| File name: | 20240726@j.exe |
| Full analysis: | https://app.any.run/tasks/f062fc3a-8b25-4f8d-93d8-8ab6d3383efb |
| Verdict: | Malicious activity |
| Analysis date: | July 27, 2024, 17:53:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | F5E1F0602042C8357905C474019A1889 |
| SHA1: | 45BCE2BFF3D905235BCD3B158A6761320D72A2C2 |
| SHA256: | 6A6AC7D5693B7016F07B60646C5DE9C503D4EE7F0676F0927742DF2E340A4E83 |
| SSDEEP: | 98304:fi2z1YmXJBwxiu33cseut7IizbYjB4kpMc8tX2sqmsTT4f0Yj5DSTfXE7qYjt7zx:K9Znc |
MALICIOUS
Drops the executable file immediately after the start
- 20240726@j.exe (PID: 7480)
- cmd.exe (PID: 3188)
- Client.exe (PID: 4808)
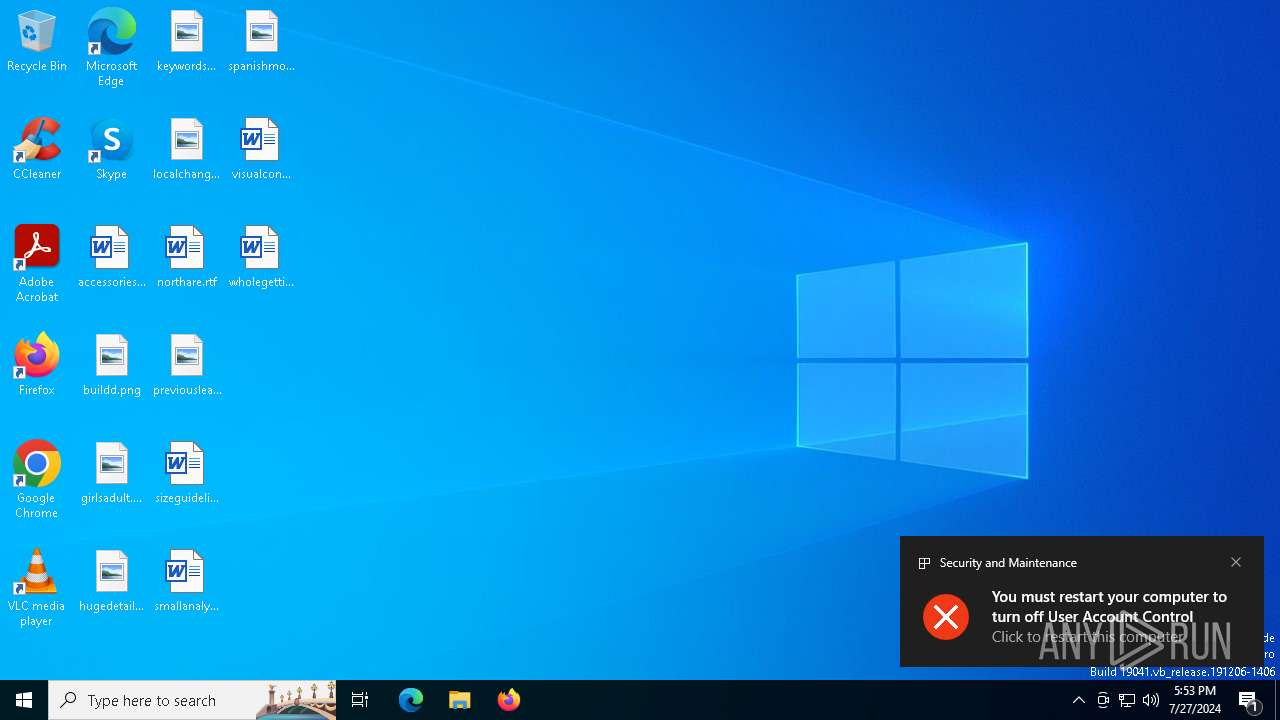
UAC/LUA settings modification
- reg.exe (PID: 8144)
SUSPICIOUS
Reads security settings of Internet Explorer
- 20240726@j.exe (PID: 7480)
- ShellExperienceHost.exe (PID: 7208)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 7748)
- cmd.exe (PID: 7268)
Starts CMD.EXE for commands execution
- 20240726@j.exe (PID: 7480)
- Client.exe (PID: 4808)
Reads the date of Windows installation
- 20240726@j.exe (PID: 7480)
Suspicious use of NETSH.EXE
- 20240726@j.exe (PID: 7480)
Mutex name with non-standard characters
- 20240726@j.exe (PID: 7480)
- Client.exe (PID: 4808)
Executing commands from a ".bat" file
- 20240726@j.exe (PID: 7480)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8064)
Executable content was dropped or overwritten
- cmd.exe (PID: 3188)
- Client.exe (PID: 4808)
- 20240726@j.exe (PID: 7480)
Connects to unusual port
- Client.exe (PID: 4808)
There is functionality for communication over UDP network (YARA)
- Client.exe (PID: 4808)
INFO
Reads the computer name
- 20240726@j.exe (PID: 7480)
- Client.exe (PID: 4808)
- ShellExperienceHost.exe (PID: 7208)
Creates files in the program directory
- 20240726@j.exe (PID: 7480)
- cmd.exe (PID: 3188)
- Client.exe (PID: 4808)
Process checks computer location settings
- 20240726@j.exe (PID: 7480)
Checks supported languages
- 20240726@j.exe (PID: 7480)
- ShellExperienceHost.exe (PID: 7208)
- Client.exe (PID: 4808)
Creates files or folders in the user directory
- 20240726@j.exe (PID: 7480)
Reads security settings of Internet Explorer
- mmc.exe (PID: 7192)
Reads CPU info
- Client.exe (PID: 4808)
UPX packer has been detected
- Client.exe (PID: 4808)
Reads the software policy settings
- slui.exe (PID: 5532)
Attempting to connect via WebSocket
- Client.exe (PID: 4808)
VMProtect protector has been detected
- Client.exe (PID: 4808)
Checks proxy server information
- slui.exe (PID: 5532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (46.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (41) |
| .exe | | | Win32 Executable (generic) (6.6) |
| .exe | | | Generic Win/DOS Executable (2.9) |
| .exe | | | DOS Executable Generic (2.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:07:26 13:29:22+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 9 |
| CodeSize: | 255488 |
| InitializedDataSize: | 5700608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2a718 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
Total processes
154
Monitored processes
21
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3188 | "C:\Windows\System32\cmd.exe" /c copy /b C:\ProgramData\ricka\v2E9L@j\v + C:\ProgramData\ricka\v2E9L@j\b C:\ProgramData\ricka\v2E9L@j\ClientModule.dll | C:\Windows\System32\cmd.exe | 20240726@j.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4808 | "C:\ProgramData\ricka\v2E9L@j\Client.exe" | C:\ProgramData\ricka\v2E9L@j\Client.exe | mmc.exe | ||||||||||||
User: admin Company: 深圳市恒酷科技有限公司 Integrity Level: HIGH Description: 天舞吧视频聊天平台 Version: 5.0.1.1 Modules
| |||||||||||||||
| 5532 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7192 | C:\WINDOWS\system32\mmc.exe -Embedding | C:\Windows\System32\mmc.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7208 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7268 | C:\WINDOWS\system32\cmd.exe /c ipconfig /all | C:\Windows\SysWOW64\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7388 | "C:\Users\admin\AppData\Local\Temp\20240726@j.exe" | C:\Users\admin\AppData\Local\Temp\20240726@j.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7396 | ipconfig /all | C:\Windows\SysWOW64\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 198
Read events
10 175
Write events
23
Delete events
0
Modification events
| (PID) Process: | (7480) 20240726@j.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7480) 20240726@j.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7480) 20240726@j.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7480) 20240726@j.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7480) 20240726@j.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (7480) 20240726@j.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (8124) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (8144) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (8168) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
| (PID) Process: | (7208) ShellExperienceHost.exe | Key: | \REGISTRY\A\{be528cfd-612d-511a-fe51-5be4db2468e1}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000F12217DD4DE0DA01 | |||
Executable files
7
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3188 | cmd.exe | C:\ProgramData\ricka\v2E9L@j\ClientModule.dll | executable | |
MD5:F5BA22F3EB817FD5C23DC5F114DCF79C | SHA256:40D913C97E44E647AE101A71651EDD16A13200B81E2ADC4D06213F15F334365E | |||
| 7480 | 20240726@j.exe | C:\ProgramData\ricka\v2E9L@j\b | binary | |
MD5:9D293F0C66F851D1A602F50DF683CD99 | SHA256:3B22ECA15E2D63A8CB6F7950EA43F3DAEA2A07CEE67BA2AC1B71342B915154EA | |||
| 7480 | 20240726@j.exe | C:\ProgramData\ricka\v2E9L@j\Client.exe | executable | |
MD5:A13C4AFD2B44544D8950F167FE6E766A | SHA256:0A2E1C6A3D6DE252454795BD766E8040FC055A197539836686C71B8D2D320C2F | |||
| 4808 | Client.exe | C:\ProgramData\tor.dat | text | |
MD5:F58DFE59259404FD3E12E4B44F0E3E51 | SHA256:49CDB5658078B52A4901CC597BFD23E1D03A47EE20CCD12B39D567DD92F4C40B | |||
| 7480 | 20240726@j.exe | C:\Users\admin\AppData\Roaming\fcg4h.bat | text | |
MD5:30D6EB22D6AEEC10347239B17B023BF4 | SHA256:659DF6B190A0B92FC34E3A4457B4A8D11A26A4CAF55DE64DFE79EB1276181F08 | |||
| 7480 | 20240726@j.exe | C:\ProgramData\ricka\v2E9L@j\PX.TXT | binary | |
MD5:3005E88FB7D55D32DA7C6F3C2A18498E | SHA256:FC30C532756489B3CCC5E2B0F61FF143AA4AB5E88F3869450618AD1A3D05B2A5 | |||
| 7480 | 20240726@j.exe | C:\ProgramData\ricka\v2E9L@j\v | executable | |
MD5:8561FC9E2B037DA751152490A40A3CC7 | SHA256:CCD67B5ABD5916BA66C2669AB443CCC1D9B583566C9786CB988BBBF06B3D5A44 | |||
| 4808 | Client.exe | C:\Users\admin\Videos\E652BE8@j\Hpppo.exe | executable | |
MD5:A13C4AFD2B44544D8950F167FE6E766A | SHA256:0A2E1C6A3D6DE252454795BD766E8040FC055A197539836686C71B8D2D320C2F | |||
| 4808 | Client.exe | C:\Users\admin\Videos\E652BE8@j\ClientModule.dll | executable | |
MD5:F5BA22F3EB817FD5C23DC5F114DCF79C | SHA256:40D913C97E44E647AE101A71651EDD16A13200B81E2ADC4D06213F15F334365E | |||
| 4808 | Client.exe | C:\Users\admin\Videos\E652BE8@j\VMProtectSDK32.dll | executable | |
MD5:460839680454DAA5DD1B8E83924D7A1E | SHA256:097FFB217EC1E2C305456BBB5822EB4F4C9DD19A6EF09816ED8AC7F19DA08C89 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
43
DNS requests
25
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5864 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4808 | Client.exe | GET | 101 | 143.92.61.34:15628 | http://143.92.61.34:15628/\ | unknown | — | — | unknown |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 92.123.104.6:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3992 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4424 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4424 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4808 | Client.exe | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
4808 | Client.exe | Generic Protocol Command Decode | SURICATA HTTP Request line incomplete |