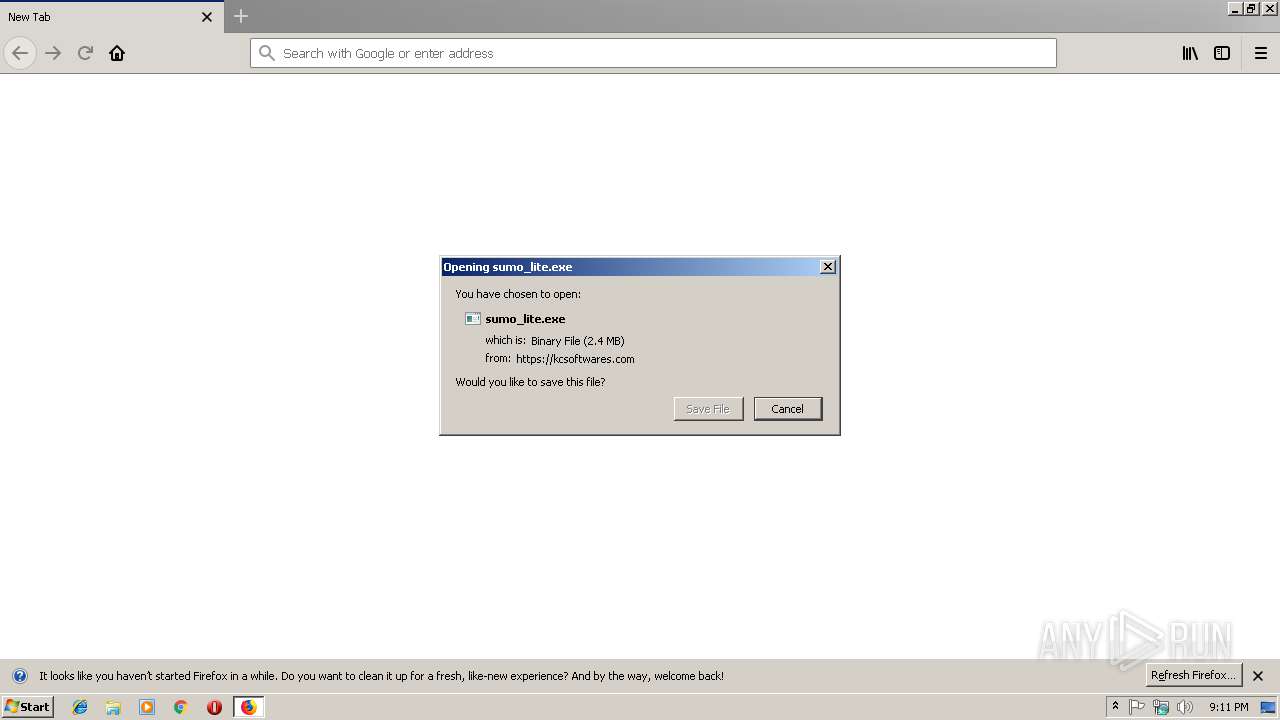
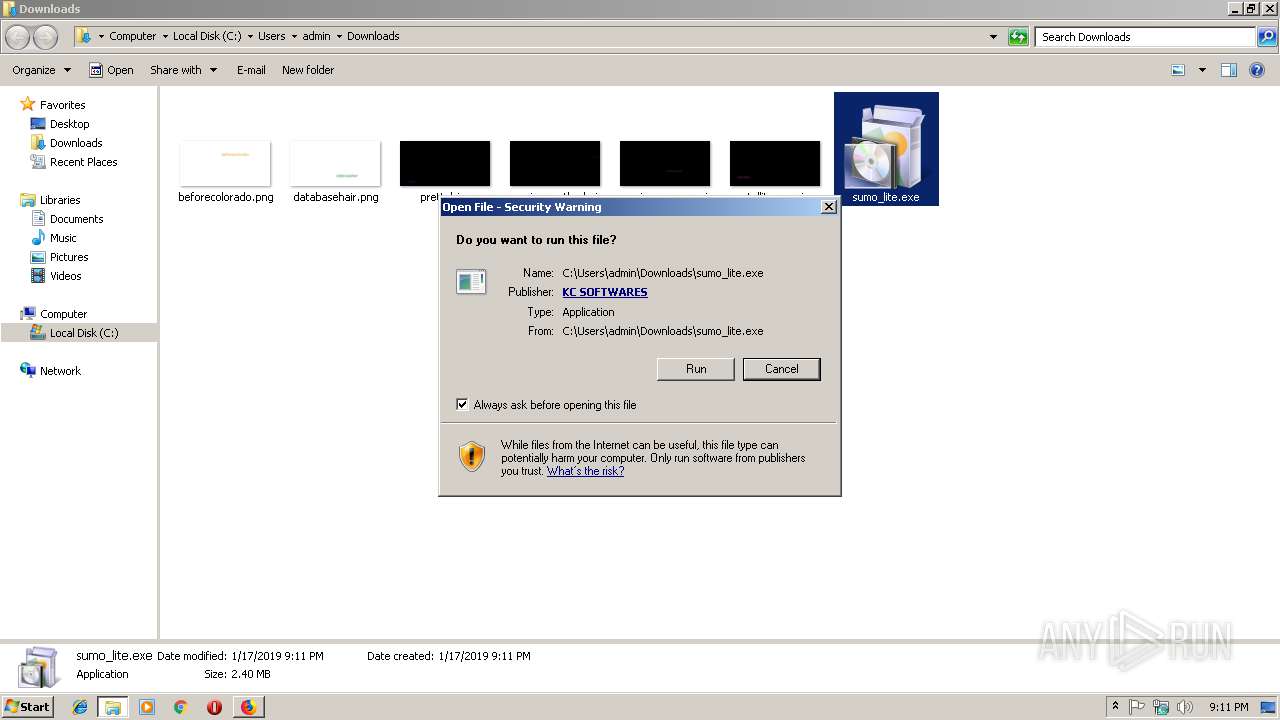
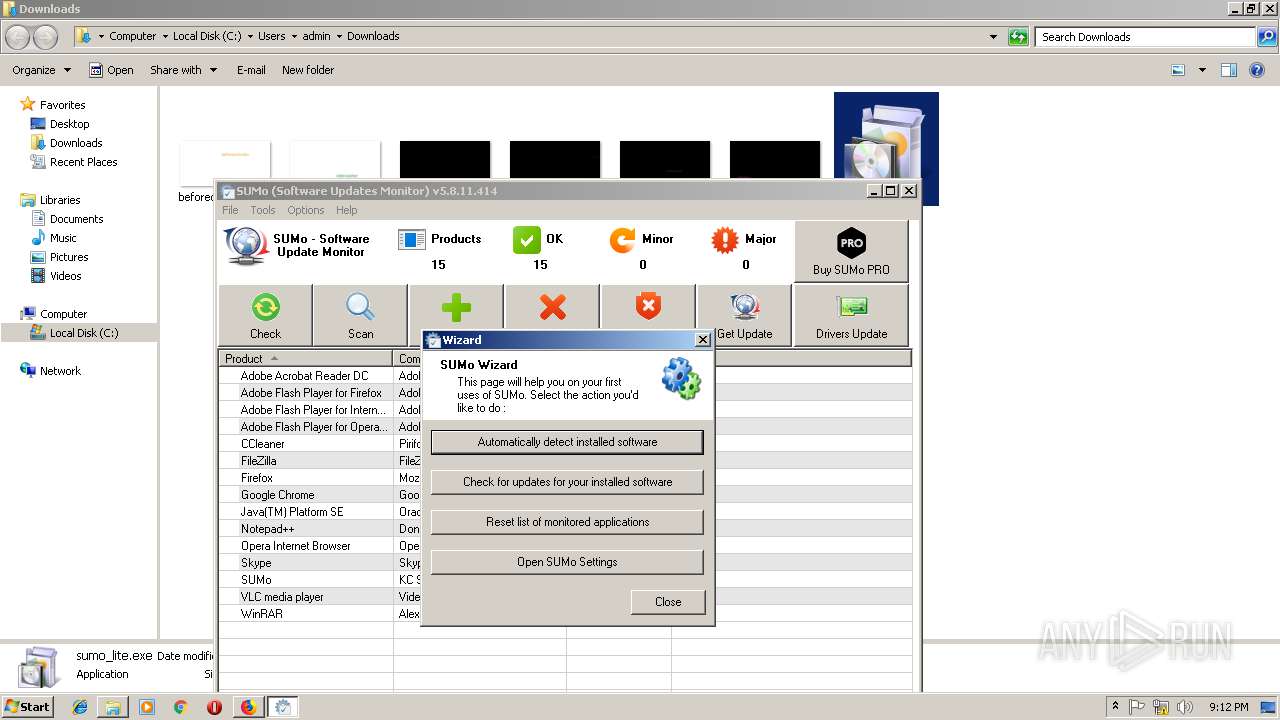
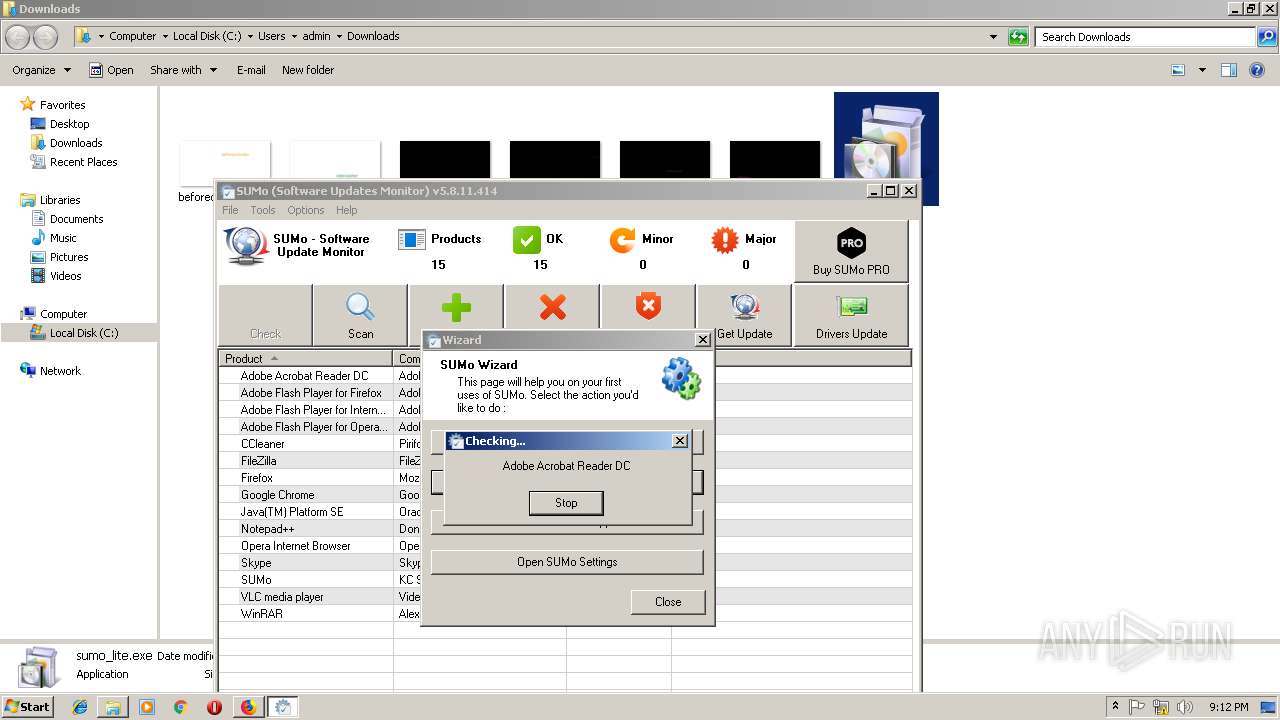
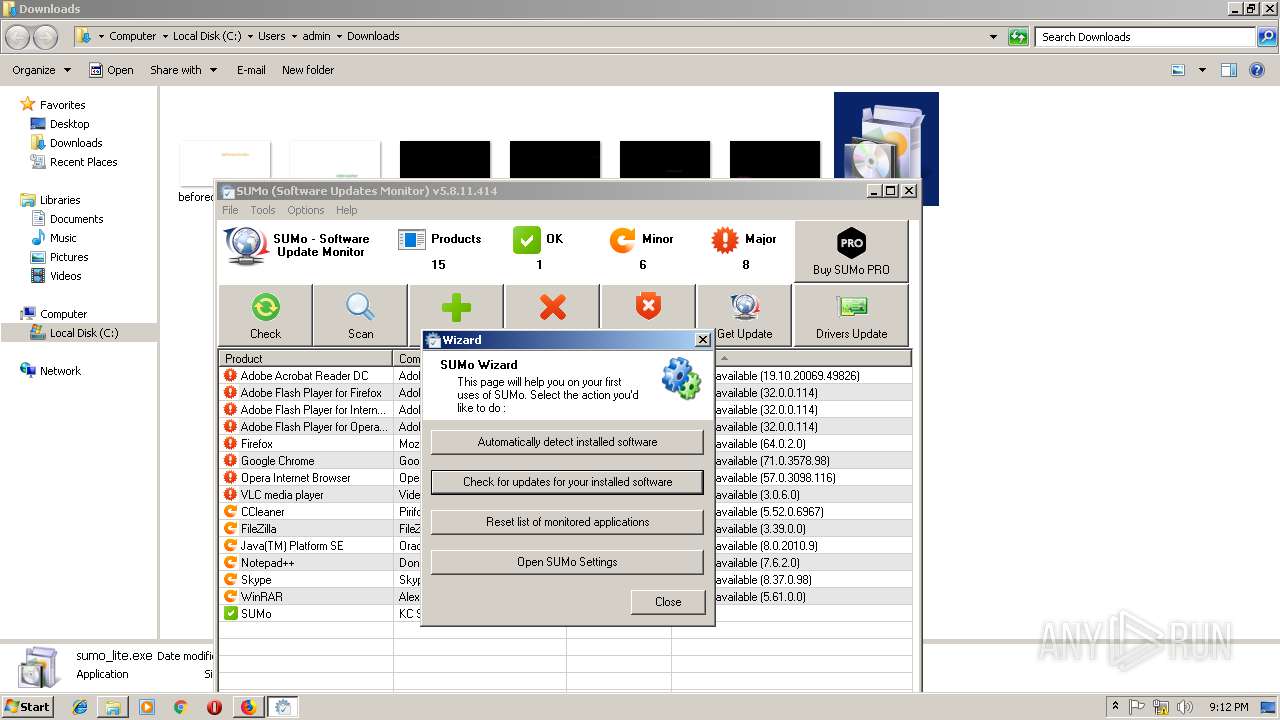
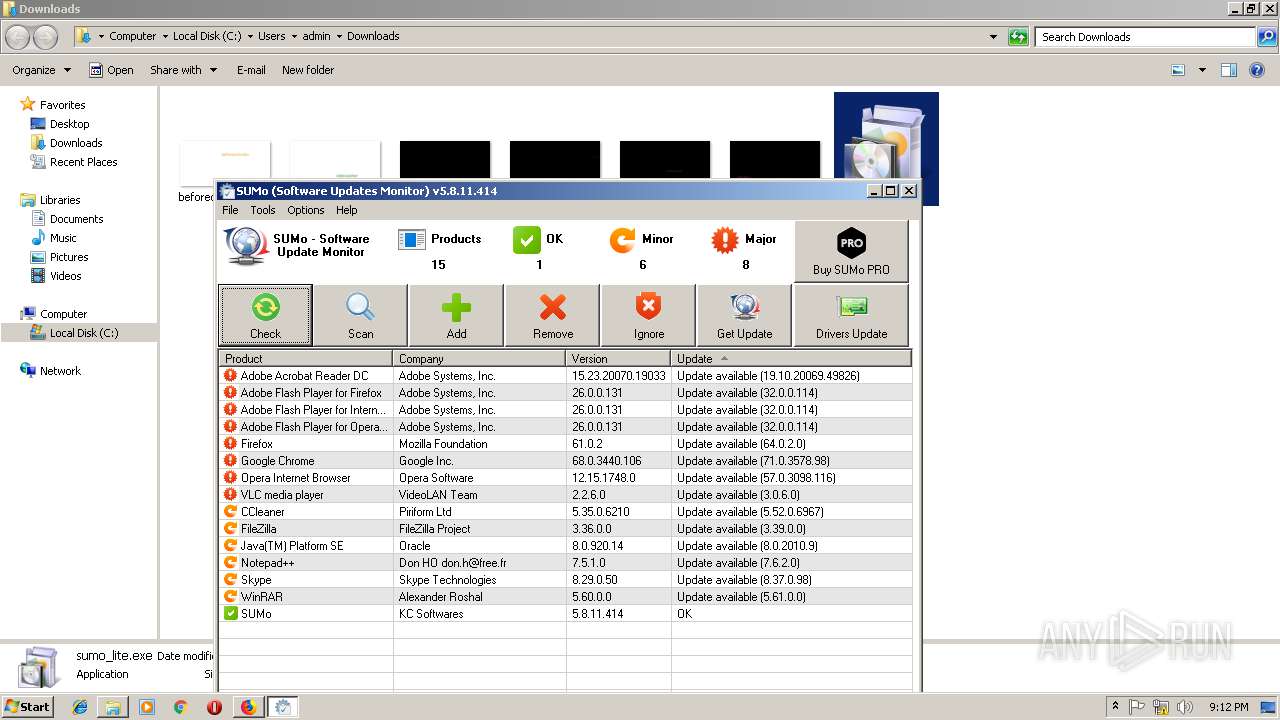
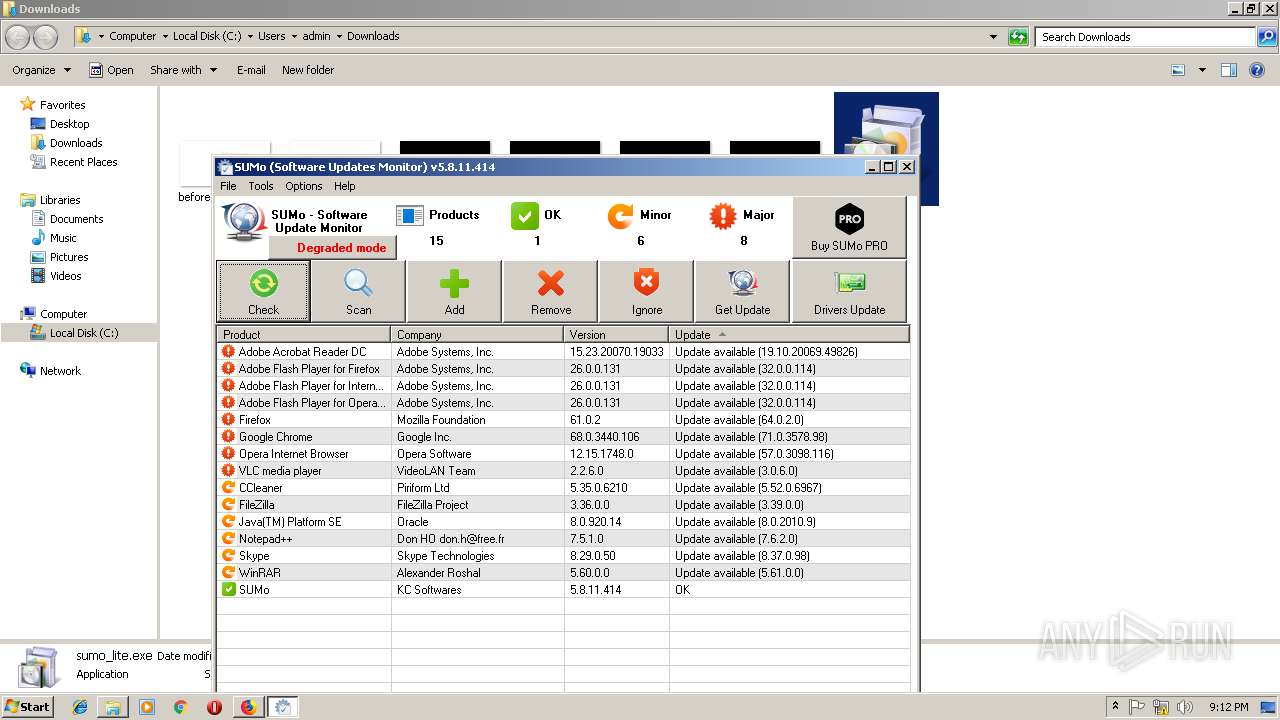
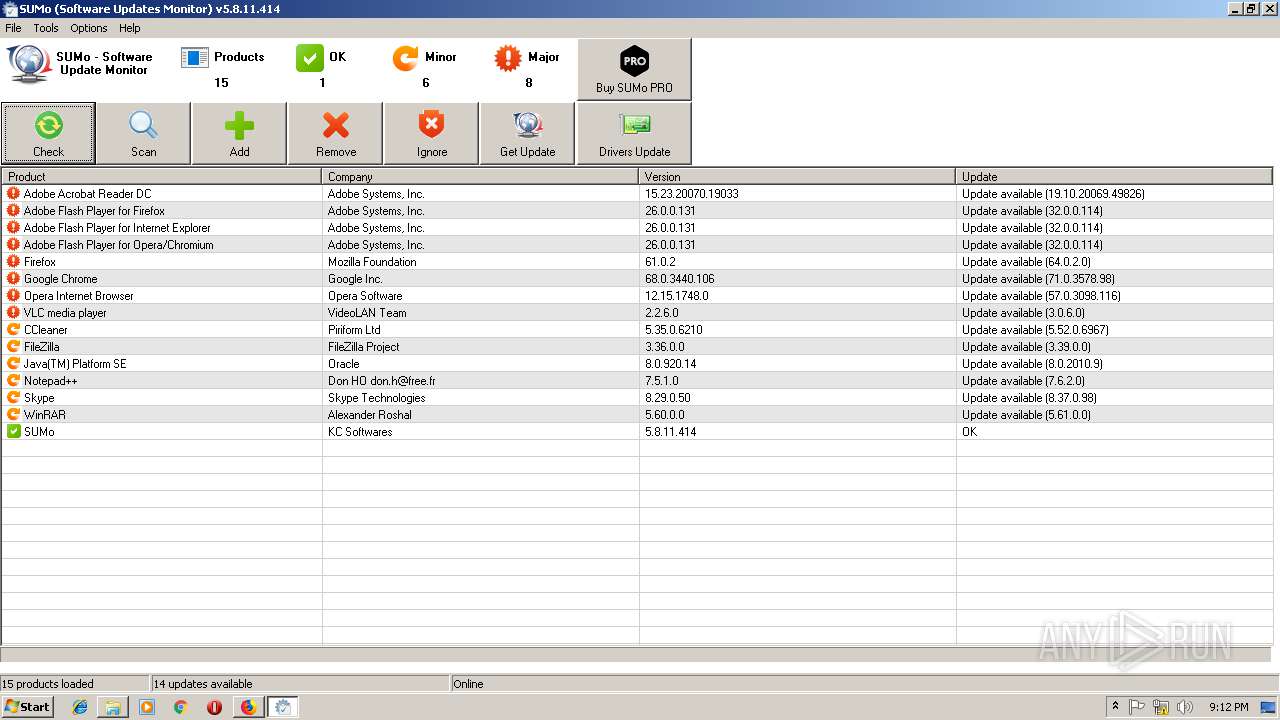
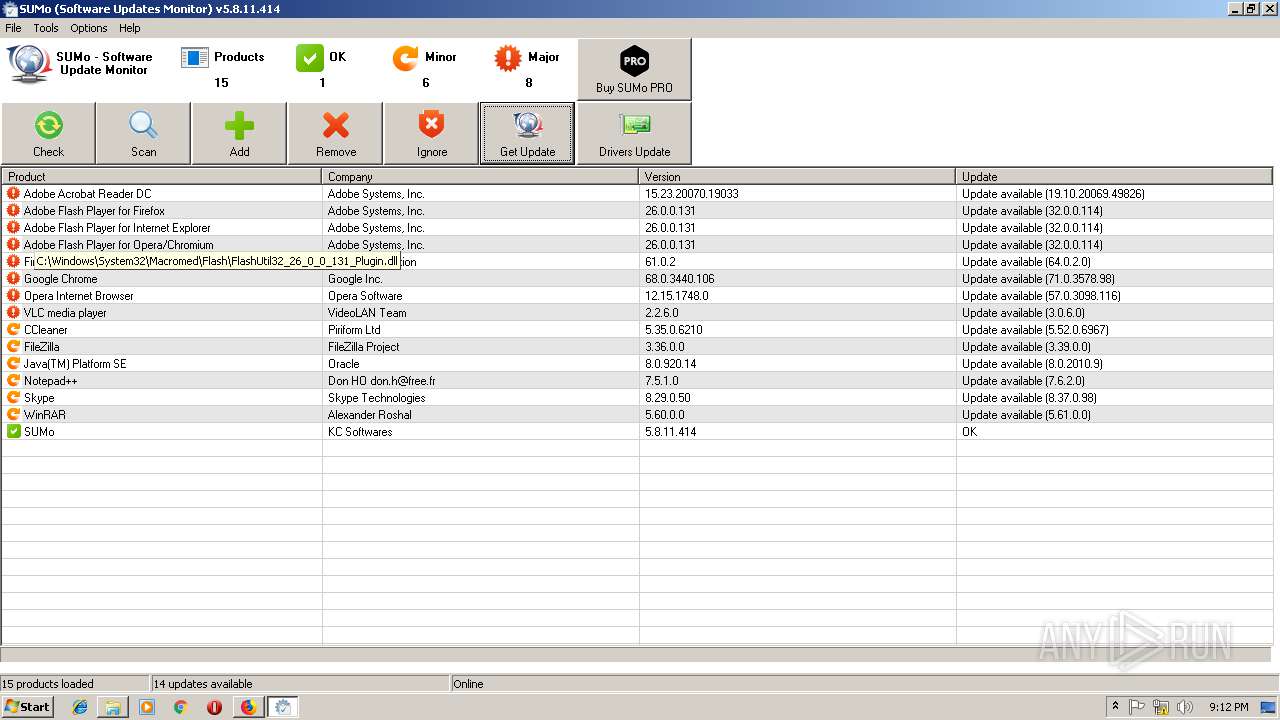
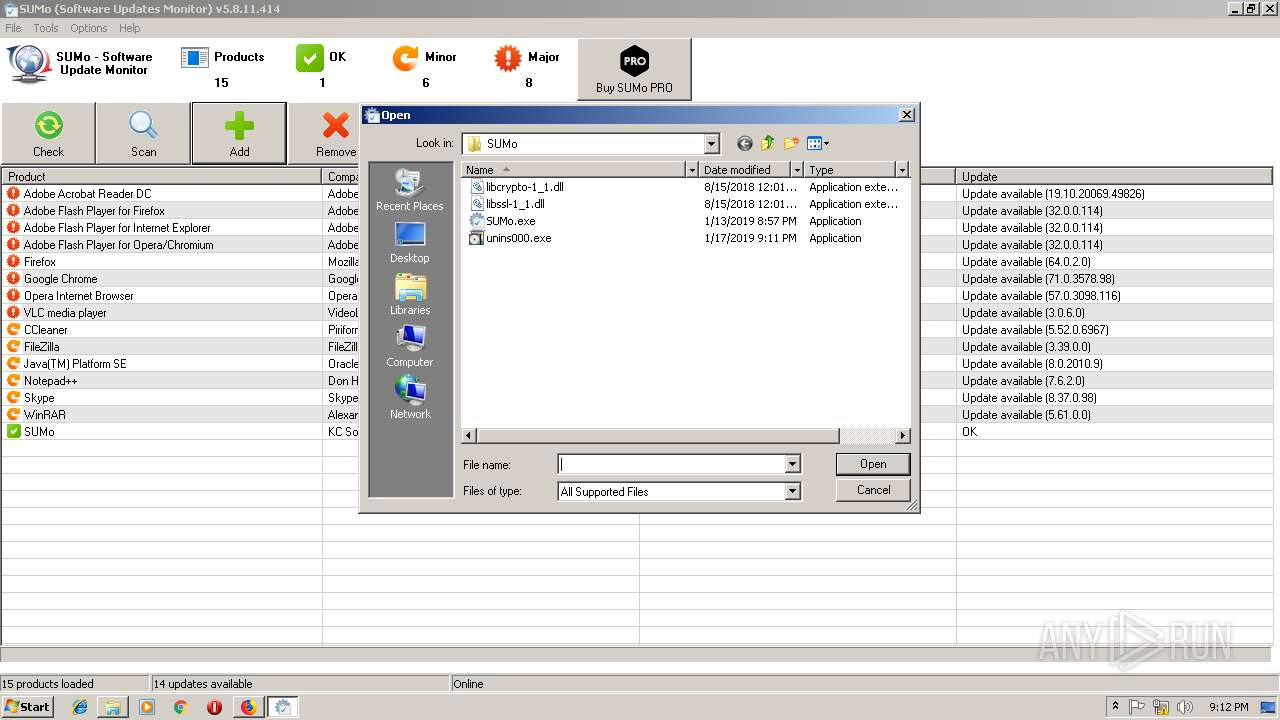
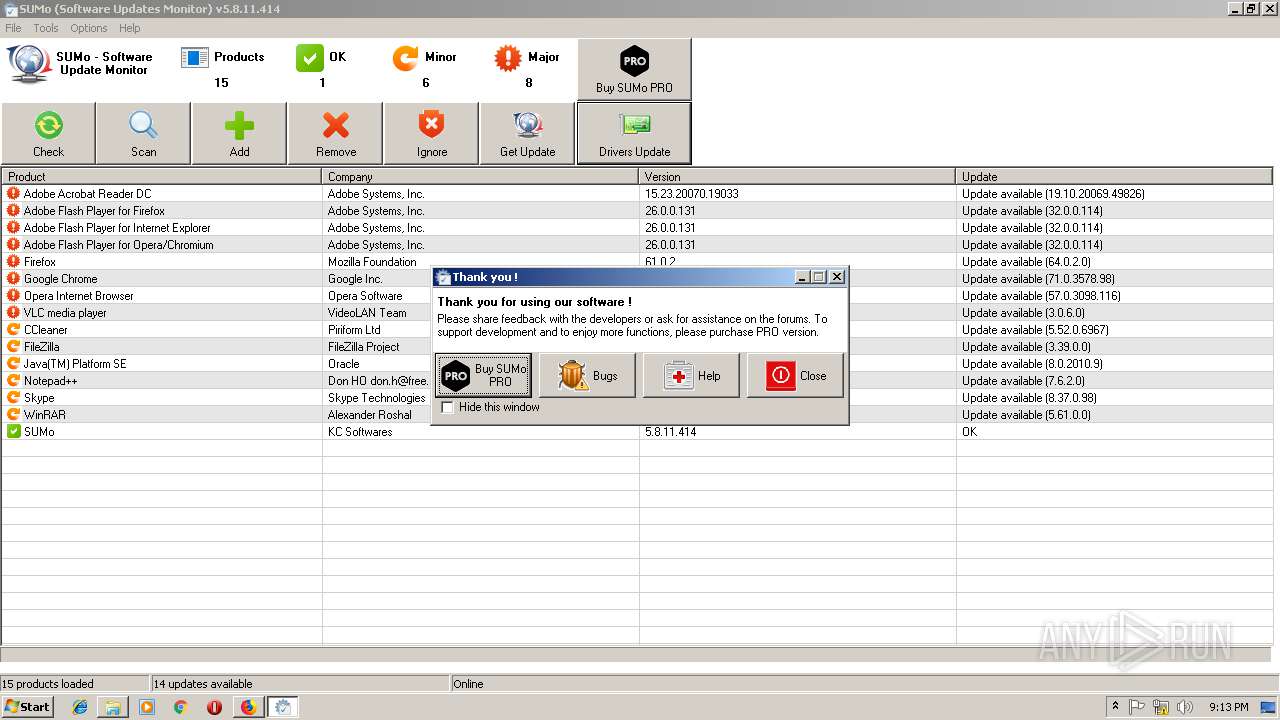
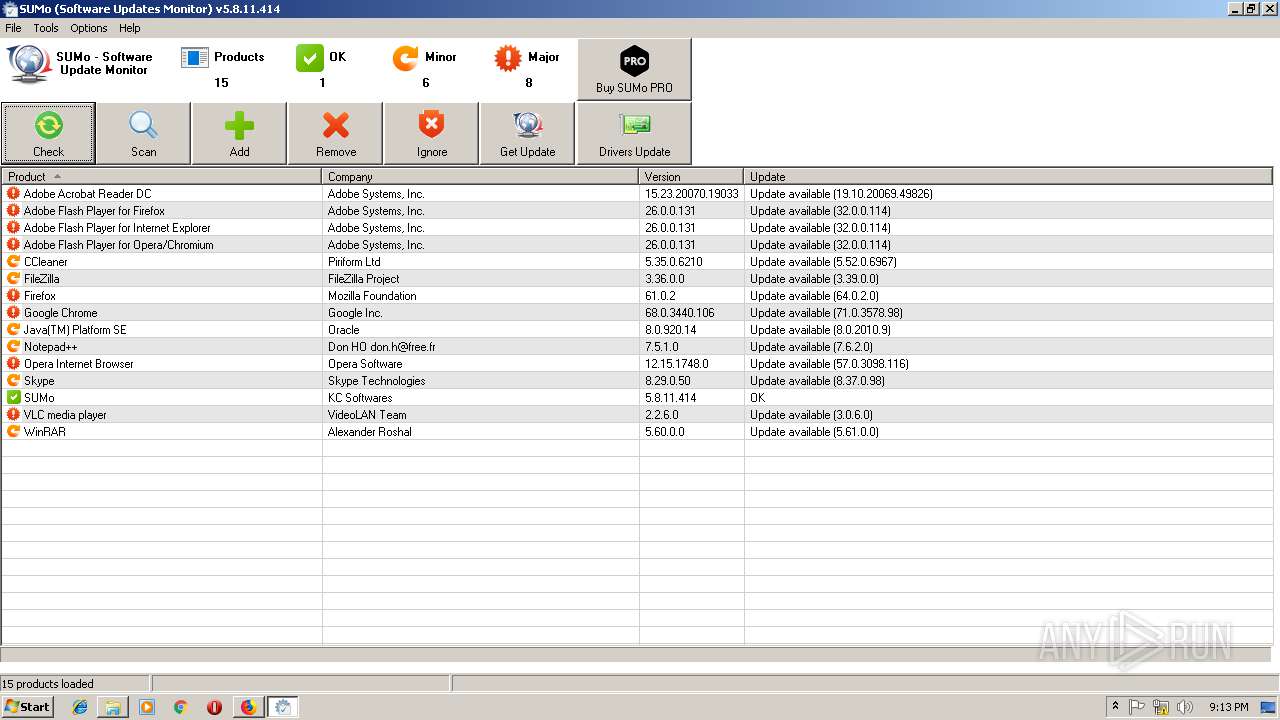
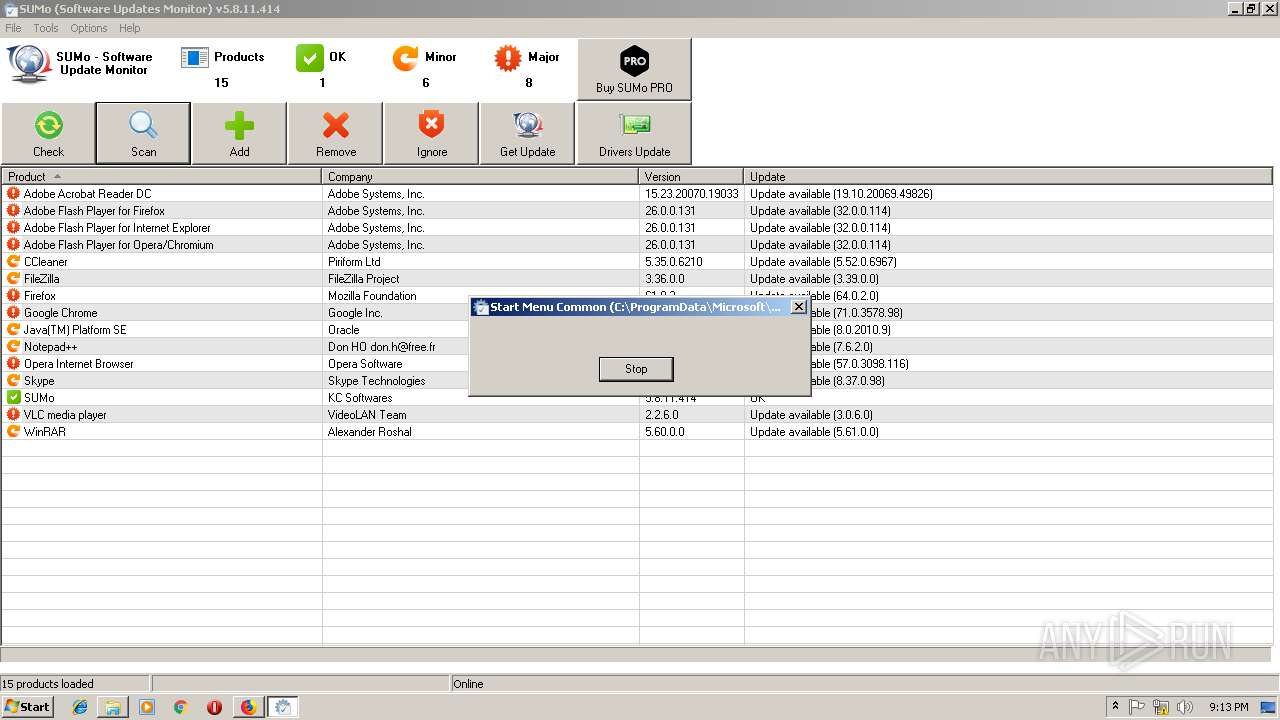
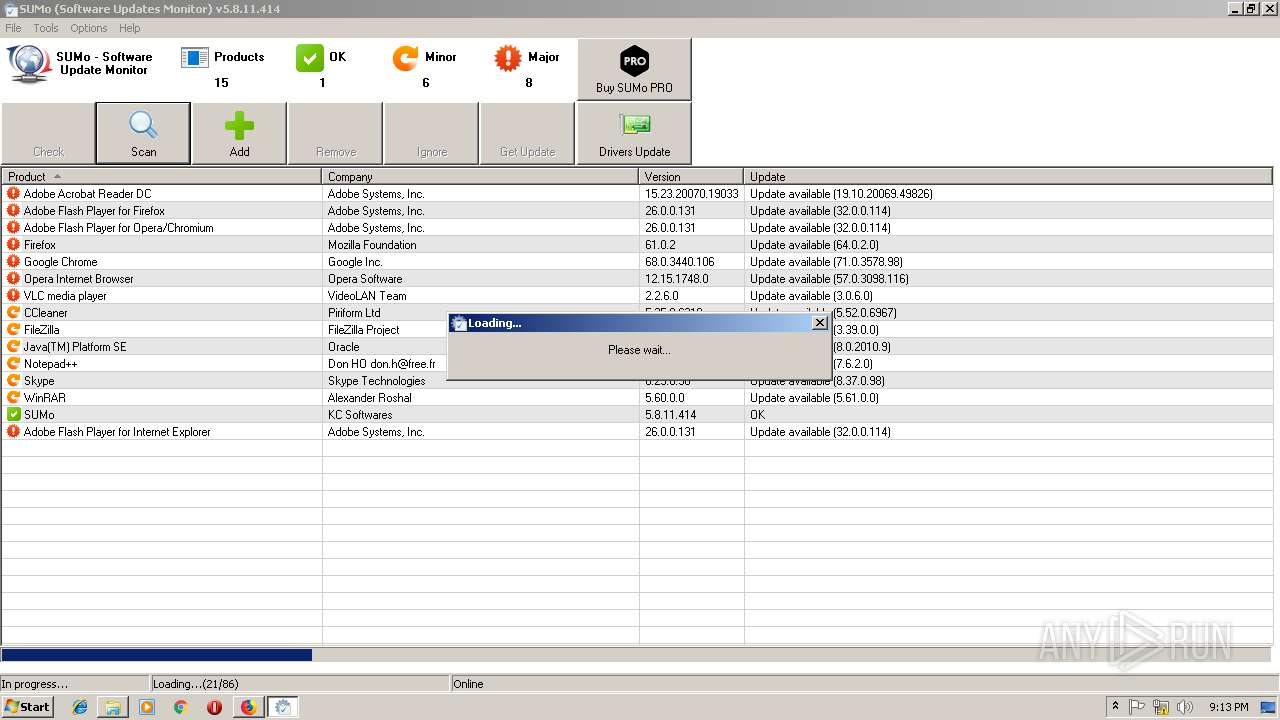
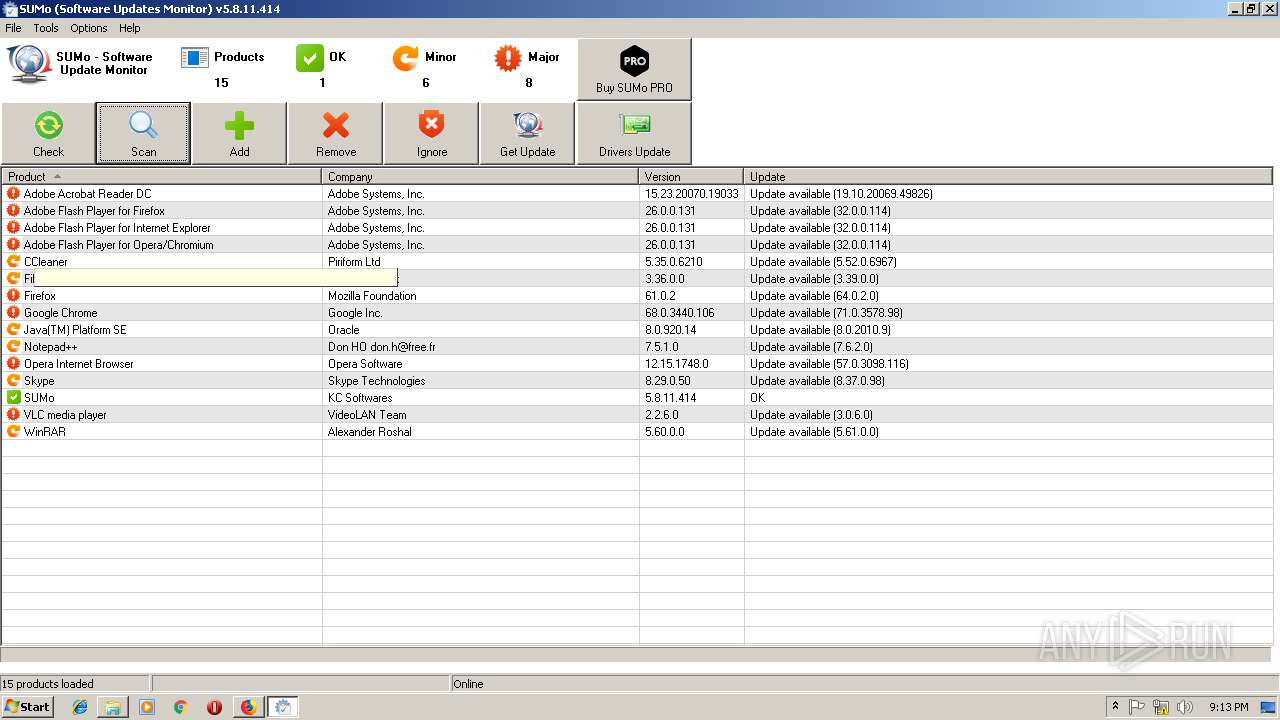
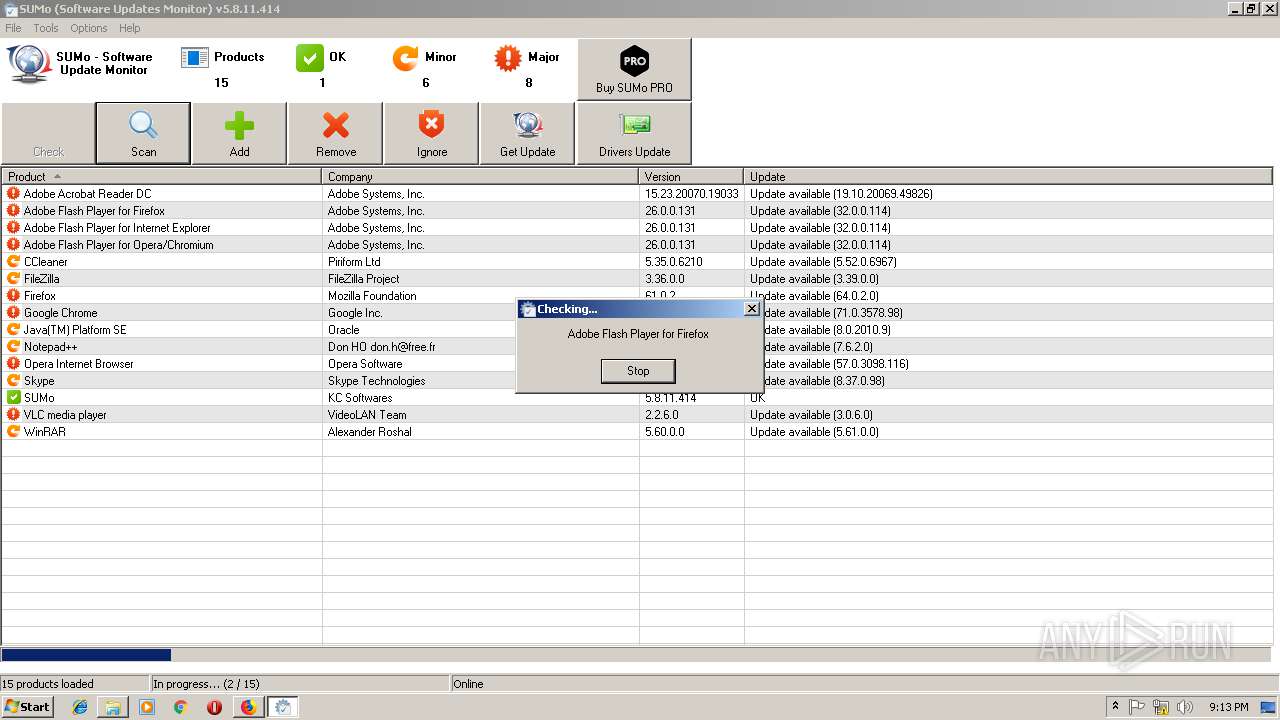
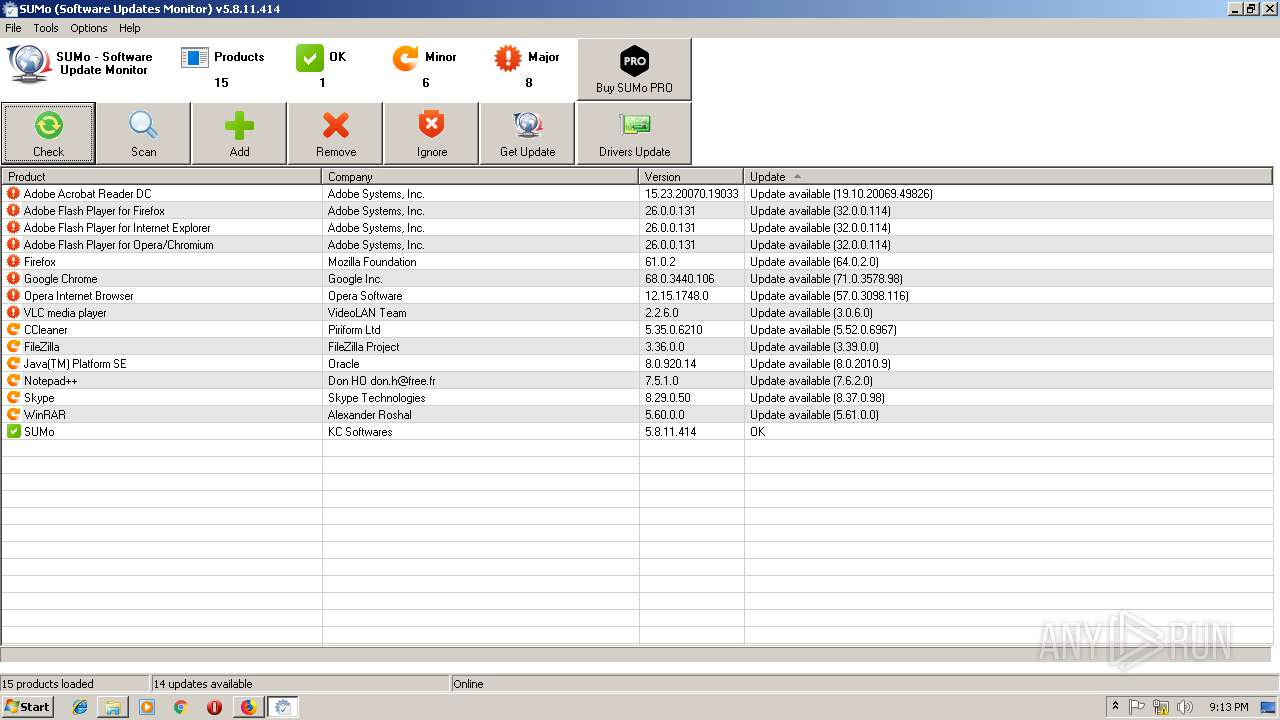
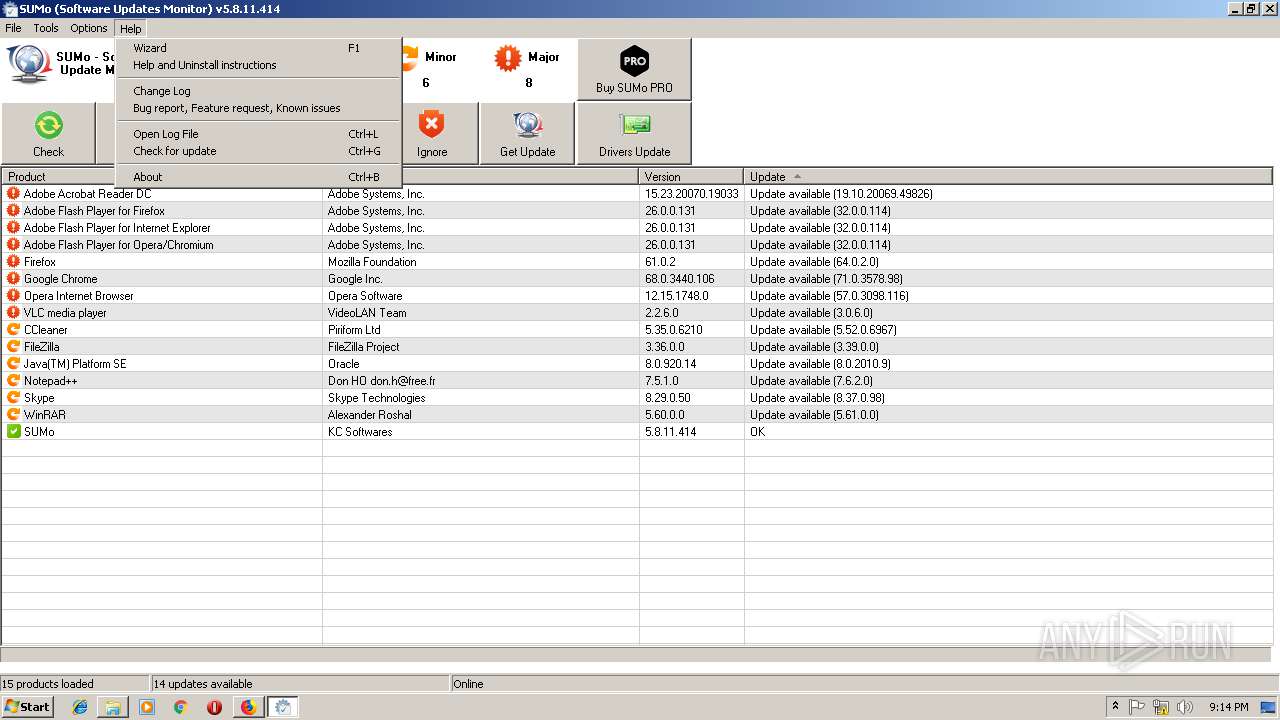
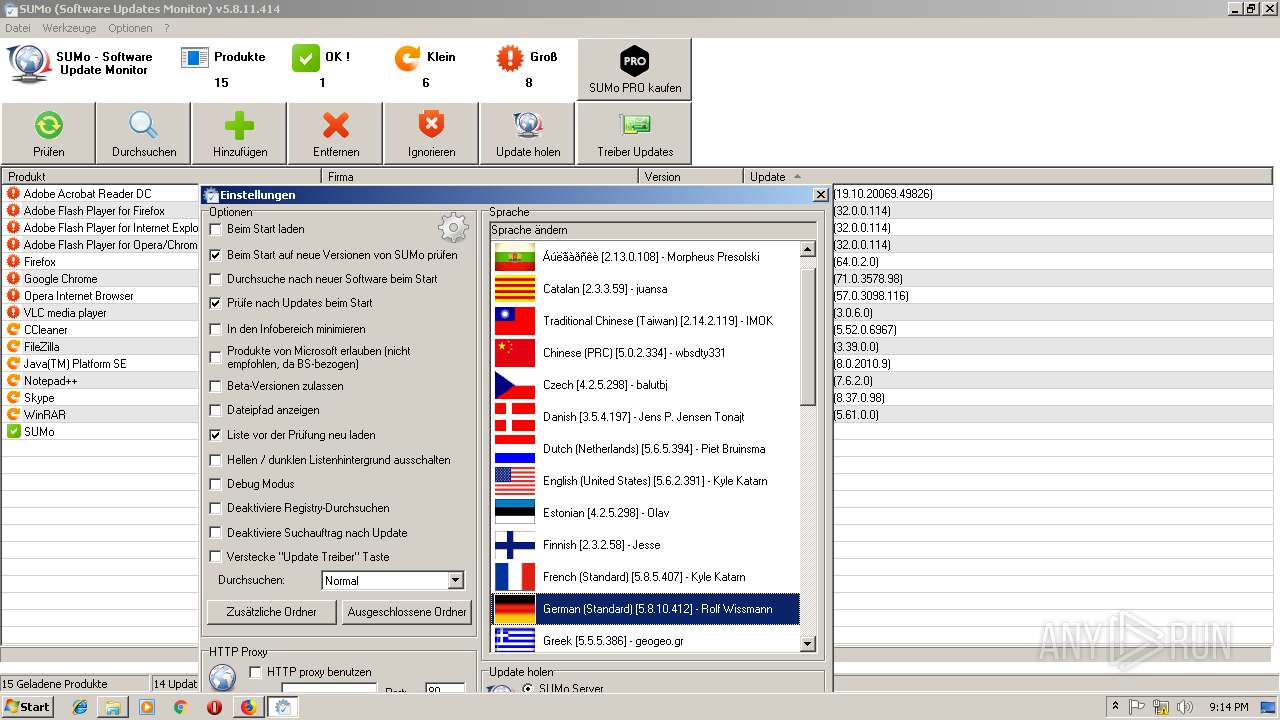
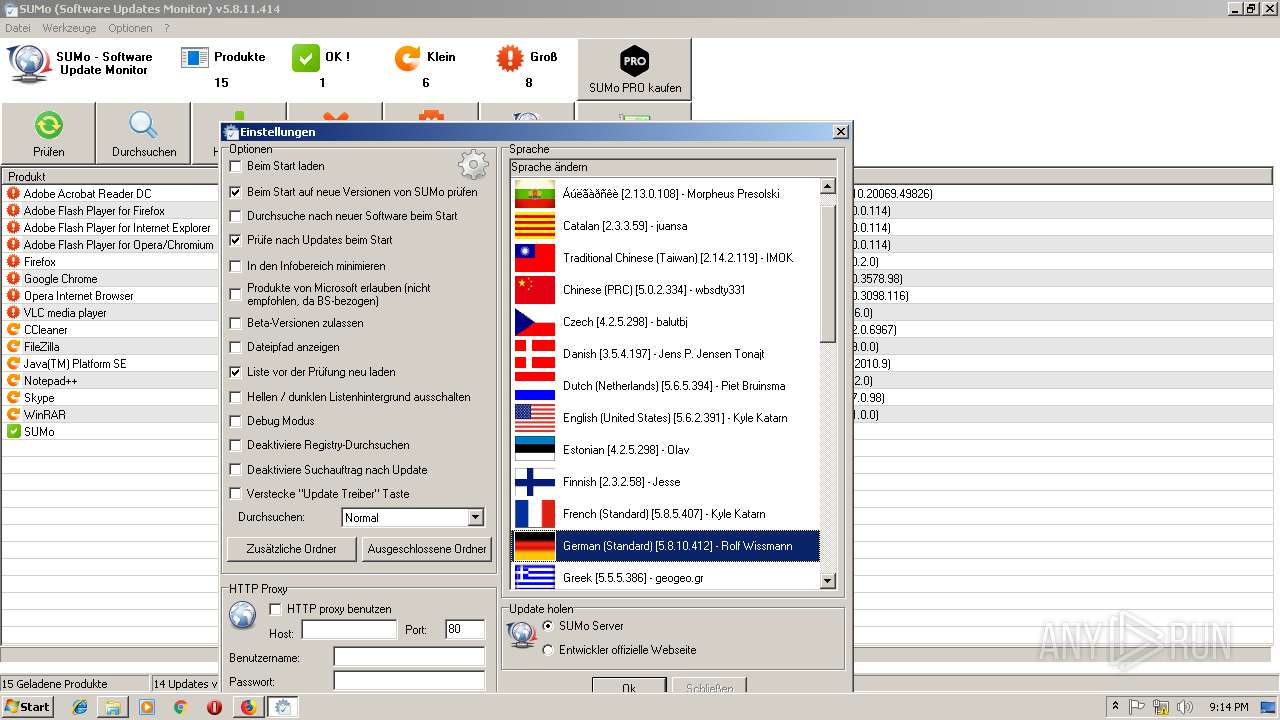
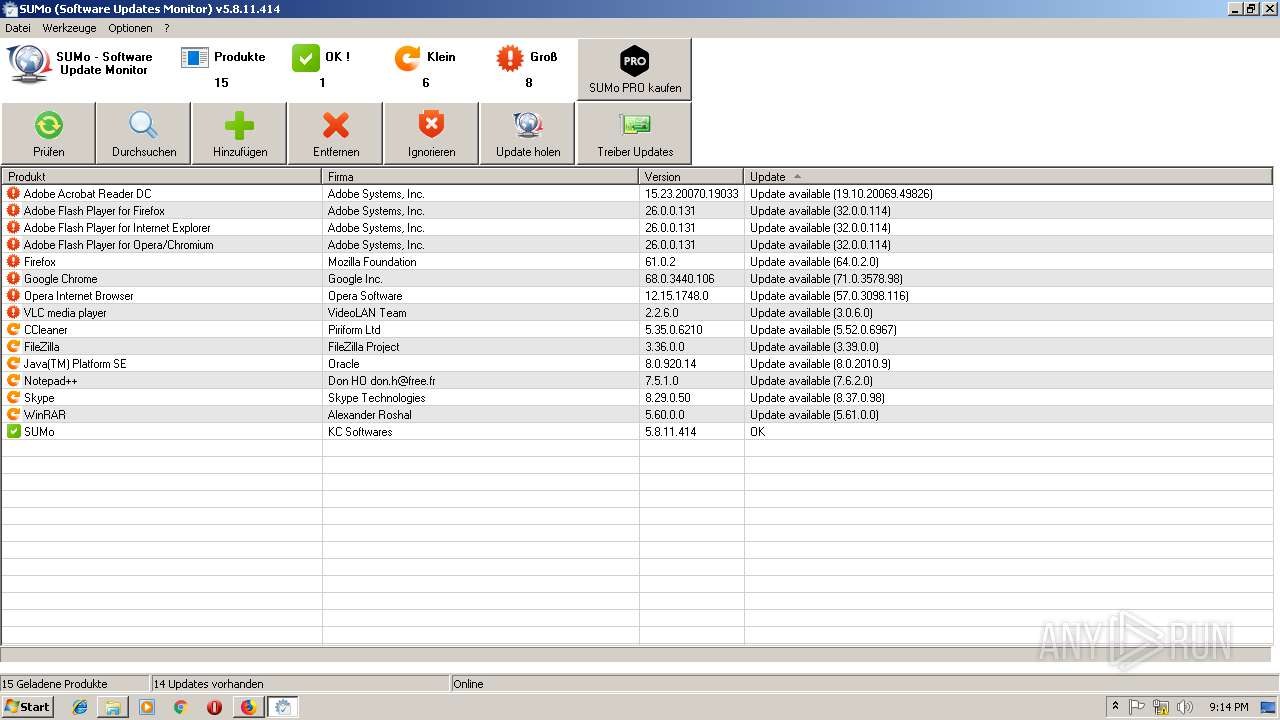
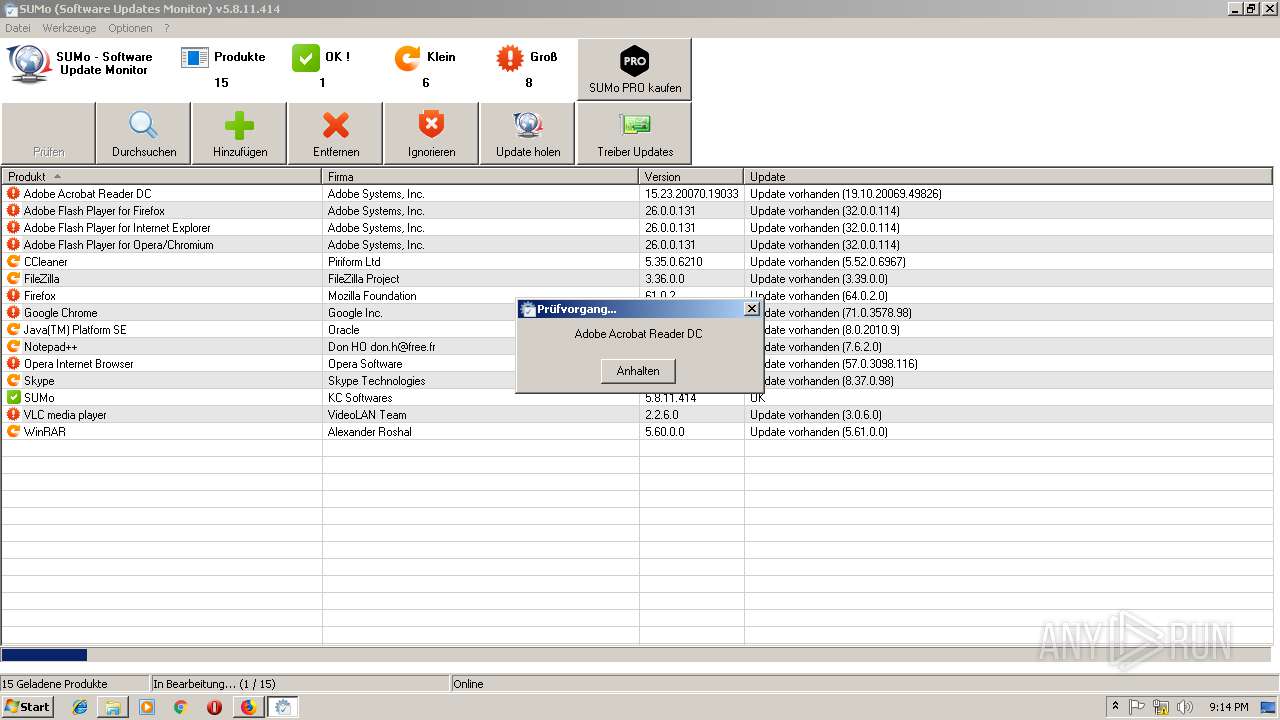
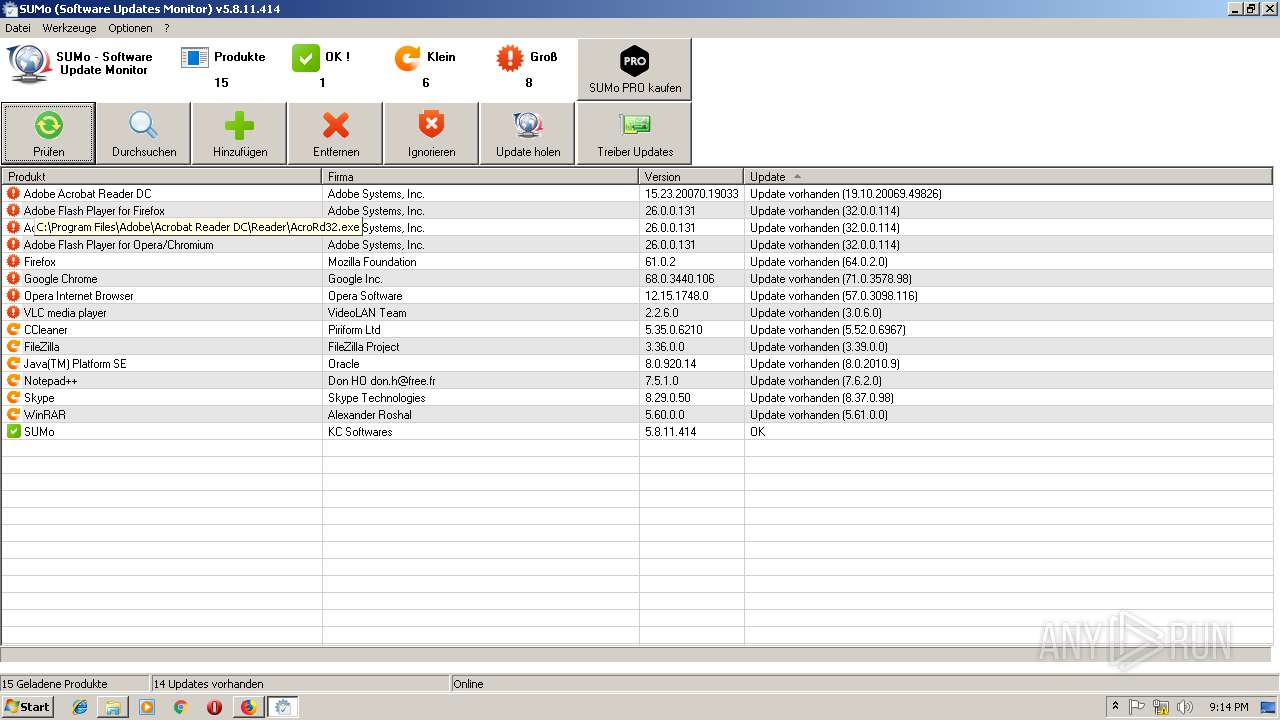
| URL: | https://kcsoftwares.com/files/sumo_lite.exe |
| Full analysis: | https://app.any.run/tasks/5b791a89-84f3-4d17-8aec-10f7dd1e8054 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2019, 21:10:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E1A24CFD2C6FAB2DA60783D4841DF3A3 |
| SHA1: | 5E6276931D369BE311B13649494F6FBDA2787C6E |
| SHA256: | 6A099BE79F603AACCD849B6C8600042529A36B1B2BFA277C2A0CAC3E55ADD182 |
| SSDEEP: | 3:N8DWY0EXGU0KYhAC:2KY0EWqC |
MALICIOUS
Changes settings of System certificates
- explorer.exe (PID: 2028)
Application was dropped or rewritten from another process
- sumo_lite.exe (PID: 2188)
- sumo_lite.exe (PID: 3232)
- SUMo.exe (PID: 3216)
- SUMo.exe (PID: 2352)
Loads dropped or rewritten executable
- SUMo.exe (PID: 3216)
- SUMo.exe (PID: 2352)
SUSPICIOUS
Executable content was dropped or overwritten
- sumo_lite.exe (PID: 3232)
- sumo_lite.tmp (PID: 3272)
- sumo_lite.exe (PID: 2188)
- firefox.exe (PID: 3000)
Starts Internet Explorer
- sumo_lite.tmp (PID: 3272)
- SUMo.exe (PID: 3216)
Creates files in the user directory
- sumo_lite.tmp (PID: 3272)
- SUMo.exe (PID: 3216)
- SUMo.exe (PID: 2352)
Reads Internet Cache Settings
- SUMo.exe (PID: 3216)
- explorer.exe (PID: 2028)
Creates files in the program directory
- iexplore.exe (PID: 1488)
- SUMo.exe (PID: 2352)
INFO
Reads CPU info
- firefox.exe (PID: 2608)
- firefox.exe (PID: 3000)
- firefox.exe (PID: 3336)
- firefox.exe (PID: 3620)
Reads settings of System Certificates
