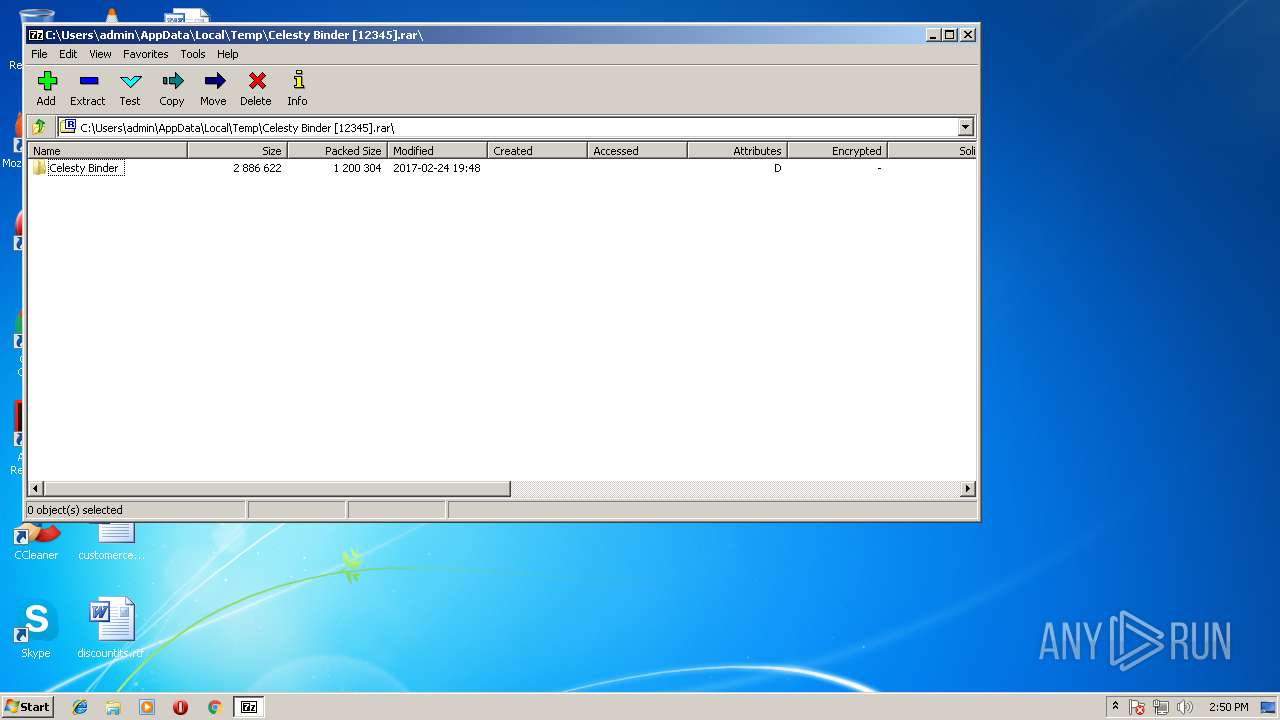
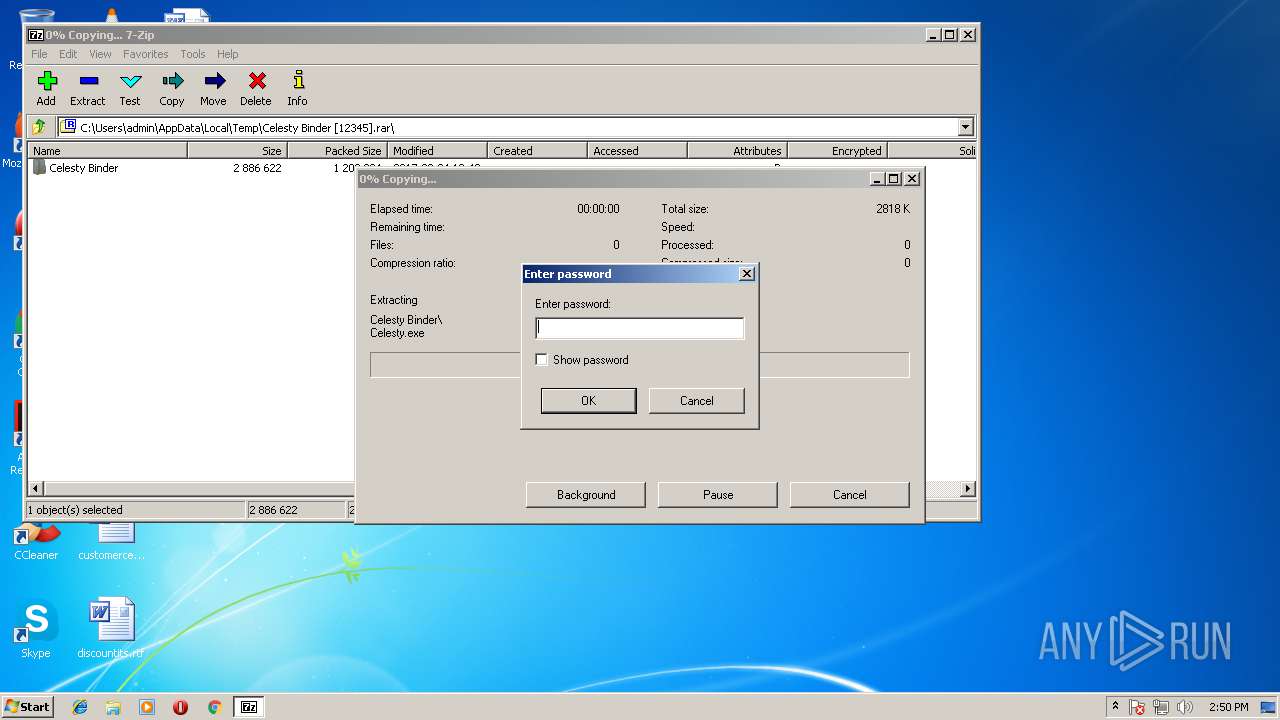
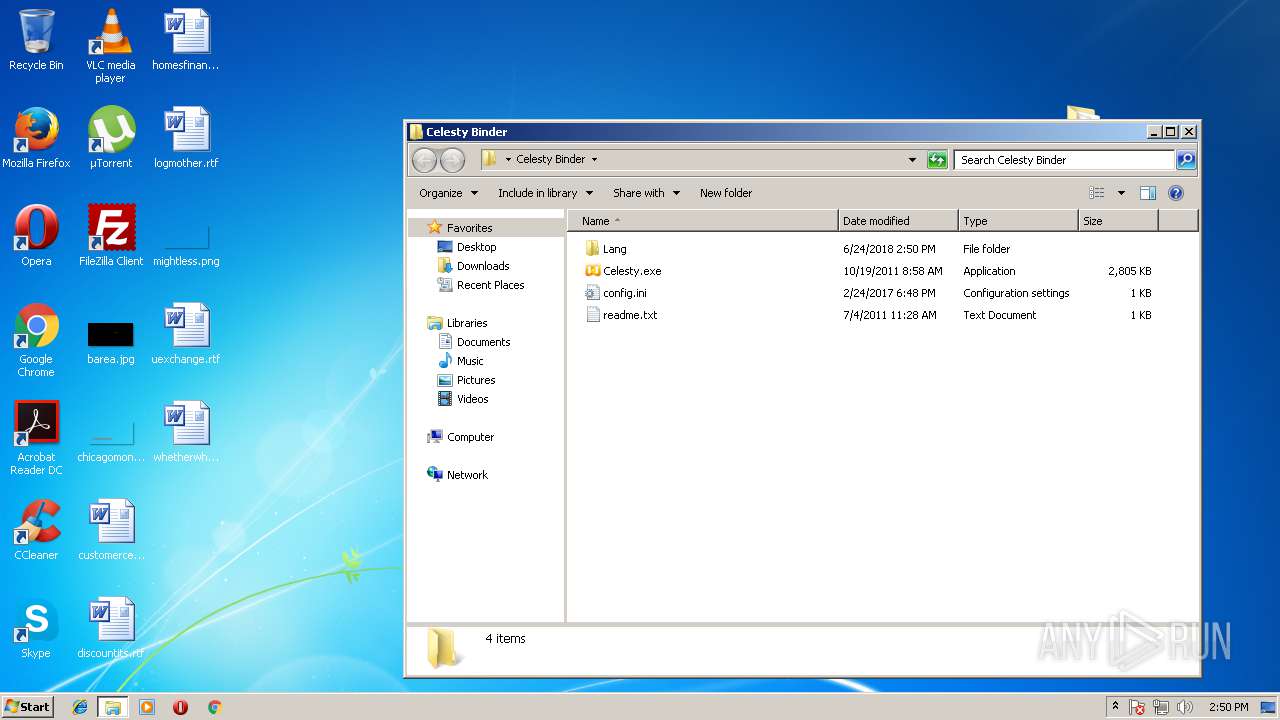
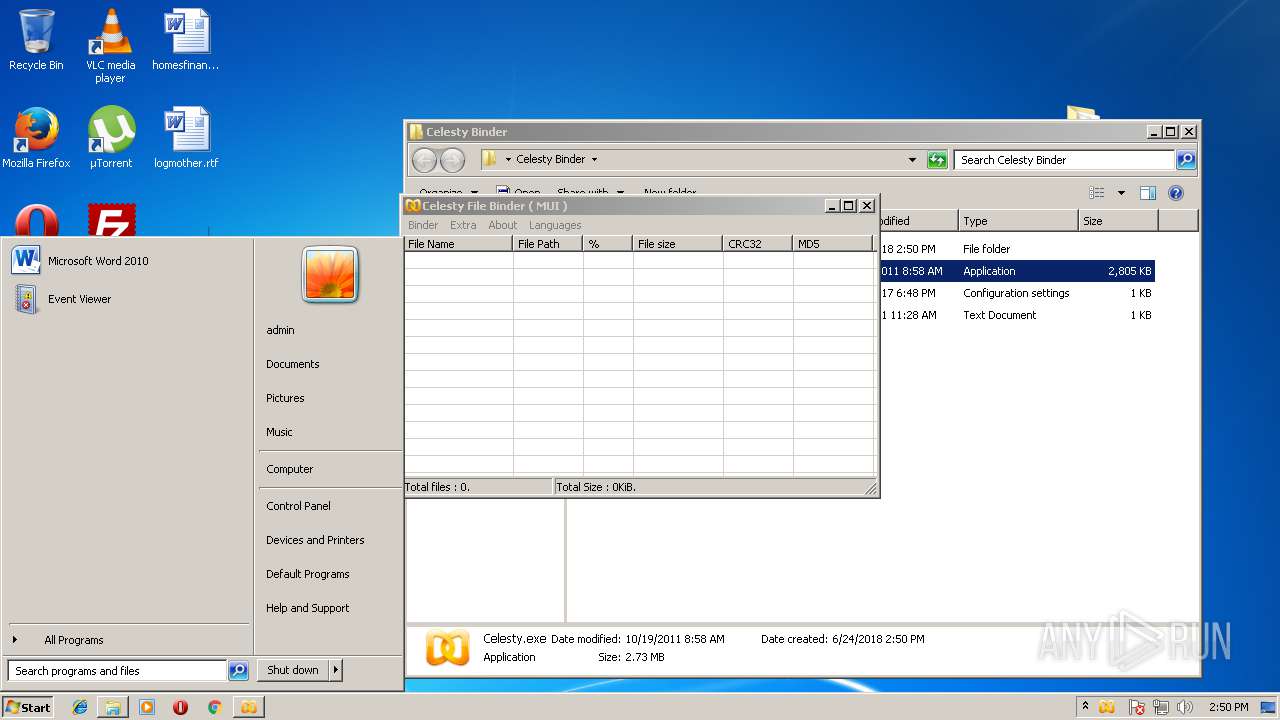
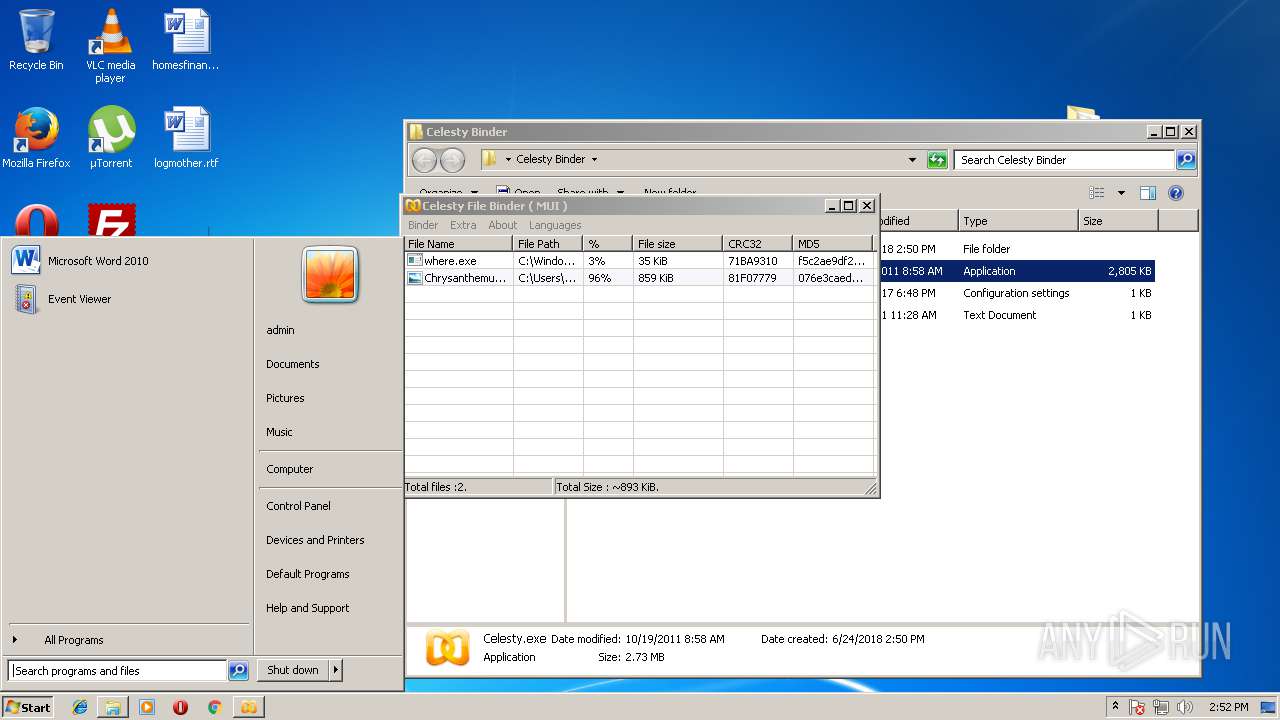
| File name: | Celesty Binder [12345].rar |
| Full analysis: | https://app.any.run/tasks/8de628b7-4c9a-483b-8c09-fddff9008e01 |
| Verdict: | Malicious activity |
| Analysis date: | June 24, 2018, 13:49:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 8E35730B0FCFAFC368EA0DAA0B42EC8A |
| SHA1: | 53910302004978A072C808FF357B90A6BCE2BE75 |
| SHA256: | 69D75137CAFC8CF4BD3EA635A75BECE67C9F7F0A02227F3BC5C99AE6FE99AF5C |
| SSDEEP: | 24576:wJaAAYvi9fKZ5/PMRKi6wzJP6EIJBp/hGEli5qE8v1Ow+IT8O20d:tAAYvoyQRHwTFi4EwlzT8id |
MALICIOUS
Application was dropped or rewritten from another process
- test.exe.exe (PID: 1264)
- Celesty.exe (PID: 3620)
- test.exe (PID: 2024)
- WHERE.EXE (PID: 3464)
- WHERE.EXE (PID: 2076)
SUSPICIOUS
Executable content was dropped or overwritten
- test.exe.exe (PID: 1264)
- Celesty.exe (PID: 3620)
- test.exe (PID: 2024)
INFO
Dropped object may contain URL's
- Celesty.exe (PID: 3620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1191927 |
|---|---|
| UncompressedSize: | 2871808 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2011:10:19 08:58:27 |
| PackingMethod: | Normal |
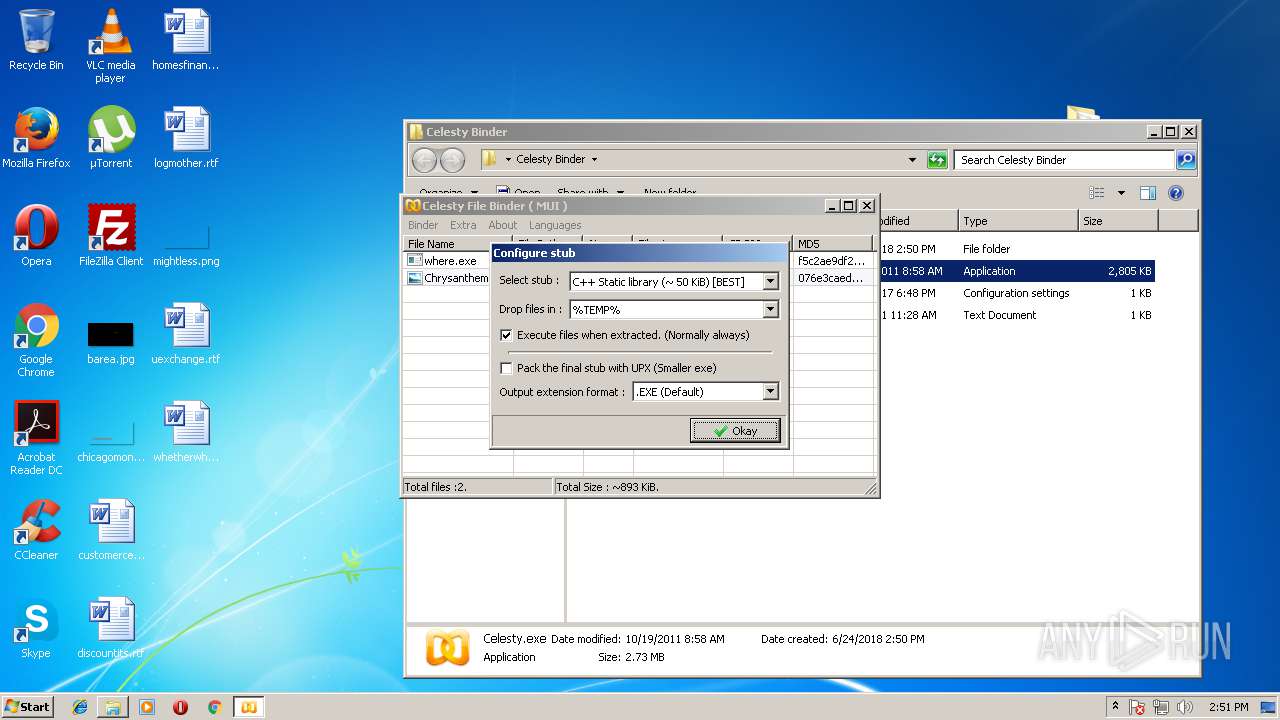
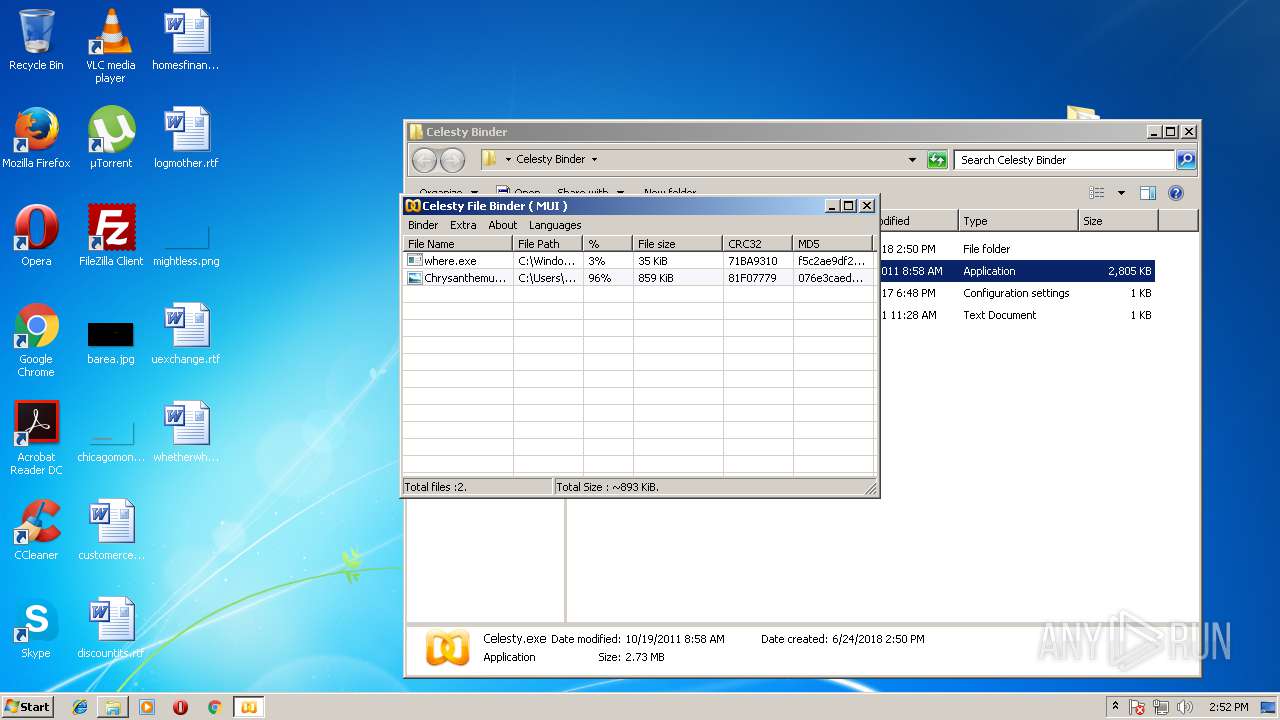
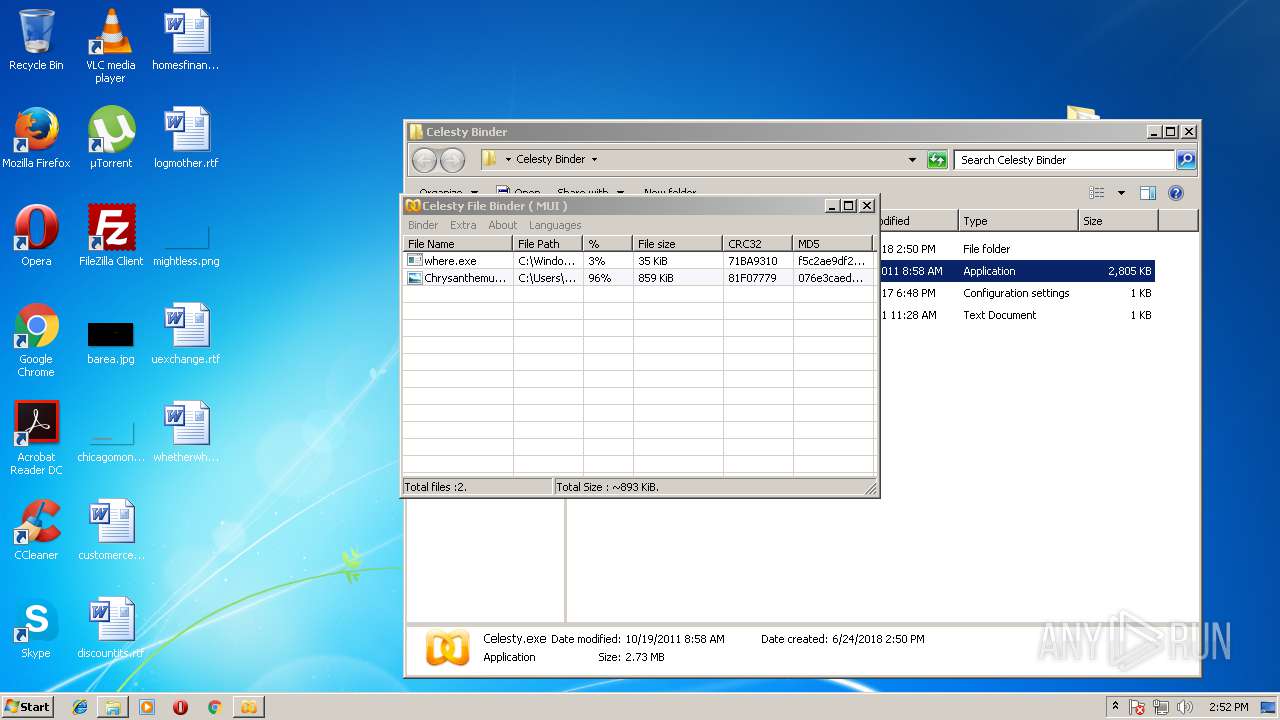
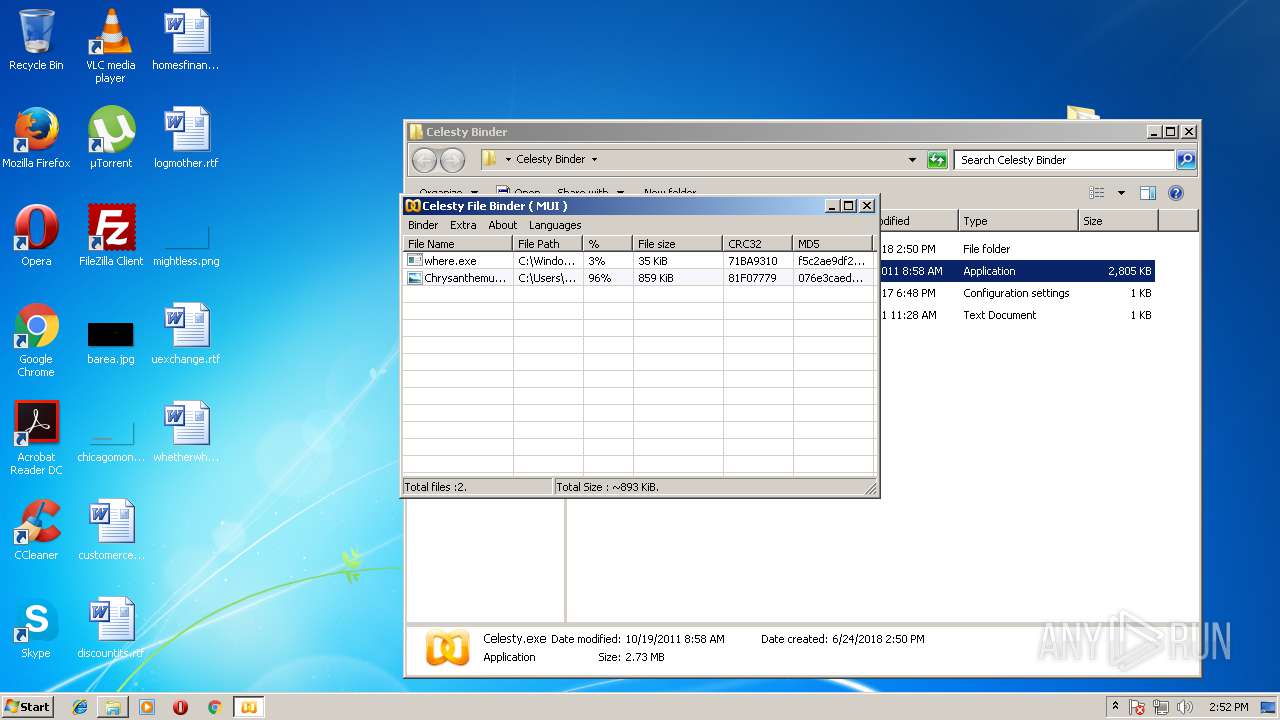
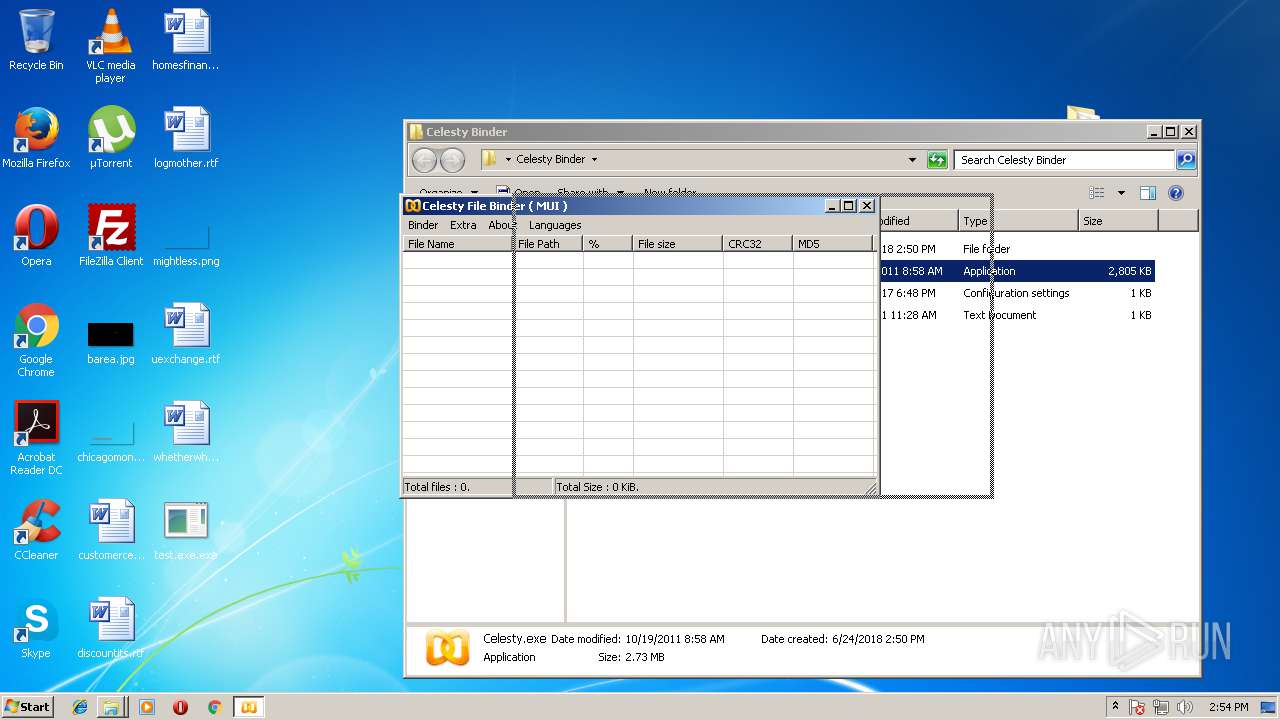
| ArchivedFileName: | Celesty Binder\Celesty.exe |
Total processes
54
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1264 | "C:\Users\admin\Desktop\test.exe.exe" | C:\Users\admin\Desktop\test.exe.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1520 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\Celesty Binder [12345].rar" | C:\Program Files\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 1540 | "C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2024 | "C:\Users\admin\Desktop\test.exe" | C:\Users\admin\Desktop\test.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2076 | "C:\Users\admin\AppData\Local\Temp\WHERE.EXE" | C:\Users\admin\AppData\Local\Temp\WHERE.EXE | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Where - Lists location of files Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2156 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3420 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\AppData\Local\Temp\WHERE.EXE" | C:\Users\admin\AppData\Local\Temp\WHERE.EXE | — | test.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Where - Lists location of files Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3620 | "C:\Users\admin\Desktop\Celesty Binder\Celesty.exe" | C:\Users\admin\Desktop\Celesty Binder\Celesty.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 346
Read events
1 250
Write events
94
Delete events
2
Modification events
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00430065006C0065007300740079002000420069006E0064006500720020005B00310032003300340035005D002E007200610072005C000000 | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 1600000016000000D60300000B02000000000000 | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (1520) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000000F00000001000000640000000D00000001000000640000000E00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000002100000001000000640000001F0000000100000064000000200000000100000064000000 | |||
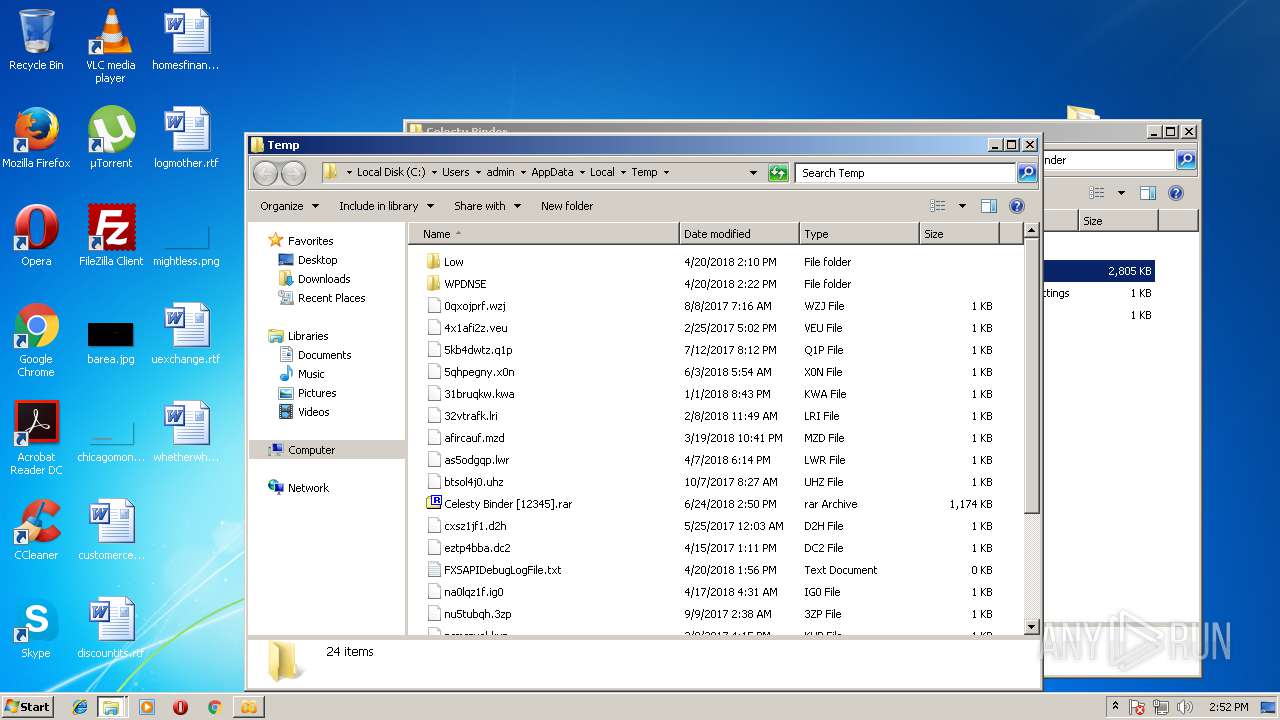
Executable files
6
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Celesty.exe | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\config.ini | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Lang\AR.ini | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Lang\EN.ini | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Lang\ES.ini | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Lang\FR.ini | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Lang\GR.ini | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Lang\IT.ini | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Lang\LV.ini | — | |
MD5:— | SHA256:— | |||
| 1520 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE0F574BAA\Celesty Binder\Lang\NO.ini | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
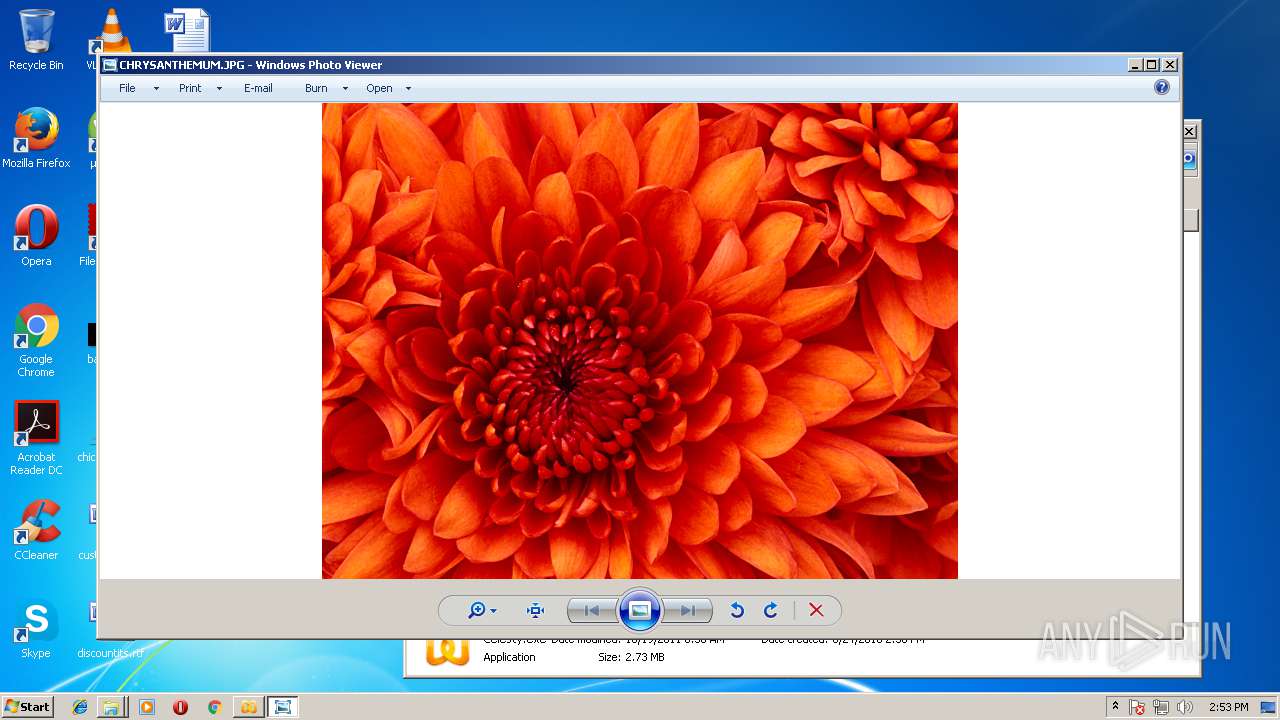
test.exe.exe | C:\Users\admin\AppData\Local\Temp\CHRYSANTHEMUM.JPG |
test.exe.exe | C:\Users\admin\AppData\Local\Temp\WHERE.EXE |
test.exe | C:\Users\admin\AppData\Local\Temp\CHRYSANTHEMUM.JPG |
test.exe | C:\Users\admin\AppData\Local\Temp\WHERE.EXE |