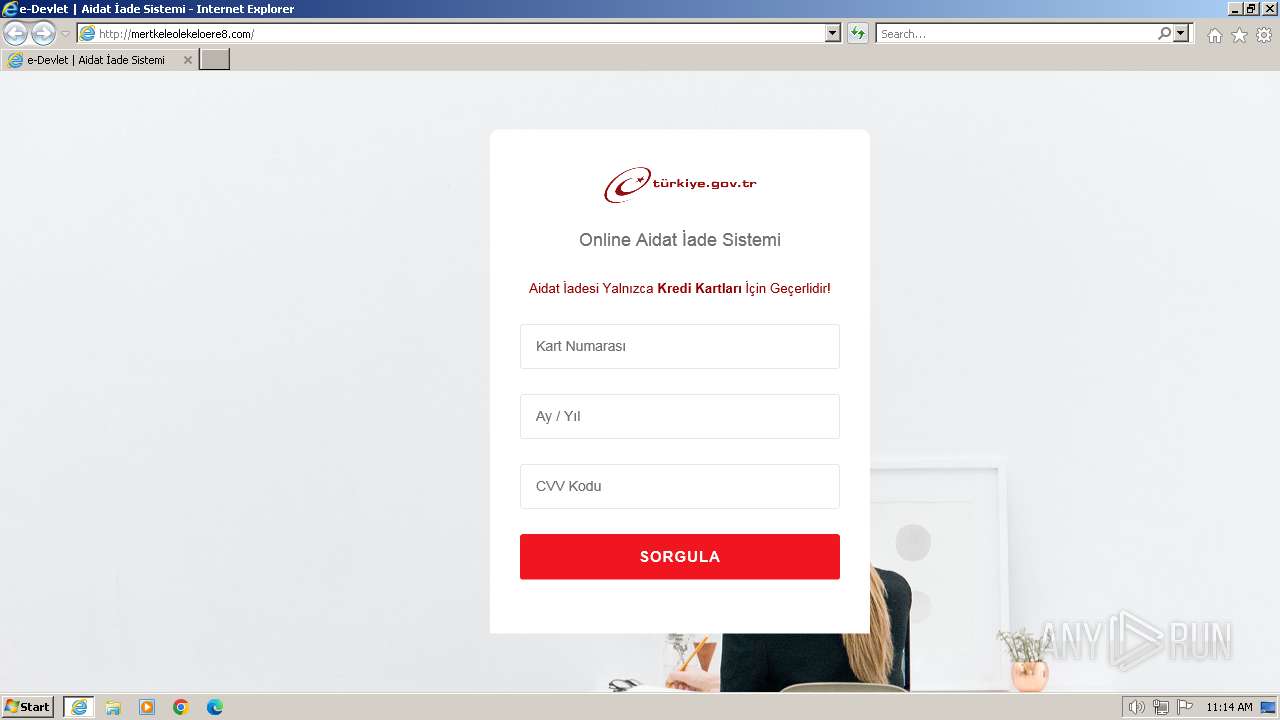
| URL: | mertkeleolekeloere8.com |
| Full analysis: | https://app.any.run/tasks/9283997f-1389-49ec-83d9-7f7e15c04654 |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2024, 11:14:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4340D1CF3F67BE30E014F1B7C86BE447 |
| SHA1: | 7BC07BB106371FD01C3A56B65489D81A8B2D24DF |
| SHA256: | 6A1B37B2B4FB0572B70F49A63EF516206D488265E86AD99ECF92E8B6EC893D6D |
| SSDEEP: | 3:9qRbXAdZI:QRs4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2560 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2640 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2640 | "C:\Program Files\Internet Explorer\iexplore.exe" "mertkeleolekeloere8.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
13 681
Read events
13 602
Write events
73
Delete events
6
Modification events
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2640) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
12
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\default(1)[1].css | text | |
MD5:E9F75C016866EEE7CE7FBC02D56D63DE | SHA256:CBB81F38EE322ED3D62AF6BB700DEF6A6BE839B1EDAFCB6261FC2A78ED4FFDB3 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\font-awesome.min(1)[1].css | text | |
MD5:7F71F41CF0D1818F3AD2B7607A1037E0 | SHA256:2F499490B865EA22B5A1EFDEADE6D8B977073B0642238B51109CD202167D173E | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\US86LG0U.htm | html | |
MD5:E0C97291169237A17F32BFC3BD70332A | SHA256:2A9DB45D409FE710B3EFDD0E68506F5FA405CAEDC17FC71C35FFBFC8B9B94304 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\creditly.js[1].js | text | |
MD5:E46AEAA8F644707EFFF00F55B9311584 | SHA256:87F22C41DBCB26BAD91FBAF973D978AB76CD68A768AD20B3A3596C9277CB113C | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:4F95CDFFAB13327B0C418ED852C863B5 | SHA256:CA15AAB403EE185633F91F47E4A38B1EF934B0CE1FFBC039E4954876469ADD6B | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\style(1)[1].css | text | |
MD5:71965F114E5D9959D83CF148F625AD8C | SHA256:CB409CA7227F6EA8937B56B2C90284AFE4F0596944940317B3FB7BB8444A69B2 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\jquery.creditCardValidator.js[1].js | text | |
MD5:0BD4315906225C8D21713149D658CDCD | SHA256:C5F8FCC96153880F57CB501646DCA91AB644F972B43A851E3B087CE4339E5079 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:73CE21FF1FB2989F6350ACE9274AE9B5 | SHA256:D7005273BAB949C42FCC73EAC7820C4C5F08DF1E9095020CDB0E17FC9E282D50 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\logo-2[1].png | image | |
MD5:6CA8C4F645ECBD51C1BF5511AAC67E8A | SHA256:257461ED4D440311FFC7147309E879BC3EA33DC97C7F7CD15E17BC5AB0DD538E | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:3366ECFF24A65276CF0776270C7CB157 | SHA256:AD5A265647E53CF6918DF5DB61467971FE273114E1C243E3D18FC3569E360321 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
28
DNS requests
12
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2560 | iexplore.exe | GET | 200 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/ | unknown | html | 2.44 Kb | unknown |
2560 | iexplore.exe | GET | 404 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/gtm.js.indir | unknown | html | 315 b | unknown |
2560 | iexplore.exe | GET | 404 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/font-awesome.min.css | unknown | html | 315 b | unknown |
2560 | iexplore.exe | GET | 404 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/bootstrap.min.css | unknown | html | 315 b | unknown |
2560 | iexplore.exe | GET | 200 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/css | unknown | text | 30.7 Kb | unknown |
2560 | iexplore.exe | GET | 404 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/flaticon.css | unknown | html | 315 b | unknown |
2560 | iexplore.exe | GET | 404 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/default.css | unknown | html | 315 b | unknown |
2560 | iexplore.exe | GET | 404 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/style.css | unknown | html | 315 b | unknown |
2560 | iexplore.exe | GET | 200 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/bootstrap.min(1).css | unknown | text | 21.1 Kb | unknown |
2560 | iexplore.exe | GET | 200 | 92.205.171.217:80 | http://mertkeleolekeloere8.com/index_files/font-awesome.min(1).css | unknown | text | 7.09 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2560 | iexplore.exe | 92.205.171.217:80 | mertkeleolekeloere8.com | — | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2560 | iexplore.exe | 142.250.184.232:443 | www.googletagmanager.com | GOOGLE | US | unknown |
2560 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2560 | iexplore.exe | 142.250.185.67:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2640 | iexplore.exe | 92.205.171.217:80 | mertkeleolekeloere8.com | — | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2560 | iexplore.exe | 216.239.32.36:443 | region1.google-analytics.com | GOOGLE | US | unknown |
2640 | iexplore.exe | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mertkeleolekeloere8.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2560 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious message detected (saved from) |