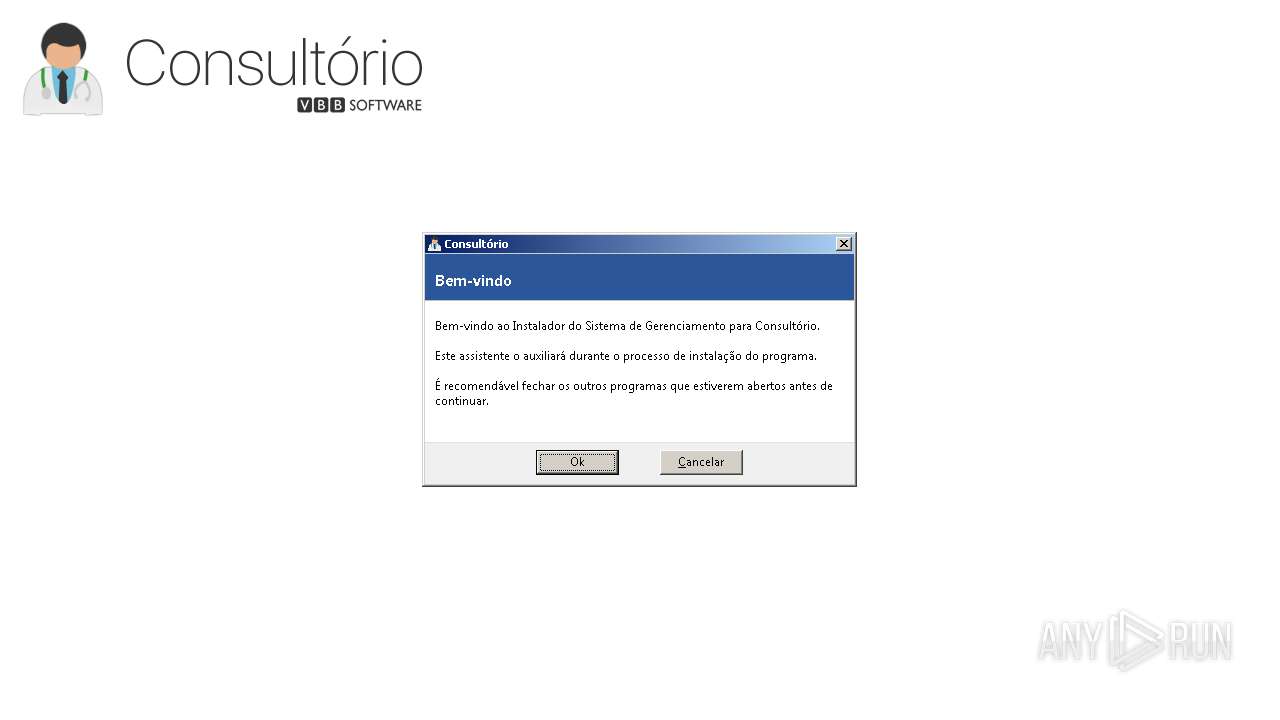
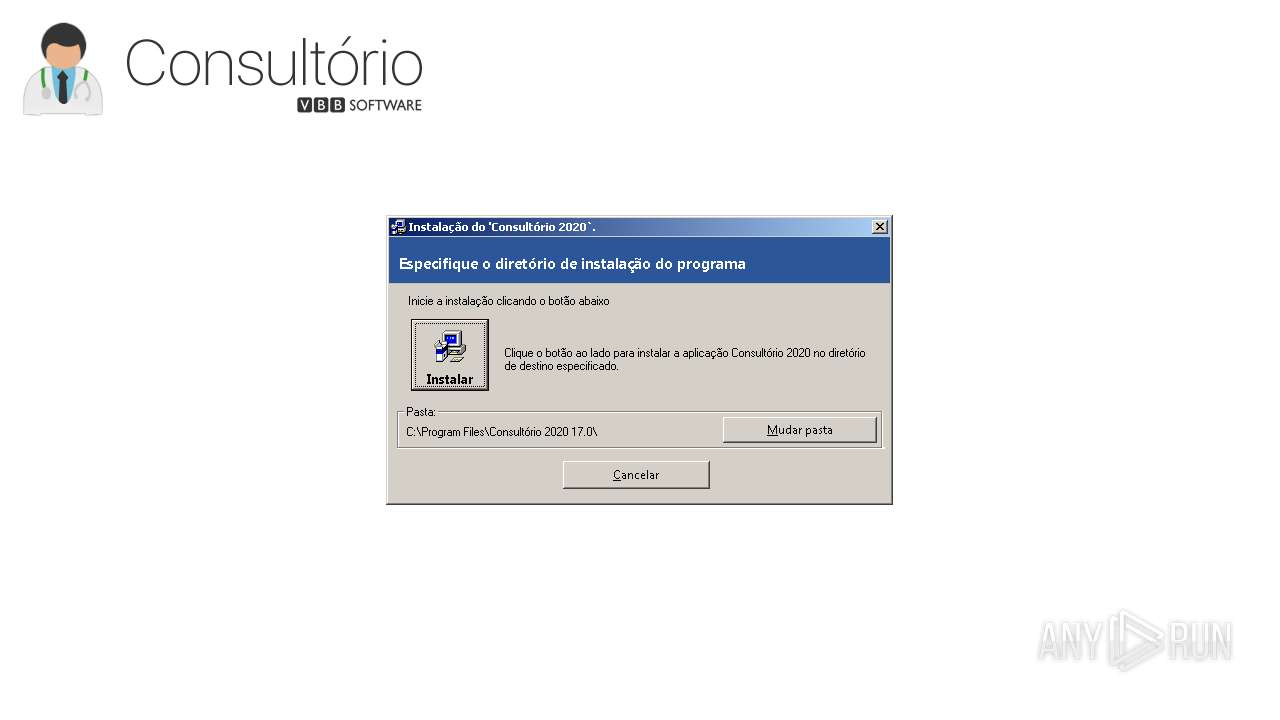
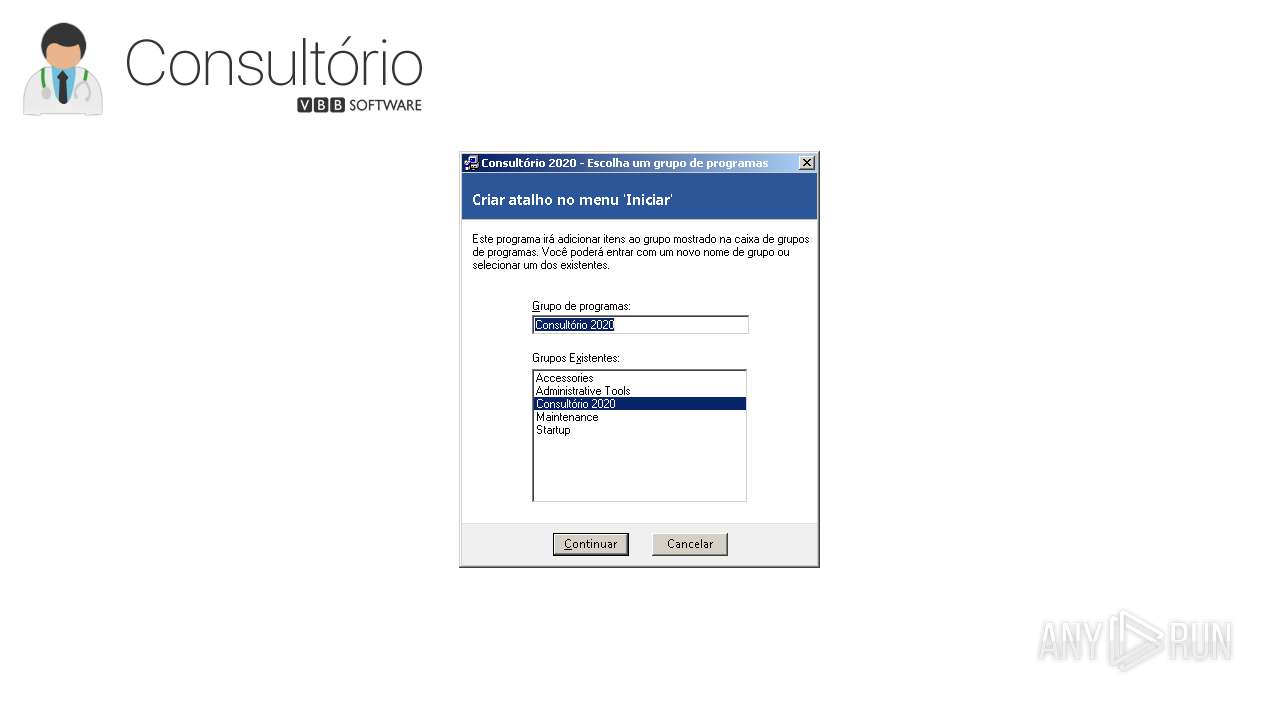
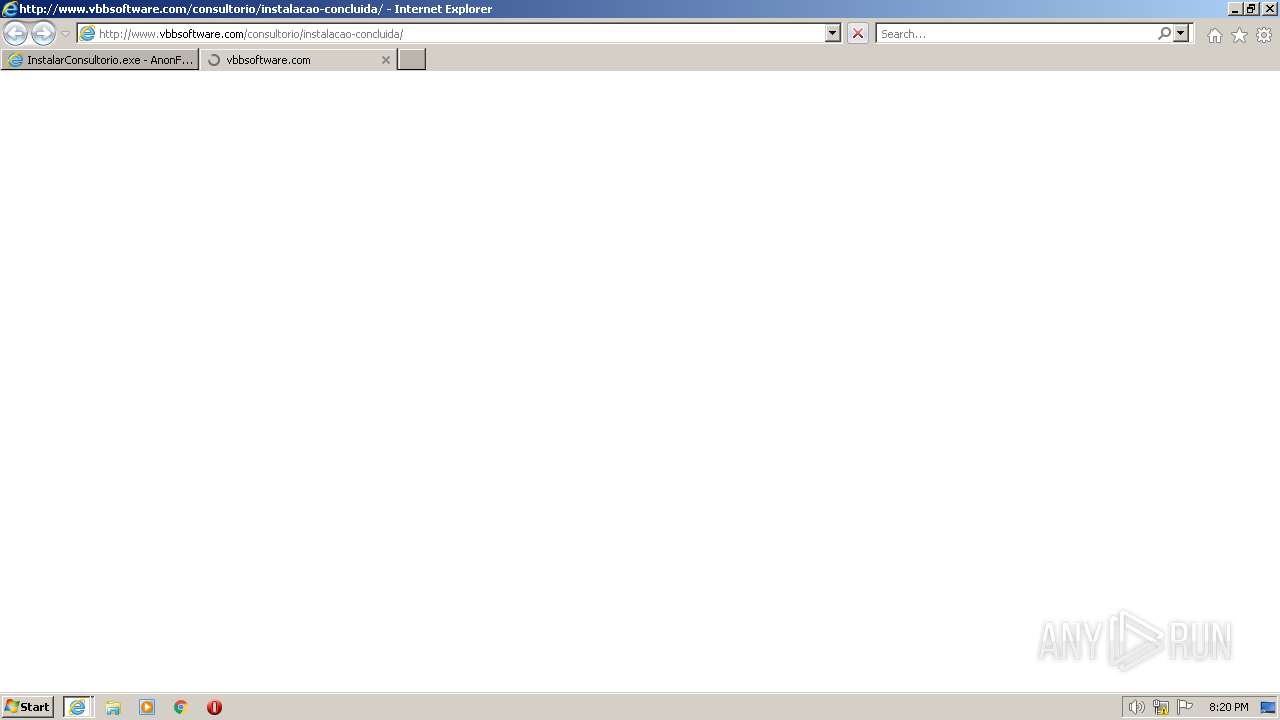
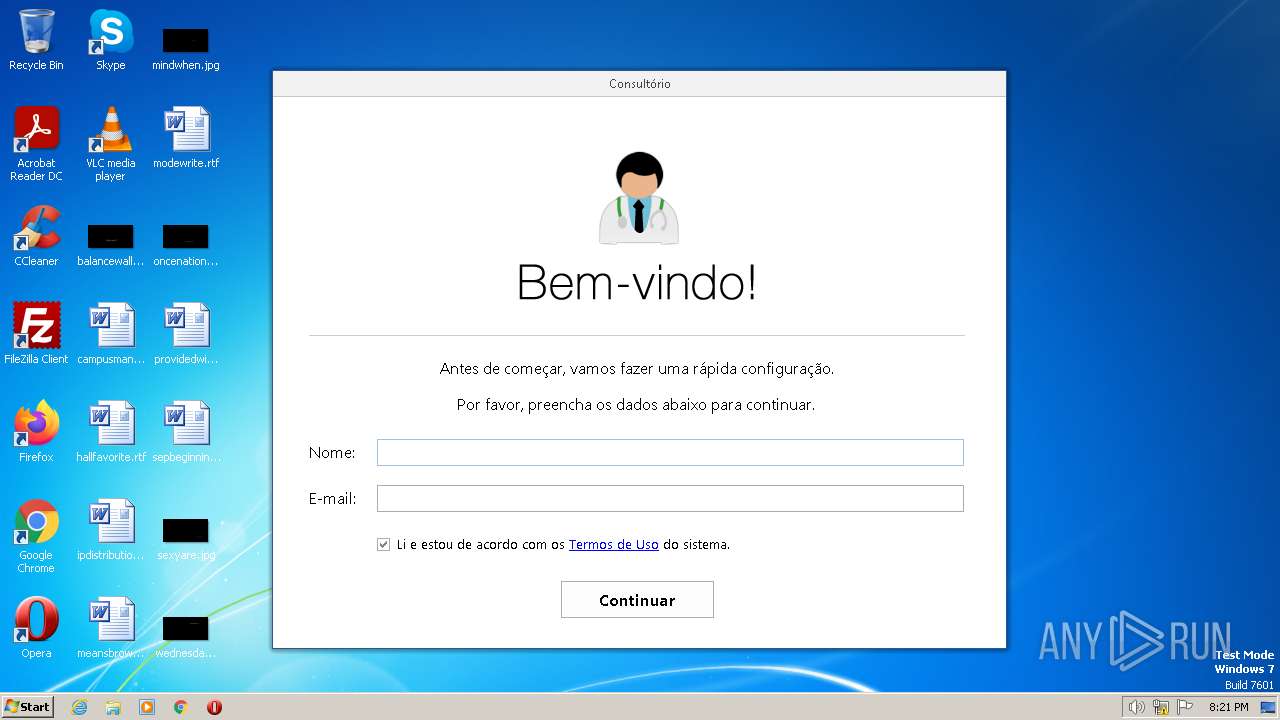
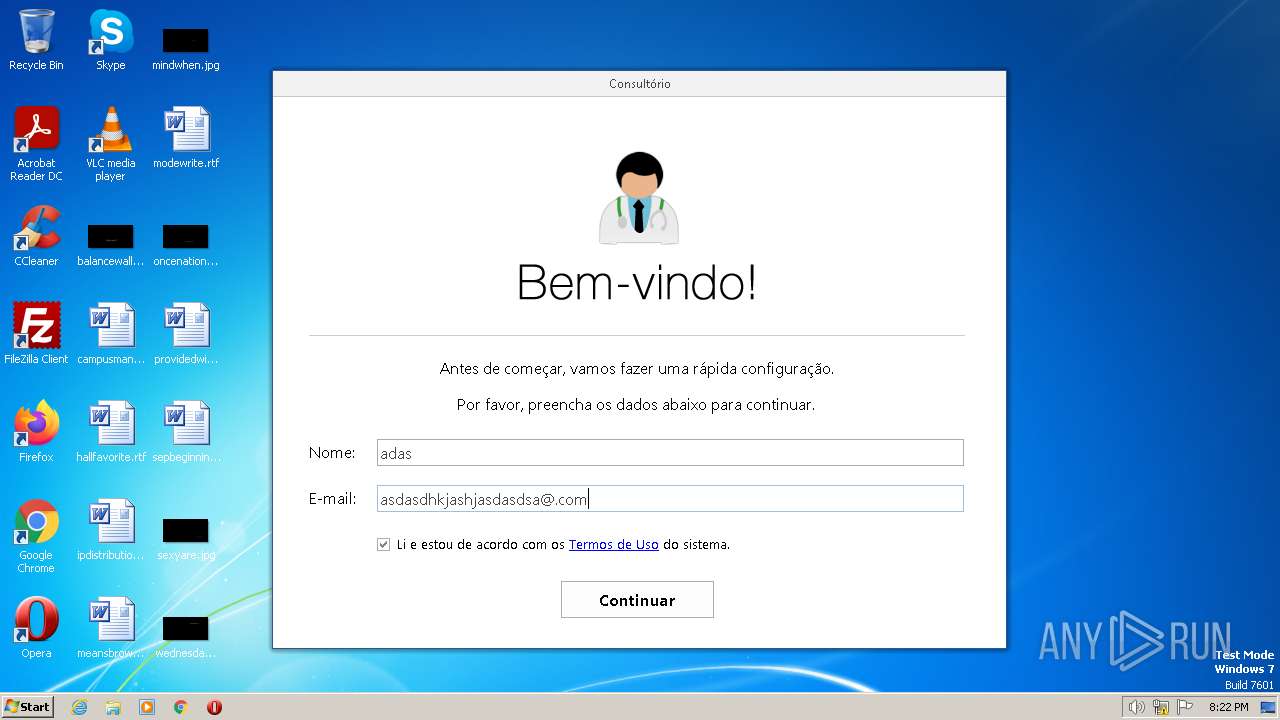
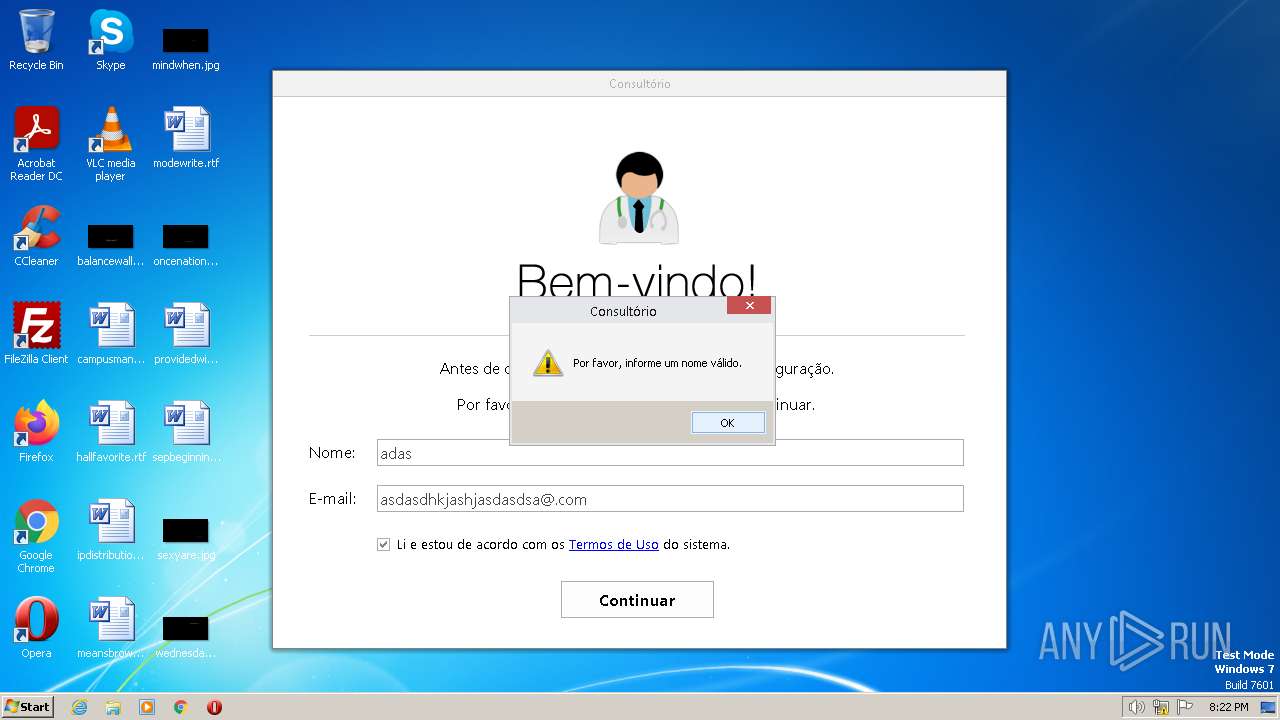
| URL: | https://anonfiles.com/t9fa70rbz3/InstalarConsultorio_exe |
| Full analysis: | https://app.any.run/tasks/31147fec-0353-4b73-ae65-a2337387a46f |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2023, 19:18:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 554269BFA28E48AFB7395439B581CA7F |
| SHA1: | 9ABEF757FB1E0824319CB01E9E557B5FDCB21D9C |
| SHA256: | 6A44F928C920485FDD13BBDB574FB5DF42918458A9BDF1BD8C4191C410FFDE52 |
| SSDEEP: | 3:N8M2KcdP+TQl:2M2HdP4Ql |
MALICIOUS
Create files in the Startup directory
- setup.exe (PID: 3444)
Creates a writable file the system directory
- setup.exe (PID: 3444)
- Setup1.exe (PID: 3824)
SUSPICIOUS
Executable content was dropped or overwritten
- mdac_typ.exe (PID: 2400)
- Setup1.exe (PID: 3824)
- InstalarConsultorio.exe (PID: 3140)
- setup.exe (PID: 3444)
Creates/Modifies COM task schedule object
- Setup1.exe (PID: 3824)
Searches for installed software
- Setup1.exe (PID: 3824)
Reads the Internet Settings
- Setup1.exe (PID: 3824)
- Consult.exe (PID: 3612)
INFO
Create files in a temporary directory
- iexplore.exe (PID: 1604)
- iexplore.exe (PID: 3932)
- setup.exe (PID: 3444)
- mdac_typ.exe (PID: 2400)
- Setup1.exe (PID: 3824)
- Consult.exe (PID: 3612)
- InstalarConsultorio.exe (PID: 3140)
Reads the computer name
- setup.exe (PID: 3444)
- Setup1.exe (PID: 3824)
- Consult.exe (PID: 3612)
The process checks LSA protection
- setup.exe (PID: 3444)
- Setup1.exe (PID: 3824)
- Consult.exe (PID: 3612)
Creates files or folders in the user directory
- setup.exe (PID: 3444)
Checks supported languages
- Setup1.exe (PID: 3824)
- InstalarConsultorio.exe (PID: 3140)
- setup.exe (PID: 2520)
- dasetup.exe (PID: 3696)
- mdac_typ.exe (PID: 2400)
- Consult.exe (PID: 3612)
- setup.exe (PID: 3444)
Executable content was dropped or overwritten
- iexplore.exe (PID: 1604)
- iexplore.exe (PID: 3932)
Application launched itself
- iexplore.exe (PID: 3932)
Reads the machine GUID from the registry
- Setup1.exe (PID: 3824)
- Consult.exe (PID: 3612)
Reads mouse settings
- Setup1.exe (PID: 3824)
Creates files in the program directory
- Setup1.exe (PID: 3824)
Manual execution by a user
- Consult.exe (PID: 3612)
Checks proxy server information
- Consult.exe (PID: 3612)
The process uses the downloaded file
- iexplore.exe (PID: 3932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
11
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3932 CREDAT:3872032 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3932 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2400 | C:\Users\admin\AppData\Local\Temp\msftqws.pdw\mdac_typ.exe /q:a /c:"setup.exe /QN1" | C:\Users\admin\AppData\Local\Temp\msftqws.pdw\mdac_typ.exe | Setup1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 2.50.4403.12 Modules
| |||||||||||||||
| 2520 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe /QN1 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | — | mdac_typ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2608 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\InstalarConsultorio.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\InstalarConsultorio.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3140 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\InstalarConsultorio.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\InstalarConsultorio.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3444 | .\setup.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\setup.exe | InstalarConsultorio.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Bootstrap for Visual Basic Setup Toolkit Exit code: 0 Version: 6.00.8804 Modules
| |||||||||||||||
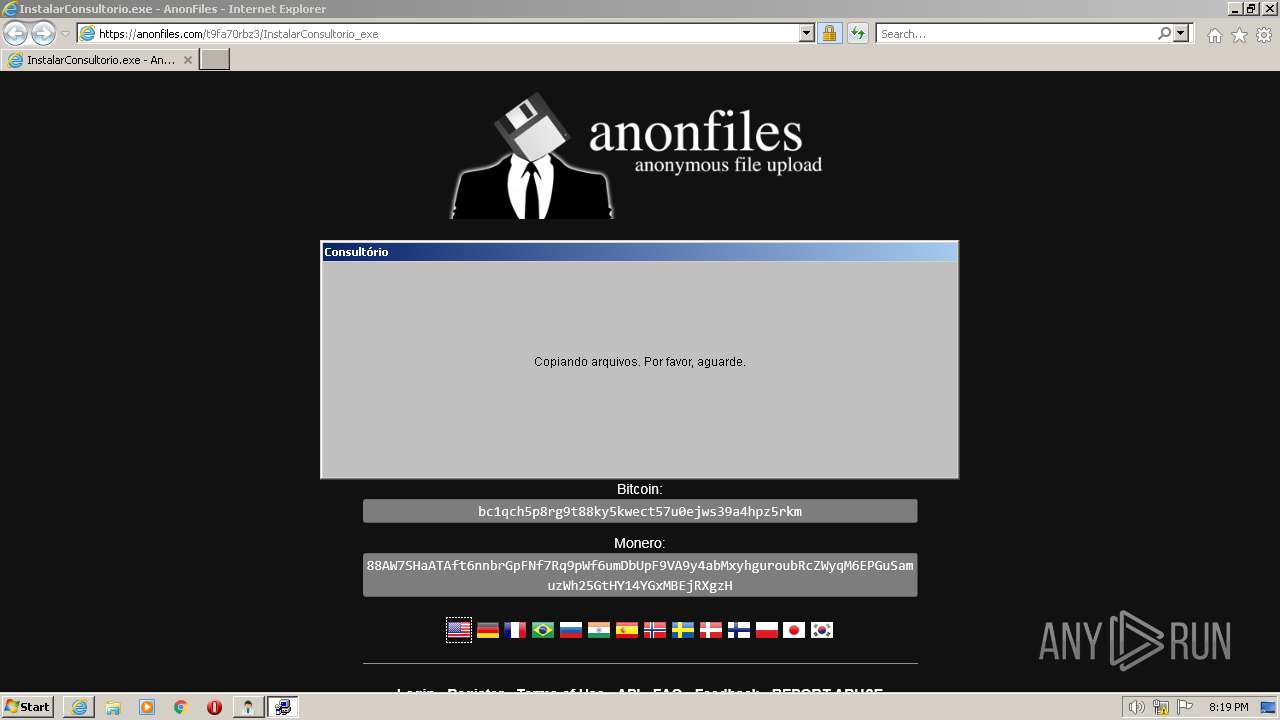
| 3612 | "C:\Program Files\Consultório 2020 17.0\Consult.exe" | C:\Program Files\Consultório 2020 17.0\Consult.exe | explorer.exe | ||||||||||||
User: admin Company: VBB Software Integrity Level: MEDIUM Description: Sistema de Gerenciamento para Consultório Exit code: 0 Version: 17.00 Modules
| |||||||||||||||
| 3696 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dasetup.exe /Q /N | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dasetup.exe | — | setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3824 | C:\WINDOWS\Setup1.exe "C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\" "C:\WINDOWS\ST6UNST.000" "C:\WINDOWS\st6unst.exe" | C:\Windows\Setup1.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic 6.0 Setup Toolkit Exit code: 0 Version: 6.00.8450 Modules
| |||||||||||||||
Total events
53 216
Read events
52 450
Write events
468
Delete events
298
Modification events
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
474
Suspicious files
138
Text files
2 118
Unknown types
79
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\br[1].png | image | |
MD5:6A5938D2E7F7D6F4026D6EB1B4B4F2CD | SHA256:0AB6C46E677FA7E49B6344FCDE39C06FF6C014D9163571CDB36F8B5FC59C17EB | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:F00B5D9B3A99FD5BB8375BC7C5931AA0 | SHA256:29AC3EDD3D150567A3CADE0E3BD134A1A78822D1E44A2F8F3C8C6CEBBC3DA9D2 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\de[1].png | image | |
MD5:9F8CC07C258BCD2DE0C7900861E20FFC | SHA256:07CD5A4CAD20604F77DCED9C7D8A92CA9AE3321718E5A1935296E4D75F921A19 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab19AF.tmp | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A11DD062BD6941BA904CE326B76441E7 | binary | |
MD5:D5316B80011376FCC4AEF5A2FD2B9388 | SHA256:424A261EF15B33CED20FAC41A4701CE472931807F86D0B2F1E4B2B25FE3B4130 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:36B67BE9A16B7A74A95AB64DD3597014 | SHA256:1F4151A39608794DFFE248F1115ACFC8F25B279A1EC6B65FE049B973DF63D250 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar19B2.tmp | cat | |
MD5:4FF65AD929CD9A367680E0E5B1C08166 | SHA256:C8733C93CC5AAF5CA206D06AF22EE8DBDEC764FB5085019A6A9181FEB9DFDEE6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
51
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
568 | iexplore.exe | GET | — | 35.208.72.84:80 | http://www.vbbsoftware.com/consultorio/instalacao-concluida/ | US | — | — | unknown |
3612 | Consult.exe | GET | — | 35.208.72.84:80 | http://www.vbbsoftware.com/ccad_auto.php?nome=adas%20asdasd&email=asdasdhkjashjasdasdsa@asasasas.com&time=30121899202335 | US | — | — | unknown |
1604 | iexplore.exe | GET | 200 | 108.138.2.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
1604 | iexplore.exe | GET | 200 | 23.56.202.135:80 | http://x1.c.lencr.org/ | GB | der | 717 b | whitelisted |
1604 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4b6ce48912f6c30d | US | compressed | 4.70 Kb | whitelisted |
1604 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?345a7c7068bb3aa6 | US | compressed | 4.70 Kb | whitelisted |
1604 | iexplore.exe | GET | 200 | 184.24.77.64:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgOI%2Fr6VlRk2IWfPujbwCtjKYg%3D%3D | US | der | 503 b | shared |
1604 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHwqDCE%2FxlVTRckfGR%2B4Tvo%3D | US | der | 1.40 Kb | whitelisted |
1604 | iexplore.exe | GET | 200 | 52.222.206.202:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | US | der | 1.39 Kb | shared |
1604 | iexplore.exe | GET | 200 | 18.66.107.167:80 | http://crl.rootg2.amazontrust.com/rootg2.crl | US | der | 660 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1604 | iexplore.exe | 45.154.253.150:443 | — | Svea Hosting AB | GB | suspicious |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
1604 | iexplore.exe | 45.154.253.151:443 | — | Svea Hosting AB | GB | suspicious |
1604 | iexplore.exe | 23.56.202.135:80 | x1.c.lencr.org | AKAMAI-AS | GB | suspicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1604 | iexplore.exe | 184.24.77.64:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
3932 | iexplore.exe | 92.123.104.63:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
1604 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1604 | iexplore.exe | 13.224.194.18:443 | djv99sxoqpv11.cloudfront.net | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
vjs.zencdn.net |
| whitelisted |
djv99sxoqpv11.cloudfront.net |
| shared |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |