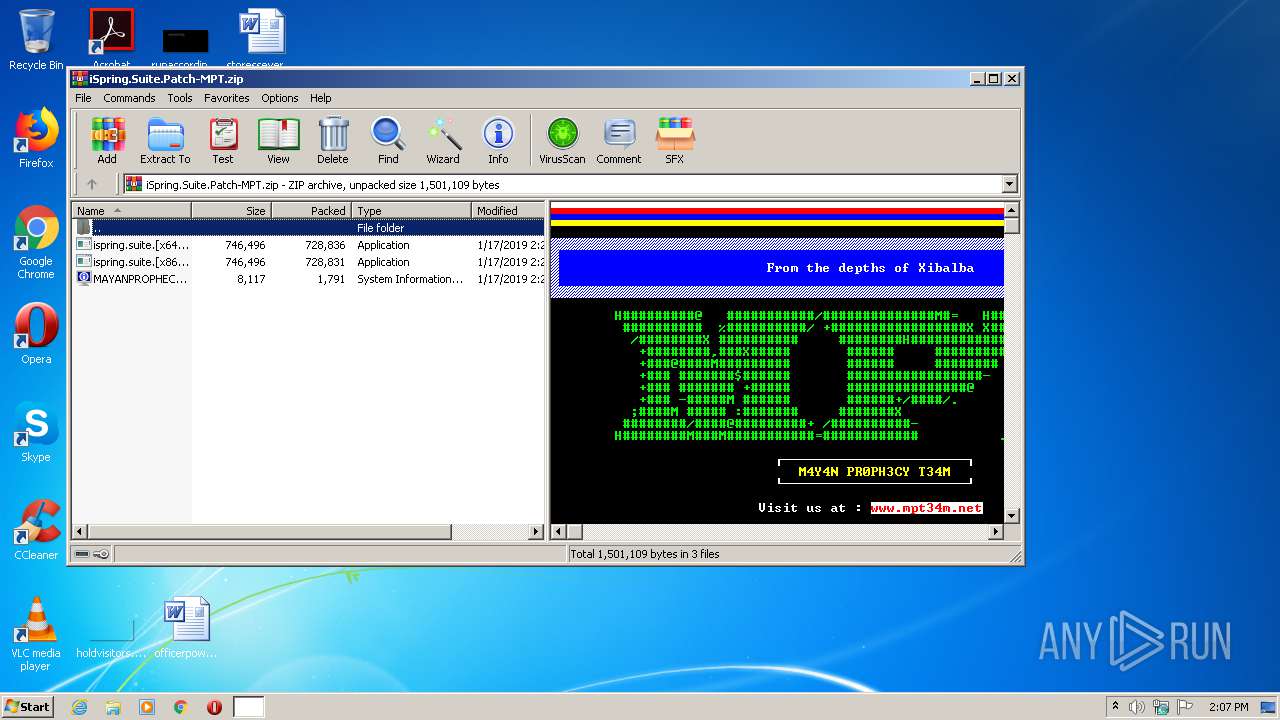
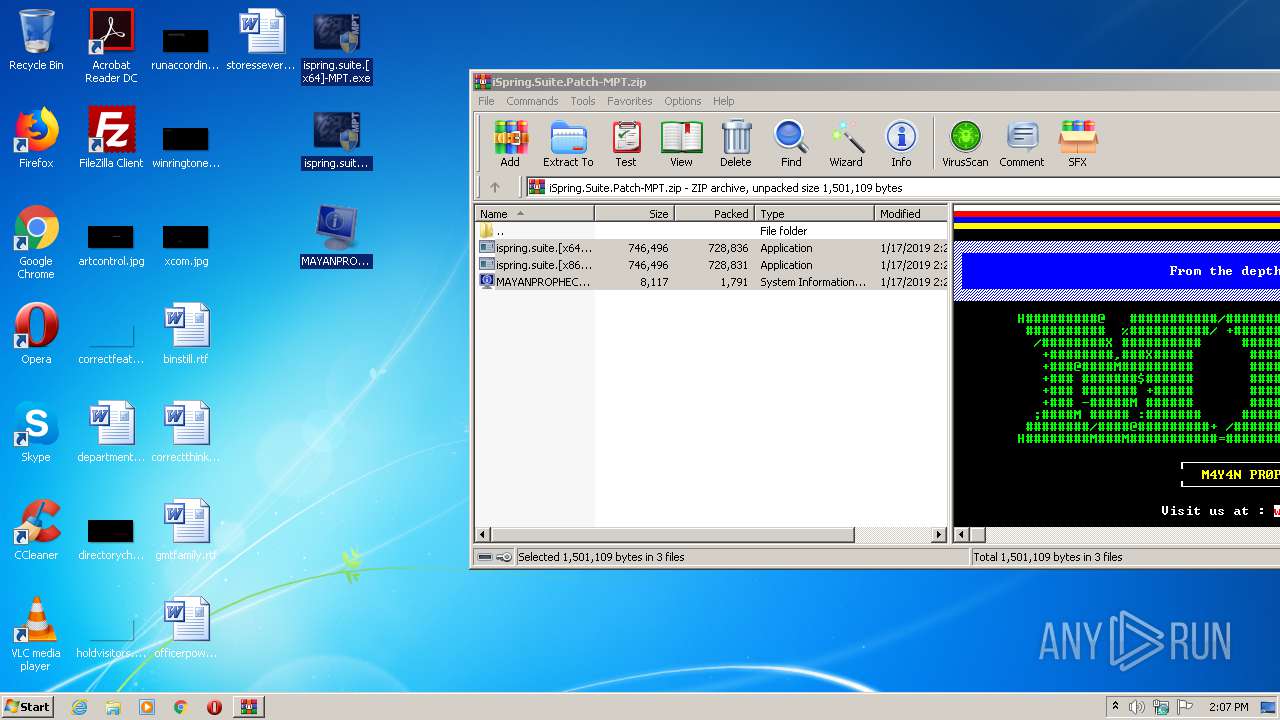
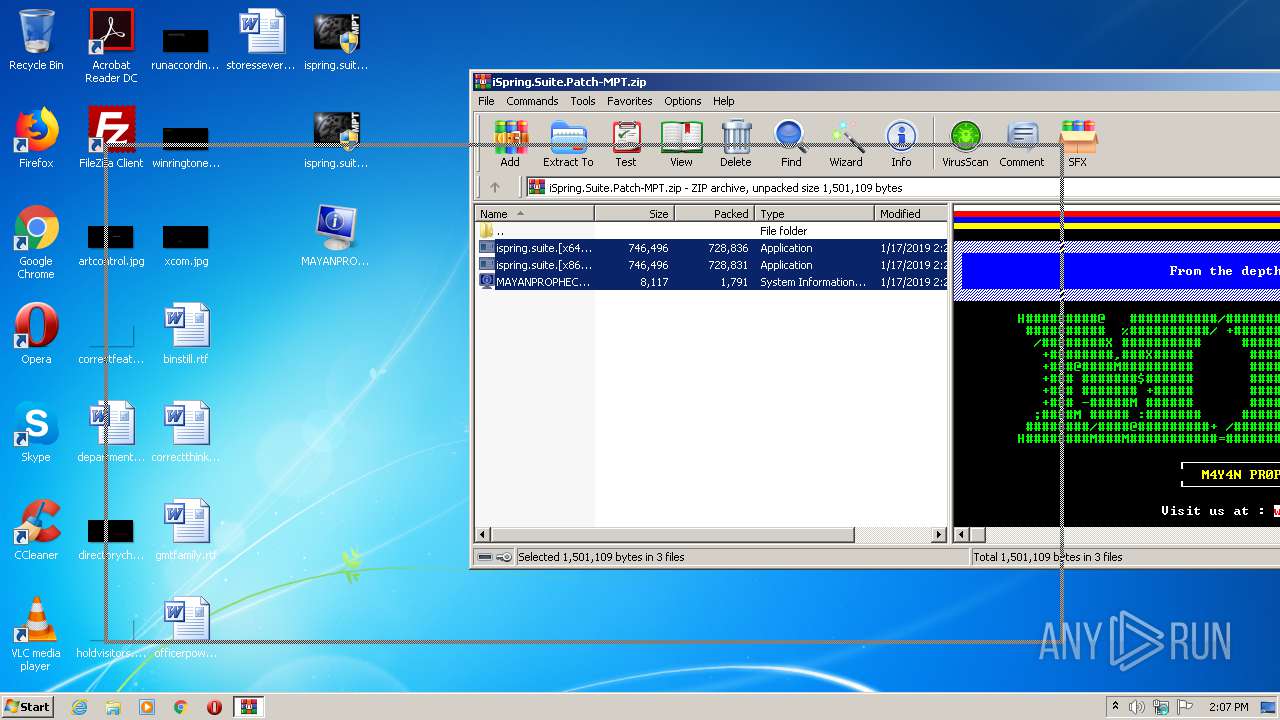
| File name: | iSpring.Suite.Patch-MPT.zip |
| Full analysis: | https://app.any.run/tasks/89250fa0-4de6-4aca-9889-53f2a4ea6234 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2020, 13:07:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 0F1AE32AA0E2F1B505A97736482A5A93 |
| SHA1: | AA484592B1843E92BFFD6D3E057CE5CF4F506C8C |
| SHA256: | 69D6A73B6297EF0AD5D2CDC5E3BAC8CA1BFA14B8D7A7D859921D839CC9DC8D7B |
| SSDEEP: | 24576:Dc9kZvxR3R+Ab+I7tF5sIqNuPb5+86EY8oTD1xT6tlODjtbrCzgYa4cp4:DcyvBFb+OFiIq4Pb5+38K4lODZb+a4ci |
MALICIOUS
Application was dropped or rewritten from another process
- ispring.suite.[x86]-MPT.exe (PID: 2884)
- ispring.suite.[x86]-MPT.exe (PID: 3912)
Loads dropped or rewritten executable
- ispring.suite.[x86]-MPT.exe (PID: 3912)
SUSPICIOUS
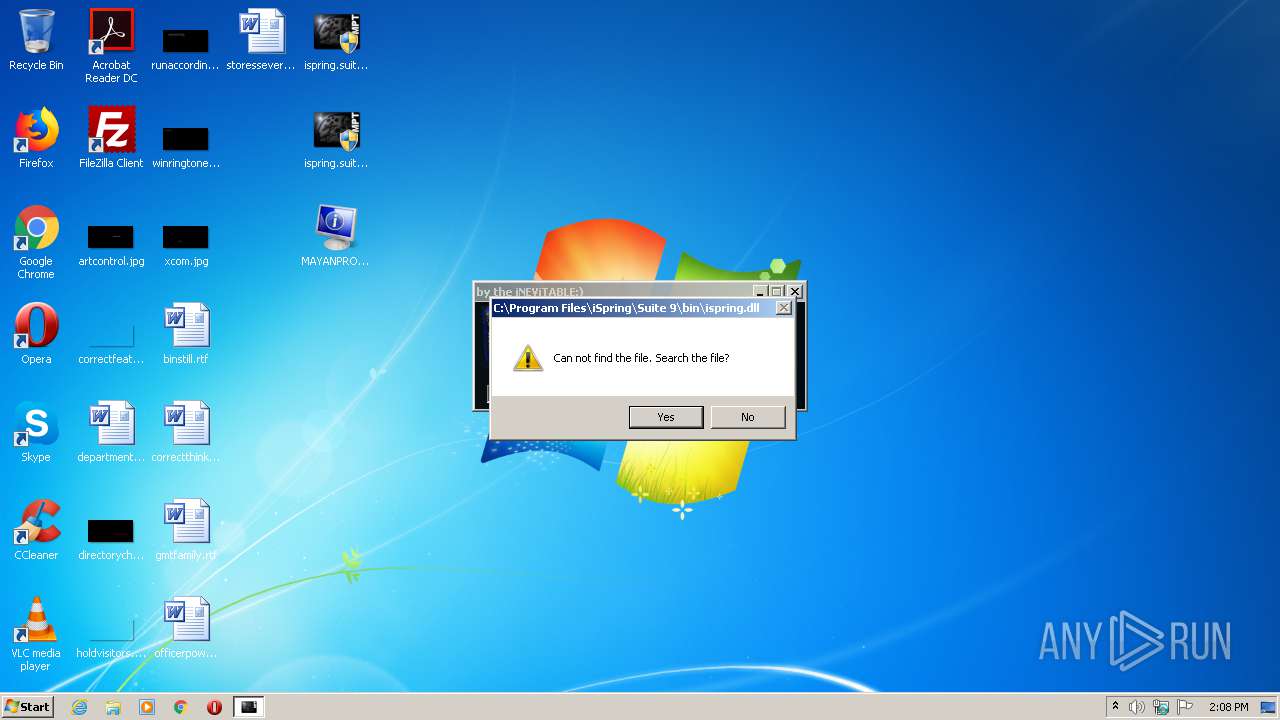
Executable content was dropped or overwritten
- ispring.suite.[x86]-MPT.exe (PID: 3912)
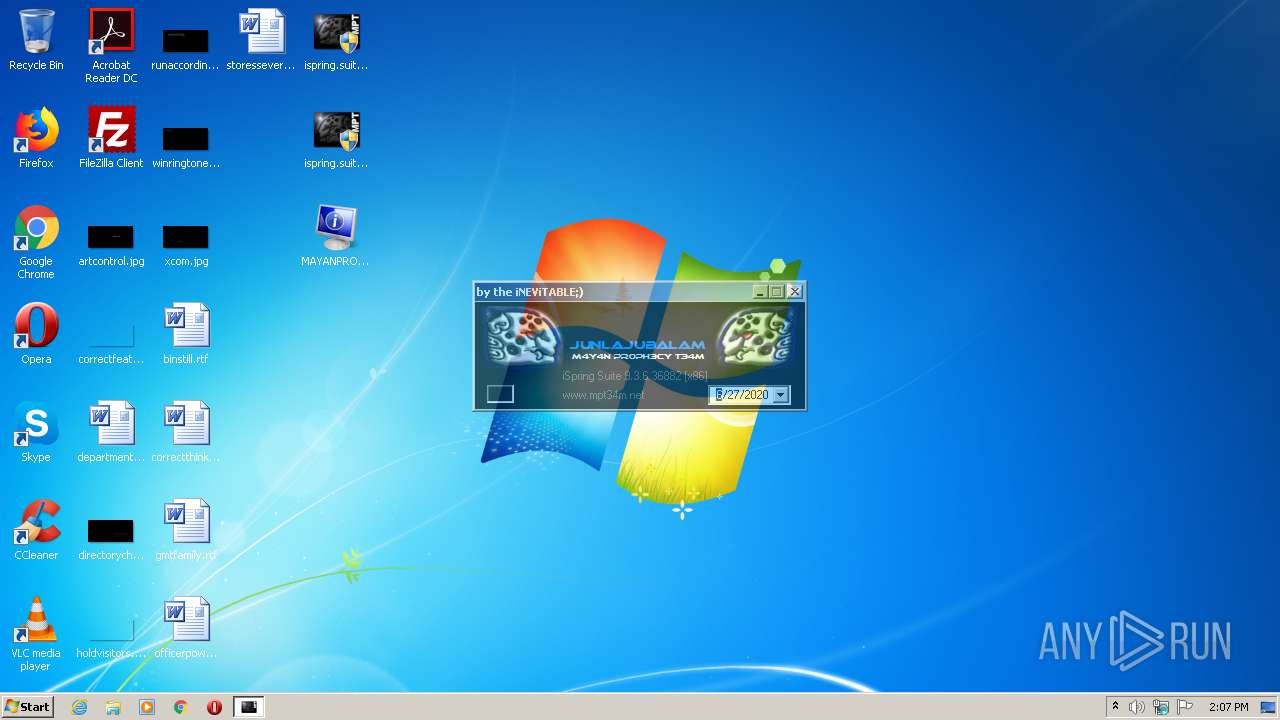
Starts Internet Explorer
- ispring.suite.[x86]-MPT.exe (PID: 3912)
INFO
Manual execution by user
- ispring.suite.[x86]-MPT.exe (PID: 3912)
- ispring.suite.[x86]-MPT.exe (PID: 2884)
Reads Internet Cache Settings
- iexplore.exe (PID: 3088)
- iexplore.exe (PID: 2504)
Changes internet zones settings
- iexplore.exe (PID: 3088)
Reads settings of System Certificates
- iexplore.exe (PID: 2504)
Changes settings of System certificates
- iexplore.exe (PID: 2504)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:17 15:26:05 |
| ZipCRC: | 0x6ee93a18 |
| ZipCompressedSize: | 1791 |
| ZipUncompressedSize: | 8117 |
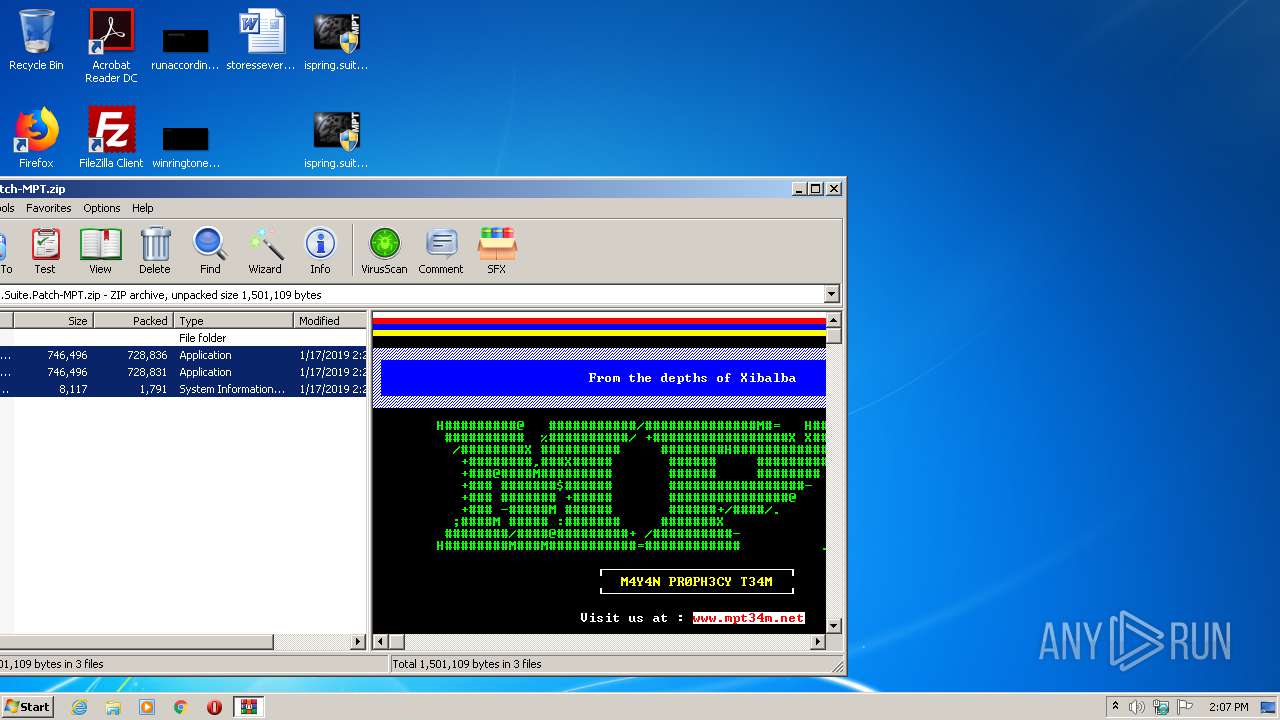
| ZipFileName: | MAYANPROPHECY.nfo |
Total processes
42
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1704 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\iSpring.Suite.Patch-MPT.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3088 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
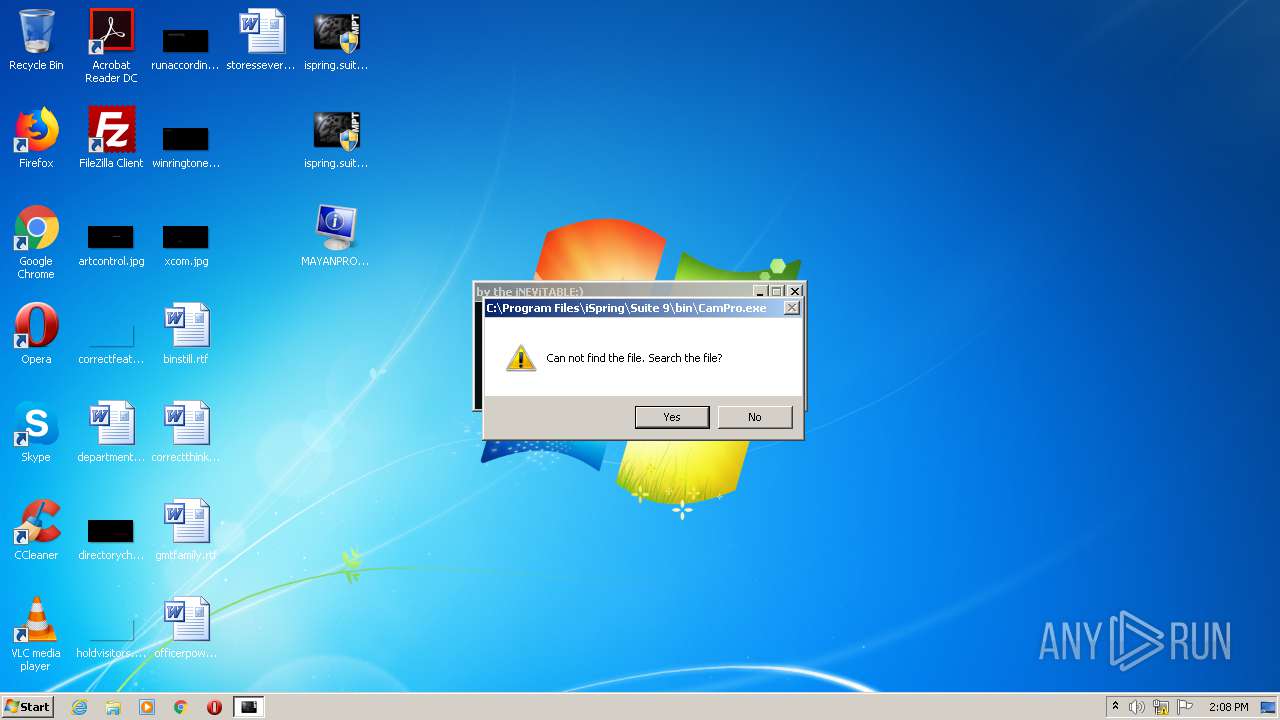
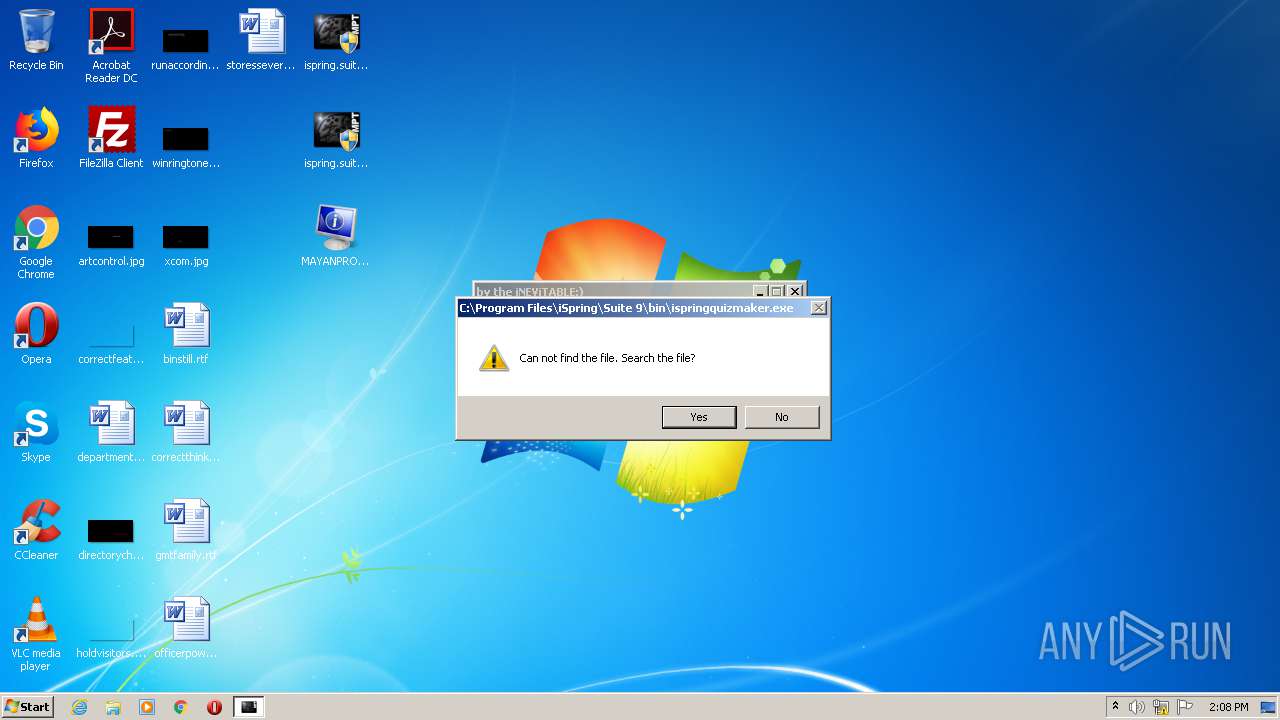
| 2884 | "C:\Users\admin\Desktop\ispring.suite.[x86]-MPT.exe" | C:\Users\admin\Desktop\ispring.suite.[x86]-MPT.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
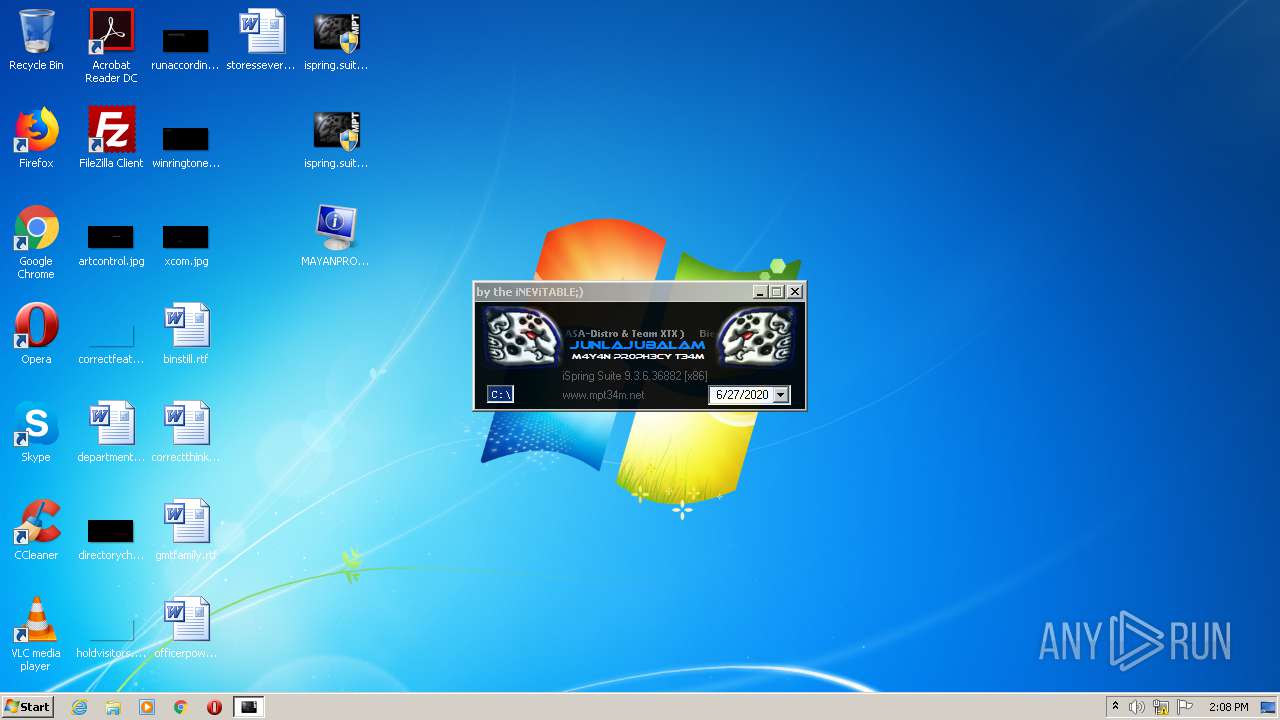
| 3088 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.mpt34m.net/ | C:\Program Files\Internet Explorer\iexplore.exe | — | ispring.suite.[x86]-MPT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3912 | "C:\Users\admin\Desktop\ispring.suite.[x86]-MPT.exe" | C:\Users\admin\Desktop\ispring.suite.[x86]-MPT.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 606
Read events
1 451
Write events
1 148
Delete events
7
Modification events
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\iSpring.Suite.Patch-MPT.zip | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\msinfo32.exe,-10001 |
Value: System Information File | |||
Executable files
3
Suspicious files
3
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1704 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1704.8270\MAYANPROPHECY.nfo | — | |
MD5:— | SHA256:— | |||
| 1704 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1704.8270\ispring.suite.[x86]-MPT.exe | — | |
MD5:— | SHA256:— | |||
| 1704 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1704.8270\ispring.suite.[x64]-MPT.exe | — | |
MD5:— | SHA256:— | |||
| 3088 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA8BAD018441A2592.TMP | — | |
MD5:— | SHA256:— | |||
| 3088 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF187838B7FCF2966A.TMP | — | |
MD5:— | SHA256:— | |||
| 3088 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF5020211623C382C5.TMP | — | |
MD5:— | SHA256:— | |||
| 3088 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC16746FDDC940948.TMP | — | |
MD5:— | SHA256:— | |||
| 3088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\RecoveryStore.{3C903403-B877-11EA-8526-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{3C903405-B877-11EA-8526-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Last Active\{3C903407-B877-11EA-8526-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2504 | iexplore.exe | GET | 302 | 91.223.82.39:80 | http://www.mpt34m.net/ | NL | html | 681 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2504 | iexplore.exe | 91.223.82.39:80 | www.mpt34m.net | Iws Networks LLC | NL | malicious |
2504 | iexplore.exe | 91.223.82.39:443 | www.mpt34m.net | Iws Networks LLC | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mpt34m.net |
| malicious |
mpt34m.net |
| malicious |