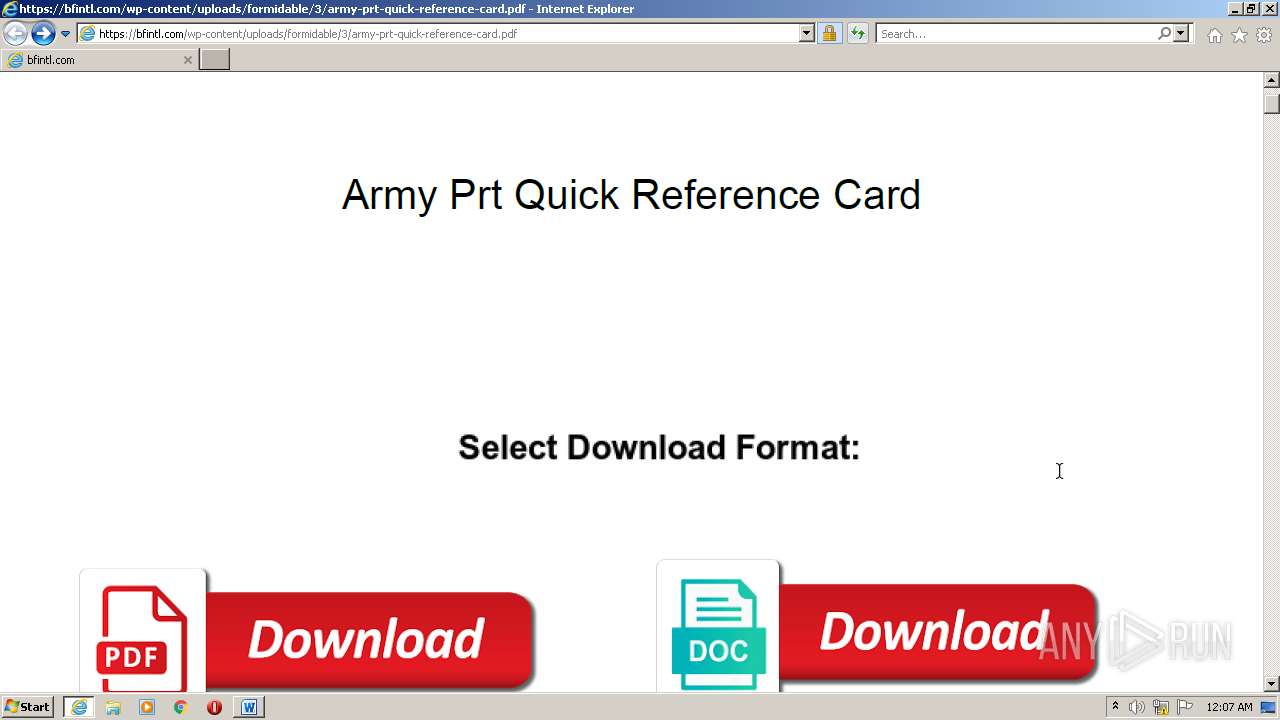
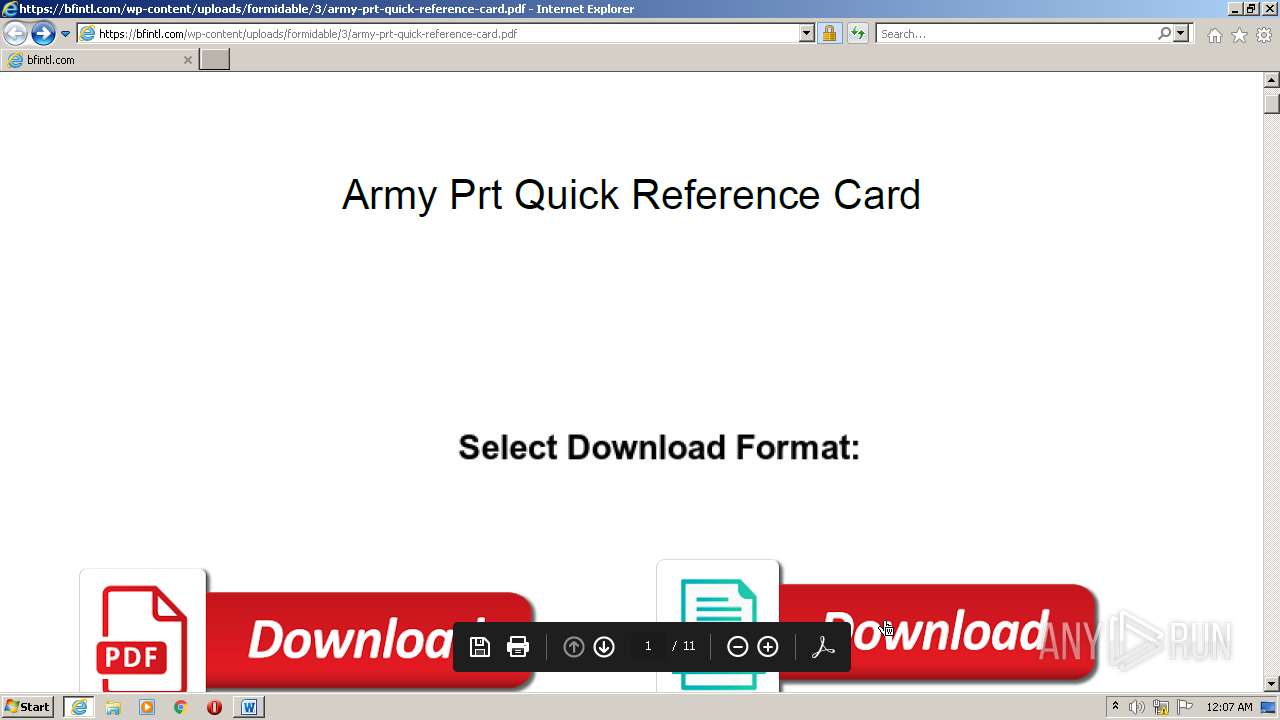
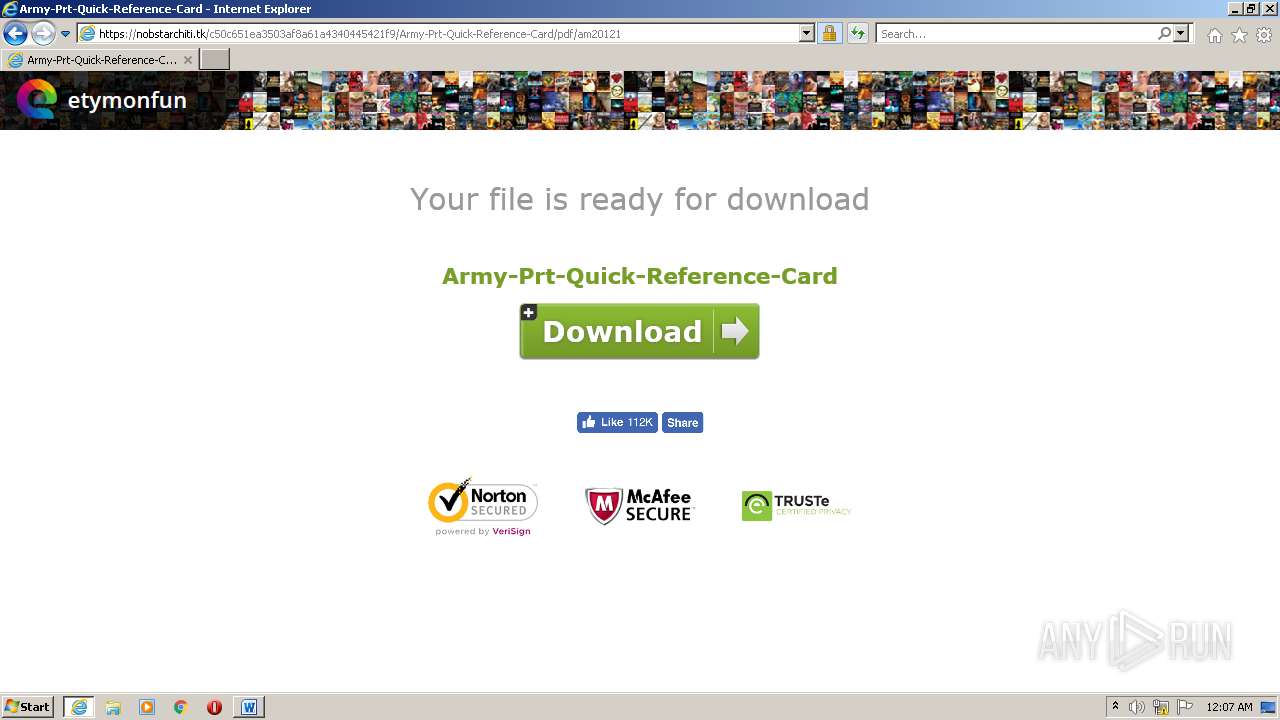
| URL: | https://bfintl.com/wp-content/uploads/formidable/3/army-prt-quick-reference-card.pdf |
| Full analysis: | https://app.any.run/tasks/52f53478-0096-40ca-9494-67d741346e74 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 23:02:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 78C16DECB8BA45648B94F97E09F1B21C |
| SHA1: | BE30A48BE778C8AFE4BC0A2468F32E05DC5DABF3 |
| SHA256: | 699BE1200E8D65E91E7BB36F163C348639CF11812B704C0EF07AC3C74B94F4D8 |
| SSDEEP: | 3:N8+TZIJVOlAQyg/KEMZqnuGAIb31:2UgVOlAZg/KlwnuG131 |
MALICIOUS
Drops executable file immediately after starts
- RdrCEF.exe (PID: 1252)
- AdobeARM.exe (PID: 308)
- RdrCEF.exe (PID: 2052)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3468)
Checks supported languages
- AdobeARM.exe (PID: 308)
- Reader_sl.exe (PID: 3104)
- notepad++.exe (PID: 3404)
- msiexec.exe (PID: 3212)
Reads the computer name
- AdobeARM.exe (PID: 308)
- msiexec.exe (PID: 3212)
Creates files in the program directory
- AdobeARM.exe (PID: 308)
Drops a file with a compile date too recent
- RdrCEF.exe (PID: 1252)
- AdobeARM.exe (PID: 308)
- RdrCEF.exe (PID: 2052)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 308)
Reads default file associations for system extensions
