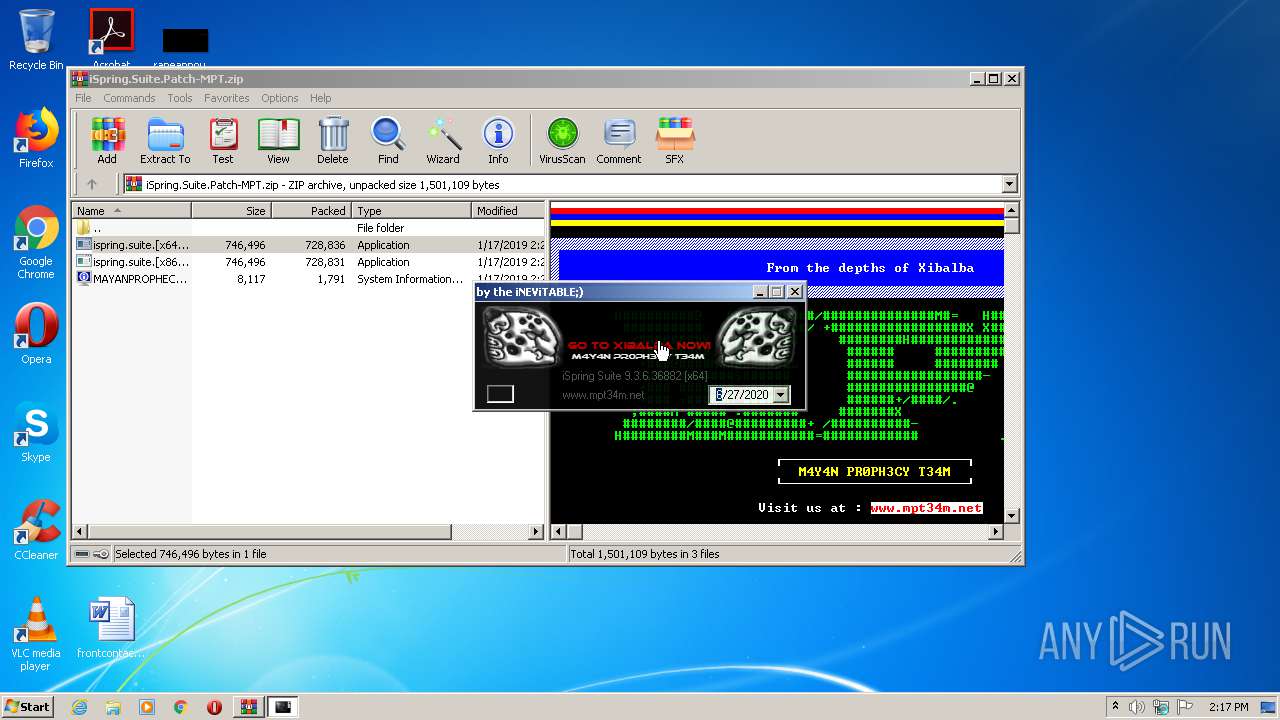
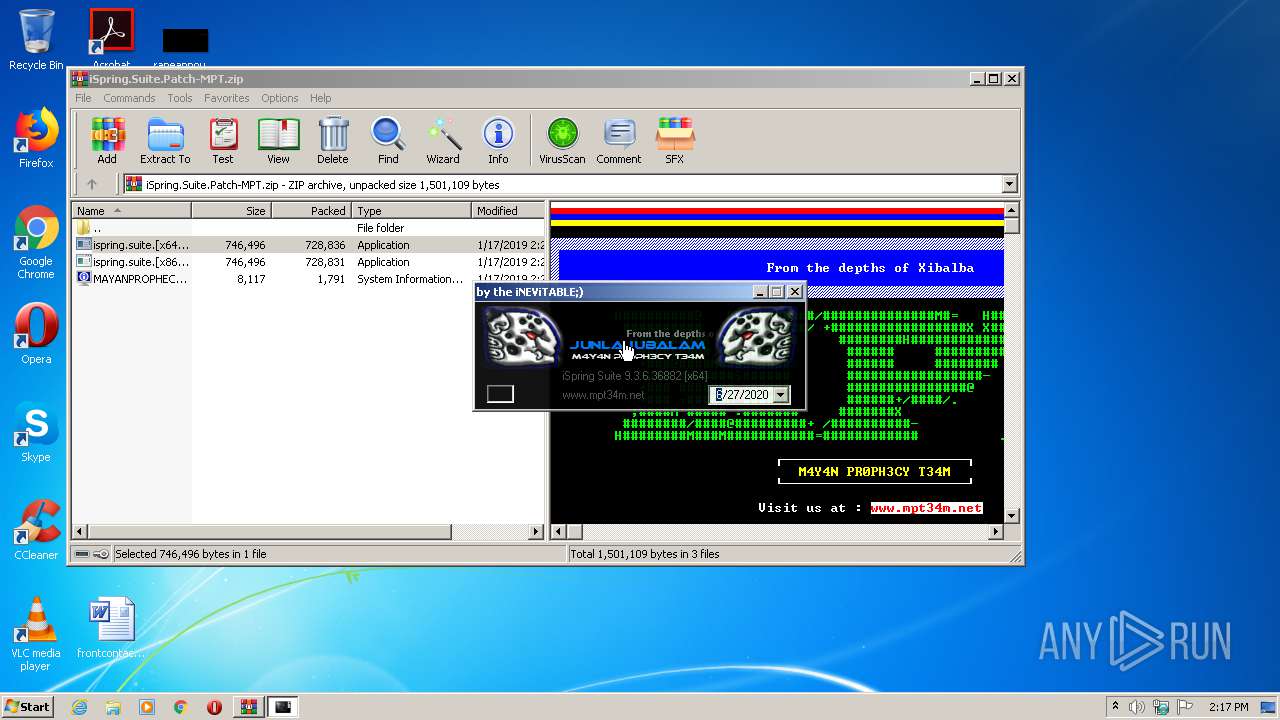
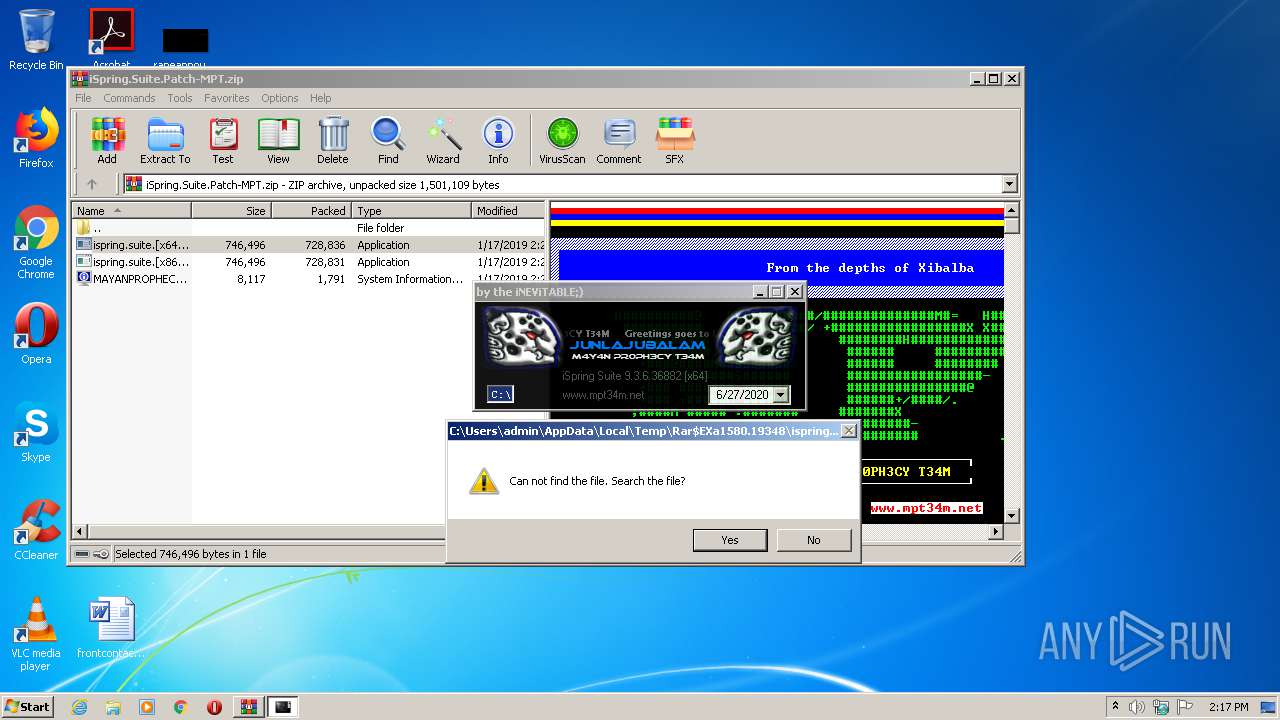
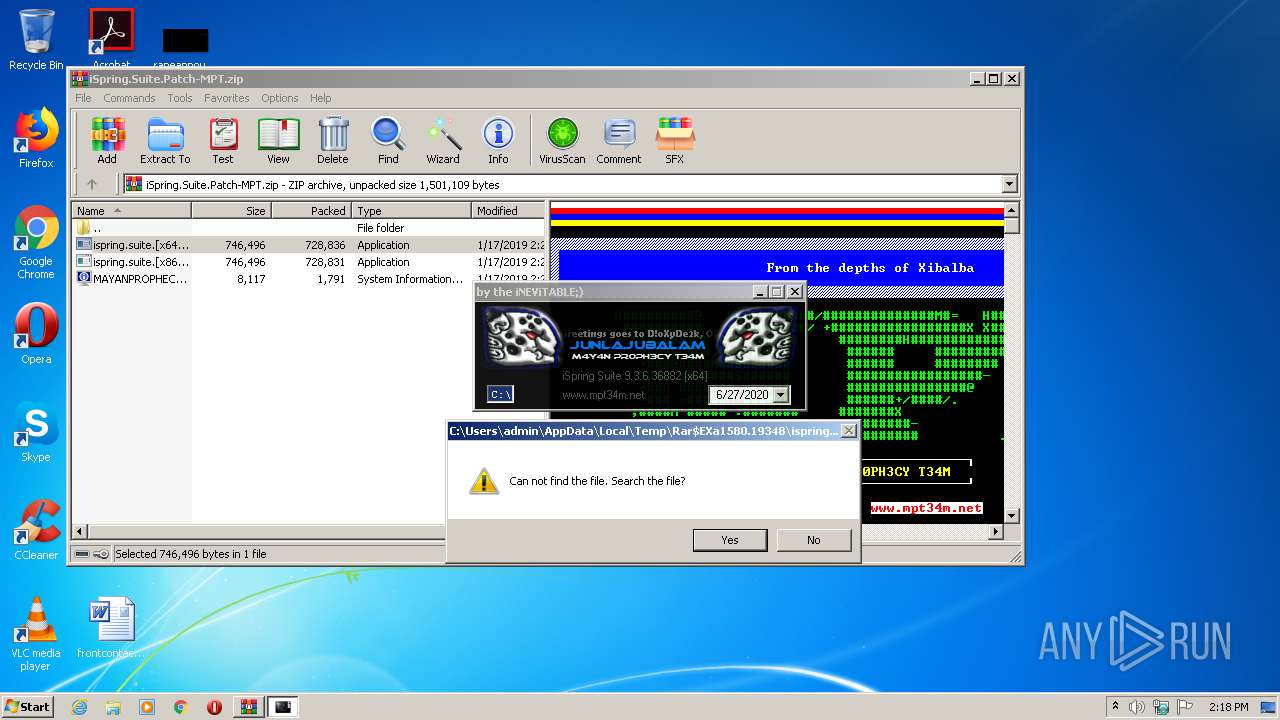
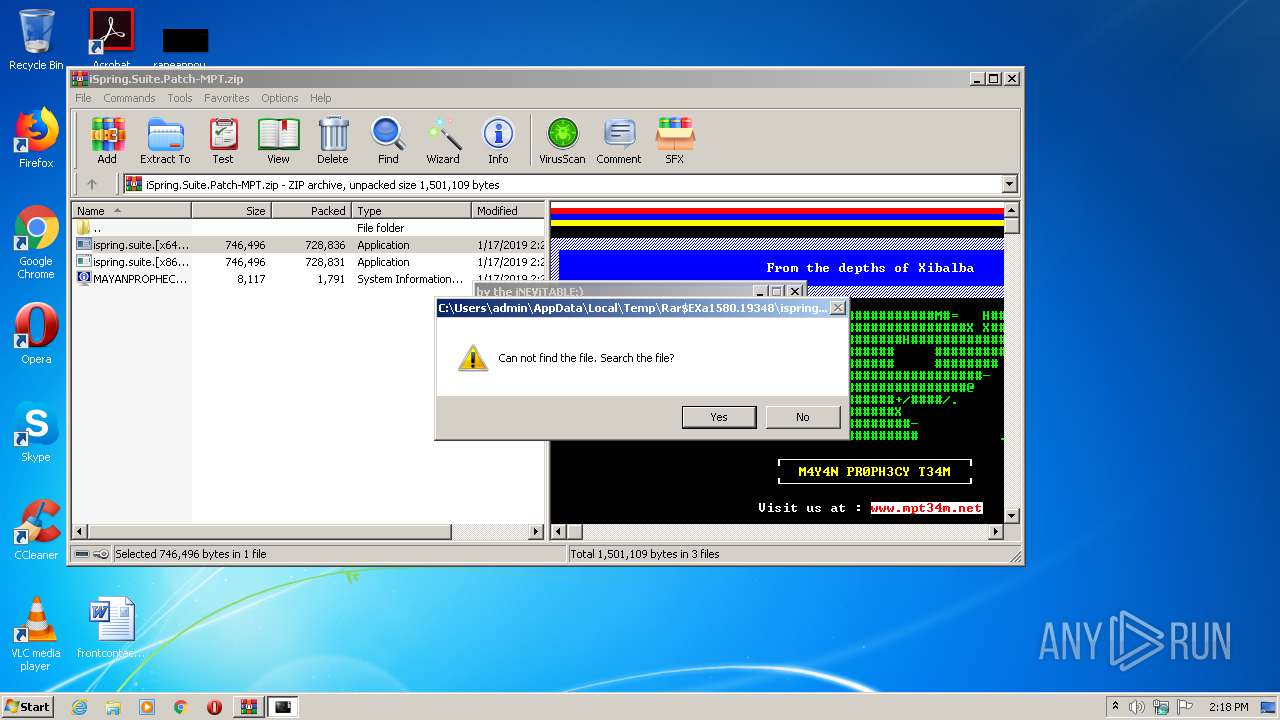
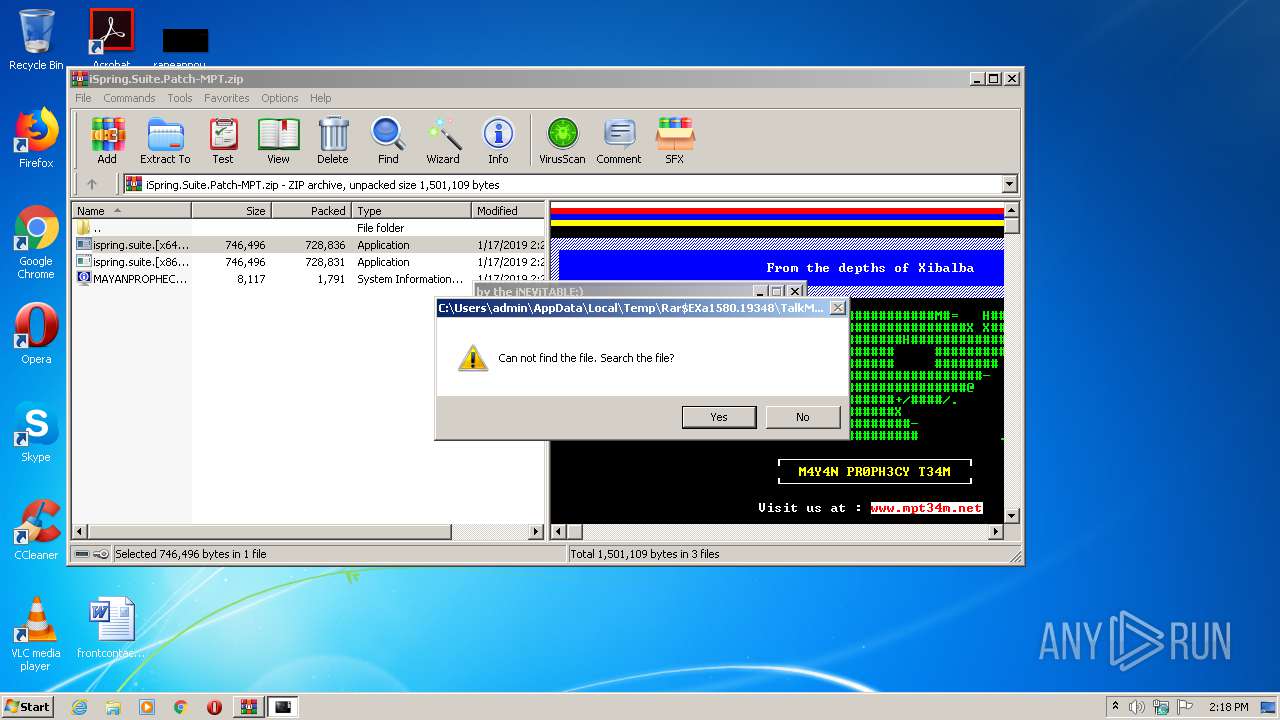
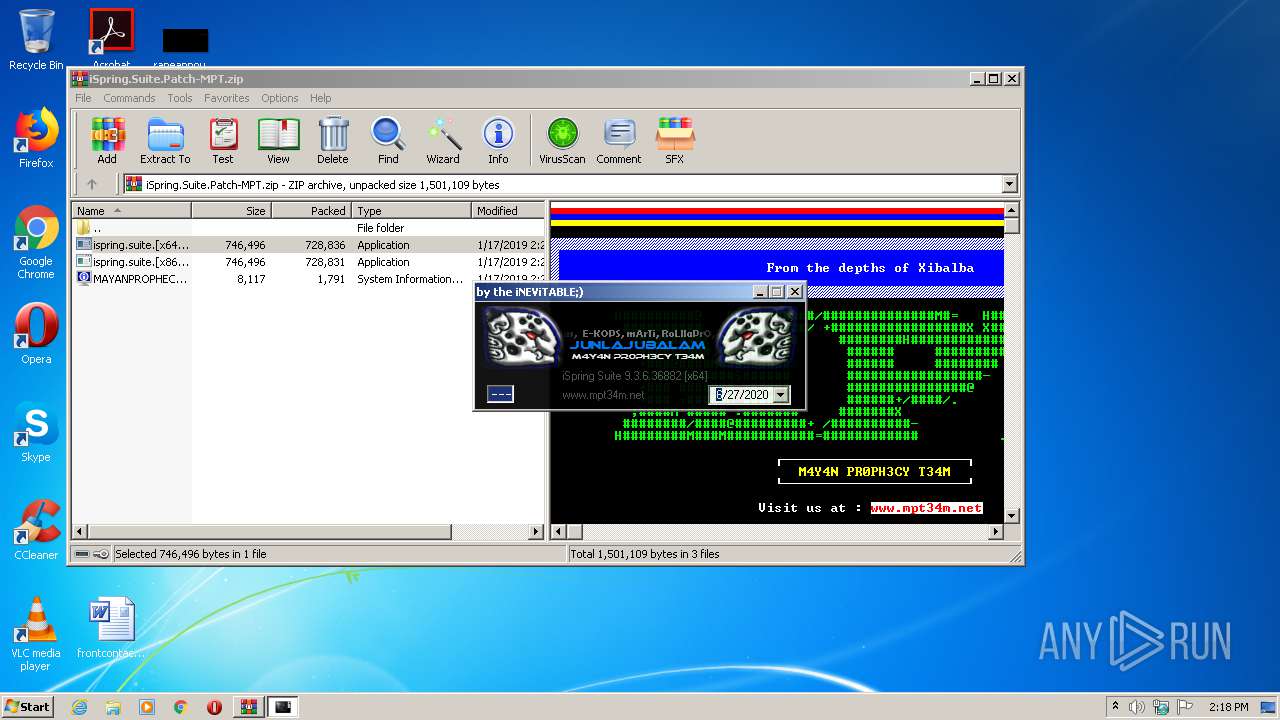
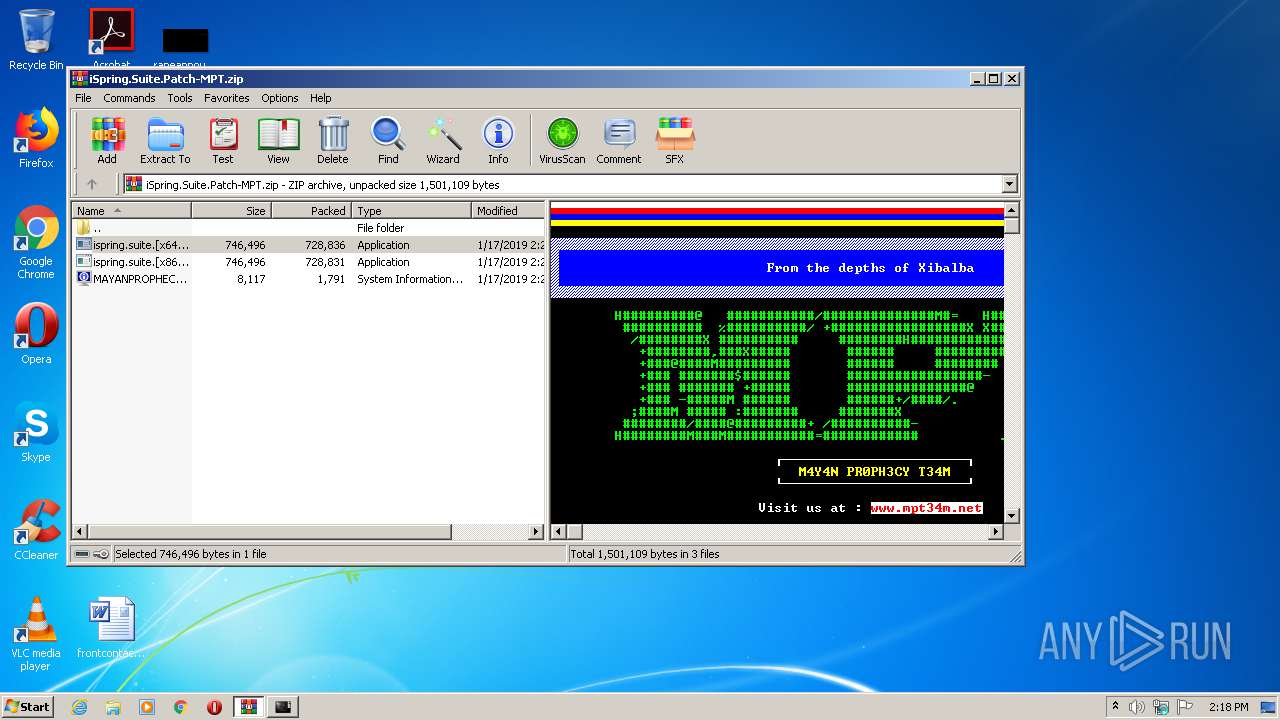
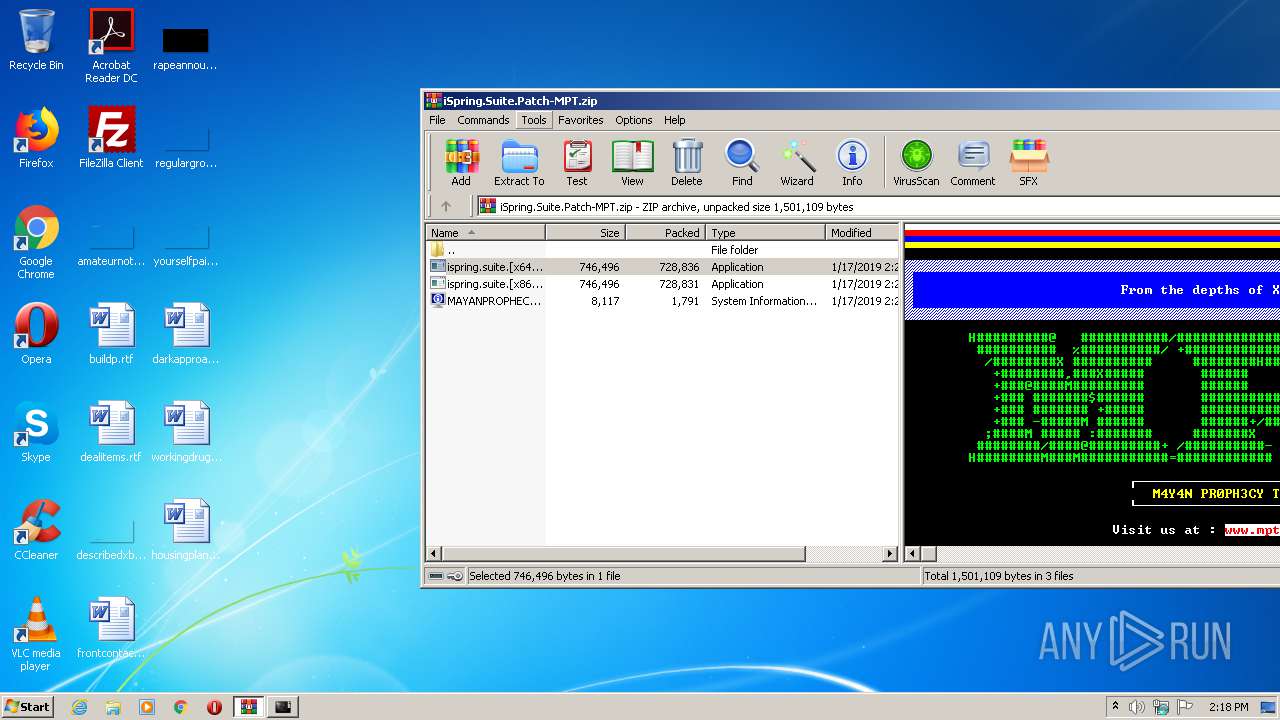
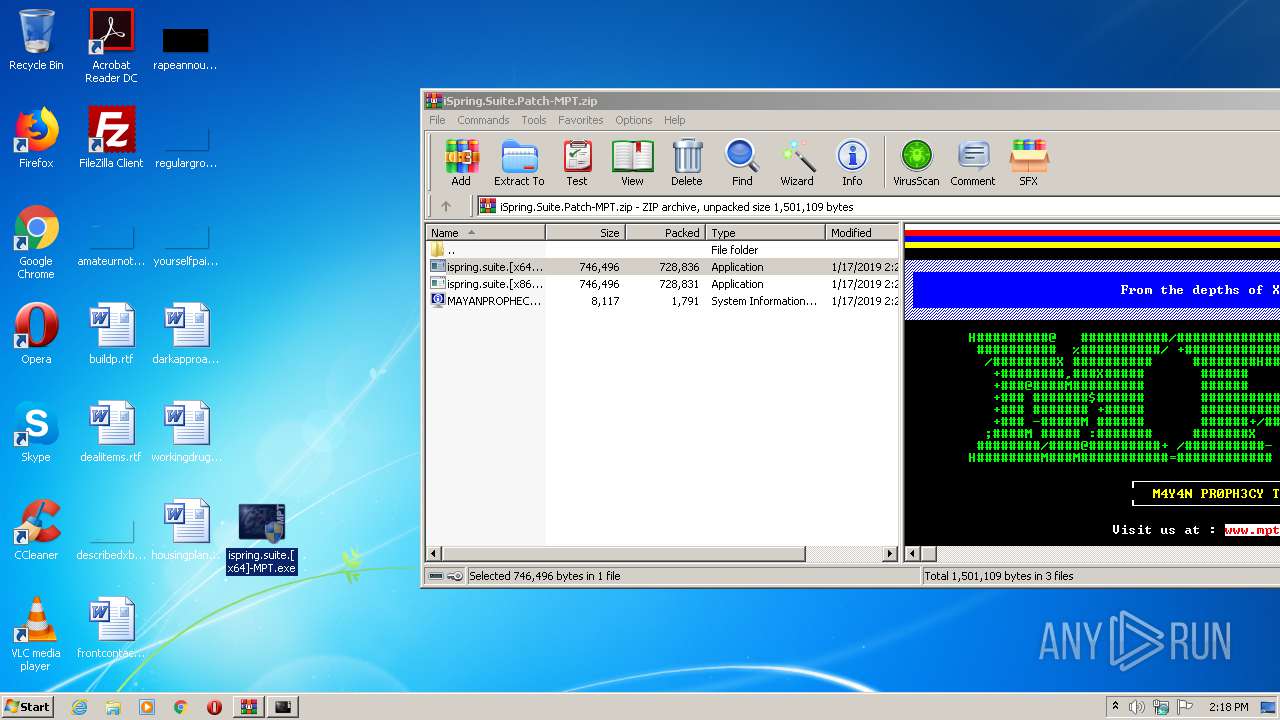
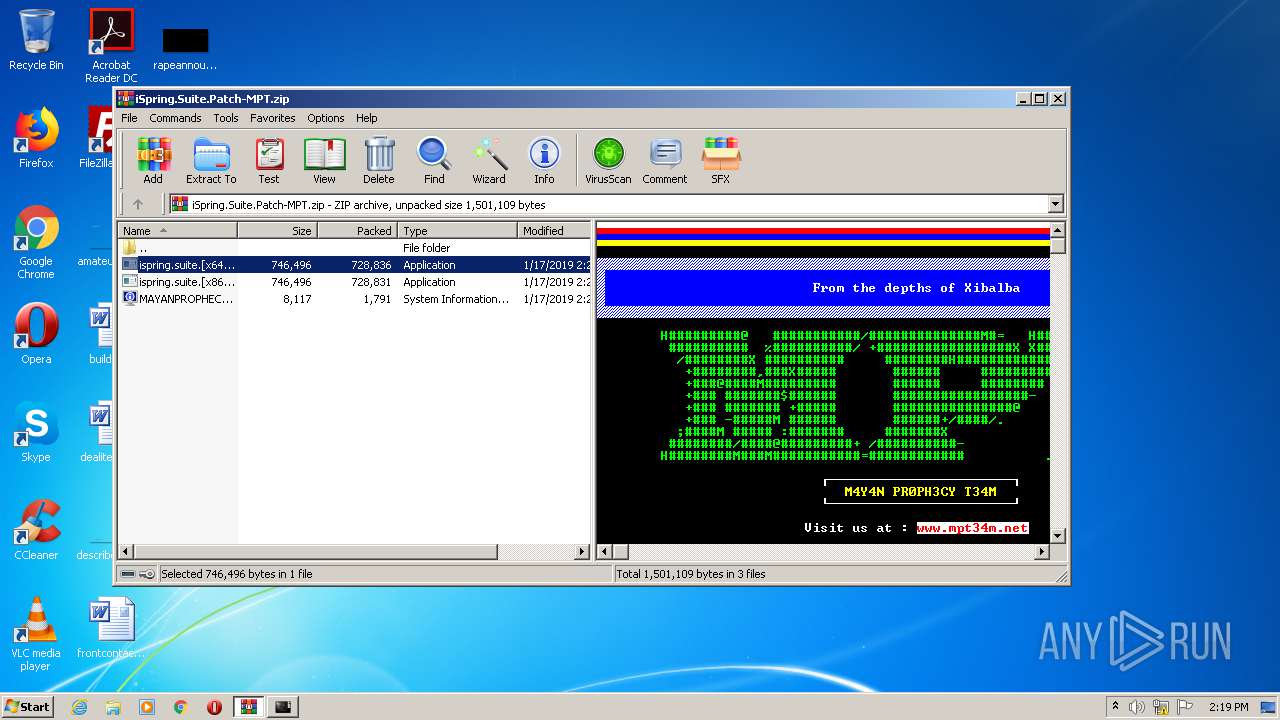
| File name: | iSpring.Suite.Patch-MPT.zip |
| Full analysis: | https://app.any.run/tasks/bb078ee9-023e-4f00-975b-1eeca8c0395d |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2020, 13:17:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 0F1AE32AA0E2F1B505A97736482A5A93 |
| SHA1: | AA484592B1843E92BFFD6D3E057CE5CF4F506C8C |
| SHA256: | 69D6A73B6297EF0AD5D2CDC5E3BAC8CA1BFA14B8D7A7D859921D839CC9DC8D7B |
| SSDEEP: | 24576:Dc9kZvxR3R+Ab+I7tF5sIqNuPb5+86EY8oTD1xT6tlODjtbrCzgYa4cp4:DcyvBFb+OFiIq4Pb5+38K4lODZb+a4ci |
MALICIOUS
Application was dropped or rewritten from another process
- ispring.suite.[x64]-MPT.exe (PID: 1552)
- ispring.suite.[x64]-MPT.exe (PID: 1948)
- ispring.suite.[x64]-MPT.exe (PID: 1308)
- ispring.suite.[x64]-MPT.exe (PID: 2600)
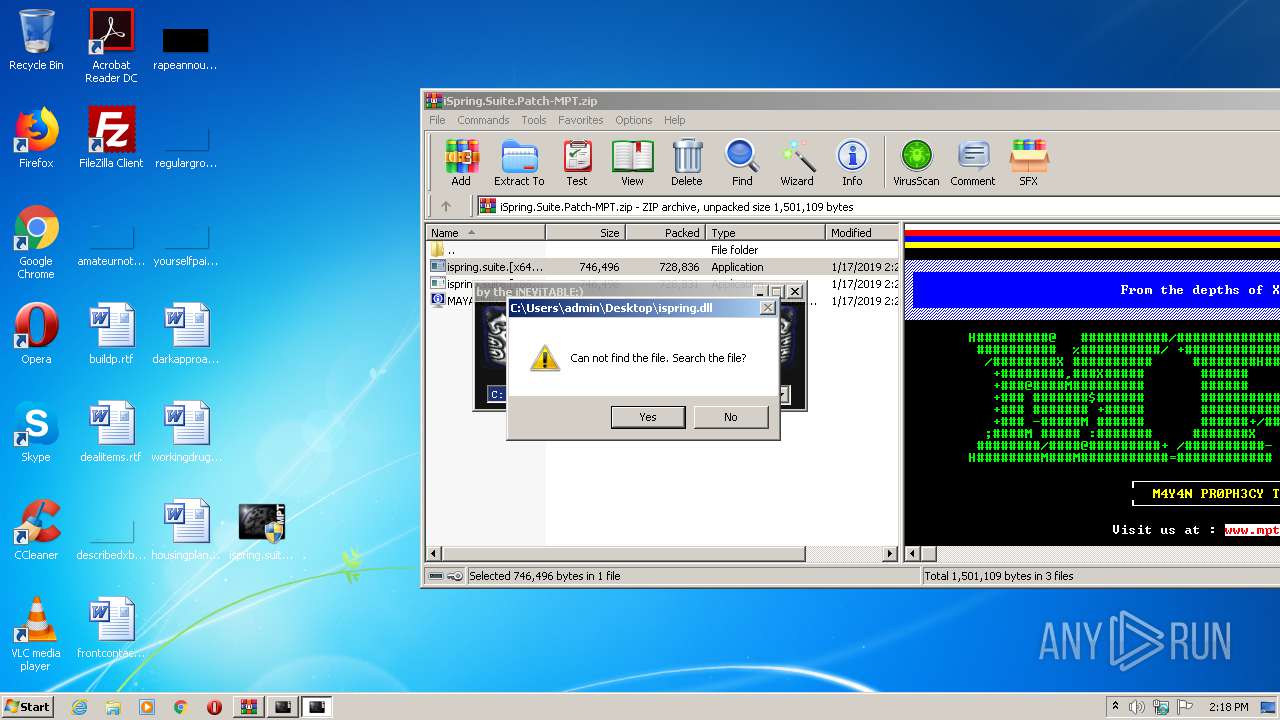
Loads dropped or rewritten executable
- ispring.suite.[x64]-MPT.exe (PID: 1948)
- ispring.suite.[x64]-MPT.exe (PID: 2600)
SUSPICIOUS
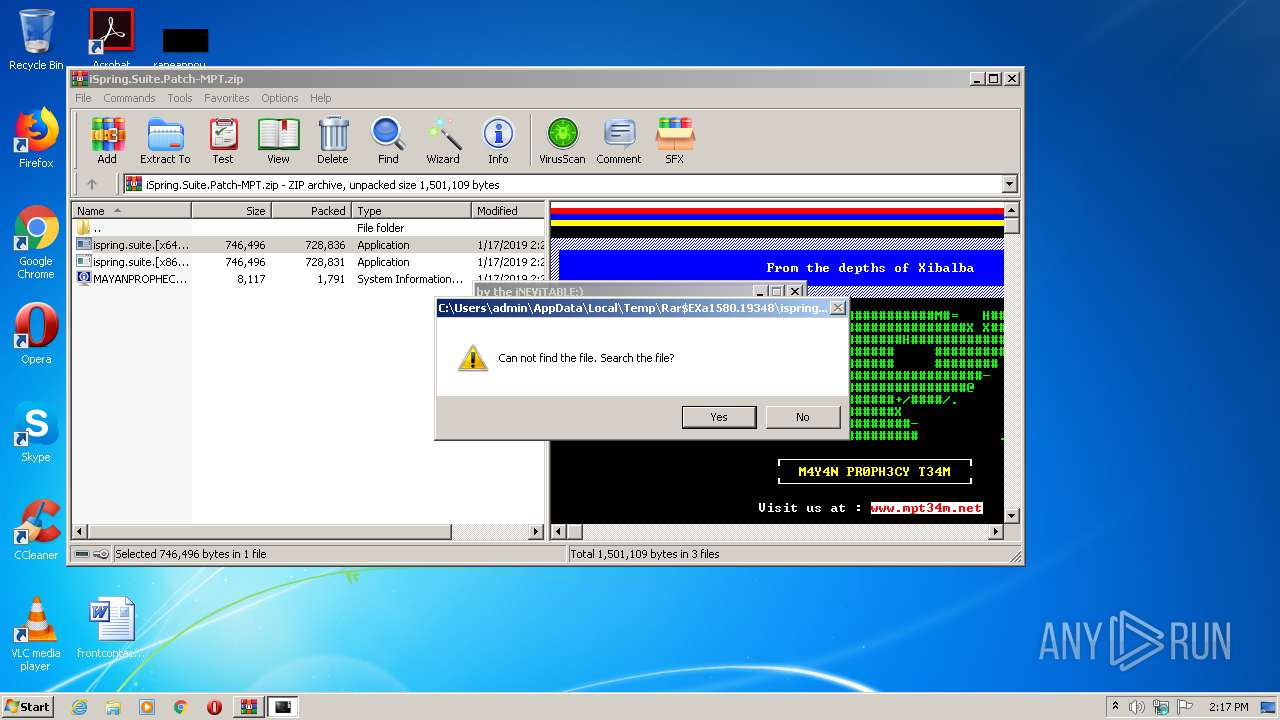
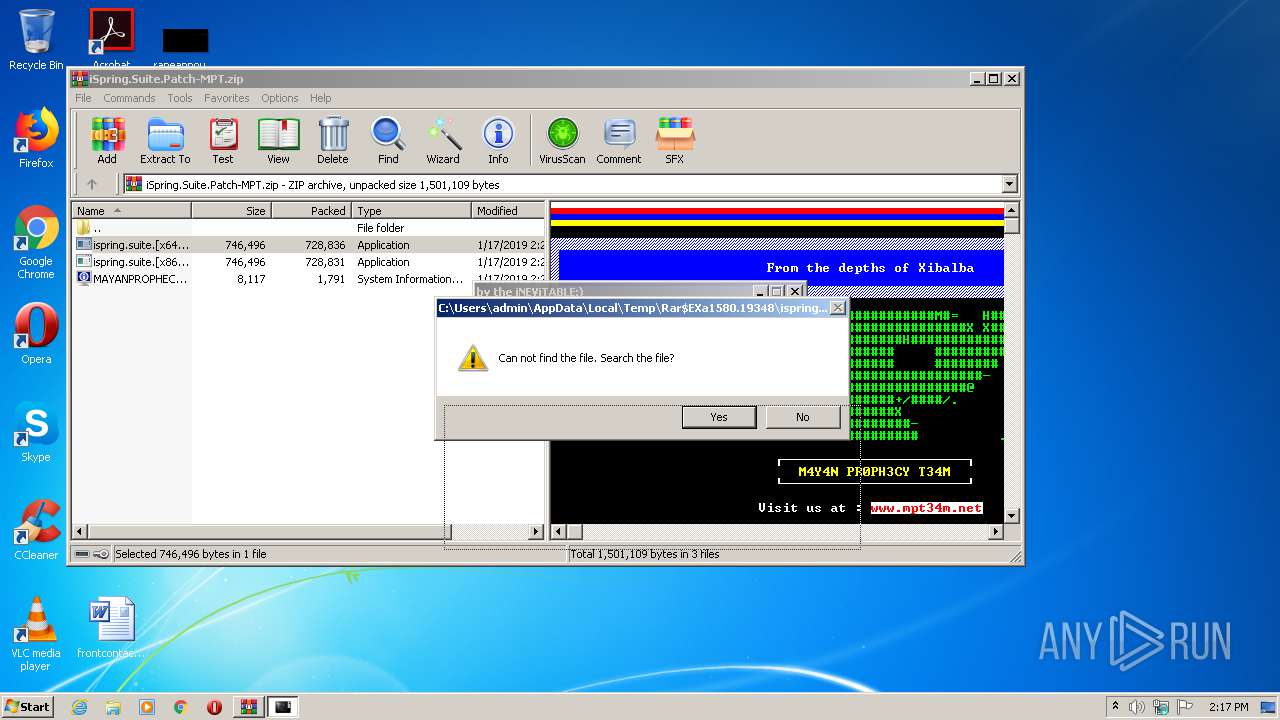
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1580)
- ispring.suite.[x64]-MPT.exe (PID: 1948)
INFO
Manual execution by user
- ispring.suite.[x64]-MPT.exe (PID: 1308)
- ispring.suite.[x64]-MPT.exe (PID: 2600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:17 15:26:05 |
| ZipCRC: | 0x6ee93a18 |
| ZipCompressedSize: | 1791 |
| ZipUncompressedSize: | 8117 |
| ZipFileName: | MAYANPROPHECY.nfo |
Total processes
45
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1308 | "C:\Users\admin\Desktop\ispring.suite.[x64]-MPT.exe" | C:\Users\admin\Desktop\ispring.suite.[x64]-MPT.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1552 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1580.19348\ispring.suite.[x64]-MPT.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1580.19348\ispring.suite.[x64]-MPT.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1580 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\iSpring.Suite.Patch-MPT.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1948 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1580.19348\ispring.suite.[x64]-MPT.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1580.19348\ispring.suite.[x64]-MPT.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2600 | "C:\Users\admin\Desktop\ispring.suite.[x64]-MPT.exe" | C:\Users\admin\Desktop\ispring.suite.[x64]-MPT.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
485
Read events
458
Write events
27
Delete events
0
Modification events
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\iSpring.Suite.Patch-MPT.zip | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\msinfo32.exe,-10001 |
Value: System Information File | |||
Executable files
6
Suspicious files
0
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1948 | ispring.suite.[x64]-MPT.exe | C:\Users\admin\AppData\Local\Temp\dup2patcher.dll | executable | |
MD5:— | SHA256:— | |||
| 1580 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1580.19348\MAYANPROPHECY.nfo | text | |
MD5:B770796921F1FDD4F4B21F6F53DF79BB | SHA256:67FE058CA734D7A3DEE53FE5E4645103EE19F4F33E80BD5A8B5A965AA0AB17AD | |||
| 1580 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1580.19348\ispring.suite.[x64]-MPT.exe | executable | |
MD5:1E1E956A53E659F321D217B6B290E00E | SHA256:6EF391412A9D917D2D318A5DDB001A9AAF2503A4AF3FB2D36F70658917BB47CF | |||
| 1948 | ispring.suite.[x64]-MPT.exe | C:\Users\admin\AppData\Local\Temp\bassmod.dll | executable | |
MD5:780D14604D49E3C634200C523DEF8351 | SHA256:844EB66A10B848D3A71A8C63C35F0A01550A46D2FF8503E2CA8947978B03B4D2 | |||
| 1580 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1580.22167\ispring.suite.[x64]-MPT.exe | executable | |
MD5:1E1E956A53E659F321D217B6B290E00E | SHA256:6EF391412A9D917D2D318A5DDB001A9AAF2503A4AF3FB2D36F70658917BB47CF | |||
| 1948 | ispring.suite.[x64]-MPT.exe | C:\Users\admin\AppData\Local\Temp\7CEB9B2A0E395BD64E74381485A106AF.dll | executable | |
MD5:5AFB011D9DB047BB0400C5C5CA2E450B | SHA256:125FC74E03435B3E0EDE0FF523D625D9C1FBB299286E9E2DBD1442E506150DA6 | |||
| 1948 | ispring.suite.[x64]-MPT.exe | C:\Users\admin\AppData\Local\Temp\Berlin Sans FB.TTF | odttf | |
MD5:FE2027C27B6A24505F548C6FD2E1076D | SHA256:0B6044C72E67AAAE9C2AE3C8B4BB06D066FDBC02779C68E3883984ACBBE24CB8 | |||
| 2600 | ispring.suite.[x64]-MPT.exe | C:\Users\admin\AppData\Local\Temp\Berlin Sans FB.TTF | odttf | |
MD5:FE2027C27B6A24505F548C6FD2E1076D | SHA256:0B6044C72E67AAAE9C2AE3C8B4BB06D066FDBC02779C68E3883984ACBBE24CB8 | |||
| 1580 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1580.19348\ispring.suite.[x86]-MPT.exe | executable | |
MD5:002F32C683F6D007EB52F330BAABE6B2 | SHA256:1E296C8D38A3CCB327122290C5177ACCF2EFA0DA2CBB6BFB402F213C4F86F34D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report