- firefox.exe (PID: 3000)
- explorer.exe (PID: 2028)
Application launched itself
- firefox.exe (PID: 3000)
- iexplore.exe (PID: 2516)
Loads dropped or rewritten executable
- sumo_lite.tmp (PID: 3272)
Creates files in the program directory
- sumo_lite.tmp (PID: 3272)
Creates files in the user directory
- firefox.exe (PID: 3000)
- iexplore.exe (PID: 1488)
- iexplore.exe (PID: 2128)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3752)
Creates a software uninstall entry
- sumo_lite.tmp (PID: 3272)
Application was dropped or rewritten from another process
- sumo_lite.tmp (PID: 2812)
- sumo_lite.tmp (PID: 3272)
Changes internet zones settings
- iexplore.exe (PID: 1944)
- iexplore.exe (PID: 2516)
Changes settings of System certificates
- iexplore.exe (PID: 1488)
Reads internet explorer settings
- iexplore.exe (PID: 1488)
- iexplore.exe (PID: 2128)
Reads Internet Cache Settings
- iexplore.exe (PID: 1488)
- iexplore.exe (PID: 1944)
- iexplore.exe (PID: 2128)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
16
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1944 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | sumo_lite.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2516 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
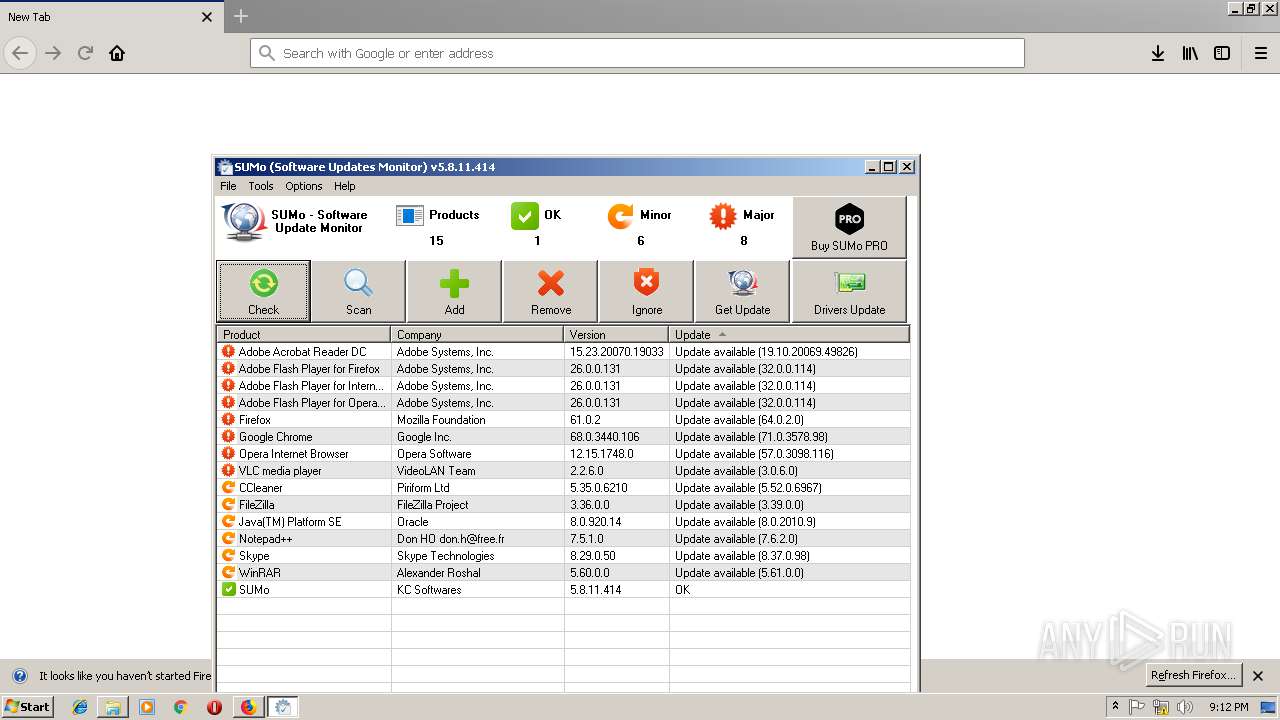
| 2188 | "C:\Users\admin\Downloads\sumo_lite.exe" /SPAWNWND=$301F6 /NOTIFYWND=$40204 | C:\Users\admin\Downloads\sumo_lite.exe | sumo_lite.tmp | ||||||||||||
User: admin Company: KC Softwares Integrity Level: HIGH Description: KC Softwares SUMo Setup Exit code: 0 Version: 5.8.11.414 Modules
| |||||||||||||||
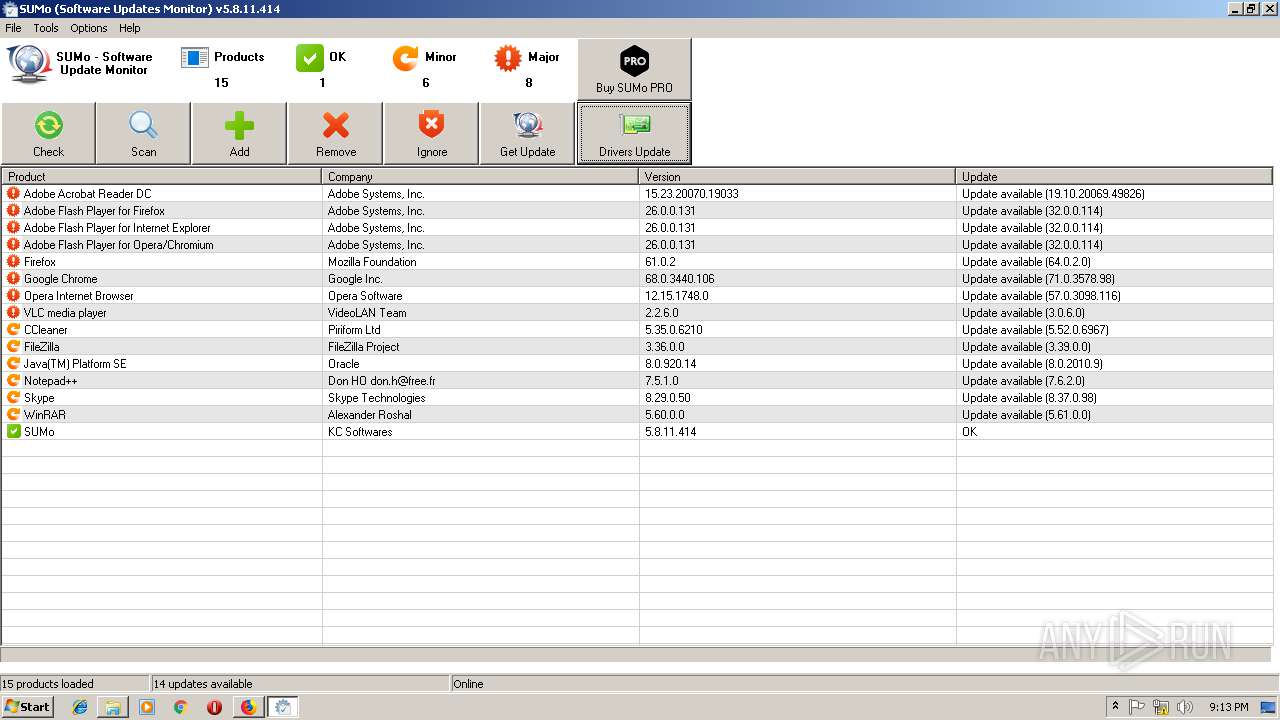
| 2352 | "C:\Program Files\KC Softwares\SUMo\SUMo.exe" | C:\Program Files\KC Softwares\SUMo\SUMo.exe | explorer.exe | ||||||||||||
User: admin Company: KC Softwares Integrity Level: MEDIUM Description: SUMo Exit code: 0 Version: 5.8.11.414 Modules
| |||||||||||||||
| 2516 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | SUMo.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2608 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3000.0.281993157\1447491283" -childID 1 -isForBrowser -prefsHandle 1360 -prefsLen 8310 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3000 "\\.\pipe\gecko-crash-server-pipe.3000" 708 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2812 | "C:\Users\admin\AppData\Local\Temp\is-AUP7P.tmp\sumo_lite.tmp" /SL5="$40204,2106972,163328,C:\Users\admin\Downloads\sumo_lite.exe" | C:\Users\admin\AppData\Local\Temp\is-AUP7P.tmp\sumo_lite.tmp | — | sumo_lite.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://kcsoftwares.com/files/sumo_lite.exe | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
Total events
5 344
Read events
4 605
Write events
723
Delete events
16
Modification events
| (PID) Process: | (3000) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3000) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | 308046O0NS4N39PO |
Value: 000000000300000004000000F5200000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF80FBE5745B48D40100000000 | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002D0000003E000000B34B1500090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000F000000E21705007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E006500780065000000D201B0E536027CE43602A532DC75BCE4360294E5360200000000B432DC75F4E536020145DC756A00CA028C00CA02B8ACCA0278E336020001000101000000000100000000000028FCA802C8E53602E0E2BF02A4E53602CAFEBF02A0E33602D4E536026000CA022B0000006A00CA0228FCA802000000008C00CA025CE536020A00CA020000000005000500A823D3016601CA022B0000000F000000F4E53602BCE5360228FCA8021000000074FFA802050017004E1ED301BCE436021600000002000000B8ACCA020400360228FCA80203000000000000000909090009090909000911110000000011000000B8452700B04527000000000000000000000000000000000000000000000000001CE400005A743083D0E336028291F5751CE43602CCB700002E743083E4E33602B69CF575D0B7DD024C060000FCE3360240B3DD0208E43602789CF57511000000B8452700B045270060B3DD026CE40000E67330831CE436028291F5756CE4360220E436022795F57500000000CCB7DD0248E43602CD94F575CCB7DD02F4E4360240B3DD02E194F5750000000040B3DD02F4E4360250E43602090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
| (PID) Process: | (3000) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3000) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3000) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000020000000700000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0000000001000000020000000400000003000000FFFFFFFF | |||
Executable files
10
Suspicious files
112
Text files
128
Unknown types
42
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cert9.db-journal | — | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\cache2\entries\E53F2EE24A155615482D34F5E87147E8DDADD57D | der | |
