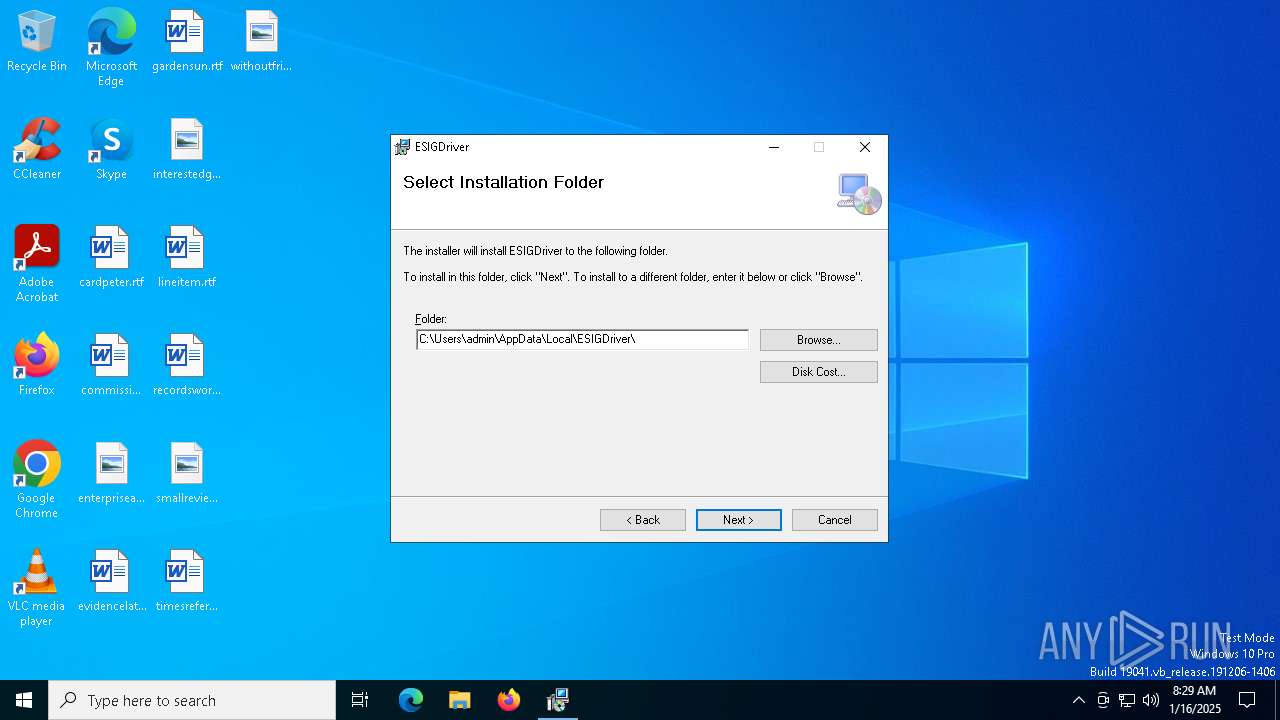
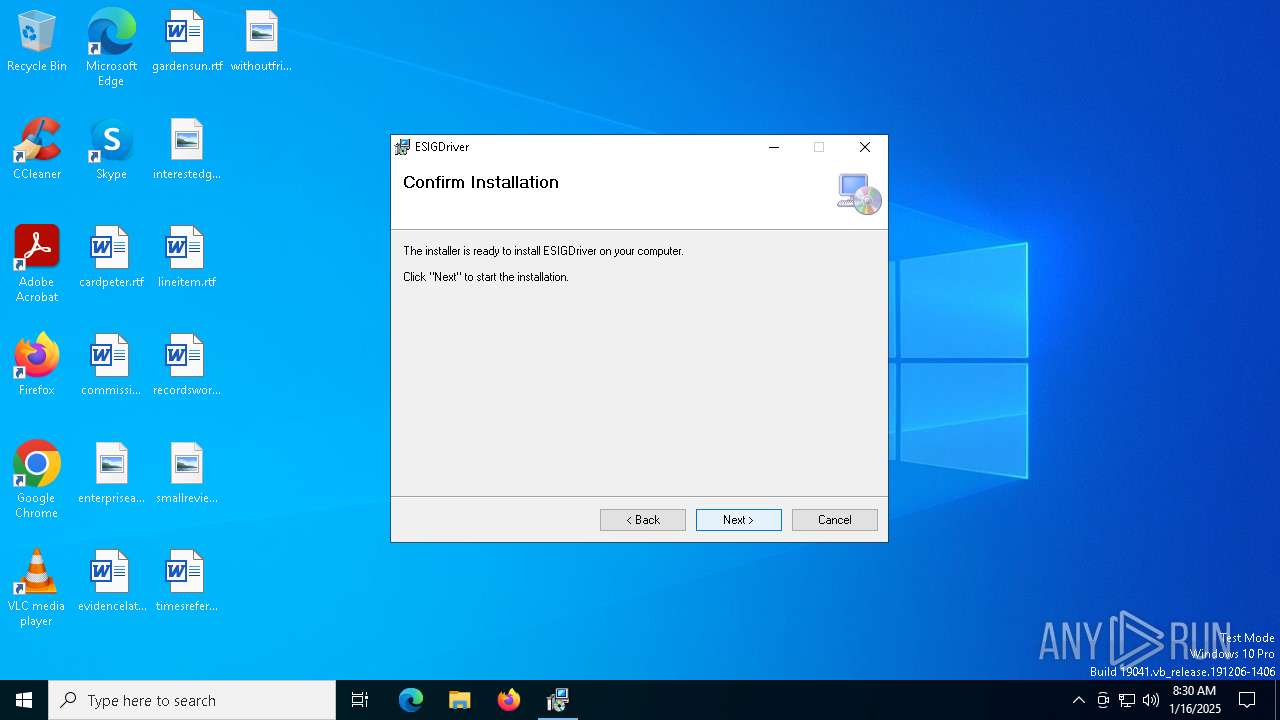
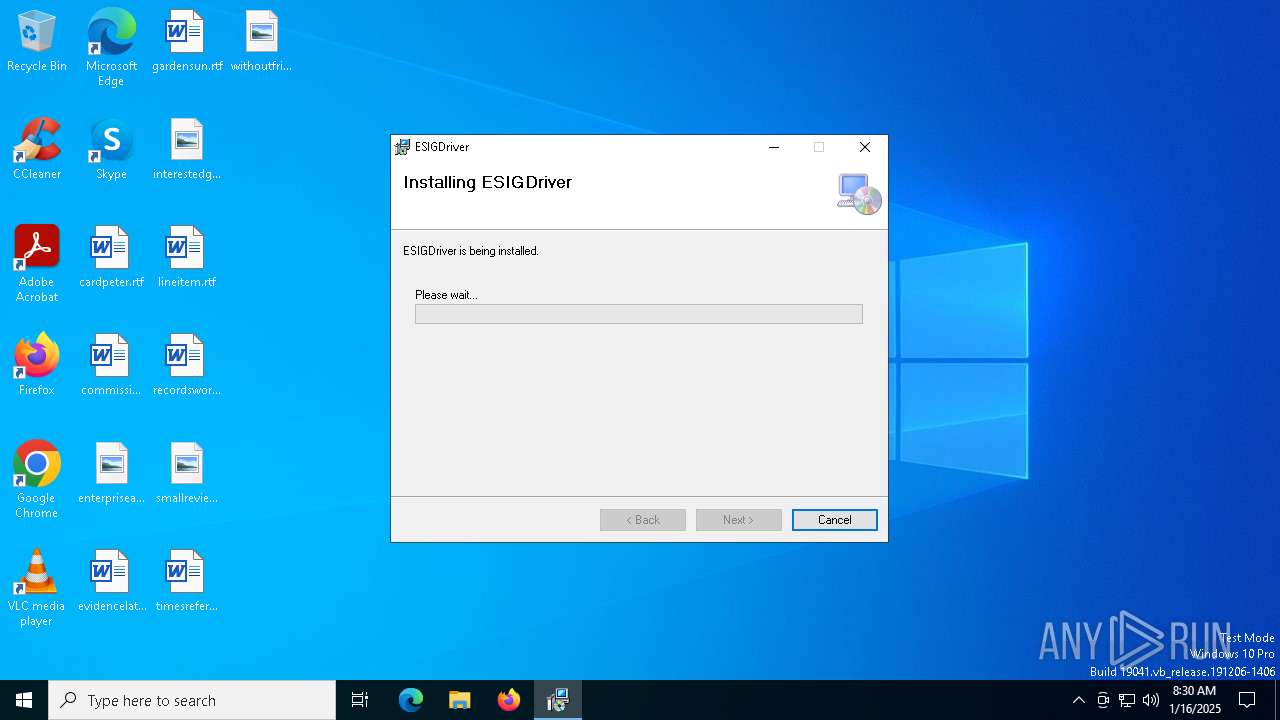
| File name: | ESIGDriverSetup.msi |
| Full analysis: | https://app.any.run/tasks/ed85e50b-67ac-4d73-8ec2-ab0111027662 |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2025, 08:29:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-msi |
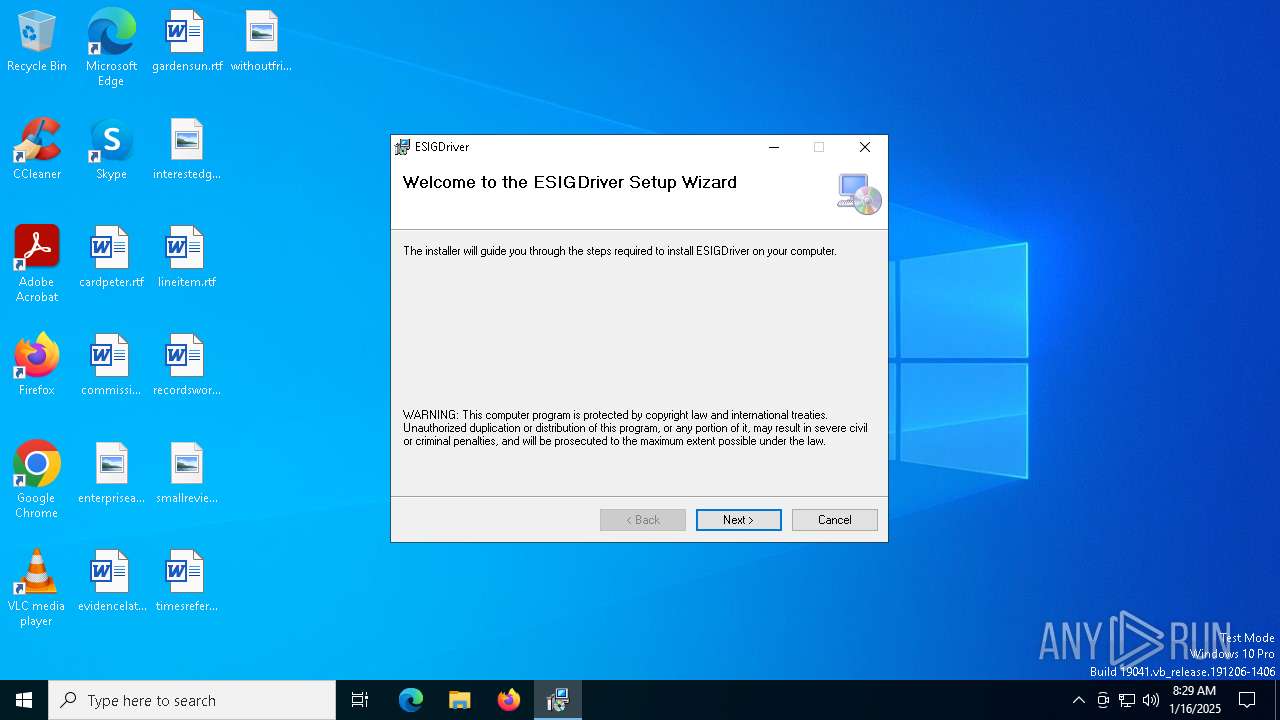
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 07:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: x64;1033, Number of Pages: 200, Revision Number: {49DF263E-884F-4424-BA76-D71B813C02C9}, Title: ESIGDriverSetup, Author: TIS, Last Saved Time/Date: Mon Sep 19 13:47:28 2022, Last Printed: Mon Sep 19 13:47:28 2022, Number of Words: 10 |
| MD5: | 826EE66774F35E6FC4CAABDB53257A53 |
| SHA1: | 36860EAFF51421A27F721EBD1E66ADD02F8D0326 |
| SHA256: | 69C2E44CA525D2ECA66373AE7EEE2D7C52B3ED763D3E9F653D6D545003D06591 |
| SSDEEP: | 98304:b0el1e4PIIrxVnbHh07ipPvz8ve+VvZ2QG8a+C2ksHhg/2jQAqfgiCFrFec6fW5Q:dUAomApe0kCY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 6728)
- msiexec.exe (PID: 6880)
Executes as Windows Service
- VSSVC.exe (PID: 3820)
Checks Windows Trust Settings
- msiexec.exe (PID: 6880)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6880)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6728)
The sample compiled with english language support
- msiexec.exe (PID: 6728)
- msiexec.exe (PID: 6880)
Creates files or folders in the user directory
- msiexec.exe (PID: 6728)
Checks proxy server information
- msiexec.exe (PID: 6728)
Checks supported languages
- msiexec.exe (PID: 6880)
- msiexec.exe (PID: 6928)
- msiexec.exe (PID: 7160)
- ESIGDriverCert.exe (PID: 6516)
Reads the software policy settings
- msiexec.exe (PID: 6728)
Reads the computer name
- msiexec.exe (PID: 6928)
- msiexec.exe (PID: 6880)
- msiexec.exe (PID: 7160)
- ESIGDriverCert.exe (PID: 6516)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6728)
- msiexec.exe (PID: 6880)
Create files in a temporary directory
- msiexec.exe (PID: 6928)
Manages system restore points
- SrTasks.exe (PID: 5628)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6880)
Creates a software uninstall entry
- msiexec.exe (PID: 6880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | x64;1033 |
| Pages: | 200 |
| RevisionNumber: | {49DF263E-884F-4424-BA76-D71B813C02C9} |
| Title: | ESIGDriverSetup |
| Subject: | - |
| Author: | TIS |
| Keywords: | - |
| Comments: | - |
| ModifyDate: | 2022:09:19 13:47:28 |
| LastPrinted: | 2022:09:19 13:47:28 |
| Words: | 10 |
Total processes
140
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3820 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ESIGDriverCert.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5628 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | "C:\Users\admin\AppData\Local\ESIGDriver\ESIGDriverCert.exe" | C:\Users\admin\AppData\Local\ESIGDriver\ESIGDriverCert.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ESIGDriverCert Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 6728 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\ESIGDriverSetup.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6880 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6928 | C:\Windows\syswow64\MsiExec.exe -Embedding 36DCE9560EBED8BC4F975E2E107C9045 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7160 | C:\Windows\syswow64\MsiExec.exe -Embedding C147843328D403B4B3220E8BE2D18DE9 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 790
Read events
9 445
Write events
327
Delete events
18
Modification events
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000AFF55ED6F067DB01E01A0000940F0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000945861D6F067DB01E01A0000940F0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000DDE718D7F067DB01E01A0000940F0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000534B1BD7F067DB01E01A00004C120000E803000001000000000000000000000004FCFD74678D9049832BAC452BD2164700000000000000000000000000000000 | |||
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000009281A6D6F067DB01E01A0000940F0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000009281A6D6F067DB01E01A0000940F0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000057D2A8D6F067DB01E01A0000940F0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000004736ABD6F067DB01E01A0000940F0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6880) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3820) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000FDFE24D7F067DB01EC0E0000FC110000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
35
Suspicious files
34
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6880 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6880 | msiexec.exe | C:\Windows\Installer\13eb0f.msi | — | |
MD5:— | SHA256:— | |||
| 6728 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_E6095CD2AECC9011BCD0D7B421356B17 | binary | |
MD5:EDFCFF31F2F44DEDE9339DE0FE66BAE1 | SHA256:F8C5E303C7B04172CA65BA6B67CBFA4B04597326E8A79A1E8F7FD46FEFD04453 | |||
| 6880 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:3D09285CDAA5BF2A9176F5A5C434442B | SHA256:84936B3B3100AAB4AF17A989ABCE57DE683FCF20FB743183632BCF323DEE803F | |||
| 6728 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_E6095CD2AECC9011BCD0D7B421356B17 | binary | |
MD5:798B9BFD53E25AF9671FE1A5DEA03796 | SHA256:64E61E91973E27590F01E484843618525BC0B565A4247DBF4DA8676E68EDA7A1 | |||
| 6728 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D7833C286363AD25C70511661A83D581_EA291FB41B9E630F0015855943F3AB30 | binary | |
MD5:FC645556E0862FAE643FC6E68DF06B9A | SHA256:F251B310A899DDDB707DFD50263C2DF34B935501E1F92EF208836C9A1864DB22 | |||
| 6728 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5E6F.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 6880 | msiexec.exe | C:\Windows\Installer\MSIEC28.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 6728 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5FB8.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 6728 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D7833C286363AD25C70511661A83D581_EA291FB41B9E630F0015855943F3AB30 | binary | |
MD5:2DE9A7EAB645457B0E7F62B2D98D2E0F | SHA256:C6FF2D77453780E86A43AA77B30FCAC1050EFF2BE0F84E344C0AC95CCA690B96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
35
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4056 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4056 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6728 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
420 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6728 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEB2iSDBvmyYY0ILgln0z02o%3D | unknown | — | — | whitelisted |
6484 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6728 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ5suEceKjAJbxseAmHFkQ9FrhTWQQUDuE6qFM6MdWKvsG7rWcaA4WtNA4CEFoDbc7hzkcqfvzVGBYg284%3D | unknown | — | — | whitelisted |
420 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4056 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4056 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1176 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |