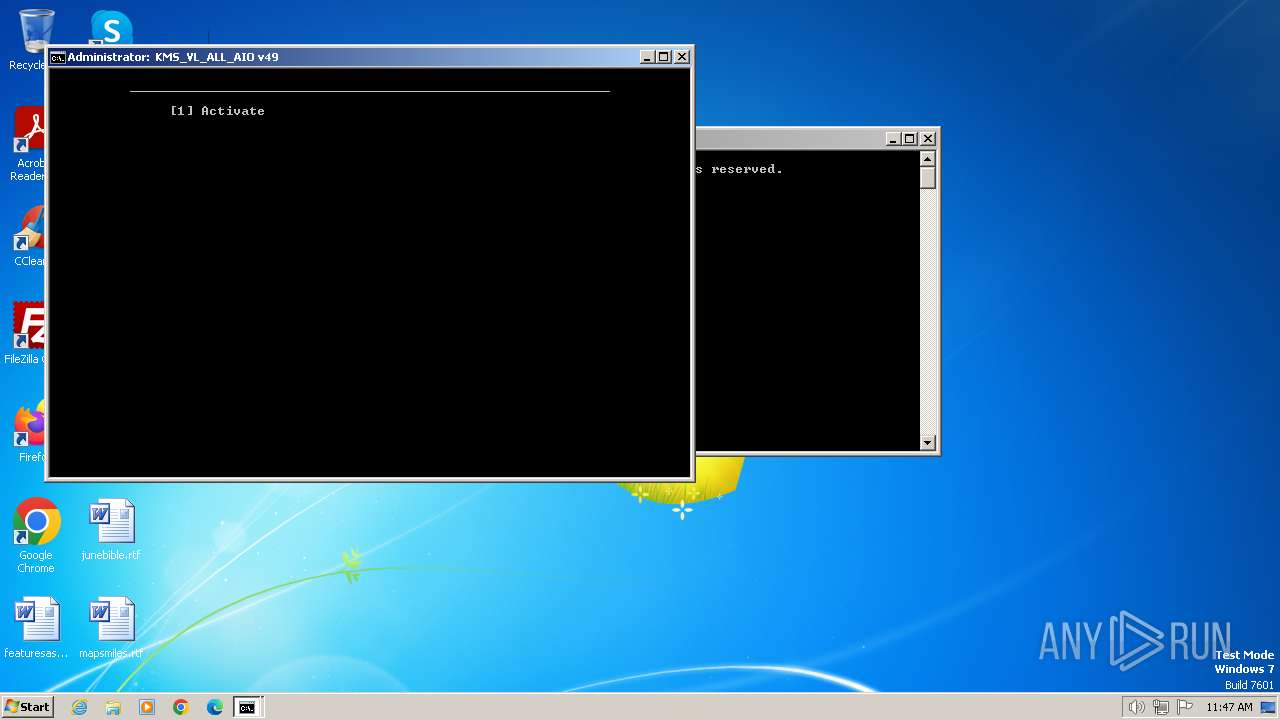
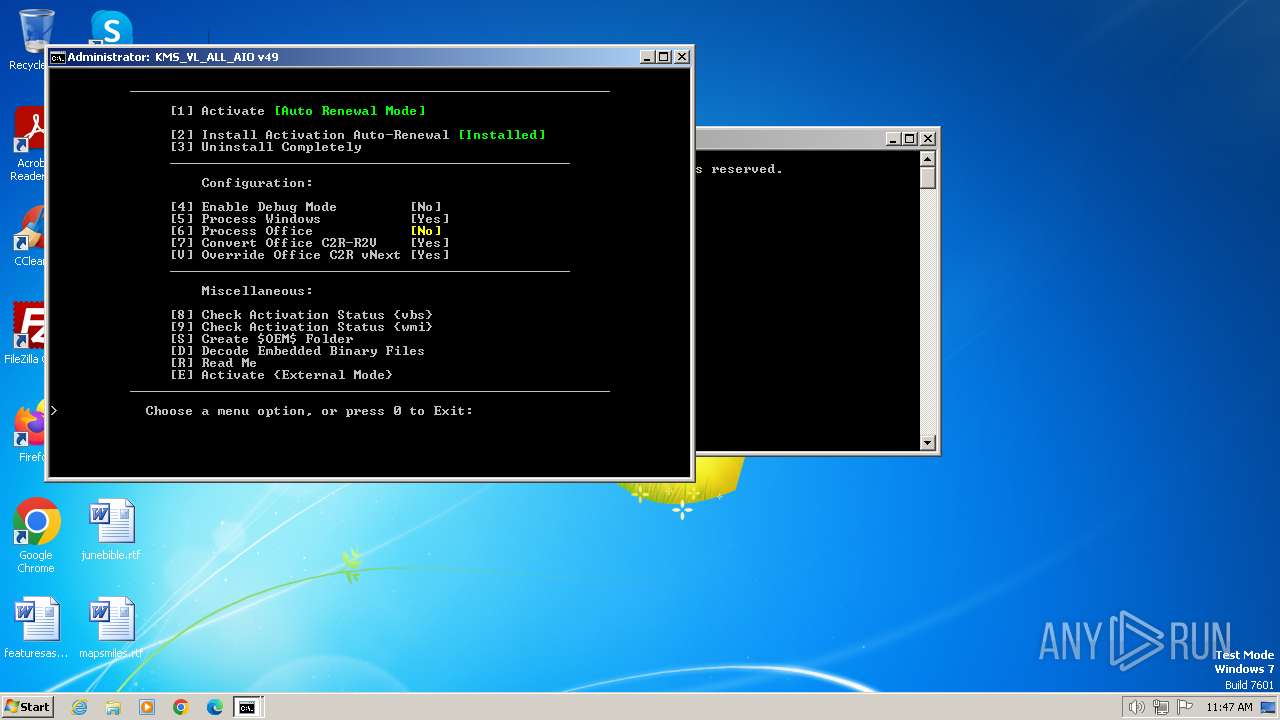
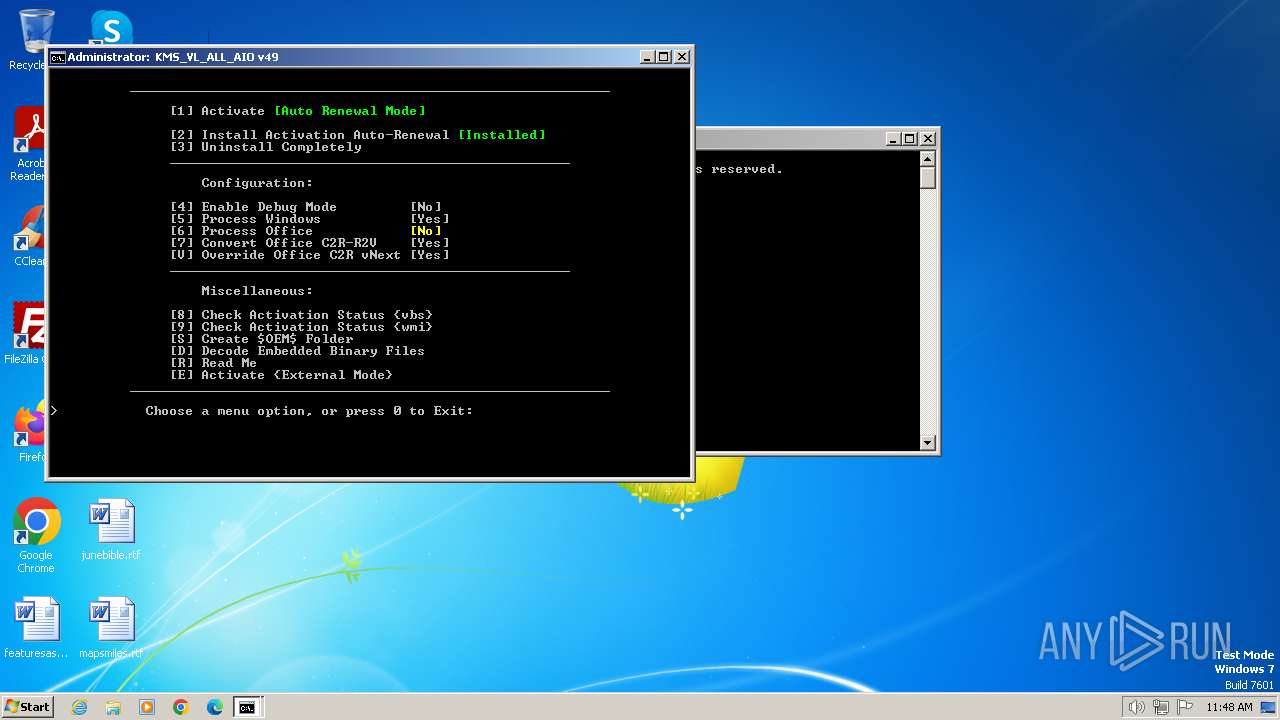
| File name: | KMS_VL_ALL_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/1e96e3ad-468f-4743-b6b1-d7616acf64ff |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2024, 11:45:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | exported SGML document, ASCII text, with CRLF line terminators |
| MD5: | B7704F8278FF47C8E3CBCBC05C0F584E |
| SHA1: | 38E74790E64A034FF2D1AFCF2017E5CD640CEA3C |
| SHA256: | 69F3684EB086EB71D86869CDDA94BA2E58BA5B5BE0803A3572891ED532CCE94C |
| SSDEEP: | 6144:bcJDJzLuHpIvzGDNS8xFfKR5pw9rIjEUqbj8Hm6p/fH:4JDJzApIqxFyR5pmUjE/j8G2/f |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 2268)
Drops the executable file immediately after the start
- csc.exe (PID: 3084)
- powershell.exe (PID: 2268)
Creates a writable file in the system directory
- powershell.exe (PID: 2268)
Starts NET.EXE for service management
- cmd.exe (PID: 3980)
- net.exe (PID: 3472)
- net.exe (PID: 3024)
- net.exe (PID: 1036)
- net.exe (PID: 2320)
- net.exe (PID: 2644)
SUSPICIOUS
Reads the Internet Settings
- cscript.exe (PID: 1368)
- wscript.exe (PID: 4004)
- WMIC.exe (PID: 848)
- WMIC.exe (PID: 2668)
- WMIC.exe (PID: 2596)
- WMIC.exe (PID: 3224)
- WMIC.exe (PID: 3036)
- WMIC.exe (PID: 1780)
- WMIC.exe (PID: 764)
- WMIC.exe (PID: 552)
- WMIC.exe (PID: 2792)
- WMIC.exe (PID: 1316)
- WMIC.exe (PID: 268)
- WMIC.exe (PID: 1336)
- WMIC.exe (PID: 2324)
- WMIC.exe (PID: 1368)
- WMIC.exe (PID: 2432)
- WMIC.exe (PID: 2064)
- WMIC.exe (PID: 2632)
- WMIC.exe (PID: 2324)
- WMIC.exe (PID: 764)
- WMIC.exe (PID: 3828)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1496)
- cmd.exe (PID: 3980)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1496)
- cmd.exe (PID: 3980)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 1496)
- cmd.exe (PID: 3980)
Uses RUNDLL32.EXE to load library
- cscript.exe (PID: 1368)
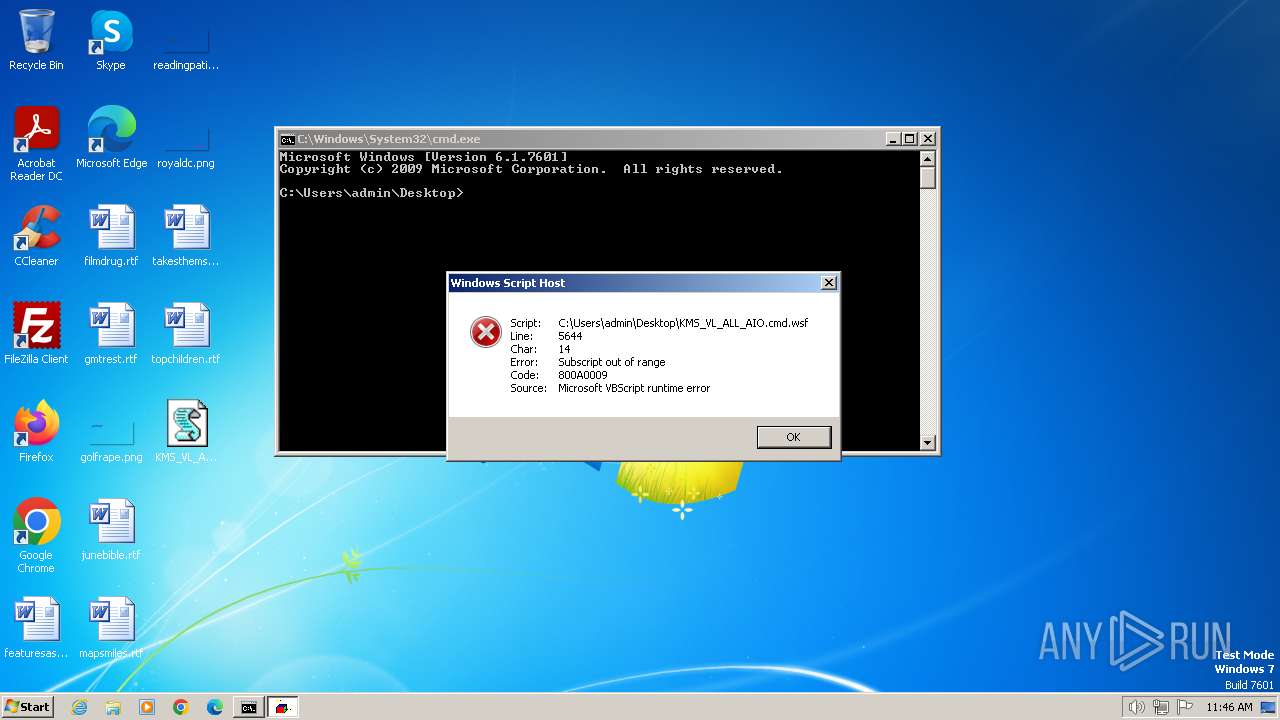
Runs shell command (SCRIPT)
- cscript.exe (PID: 1368)
Executing commands from ".cmd" file
- cscript.exe (PID: 1368)
Starts CMD.EXE for commands execution
- cscript.exe (PID: 1368)
- cmd.exe (PID: 3980)
Starts SC.EXE for service management
- cmd.exe (PID: 3980)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3980)
- cmd.exe (PID: 3636)
- cmd.exe (PID: 2040)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3980)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 3980)
Uses .NET C# to load dll
- powershell.exe (PID: 2268)
Application launched itself
- cmd.exe (PID: 3980)
Hides command output
- cmd.exe (PID: 2432)
- cmd.exe (PID: 3684)
- cmd.exe (PID: 2580)
- cmd.exe (PID: 1928)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 1236)
- cmd.exe (PID: 1572)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3980)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 2488)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 3980)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 840)
- cmd.exe (PID: 3224)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 2560)
- cmd.exe (PID: 3636)
Executable content was dropped or overwritten
- csc.exe (PID: 3084)
- powershell.exe (PID: 2268)
INFO
Manual execution by a user
- cmd.exe (PID: 1496)
- wscript.exe (PID: 4004)
Reads security settings of Internet Explorer
- cscript.exe (PID: 1368)
Checks operating system version
- cmd.exe (PID: 3980)
Checks supported languages
- mode.com (PID: 784)
- mode.com (PID: 4064)
- csc.exe (PID: 3084)
- cvtres.exe (PID: 2556)
- mode.com (PID: 3644)
- mode.com (PID: 3708)
- mode.com (PID: 2964)
- mode.com (PID: 3996)
- mode.com (PID: 2984)
Reads the machine GUID from the registry
- csc.exe (PID: 3084)
- cvtres.exe (PID: 2556)
Reads Microsoft Office registry keys
- reg.exe (PID: 4000)
- reg.exe (PID: 2232)
- reg.exe (PID: 2960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .wsf | | | Windows Script File (72.7) |
|---|---|---|
| .html | | | HyperText Markup Language (27.2) |
Total processes
291
Monitored processes
242
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | reg query HKLM\SOFTWARE\Microsoft\Office\ClickToRun /v InstallPath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 124 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | powershell -nop -c $ExecutionContext.SessionState.LanguageMode | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 268 | wmic path OfficeSoftwareProtectionProduct where (ApplicationID='0ff1ce15-a989-479d-af46-f275c6370663' AND NOT Name like '%O365%' ) get Name /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 324 | find /i "STOPPED" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v KMS_RenewalInterval /t REG_DWORD /d 10080 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | find /i "STOPPED" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | reg query "HKCU\SOFTWARE\Microsoft\Windows Script Host\Settings" /v Enabled | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | wmic path SoftwareLicensingProduct where (ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f' and LicenseStatus='1' ) get Name /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | sc query sppsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
21 196
Read events
21 155
Write events
39
Delete events
2
Modification events
| (PID) Process: | (1368) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1368) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1368) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1368) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
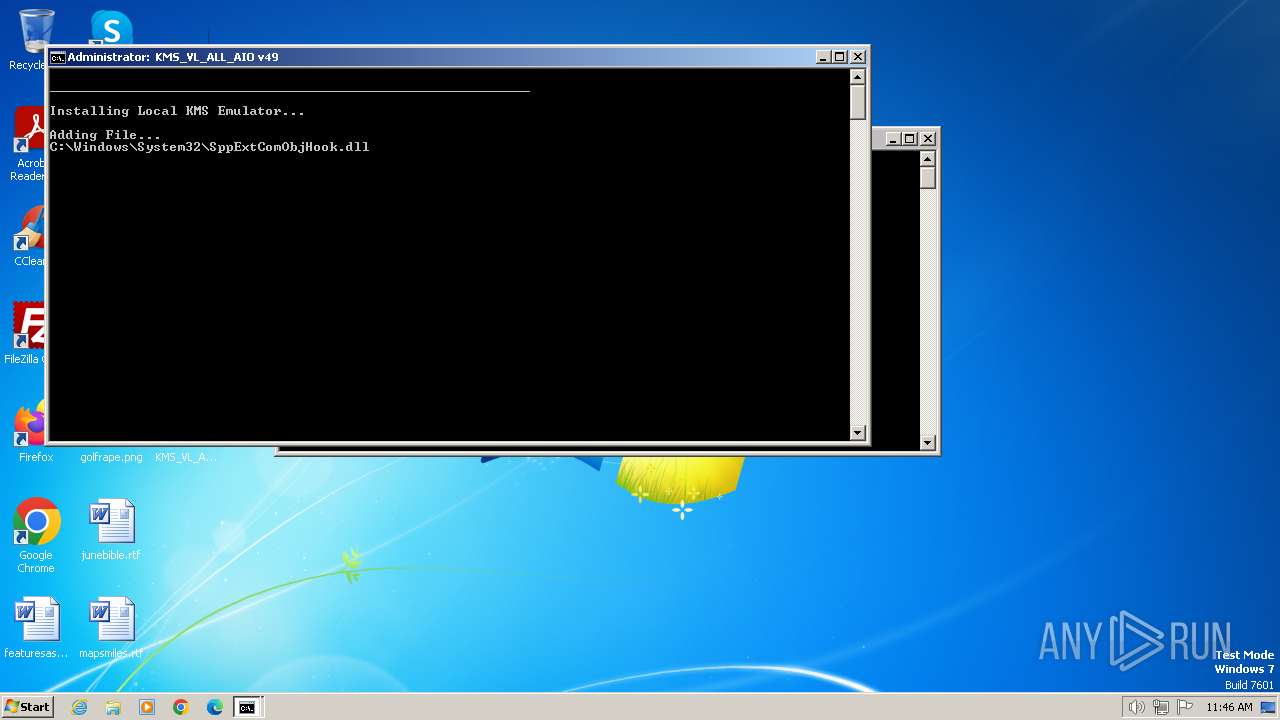
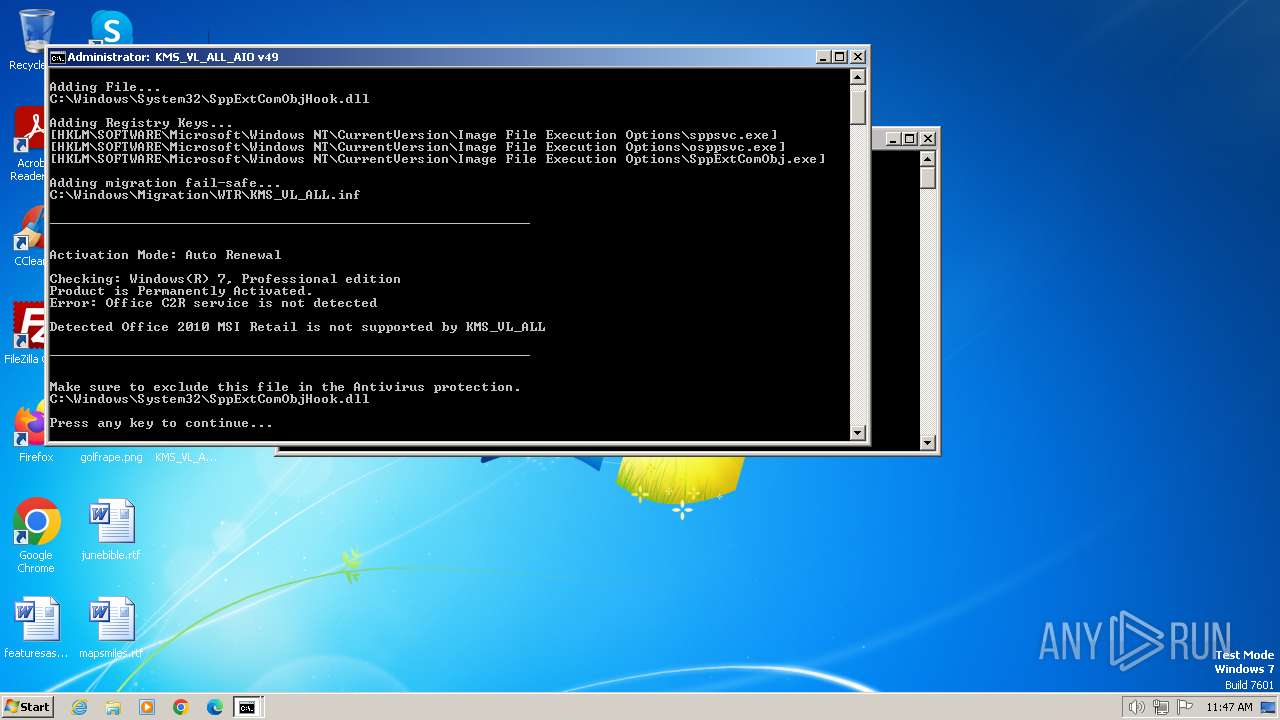
| (PID) Process: | (3016) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | VerifierDlls |
Value: SppExtComObjHook.dll | |||
| (PID) Process: | (1932) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | VerifierDebug |
Value: 0 | |||
| (PID) Process: | (3048) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | VerifierFlags |
Value: | |||
| (PID) Process: | (3440) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | GlobalFlag |
Value: 256 | |||
| (PID) Process: | (908) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 1 | |||
| (PID) Process: | (3416) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe |
| Operation: | write | Name: | KMS_ActivationInterval |
Value: 120 | |||
Executable files
2
Suspicious files
14
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2172 | powershell.exe | C:\Users\admin\AppData\Local\Temp\lnynliix.ywk.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\Local\Temp\vrklojrn.g3h.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2268 | powershell.exe | C:\Windows\Temp\qlrr4bor.fbp.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3980 | cmd.exe | C:\Windows\Temp\' | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\5j0ye53m.h1l.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3980 | cmd.exe | C:\Windows\Temp\`.txt | binary | |
MD5:FFE40BE0916C7302AE237FEEBE53CF4B | SHA256:6EF78A8EF8E0752565DCC75E10DB254A573A51EAA183F0BFF99494E62F0B57C6 | |||
| 2268 | powershell.exe | C:\Windows\Temp\rbchu4ax.bqm.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\vixxjkqa.ynu.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\5mqlm4l3.0rx.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |