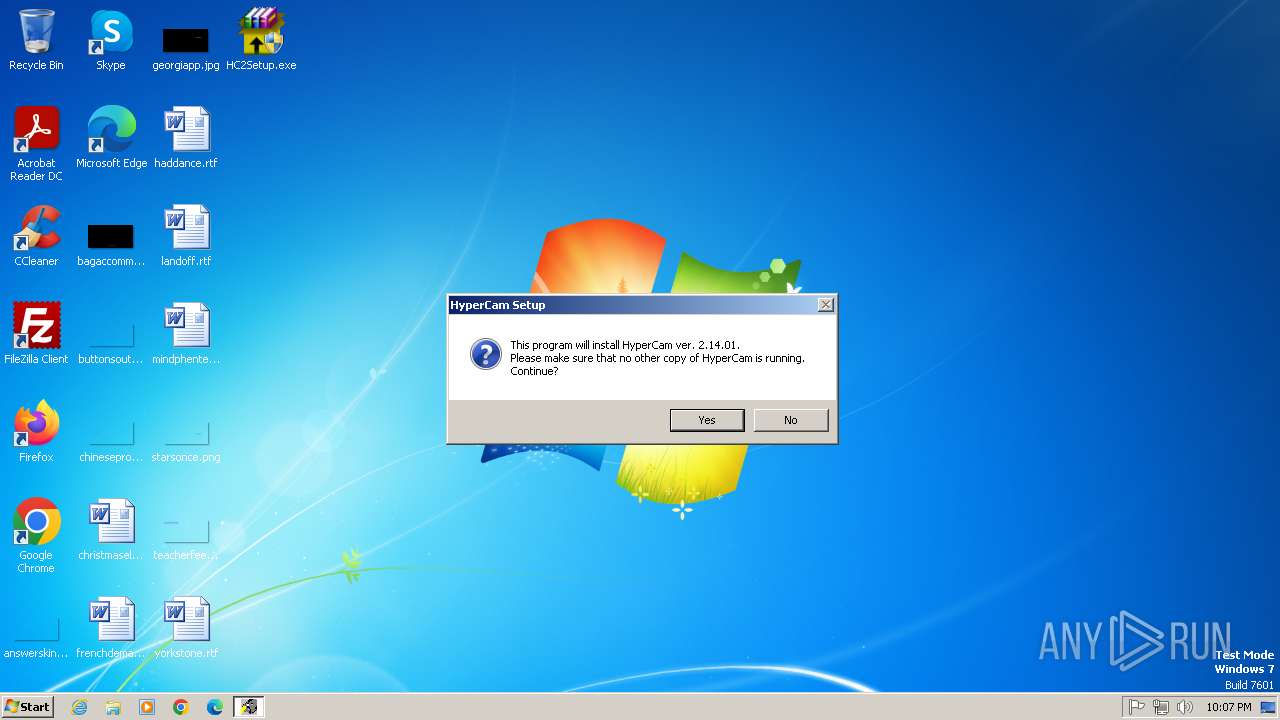
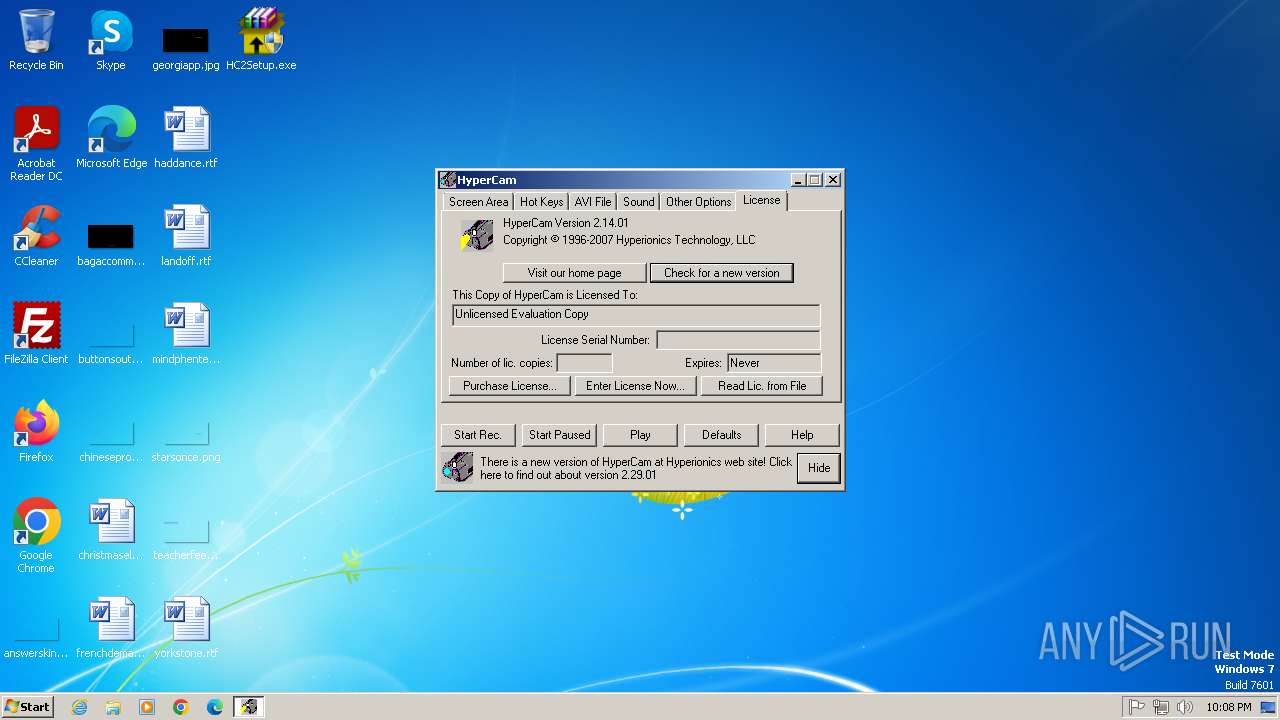
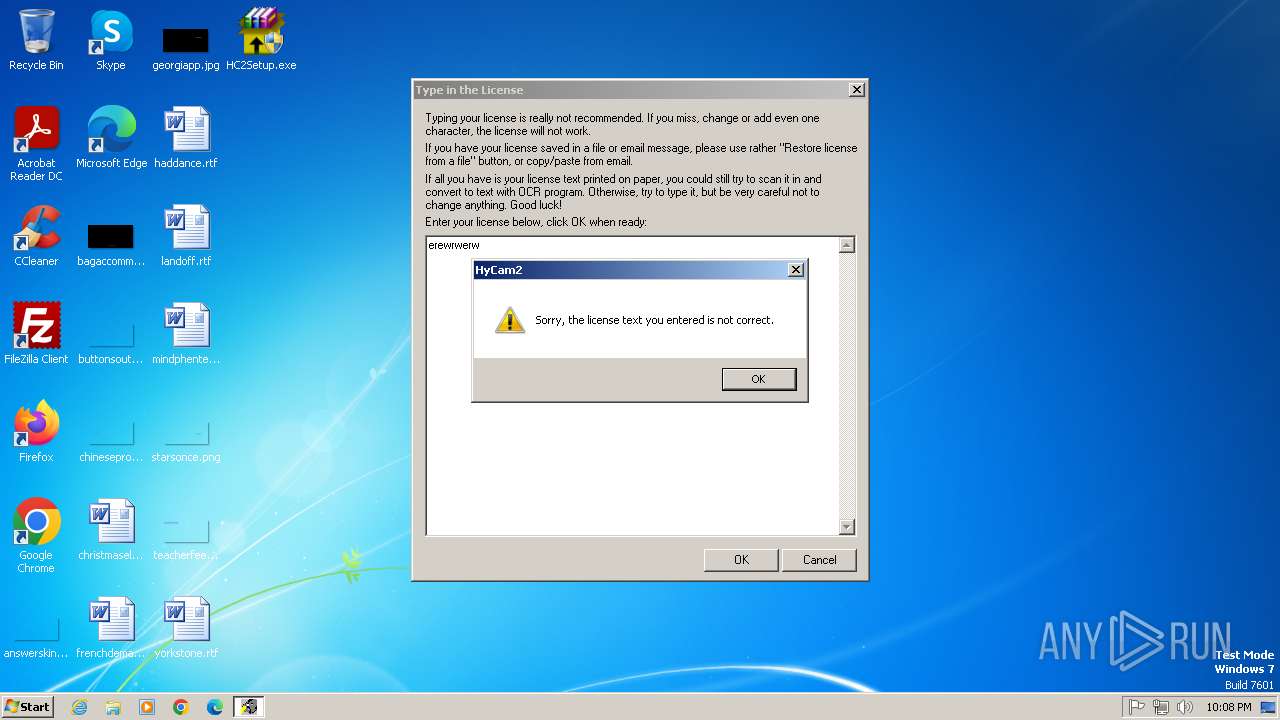
| File name: | HC2Setup.exe |
| Full analysis: | https://app.any.run/tasks/f6494e40-9a02-495f-852e-357b998bcad7 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 21:07:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive, 4 sections |
| MD5: | F96A73B23464366E4158620B10FA52C5 |
| SHA1: | 1B048D127670EA9C113C3582C7D2BFDE2BC4B32A |
| SHA256: | 6A06B2BA1A32B703D65F43D49DDAA8E74D8F5ADD21A8AB04AA0044937A5A50C5 |
| SSDEEP: | 24576:Lev+eq3WBaH4tnpWrcLkx0j6a0BkIgsgq4bSu2wU1DjsJMY9cLYelTgJORXs:a5BaYtnpWrcLkx0j6amkIgsgqASu2wU+ |
MALICIOUS
Executing a file with an untrusted certificate
- HC2Setup.exe (PID: 2060)
- HC2Setup.exe (PID: 576)
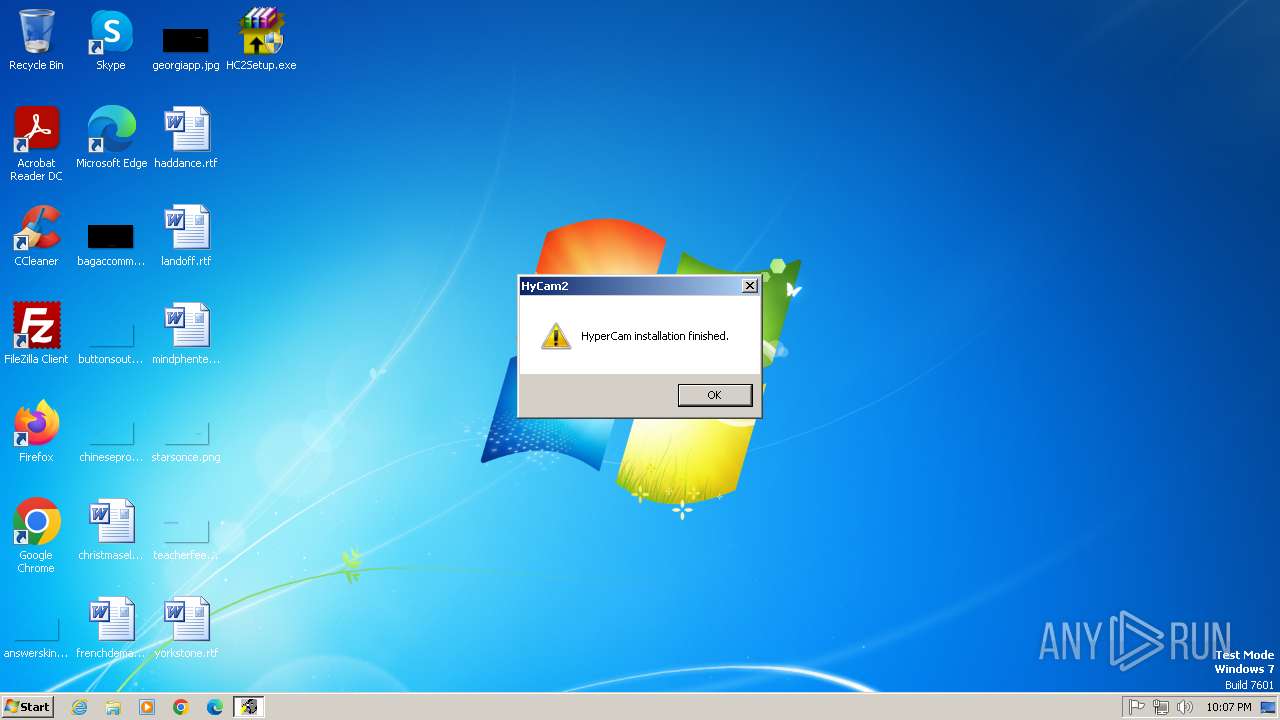
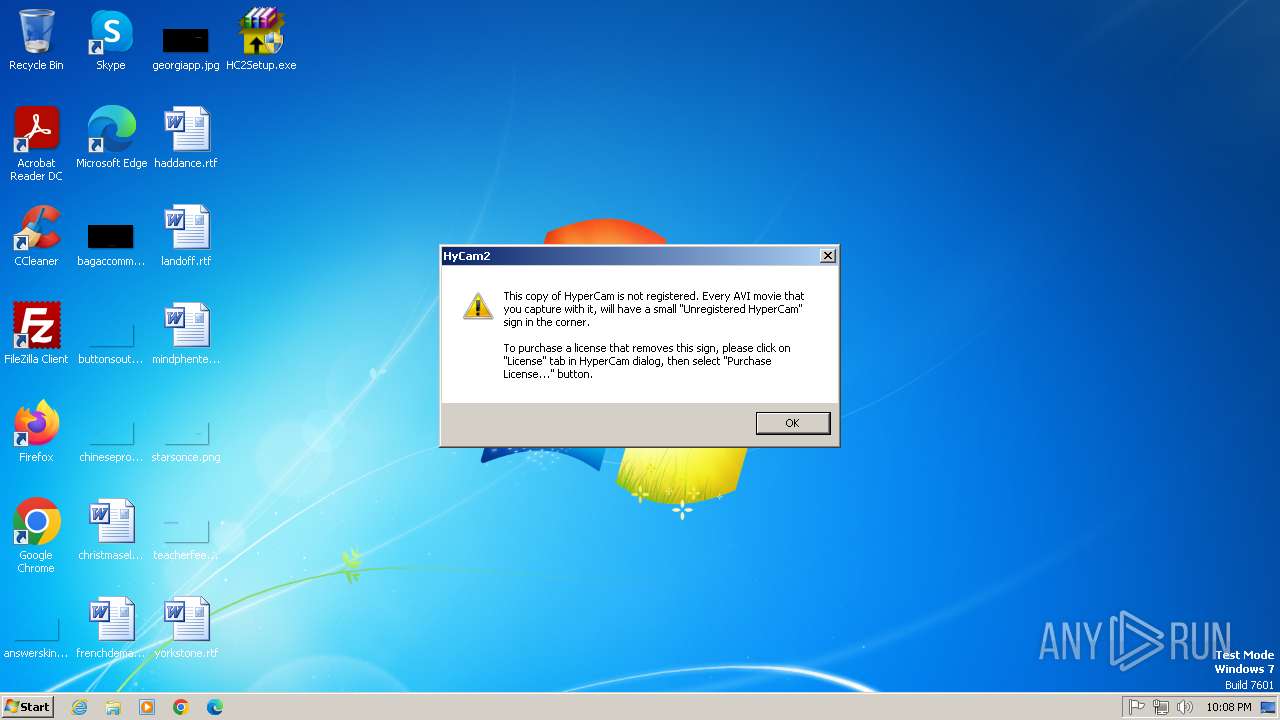
- HyCam2.exe (PID: 1824)
- HyCam2.exe (PID: 2304)
- HyCam2.exe (PID: 3016)
SUSPICIOUS
Executable content was dropped or overwritten
- HC2Setup.exe (PID: 576)
- HyCam2.exe (PID: 1824)
- CCleaner.exe (PID: 988)
Reads security settings of Internet Explorer
- HC2Setup.exe (PID: 576)
- HyCam2.exe (PID: 3016)
- CCleaner.exe (PID: 988)
Reads the Internet Settings
- HC2Setup.exe (PID: 576)
- HyCam2.exe (PID: 3016)
- CCleaner.exe (PID: 988)
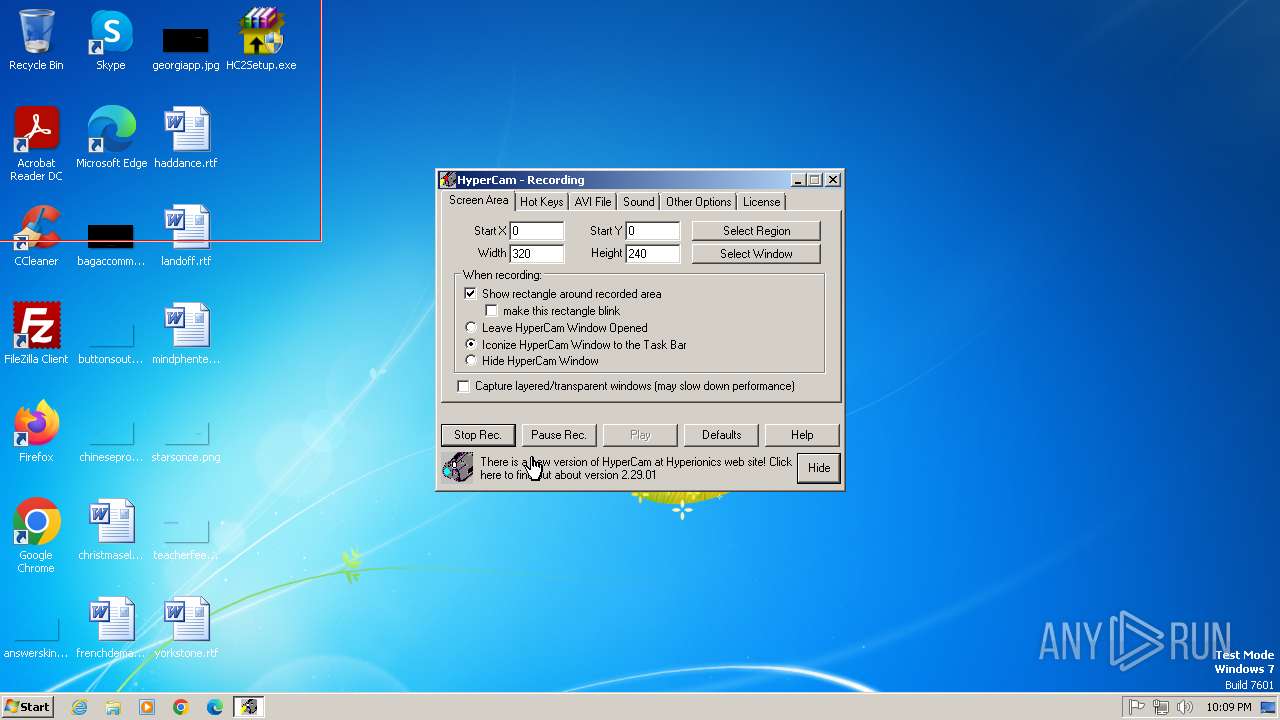
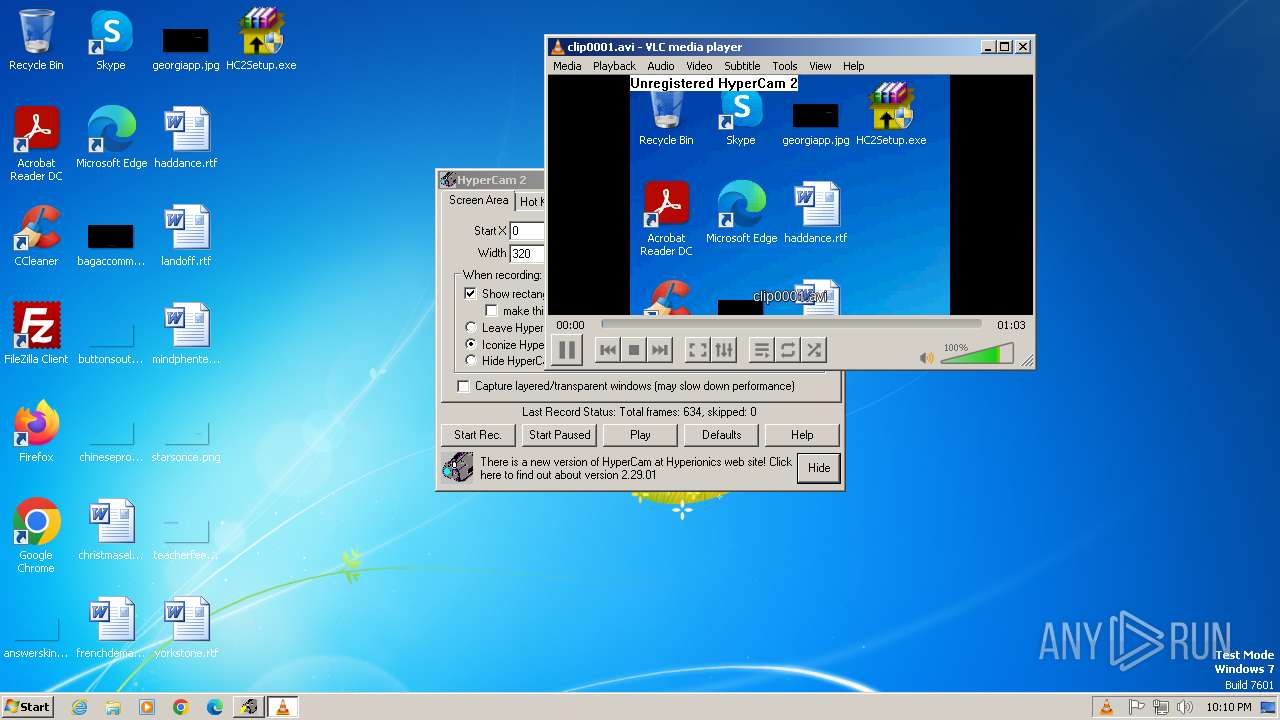
There is functionality for taking screenshot (YARA)
- HyCam2.exe (PID: 1824)
- HyCam2.exe (PID: 3016)
- vlc.exe (PID: 2784)
Starts itself from another location
- HyCam2.exe (PID: 1824)
Creates a software uninstall entry
- HyCam2.exe (PID: 1824)
The process executes via Task Scheduler
- CCleaner.exe (PID: 988)
Reads Internet Explorer settings
- CCleaner.exe (PID: 988)
Reads the date of Windows installation
- CCleaner.exe (PID: 988)
Reads settings of System Certificates
- CCleaner.exe (PID: 988)
Checks for external IP
- svchost.exe (PID: 1080)
- CCleaner.exe (PID: 988)
Searches for installed software
- CCleaner.exe (PID: 988)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 988)
INFO
Checks supported languages
- HC2Setup.exe (PID: 576)
- HyCam2.exe (PID: 1824)
- HyCam2.exe (PID: 2304)
- HyCam2.exe (PID: 3016)
- CCleaner.exe (PID: 1500)
- CCleaner.exe (PID: 988)
- vlc.exe (PID: 2784)
The sample compiled with english language support
- HC2Setup.exe (PID: 576)
- HyCam2.exe (PID: 1824)
- CCleaner.exe (PID: 988)
Create files in a temporary directory
- HC2Setup.exe (PID: 576)
Reads the computer name
- HC2Setup.exe (PID: 576)
- HyCam2.exe (PID: 1824)
- HyCam2.exe (PID: 2304)
- HyCam2.exe (PID: 3016)
- CCleaner.exe (PID: 1500)
- CCleaner.exe (PID: 988)
- vlc.exe (PID: 2784)
Creates files in the program directory
- HyCam2.exe (PID: 1824)
- CCleaner.exe (PID: 988)
Checks proxy server information
- HyCam2.exe (PID: 3016)
- CCleaner.exe (PID: 988)
Reads the machine GUID from the registry
- HyCam2.exe (PID: 3016)
- CCleaner.exe (PID: 988)
Creates files or folders in the user directory
- HyCam2.exe (PID: 3016)
- CCleaner.exe (PID: 988)
Manual execution by a user
- CCleaner.exe (PID: 1500)
- HyCam2.exe (PID: 3016)
Reads Environment values
- CCleaner.exe (PID: 1500)
- CCleaner.exe (PID: 988)
Reads CPU info
- CCleaner.exe (PID: 988)
Reads product name
- CCleaner.exe (PID: 988)
Reads the software policy settings
- CCleaner.exe (PID: 988)
The process uses Lua
- vlc.exe (PID: 2784)
Detects AutoHotkey samples (YARA)
- CCleaner.exe (PID: 988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.8) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2006:09:13 18:20:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 77824 |
| InitializedDataSize: | 28672 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
49
Monitored processes
9
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 576 | "C:\Users\admin\Desktop\HC2Setup.exe" | C:\Users\admin\Desktop\HC2Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 988 | "C:\Program Files\CCleaner\CCleaner.exe" /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1500 | "C:\Program Files\CCleaner\CCleaner.exe" | C:\Program Files\CCleaner\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\HyCam2.exe" -install | C:\Users\admin\AppData\Local\Temp\RarSFX0\HyCam2.exe | HC2Setup.exe | ||||||||||||
User: admin Company: Hyperionics Integrity Level: HIGH Description: HyperCam Exit code: 0 Version: 2, 14, 1, 0 Modules
| |||||||||||||||
| 2060 | "C:\Users\admin\Desktop\HC2Setup.exe" | C:\Users\admin\Desktop\HC2Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2304 | "C:\Program Files\HyCam2\HyCam2.exe" -regonly | C:\Program Files\HyCam2\HyCam2.exe | — | HyCam2.exe | |||||||||||
User: admin Company: Hyperionics Integrity Level: HIGH Description: HyperCam Exit code: 0 Version: 2, 14, 1, 0 Modules
| |||||||||||||||
| 2784 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Documents\clip0001.avi" | C:\Program Files\VideoLAN\VLC\vlc.exe | HyCam2.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 3016 | "C:\Program Files\HyCam2\HyCam2.exe" | C:\Program Files\HyCam2\HyCam2.exe | explorer.exe | ||||||||||||
User: admin Company: Hyperionics Integrity Level: MEDIUM Description: HyperCam Exit code: 20 Version: 2, 14, 1, 0 Modules
| |||||||||||||||
Total events
39 433
Read events
38 996
Write events
351
Delete events
86
Modification events
| (PID) Process: | (576) HC2Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (576) HC2Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (576) HC2Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (576) HC2Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: D4DA6D3E3157 | |||
| (PID) Process: | (1824) HyCam2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HyperCam 2 |
| Operation: | write | Name: | DisplayName |
Value: HyperCam 2 | |||
| (PID) Process: | (1824) HyCam2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HyperCam 2 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\HyCam2\UnHyCam2.exe" | |||
| (PID) Process: | (2304) HyCam2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{AAA0A636-928C-11D1-9AD0-0000C0597CC8}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3016) HyCam2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3016) HyCam2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
Executable files
15
Suspicious files
77
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\8-8000d.wav | binary | |
MD5:1912519EA64D50843AE9084D37E8A0C1 | SHA256:5F8D2BDA27A1036902C82778FF4C947AC57D63D558C1D6F0AA4B168489774538 | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\16-8000u.wav | binary | |
MD5:0FCE94CFEC32E5D6084184A34DC60501 | SHA256:2A23479428FCD329D4025FB24C112466237B512A233828FA40B215276CCB84ED | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\8-11025d.wav | binary | |
MD5:A8BBF1676207514D90693EE2FB0364F8 | SHA256:D6A44B57B047E4FBCF4886A713CC5143AF065D157FD4972334DD7B5861798FE5 | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\HyCam2.exe | executable | |
MD5:596580454699FDC01B48029905171BD3 | SHA256:7465A6B09B41DBC3D0E3B564C6AC6334DC41FF2F3C2DC39BC9E37AEDE51B7272 | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\16-44100u.wav | binary | |
MD5:A1F0AB08672C56580FE2B1E5C08E8C03 | SHA256:798240FE89FD38E5FD6A57FBE4B683D8A93C78B9408349C50C0423637243ED27 | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\8-11025u.wav | binary | |
MD5:C928167AE840C4D092D2D11157458B72 | SHA256:C1D1F055679140D002EEADCD16FD2D72FA6BDC03E0649520E1CF4EEEA6182EF7 | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\16-44100d.wav | binary | |
MD5:77F67F35EE1E4F5BF4F76CCC072550BE | SHA256:46F00FEF0CEBE38DEEFBBA59F859B4A72906FA4A894DB552B0AFDB213C61FCFE | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\8-44100u.wav | binary | |
MD5:FA7805635EFE3D2B2F1891274413731F | SHA256:9CBB2AD958F1CF1D8EB111CF8813C18596473679220B393C6689F745CD9FDEB3 | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\16-8000d.wav | binary | |
MD5:596ED55E171623AD208EE78F1301F007 | SHA256:60C6967511ED8F42C1861F6396B36AE3838721E9FD1CCE512BB3C187D3C04A7D | |||
| 576 | HC2Setup.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\16-11025u.wav | binary | |
MD5:12A8E35F4B87AAE6DF4D824D4BF2D601 | SHA256:ED614186535078B71D7534F1B2A4DB00BB04389C81D7865D0241C7548A9B5D93 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
26
DNS requests
18
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3016 | HyCam2.exe | GET | 200 | 66.135.60.154:80 | http://www.hyperionics.com/vers/hc2.txt | unknown | — | — | malicious |
988 | CCleaner.exe | GET | 200 | 2.19.126.142:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
988 | CCleaner.exe | GET | 200 | 208.89.74.19:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?63d1509ae23d71fa | unknown | — | — | whitelisted |
988 | CCleaner.exe | GET | 200 | 208.89.74.19:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d1b9c1867f8c92da | unknown | — | — | whitelisted |
988 | CCleaner.exe | GET | 200 | 208.89.74.19:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c09d7db11f8f83d7 | unknown | — | — | whitelisted |
988 | CCleaner.exe | GET | 200 | 208.89.74.19:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6db5d24d9682e86a | unknown | — | — | whitelisted |
988 | CCleaner.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
988 | CCleaner.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
988 | CCleaner.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAXfj0A2M0oL7zuU%2F%2F2jetU%3D | unknown | — | — | whitelisted |
988 | CCleaner.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3016 | HyCam2.exe | 66.135.60.154:80 | www.hyperionics.com | COGECO-PEER1 | US | malicious |
988 | CCleaner.exe | 2.19.126.142:80 | ncc.avast.com | Akamai International B.V. | DE | whitelisted |
988 | CCleaner.exe | 34.117.223.223:443 | analytics.ff.avast.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
988 | CCleaner.exe | 2.19.225.128:443 | www.ccleaner.com | AKAMAI-AS | FR | whitelisted |
988 | CCleaner.exe | 34.111.24.1:443 | ipm-provider.ff.avast.com | GOOGLE | US | whitelisted |
988 | CCleaner.exe | 34.160.176.28:443 | shepherd.ff.avast.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.hyperionics.com |
| malicious |
ncc.avast.com |
| whitelisted |
analytics.ff.avast.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ipm-provider.ff.avast.com |
| whitelisted |
shepherd.ff.avast.com |
| whitelisted |
ip-info.ff.avast.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
988 | CCleaner.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
CCleaner.exe | [2025-04-29 21:09:01.739] [error ] [settings ] [ 988: 2356] [6000C4: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | [2025-04-29 21:09:03.170] [error ] [settings ] [ 988: 2420] [9434E9: 359] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | [2025-04-29 21:09:03.205] [error ] [Burger ] [ 988: 2420] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | [2025-04-29 21:09:03.206] [error ] [Burger ] [ 988: 2420] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | startCheckingLicense()
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|