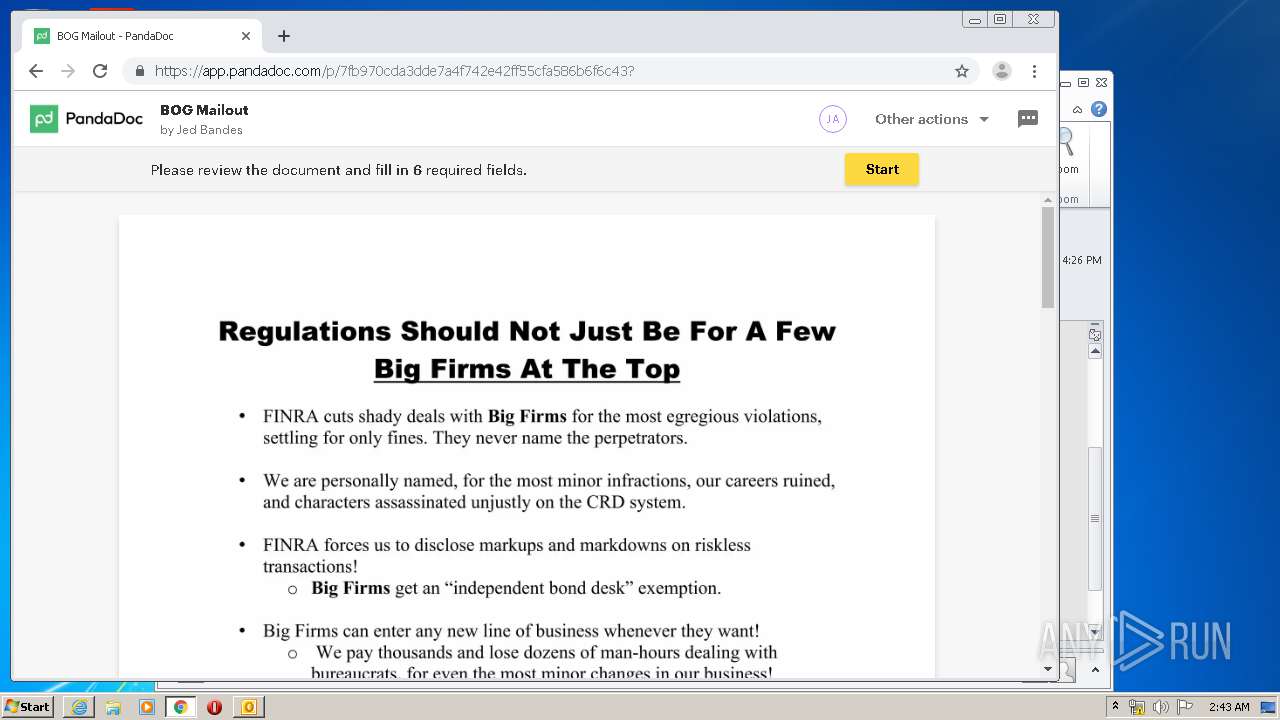
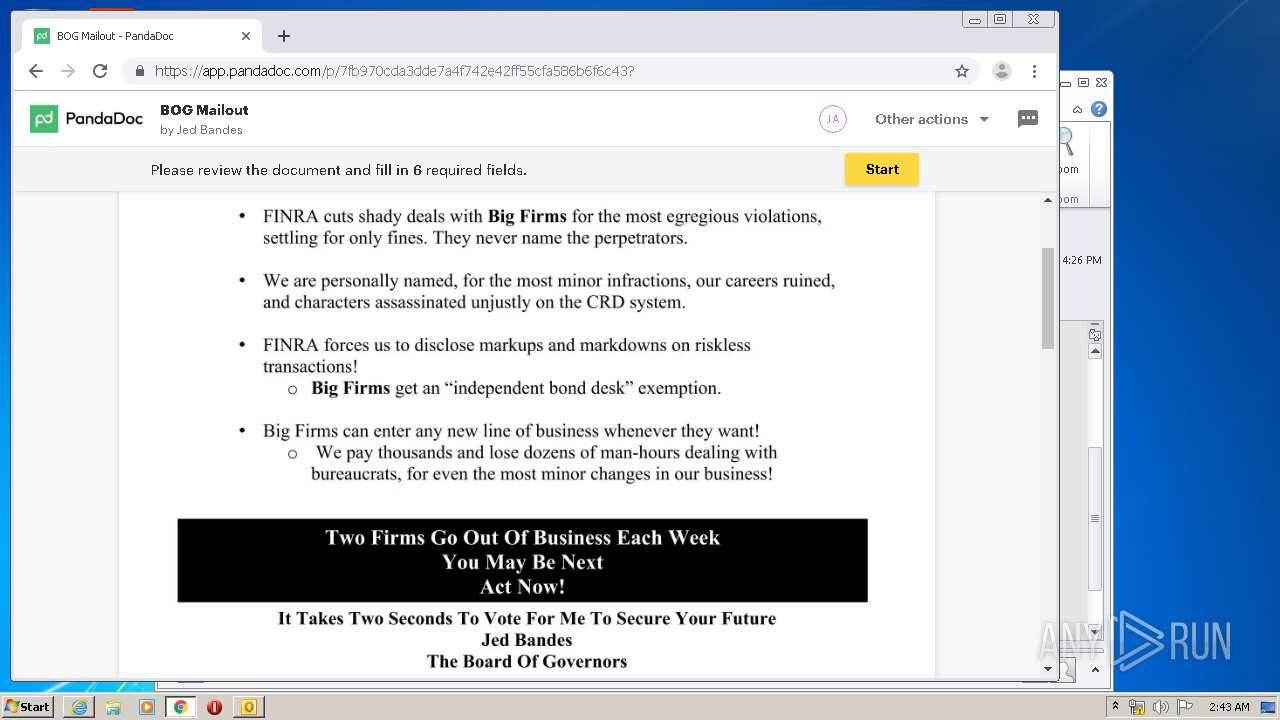
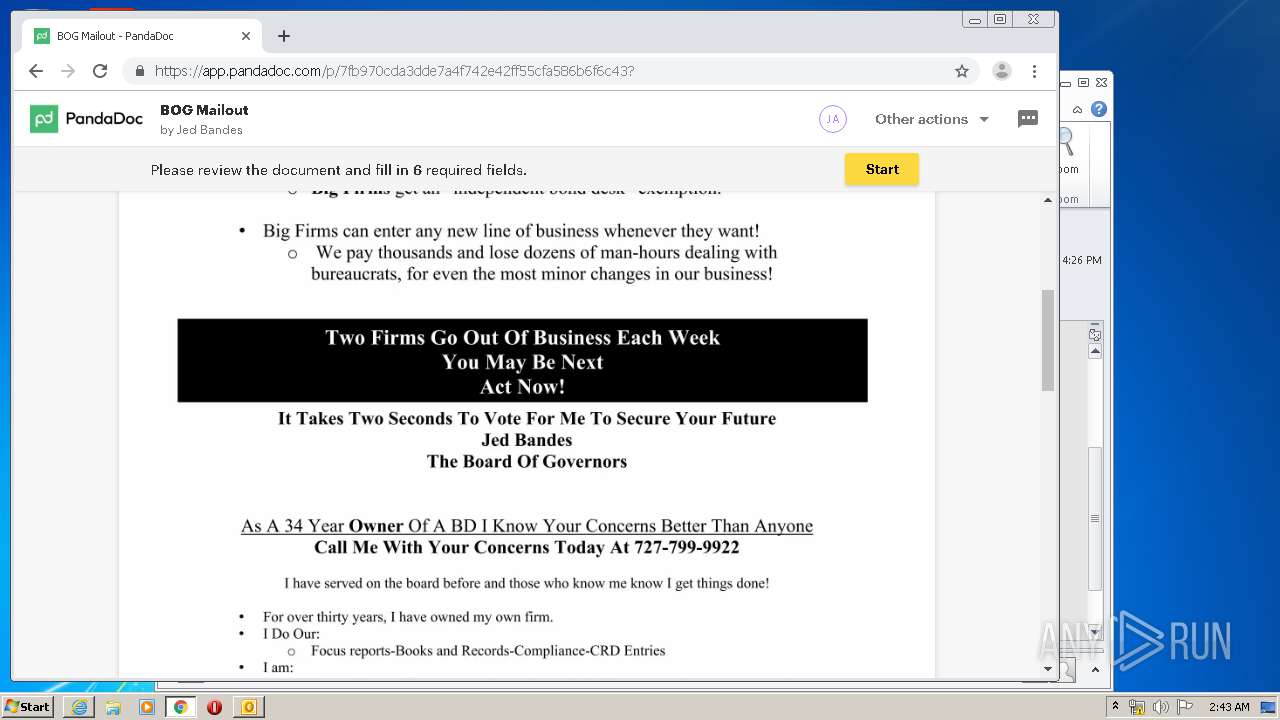
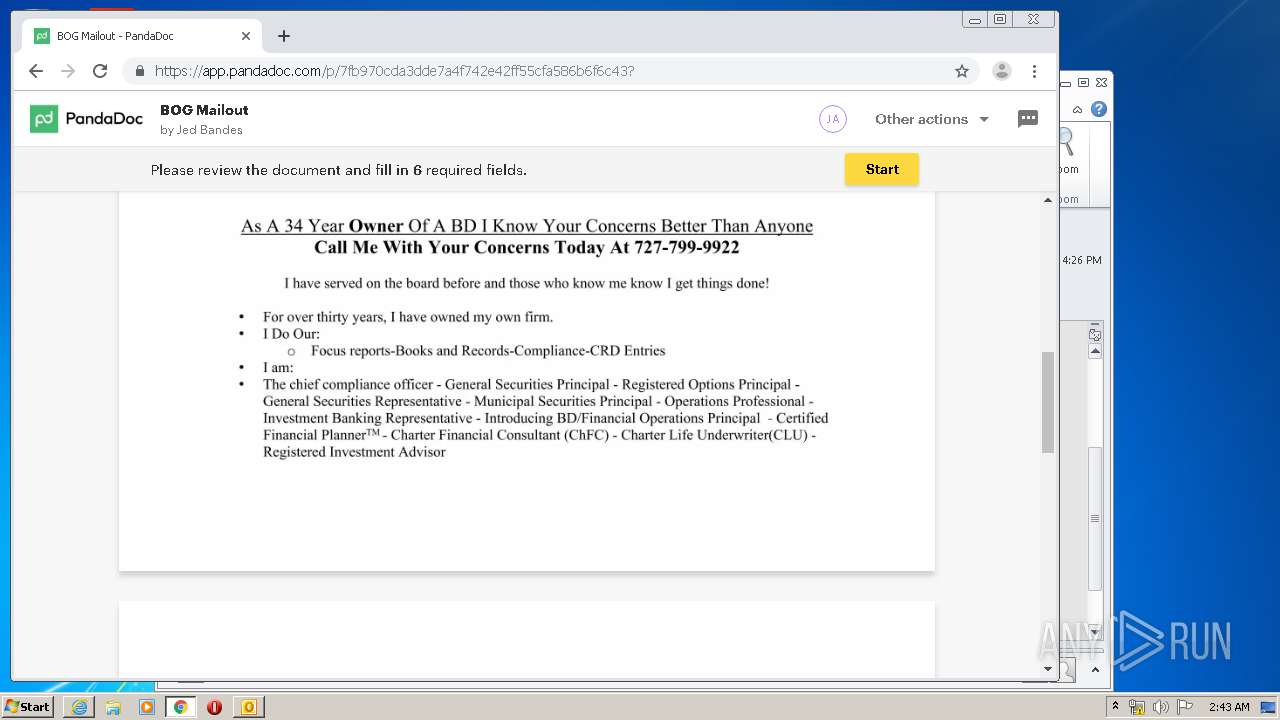
| File name: | cjgqc431.eml |
| Full analysis: | https://app.any.run/tasks/904ad1b5-e069-4f43-ba40-171f36d2569d |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 01:42:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 7B8EF2EB5FC209EA866D7F10C86B886C |
| SHA1: | 52E5B19CA457FB9AF35E123228C21746F64EC2BA |
| SHA256: | 6A52F5EB1AF06CC21F99DE8724EA04662FFB10935F7CECC247C193414162A5B2 |
| SSDEEP: | 384:cR65ubp1u+wieEsvxN0Hp/vF6Qfl9UGrq31QguR:U1d6s3q1uR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2316)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2316)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2316)
Modifies files in Chrome extension folder
- chrome.exe (PID: 932)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2316)
Application launched itself
- iexplore.exe (PID: 2872)
- chrome.exe (PID: 932)
Manual execution by user
- chrome.exe (PID: 932)
Changes internet zones settings
- iexplore.exe (PID: 2872)
Reads internet explorer settings
- iexplore.exe (PID: 2696)
Reads Internet Cache Settings
- iexplore.exe (PID: 2696)
- iexplore.exe (PID: 2872)
Reads the hosts file
- chrome.exe (PID: 932)
- chrome.exe (PID: 2044)
Reads settings of System Certificates
- iexplore.exe (PID: 2696)
- chrome.exe (PID: 2044)
- iexplore.exe (PID: 2872)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2872)
Changes settings of System certificates
- iexplore.exe (PID: 2872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
74
Monitored processes
34
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=871317848722236717 --mojo-platform-channel-handle=3736 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9633794036494207313 --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3924 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8809365817447090938 --mojo-platform-channel-handle=3152 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16048749823699322710 --mojo-platform-channel-handle=3836 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10006196731238505080 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2452 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17406478307357411208 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3396 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2096921356099824385 --mojo-platform-channel-handle=2620 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13756845072089002241 --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4240 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,5169022334238641342,11943846319091531275,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=13746828332416759395 --mojo-platform-channel-handle=1648 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
8 329
Read events
2 068
Write events
4 499
Delete events
1 762
Modification events
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
86
Text files
295
Unknown types
55
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2316 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9983.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2696 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabC258.tmp | — | |
MD5:— | SHA256:— | |||
| 2696 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarC259.tmp | — | |
MD5:— | SHA256:— | |||
| 2316 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2316 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:— | SHA256:— | |||
| 2696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FC5A820A001B41D68902E051F36A5282_2221F405FB6357E9E5DDBB07F6192674 | der | |
MD5:— | SHA256:— | |||
| 2696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 2696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FC5A820A001B41D68902E051F36A5282_BE8D2F02AA6642F4C148C8FAC1932309 | der | |
MD5:— | SHA256:— | |||
| 2696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
121
DNS requests
70
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2316 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2696 | iexplore.exe | GET | 200 | 52.222.157.23:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
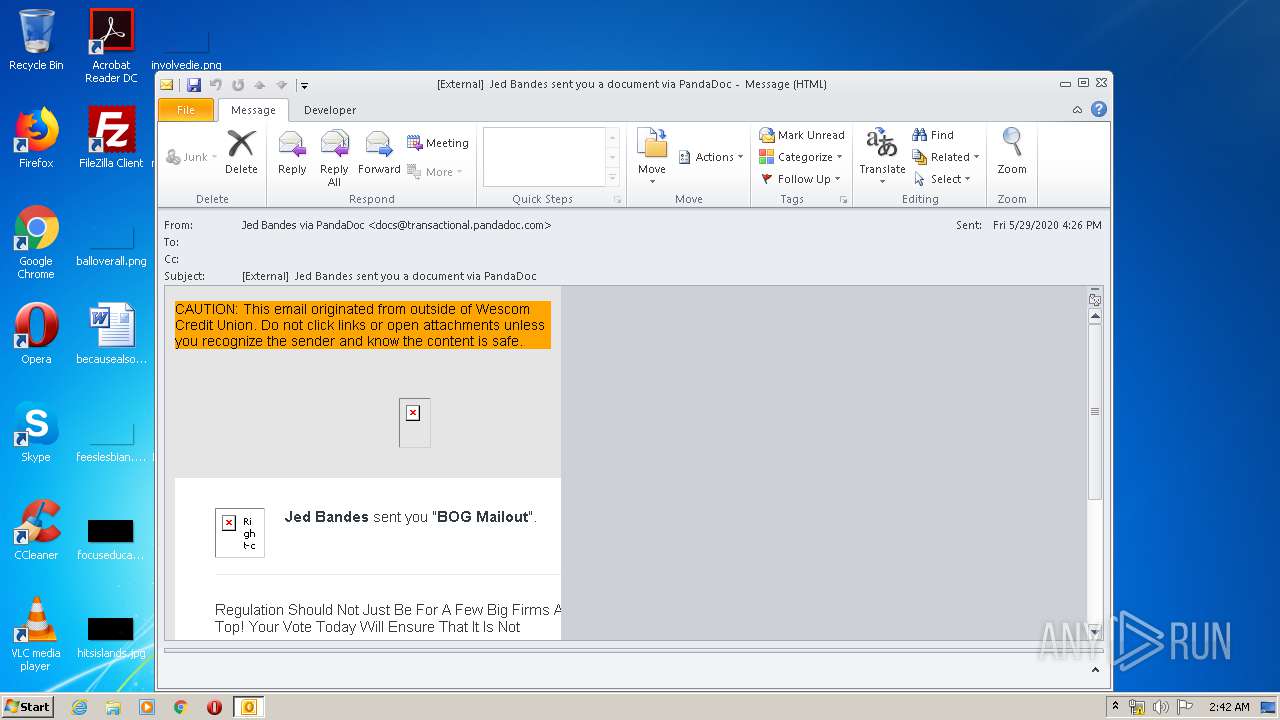
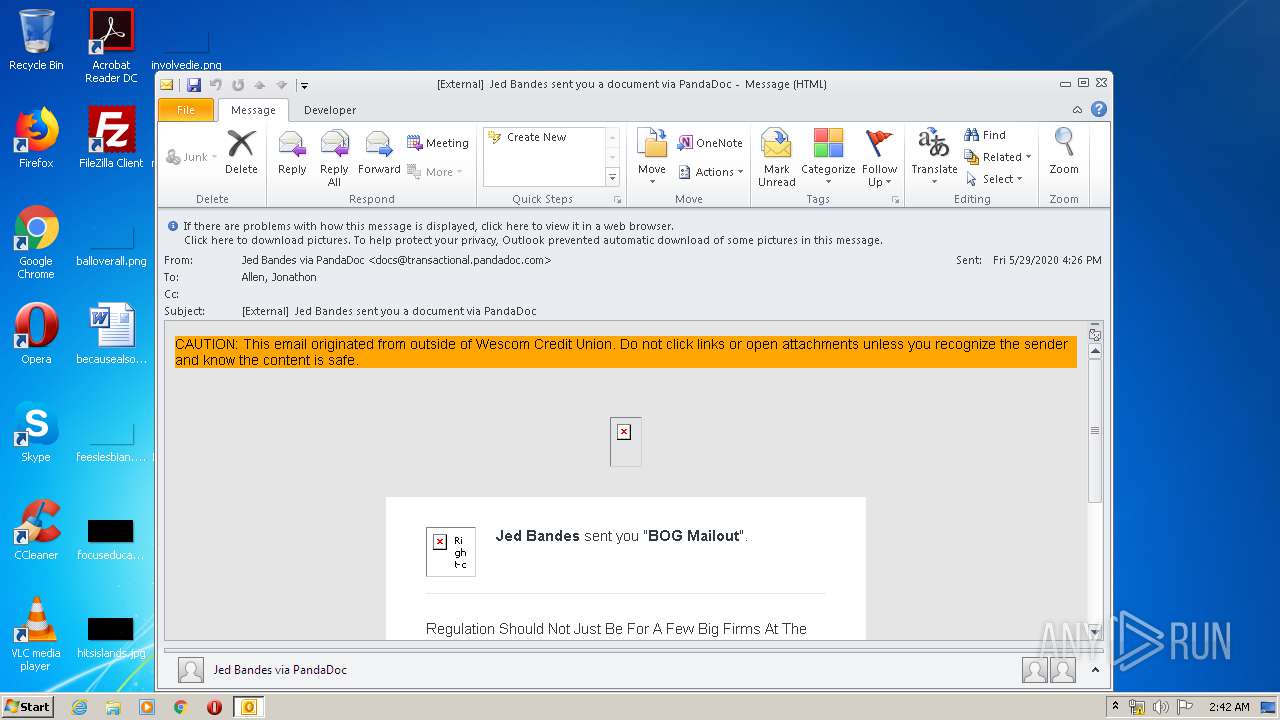
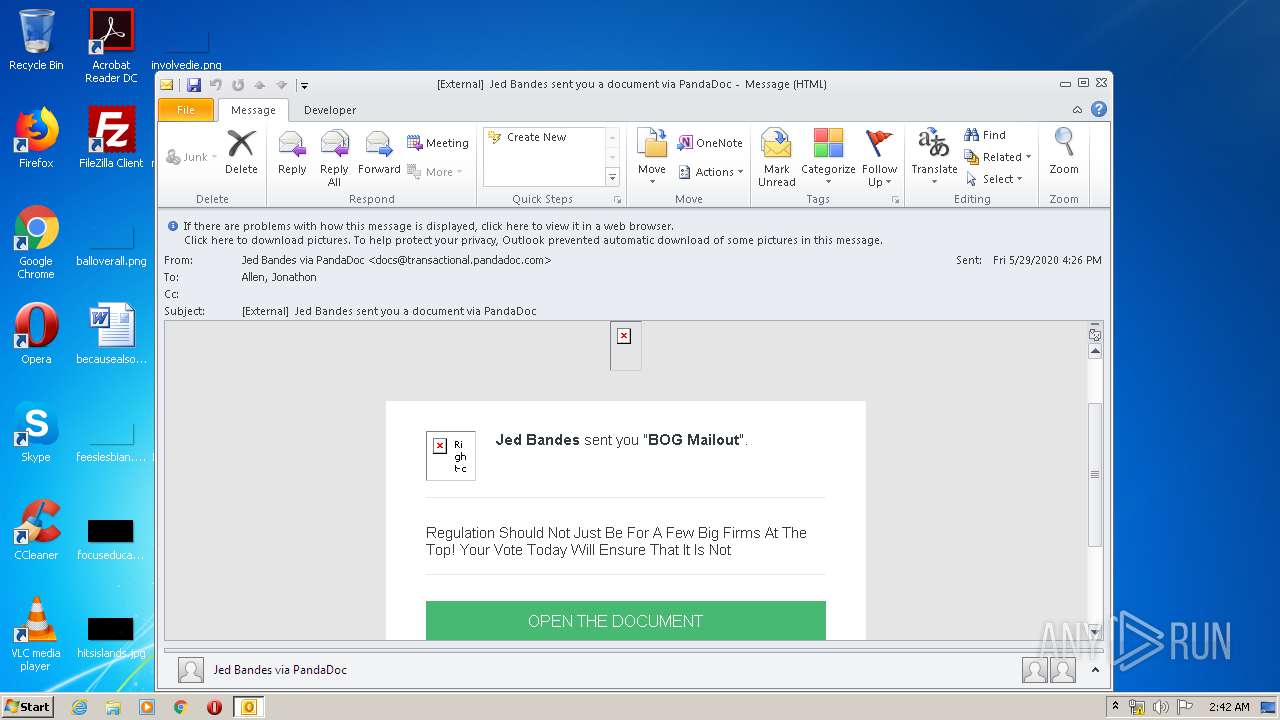
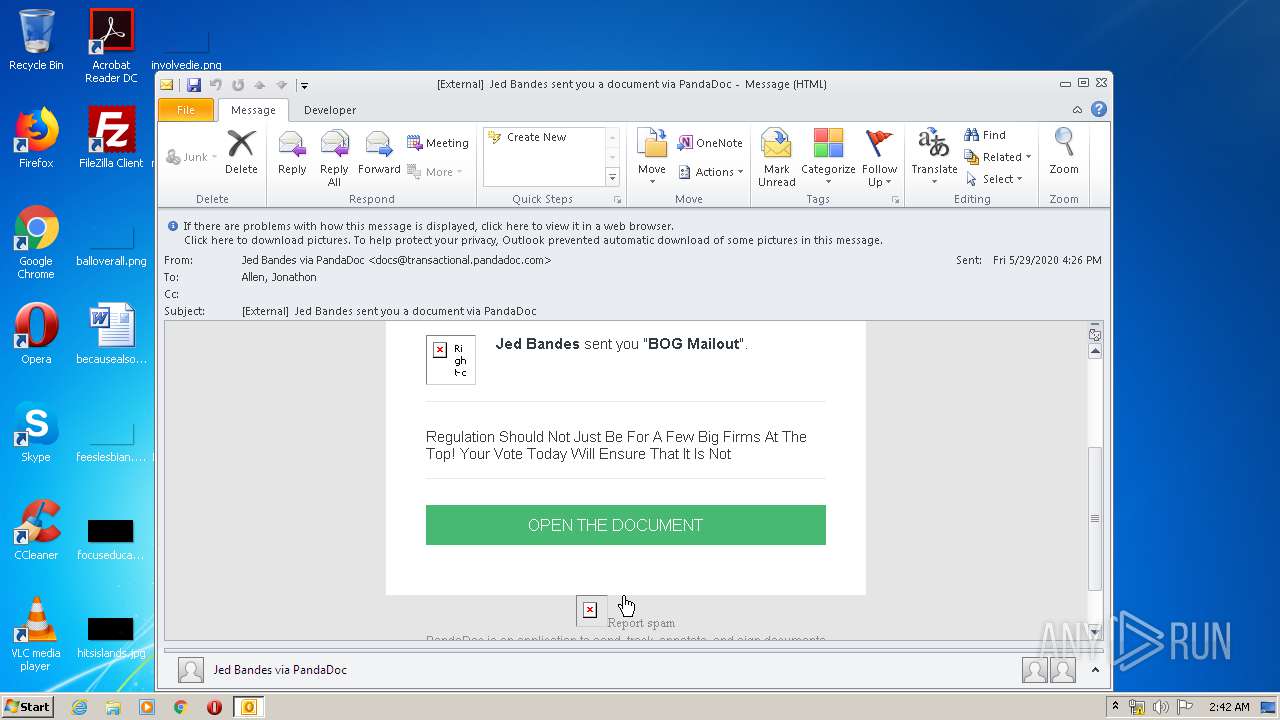
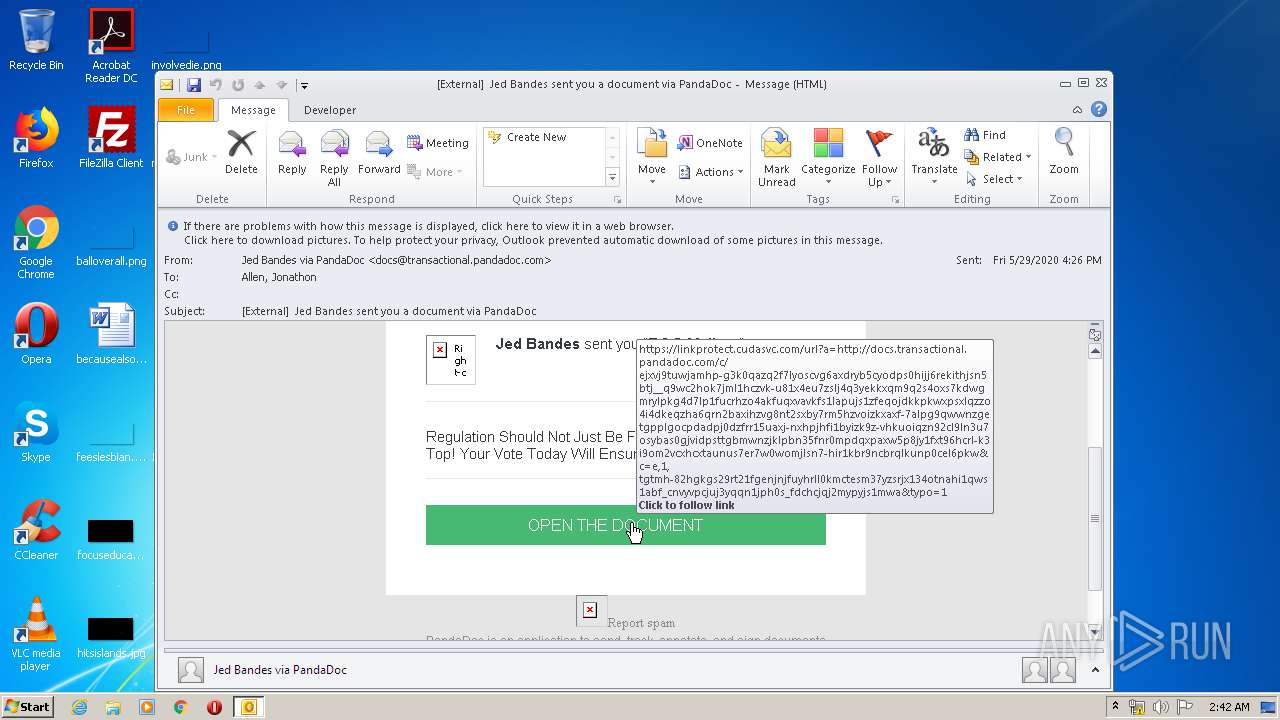
2696 | iexplore.exe | GET | 302 | 52.1.14.103:80 | http://docs.transactional.pandadoc.com/c/eJxVj9tuwjAMhp-G3K0qaZq2F7lYoSCVg6axDrYb5CYOdPS0Hijj6RekITHJsn5btj__Q9Wc2hok7jMl1hcZvk-u81X4EU7ZsLj4Q3yekkxQm9q2S4OxS7kdWGMrYlPKg4D7Lp1FUcRHzO4aKFuQXVaVkFs1lApUJS1ZFeQoJDKKPkWXpsxLqZZO4I4DkEqZhA6QrN2bAxIhzVG8NT2SXBy7rm5HzvOIzkxAXf-7alpG9QWWnZGeTgPPlgocpdADpj0DZFRr15UaXJ-nXHPJHFI1ByizK9z-vHkuoIqzn92cL9ln3U7OsYbaS0gjviDPsTTGBmwNzjKLpBN35FNr0mPdQXPAxw5p8Jy1fxT96hcrL-k3i9Om2vCXHcXtaUnus7eR7w0WoMJLsN7-HIr1kBR9nCBRQlKUnP0CEL6PKw | US | html | 355 b | malicious |
2696 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2696 | iexplore.exe | GET | 200 | 52.222.157.3:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAS8VnSzwVKQtjWbxZiQsAk%3D | US | der | 471 b | whitelisted |
2696 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
2696 | iexplore.exe | GET | 200 | 52.222.157.28:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2696 | iexplore.exe | GET | 200 | 52.222.157.76:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2696 | iexplore.exe | GET | 200 | 52.222.157.60:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
2696 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2316 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2696 | iexplore.exe | 52.10.137.7:443 | app.pandadoc.com | Amazon.com, Inc. | US | unknown |
2696 | iexplore.exe | 52.222.157.76:80 | o.ss2.us | Amazon.com, Inc. | US | whitelisted |
2696 | iexplore.exe | 18.156.180.118:443 | linkprotect.cudasvc.com | Massachusetts Institute of Technology | US | unknown |
2696 | iexplore.exe | 52.222.157.28:80 | o.ss2.us | Amazon.com, Inc. | US | whitelisted |
2696 | iexplore.exe | 52.222.157.60:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
2696 | iexplore.exe | 52.222.157.23:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
2696 | iexplore.exe | 52.222.157.3:80 | ocsp.sca1b.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
2696 | iexplore.exe | 52.222.157.225:443 | dr79nymq4x8i9.cloudfront.net | Amazon.com, Inc. | US | whitelisted |
2696 | iexplore.exe | 2.16.186.59:443 | use.typekit.net | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
linkprotect.cudasvc.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
docs.transactional.pandadoc.com |
| malicious |
app.pandadoc.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |