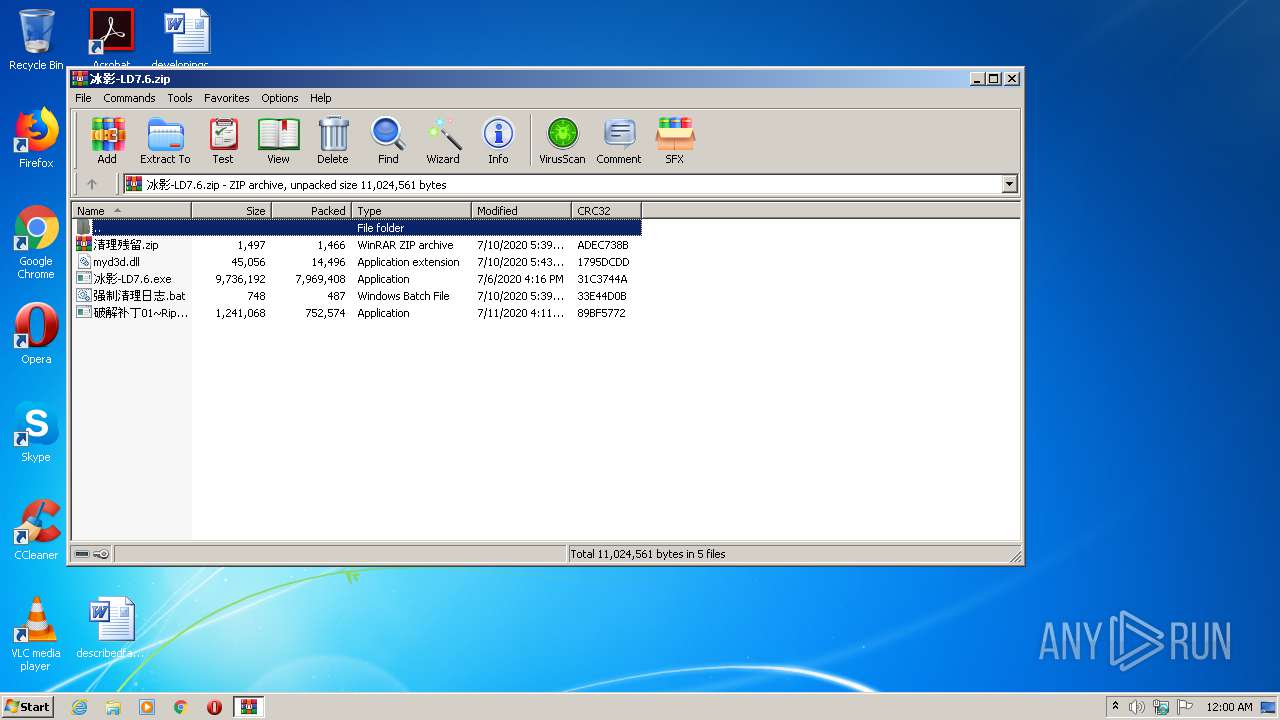
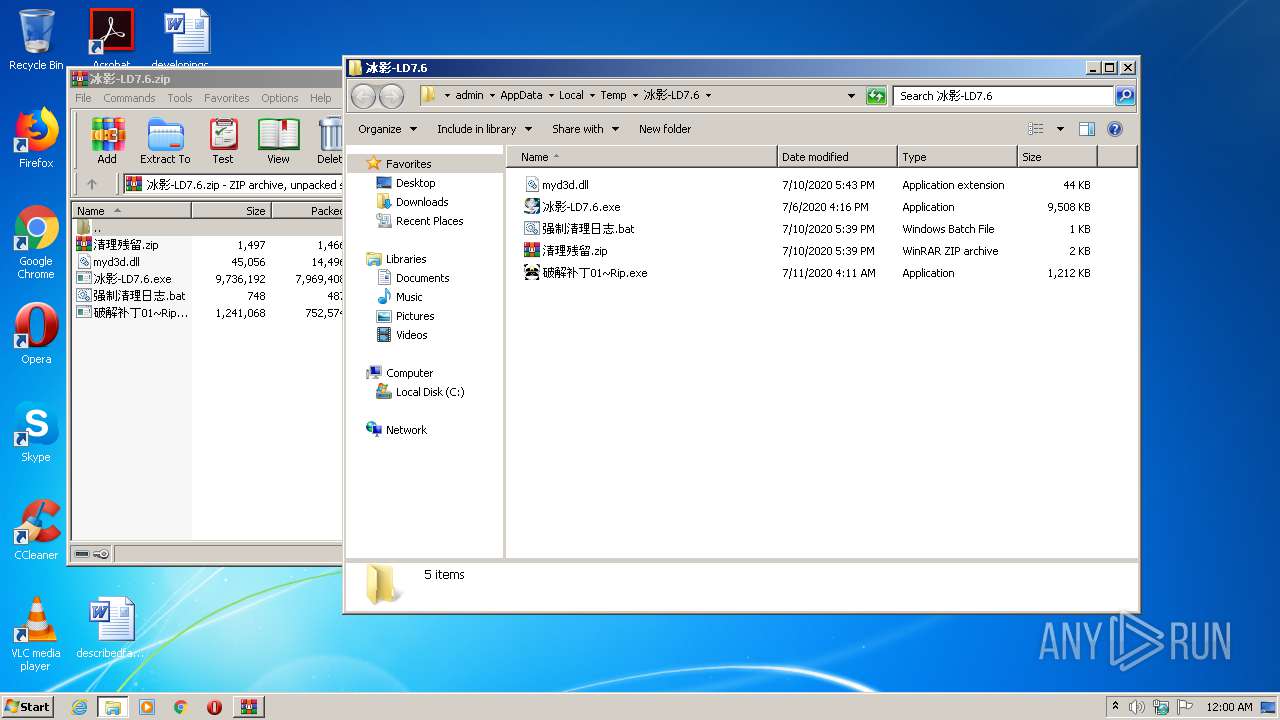
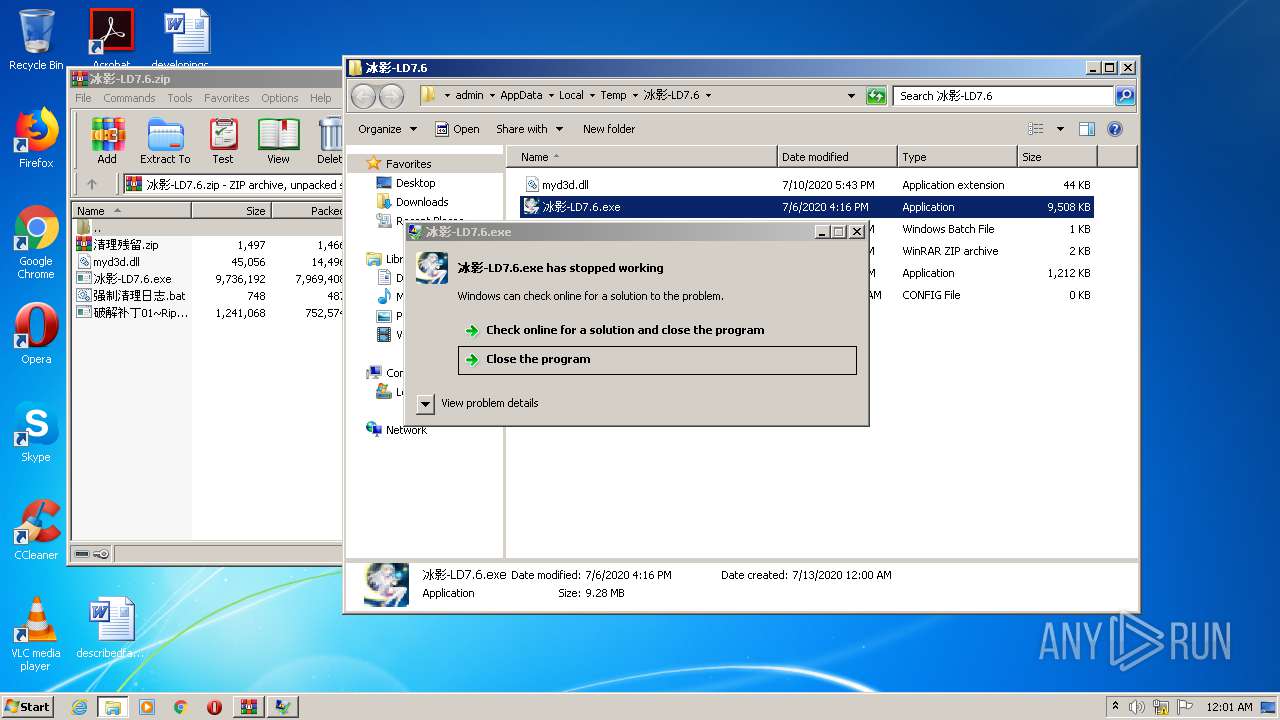
| File name: | 冰影-LD7.6.zip |
| Full analysis: | https://app.any.run/tasks/854c0d77-a16b-467e-bba5-f409a1e90c64 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 23:00:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 12717BB161B26457D60C8889A5F8A11A |
| SHA1: | 4DE0AC3A17370116A412A32EB535CEBDFE283F52 |
| SHA256: | 699A94781124C41CB11CFAFA3F8423B296AFA1B69E17723A06D26FD07C5314E1 |
| SSDEEP: | 196608:aFnBiQNQ0W5I7dbHp3y70Q1+VPEsP4bVqBWell6O1kiHq04snMBq:amADly7UpEsPjWm9kiHcsMY |
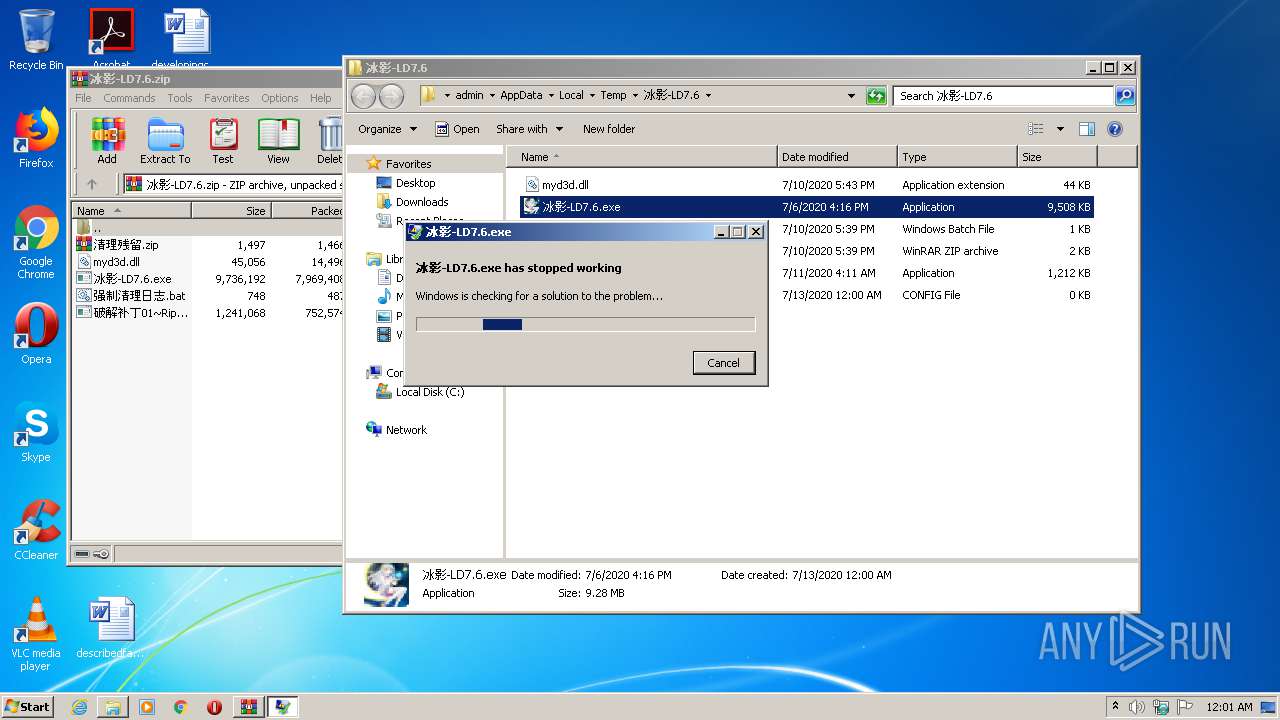
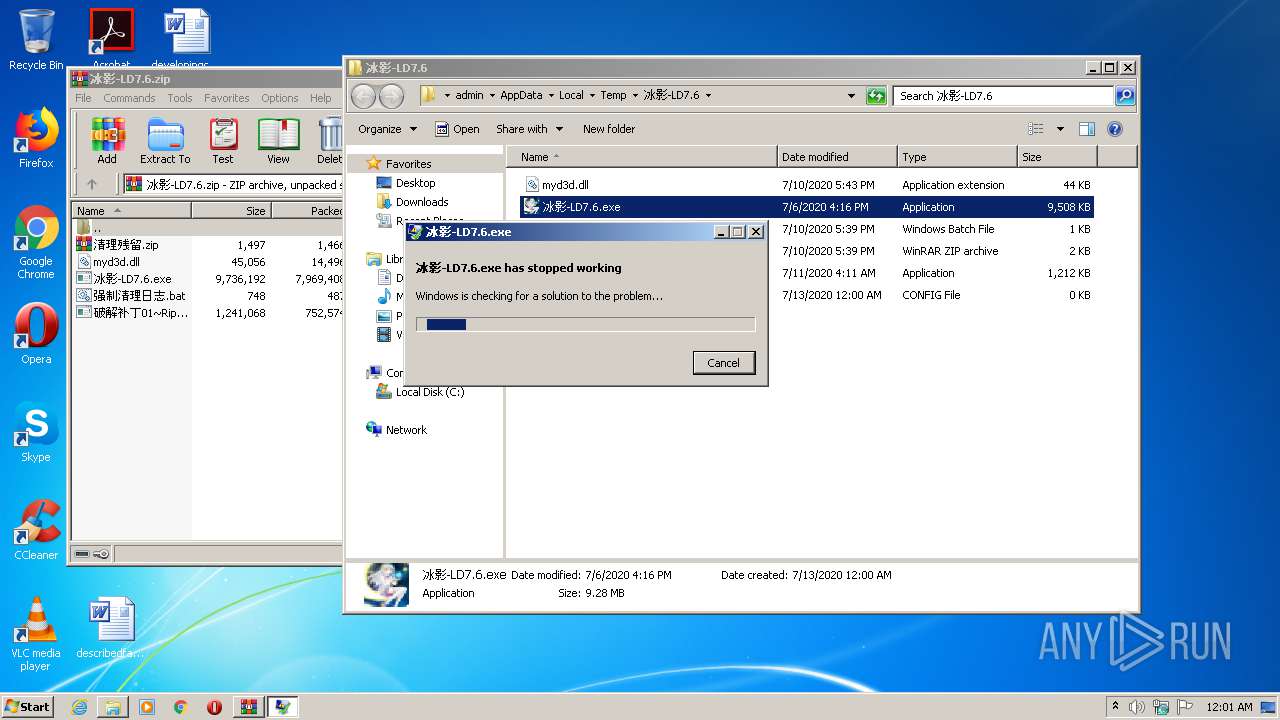
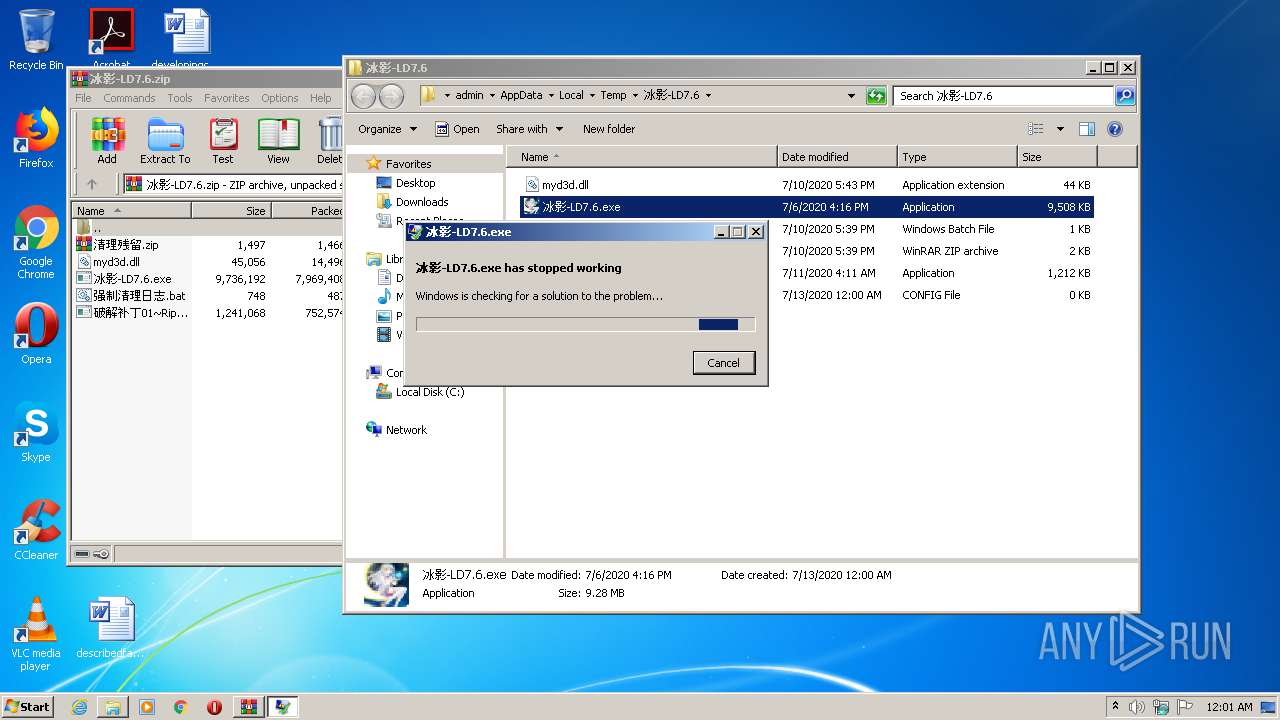
MALICIOUS
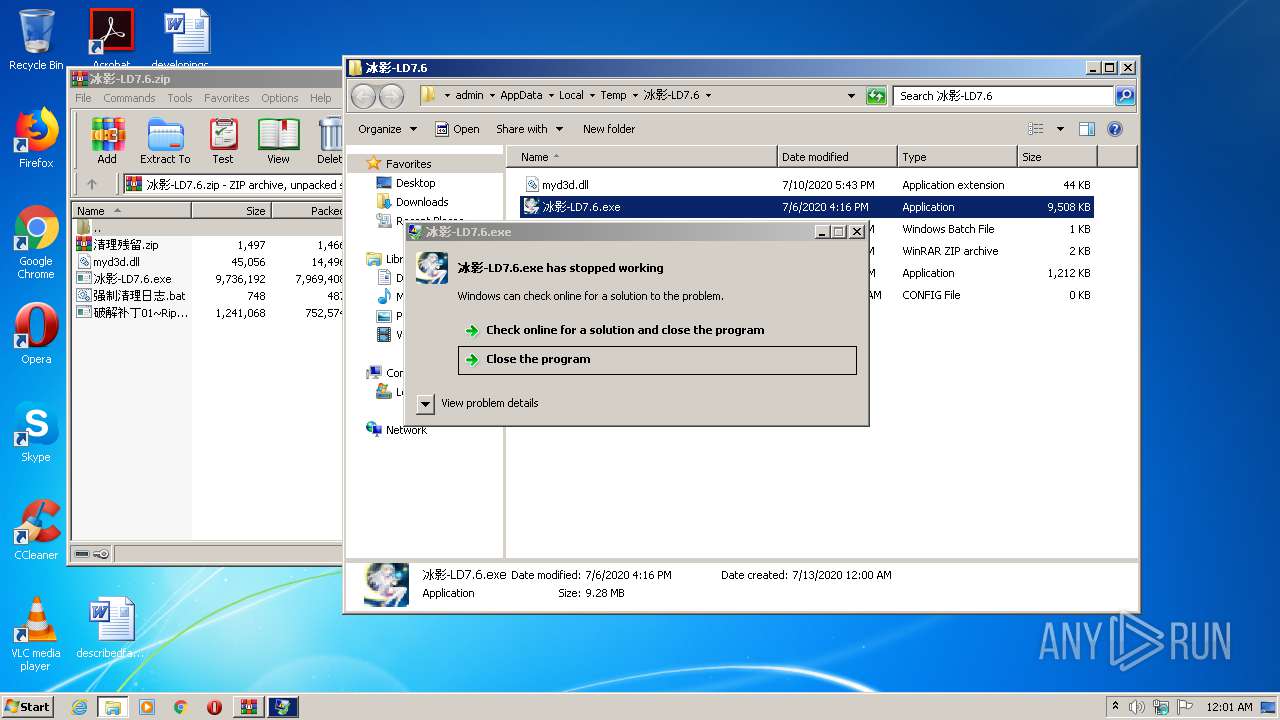
Application was dropped or rewritten from another process
- 冰影-LD7.6.exe (PID: 3004)
- 冰影-LD7.6.exe (PID: 2624)
- 冰影-LD7.6.exe (PID: 2616)
Loads dropped or rewritten executable
- explorer.exe (PID: 292)
SUSPICIOUS
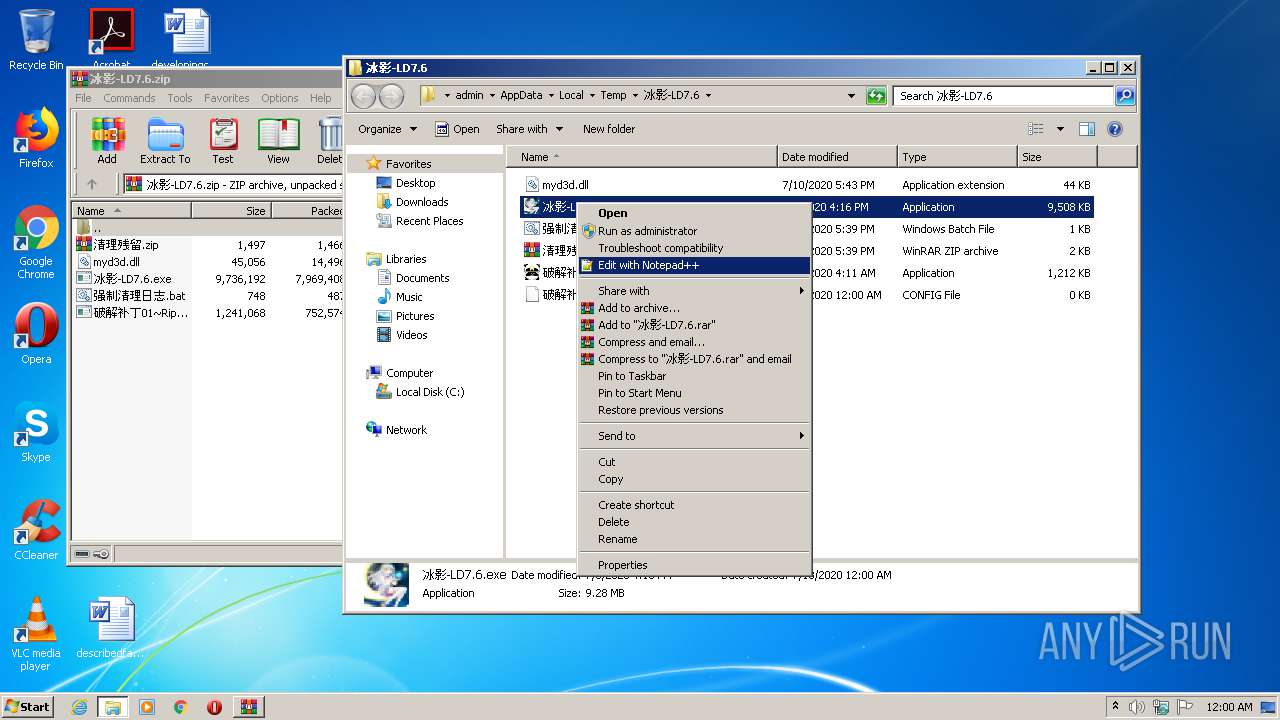
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3312)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:07:06 23:16:13 |
| ZipCRC: | 0x31c3744a |
| ZipCompressedSize: | 7969408 |
| ZipUncompressedSize: | 9736192 |
| ZipFileName: | ??Ӱ-LD7.6.exe |
Total processes
45
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2616 | "C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\冰影-LD7.6.exe" | C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\冰影-LD7.6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2624 | "C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\冰影-LD7.6.exe" | C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\冰影-LD7.6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 2764 | "C:\Windows\system32\wermgr.exe" "-outproc" "292" "2760" | C:\Windows\system32\wermgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3004 | "C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\冰影-LD7.6.exe" | C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\冰影-LD7.6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 3312 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\冰影-LD7.6.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
981
Read events
840
Write events
141
Delete events
0
Modification events
| (PID) Process: | (292) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\冰影-LD7.6.zip | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3312) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 292 | explorer.exe | C:\Users\admin\AppData\Local\Temp\TabAE6D.tmp | — | |
MD5:— | SHA256:— | |||
| 292 | explorer.exe | C:\Users\admin\AppData\Local\Temp\{5bb56fb0-dce9-4696-887a-6056d20f740e}\appcompat.txt | — | |
MD5:— | SHA256:— | |||
| 292 | explorer.exe | C:\Users\admin\AppData\Local\Temp\OutofProcReport2666329.txt | — | |
MD5:— | SHA256:— | |||
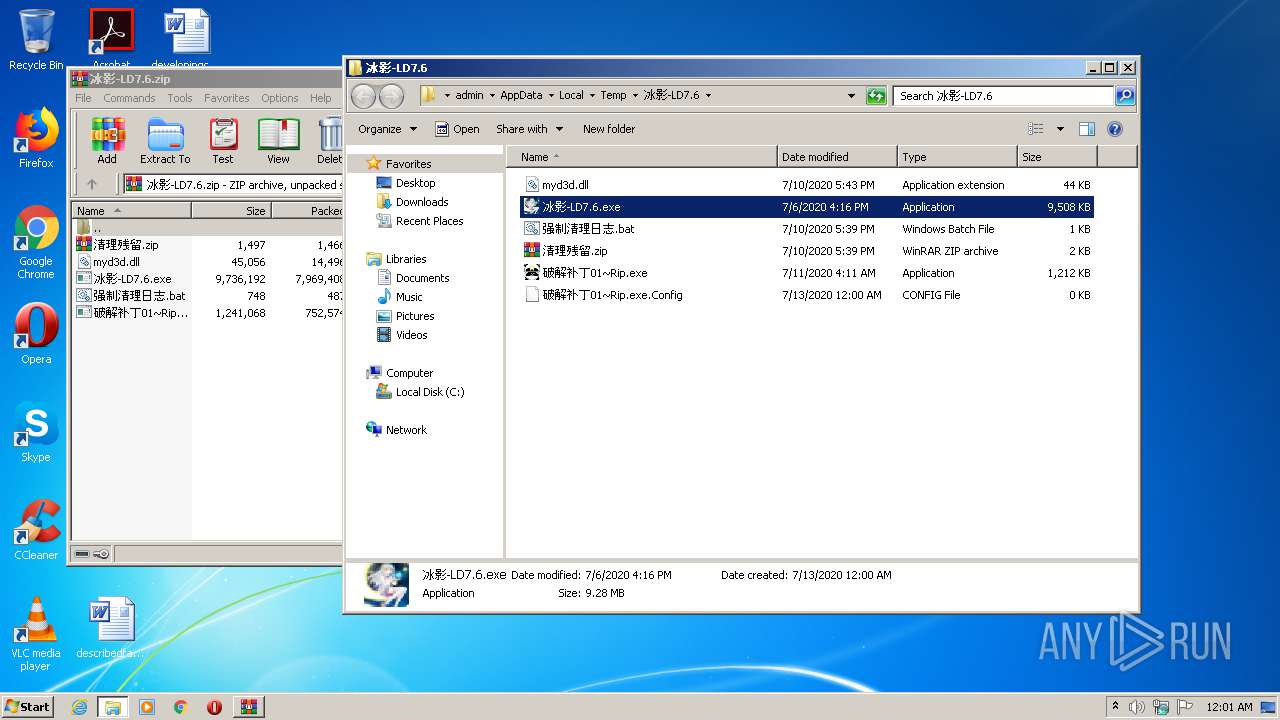
| 3312 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\强制清理日志.bat | text | |
MD5:— | SHA256:— | |||
| 3312 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\清理残留.zip | compressed | |
MD5:— | SHA256:— | |||
| 3312 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\冰影-LD7.6.exe | executable | |
MD5:— | SHA256:— | |||
| 3312 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\破解补丁01~Rip.exe | executable | |
MD5:— | SHA256:— | |||
| 3312 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\冰影-LD7.6\myd3d.dll | executable | |
MD5:7C0D03B2CCF87473B9809C2EC1AD6A15 | SHA256:3F966C651A622CF9D11395D07CD266E2B7671C8579A8730E05BD7DFC1226D34E | |||
| 2764 | wermgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\NonCritical_冰影-LD7.6.exe_4bf9a379673dd2a6ba88c25c292f27e8f0618a_cab_0ae4aecb\appcompat.txt | xml | |
MD5:— | SHA256:— | |||
| 2764 | wermgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\NonCritical_冰影-LD7.6.exe_4bf9a379673dd2a6ba88c25c292f27e8f0618a_cab_0ae4aecb\Report.wer | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
400 | WerFault.exe | GET | — | 52.158.209.219:80 | http://watson.microsoft.com/StageOne/%E5%86%B0%E5%BD%B1-LD7_6_exe/0_0_0_0/5f033ffe/%E5%86%B0%E5%BD%B1-LD7_6_exe/0_0_0_0/5f033ffe/c0000005/0000dceb.htm?LCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=DELL&SPN=DELL&BV=DELL&MID=3ADE2C42-4AB9-49B7-B142-BE9AEEA69063 | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1924 | WerFault.exe | 52.158.209.219:80 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
400 | WerFault.exe | 52.158.209.219:80 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1924 | WerFault.exe | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |
1924 | WerFault.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
400 | WerFault.exe | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |
Process | Message |
|---|---|
冰影-LD7.6.exe | FTH: (2616): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|