MD5:— | SHA256:— | |||
| 3000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cert9.db | sqlite | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
72
DNS requests
59
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3000 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3000 | firefox.exe | POST | 200 | 72.247.178.18:80 | http://ocsp.int-x3.letsencrypt.org/ | NL | der | 527 b | whitelisted |
2128 | iexplore.exe | GET | 200 | 213.186.33.69:80 | http://www.kcsoftwares.com/?page=dumo&showads | FR | html | 5.80 Kb | malicious |
3000 | firefox.exe | POST | 200 | 172.217.22.14:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
3000 | firefox.exe | POST | 200 | 172.217.22.14:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
2128 | iexplore.exe | GET | 200 | 213.186.33.69:80 | http://www.kcsoftwares.com/images/kclogo.png | FR | image | 1.15 Kb | malicious |
2128 | iexplore.exe | GET | 404 | 173.194.76.82:80 | http://html5shim.googlecode.com/svn/trunk/html5.js | US | html | 1.54 Kb | whitelisted |
2028 | explorer.exe | GET | 200 | 91.199.212.52:80 | http://crt.comodoca.com/COMODORSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
2128 | iexplore.exe | GET | 200 | 172.217.22.34:80 | http://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 29.1 Kb | whitelisted |
3216 | SUMo.exe | GET | 200 | 185.7.248.1:80 | http://www.kc-softwares.com/check.txt | NL | binary | 1 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3000 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3000 | firefox.exe | 213.186.33.69:443 | kcsoftwares.com | OVH SAS | FR | malicious |
3000 | firefox.exe | 72.247.178.18:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | NL | whitelisted |
3000 | firefox.exe | 52.89.32.107:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3000 | firefox.exe | 52.34.107.172:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3000 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3000 | firefox.exe | 172.217.22.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
1944 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3000 | firefox.exe | 172.217.22.14:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3000 | firefox.exe | 172.217.21.206:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
kcsoftwares.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
a771.dscq.akamai.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |