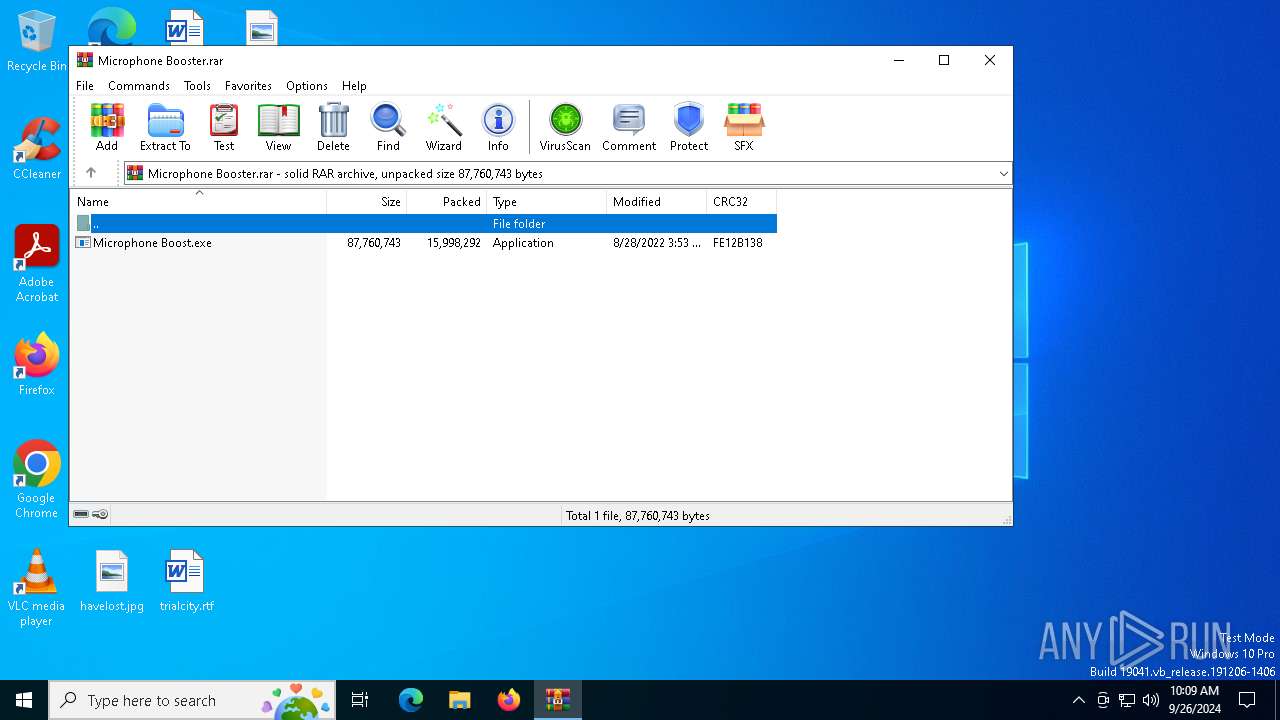
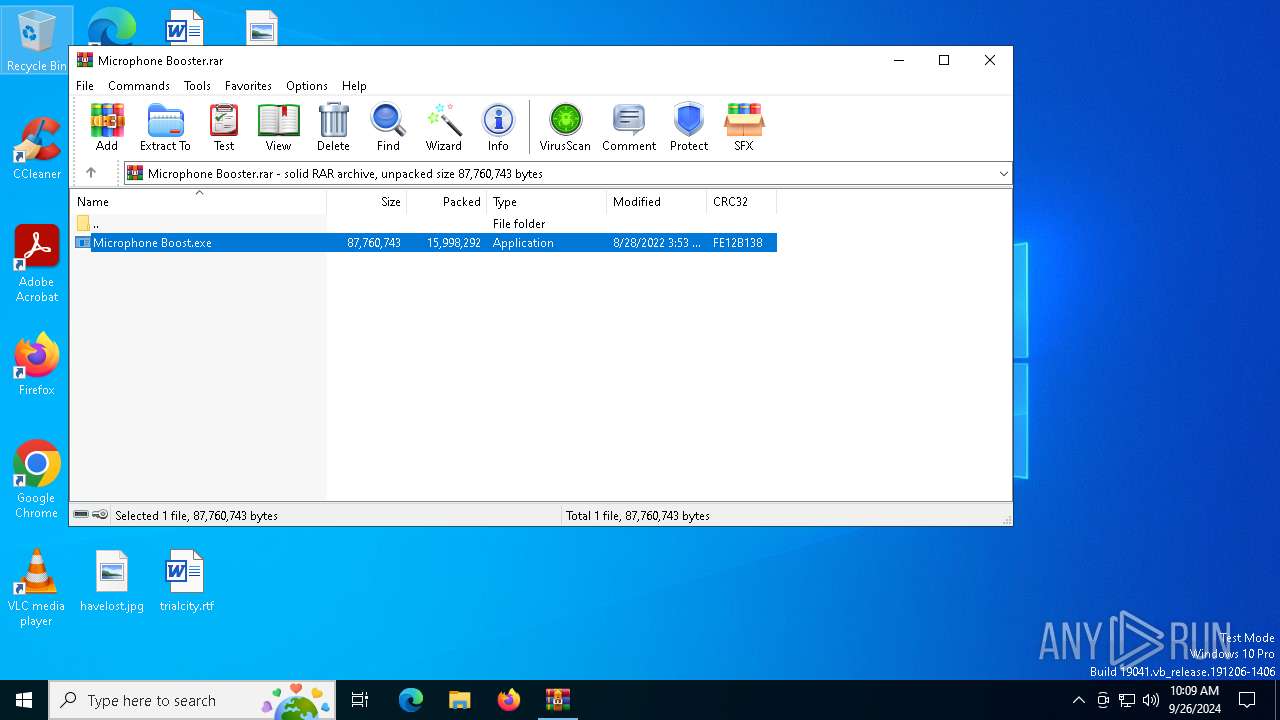
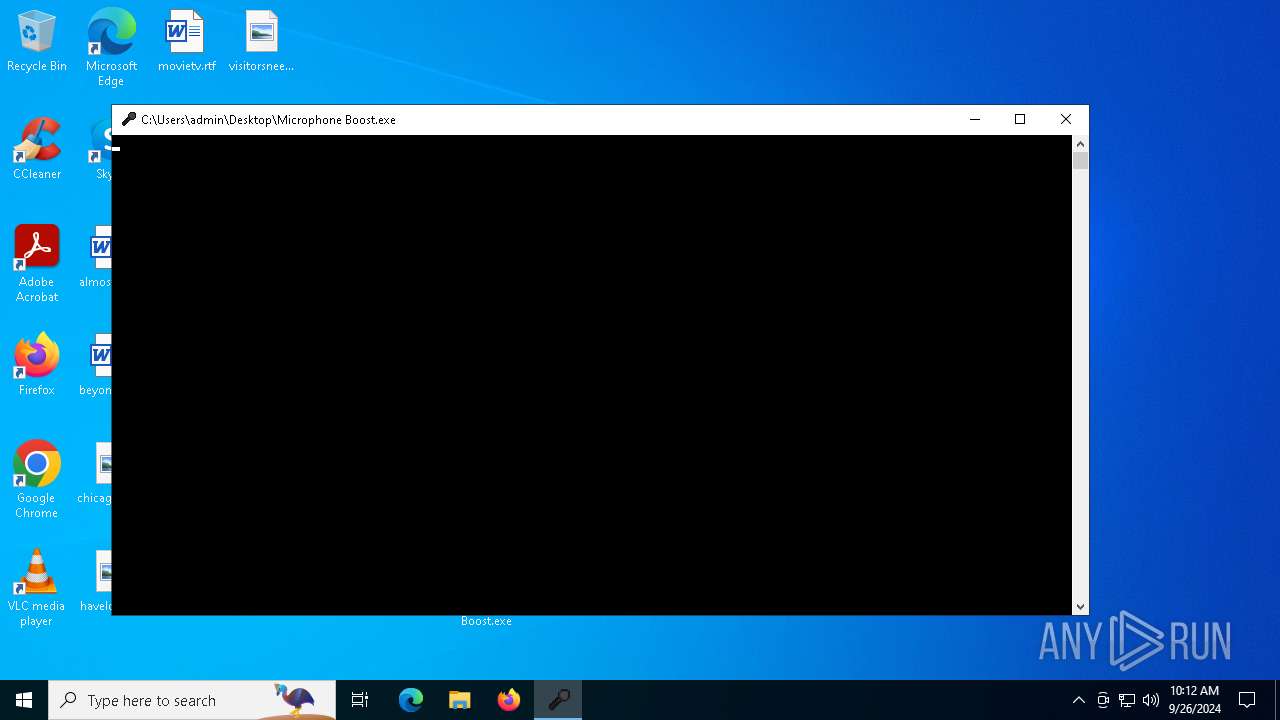
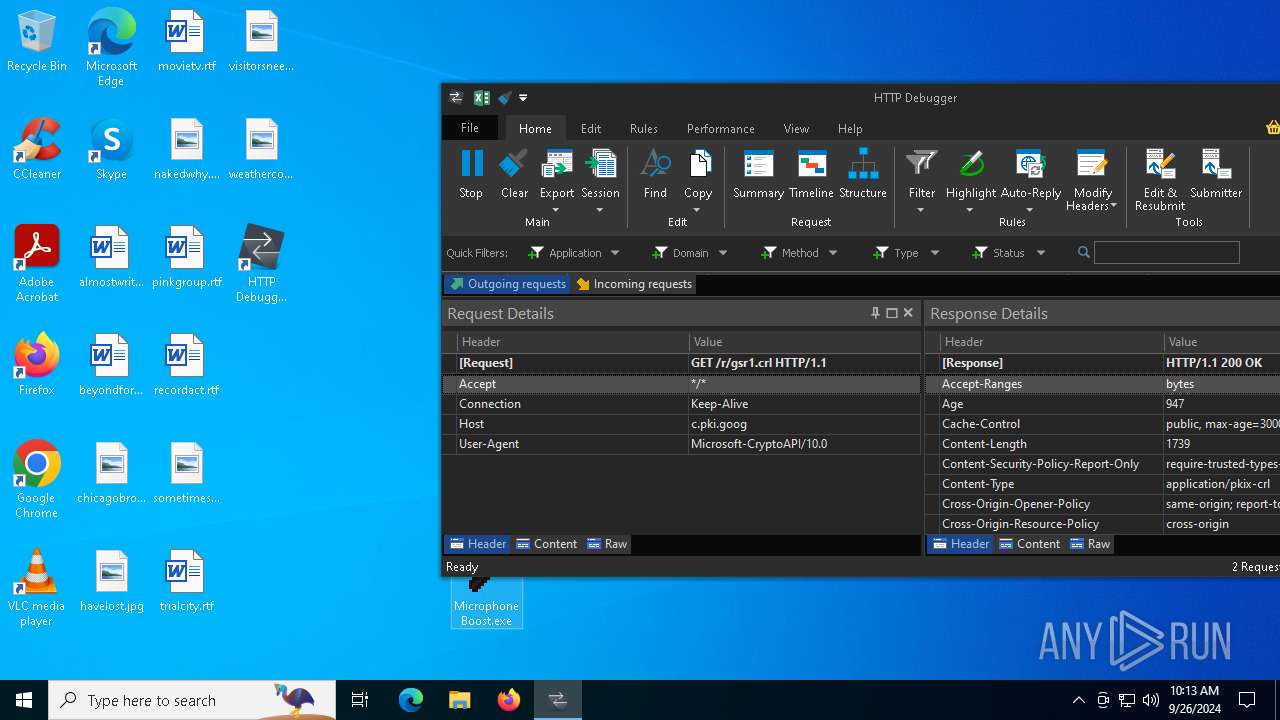
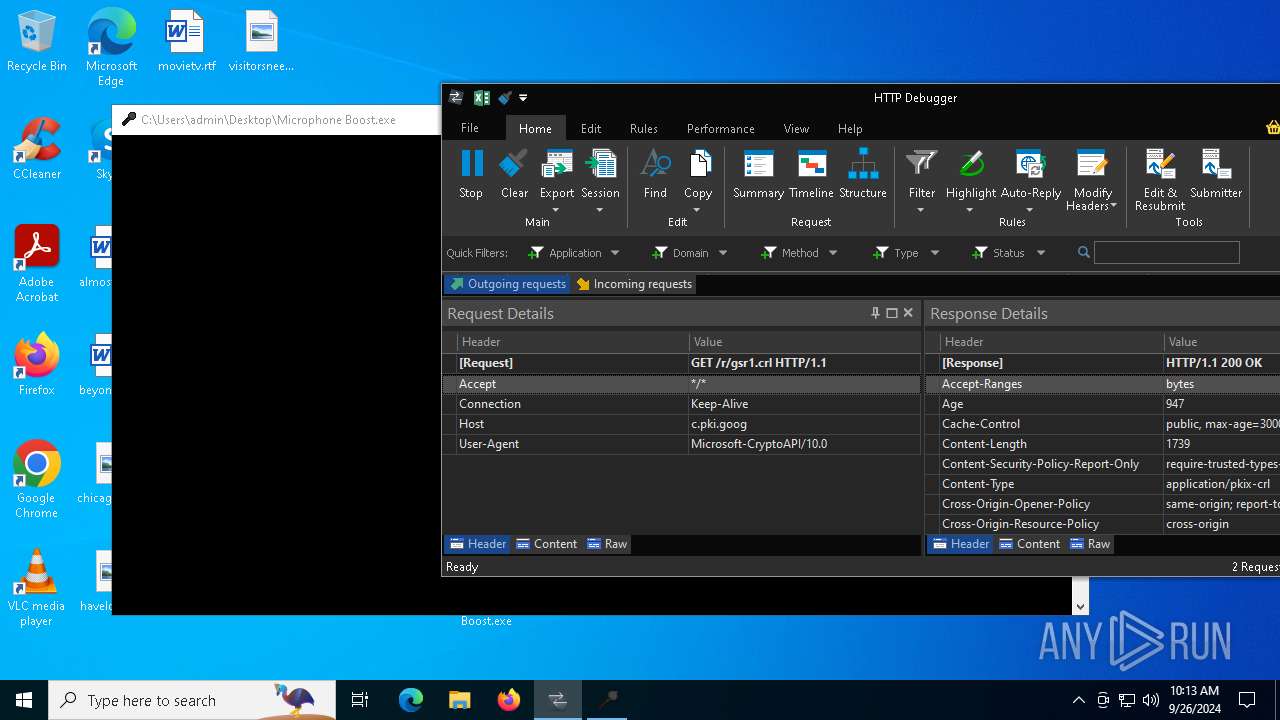
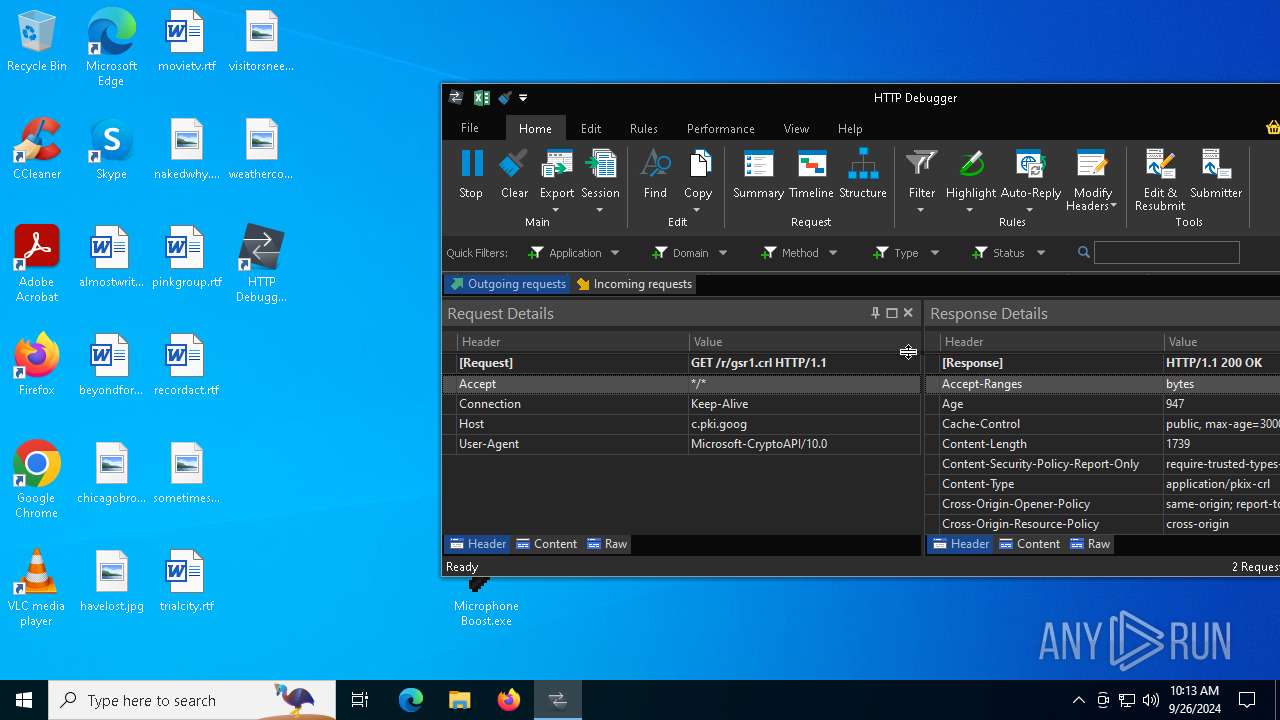
| File name: | Microphone Booster.rar |
| Full analysis: | https://app.any.run/tasks/0b936ff6-6082-4283-8d2e-561015fde6a3 |
| Verdict: | Malicious activity |
| Analysis date: | September 26, 2024, 10:09:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B560B90DA54BFF28B7D32103013FDA4B |
| SHA1: | D2C431BA0EBCB34481961F1EA93D822594E58CF0 |
| SHA256: | 6A952DE1B42DD42717023ACEA7C49E36122B4C96F7F1528C5491ADE65C50DA2D |
| SSDEEP: | 98304:OTMYXJ87NXVZq/K+VR2uDDL63lZwW1r7oGM54SDmj5FgPHl531BGV/DO4VKVJ9+e:pJxTiw4keo8QgQR5yRR5FqaJs/q3gbA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 1176)
- Microphone Boost.exe (PID: 5616)
- Microphone Boost.exe (PID: 4164)
- Microphone Boost.exe (PID: 7156)
- Microphone Boost.exe (PID: 6632)
Executable content was dropped or overwritten
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 1176)
- Microphone Boost.exe (PID: 5616)
- Microphone Boost.exe (PID: 4164)
- HTTPDebuggerSvc.exe (PID: 1748)
- Microphone Boost.exe (PID: 7156)
- Microphone Boost.exe (PID: 6632)
The process drops C-runtime libraries
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 1176)
- Microphone Boost.exe (PID: 5616)
- Microphone Boost.exe (PID: 4164)
- Microphone Boost.exe (PID: 7156)
- Microphone Boost.exe (PID: 6632)
Process drops legitimate windows executable
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 1176)
- Microphone Boost.exe (PID: 5616)
- Microphone Boost.exe (PID: 4164)
- Microphone Boost.exe (PID: 7156)
- Microphone Boost.exe (PID: 6632)
Application launched itself
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 1176)
- Microphone Boost.exe (PID: 5616)
- Microphone Boost.exe (PID: 4164)
- Microphone Boost.exe (PID: 7156)
- Microphone Boost.exe (PID: 6632)
Loads Python modules
- Microphone Boost.exe (PID: 6872)
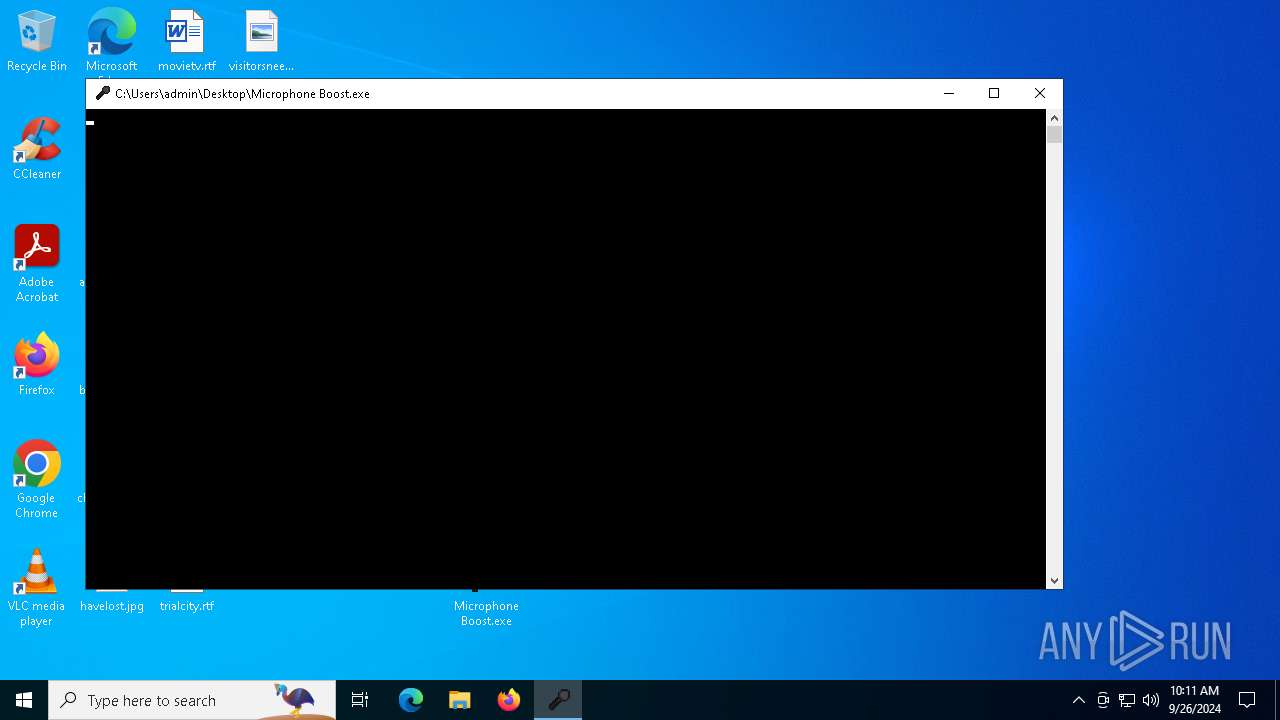
Starts CMD.EXE for commands execution
- Microphone Boost.exe (PID: 6872)
- Microphone Boost.exe (PID: 1488)
- Microphone Boost.exe (PID: 1748)
- Microphone Boost.exe (PID: 6224)
- Microphone Boost.exe (PID: 6972)
- Microphone Boost.exe (PID: 6516)
Executes as Windows Service
- VSSVC.exe (PID: 6280)
- HTTPDebuggerSvc.exe (PID: 1748)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6044)
- HTTPDebuggerSvc.exe (PID: 1748)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 1680)
- explorer.exe (PID: 4552)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
Manual execution by a user
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 5616)
- firefox.exe (PID: 6772)
- msiexec.exe (PID: 6540)
- Microphone Boost.exe (PID: 1176)
- Microphone Boost.exe (PID: 7156)
- Microphone Boost.exe (PID: 4164)
- Microphone Boost.exe (PID: 6632)
Checks supported languages
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 6872)
Create files in a temporary directory
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 6872)
Reads the computer name
- Microphone Boost.exe (PID: 6792)
- Microphone Boost.exe (PID: 6872)
Reads the machine GUID from the registry
- Microphone Boost.exe (PID: 6872)
Checks operating system version
- Microphone Boost.exe (PID: 6872)
- Microphone Boost.exe (PID: 1488)
- Microphone Boost.exe (PID: 1748)
- Microphone Boost.exe (PID: 6224)
- Microphone Boost.exe (PID: 6972)
- Microphone Boost.exe (PID: 6516)
Checks proxy server information
- Microphone Boost.exe (PID: 6872)
Application launched itself
- firefox.exe (PID: 6772)
- firefox.exe (PID: 1480)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6540)
- msiexec.exe (PID: 6044)
Manages system restore points
- SrTasks.exe (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
188
Monitored processes
52
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2936 -childID 1 -isForBrowser -prefsHandle 2928 -prefMapHandle 2924 -prefsLen 30953 -prefMapSize 244343 -jsInitHandle 1504 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e438c0a5-c56e-40a5-838c-0092e2abfd87} 1480 "\\.\pipe\gecko-crash-server-pipe.1480" 1b8abb5d150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4588 -childID 2 -isForBrowser -prefsHandle 4580 -prefMapHandle 4576 -prefsLen 36263 -prefMapSize 244343 -jsInitHandle 1504 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {7f458f5e-bb96-4be6-af44-e8cd284b205b} 1480 "\\.\pipe\gecko-crash-server-pipe.1480" 1b8ad079bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 892 | "C:\Program Files (x86)\HTTPDebuggerPro\HTTPDebuggerUI.exe" | C:\Program Files (x86)\HTTPDebuggerPro\HTTPDebuggerUI.exe | — | msiexec.exe | |||||||||||
User: admin Company: HttpDebugger.com Integrity Level: MEDIUM Description: HTTP Debugger Exit code: 0 Version: 9.0.0.12 | |||||||||||||||
| 904 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Microphone Boost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6052 -childID 6 -isForBrowser -prefsHandle 5256 -prefMapHandle 6532 -prefsLen 31242 -prefMapSize 244343 -jsInitHandle 1504 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {40fa725a-b8e6-46c3-9b0f-d757cc3cc9dd} 1480 "\\.\pipe\gecko-crash-server-pipe.1480" 1b8ae4dcd90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1176 | "C:\Users\admin\Desktop\Microphone Boost.exe" | C:\Users\admin\Desktop\Microphone Boost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6584 -childID 9 -isForBrowser -prefsHandle 6844 -prefMapHandle 6848 -prefsLen 31997 -prefMapSize 244343 -jsInitHandle 1504 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {725aa18b-51a3-4e4b-874d-57cfee3227cd} 1480 "\\.\pipe\gecko-crash-server-pipe.1480" 1b8af6f9bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1480 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\Desktop\Microphone Boost.exe" | C:\Users\admin\Desktop\Microphone Boost.exe | Microphone Boost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1680 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Microphone Booster.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
30 909
Read events
30 833
Write events
70
Delete events
6
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000006039A |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Microphone Booster.rar | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010015000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C000000130000000000000061006C006D006F0073007400770072006900740065002E007200740066003E0020002000000012000000000000006200650079006F006E00640066006F0072006D002E007200740066003E0020002000000015000000000000006300680069006300610067006F00620072006F007700730065002E006A00700067003E00200020000000100000000000000068006100760065006C006F00730074002E006A00700067003E002000200000000F000000000000006D006F00760069006500740076002E007200740066003E0020002000000010000000000000006E0061006B00650064007700680079002E0070006E0067003E002000200000001100000000000000700069006E006B00670072006F00750070002E007200740066003E0020002000000011000000000000007200650063006F00720064006100630074002E007200740066003E00200020000000150000000000000073006F006D006500740069006D006500730073007500720065002E006A00700067003E00200020000000110000000000000074007200690061006C0063006900740079002E007200740066003E002000200000001400000000000000760069007300690074006F00720073006E006500650064002E006A00700067003E002000200000001500000000000000770065006100740068006500720063006F0075006E00740079002E0070006E0067003E0020002000000018000000000000004D006900630072006F00700068006F006E006500200042006F006F00730074002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001500000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A040110000004040000000001200000040400000803F1300000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F07000000C0400000A0401400 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: EE32F56600000000 | |||
Executable files
508
Suspicious files
239
Text files
59
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1680.19961\Microphone Boost.exe | — | |
MD5:— | SHA256:— | |||
| 4552 | explorer.exe | C:\Users\admin\Desktop\Microphone Boost.exe | — | |
MD5:— | SHA256:— | |||
| 6792 | Microphone Boost.exe | C:\Users\admin\AppData\Local\Temp\_MEI67922\Cryptodome\Cipher\_ARC4.pyd | executable | |
MD5:FC3AA8A94AAB11264D39D1D859C3C45F | SHA256:BAB6245A6FC2F7FE7887ADD70FB83FF687DC6D80A186AB02232C2793F8B305B3 | |||
| 6792 | Microphone Boost.exe | C:\Users\admin\AppData\Local\Temp\_MEI67922\Cryptodome\Cipher\_Salsa20.pyd | executable | |
MD5:91B3F04740ADEEF96AC0EAB4BFFBAB0A | SHA256:A4DA10DA7612CB7E3436903BB25C8C53C982A912E2E38D0EE40D020E1A67BAED | |||
| 6792 | Microphone Boost.exe | C:\Users\admin\AppData\Local\Temp\_MEI67922\Cryptodome\Cipher\_raw_ctr.pyd | executable | |
MD5:46CBD5F5403355255B3C5A7616C2196D | SHA256:3840FC7CABEB4BF9DC45FD923C61B775C71FEC9D42B4E672C30BA4E111507042 | |||
| 6792 | Microphone Boost.exe | C:\Users\admin\AppData\Local\Temp\_MEI67922\Cryptodome\Cipher\_chacha20.pyd | executable | |
MD5:BBF0959111A4038308B68E959AB6F083 | SHA256:0DCC5FD5CCFAC29521A22BD255E3FE449F5FA82E884BCFDBF30E8CF802BC26E1 | |||
| 6792 | Microphone Boost.exe | C:\Users\admin\AppData\Local\Temp\_MEI67922\Cryptodome\Cipher\_raw_cast.pyd | executable | |
MD5:619BC1CBA5D94F35E1FFAA7F025AD656 | SHA256:24040F9FDA7FC462BD913F06D07CD415E18604F9411913BCC10DE701EB0D38B7 | |||
| 6792 | Microphone Boost.exe | C:\Users\admin\AppData\Local\Temp\_MEI67922\Cryptodome\Cipher\_raw_aesni.pyd | executable | |
MD5:A0987518E52930C17243B8E7196C652E | SHA256:CD3D976B9A90747F790AA141068531B7DCA5F7FE1621EB703A6A74526D0410CB | |||
| 6792 | Microphone Boost.exe | C:\Users\admin\AppData\Local\Temp\_MEI67922\Cryptodome\Cipher\_raw_aes.pyd | executable | |
MD5:9B0F46757D70DA38C6B48E3166374D99 | SHA256:5EB0B6364B9CBE5AA0CB4CFDF78C2DF65877B39374A6C3CA9D2412DA5225B355 | |||
| 6792 | Microphone Boost.exe | C:\Users\admin\AppData\Local\Temp\_MEI67922\Cryptodome\Cipher\_raw_blowfish.pyd | executable | |
MD5:4DB6EACC52BB8A4CBE3B70AE57659877 | SHA256:CDBD743848DD7B0C06550798ADD1A9340E871A55D8842FAB75D7679AEC2BC3E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
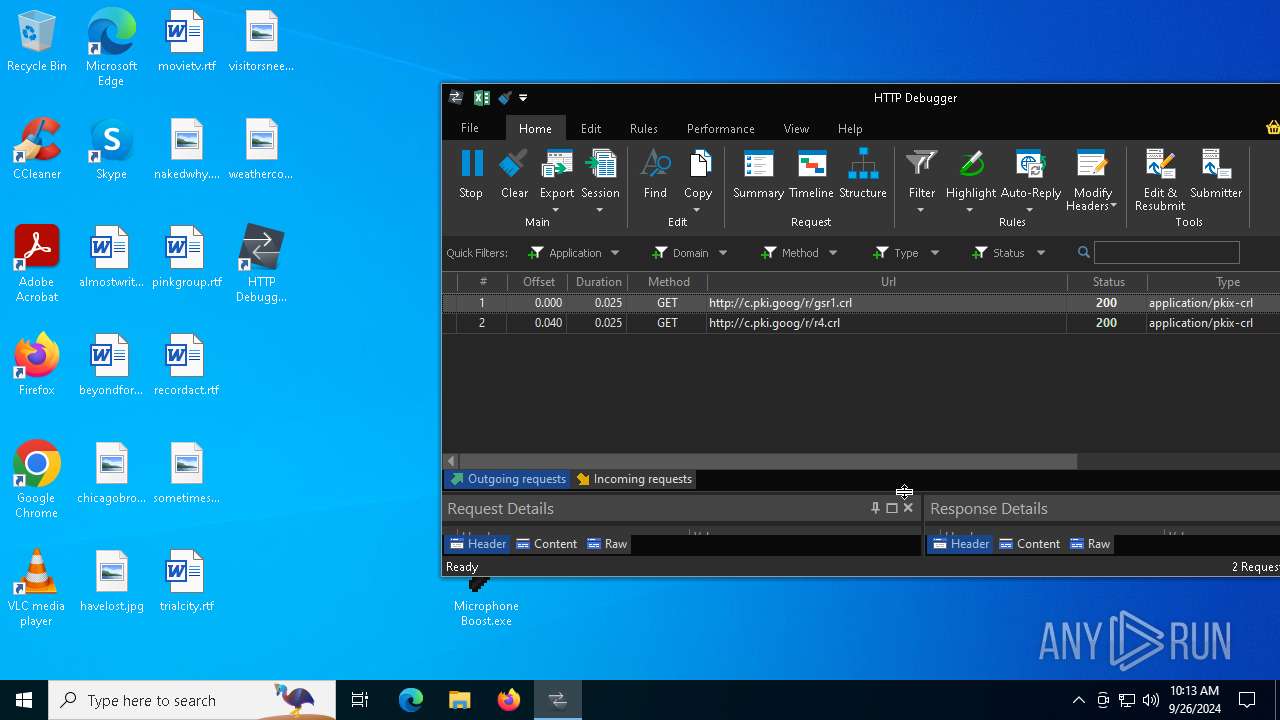
HTTP(S) requests
44
TCP/UDP connections
176
DNS requests
188
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5196 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2064 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1480 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1480 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1480 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
1480 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/s/wr3/XjA | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5196 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
32 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.189.173.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5196 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5196 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6872 | Microphone Boost.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
findthehidder.com |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
Microphone Boost.exe | FTH: (5616): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
Microphone Boost.exe | FTH: (1748): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
cmd.exe | FTH: (6212): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|