| File name: | invoice_2318362983713_823931342io.pdf.exe |
| Full analysis: | https://app.any.run/tasks/6f3b238a-50a8-4bce-a0df-e226f5637726 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 14:18:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | EA039A854D20D7734C5ADD48F1A51C34 |
| SHA1: | 9615DCA4C0E46B8A39DE5428AF7DB060399230B2 |
| SHA256: | 69E966E730557FDE8FD84317CDEF1ECE00A8BB3470C0B58F3231E170168AF169 |
| SSDEEP: | 6144:tg+buboEf6ZsYxQWzMTohPdrDdkyRcpD7r:GmubXyQWQToDrDnED7r |
MALICIOUS
ZEROACCESS has been detected
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
ZEROACCESS has been detected (SURICATA)
- InstallFlashPlayer.exe (PID: 7412)
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
Changes the autorun value in the registry
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
ZEROACCESS mutex has been found
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
- explorer.exe (PID: 5492)
- InstallFlashPlayer.exe (PID: 7412)
Runs injected code in another process
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
Application was injected by another process
- explorer.exe (PID: 5492)
SUSPICIOUS
Reads security settings of Internet Explorer
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
- InstallFlashPlayer.exe (PID: 7412)
Executable content was dropped or overwritten
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
Starts CMD.EXE for commands execution
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
There is functionality for taking screenshot (YARA)
- InstallFlashPlayer.exe (PID: 7412)
There is functionality for lookup Geolocation (YARA)
- InstallFlashPlayer.exe (PID: 7412)
INFO
Creates files or folders in the user directory
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
Checks proxy server information
- InstallFlashPlayer.exe (PID: 7412)
- slui.exe (PID: 8144)
The sample compiled with english language support
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
Checks supported languages
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
- InstallFlashPlayer.exe (PID: 7412)
Create files in a temporary directory
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
Process checks computer location settings
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
Reads the computer name
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
- InstallFlashPlayer.exe (PID: 7412)
Reads the machine GUID from the registry
- invoice_2318362983713_823931342io.pdf.exe (PID: 6392)
Reads the software policy settings
- slui.exe (PID: 7240)
- slui.exe (PID: 8144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:11:25 10:32:03+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 144384 |
| InitializedDataSize: | 107520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa3b6 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
141
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6392 | "C:\Users\admin\AppData\Local\Temp\invoice_2318362983713_823931342io.pdf.exe" | C:\Users\admin\AppData\Local\Temp\invoice_2318362983713_823931342io.pdf.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7204 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7240 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
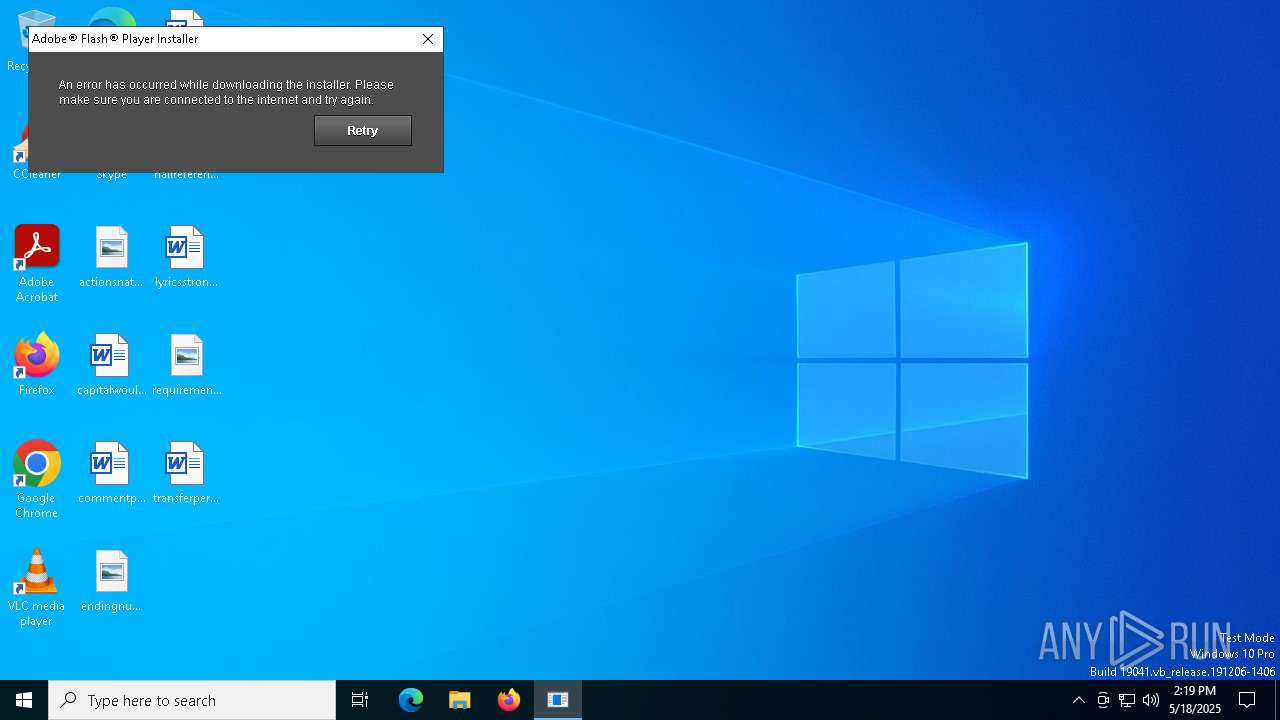
| 7412 | "C:\Users\admin\AppData\Local\Temp\InstallFlashPlayer.exe" | C:\Users\admin\AppData\Local\Temp\InstallFlashPlayer.exe | invoice_2318362983713_823931342io.pdf.exe | ||||||||||||
User: admin Company: Adobe Systems, Inc. Integrity Level: HIGH Description: Adobe® Flash® Player Installer/Uninstaller 11.0 r1 Version: 11,0,1,152 Modules
| |||||||||||||||
| 7424 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\SysWOW64\cmd.exe | — | invoice_2318362983713_823931342io.pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 4294967295 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8144 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 830
Read events
2 819
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6392) invoice_2318362983713_823931342io.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Google Update |
Value: "C:\Users\admin\AppData\Local\Google\Desktop\Install\{81b8c3da-9d80-cef9-7346-aaa39584b477}\❤≸⋙\Ⱒ☠⍨\ﯹ๛\{81b8c3da-9d80-cef9-7346-aaa39584b477}\GoogleUpdate.exe" > | |||
| (PID) Process: | (6392) invoice_2318362983713_823931342io.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6392) invoice_2318362983713_823931342io.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000060B81DB4E48ED2119906E49FADC173CA9D000000 | |||
| (PID) Process: | (6392) invoice_2318362983713_823931342io.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 5BEC296800000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000070256 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (7412) InstallFlashPlayer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7412) InstallFlashPlayer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7412) InstallFlashPlayer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
3
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6392 | invoice_2318362983713_823931342io.pdf.exe | C:\Users\admin\AppData\Local\Google\Desktop\Install\{81b8c3da-9d80-cef9-7346-aaa39584b477}\❤≸⋙\Ⱒ☠⍨\ﯹ๛\{81b8c3da-9d80-cef9-7346-aaa39584b477}\GoogleUpdate.exe | executable | |
MD5:EA039A854D20D7734C5ADD48F1A51C34 | SHA256:69E966E730557FDE8FD84317CDEF1ECE00A8BB3470C0B58F3231E170168AF169 | |||
| 6392 | invoice_2318362983713_823931342io.pdf.exe | C:\Users\admin\AppData\Local\Temp\msimg32.dll | executable | |
MD5:E051308C2F0C1B280514C99AABD36E34 | SHA256:DDF7CCAB32E8C0EE6294DF2591EFAC632C27C61D073B86B97DE62311F9379212 | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6392 | invoice_2318362983713_823931342io.pdf.exe | C:\Users\admin\AppData\Local\Google\Desktop\Install\{81b8c3da-9d80-cef9-7346-aaa39584b477}\❤≸⋙\Ⱒ☠⍨\ﯹ๛\{81b8c3da-9d80-cef9-7346-aaa39584b477}\@ | binary | |
MD5:A8D6E2633BD011F5F4F64B32DC800E27 | SHA256:BC5FCC619D8A5369012F6C4E790662FE8AF8B25A187042257ED954344CE06AF2 | |||
| 6392 | invoice_2318362983713_823931342io.pdf.exe | C:\Users\admin\AppData\Local\Temp\InstallFlashPlayer.exe | executable | |
MD5:2FF9B590342C62748885D459D082295F | SHA256:672EC8DCEAFD429C1A09CFAFBC4951968953E2081E0D97243040DB16EDB24429 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
16
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7412 | InstallFlashPlayer.exe | GET | 404 | 104.102.57.130:80 | http://fpdownload.macromedia.com/get/flashplayer/update/current/install/install_all_win_cab_64_ax_sgn.z | unknown | — | — | whitelisted |
7976 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7412 | InstallFlashPlayer.exe | GET | 404 | 104.102.57.130:80 | http://fpdownload.macromedia.com/get/flashplayer/update/current/install/install_all_win_cab_64_ax_sgn.z | unknown | — | — | whitelisted |
7976 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2152 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
6392 | invoice_2318362983713_823931342io.pdf.exe | 85.114.128.127:53 | — | — | — | malicious |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
j.maxmind.com |
| shared |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fpdownload.macromedia.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6392 | invoice_2318362983713_823931342io.pdf.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
6392 | invoice_2318362983713_823931342io.pdf.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
6392 | invoice_2318362983713_823931342io.pdf.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
6392 | invoice_2318362983713_823931342io.pdf.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
6392 | invoice_2318362983713_823931342io.pdf.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
6392 | invoice_2318362983713_823931342io.pdf.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
6392 | invoice_2318362983713_823931342io.pdf.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
6392 | invoice_2318362983713_823931342io.pdf.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
7412 | InstallFlashPlayer.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |