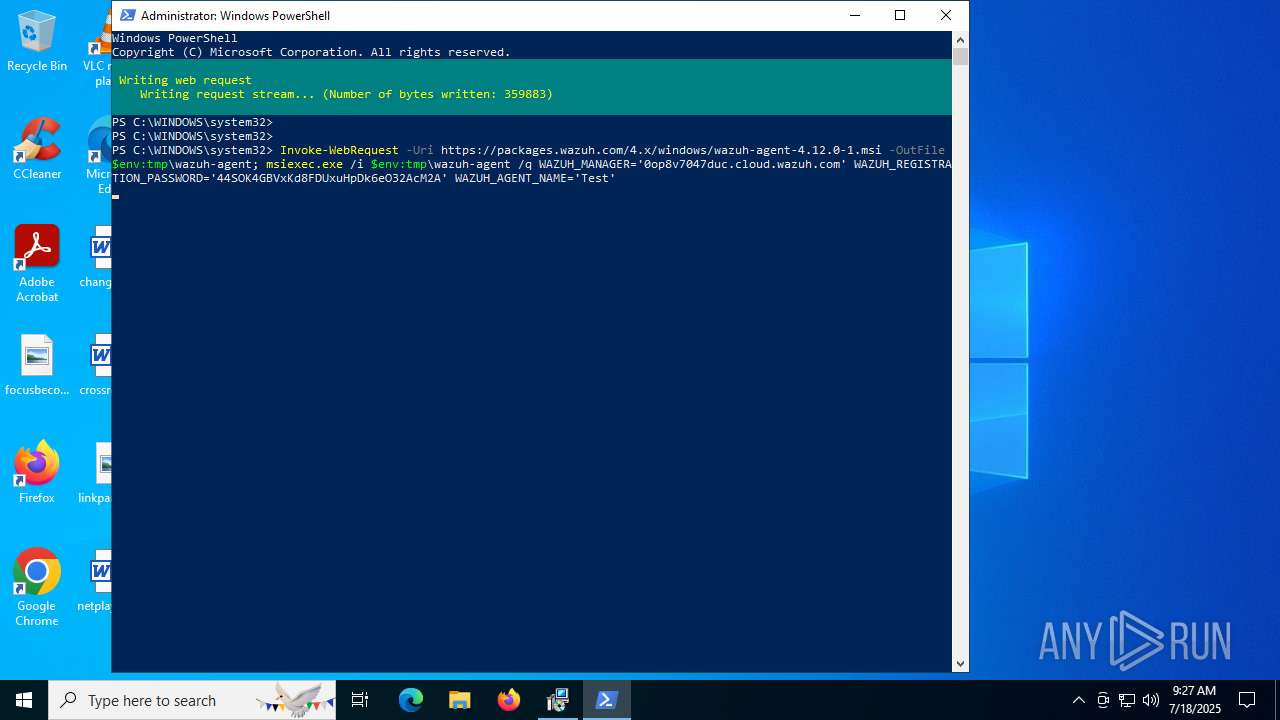
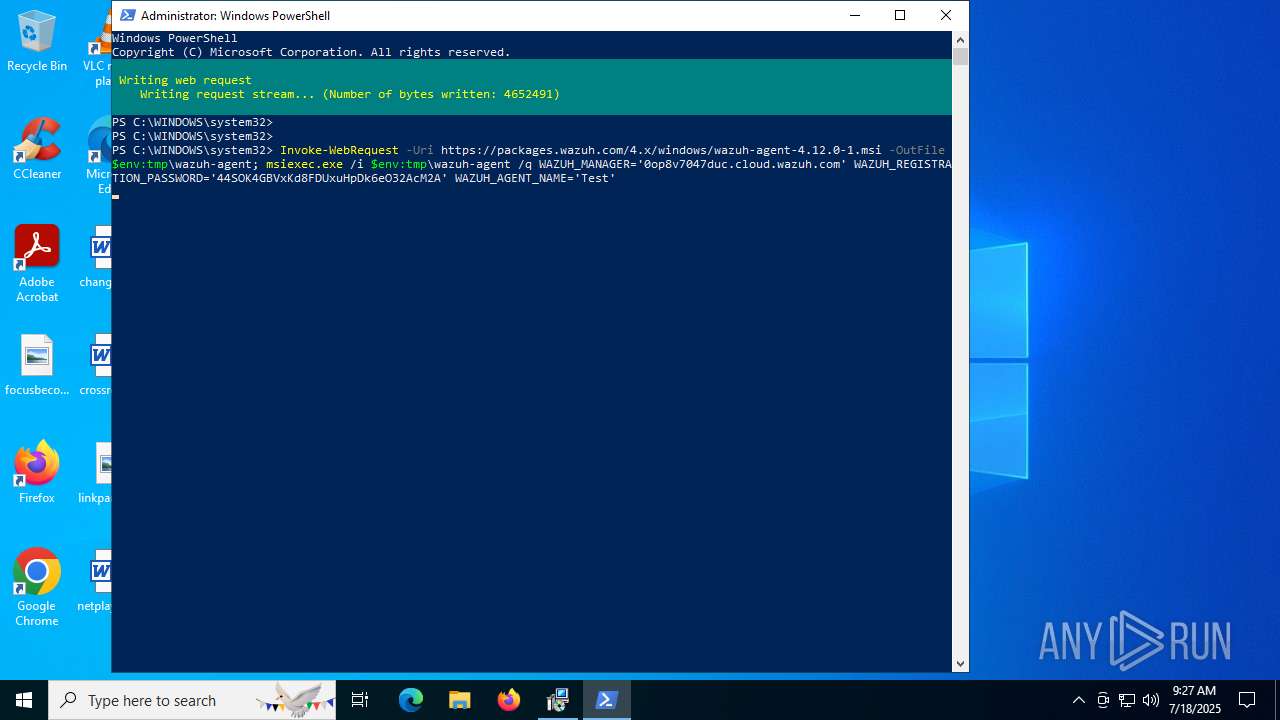
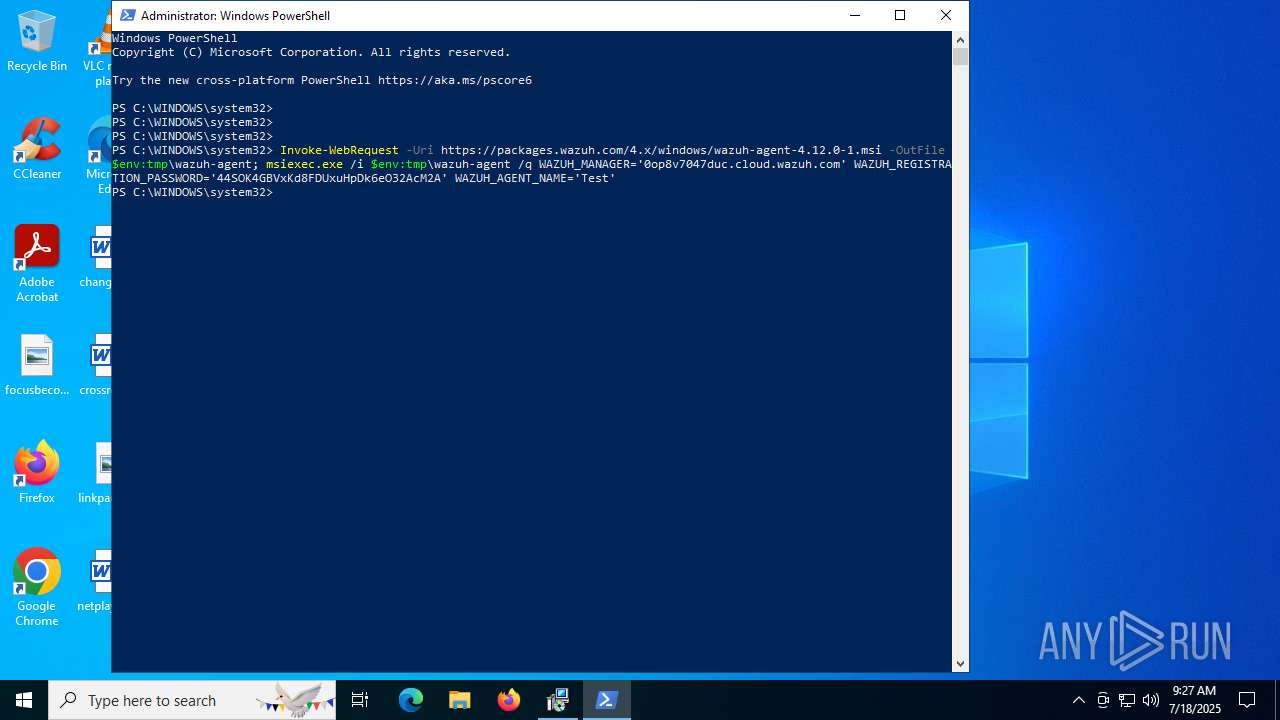
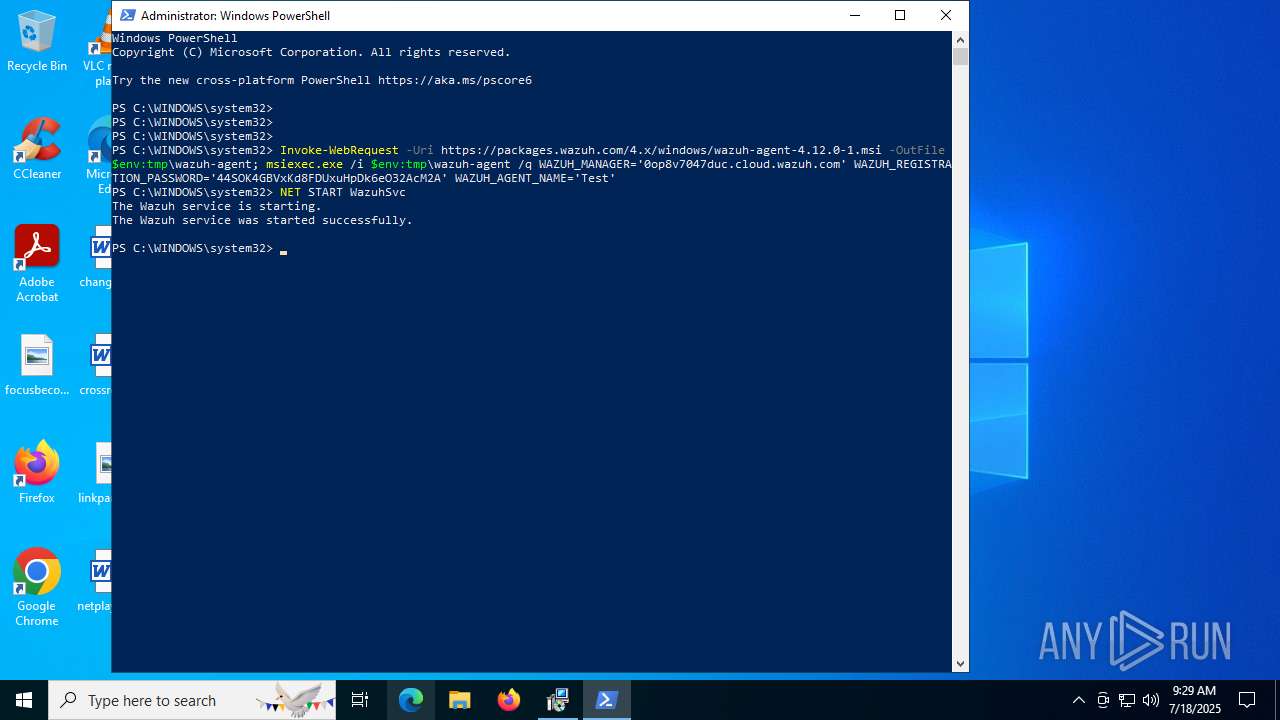
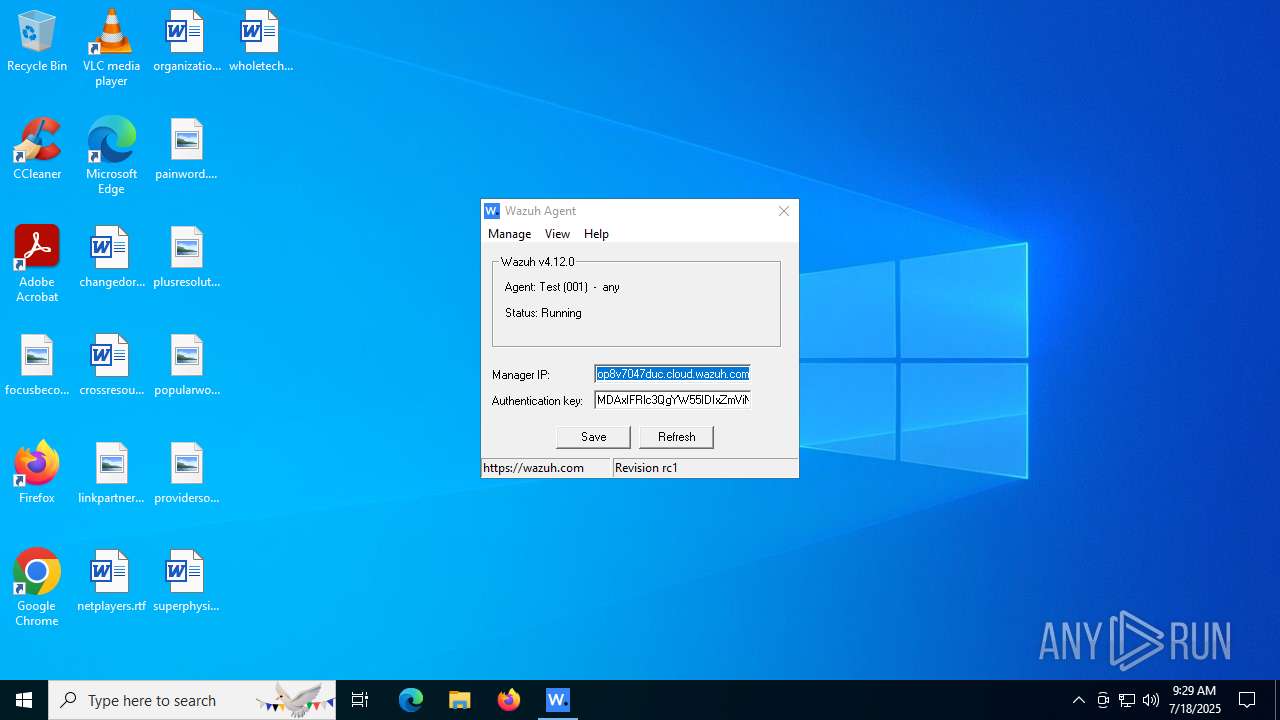
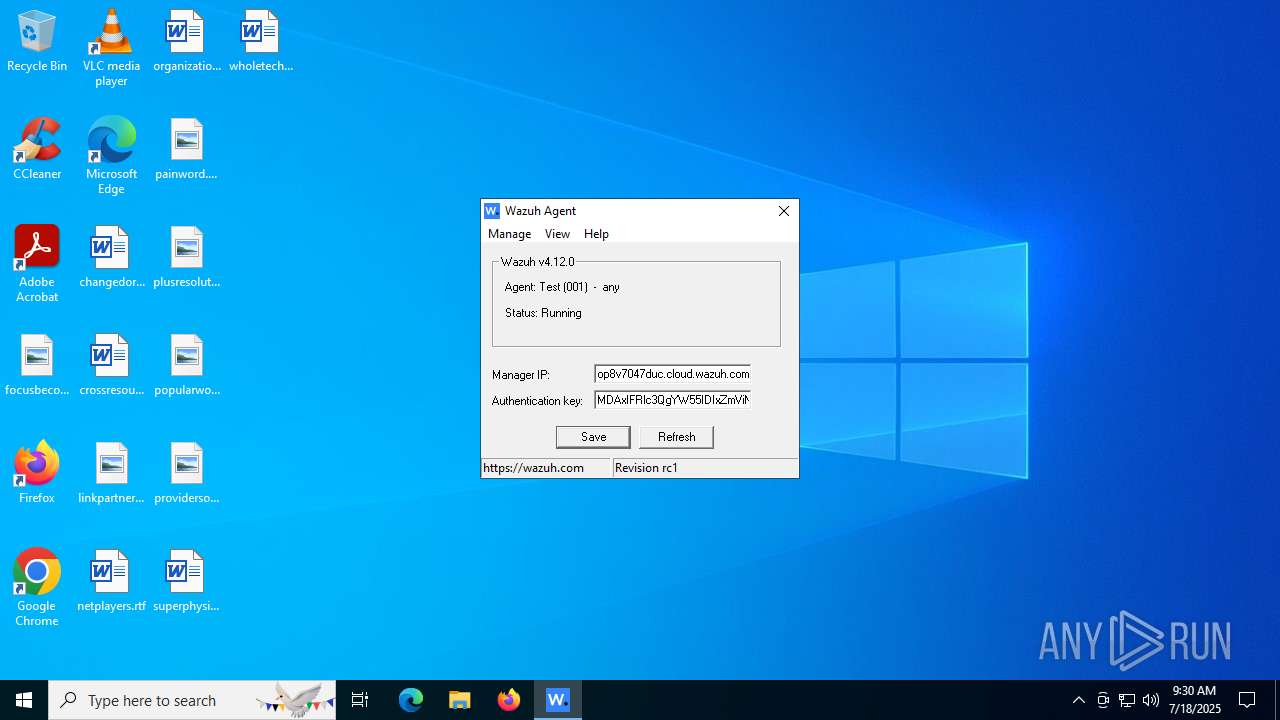
| download: | /4.x/windows/wazuh-agent-4.12.0-1.msi |
| Full analysis: | https://app.any.run/tasks/0f422bdf-b436-4106-9b61-caa29bf1cc6b |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2025, 09:25:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Wazuh helps you to gain security visibility into your infrastructure by monitoring hosts at an operating system and application level. It provides the following capabilities: log analysis, file integrity monitoring, intrusions detection and policy and compliance monitoring, Author: Wazuh, Inc., Keywords: Installer, Comments: wazuh-agent, Template: Intel;1033, Revision Number: {8D57269C-2008-4289-AD64-3C477FEA0843}, Create Time/Date: Mon Mar 31 11:06:00 2025, Last Saved Time/Date: Mon Mar 31 11:06:00 2025, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | CF4EB5E35B9821BE0B1FF08970E5F838 |
| SHA1: | 91D34A8F912AB1423D72F53E452FA49EC76A0841 |
| SHA256: | 69FE54ADDDBB0340B013B1F0DA6DA9E531E674A360590B4DF212984B50FCEC5B |
| SSDEEP: | 98304:HtjFmVWUqWYsJ3hCSGpxjMQrNsbZfDEy4iRLiVRjnuhZbaNRxAHicx7iD6XNyF4d:H9EzeWMOL |
MALICIOUS
Accesses system services(Win32_Service) via WMI (SCRIPT)
- msiexec.exe (PID: 2148)
Opens a text file (SCRIPT)
- msiexec.exe (PID: 6620)
Starts NET.EXE for service management
- powershell.exe (PID: 6860)
- net.exe (PID: 3788)
- cmd.exe (PID: 2612)
- net.exe (PID: 6544)
- cmd.exe (PID: 1592)
- net.exe (PID: 788)
Executing a file with an untrusted certificate
- wazuh-agent.exe (PID: 6140)
- restart-wazuh.exe (PID: 6488)
- wazuh-agent.exe (PID: 1388)
- win32ui.exe (PID: 7108)
- win32ui.exe (PID: 5712)
Starts NET.EXE to view/change login properties
- wazuh-agent.exe (PID: 6140)
- net.exe (PID: 2604)
- net.exe (PID: 6488)
- net.exe (PID: 6312)
- net.exe (PID: 6940)
- net.exe (PID: 3908)
- net.exe (PID: 480)
- net.exe (PID: 1480)
- net.exe (PID: 4528)
- net.exe (PID: 6068)
- net.exe (PID: 7064)
- net.exe (PID: 440)
- net.exe (PID: 4120)
- net.exe (PID: 828)
- net.exe (PID: 5652)
- wazuh-agent.exe (PID: 1388)
- net.exe (PID: 2168)
- net.exe (PID: 1712)
- net.exe (PID: 4264)
- net.exe (PID: 4676)
Starts NET.EXE to view/add/change user profiles
- wazuh-agent.exe (PID: 6140)
- net.exe (PID: 5432)
- net.exe (PID: 5140)
- net.exe (PID: 6620)
- net.exe (PID: 5928)
- net.exe (PID: 5240)
- net.exe (PID: 2328)
- net.exe (PID: 1624)
- net.exe (PID: 2704)
- wazuh-agent.exe (PID: 1388)
- net.exe (PID: 5300)
- net.exe (PID: 6912)
MIMIKATZ has been detected (YARA)
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
SUSPICIOUS
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2148)
- msiexec.exe (PID: 6620)
- msiexec.exe (PID: 188)
- msiexec.exe (PID: 3968)
- msiexec.exe (PID: 6680)
- win32ui.exe (PID: 5712)
The process creates files with name similar to system file names
- msiexec.exe (PID: 6256)
Creates an object to access WMI (SCRIPT)
- msiexec.exe (PID: 2148)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 6620)
- msiexec.exe (PID: 6680)
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 6620)
Checks whether a specific file exists (SCRIPT)
- msiexec.exe (PID: 6620)
Writes binary data to a Stream object (SCRIPT)
- msiexec.exe (PID: 6620)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- msiexec.exe (PID: 2148)
- msiexec.exe (PID: 6620)
Executes WMI query (SCRIPT)
- msiexec.exe (PID: 2148)
- msiexec.exe (PID: 6620)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6256)
Reads data from a binary Stream object (SCRIPT)
- msiexec.exe (PID: 6620)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- msiexec.exe (PID: 6620)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 6620)
- msiexec.exe (PID: 6680)
Uses ICACLS.EXE to modify access control lists
- msiexec.exe (PID: 6620)
Executes as Windows Service
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
Connects to unusual port
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
Searches for installed software
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
Manipulates environment variables
- powershell.exe (PID: 3964)
- powershell.exe (PID: 6876)
Probably obfuscated PowerShell command line is found
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
Starts CMD.EXE for commands execution
- restart-wazuh.exe (PID: 6488)
Starts POWERSHELL.EXE for commands execution
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
INFO
Checks supported languages
- msiexec.exe (PID: 2148)
- msiexec.exe (PID: 6256)
- msiexec.exe (PID: 6620)
- wazuh-agent.exe (PID: 6140)
- restart-wazuh.exe (PID: 6488)
- wazuh-agent.exe (PID: 1388)
- msiexec.exe (PID: 3968)
- msiexec.exe (PID: 6680)
- msiexec.exe (PID: 188)
- win32ui.exe (PID: 5712)
Reads the software policy settings
- msiexec.exe (PID: 6256)
- msiexec.exe (PID: 640)
- wazuh-agent.exe (PID: 6140)
- restart-wazuh.exe (PID: 6488)
- wazuh-agent.exe (PID: 1388)
- slui.exe (PID: 7124)
- win32ui.exe (PID: 5712)
Disables trace logs
- powershell.exe (PID: 6860)
Create files in a temporary directory
- msiexec.exe (PID: 3760)
- msiexec.exe (PID: 640)
Reads the computer name
- msiexec.exe (PID: 6256)
- msiexec.exe (PID: 6620)
- msiexec.exe (PID: 2148)
- wazuh-agent.exe (PID: 6140)
- restart-wazuh.exe (PID: 6488)
- wazuh-agent.exe (PID: 1388)
- msiexec.exe (PID: 3968)
- msiexec.exe (PID: 188)
- win32ui.exe (PID: 5712)
- msiexec.exe (PID: 6680)
Checks proxy server information
- powershell.exe (PID: 6860)
- msiexec.exe (PID: 640)
- slui.exe (PID: 7124)
Creates files or folders in the user directory
- msiexec.exe (PID: 640)
Manual execution by a user
- powershell.exe (PID: 6860)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 640)
The sample compiled with english language support
- msiexec.exe (PID: 640)
- msiexec.exe (PID: 6256)
Creates a software uninstall entry
- msiexec.exe (PID: 6256)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6256)
- msiexec.exe (PID: 640)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6256)
- wazuh-agent.exe (PID: 6140)
- restart-wazuh.exe (PID: 6488)
- wazuh-agent.exe (PID: 1388)
- win32ui.exe (PID: 5712)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6860)
Process checks computer location settings
- msiexec.exe (PID: 6620)
- msiexec.exe (PID: 6680)
- msiexec.exe (PID: 188)
Reads Environment values
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
Creates files in the program directory
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
Reads product name
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
Reads CPU info
- wazuh-agent.exe (PID: 6140)
- wazuh-agent.exe (PID: 1388)
Reads the time zone
- net1.exe (PID: 3960)
- net1.exe (PID: 3964)
- net1.exe (PID: 5724)
- net1.exe (PID: 6704)
- net1.exe (PID: 1508)
- net1.exe (PID: 6356)
- net1.exe (PID: 7108)
- net1.exe (PID: 6232)
- net1.exe (PID: 4120)
- net1.exe (PID: 2876)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3964)
- powershell.exe (PID: 6876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Wazuh helps you to gain security visibility into your infrastructure by monitoring hosts at an operating system and application level. It provides the following capabilities: log analysis, file integrity monitoring, intrusions detection and policy and compliance monitoring |
| Author: | Wazuh, Inc. |
| Keywords: | Installer |
| Comments: | wazuh-agent |
| Template: | Intel;1033 |
| RevisionNumber: | {8D57269C-2008-4289-AD64-3C477FEA0843} |
| CreateDate: | 2025:04:30 11:06:00 |
| ModifyDate: | 2025:04:30 11:06:00 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
407
Monitored processes
256
Malicious processes
6
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\Windows\syswow64\MsiExec.exe -Embedding 277033DFD53E0399D702F02A0103E9F0 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | net.exe accounts | C:\Windows\SysWOW64\net.exe | — | wazuh-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 480 | net.exe accounts | C:\Windows\SysWOW64\net.exe | — | wazuh-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | auditpol.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 504 | auditpol.exe /get /subcategory:"Group Membership" | C:\Windows\SysWOW64\auditpol.exe | — | wazuh-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Audit Policy Program Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\wazuh-agent-4.12.0-1.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 788 | C:\WINDOWS\system32\net.exe start Wazuh | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 828 | net.exe accounts | C:\Windows\SysWOW64\net.exe | — | wazuh-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | auditpol.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | C:\WINDOWS\system32\net1 accounts | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
67 007
Read events
66 771
Write events
225
Delete events
11
Modification events
| (PID) Process: | (2148) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings |
| Operation: | write | Name: | JITDebug |
Value: 0 | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\3885C51CBF007D147B6E358CCB0367F1 |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: C:\Program Files (x86)\ossec-agent\manage_agents.exe | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\7997E4406B218714DB009B5000BD5AF3 |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: C:\Program Files (x86)\ossec-agent\wazuh-agent.exe | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\CD6AECC543487314496855EA939462B6 |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\1085FE02B9632CE4782A95CD5E36809D |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: C:\Program Files (x86)\ossec-agent\vista_sec.txt | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\F6CBCA7E0A8DB0148B2DA29D5F51B20A |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: C:\Program Files (x86)\ossec-agent\win32ui.exe | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\B9326353D220B9A47A8FF246311251DE |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: C:\Program Files (x86)\ossec-agent\ | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\BC470A12BFB32D540ACE5D293959D09D |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: C:\Program Files (x86)\ossec-agent\help.txt | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\4F17569289426FC42B682B5C440376E8 |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: C:\Program Files (x86)\ossec-agent\VERSION.json | |||
| (PID) Process: | (6256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\3778FBAE9B758DC48A26780B0E06BD8F |
| Operation: | write | Name: | DE7D7B08736A3F6469CFF2E94AF48968 |
Value: C:\Program Files (x86)\ossec-agent\wpk_root.pem | |||
Executable files
27
Suspicious files
48
Text files
92
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6860 | powershell.exe | C:\Users\admin\AppData\Local\Temp\wazuh-agent | — | |
MD5:— | SHA256:— | |||
| 6256 | msiexec.exe | C:\Windows\Installer\19c28b.msi | — | |
MD5:— | SHA256:— | |||
| 640 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:CE8B2D7AC0471DFA0C96BF02FEFE34C2 | SHA256:CEAF87E48FD9FC0ED141A32772B58971CFFCB615E21376B233C2F27BCF88F8AA | |||
| 6256 | msiexec.exe | C:\Program Files (x86)\ossec-agent\active-response\active-responses.log | — | |
MD5:— | SHA256:— | |||
| 6860 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_inrmhx1t.rwh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 640 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_4CAFA09964FFF678458D56D5ABF1D678 | binary | |
MD5:2CBBBD1FB7A80B38A04453262DE7B205 | SHA256:683CAE80104CC360E22C516E3D99F58E661793560CB2DB9F63CCCD046F3A2C06 | |||
| 640 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:45EDFA0F1848F696AE86E8BB228BEDDD | SHA256:2CFCA4FC9213B0E614BEAECB70C8DA46CBCA0BCFC39801B72F59AC089901CAF6 | |||
| 640 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:7CB6702B7B09666A90AFAD008835C25D | SHA256:E51CCE3893063D370F695E2EAD5B110F43C9AA9F27F28E3060058D1C7FBBD93A | |||
| 640 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:2A839EFA047BC6864DBCBC7C902A610F | SHA256:0EAFD6B23DA15D6ABB1B18BC7C61879C64CC63090BAFF61FC0A62D8E8466D02B | |||
| 6860 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\CXM6LAX9QWM23CLLHELR.temp | binary | |
MD5:C21B4BA52CEA1DB7DA61D399924E3EB3 | SHA256:FCA4C83039B6277F40887D05DE9D0465BEF1E02808F5393E06EF34EAC1A00AE7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
46
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
640 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
640 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
640 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA4sUPeSVHoAfRnTvgHTO6k%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4892 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2596 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2596 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1352 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
640 | msiexec.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5328 | SearchApp.exe | 2.16.241.201:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |