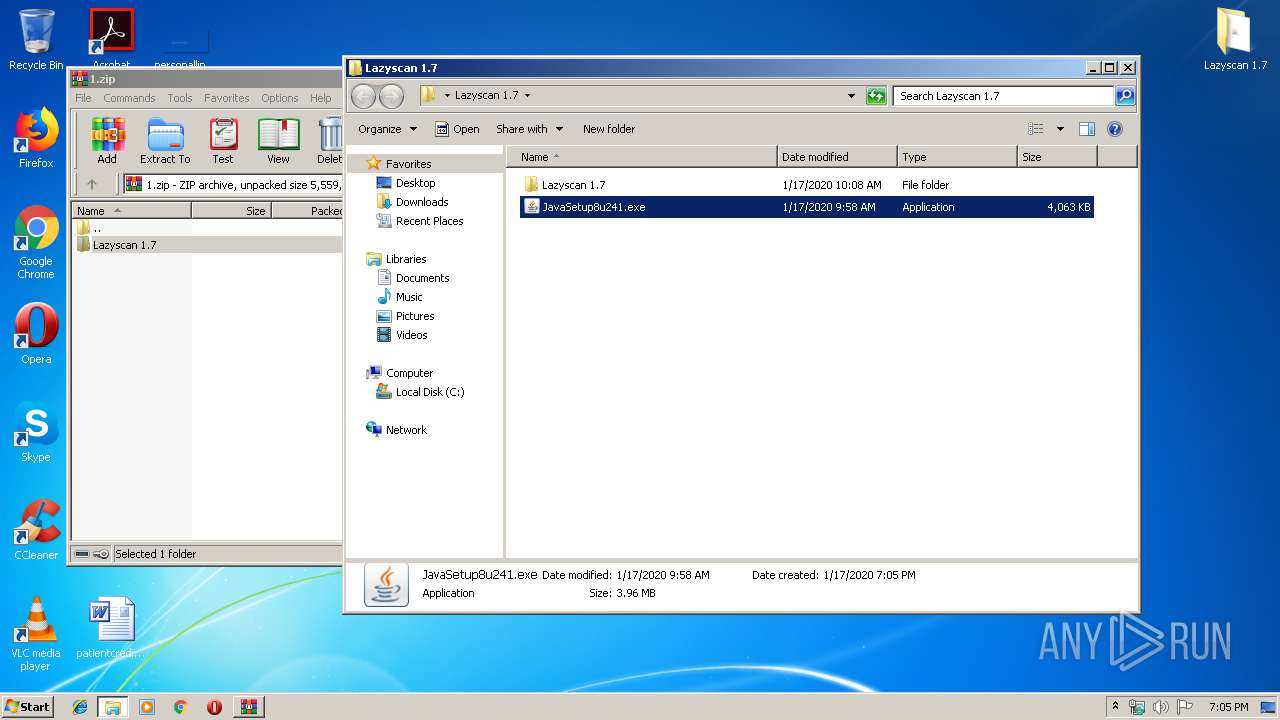
| File name: | 1.zip |
| Full analysis: | https://app.any.run/tasks/7c1ac9f8-4dd2-4d14-b4c4-052f1b17d772 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2020, 19:04:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D2E41C24C0ED4A673CF531DBF86FE661 |
| SHA1: | 4364C0CB16DE2E53D622207B022E0256EC80F803 |
| SHA256: | 6A056124300512066DD5894A36BA0C6C18D60E5617BA3BCBF8D595B3EEC6B6B4 |
| SSDEEP: | 98304:Ld2EgbacXP80VlECu8RkBaolRbGVINkNC7/P2EBTOrfLVMpl55EmURncmNTd:Ld5tGzlECuekBaofbGNCrtO7a750ppNR |
MALICIOUS
Application was dropped or rewritten from another process
- JavaSetup8u241.exe (PID: 1028)
- JavaSetup.exe (PID: 2604)
- Pictures.exe (PID: 2440)
- windows.exe (PID: 252)
- JavaSetup.exe (PID: 2840)
- JavaSetup.exe (PID: 1916)
Writes to a start menu file
- windows.exe (PID: 252)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2720)
- JavaSetup8u241.exe (PID: 1028)
- Pictures.exe (PID: 2440)
- JavaSetup.exe (PID: 1916)
Creates files in the program directory
- JavaSetup8u241.exe (PID: 1028)
- Pictures.exe (PID: 2440)
Creates files in the user directory
- windows.exe (PID: 252)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2440)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2440)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2484)
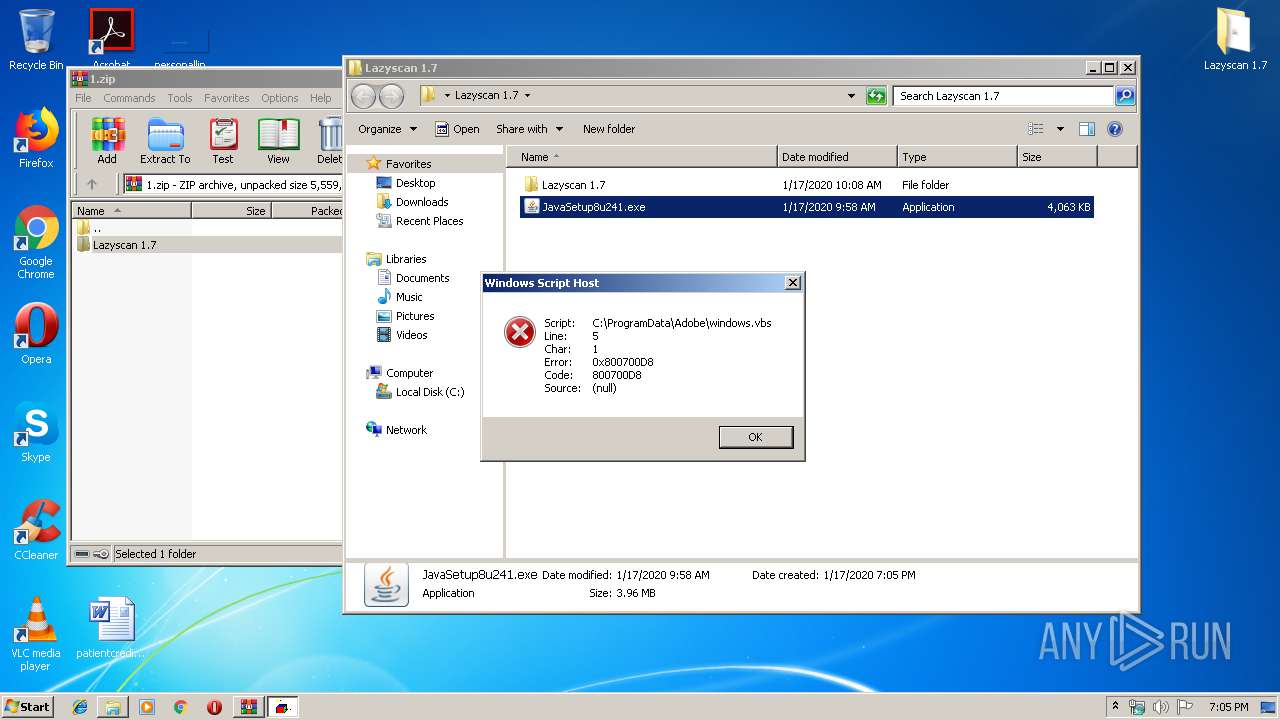
Executes scripts
- windows.exe (PID: 252)
Reads internet explorer settings
- JavaSetup.exe (PID: 2840)
INFO
Manual execution by user
- JavaSetup8u241.exe (PID: 1028)
- javaw.exe (PID: 2832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:01:17 20:12:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Lazyscan 1.7/ |
Total processes
51
Monitored processes
12
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\ProgramData\Adobe\windows.exe" | C:\ProgramData\Adobe\windows.exe | Pictures.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 964 | attrib +s +h C:\ProgramData\Adobe | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
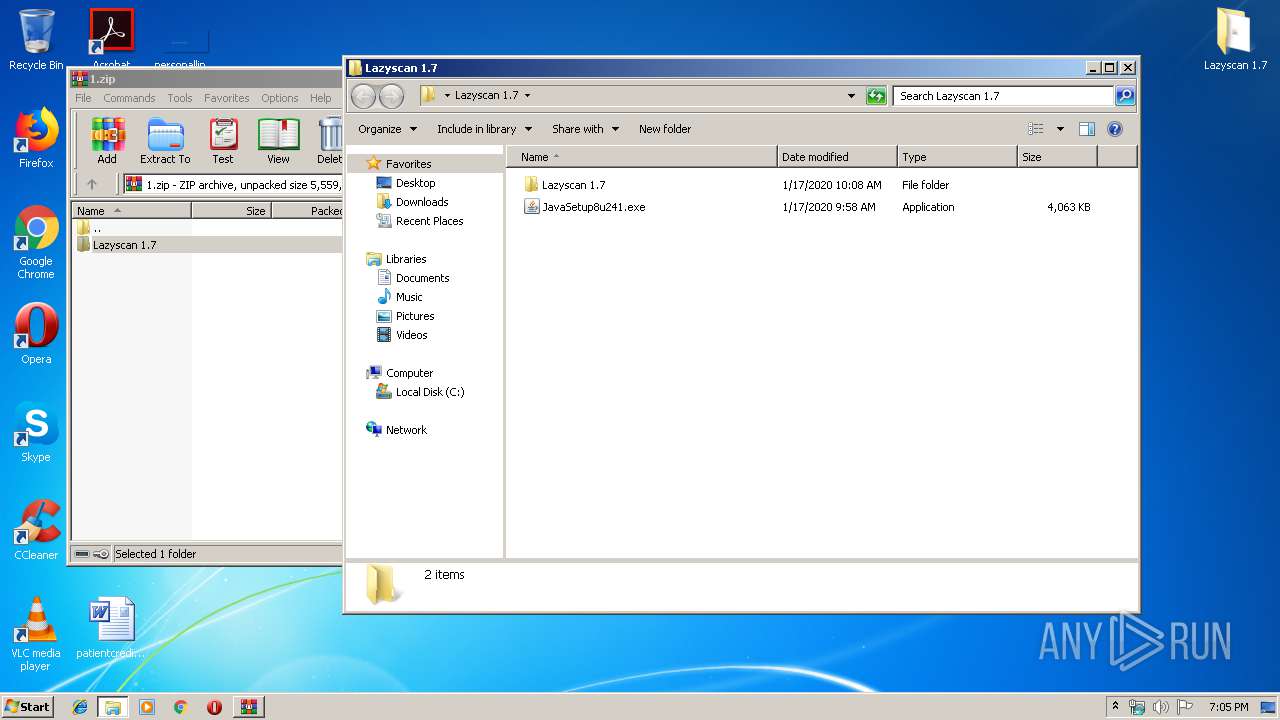
| 1028 | "C:\Users\admin\Desktop\Lazyscan 1.7\JavaSetup8u241.exe" | C:\Users\admin\Desktop\Lazyscan 1.7\JavaSetup8u241.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1876 | reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender" /v "DisableAntiSpyware" /t "REG_DWORD" /d "1" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1916 | "C:\ProgramData\JavaSetup.exe" | C:\ProgramData\JavaSetup.exe | JavaSetup8u241.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.2410.7 Modules
| |||||||||||||||
| 2440 | "C:\ProgramData\Pictures.exe" | C:\ProgramData\Pictures.exe | JavaSetup8u241.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2440 | cmd /c ""C:\ProgramData\Adobe\Disables.cmd" " | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2484 | "C:\Windows\System32\WScript.exe" "C:\ProgramData\Adobe\windows.vbs" | C:\Windows\System32\WScript.exe | — | windows.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2604 | "C:\ProgramData\JavaSetup.exe" | C:\ProgramData\JavaSetup.exe | — | JavaSetup8u241.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Exit code: 3221226540 Version: 8.0.2410.7 Modules
| |||||||||||||||
| 2720 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
727
Read events
674
Write events
53
Delete events
0
Modification events
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1.zip | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1028) JavaSetup8u241.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1028) JavaSetup8u241.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
7
Suspicious files
0
Text files
124
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
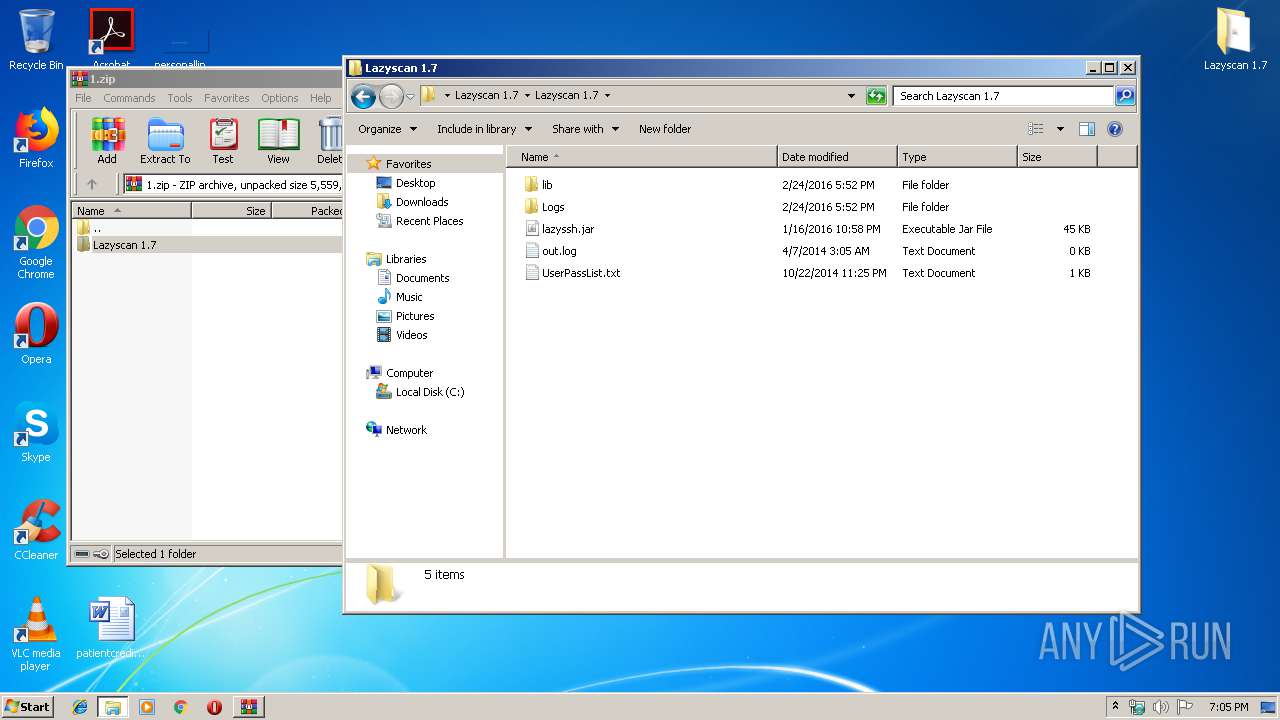
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2720.42148\Lazyscan 1.7\Lazyscan 1.7\lazyssh.jar | — | |
MD5:— | SHA256:— | |||
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2720.42148\Lazyscan 1.7\Lazyscan 1.7\lib\jsch-0.1.51.jar | — | |
MD5:— | SHA256:— | |||
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2720.42148\Lazyscan 1.7\Lazyscan 1.7\lib\mysql-connector-java-5.1.33-bin.jar | — | |
MD5:— | SHA256:— | |||
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2720.42148\Lazyscan 1.7\Lazyscan 1.7\lib\zip4j_1.3.2.jar | — | |
MD5:— | SHA256:— | |||
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2720.42148\Lazyscan 1.7\Lazyscan 1.7\Logs\LIVE.txt | — | |
MD5:— | SHA256:— | |||
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2720.42148\Lazyscan 1.7\Lazyscan 1.7\Logs\WRONG.txt | — | |
MD5:— | SHA256:— | |||
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2720.42148\Lazyscan 1.7\Lazyscan 1.7\UserPassList.txt | — | |
MD5:— | SHA256:— | |||
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2720.42148\Lazyscan 1.7\JavaSetup8u241.exe | executable | |
MD5:— | SHA256:— | |||
| 2440 | Pictures.exe | C:\ProgramData\Adobe\config.json | text | |
MD5:— | SHA256:— | |||
| 1028 | JavaSetup8u241.exe | C:\ProgramData\JavaSetup.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2840 | JavaSetup.exe | 95.100.141.142:443 | javadl-esd-secure.oracle.com | Akamai Technologies, Inc. | — | unknown |
2840 | JavaSetup.exe | 2.19.41.212:443 | javadl.oracle.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
javadl-esd-secure.oracle.com |
| whitelisted |
dns.msftncsi.com |
| shared |
javadl.oracle.com |
| whitelisted |