| File name: | Akira_Clicker.exe |
| Full analysis: | https://app.any.run/tasks/5be6cf9b-2ce8-4a3f-8df5-fae8e86b3a1a |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 00:35:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 12 sections |
| MD5: | CF9BA602EC0CF268973953282A850588 |
| SHA1: | A95E1EF20AB659F0A3BA7745FECF9664181513EB |
| SHA256: | 69E0C57E979B2E17C90F7601B7C96872F3C870743ED60E1EC427256029DFFA79 |
| SSDEEP: | 98304:Xb9rT71VQIelkSbGUOqwQCj7qkIx99zl61l0Q1V+szDERJTSootuvqVJsVa/vsPp:ItwJFXmer6LRakoMP4HZ14uf2tZP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- Akira_Clicker.exe (PID: 720)
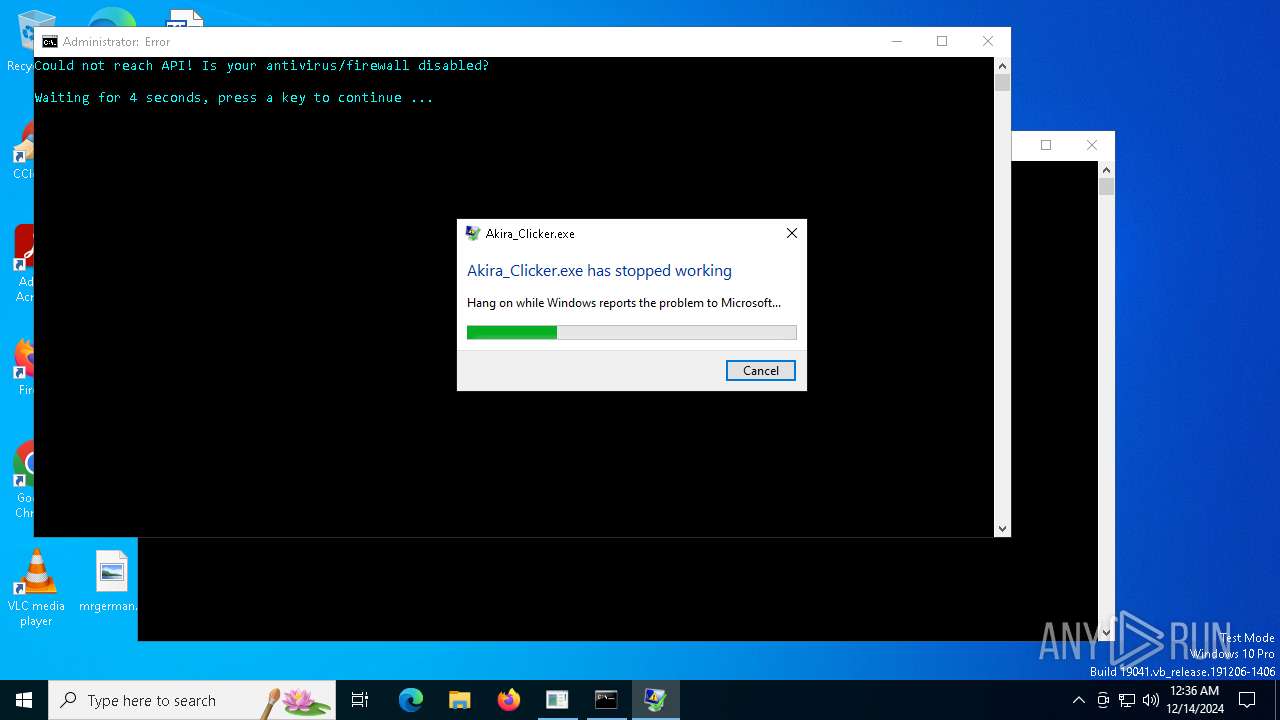
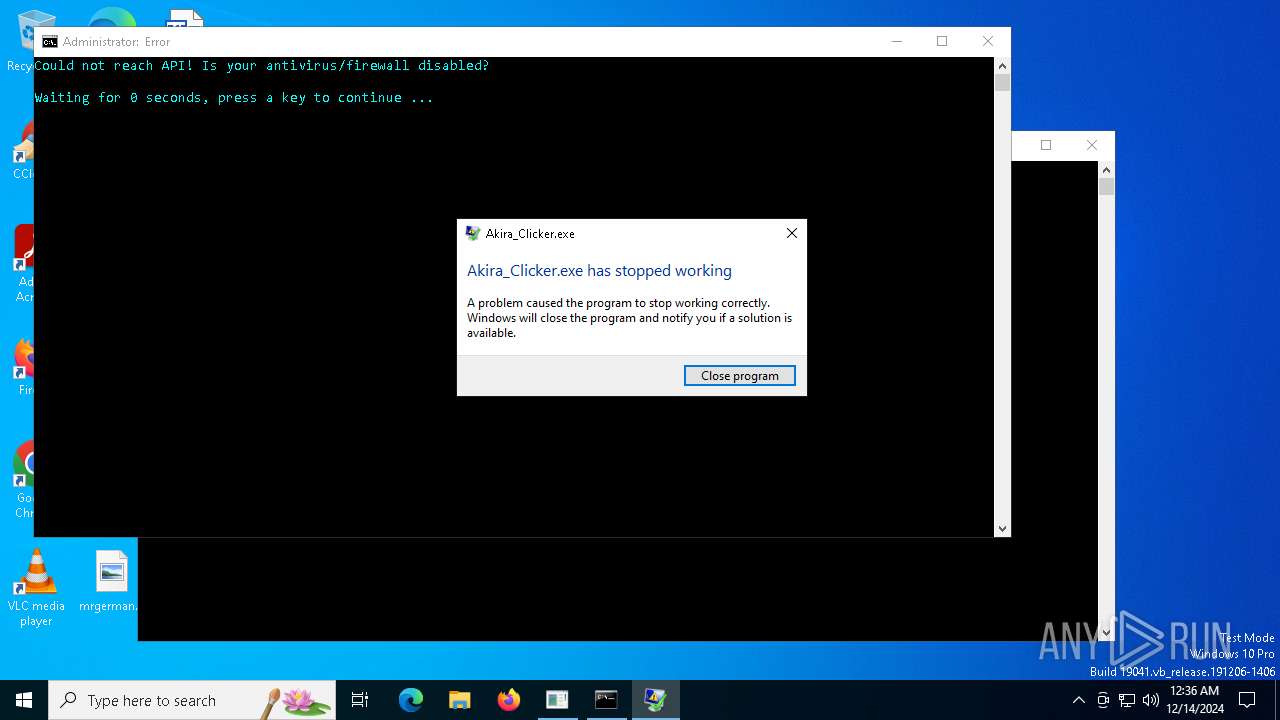
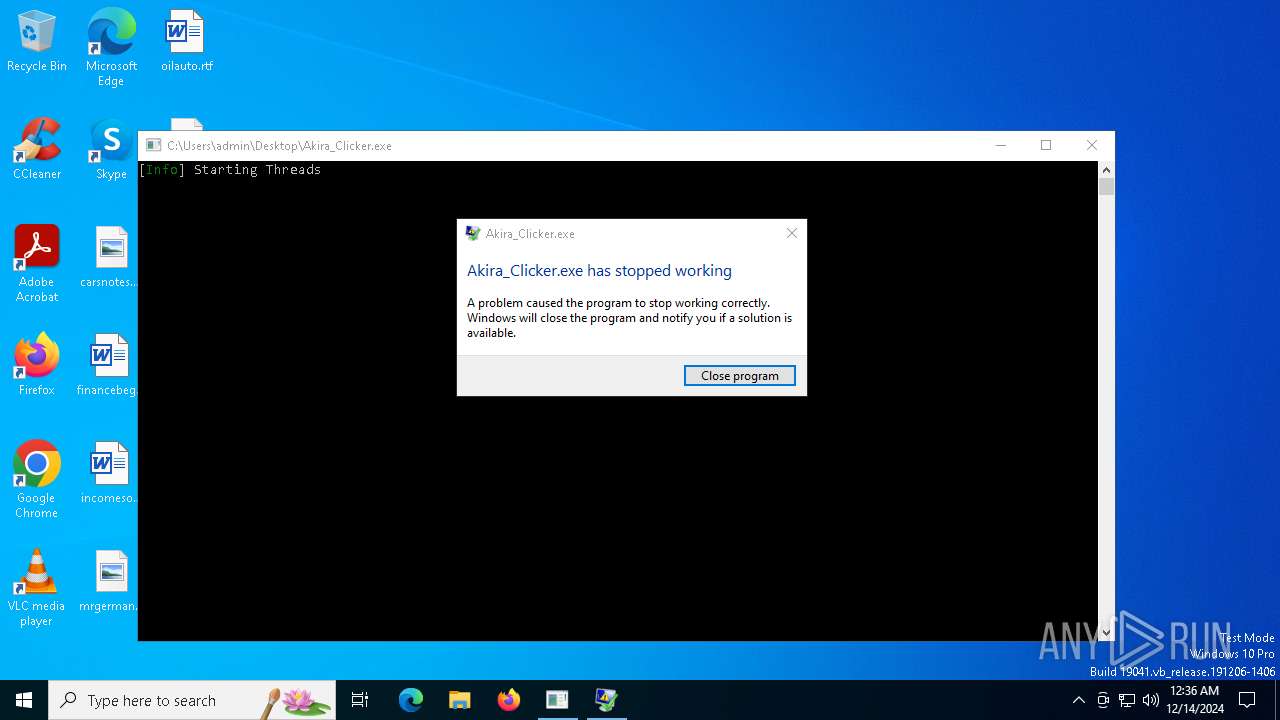
Executes application which crashes
- Akira_Clicker.exe (PID: 720)
Application launched itself
- cmd.exe (PID: 3640)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3640)
- Akira_Clicker.exe (PID: 720)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2972)
Reads security settings of Internet Explorer
- Akira_Clicker.exe (PID: 720)
INFO
Checks supported languages
- Akira_Clicker.exe (PID: 720)
Process checks whether UAC notifications are on
- Akira_Clicker.exe (PID: 720)
Reads the computer name
- Akira_Clicker.exe (PID: 720)
Sends debugging messages
- Akira_Clicker.exe (PID: 720)
Creates files or folders in the user directory
- WerFault.exe (PID: 4500)
Reads the software policy settings
- WerFault.exe (PID: 4500)
Checks proxy server information
- WerFault.exe (PID: 4500)
- Akira_Clicker.exe (PID: 720)
Gets the hash of the file via CERTUTIL.EXE
- certutil.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:11 18:24:23+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.38 |
| CodeSize: | 2344960 |
| InitializedDataSize: | 2392576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xfae058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
131
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | find /i /v "certutil" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\Users\admin\Desktop\Akira_Clicker.exe" | C:\Users\admin\Desktop\Akira_Clicker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221226505 Modules
| |||||||||||||||
| 1596 | find /i /v "md5" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | certutil -hashfile "C:\Users\admin\Desktop\Akira_Clicker.exe" MD5 | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
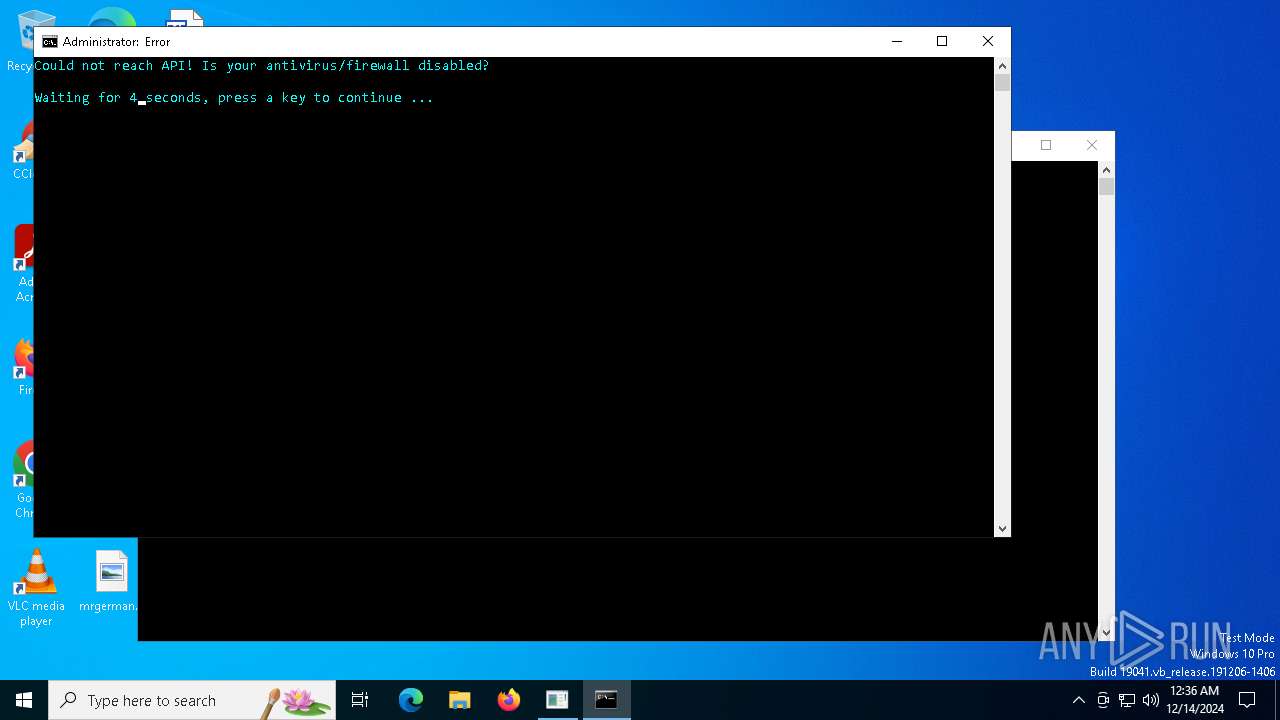
| 2972 | cmd /C "color b && title Error && echo Could not reach API! Is your antivirus/firewall disabled? && timeout /t 5" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3640 | C:\WINDOWS\system32\cmd.exe /c start cmd /C "color b && title Error && echo Could not reach API! Is your antivirus/firewall disabled? && timeout /t 5" | C:\Windows\System32\cmd.exe | — | Akira_Clicker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3836 | C:\WINDOWS\system32\cmd.exe /c certutil -hashfile "C:\Users\admin\Desktop\Akira_Clicker.exe" MD5 | find /i /v "md5" | find /i /v "certutil" | C:\Windows\System32\cmd.exe | — | Akira_Clicker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4500 | C:\WINDOWS\system32\WerFault.exe -u -p 720 -s 2120 | C:\Windows\System32\WerFault.exe | Akira_Clicker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | timeout /t 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | "C:\Users\admin\Desktop\Akira_Clicker.exe" | C:\Users\admin\Desktop\Akira_Clicker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
7 369
Read events
7 360
Write events
6
Delete events
3
Modification events
| (PID) Process: | (1760) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (1760) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (1760) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
| (PID) Process: | (4500) WerFault.exe | Key: | \REGISTRY\A\{ca34cd2c-a46f-3d77-45c8-99702236d14a}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (4500) WerFault.exe | Key: | \REGISTRY\A\{ca34cd2c-a46f-3d77-45c8-99702236d14a}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4500 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Akira_Clicker.ex_6ef6a885957956375bd973278efd48df5d367cc_14d3f46a_a476d9d5-91e6-41c8-abad-e60d551deecb\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4500 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Akira_Clicker.exe.720.dmp | — | |
MD5:— | SHA256:— | |||
| 4500 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:5DB35B8AF401C128557C10404B1128EF | SHA256:DC444E88C81F10C67A2DCB320EA5C3C4A185323C2158546FCA7EA1851700051E | |||
| 4500 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA8C8.tmp.xml | xml | |
MD5:7FC54DD3D7E24F7AF02C0EB1DA8014F4 | SHA256:BFA4C30E11378A2EB026EAF0CD2CD7C33FC4F298B3814D99C29B8A29EA2E2579 | |||
| 4500 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA77E.tmp.dmp | binary | |
MD5:5543CA23A5E98AF6B78BC265BAC9D1B3 | SHA256:A89E811C9A3791C85B2A37F336C43F20CC3E7D43C73CDAFA7C93F03571F83E6E | |||
| 4500 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA8A8.tmp.WERInternalMetadata.xml | xml | |
MD5:3C4476D9FA88F04A81446B2C4DE23005 | SHA256:67493FF60B23D6978E80675B6858E8F8281AA446EB84DD0703CA9B2AE757C08B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
20
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1684 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
720 | Akira_Clicker.exe | 142.250.186.164:443 | www.google.com | GOOGLE | US | whitelisted |
3976 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
720 | Akira_Clicker.exe | 104.21.112.1:443 | happyhippo.cloud | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
happyhippo.cloud |
| unknown |
watson.events.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Akira_Clicker.exe | if u see this message then you should prepare. I dont like reverse engineers so i put some stuff into Akira that will probably damage your PC if u try to unpack or debug it :D HF |
Akira_Clicker.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |