34B97 | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x0406.ini | text | |
MD5:7C6AD5705B8C076697C1CA0EB6229F6F | SHA256:FAD1187DF234B8B2B27C3F866B218036E377469871E0816FA6CC38C391D5AD93 | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x0407.ini | text | |
MD5:9A62DA6C523506355C1BF1B30DB73EDD | SHA256:8B5D7BC395D0D6980299702D0573C6019FEFEA92EB98701D1894A5623B2691A0 | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x0409.ini | text | |
MD5:BE345D0260AE12C5F2F337B17E07C217 | SHA256:E994689A13B9448C074F9B471EDEEC9B524890A0D82925E98AB90B658016D8F3 | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x040c.ini | text | |
MD5:35989450C8121207917F04D1EBE4CA2A | SHA256:B14D9D7AFC505868407C425CB5A78C891BAA8A6AC8EB35CFB3D71C71F5BEE1FA | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x040e.ini | text | |
MD5:A143F6D5AC3832B025C9D04855A790FD | SHA256:6A0F69C2918A51E38907A2501DA4169DA506D461031576A39F3D6D33C53F976C | |||
| 3620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3620.31221\Diagnostic_v2.0.4.2_AllInOne_20190502_latest_V3_for_release\0x0403.ini | text | |
MD5:04B3D8BE6E6F17F13A3BE3F24E3AC1B0 | SHA256:BAD754F1F64BC40D1AA6D037179C4DEDB41E9237D3B5E05BFFF4F92ECF623E02 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report