- iexplore.exe (PID: 3456)
- WINWORD.EXE (PID: 120)
- WINWORD.EXE (PID: 2432)
Reads Windows owner or organization settings
- msiexec.exe (PID: 3212)
Reads the Windows organization settings
- msiexec.exe (PID: 3212)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3456)
Application launched itself
- iexplore.exe (PID: 3456)
- AcroRd32.exe (PID: 3244)
- RdrCEF.exe (PID: 1252)
- AcroRd32.exe (PID: 2540)
- RdrCEF.exe (PID: 2052)
Reads the computer name
- iexplore.exe (PID: 3468)
- iexplore.exe (PID: 3456)
- AcroRd32.exe (PID: 3244)
- AcroRd32.exe (PID: 1492)
- RdrCEF.exe (PID: 1252)
- WINWORD.EXE (PID: 120)
- WINWORD.EXE (PID: 3964)
- WINWORD.EXE (PID: 2432)
- AcroRd32.exe (PID: 2540)
- AcroRd32.exe (PID: 2608)
- RdrCEF.exe (PID: 2052)
Checks supported languages
- iexplore.exe (PID: 3456)
- iexplore.exe (PID: 3468)
- AcroRd32.exe (PID: 3244)
- RdrCEF.exe (PID: 1252)
- AcroRd32.exe (PID: 1492)
- RdrCEF.exe (PID: 3268)
- RdrCEF.exe (PID: 2952)
- RdrCEF.exe (PID: 3240)
- RdrCEF.exe (PID: 2060)
- RdrCEF.exe (PID: 460)
- RdrCEF.exe (PID: 2592)
- WINWORD.EXE (PID: 120)
- WINWORD.EXE (PID: 3216)
- WINWORD.EXE (PID: 3964)
- WINWORD.EXE (PID: 2432)
- AcroRd32.exe (PID: 2540)
- AcroRd32.exe (PID: 2608)
- RdrCEF.exe (PID: 2052)
- RdrCEF.exe (PID: 288)
- RdrCEF.exe (PID: 3448)
- RdrCEF.exe (PID: 496)
- RdrCEF.exe (PID: 1264)
- RdrCEF.exe (PID: 700)
- RdrCEF.exe (PID: 1144)
- WINWORD.EXE (PID: 3608)
Reads settings of System Certificates
- iexplore.exe (PID: 3468)
- iexplore.exe (PID: 3456)
- AcroRd32.exe (PID: 3244)
- RdrCEF.exe (PID: 1252)
- AdobeARM.exe (PID: 308)
- AcroRd32.exe (PID: 2540)
Searches for installed software
- AcroRd32.exe (PID: 3244)
- AcroRd32.exe (PID: 1492)
- AcroRd32.exe (PID: 2540)
- AcroRd32.exe (PID: 2608)
Checks Windows Trust Settings
- iexplore.exe (PID: 3468)
- iexplore.exe (PID: 3456)
- AcroRd32.exe (PID: 3244)
- AdobeARM.exe (PID: 308)
- AcroRd32.exe (PID: 2540)
Reads CPU info
- AcroRd32.exe (PID: 1492)
- AcroRd32.exe (PID: 2608)
Reads internet explorer settings
- iexplore.exe (PID: 3468)
Changes settings of System certificates
- iexplore.exe (PID: 3456)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3456)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3468)
Manual execution by user
- WINWORD.EXE (PID: 120)
- WINWORD.EXE (PID: 3216)
- WINWORD.EXE (PID: 3964)
- WINWORD.EXE (PID: 2432)
- notepad++.exe (PID: 3404)
- WINWORD.EXE (PID: 3608)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3456)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 120)
- WINWORD.EXE (PID: 3216)
- WINWORD.EXE (PID: 3964)
- WINWORD.EXE (PID: 2432)
- WINWORD.EXE (PID: 3608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
81
Monitored processes
31
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\Army-Prt-Quick-Reference-Card.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 288 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1184,18023891743285570481,5223221610722059987,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=9182056254433274592 --mojo-platform-channel-handle=1208 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 308 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:20.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.39.9311 Modules
| |||||||||||||||
| 460 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1184,6894814315681393517,12504058350164260510,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=8639592367051923097 --mojo-platform-channel-handle=1476 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 496 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1184,18023891743285570481,5223221610722059987,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=5391788848869133795 --mojo-platform-channel-handle=1396 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 700 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1184,18023891743285570481,5223221610722059987,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13644291602041282123 --renderer-client-id=6 --mojo-platform-channel-handle=1208 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1144 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1184,18023891743285570481,5223221610722059987,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16588030134132621597 --renderer-client-id=7 --mojo-platform-channel-handle=1372 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1252 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1184,18023891743285570481,5223221610722059987,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=13379406442360872446 --mojo-platform-channel-handle=1412 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer /o /eo /l /b /id 3468 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
49 973
Read events
48 161
Write events
1 502
Delete events
310
Modification events
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30977695 | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30977695 | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3456) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
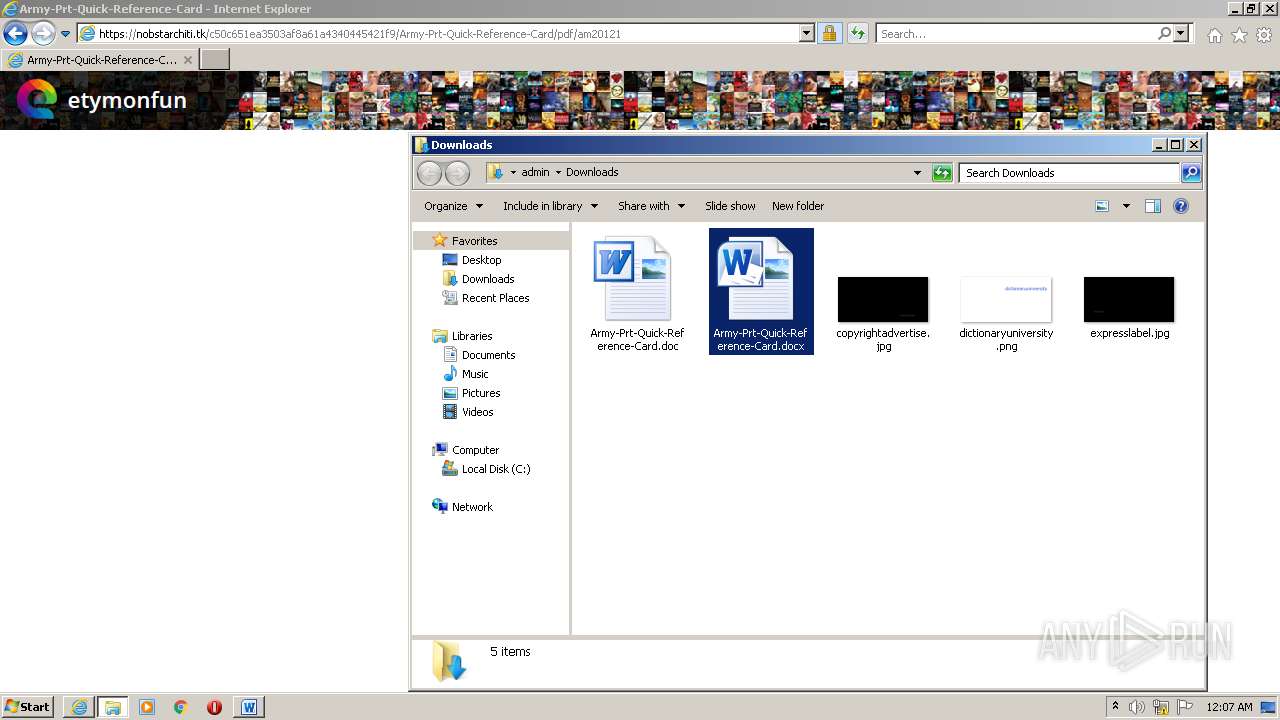
Executable files
3
Suspicious files
188
Text files
36
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3456 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
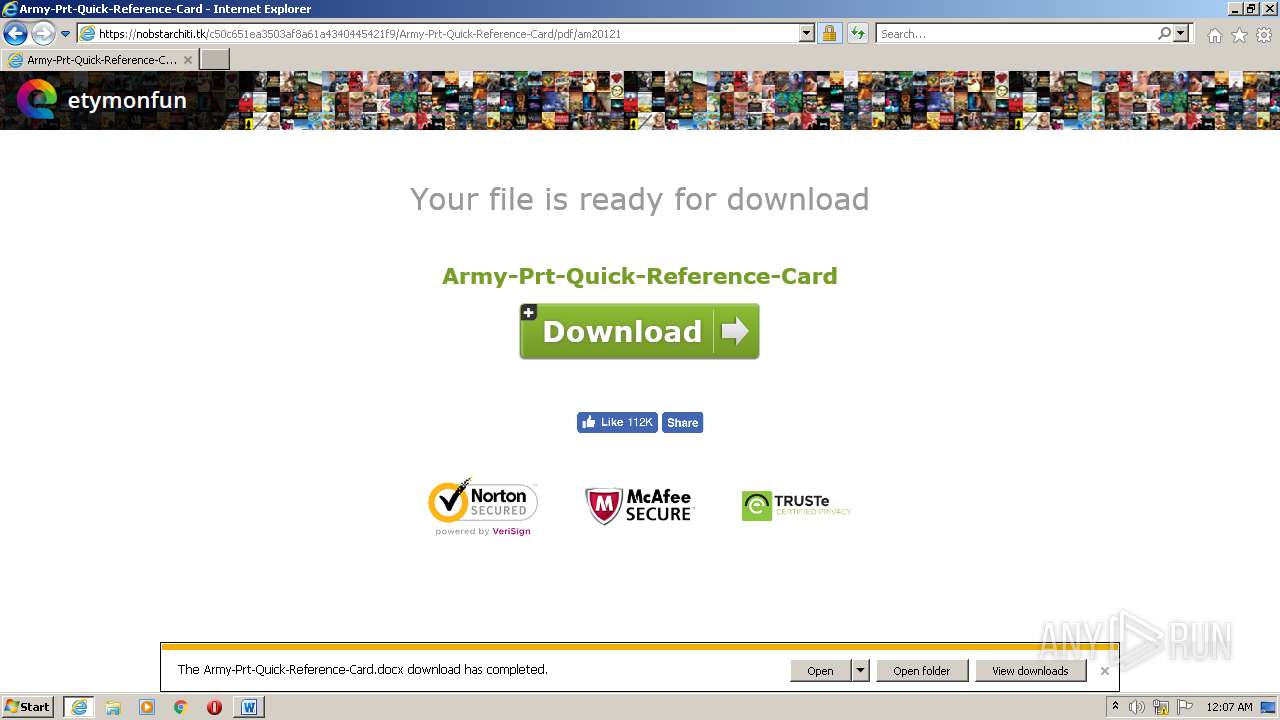
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\army-prt-quick-reference-card[1].pdf | ||
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1252 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:— | SHA256:— | |||
| 1492 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\UserCache.bin | binary | |
MD5:— | SHA256:— | |||
| 1252 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
52
DNS requests
23
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3456 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
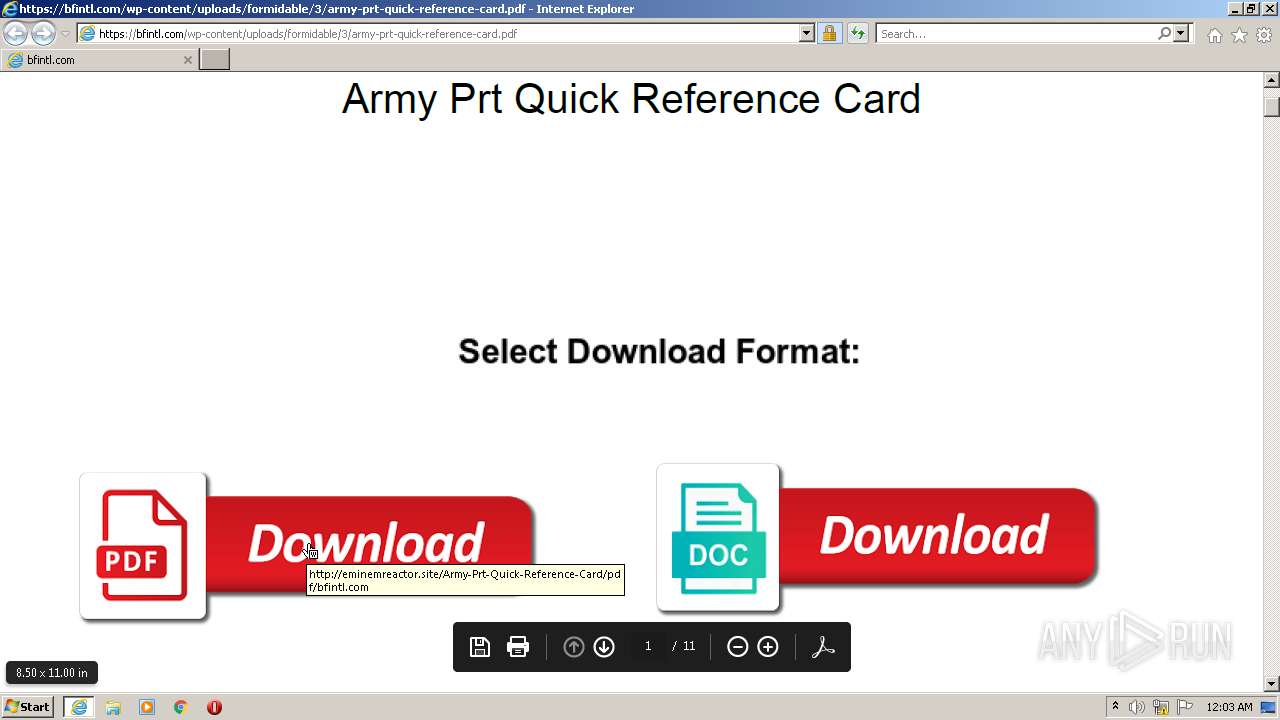
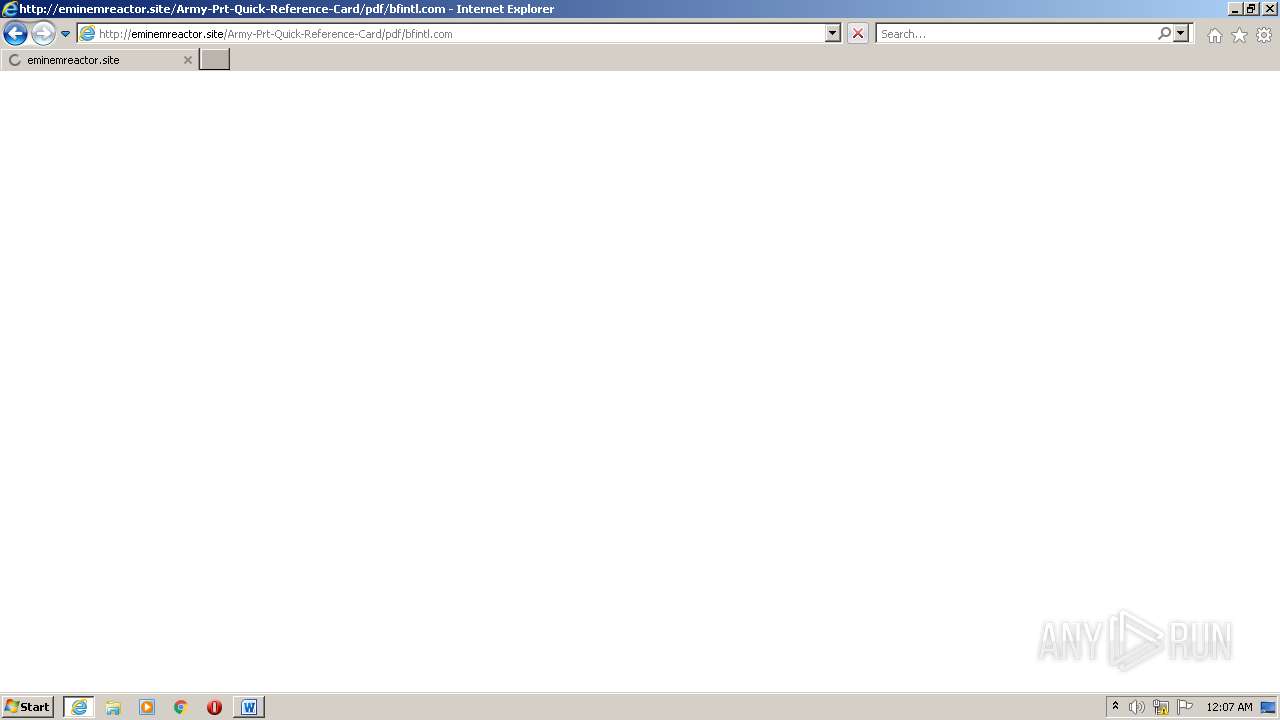
3468 | iexplore.exe | GET | 200 | 104.21.83.48:80 | http://eminemreactor.site/Army-Prt-Quick-Reference-Card/pdf/bfintl.com | US | text | 153 b | malicious |
3468 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3244 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3456 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3456 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
3468 | iexplore.exe | GET | 200 | 104.21.83.48:80 | http://eminemreactor.site/Army-Prt-Quick-Reference-Card/pdf/bfintl.com | US | text | 153 b | malicious |
3468 | iexplore.exe | GET | 200 | 8.253.95.249:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e28722ac4d077435 | US | compressed | 4.70 Kb | whitelisted |
3456 | iexplore.exe | GET | 404 | 104.21.83.48:80 | http://eminemreactor.site/favicon.ico | US | binary | 20 b | malicious |
3456 | iexplore.exe | GET | 404 | 104.21.83.48:80 | http://eminemreactor.site/favicon.ico | US | binary | 20 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
928 | svchost.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
3468 | iexplore.exe | 172.67.195.235:443 | bfintl.com | — | US | unknown |
3468 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3456 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3468 | iexplore.exe | 8.253.95.249:80 | ctldl.windowsupdate.com | Global Crossing | US | suspicious |
3456 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1252 | RdrCEF.exe | 23.35.236.137:443 | geo2.adobe.com | Zayo Bandwidth Inc | US | suspicious |
3456 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
928 | svchost.exe | 23.48.23.25:443 | ardownload3.adobe.com | TRUE INTERNET Co.,Ltd. | US | suspicious |
3456 | iexplore.exe | 104.21.83.48:80 | eminemreactor.site | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bfintl.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
928 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ga Domain |
3468 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.ga) in TLS SNI |
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3468 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.ga) in TLS SNI |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|