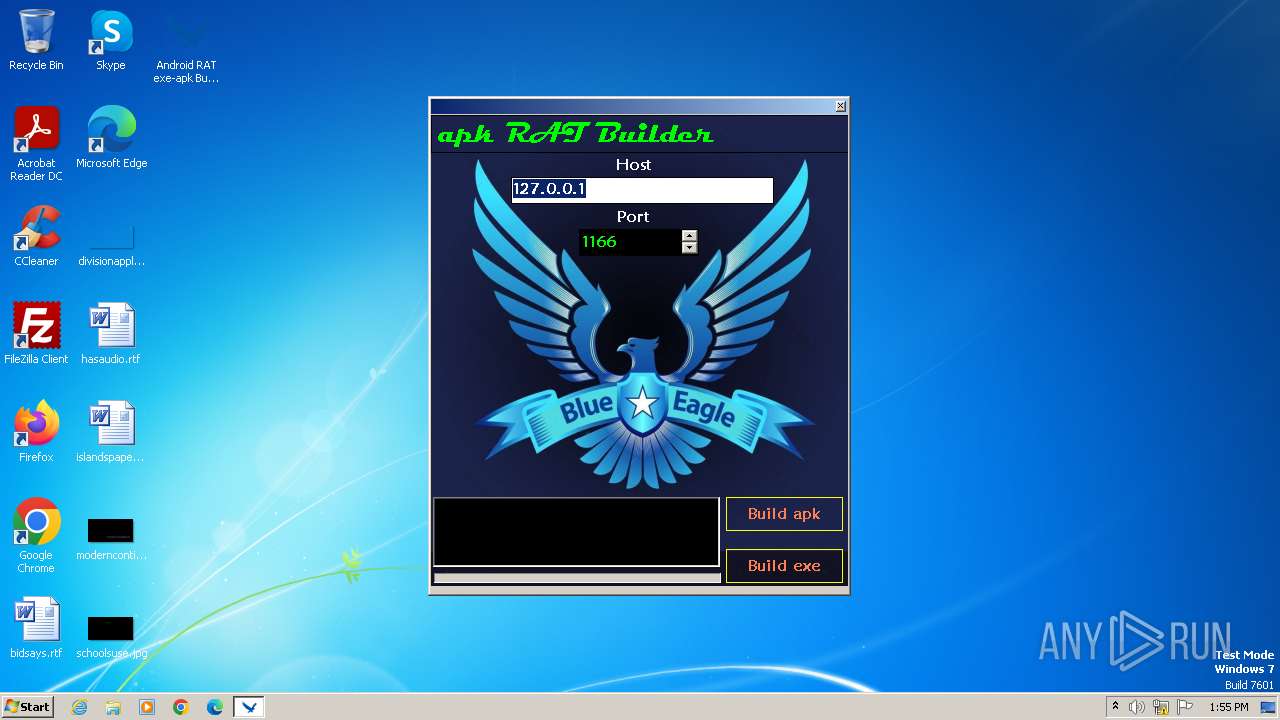
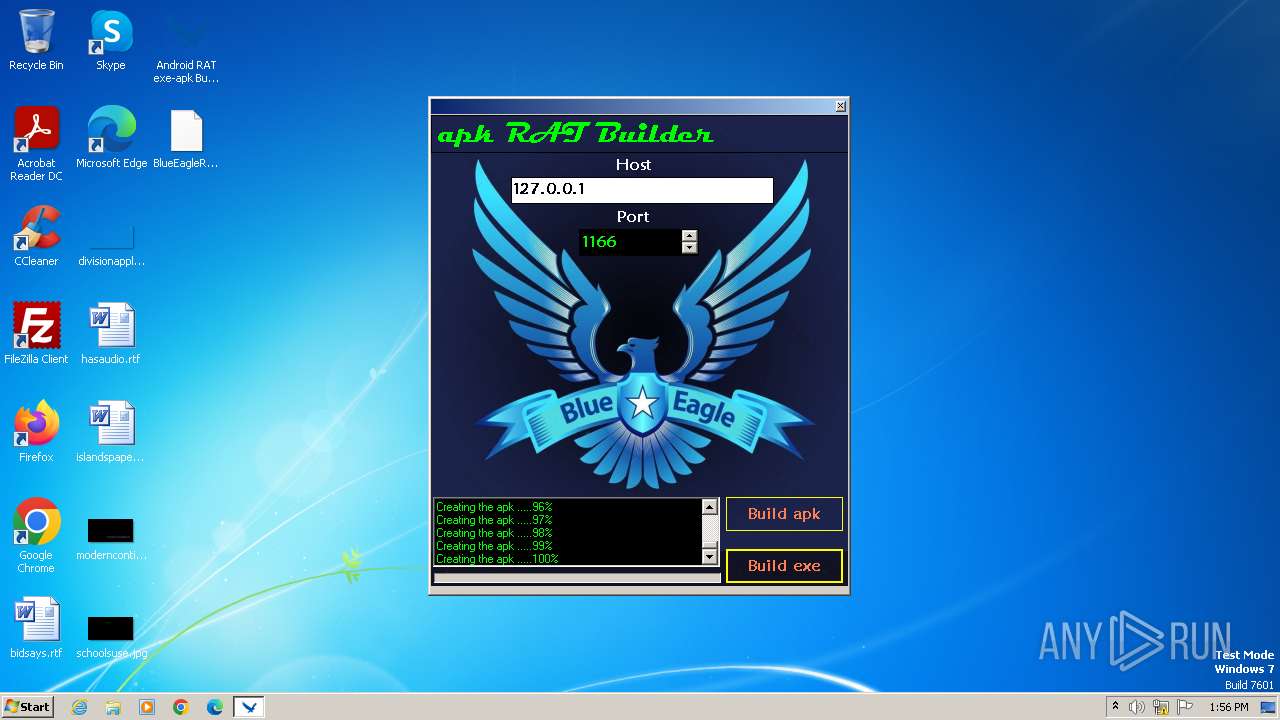
| File name: | Android RAT exe-apk Builder_Win8.exe |
| Full analysis: | https://app.any.run/tasks/a927eb01-f2ff-436a-9ad3-af564b9b4b43 |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2024, 12:55:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | C274D2F6D487AC1E2B54C4D8F84B7AA5 |
| SHA1: | 9BADDEDF22B01289BAE6E7757A1893A424E31311 |
| SHA256: | 6A2CD3B618CB91B0ABE525D42B9B6D7A5DB9BF46D919FB5A8599C6D8A1EB947F |
| SSDEEP: | 98304:4wrTVK+ZIoPGqoF64w0kMpJ0RWRKCEs4SCK/LMaR/HgV2vECQzuRkXNTHGVlTcbi:pVL6RHaRo7l0R |
MALICIOUS
Drops the executable file immediately after the start
- Android RAT exe-apk Builder_Win8.exe (PID: 3980)
- vbc.exe (PID: 2204)
- trojan.exe (PID: 1488)
Create files in the Startup directory
- trojan.exe (PID: 1488)
SUSPICIOUS
Reads the Internet Settings
- Android RAT exe-apk Builder_Win8.exe (PID: 3980)
The process executes VB scripts
- Android RAT exe-apk Builder_Win8.exe (PID: 3980)
Executable content was dropped or overwritten
- trojan.exe (PID: 1488)
- vbc.exe (PID: 2204)
INFO
Checks supported languages
- Android RAT exe-apk Builder_Win8.exe (PID: 3980)
- trojan.exe (PID: 1488)
- trojan.exe (PID: 692)
- trojan.exe (PID: 2052)
- trojan.exe (PID: 768)
- trojan.exe (PID: 1948)
- cvtres.exe (PID: 1764)
- vbc.exe (PID: 2204)
Reads the machine GUID from the registry
- Android RAT exe-apk Builder_Win8.exe (PID: 3980)
- trojan.exe (PID: 1488)
- trojan.exe (PID: 692)
- trojan.exe (PID: 768)
- trojan.exe (PID: 2052)
- trojan.exe (PID: 1948)
- cvtres.exe (PID: 1764)
- vbc.exe (PID: 2204)
Reads the computer name
- Android RAT exe-apk Builder_Win8.exe (PID: 3980)
- trojan.exe (PID: 1488)
- trojan.exe (PID: 692)
- trojan.exe (PID: 768)
- trojan.exe (PID: 2052)
- trojan.exe (PID: 1948)
Create files in a temporary directory
- Android RAT exe-apk Builder_Win8.exe (PID: 3980)
- vbc.exe (PID: 2204)
- cvtres.exe (PID: 1764)
Manual execution by a user
- trojan.exe (PID: 1488)
- trojan.exe (PID: 692)
- trojan.exe (PID: 768)
- trojan.exe (PID: 2052)
- trojan.exe (PID: 1948)
Creates files or folders in the user directory
- trojan.exe (PID: 1488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:03:10 22:17:21+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 33792 |
| InitializedDataSize: | 8511488 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x82e00a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | ApkRAT_exe_Builder |
| FileVersion: | 1.0.0.0 |
| InternalName: | ApkRAT_exe_Builder.exe |
| LegalCopyright: | Copyright © 2023 |
| OriginalFileName: | ApkRAT_exe_Builder.exe |
| ProductName: | ApkRAT_exe_Builder |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
43
Monitored processes
8
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 692 | "C:\Users\admin\Desktop\trojan.exe" | C:\Users\admin\Desktop\trojan.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 768 | "C:\Users\admin\Desktop\trojan.exe" | C:\Users\admin\Desktop\trojan.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\Desktop\trojan.exe" | C:\Users\admin\Desktop\trojan.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1764 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES4D42.tmp" "C:\Users\admin\AppData\Local\Temp\vbcC4B0136D4F9F4152A0C1907E57BE21DD.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | vbc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 1948 | "C:\Users\admin\Desktop\trojan.exe" | C:\Users\admin\Desktop\trojan.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 2052 | "C:\Users\admin\Desktop\trojan.exe" | C:\Users\admin\Desktop\trojan.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 2204 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" /noconfig @"C:\Users\admin\AppData\Local\Temp\gkq1qx01.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | Android RAT exe-apk Builder_Win8.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 14.8.3761.0 Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\Desktop\Android RAT exe-apk Builder_Win8.exe" | C:\Users\admin\Desktop\Android RAT exe-apk Builder_Win8.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ApkRAT_exe_Builder Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
9 245
Read events
9 103
Write events
128
Delete events
14
Modification events
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 4 |
Value: 41006E00640072006F0069006400200052004100540020006500780065002D00610070006B0020004200750069006C006400650072005F00570069006E0038002E0065007800650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000010000000700000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (3980) Android RAT exe-apk Builder_Win8.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: | |||
Executable files
3
Suspicious files
2
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | vbc.exe | C:\Users\admin\AppData\Local\Temp\vbc8EF23E0E9574F778D26F930918F6783.TMP | binary | |
MD5:FFB3450A99D5922BE85813D0954847A0 | SHA256:411979A866A3CEECE601AF2E50E43611CB3673BC16254510659FEBE1E80CEEC7 | |||
| 2204 | vbc.exe | C:\Users\admin\AppData\Local\Temp\vbcC4B0136D4F9F4152A0C1907E57BE21DD.TMP | binary | |
MD5:F6042634973AA457E865DC8B319CE261 | SHA256:FD64A57396FEA949C3E3478F51C6BDFA189724C40D189F01AA36074DF9DAEA0D | |||
| 1764 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES4D42.tmp | binary | |
MD5:8C3BAF96F2EB36F085A89DFE41D56E63 | SHA256:B7823A9E1E27ACEB86AA18745723215447CAA8ED90F9ECB2C25D9FA22805C426 | |||
| 2204 | vbc.exe | C:\Users\admin\Desktop\trojan.exe | executable | |
MD5:F972085777DFF1BAD4510F1FCDC19701 | SHA256:514D640BDA65DD2A28108F1E21EC09184E4E7E932BCA1FC467E7D63AC548B878 | |||
| 3980 | Android RAT exe-apk Builder_Win8.exe | C:\Users\admin\AppData\Local\Temp\gkq1qx01.0.vb | text | |
MD5:35127E9B9652D7DFB0DA0E0A8EFD05AF | SHA256:9CEBF35E1372535B0B1A477703AA4D4B2D0AC52CB39E7A45B7A36949FC50DC78 | |||
| 3980 | Android RAT exe-apk Builder_Win8.exe | C:\Users\admin\AppData\Local\Temp\gkq1qx01.cmdline | text | |
MD5:1DD9CCA1648F03A17D2C532218D6975D | SHA256:14A48388508B511823A3DAC310B5C681D62AF90452F56CE3BE7696D5ED7CF9FD | |||
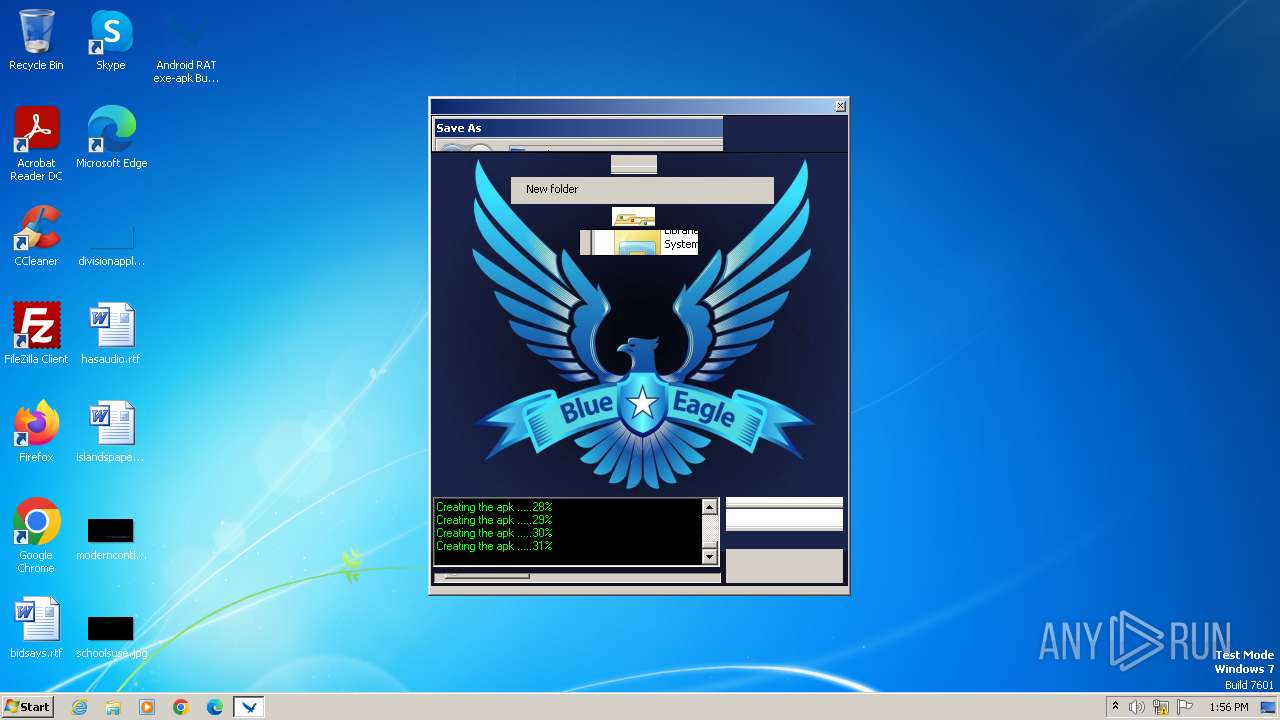
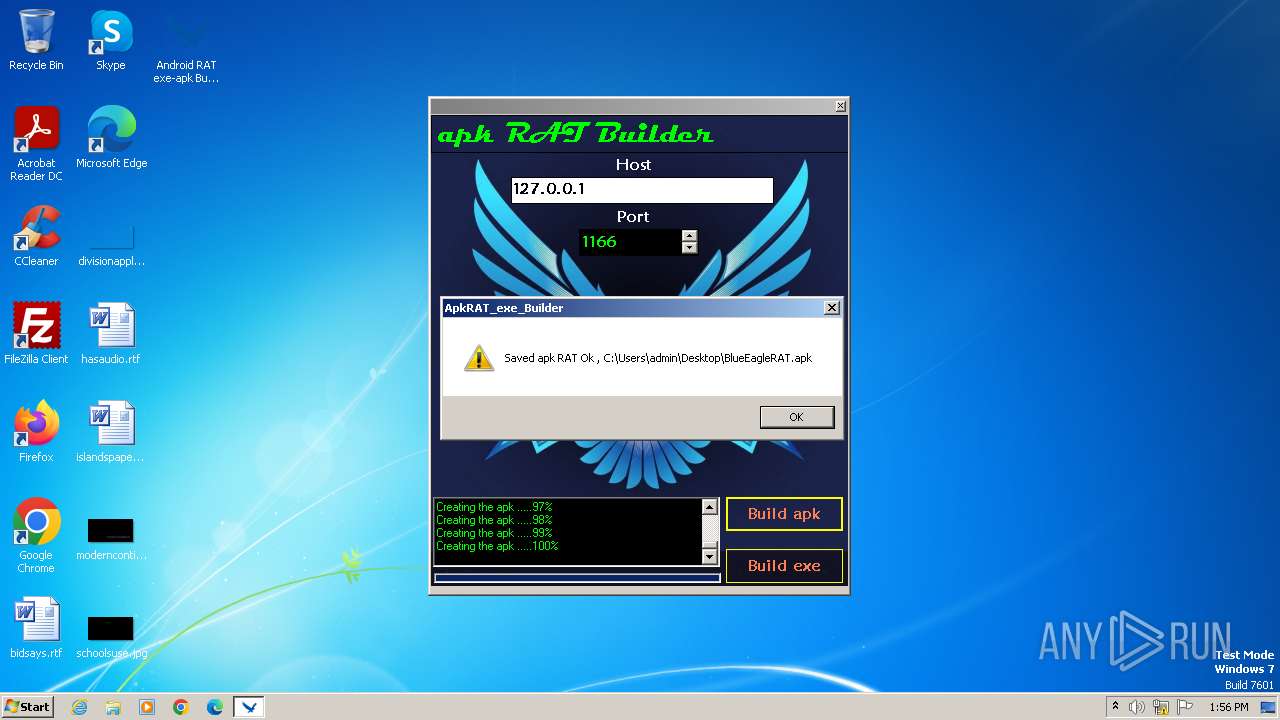
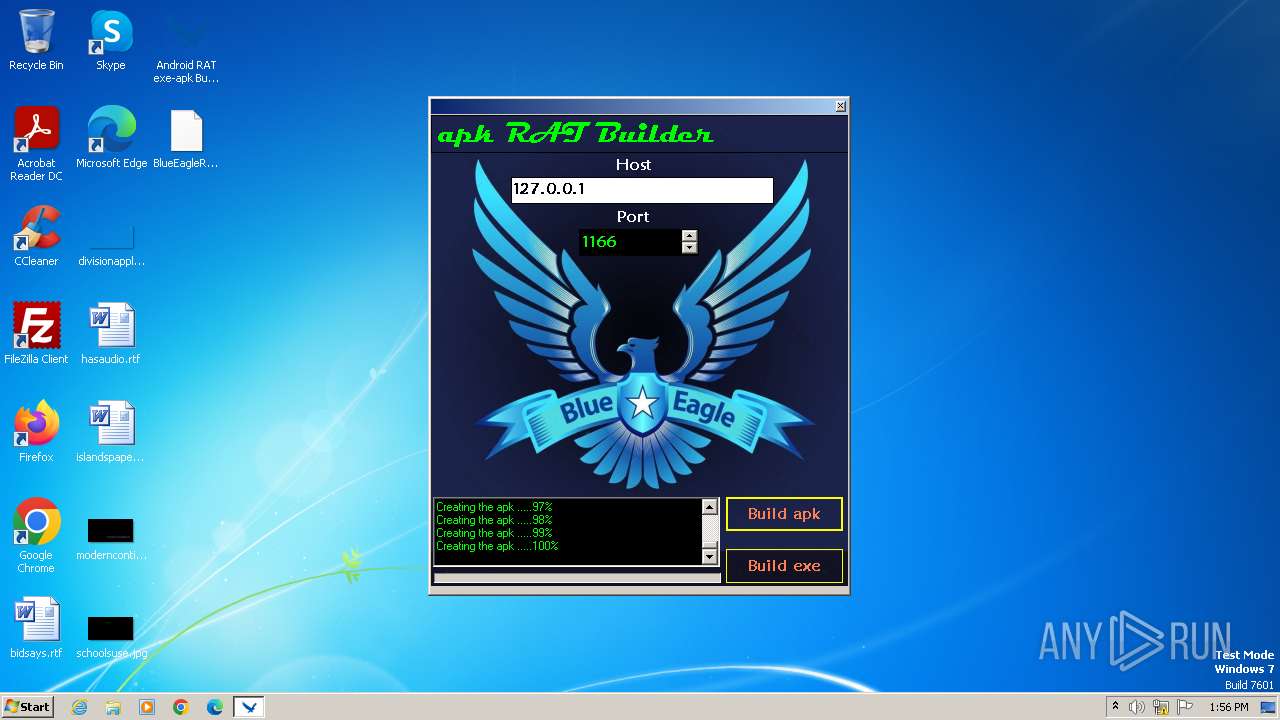
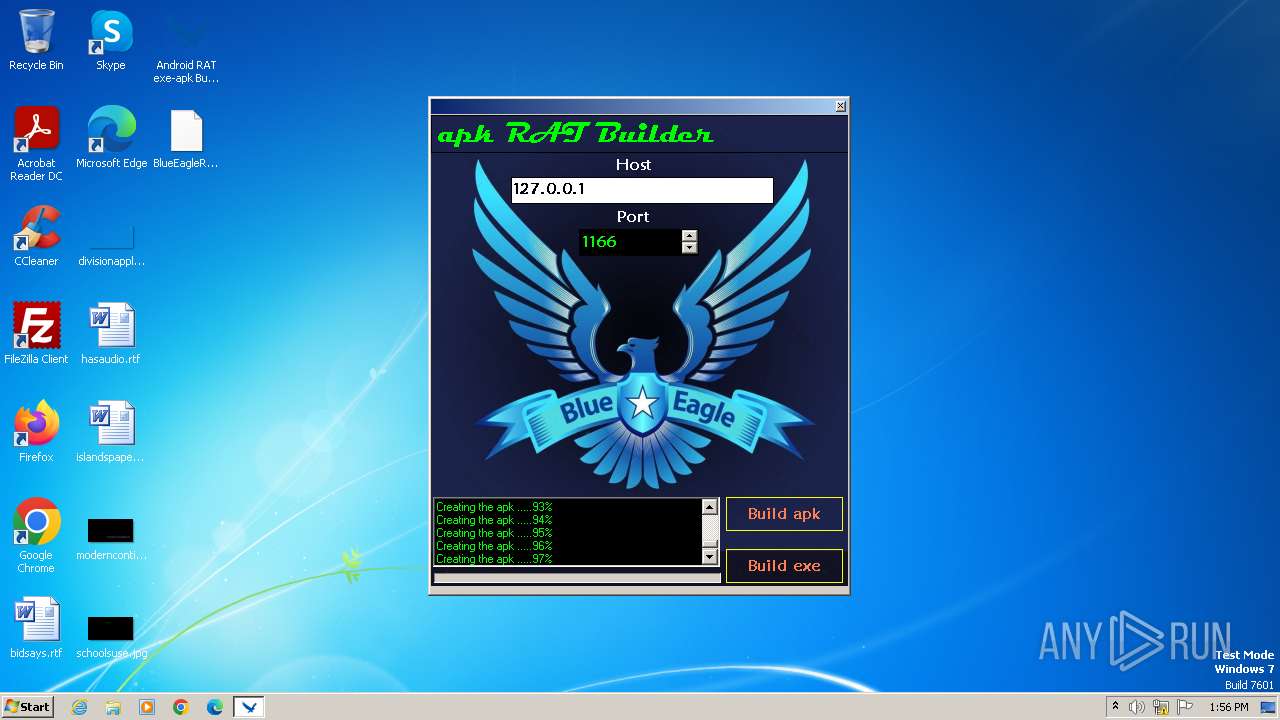
| 3980 | Android RAT exe-apk Builder_Win8.exe | C:\Users\admin\Desktop\BlueEagleRAT.apk | java | |
MD5:01618F824301734A4E6E1853CCBEDD0E | SHA256:F6EB5C118DF40119FF01D6AB6BAB29329CB366569C1AA9919F98F4C60E0BB3B3 | |||
| 1488 | trojan.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\trojan.exe | executable | |
MD5:F972085777DFF1BAD4510F1FCDC19701 | SHA256:514D640BDA65DD2A28108F1E21EC09184E4E7E932BCA1FC467E7D63AC548B878 | |||
| 2204 | vbc.exe | C:\Users\admin\AppData\Local\Temp\gkq1qx01.out | text | |
MD5:9BA0AC89CC1FAA5CD472C0417E9D1D60 | SHA256:8B988B0E5A490DA0923A207B3D73A74DA957270631432214D6BF67B9B4BB0D24 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |