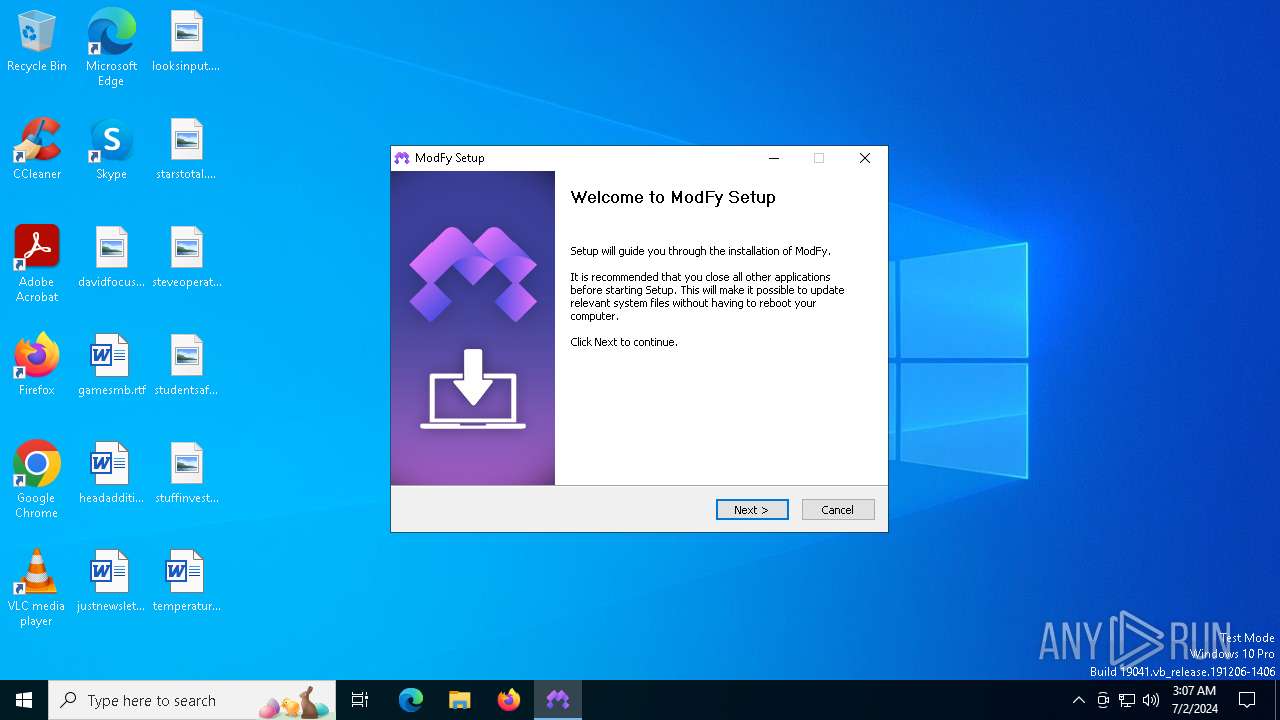
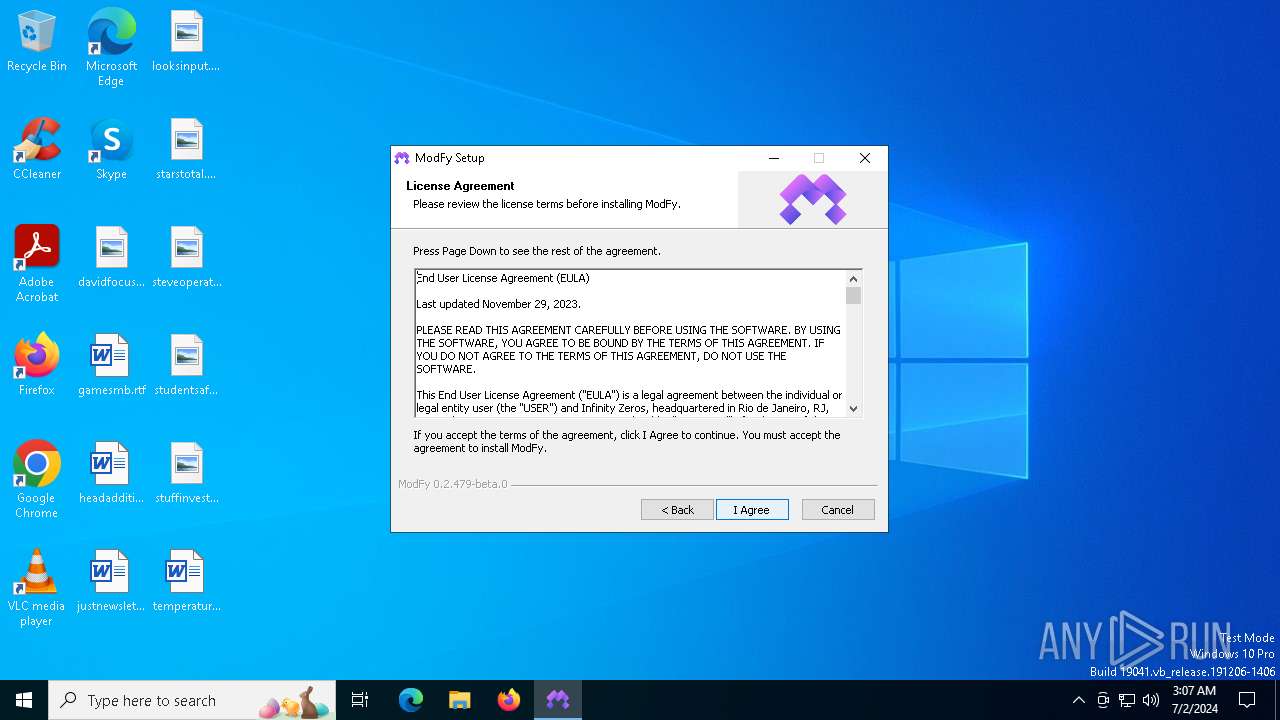
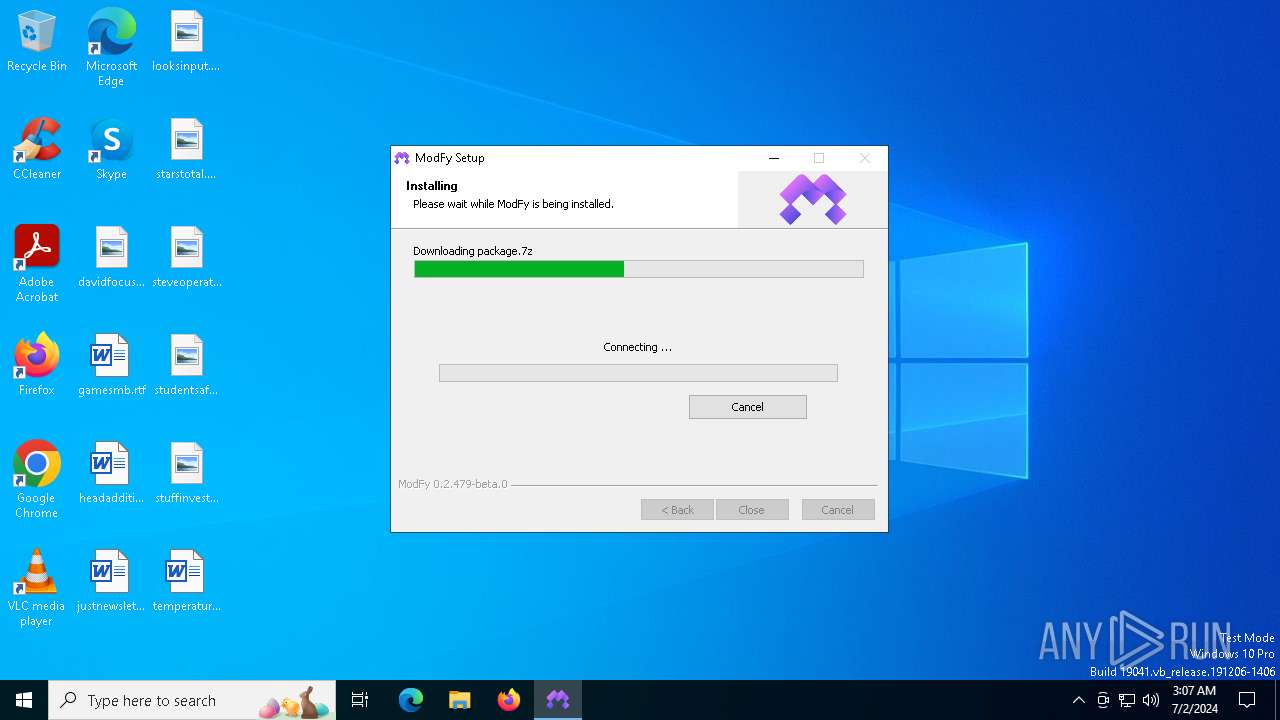
| File name: | ModFy Installer 0.2.479-beta.0.exe |
| Full analysis: | https://app.any.run/tasks/9905413d-1676-4524-96f3-7bfefb57cf8f |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 03:07:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 2D0861BE0E455C03B4C65F6AB52F5FB1 |
| SHA1: | 567F0932EAB5CB97D3F91368C0A48D278724ECBF |
| SHA256: | 6A9FF549D5A4FFC902785C516322714B076DF28D8B76875168717A1036BD06A5 |
| SSDEEP: | 24576:1JtzTubwotdCy4HyNt85nq2O6vhCmSxbv0kFgQ0Qh1lhUqBBxcn+aSbWiju3R/j:1fusotdCy4HyNt85q2O6ZCmSxbv0kFgr |
MALICIOUS
Drops the executable file immediately after the start
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
The process creates files with name similar to system file names
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Reads security settings of Internet Explorer
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Executable content was dropped or overwritten
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Checks Windows Trust Settings
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
INFO
Checks supported languages
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Reads the computer name
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Creates files in the program directory
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Checks proxy server information
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Create files in a temporary directory
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Reads the machine GUID from the registry
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Reads the software policy settings
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Creates files or folders in the user directory
- ModFy Installer 0.2.479-beta.0.exe (PID: 5124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.2.479.0 |
| ProductVersionNumber: | 0.2.479.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Infinity Zeros |
| FileDescription: | ModFy |
| FileVersion: | 0.2.479-beta.0 |
| LegalCopyright: | Copyright(C) Infinity Zeros 2022-2024 |
| ProductName: | ModFy |
| ProductVersion: | 0.2.479-beta.0 |
Total processes
138
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3512 | "C:\Users\admin\Downloads\ModFy Installer 0.2.479-beta.0.exe" | C:\Users\admin\Downloads\ModFy Installer 0.2.479-beta.0.exe | — | explorer.exe | |||||||||||
User: admin Company: Infinity Zeros Integrity Level: MEDIUM Description: ModFy Exit code: 3221226540 Version: 0.2.479-beta.0 Modules
| |||||||||||||||
| 5124 | "C:\Users\admin\Downloads\ModFy Installer 0.2.479-beta.0.exe" | C:\Users\admin\Downloads\ModFy Installer 0.2.479-beta.0.exe | explorer.exe | ||||||||||||
User: admin Company: Infinity Zeros Integrity Level: HIGH Description: ModFy Version: 0.2.479-beta.0 Modules
| |||||||||||||||
Total events
1 184
Read events
1 173
Write events
11
Delete events
0
Modification events
| (PID) Process: | (5124) ModFy Installer 0.2.479-beta.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5124) ModFy Installer 0.2.479-beta.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5124) ModFy Installer 0.2.479-beta.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5124) ModFy Installer 0.2.479-beta.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5124) ModFy Installer 0.2.479-beta.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5124) ModFy Installer 0.2.479-beta.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5124) ModFy Installer 0.2.479-beta.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
6
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Program Files\ModFy\uninstallerIcon.ico | image | |
MD5:E60681343F0F2AE17F7AAD97238C3502 | SHA256:669F59561F8F2C9897E82C3B8B891E7711C8FE6768F06A5572A161B904DCA1C0 | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\Local\Temp\nstCFC6.tmp\modern-header.bmp | image | |
MD5:D39D163CA5888316820DA713E179ED5C | SHA256:A749DCDA311651636D9266CC06D88219FCA2F01C9FFFA6E82EE84C2FF64CF963 | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\Local\Temp\nstCFC6.tmp\modern-wizard.bmp | image | |
MD5:7D6D4050CE858FE693A24EF5C842DB62 | SHA256:4303CFC54F7D7F9D1808F134B337F635FD38D8C47B29BE52E73689231B58C7D0 | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\Local\Temp\nstCFC6.tmp\INetC.dll | executable | |
MD5:38CAA11A462B16538E0A3DAEB2FC0EAF | SHA256:ED04A4823F221E9197B8F3C3DA1D6859FF5B176185BDE2F1C923A442516C810A | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\Local\Temp\nstCFC6.tmp\nsProcess.dll | executable | |
MD5:F0438A894F3A7E01A4AAE8D1B5DD0289 | SHA256:30C6C3DD3CC7FCEA6E6081CE821ADC7B2888542DAE30BF00E881C0A105EB4D11 | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:32A629A20D820F204CBF87C0C23A3CBC | SHA256:694338445D737BA693079A8BE15B31BB51A0D21C301A63CD6965A95C4AB17FDD | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:5AE8478AF8DD6EEC7AD4EDF162DD3DF1 | SHA256:FE42AC92EAE3B2850370B73C3691CCF394C23AB6133DE39F1697A6EBAC4BEDCA | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\Local\Temp\nstCFC6.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\Local\Temp\nstCFC6.tmp\UAC.dll | executable | |
MD5:ADB29E6B186DAA765DC750128649B63D | SHA256:2F7F8FC05DC4FD0D5CDA501B47E4433357E887BBFED7292C028D99C73B52DC08 | |||
| 5124 | ModFy Installer 0.2.479-beta.0.exe | C:\Users\admin\AppData\Local\Temp\nstCFC6.tmp\StdUtils.dll | executable | |
MD5:C6A6E03F77C313B267498515488C5740 | SHA256:B72E9013A6204E9F01076DC38DABBF30870D44DFC66962ADBF73619D4331601E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
59
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2520 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2520 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5124 | ModFy Installer 0.2.479-beta.0.exe | GET | 200 | 2.19.105.18:80 | http://x2.c.lencr.org/ | unknown | — | — | unknown |
3940 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
3940 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4280 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2328 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3172 | RUXIMICS.exe | 51.11.168.232:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2044 | MoUsoCoreWorker.exe | 51.11.168.232:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
2520 | svchost.exe | 51.11.168.232:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
4656 | SearchApp.exe | 2.19.96.128:443 | — | Akamai International B.V. | DE | unknown |
2520 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
2520 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
5124 | ModFy Installer 0.2.479-beta.0.exe | 188.114.96.3:443 | update.modfyapp.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
update.modfyapp.com |
| unknown |
x2.c.lencr.org |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |