| File name: | script.exe |
| Full analysis: | https://app.any.run/tasks/1a84b27c-3305-4061-87b6-8df25757c594 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 16:21:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 952DFCB0A569172586C46C3F6B22A3B9 |
| SHA1: | 3ACE06404485C4C4A1A7278B65AA90077A63D831 |
| SHA256: | 6A5BCE1C5911DD7B62C5991F9CC523466F39871FBD9BA02BE87609258144989F |
| SSDEEP: | 98304:uCYzBZBqZVs3Fr5qXd6cGEUJHOnZkSOV0rjjjsyTe26Bb/ncfRkzKVfq7AnYRO4Y:tvfk91881mwe/kil49D96akh |
MALICIOUS
No malicious indicators.SUSPICIOUS
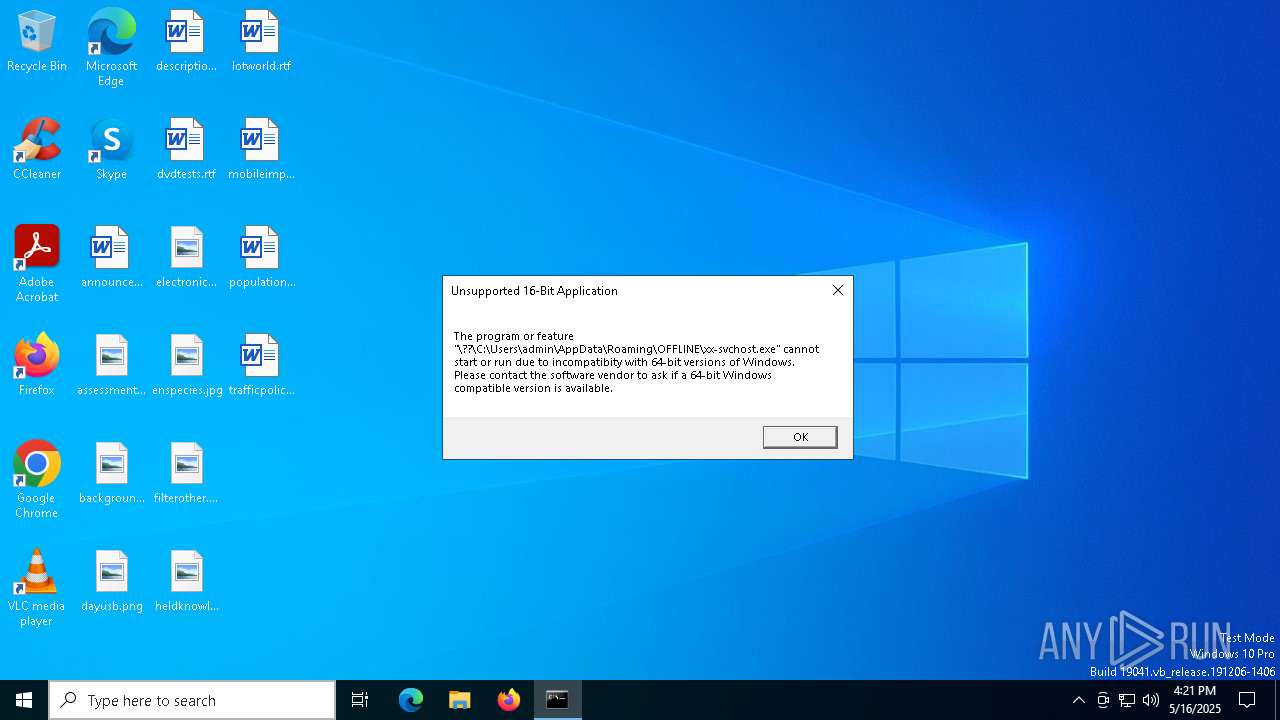
The process creates files with name similar to system file names
- script.exe (PID: 7644)
- script.exe (PID: 7704)
Process drops python dynamic module
- script.exe (PID: 7644)
Application launched itself
- powershell.exe (PID: 7724)
- script.exe (PID: 7644)
Loads Python modules
- script.exe (PID: 7704)
Base64-obfuscated command line is found
- script.exe (PID: 7704)
- powershell.exe (PID: 7724)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 7724)
- script.exe (PID: 7704)
- cmd.exe (PID: 5680)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 7724)
- script.exe (PID: 7704)
Process drops legitimate windows executable
- script.exe (PID: 7644)
Executable content was dropped or overwritten
- script.exe (PID: 7644)
- script.exe (PID: 7704)
The process drops C-runtime libraries
- script.exe (PID: 7644)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 5680)
Starts CMD.EXE for commands execution
- script.exe (PID: 7704)
There is functionality for taking screenshot (YARA)
- script.exe (PID: 7644)
- script.exe (PID: 7704)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 7352)
Executing commands from a ".bat" file
- script.exe (PID: 7704)
INFO
Create files in a temporary directory
- script.exe (PID: 7644)
Reads the computer name
- script.exe (PID: 7644)
Checks supported languages
- script.exe (PID: 7644)
- script.exe (PID: 7704)
The sample compiled with english language support
- script.exe (PID: 7644)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 8068)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8068)
Creates files or folders in the user directory
- script.exe (PID: 7704)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7352)
PyInstaller has been detected (YARA)
- script.exe (PID: 7644)
- script.exe (PID: 7704)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- script.exe (PID: 7704)
Checks proxy server information
- slui.exe (PID: 1180)
Reads the software policy settings
- slui.exe (PID: 1180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:16 16:19:27+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 173568 |
| InitializedDataSize: | 194560 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce30 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
155
Monitored processes
14
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5404 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 5680 | cmd.exe /c C:\Users\admin\AppData\Roaming\OFFLINE\dec-excute-main.bat | C:\Windows\System32\cmd.exe | — | script.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7352 | powershell -NoProfile -Command "$key = 'now';" "$content = [System.IO.File]::ReadAllBytes(\"C:\Users\admin\AppData\Roaming\OFFLINE\xx-svchost.exe.dead\");" "$keyBytes = [System.Text.Encoding]::UTF8.GetBytes($key);" "for ($i = 0; $i -lt $content.Length; $i++) {" " $content[$i] = $content[$i] -bxor $keyBytes[$i % $keyBytes.Length];" "}" "[System.IO.File]::WriteAllBytes(\"C:\Users\admin\AppData\Roaming\OFFLINE\xx-svchost.exe.dead\", $content);" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7396 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 7520 | "C:\Users\admin\AppData\Local\Temp\script.exe" | C:\Users\admin\AppData\Local\Temp\script.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7644 | "C:\Users\admin\AppData\Local\Temp\script.exe" | C:\Users\admin\AppData\Local\Temp\script.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7704 | "C:\Users\admin\AppData\Local\Temp\script.exe" | C:\Users\admin\AppData\Local\Temp\script.exe | script.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
14 028
Read events
14 028
Write events
0
Delete events
0
Modification events
Executable files
109
Suspicious files
5
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_Salsa20.pyd | executable | |
MD5:62959C0AB456D56FFA1D140771FCFC2C | SHA256:82BBCEAA3D6AB29E1B80F7C1594DBCAC0EA7571DB821BA7A344770D8711BE282 | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_chacha20.pyd | executable | |
MD5:CCC8A9191FB20271491FECB71827528B | SHA256:C8A097FA3A1B4E18844D1D24BBD6A7572774BA41859111DD3D5526FA003E6B72 | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_raw_aes.pyd | executable | |
MD5:92544E66B8A0F0D6AF0028D88CEC6C9E | SHA256:2809202F930BD4B5D3AE89F3296CDF8AE24B61C95D9F3A40F448015EFF2218B3 | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_raw_ctr.pyd | executable | |
MD5:96CDB3E5D9AA4AC2227AEEAF9327AD27 | SHA256:6ED9AC55EFBCEAF7355E268268C9BAA8BF57458180DDAF80982933648DE3946D | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_raw_arc2.pyd | executable | |
MD5:3CC3EF2F9D530966158F096F66A5E47D | SHA256:505CCAB30197A1E0F724B7868BBF4C34957FBFE3BE0AB161195D1FCD7BC73E61 | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_raw_cfb.pyd | executable | |
MD5:5699C1E209D722B3CF45D0CF1F3B4318 | SHA256:75095D841809A285813D4D4DF0063F74084040C7BD492264290DBA4D52E24A24 | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_raw_cbc.pyd | executable | |
MD5:3FD28E31D907C7FFF1AF815DFD76E952 | SHA256:7F649276BCBEDABC4AA409DB28631D68C55CB602D309BDE1CB09D11D8CDA9808 | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_raw_cast.pyd | executable | |
MD5:902F3B0D233FF262A9037ACCF2BBCCA7 | SHA256:D5B1E41CE19268FD7E4B4273BD5F94B1D30C3F705465A1AC66553757A2FC9C71 | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Hash\_BLAKE2b.pyd | executable | |
MD5:94397C5EC27EC24BDB0891A7DF749022 | SHA256:2FF06D0F02BEEE261F9D60FF9BCD6C2EFF4D39DB99A3A36407B37DF18ADE93C5 | |||
| 7644 | script.exe | C:\Users\admin\AppData\Local\Temp\_MEI76442\Cryptodome\Cipher\_raw_ecb.pyd | executable | |
MD5:F80CE894517427B80BB308A9C18C6028 | SHA256:3B2D667316667BE58BB2CC61EBB77DED2DBC932C3D2BE65F1EFCC8FBF3E39382 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
39
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
900 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
900 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |