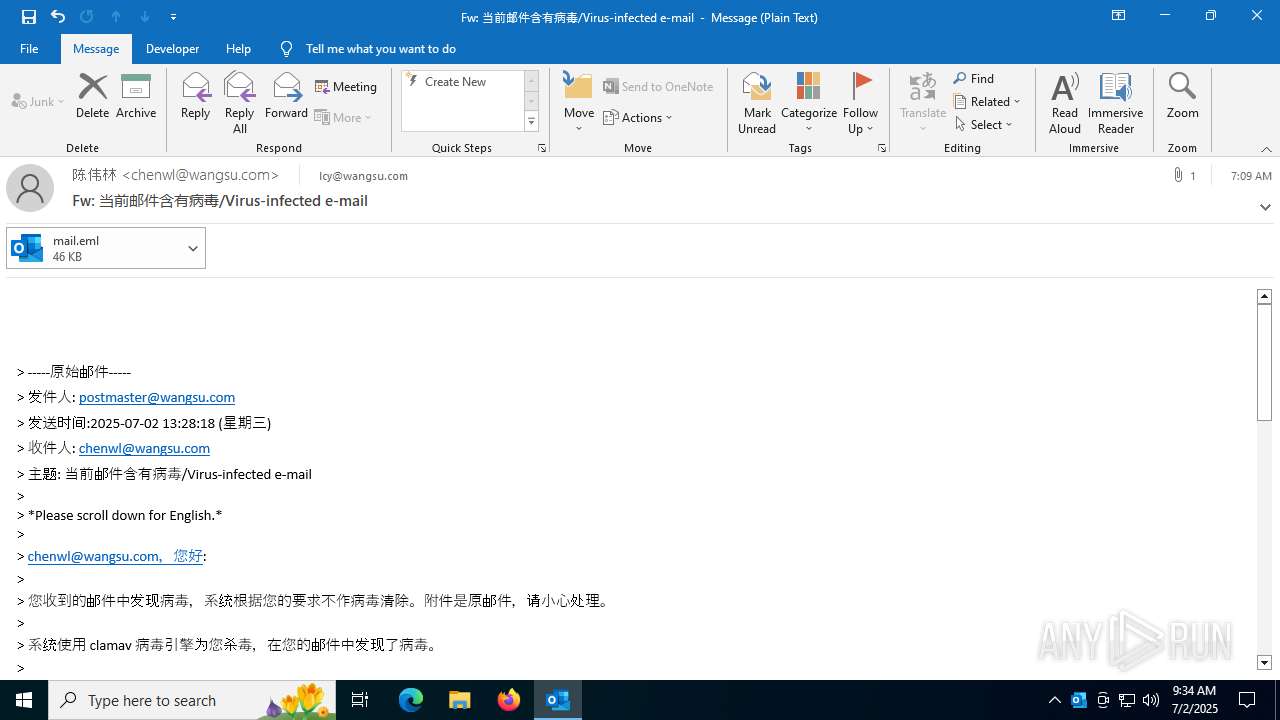
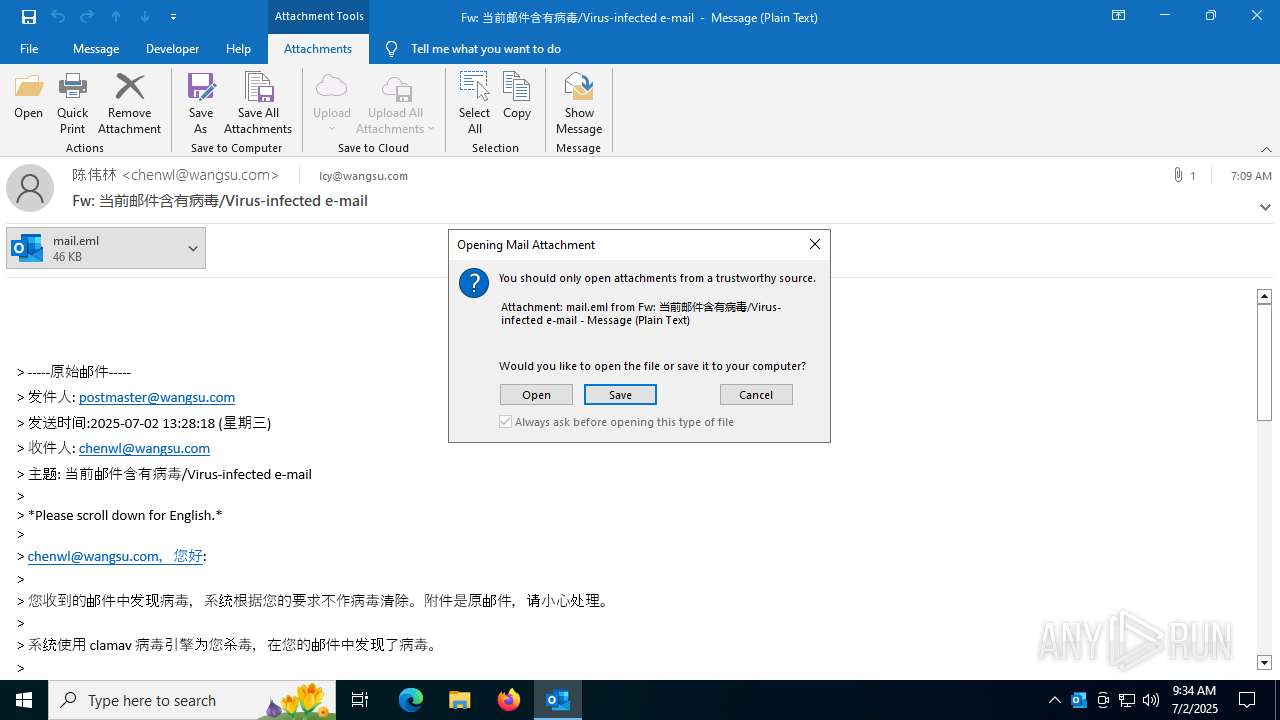
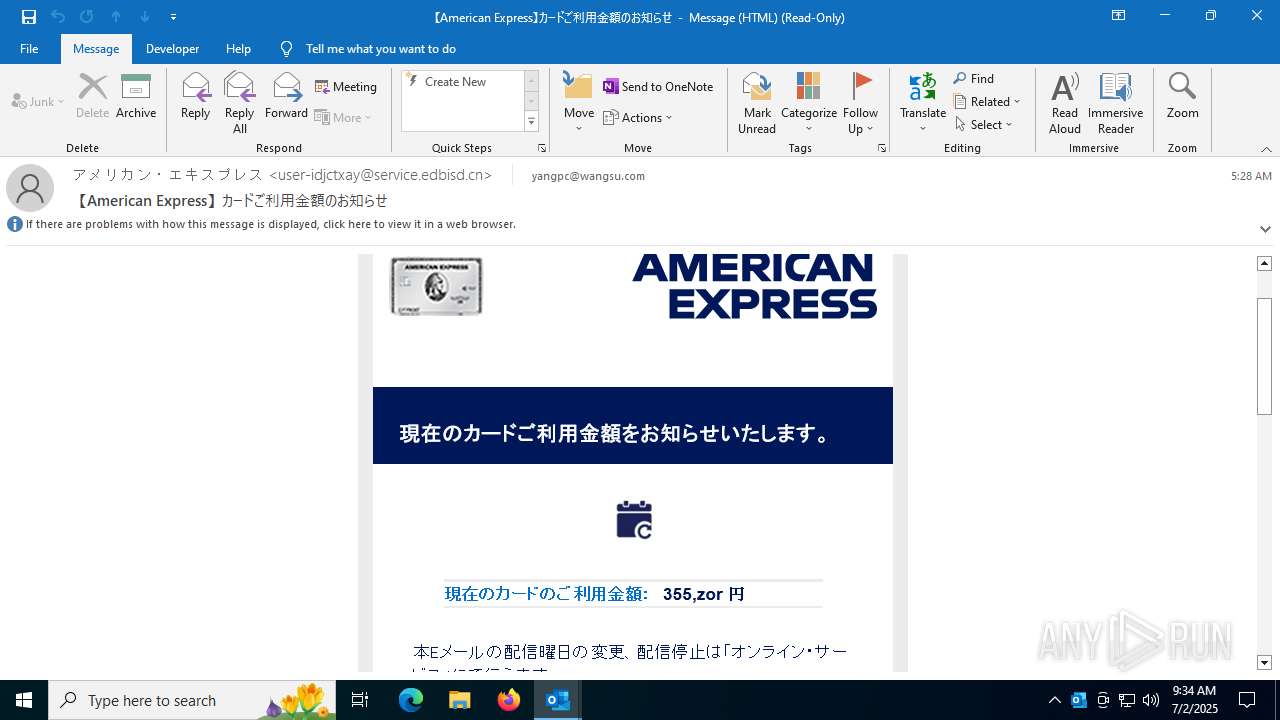
| File name: | mail.eml |
| Full analysis: | https://app.any.run/tasks/b758099e-442f-40fe-81b2-0753ff381eeb |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 09:34:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | F71C303D37FDFAA0626B1C74A970B144 |
| SHA1: | D42C84D59D8D7B963C6D5546E5FAF6F0BE08922E |
| SHA256: | 6A73685BB121B74BAB18C047A415CFAC2EB5FA6AF6817E2C7FBB7F1208432E14 |
| SSDEEP: | 768:4EqpnFjq2kbbtlk9rpJscrocMLDJ81dVkxidPve6hL+PxfXcnRAcyCS+WBPVqMDB:4EqFFjq2kbBlaw4oL4VmL/1S82I |
MALICIOUS
No malicious indicators.SUSPICIOUS
Detected use of alternative data streams (AltDS)
- OUTLOOK.EXE (PID: 7100)
Application launched itself
- OUTLOOK.EXE (PID: 7100)
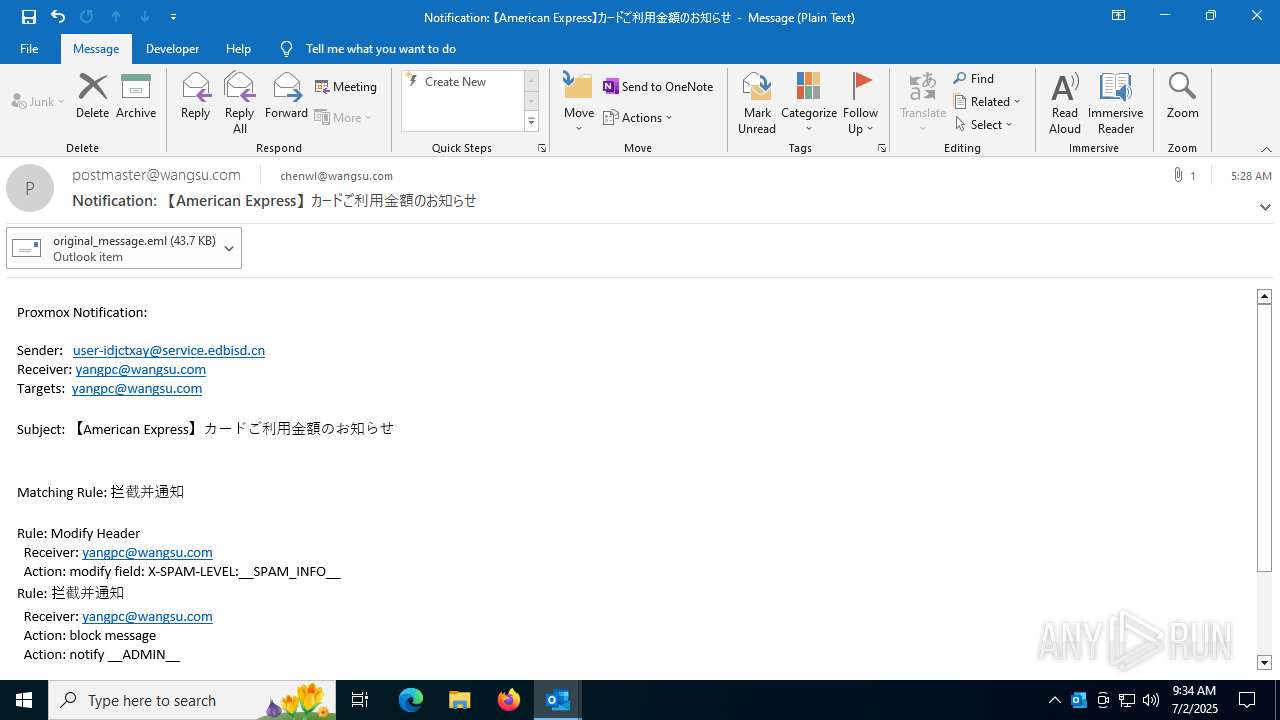
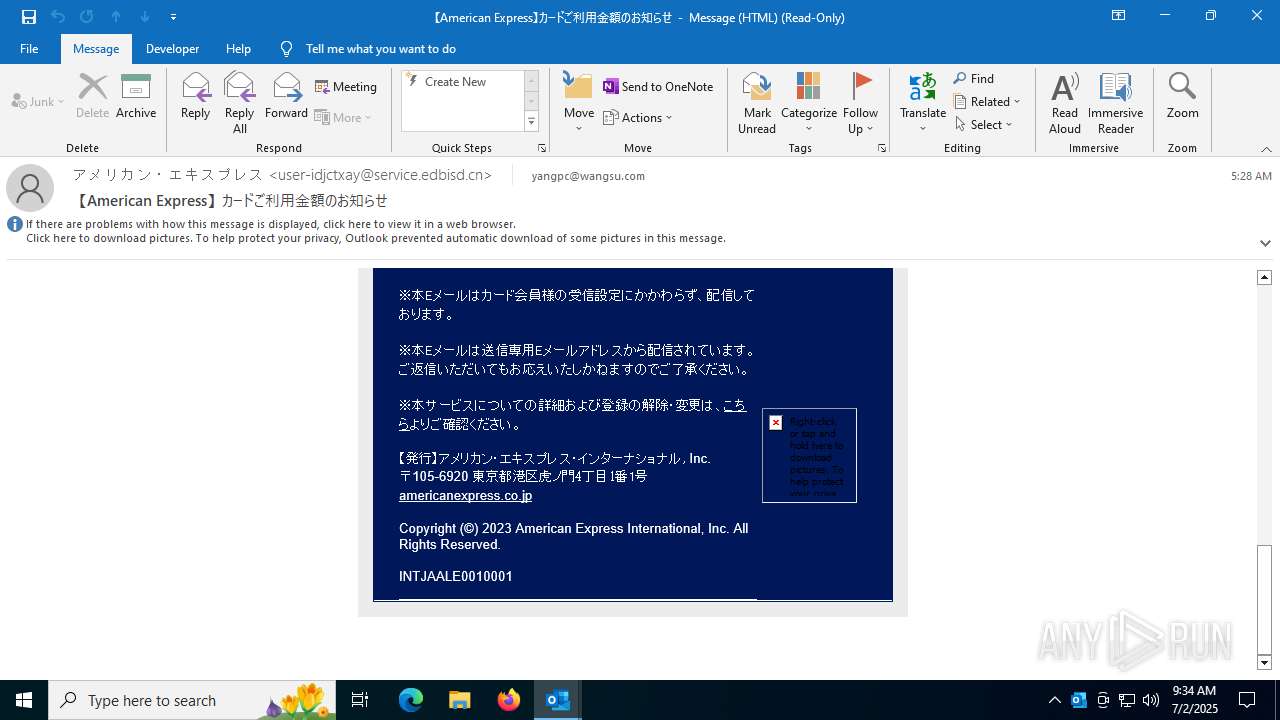
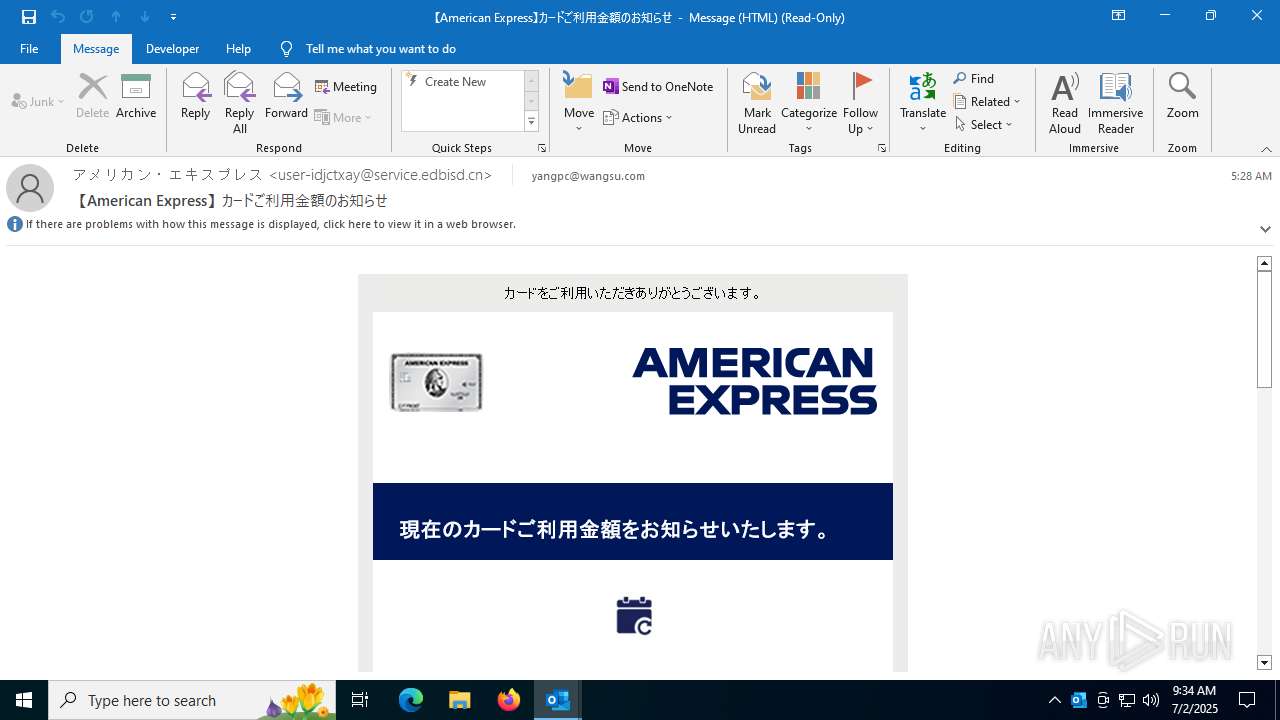
Email with suspicious attachment
- OUTLOOK.EXE (PID: 7100)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 7100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
142
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1480 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "D1FBFA1D-39A4-4034-A0BF-905F84944581" "C2CD0743-FA0B-429D-B943-741DC96372F1" "7100" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 3876 | "C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\IGDWR0W1\mail.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7100 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\mail.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
12 198
Read events
11 800
Write events
341
Delete events
57
Modification events
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7100 |
| Operation: | write | Name: | 0 |
Value: 0B0E10C94A5324851C974FA32E06ADF41F6D6A230046B0B8E2E9C7E6FAED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511BC37D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (7100) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
8
Text files
15
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7100 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\CloudFonts\MS Mincho\36042714478.ttf | — | |
MD5:— | SHA256:— | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\GJPPL5500000[1].gif | image | |
MD5:B949949BEDCFFAF22C88679DD04C8969 | SHA256:1ECDD87460EB9557CEA93C9DE978B02120EAF952E6C159F639B32532BEC5CC43 | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C31B2498754E340573F1336DE607D619 | binary | |
MD5:19ABE27EA487A5D66535331A471F7E63 | SHA256:BBE34A17109B9CC1DB92FC6F31248D132CAEA661012D21D918D22CA2D9FF41DC | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\IGDWR0W1\mail (002).eml | eml | |
MD5:5A6D384160837C93004F341F190AF60D | SHA256:3865520B4E490F27139AC238DE4E2CD15017CAA5A3DE20A2540ACB8C43E88F8F | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_27.ttf | pi2 | |
MD5:59610D64A881E76BAD429817056A9E34 | SHA256:264CEBF14D79463C65BCE44297E19FA0FC6D75848CA07B45C2F563344530336A | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:2480835370DBD30443A10159A19DDF06 | SHA256:69AF8ED16771581C823AC046837AA5B8454A454E7C73C6DBA899628F3AB170D2 | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C31B2498754E340573F1336DE607D619 | der | |
MD5:FC2E9ECE34C84570BE95908398257ABE | SHA256:4F166FC4422FCCB9AD3BD28C79BCE445C63600F9C6E04F183DB0623667041E1D | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\CatalogCacheMetaData.xml | xml | |
MD5:67EC07B10680CD7CFF0FA77F163CB5E0 | SHA256:4E8043ED1D55BAA192B84671A0786C4C5BE951DA24F7168383334BABE9118690 | |||
| 7100 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_44B7CEC7D7846BA12D21890D7AF2D759 | der | |
MD5:9744AFA80EE625A3639AA162BDE51931 | SHA256:A7FA3259F06631FD1CA5A5C689DFB91F4662CC74F3DC96F78B8776E14F985EEB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
48
DNS requests
27
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2520 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7100 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4664 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4664 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
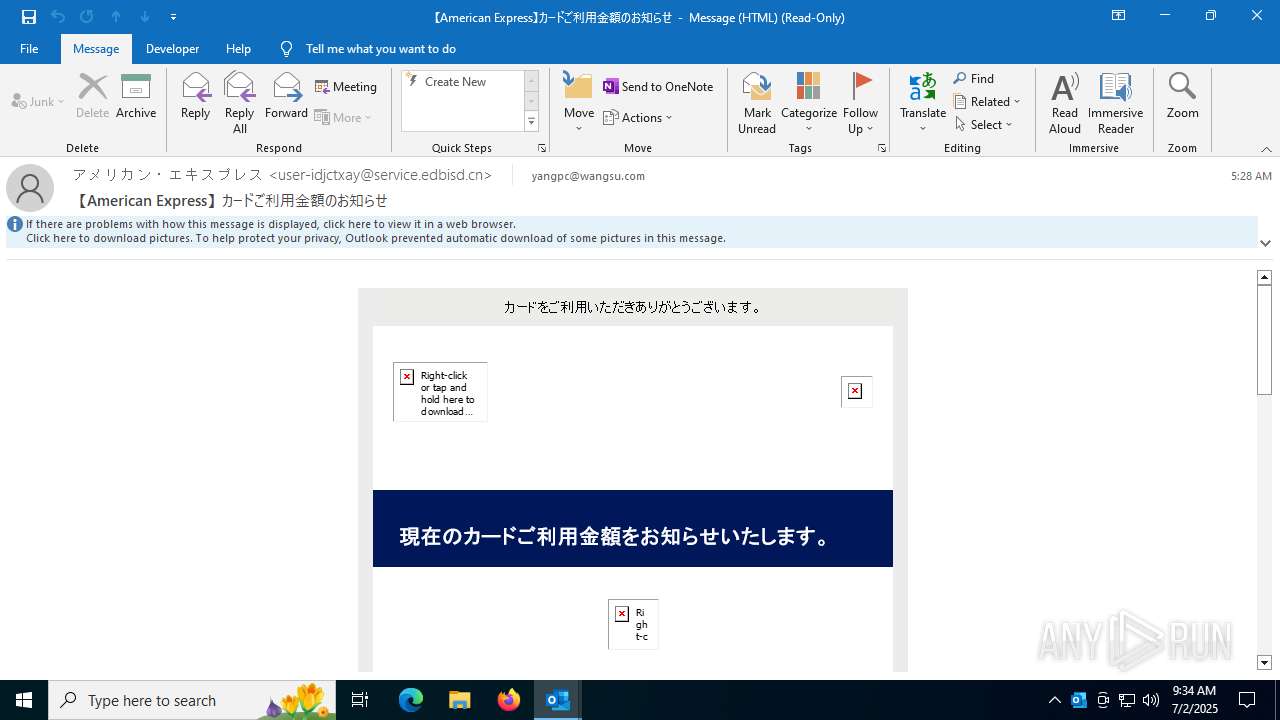
7100 | OUTLOOK.EXE | GET | 301 | 148.173.96.91:80 | http://www208.americanexpress.com/axp/icons/AmericanExpressWhiteLogo.png | unknown | — | — | whitelisted |
7100 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | unknown | — | — | whitelisted |
7100 | OUTLOOK.EXE | GET | 301 | 148.173.96.91:80 | http://www208.americanexpress.com/axp/japaneseimages/JP_Login_CTA.jpg | unknown | — | — | whitelisted |
7100 | OUTLOOK.EXE | GET | 301 | 148.173.96.91:80 | http://www208.americanexpress.com/axp/icons/JP_App_Store.png | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1232 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7100 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7100 | OUTLOOK.EXE | 2.16.168.119:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
7100 | OUTLOOK.EXE | 52.109.16.3:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7100 | OUTLOOK.EXE | Misc activity | ET INFO Observed UA-CPU Header |